Challenge 2 - garbage
Ok cool. That wasn't too bad at all. I have 1 point after chal-1-fiddler yay!
This challenge is also worth 1 point.
After unzip there are 2 files.
Alright, I ran strings on garbage.exe and there wasn’t much of note beyond the fact that this is definitely a Windows binary. I need to open this in a hex editor. xxd is included with Kali.
| ~/cybersecurity/flare-on/2020/2-garbage ··············································· 14:09:00 ─╮
❯ xxd garbage.exe ─╯
00000000: 4d5a 9000 0300 0000 0400 0000 ffff 0000 MZ..............
00000010: b800 0000 0000 0000 4000 0000 0000 0000 ........@.......
00000020: 0000 0000 0000 0000 0000 0000 0000 0000 ................
00000030: 0000 0000 0000 0000 0000 0000 f800 0000 ................
00000040: 0e1f ba0e 00b4 09cd 21b8 014c cd21 5468 ........!..L.!Th
00000050: 6973 2070 726f 6772 616d 2063 616e 6e6f is program canno
00000060: 7420 6265 2072 756e 2069 6e20 444f 5320 t be run in DOS
00000070: 6d6f 6465 2e0d 0d0a 2400 0000 0000 0000 mode....$.......
00000080: 5478 9d12 1019 f341 1019 f341 1019 f341 Tx.....A...A...A
00000090: 4b71 f040 1a19 f341 4b71 f640 9a19 f341 Kq.@...AKq.@...A
000000a0: 4b71 f740 0219 f341 9172 f640 3519 f341 Kq.@...A.r.@5..A
000000b0: 9172 f740 0119 f341 9172 f040 0119 f341 .r.@...A.r.@...A
000000c0: 4b71 f240 1519 f341 1019 f241 4219 f341 Kq.@...A...AB..A
000000d0: 2675 fa40 1119 f341 2675 0c41 1119 f341 &u.@...A&u.A...A
000000e0: 2675 f140 1119 f341 5269 6368 1019 f341 &u.@...ARich...A
000000f0: 0000 0000 0000 0000 5045 0000 4c01 0300 ........PE..L...
00000100: 73e0 a25e 0000 0000 0000 0000 e000 0201 s..^............
...
This is junk. The MZ magic byte stands for Portable Executable though, so I analyzed the exe in pestudio. This revealed that the binary was packaged by UPX. After another search I dowloaded the UPX packager from the projects github.
Came back to this after a few days. I ran upx -d on garbage.exe on Kali.
| ~/cybersecurity/flare-on/2020/2-garbage ······················································ 14:11:14 ─╮
❯ upx -d -o garbage.upx.exe copy1.garbage.exe ─╯
Ultimate Packer for eXecutables
Copyright (C) 1996 - 2020
UPX 3.96 Markus Oberhumer, Laszlo Molnar & John Reiser Jan 23rd 2020
File size Ratio Format Name
-------------------- ------ ----------- -----------
upx: copy1.garbage.exe: OverlayException: invalid overlay size; file is possibly corrupt
Unpacked 1 file: 0 ok, 1 error.
Searching that error, I found this web page. https://www.sciencedirect.com/topics/computer-science/malware-incident
This next link describes unpacking a upx packed file with ollydbg. It also gives a good rundown on what packing is, and what the unpacking overall process looks like. https://sgros-students.blogspot.com/2014/08/manual-unpacking-of-upx-304.html
I also found this stackexchange post: https://reverseengineering.stackexchange.com/questions/16087/packed-pe-file-and-weird-header
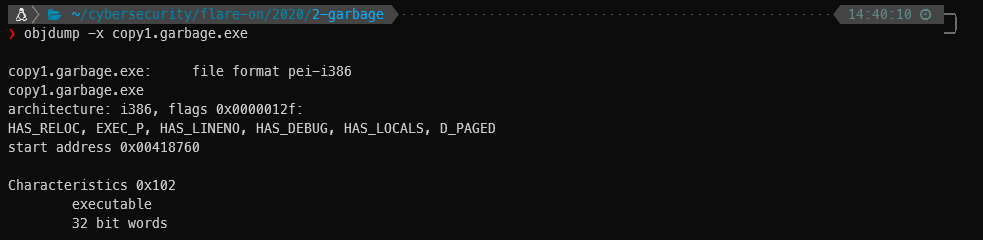
Running objdump -x to dump the headers gave me a few bits of information, including the start address, which idafree was bugging me for when I was doing this last weekend. It also gives me the address of EntryPoint, (00018760), base of code, base of data, section alignmetn, etc.
| ~/cybersecurity/flare-on/2020/2-garbage ······················································ 14:40:10 ─╮
❯ objdump -x copy1.garbage.exe ─╯
copy1.garbage.exe: file format pei-i386
copy1.garbage.exe
architecture: i386, flags 0x0000012f:
HAS_RELOC, EXEC_P, HAS_LINENO, HAS_DEBUG, HAS_LOCALS, D_PAGED
start address 0x00418760
Characteristics 0x102
executable
32 bit words
Time/Date Fri Apr 24 08:49:55 2020
Magic 010b (PE32)
MajorLinkerVersion 14
MinorLinkerVersion 21
SizeOfCode 0000a000
SizeOfInitializedData 00001000
SizeOfUninitializedData 0000e000
AddressOfEntryPoint 00018760
BaseOfCode 0000f000
BaseOfData 00019000
ImageBase 00400000
SectionAlignment 00001000
FileAlignment 00000200
MajorOSystemVersion 6
MinorOSystemVersion 0
MajorImageVersion 0
MinorImageVersion 0
MajorSubsystemVersion 6
MinorSubsystemVersion 0
Win32Version 00000000
SizeOfImage 0001a000
SizeOfHeaders 00001000
CheckSum 00000000
Subsystem 00000003 (Windows CUI)
DllCharacteristics 00008140
SizeOfStackReserve 00100000
SizeOfStackCommit 00001000
SizeOfHeapReserve 00100000
SizeOfHeapCommit 00001000
LoaderFlags 00000000
NumberOfRvaAndSizes 00000010
The Data Directory
Entry 0 00000000 00000000 Export Directory [.edata (or where ever we found it)]
Entry 1 000191dc 000000c0 Import Directory [parts of .idata]
Entry 2 00019000 000001dc Resource Directory [.rsrc]
Entry 3 00000000 00000000 Exception Directory [.pdata]
Entry 4 00000000 00000000 Security Directory
Entry 5 0001929c 00000010 Base Relocation Directory [.reloc]
Entry 6 00000000 00000000 Debug Directory
Entry 7 00000000 00000000 Description Directory
Entry 8 00000000 00000000 Special Directory
Entry 9 00000000 00000000 Thread Storage Directory [.tls]
Entry a 00018924 000000a4 Load Configuration Directory
Entry b 00000000 00000000 Bound Import Directory
Entry c 00000000 00000000 Import Address Table Directory
Entry d 00000000 00000000 Delay Import Directory
Entry e 00000000 00000000 CLR Runtime Header
Entry f 00000000 00000000 Reserved
There is an import table in .rsrc at 0x4191dc
The Import Tables (interpreted .rsrc section contents)
vma: Hint Time Forward DLL First
Table Stamp Chain Name Thunk
Sections:
Idx Name Size VMA LMA File off Algn
0 UPX0 0000e000 00401000 00401000 00000400 2**2
CONTENTS, ALLOC, CODE
1 UPX1 00009a00 0040f000 0040f000 00000400 2**2
CONTENTS, ALLOC, LOAD, CODE, DATA
2 .rsrc 00000400 00419000 00419000 00009e00 2**2
CONTENTS, ALLOC, LOAD, DATA
SYMBOL TABLE:
no symbols
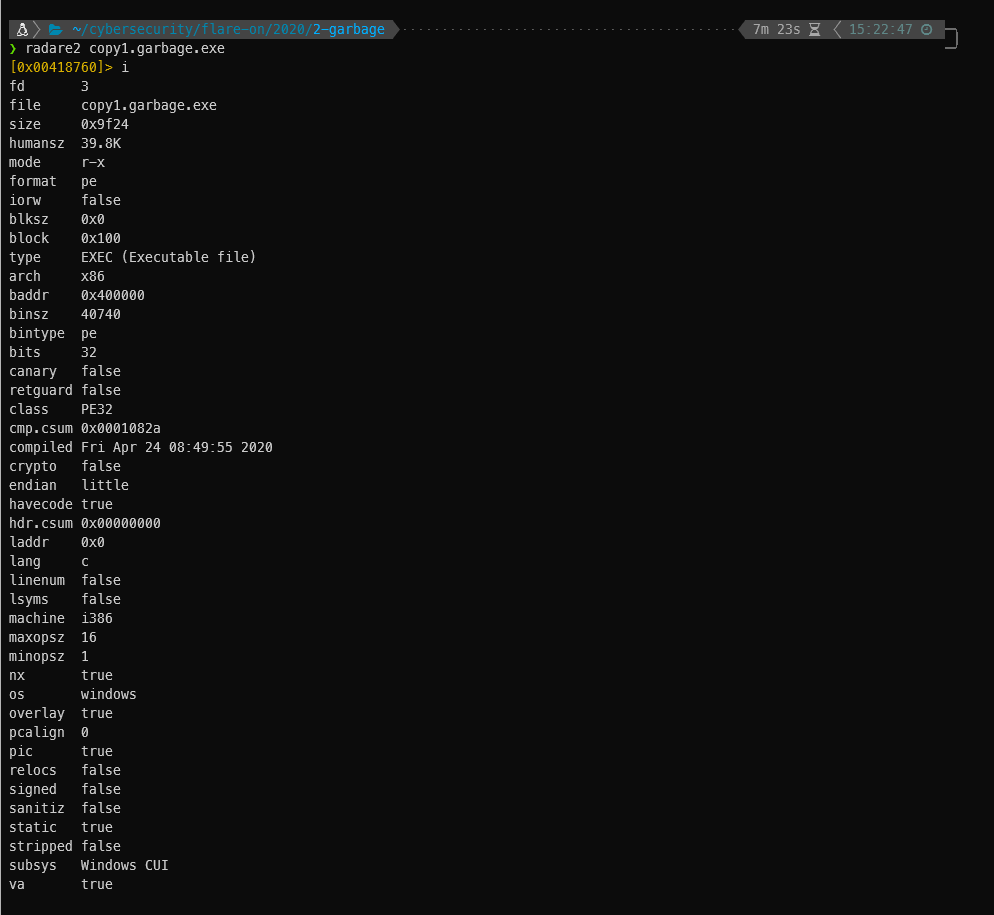
Start in debug mode, then continue to main.
I couldn’t figure out how to manually do this, but a 30-day trial of PE Explorer did it for me while opening the binary.
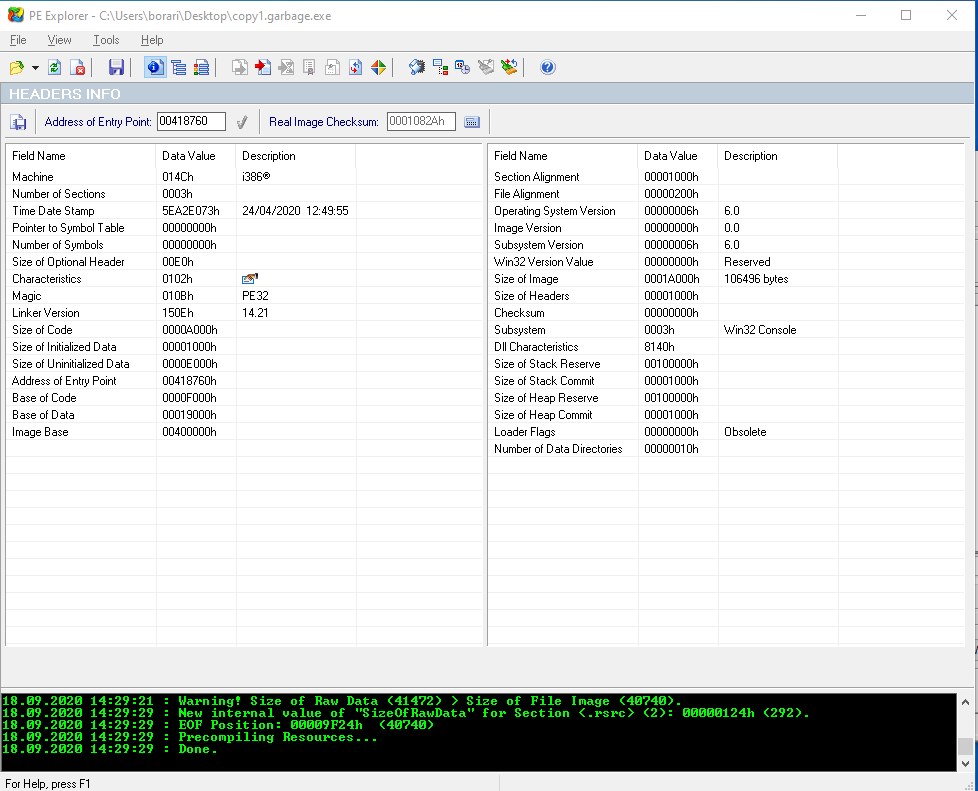
And now I can open the file in Ghidra without issue!
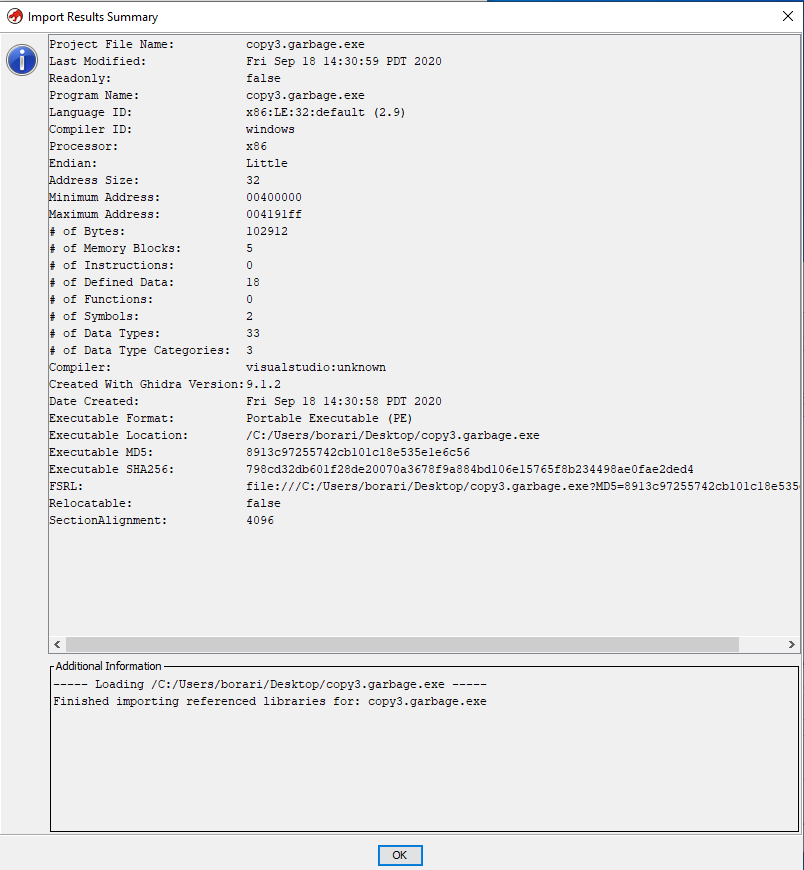
What the fuck!?!??! So I tried to add the xml manifest file, but the overlay size was still wrong. I had read some stuff about the overlay file not being necessary for the compiled program, it's extra
for users, so I hypothesized that I needed to pad out the file in order for upx to decompress the PE correctly. I don't know how to manually find the size of the file based of the upx header, it's supposed to be near the ASCII P at the end of the file I think. I just used a trial version of PE Explorer and it would tell me each time I tried to open the file. I wound up just padding the file with 00 hex characters with hexeditor until I got to the required 41472 bytes. Once I did, I was able to decompress the file with upx -d.
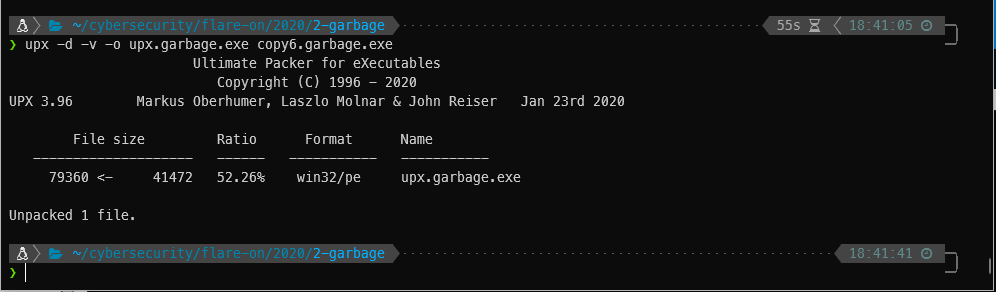
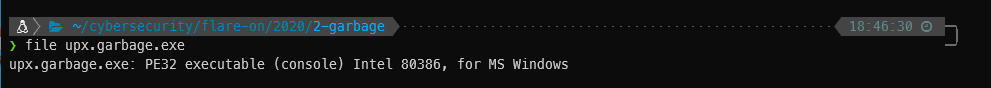
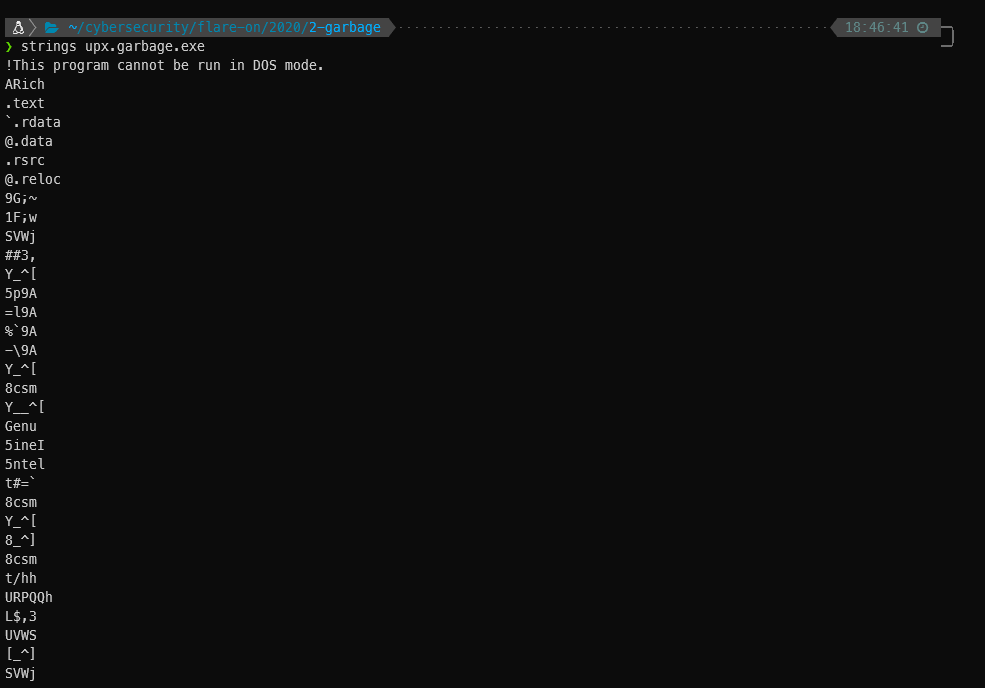
Now the file says it’s a PE32 executable like it did before, but strings has a ton more output.
Also now I can load the exe into IDA Free.
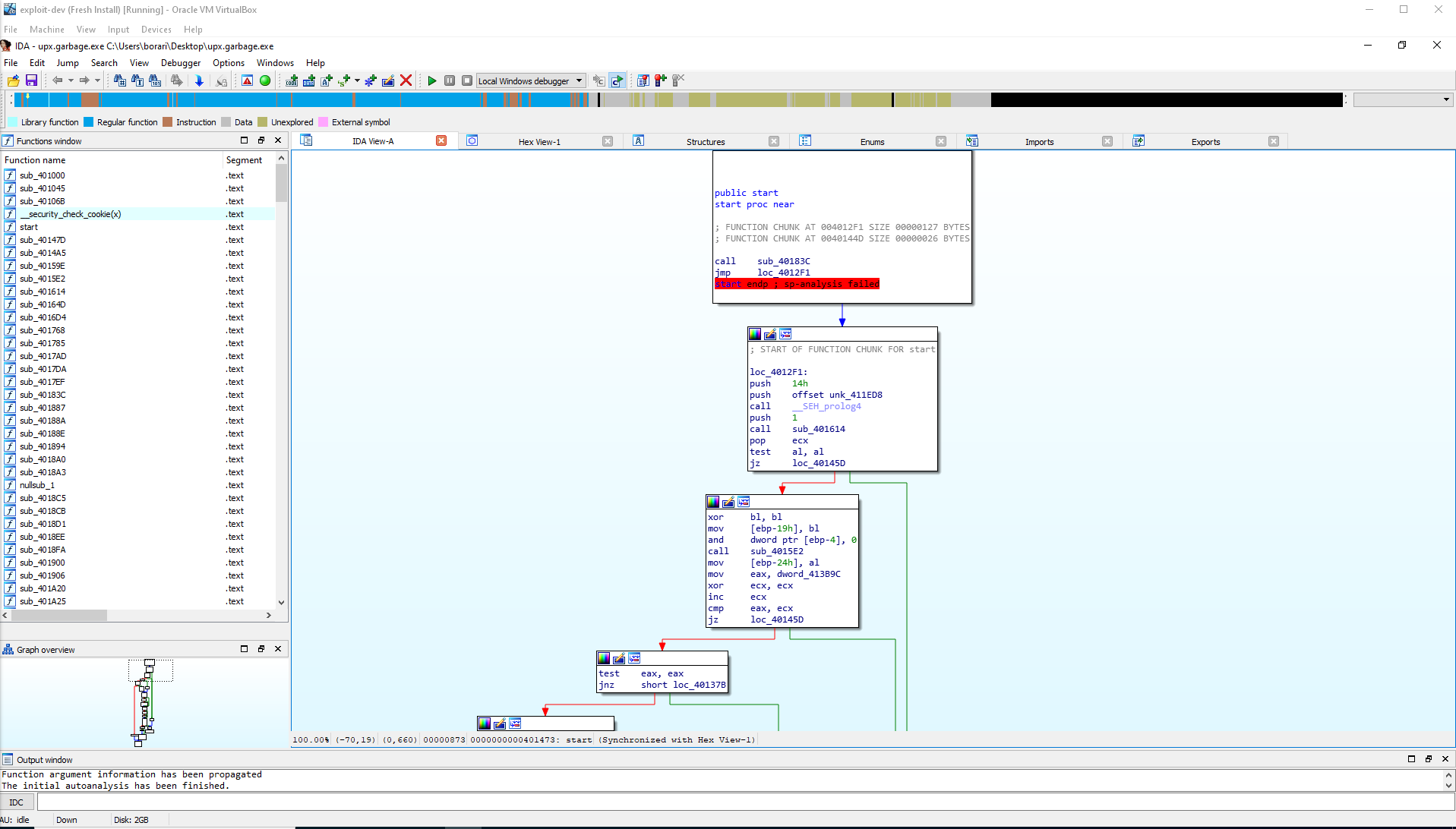
I never actually finished this challenge... :(.